HIPAA Compliance Checklist for 2025

SaaS adoption in enterprises has crossed a tipping point. Most large organizations now run hundreds of applications, many of them purchased outside central IT.
Industry studies show enterprises use 275+ SaaS applications on average, yet IT teams typically manage visibility into less than 60% of them. The rest live across departments, cards, and shadow workflows.
This is why a strong SaaS governance checklist is no longer optional. Without structured governance, SaaS spend grows unchecked, security reviews fall behind, and compliance becomes reactive instead of repeatable.
In this blog, you’ll learn what SaaS governance really means at an organizational level, why enterprises need an org-wide checklist, what controls matter most, and how to operationalize governance at scale.
TL;DR
- Enterprises use hundreds of SaaS apps, making governance difficult without structure.
- A SaaS governance checklist creates ownership, visibility, and control across teams.
- Org-level SaaS governance reduces security, compliance, and renewal risks.
- Continuous reviews are more effective than one-time governance efforts.
- CloudEagle.ai helps enforce SaaS governance at scale through automation and visibility.
1. What Is SaaS Governance?
SaaS governance is the organizational system of ownership, visibility, and control applied across all SaaS applications used by the enterprise.
It ensures applications are intentionally adopted, securely accessed, continuously reviewed, and aligned with business and compliance requirements.
At scale, SaaS governance typically covers:
- How new SaaS tools are requested, reviewed, and approved
- Who owns each application from a business and risk perspective
- How access is granted, reviewed, and removed
- How usage, risk, and compliance are monitored over time
- How renewal and expansion decisions are made
2. Why Enterprises Need an Org-Level SaaS Governance Checklist
As SaaS stacks grow, informal controls stop working. Enterprises need consistency, not case-by-case decisions.
A. SaaS ownership is fragmented across teams
In most enterprises, SaaS governance is spread across IT, security, procurement, finance, and business units, with no single system tying ownership together.
Without a clear SaaS governance framework, this fragmentation leads to:
- Applications with no defined business or risk owner
- Procurement approving tools without usage or access context
- IT manages access without understanding business criticality
- Security reviews are conducted once and never revisited
- Finance approves renewals without knowing if the app is still needed
A structured SaaS governance checklist forces ownership clarity at every stage, request, access, review, and renewal.
B. App sprawl grows faster than security reviews
SaaS adoption no longer follows formal procurement paths. Teams adopt tools through free trials, departmental budgets, and embedded AI features, often bypassing security entirely.
This creates SaaS risk management gaps, such as:
- Applications handling sensitive data without a security review
- AI features are enabled inside SaaS apps by default
- Tools operating outside SSO and access logging
- No risk tiering or security classification for new apps
- Security reviews are delayed until after incidents or audits
Research indicates 30–40% of enterprise SaaS applications are adopted outside approved workflows, making reactive governance ineffective at scale.
C. Compliance and audit readiness breaks at scale
Auditors expect evidence that SaaS compliance controls are enforced consistently across all applications, not just the most critical ones. At scale, manual evidence collection breaks down.
Common audit challenges include:
- Missing or outdated access review records
- Inconsistent enforcement of governance controls
- Unclear ownership during audits
- Shadow IT and Shadow AI exposure
- Last-minute scrambling for evidence
Audit advisory data shows over 45% of SaaS-related audit findings stem from access governance and ownership gaps, not missing policies.
3. SaaS Governance Checklist (Org-Level)
An enterprise SaaS governance checklist is not a lightweight best-practices list. It is a structured operating model that defines how SaaS is discovered, approved, governed, reviewed, and retired across the organization.
Below is a comprehensive, org-level SaaS governance checklist designed for enterprises managing hundreds of applications across multiple teams and regions.
A. Centralized SaaS inventory across the enterprise
SaaS governance begins with visibility. A centralized inventory is the single source of truth for every SaaS application used across the organization.
This inventory must go far beyond a procurement list.

