HIPAA Compliance Checklist for 2025

Audit readiness is no longer something enterprises think about once a year. With increasing regulatory scrutiny, customer audits, and internal risk reviews, compliance teams are expected to stay audit-ready at all times.
Yet many organizations still approach audits reactively. Evidence is scattered across tools, access reviews are manual, and teams scramble to prove controls when auditors ask. That’s where a structured audit readiness checklist becomes essential.
According to a Deloitte compliance survey, over 60% of enterprises cite evidence collection and access validation as their biggest audit bottlenecks.
In this blog, you’ll learn what audit readiness really means, why it matters for enterprise compliance teams, what evidence auditors expect, why teams fail readiness audits, and how modern platforms support continuous audit readiness.
TL;DR
- Audit readiness means being able to prove compliance at any time, not just during audits.
- Access governance, logs, vendor evidence, and ownership are the most reviewed areas.
- Teams fail audits due to scattered evidence, Shadow IT, and manual processes.
- A structured audit readiness checklist reduces last-minute scramble and audit risk.
- Platforms like CloudEagle.ai enable continuous, audit-ready access governance.
1. What Is Audit Readiness?
Audit readiness is the ability of an organization to demonstrate compliance controls, evidence, and governance processes at any point in time, without last-minute scrambling. It means policies, access controls, logs, and documentation are always up to date and easy to retrieve.
True audit readiness goes beyond documentation. It requires consistent execution of controls, clear ownership, and traceable evidence across systems. Auditors don’t just check whether controls exist; they verify whether they are operational and repeatable.
For enterprise teams, audit readiness is an ongoing discipline, not a milestone.
2. Why Audit Readiness Matters?
Audit readiness directly affects compliance outcomes, operational efficiency, and business credibility. Organizations that treat audits as one-off events often face repeat findings, delays, and avoidable risk.
A. Compliance Pressure
Enterprises today face overlapping audits, SOC 2, ISO 27001, SOX, GDPR, customer security reviews, and internal audits. Without a strong audit readiness framework, teams duplicate effort every cycle.
- Repeated evidence collection across audits
- Inconsistent controls mapped to frameworks
- Manual coordination between teams
- High audit fatigue and delays
An effective audit readiness & support approach reduces friction by reusing evidence and controls across frameworks.
B. Risk Mitigation
Audits often uncover risks that existed long before the audit began, such as orphaned access, Shadow IT, missing logs, or outdated policies.
- Dormant or excessive user access
- Unmonitored SaaS and Shadow IT
- Gaps in logging and activity records
- Policies not aligned with actual usage
Maintaining audit-ready access governance helps teams detect and remediate issues early, lowering the risk of audit failures or security incidents.
C. Regulatory Demands
Regulators increasingly expect proof of continuous compliance, not periodic snapshots.
- Ongoing access review
- Incident response documentation
- Vendor and third-party oversight
- Verifiable audit trails
Organizations that invest in audit readiness stay prepared for evolving regulatory requirements, without operational disruption.
3. Audit Readiness Checklist
A strong audit readiness checklist focuses on evidence, ownership, and traceability. Auditors want to see that controls are documented, enforced, and reviewed regularly.
Below are the core areas enterprise compliance teams must prepare.
A. Access governance evidence
Access controls are one of the most scrutinized audit areas. Auditors expect clear proof of who has access to what, and why.

Checklist focus areas include:
- Role-based access controls
- Joiner-mover-leaver processes
- Periodic access reviews
- Privileged access management
- Evidence of timely deprovisioning
Incomplete access evidence is a common audit finding.
B. Contracts, policies & renewal docs
Auditors validate whether policies exist and are enforced consistently. They also review contracts and renewal terms for compliance obligations.
Checklist focus areas include:
- Security and compliance policies
- Vendor contracts and SLAs
- Renewal dates and approvals
- Policy review records
- Policy acknowledgment tracking
Policies without evidence rarely pass audits.
C. User activity logs
Logs prove that controls are operational. Auditors often request logs to verify access usage, system changes, and incident timelines.

