HIPAA Compliance Checklist for 2025

When you think of cybersecurity, the image that comes to mind is usually an external hacker forcing their way into your systems. But what if the real danger lies within your own organization?
These threats don’t always come from malicious insiders with bad intentions. Sometimes, it’s a distracted employee sending confidential data to the wrong email address. Other times, it’s an external attacker hijacking a trusted account. Either way, insider incidents can be more devastating than external attacks because they exploit trust, not just technology.
That’s why enterprises must understand what is an insider threat, and more importantly, build a proactive strategy for insider threat prevention. In this guide, we’ll break down the different types of insider threats and share 10 proven strategies to help you stay protected.
TL;DR
- Understand insider threats, including malicious, negligent, compromised, and third-party insiders, to identify risks early.
- Implement key strategies like access controls, behavioral monitoring, MFA, zero-trust, and security training to reduce exposure.
- Automate access management by onboarding, offboarding, and reviewing user permissions to prevent accidental or intentional insider threats.
- Address common challenges by balancing security with employee trust, detecting subtle behaviors, and managing third-party risks.
- Leverage CloudEagle.ai with centralized dashboards, RBAC/ABAC, least privilege, and automated reviews for efficient insider threat prevention.
What is an Insider Threat?
When most people think of cybersecurity, they picture hackers breaking in from the outside. But the reality is, some of the biggest risks come from within. An insider threat happens when someone with legitimate access, like an employee, contractor, or partner, misuses that access, either intentionally or unintentionally, to compromise systems, data, or operations.
So, what is an insider threat in practice? It could be a disgruntled employee stealing sensitive files, a well-meaning staff member accidentally clicking on a phishing email, or even a contractor whose account is hijacked by a cybercriminal. Because insiders already have access, these threats are harder to detect and prevent than traditional external attacks.
In enterprises, insider threats can result in financial loss, reputational damage, and regulatory penalties. A 2024 Ponemon Institute report found that the average cost of an insider incident exceeded $15 million, making prevention a board-level priority.
What are four Insider Threats?
Insider risks can look very different depending on who’s behind them. To build effective insider threat prevention, you first need to recognize the four main types. Each carries unique challenges for security teams.
1. Malicious Insiders with Harmful Intent
Some individuals actively abuse their access to harm the organization. These are deliberate, calculated, and often the most damaging insider threats.
Key points:
- Motivated by personal gain, revenge, or competitive advantage.
- Often steal intellectual property, financial records, or customer data.
- Difficult to detect without advanced insider threat management tools.
2. Negligent Insiders Making Costly Mistakes
Many incidents stem from carelessness, not malice. Employees can unintentionally expose sensitive data or bypass security protocols.
Key points:
- Common examples: weak passwords, mishandling files, or ignoring policies.
- The root cause is usually a lack of awareness or training.
- Strong employee education is a pillar of insider threat prevention.
3. Compromised Insiders Exploited by Attackers
In this case, attackers hijack a legitimate account, using it to slip past defenses. The insider is a victim, but their account is weaponized.
Key points:
- Phishing, credential theft, and malware are common entry points.
- Attackers operate undetected under a trusted identity.
- Effective detection is critical for how to prevent insider threats.
4. Third-party Insiders with Extended Access
Partners, vendors, and contractors often require system access, but their accounts can create risks outside of direct IT control.
Key points:
- Third parties may not follow the same security standards.
- Breaches can create a hidden backdoor for attackers.
- Regular access reviews strengthen insider threat prevention.
How to Prevent Insider Threats: 10 Strategies
Understanding the different types of insider threats is only the first step. To truly safeguard your organization, you need a clear and structured roadmap for prevention. These 10 strategies will help you build a strong insider threat management program, protect sensitive assets, and balance employee trust with security.
1. Implement Strict Access Controls And Least Privilege
When it comes to insider threat prevention, access control is your first line of defense. Many enterprises unintentionally grant employees broader permissions than they actually need. This creates unnecessary exposure; if an account is misused, either maliciously or accidentally, it can open the door to serious insider threats.