A mature inventory should include:
- Applications discovered through multiple signals
SSO and identity providers, finance and expense systems, browser activity and login telemetry, and departmental or card-based purchases.
Comprehensive application coverage
Paid applications, free and freemium tools, active trials and pilots, and AI-enabled or embedded AI tools. - Detailed application context
Business purpose and primary use case, data sensitivity and risk tier, compliance relevance, and deployment scope (team, department, or enterprise-wide).
Most enterprises underestimate their SaaS footprint by 40–50%, which directly weakens SaaS risk management and compliance posture.
B. Standardized SaaS intake and approval process
Uncontrolled SaaS adoption is the root cause of sprawl. A standardized intake process ensures governance begins before a tool enters the environment.
An enterprise-grade intake process should:
- Require a formal submission for every SaaS request
No tool should be introduced without a documented business request. - Capture critical request details upfront
Business justification, intended users, data types, and the expected duration of use. - Automatically identify overlaps and redundancy
Existing tools that meet the same need and approved alternatives are already present in the SaaS stack. - Route approvals to the right stakeholders
IT for architecture and integration review, Security for risk and data assessment, Legal for contractual and data protection terms, and Finance for budget ownership. - Assign clear ownership at approval time
Ensuring accountability throughout the application lifecycle.
This control prevents duplication, reduces Shadow IT, and enforces consistency across the SaaS governance framework.
C. Security, legal, and compliance review before adoption
Every SaaS application introduces security, legal, and compliance risks. These risks must be assessed before any sensitive data or users are onboarded.
A robust governance checklist requires pre-adoption validation of:
- Vendor security posture and controls
Including certifications, security architecture, and internal control frameworks. - Data handling and residency practices
How data is processed, retained, and stored across regions. - Regulatory and compliance requirements
Obligations tied to the application’s industry, geography, and data usage. - AI-specific risk considerations
Training data usage, prompt and interaction retention, third-party model dependencies, and sub-processors or downstream integrations.
Skipping or rushing this step is one of the most common reasons SaaS compliance controls fail during audits.
D. Identity and access governance alignment (SSO, RBAC)
Access is where most SaaS risk concentrates. Even secure tools become dangerous when access is unmanaged.
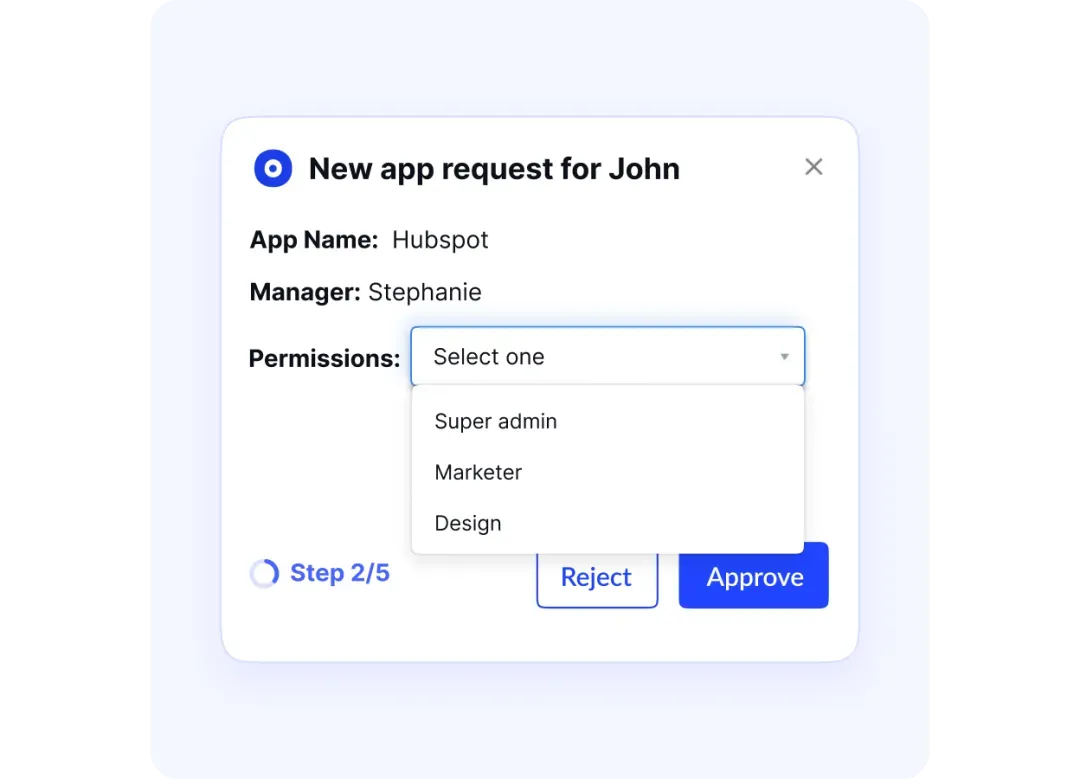
An org-level SaaS governance checklist must enforce:
- SSO integration wherever technically feasible
To centralize authentication and reduce credential sprawl. - Role-based access control aligned to job functions
Ensuring users only receive the access required for their role. - Clear separation of access levels
Standard users, power users, administrators, and super-administrators. - Explicit approval for elevated privileges
With justification and time-bound access where possible. - Automated joiner–mover–leaver workflows
To prevent orphaned accounts and lingering access. - Regular access reviews for high-risk applications
Ensuring access remains appropriate over time.
Access governance is foundational to SaaS risk management. Nearly half of enterprises report former employees retaining SaaS access, making this control non-negotiable.
E. Ongoing risk, usage, and relevance reviews
SaaS governance does not end after onboarding. Usage patterns, risk profiles, and business needs change constantly.
Ongoing reviews should evaluate:
- Active vs inactive users and licenses
- Frequency and depth of application usage
- Underutilized or redundant applications
- Changes in data sensitivity or risk exposure
- Drift in security configurations over time
- Continued alignment with business objectives
This control ensures SaaS governance remains continuous instead of collapsing into periodic cleanups.
4. Where Org-Level SaaS Governance Commonly Breaks
Even enterprises with defined policies and tooling struggle to enforce SaaS governance consistently. The issue isn’t a lack of awareness; it’s the gap between documented governance and how SaaS is actually adopted, used, and renewed across teams.
Without a strong SaaS governance checklist operating continuously, these breakdowns appear predictably.
A. Shadow IT and Shadow AI adoption
When SaaS governance feels slow or unclear, teams bypass it. Business units typically adopt tools directly, often utilizing free plans, trials, or embedded AI features within existing SaaS applications.
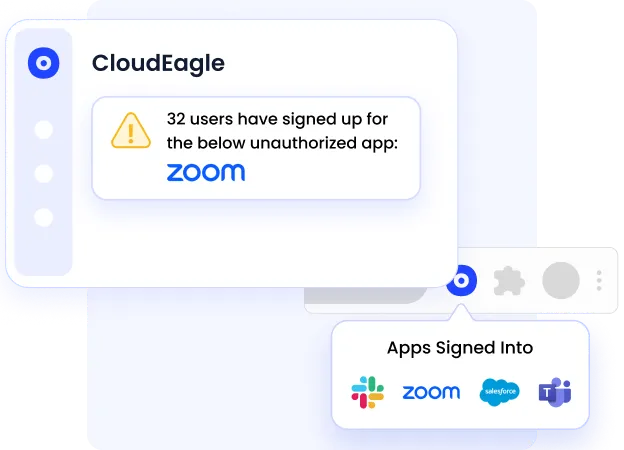
This creates serious gaps in SaaS risk management.
Common breakdowns include:
- SaaS tools purchased on corporate cards without intake or approval
- AI tools or AI features enabled by default inside approved SaaS apps
- Free or trial tools being used for production workflows
- Applications operating outside SSO and access logging
- No security or compliance review before data exposure
Without continuous discovery, Shadow IT and Shadow AI expand faster than any SaaS governance framework can contain.
B. No accountability after procurement
Many organizations enforce SaaS governance only at the point of purchase. Once the contract is signed, ownership becomes informal or disappears entirely.
Over time, this weakens both governance and compliance.
Typical failure patterns include:
- Applications with no active business or risk owner
- Access reviews are skipped after onboarding
- Usage and risk are never reassessed post-purchase
- Renewals are approved automatically without governance input
- Security and compliance issues left unresolved
Org-level SaaS governance requires ownership through the full lifecycle, not just during procurement.
C. Governance treated as a one-time exercise
Some enterprises treat SaaS governance as an annual cleanup or audit-prep activity. Unfortunately, SaaS environments evolve daily, with new users, new integrations, and new risks.
This mindset leads to:
- Outdated SaaS inventories
- Drift in access permissions and roles
- Weak enforcement of SaaS compliance controls
- Governance policies that exist only on paper
- Audit readiness that collapses under scrutiny
Effective SaaS governance is continuous. Without ongoing reviews and enforcement tied to a living SaaS governance checklist, even mature governance programs erode quickly.
5. How CloudEagle.ai Enables Org-Level SaaS Governance
Most enterprises already know what SaaS governance should look like.
The real challenge is executing it consistently across hundreds of applications, teams, and renewals.
This is where CloudEagle.ai comes in.
Instead of adding another point solution, CloudEagle acts as the operating system for SaaS governance, connecting visibility, access, risk, spend, and compliance into one enforceable model.
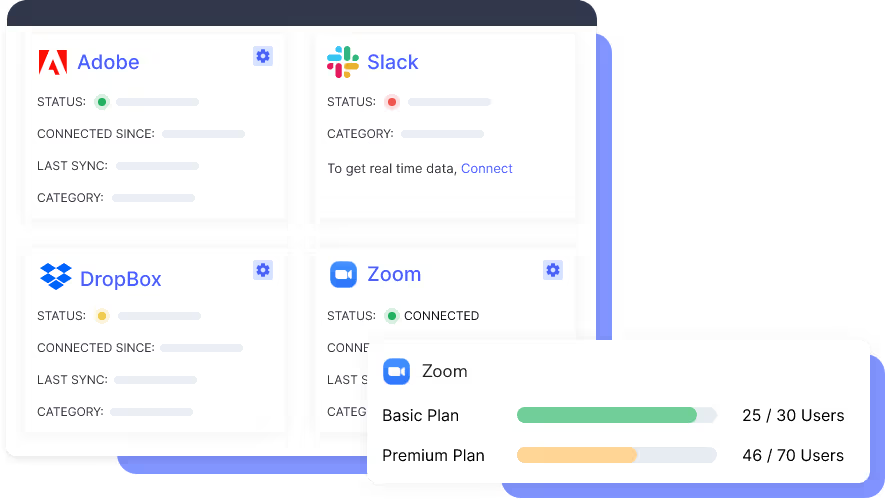
A. SaaS Visibility Across the Enterprise
In most organizations, SaaS data lives in silos.
SSO shows some apps. Finance shows spending. Security sees risk, but never the full picture.
CloudEagle changes that.