Checklist focus areas include:
- Authentication and login logs
- Admin and configuration change logs
- Application usage logs
- Log retention policies
- Monitoring and alerting records
Missing or inconsistent logs weaken audit posture.
D. Vendor compliance reports
Third-party risk is a growing audit focus. Enterprises must show how vendors are evaluated and monitored.
Checklist focus areas include:
- Vendor risk assessments
- SOC 2 / ISO reports from vendors
- Vendor access reviews
- Offboarding procedures
- Ongoing vendor monitoring evidence
Vendor gaps can create audit failures even when internal controls are strong.
E. Incident documentation
Auditors expect documented and tested incident response processes. This includes how incidents are identified, handled, and reviewed.
Checklist focus areas include:
- Incident response plans
- Incident tickets and timelines
- Root cause analysis reports
- Communication records
- Post-incident reviews
Preparation matters more than the number of incidents.
F. Ownership mappings
Every control must have a clear owner. Auditors look for accountability, not shared responsibility.
Checklist focus areas include:
- Named control owners
- RACI or ownership matrices
- Approval workflows
- Evidence of owner reviews
- Management oversight
Lack of ownership is a frequent audit gap.
4. Audit Readiness Template
An audit readiness template helps teams centralize controls, evidence, owners, and review cycles in one place. It transforms audit prep from a reactive task into a continuous process.
Using a standardized template ensures consistency across audits and reduces time spent chasing documentation.
5. Why Teams Fail Audit Readiness?
Most audit failures aren’t caused by missing controls; they happen because controls aren’t provable, consistent, or centralized.
A. No Centralized Evidence
When evidence lives across emails, shared drives, and disconnected tools, audits slow down, and gaps appear.
- Evidence scattered across teams and systems
- Delays in responding to auditor requests
- Inconsistent or outdated documentation
- Higher risk of missed or incomplete proof
Auditors expect fast, complete, and repeatable evidence; centralization is critical for sustained audit readiness.
B. Shadow IT Gaps
Unapproved tools frequently operate outside governance and monitoring boundaries.
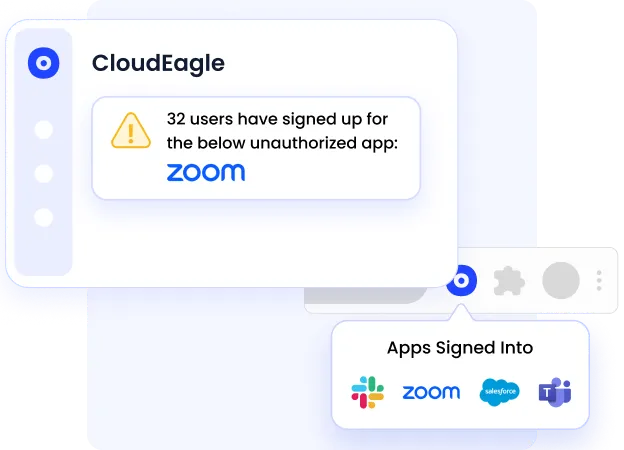
- No access controls or ownership
- Missing activity logs
- No vendor or compliance reviews
- Blind spots in data usage
Without visibility into Shadow IT, teams struggle to prove comprehensive access and compliance governance during audits.
C. Manual Complexity
Spreadsheet-driven processes break down at scale and weaken audit confidence.
- Human error in access reviews
- Inconsistent approval workflows
- Missing or unverifiable audit trails
- High operational overhead
Automation is now essential for reliable, scalable, enterprise-grade audit readiness.
6. How CloudEagle.ai Helps Teams Achieve Audit Readiness?
1. Complete SaaS Application & Access Visibility
CloudEagle.ai provides a comprehensive and continuously updated inventory of all SaaS applications in use across the organization, including sanctioned, unsanctioned, and free tools.