The principle of least privilege ensures that users can only access the minimum resources required for their role. Not only does this reduce the risk of data misuse, but it also makes it easier to track down irregular activity. Strong insider threat management starts with strict access boundaries.
Key points:
- Apply role-based access control (RBAC) to avoid excessive permissions.
- Use temporary, time-bound access instead of permanent privileges.
- Continuously review and adjust access levels as roles evolve.
- A foundational best practice in how to prevent insider threats.
2. Monitor User Activity With Behavioral Analytics
One of the most effective ways to detect insider threats is by watching how users behave. Malicious insiders rarely act without leaving a trail, and negligent insiders often exhibit warning signs like downloading too many files or logging in at odd hours. Behavioral analytics gives security teams visibility into these patterns.
By creating baselines of normal activity, you can quickly detect unusual behavior. If someone suddenly tries to access sensitive HR files they’ve never touched before, or an employee in marketing attempts to download finance data, that’s a red flag. Continuous monitoring makes insider threat prevention proactive rather than reactive.
Key points:
- Identify anomalies such as mass file transfers or suspicious login times.
- Detect compromised insiders by monitoring unexpected behavior.
- Strengthen insider threat management with early intervention.
- Reduce dwell time by acting on alerts in real time.
3. Enforce Strong Authentication And MFA
Weak or stolen credentials are one of the most common ways insiders, especially compromised ones, gain unauthorized access. Relying on passwords alone puts enterprises at serious risk. That’s why enforcing multi-factor authentication (MFA) is a cornerstone of insider threat prevention.
MFA ensures that even if a password is stolen or guessed, an attacker cannot log in without an additional verification method. Whether it’s a one-time code, biometric scan, or hardware token, strong authentication adds an essential barrier against insider threats and account misuse.
Key points:
- Require MFA across all enterprise-critical systems.
- Deploy adaptive authentication for high-risk activities.
- Prevent compromised credentials from turning into insider threats.
- A non-negotiable step in how to prevent insider threats.
4. Automate Joiner-Mover-Leaver Processes
Employees don’t stay in one role forever; they join, get promoted, move departments, or leave. If access rights don’t keep up with these changes, it creates massive security gaps. For example, ex-employees retaining access to Salesforce or Google Workspace weeks after departure is a common insider threat scenario.
Automating joiner-mover-leaver (JML) workflows eliminates this risk. As soon as someone leaves the company, their accounts are deactivated. When they move teams, access automatically adjusts to match their new responsibilities. This is one of the most effective ways to prevent insider threats caused by overlooked permissions.
Key points:
- Automatically revoke access when employees exit.
- Instantly update permissions when roles change.
- Avoid orphaned accounts that can fuel insider threats.
- A critical part of modern insider threat management.
5. Segment Data To Minimize Exposure
Enterprises often make the mistake of keeping sensitive information too accessible. Without proper data segmentation, one insider incident could compromise your entire business. By dividing data into security zones, you minimize the damage caused if an insider gains unauthorized access.
For example, not every employee should be able to see payroll data, legal contracts, or sensitive R&D documents. By segmenting and isolating these assets, insider threat prevention becomes much more manageable, and the blast radius of any potential attack is reduced.
Key points:
- Classify data into levels: public, internal, confidential, and restricted.
- Apply stricter controls on HR, finance, and customer records.
- Reduce exposure to minimize insider threat impact.
- A smart way to enforce insider threat management.
6. Train Employees On Security Awareness
Not every insider threat is malicious; many are caused by negligence. Employees clicking on phishing emails, mishandling data, or ignoring company security policies can unintentionally cause major damage. This is why security awareness training is one of the most powerful insider threat prevention tools.
When employees are educated about risks, they become active defenders of enterprise security. Regular training on phishing recognition, password hygiene, and data handling builds a culture of vigilance and responsibility, reducing the likelihood of negligent insider threats.
Key points:
- Run phishing simulations to strengthen awareness.