What changes with CloudEagle:
- One centralized view of all SaaS applications (approved + Shadow IT + Shadow AI)
- Unified visibility across usage, licenses, access, and spend
- Clear ownership and accountability are mapped to every app
Governance outcome:
SaaS governance decisions are based on complete visibility, not assumptions.
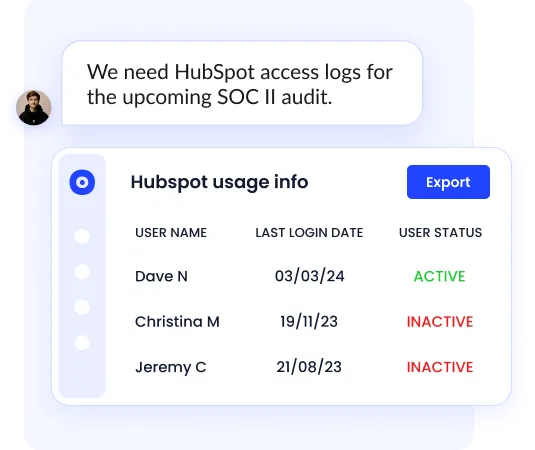
B. Usage and License Intelligence
Many tools stop at dashboards. CloudEagle focuses on decisions.
By applying AI-driven analysis to usage and licenses, CloudEagle surfaces what actually matters for governance.
Instead of asking:
“Which apps do we have?”
Teams can answer:
- Which apps are actively used vs underutilized
- Where duplicate tools exist across departments
- Which licenses should be reclaimed or downgraded
- Which apps no longer justify renewal
Governance outcome:
Usage becomes an input into SaaS risk management, renewals, and rationalization, not just reporting.
C. Access Governance Without Manual Overhead
Access governance is where most SaaS governance frameworks break.