It maps users, roles, and access levels across each application, creating a reliable system of record that auditors expect.
- Discovers 100% of SaaS applications, including shadow IT
- Maps users, roles, and privilege levels per application
- Covers applications outside SSO and traditional IAM tools
- Eliminates access blind spots during audits
2. Automated, Audit-Ready Access Reviews
CloudEagle.ai automates periodic access reviews to ensure users have appropriate access aligned with their roles.
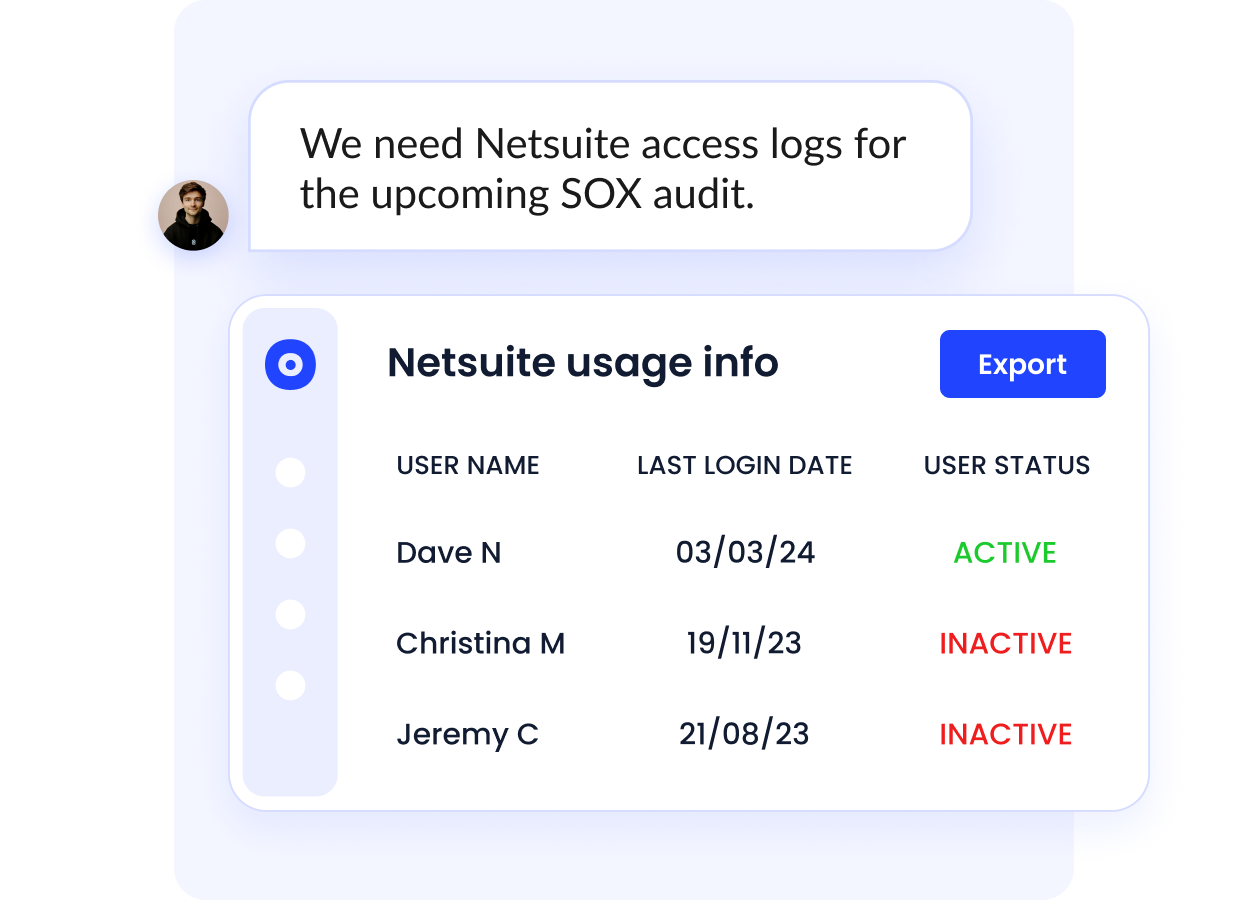
Reviews are structured, repeatable, and fully documented, reducing manual effort while improving audit defensibility.
- Configurable access review cycles (monthly, quarterly, continuous)
- Identification of inactive, orphaned, and over-privileged users
- Direct approval, revocation, or modification of access
- System-generated evidence of the reviewer, timestamp, and action
3. Consistent Onboarding and Offboarding Controls
CloudEagle.ai enforces standardized onboarding and offboarding processes by integrating with HR systems and identity providers.