- Train staff to recognize suspicious insider behavior.
- Reinforce policies around safe data handling.
- Builds an internal culture of insider threat prevention.
7. Conduct Regular Access Reviews And Audits
Even with access controls in place, permissions can expand over time without notice, a problem often called privilege creep. Regular access reviews and audits are essential for insider threat management because they ensure that no user retains unnecessary access.
By auditing permissions quarterly or even monthly, you reduce the risk of dormant or misconfigured accounts being abused. Reviews also help spot anomalies such as contractors who still have access long after their engagement ended. This is a practical step in how to prevent insider threats.
Key points:
- Schedule periodic reviews of all user permissions.
- Detect unused, expired, or excessive privileges.
- Reduce insider threat risks caused by privilege creep.
- A continuous control for strong insider threat prevention.
8. Detect Anomalies With UEBA And ITDR
Insider threats can often remain hidden until it’s too late. That’s why User and Entity Behavior Analytics (UEBA) and Identity Threat Detection and Response (ITDR) tools are vital. They analyze patterns in user activity, detecting irregularities that signal insider risks.
For example, if an employee downloads gigabytes of data outside business hours or repeatedly tries to access systems unrelated to their job, UEBA and ITDR flag these anomalies. This allows security teams to act before damage occurs, strengthening insider threat prevention.
Key points:
- Identify compromised accounts through behavioral baselines.
- Spot suspicious lateral movements across systems.
- Automate alerts for faster insider threat response.
- A proactive layer of insider threat management.
9. Establish A Zero-Trust Security Model
The traditional model of “trust but verify” no longer works against insider threats. A zero-trust security model assumes no user, device, or network can be trusted by default. Every access request must be verified, regardless of whether it comes from inside or outside the corporate network.
By adopting zero trust, enterprises close one of the biggest gaps in insider threat prevention, over-reliance on perimeter security. Zero trust continuously authenticates users, applies least privilege access, and segments systems to minimize insider risks.
Key points:
- Require continuous verification for every access attempt.
- Apply the principle of least privilege consistently across all systems.
- Strengthen defenses against both malicious and negligent insiders.
- A modern foundation for how to prevent insider threats.
10. Create An Incident Response Plan For Insider Risks
Even the best security controls cannot eliminate insider threats completely. That’s why enterprises need a dedicated incident response (IR) plan tailored to insider risks. Without one, organizations scramble when an incident occurs, wasting valuable time.
A strong insider threat IR plan outlines how to detect, contain, investigate, and recover from insider incidents. It ensures teams know their roles and can act decisively. This not only reduces damage but also helps maintain employee trust and compliance standards.
Key points:
- Define insider threat response workflows in advance.
- Assign clear roles and responsibilities during incidents.
- Conduct tabletop exercises to test readiness.
- Essential for mature insider threat management.
Challenges Of Insider Threat Prevention
Even the strongest defenses face roadblocks. Insider threat prevention is challenging because threats are often hidden within trusted environments. Enterprises must address these issues to make insider threat management truly effective.
Balancing Security With Employee Trust
Enterprises need monitoring to stop insider threats, but too much oversight can damage trust. Successful insider threat prevention depends on striking the right balance between employee privacy and strong controls.
Key points:
- Over-monitoring reduces morale and productivity.
- Weak controls create openings for insider threats.
- Transparent policies strengthen insider threat management.
Detecting Subtle Or Hidden Behaviors
Not all insider threats are obvious. Malicious insiders may act slowly, and negligent employees can create risks without realizing it. Detecting these behaviors is one of the toughest aspects of insider threat prevention.
Key points:
- Malicious insiders blend in with normal activity.
- Negligent actions often look harmless at first.
- Requires advanced insider threat detection tools.
Managing Third-Party And Contractor Risks
Third-party vendors and contractors often have access to critical systems. Without strict oversight, they can unintentionally or maliciously become insider threats.
Key points:
- Vendor accounts often lack proper monitoring.
- Compromised contractors can bypass defenses.
- Must be included in insider threat management plans.