Reviews are manual. Offboarding is inconsistent. Evidence is scattered.
CloudEagle automates this layer end-to-end.
What this enables:
- Automated onboarding and offboarding across SaaS apps
- Role-based access enforcement aligned to policy
- Continuous access reviews for audit readiness
- Immediate removal of orphaned and over-privileged access
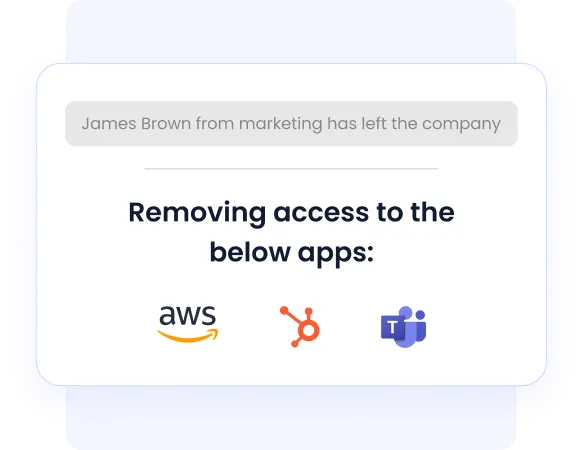
Governance outcome:
Access governance stays enforced continuously, without relying on spreadsheets or reminders.
D. Renewal and Spend Governance
SaaS governance often stops after procurement. CloudEagle deliberately extends it into renewals.
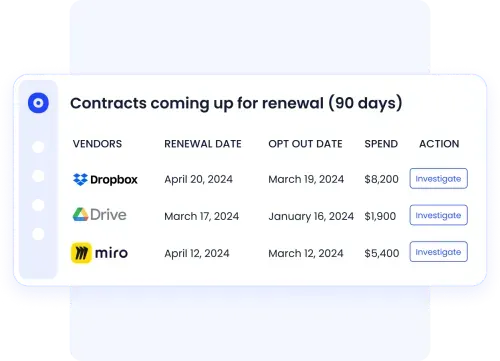
By connecting usage, contracts, and pricing, CloudEagle ensures renewals are governed, not automatic.
With CloudEagle, teams can:
- See upcoming renewals with usage and risk context
- Benchmark pricing before negotiations
- Prevent auto-renewals without governance review
- Support renegotiation or consolidation decisions
Organizations typically reduce 10–30% of SaaS spend by enforcing governance at renewal time.
Governance outcome:
Spend governance becomes proactive, not reactive.
E. Security and Compliance Support
CloudEagle supports SaaS compliance controls by embedding governance into workflows rather than treating compliance as an audit-only activity.