Access is provisioned and revoked automatically based on employee lifecycle events, ensuring compliance with least-privilege and timely deprovisioning requirements.
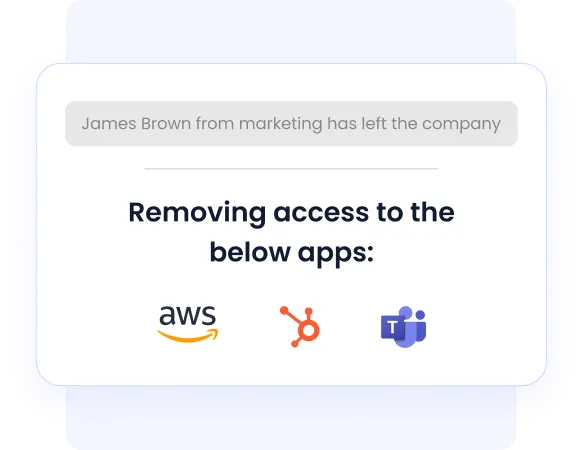
- Automated provisioning based on role and policy
- Immediate deprovisioning upon employee exit
- Coverage for applications not managed by the IDP
- Reduced the risk of ex-employees retaining access
4. Centralized Audit Evidence and Activity Logs
CloudEagle.ai maintains immutable, centralized logs of all access-related activity.
This ensures audit evidence is readily available without relying on disparate tools, emails, or manual documentation.
- Detailed logs for access changes, approvals, and removals
- Records of access reviews and certifications
- One-click export of audit-ready reports
- Clear traceability for auditors and compliance teams
5. Shadow IT Detection and Risk Mitigation
CloudEagle.ai continuously identifies unauthorized and unmanaged SaaS applications using multiple data signals.

This allows organizations to demonstrate proactive governance and risk management to auditors.
- Detection of shadow IT via login, spend, and usage data
- Identification of risky or non-compliant applications
- Visibility into duplicate and redundant tools
- Documented remediation actions for audit purposes
6. Policy-Based Access Governance
CloudEagle.ai enables consistent enforcement of access policies across the organization.
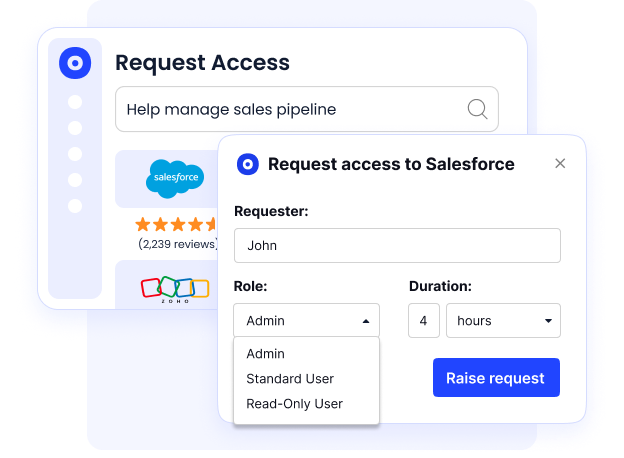
Policies are applied uniformly, reducing ad-hoc access decisions and supporting compliance with regulatory and security frameworks.
- Role-based access controls
- JIT access for contractors and temporary staff
- Continuous monitoring to prevent privilege creep
- Alignment with least-privilege principles
7. Continuous Audit Readiness
CloudEagle.ai shifts audit readiness from a point-in-time activity to a continuous state.

Teams can monitor compliance posture in real time and address gaps proactively, rather than reacting during audit cycles.
- Real-time dashboards for access and compliance posture
- Early identification of audit gaps
- Reduced audit preparation time and effort
- Improved confidence during external and internal audits
7. Conclusion
Audit readiness is no longer optional for enterprise compliance teams. As audits become more frequent and complex, organizations need repeatable processes, clear ownership, and reliable evidence to maintain compliance.
A structured audit readiness checklist helps teams prepare proactively. When access governance, logging, vendor oversight, and incident documentation are always up to date, audits become predictable instead of disruptive.
CloudEagle.ai makes audit readiness practical by unifying access governance, evidence tracking, and compliance workflows across the SaaS stack, helping teams stay audit-ready year-round.
Book a free demo to see how CloudEagle.ai helps enterprise teams achieve continuous audit readiness.
Frequently Asked Questions
1. How to ensure audit readiness?
Ensure audit readiness by maintaining documented controls, centralized evidence, regular access reviews, and continuous monitoring instead of one-time preparation.
2. How often should companies run audit readiness assessments?
Most enterprises conduct internal audit readiness assessments quarterly, with lighter monthly reviews for high-risk controls.
3. What helps speed up SOC 2 readiness?
Automated access reviews, centralized evidence collection, and real-time visibility into users and vendors significantly accelerate SOC 2 readiness.
4. What are the 7 E’s of auditing?
The 7 E’s commonly refer to economy, efficiency, effectiveness, ethics, equity, environment, and evidence—used to evaluate audit outcomes.
5. What are the 5 keys of compliance?
Clear policies, defined ownership, consistent enforcement, documented evidence, and continuous review form the foundation of strong compliance programs.

%201.svg)










.avif)




.avif)
.avif)




.png)