This means:
- Continuous evidence for access reviews and ownership
- Faster SOC 2 and ISO audit preparation
- Clear visibility into Shadow IT and Shadow AI exposure
- Fewer last-minute audit scrambles
Governance outcome:
Compliance becomes a byproduct of good SaaS governance, not a separate project.
F. No-Code Workflows That Keep Governance Moving
Governance fails when it’s slow. CloudEagle removes friction with no-code workflows that teams actually use.
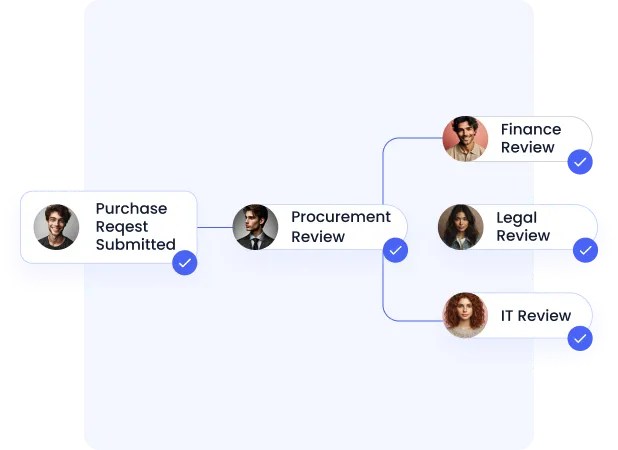
These workflows power:
- SaaS intake and approval
- Access certifications
- Renewal reviews
- Procurement collaboration
Governance outcome:
Policies are enforced through workflows, not PDFs.
Final Thoughts
SaaS governance becomes complex as enterprises scale. With hundreds of applications in use, ownership fragments, risk accumulates, and compliance controls weaken without a structured approach.
A well-defined SaaS governance checklist helps enterprises create consistency across discovery, access, risk, and renewals. When governance is applied continuously, not as a one-time exercise, SaaS becomes manageable instead of chaotic.
CloudEagle.ai helps organizations operationalize SaaS governance by turning visibility into enforceable controls across the SaaS lifecycle, supporting risk management, compliance, and cost optimization at scale.
Book a free demo to see how CloudEagle.ai enables org-level SaaS governance.
Frequently Asked Questions
1. How is SaaS governance different from SaaS management?
SaaS management focuses on administering tools and licenses, while SaaS governance defines ownership, risk controls, access policies, and accountability across the entire organization.
2. When should enterprises implement a SaaS governance framework?
Enterprises should implement a SaaS governance framework once SaaS adoption becomes decentralized across teams or when the number of applications grows beyond what IT can manually manage.
3. Which teams should be involved in SaaS governance?
Effective SaaS governance requires collaboration between IT, security, procurement, finance, legal, and business stakeholders, with clearly defined responsibilities.
4. How does SaaS governance support audit and compliance efforts?
SaaS governance supports audits by maintaining consistent access controls, ownership records, and evidence for reviews, reducing last-minute compliance gaps.
5. What risks increase when SaaS governance is not enforced?
Without SaaS governance, organizations face higher software spend, unmanaged access, Shadow IT exposure, audit failures, and increased security and data protection risks.

%201.svg)










.avif)




.avif)
.avif)




.png)