High Cost Of Continuous Monitoring
Continuous monitoring is key to insider threat prevention, but it can be expensive. Enterprises must balance budget constraints with the need for visibility.
Key points:
- Monitoring insider activity requires advanced tools.
- High costs may slow insider threat prevention efforts.
- Automation helps reduce expenses and improve control.
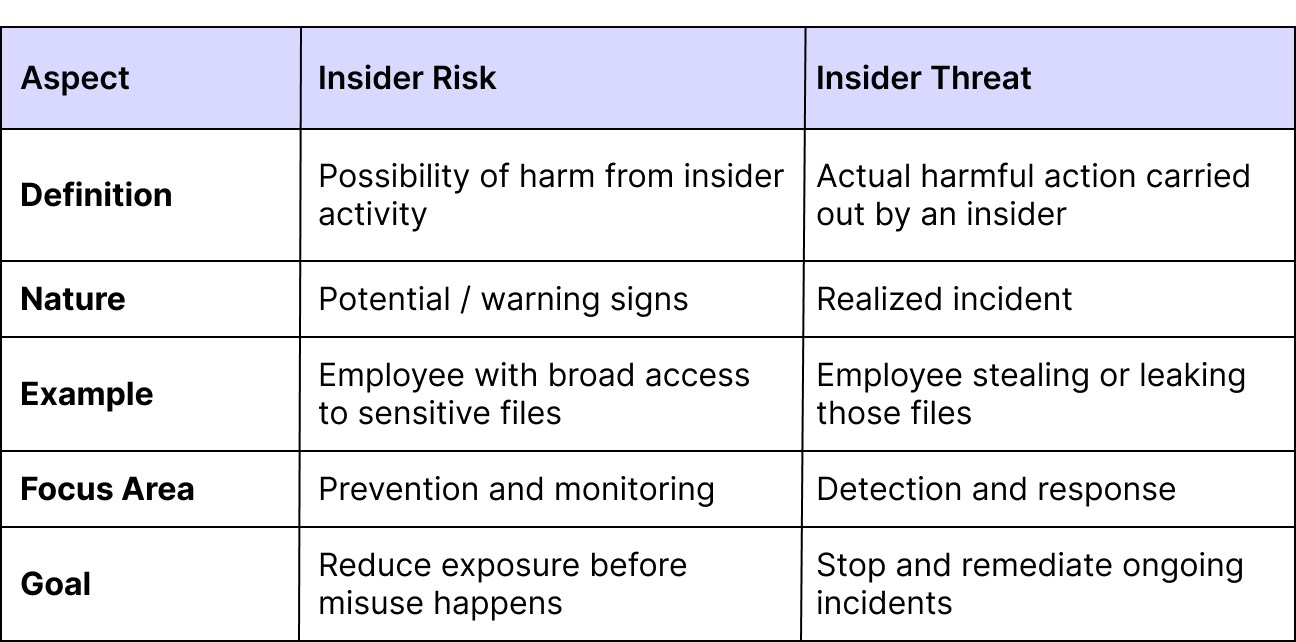
Difference Between Insider Risk and Insider Threat
When discussing insider threats, it’s easy to confuse them with insider risk. While the two concepts are closely related, they represent different stages of potential harm. Understanding this difference helps you build a proactive security strategy instead of reacting only when damage occurs.
Insider risk refers to the possibility that an employee’s action, whether intentional or accidental, could harm your business. It’s about exposure and probability. For example, an employee with excessive access permissions poses insider risk, even if they never misuse it.
Insider threats, on the other hand, are the actual incidents where harm takes place. This could be an employee stealing sensitive data, a contractor misusing login credentials, or a negligent staff member causing a breach through careless behavior.
Think of insider risk as the “warning signs” and insider threats as the “fire.” Managing both effectively is key to safeguarding your organization.
Key Differences:
- Nature:
- Insider risk = possibility of harm.
- Insider threat = actual harmful action.
- Example:
- Risk = an employee with access to sensitive financial files.
- Threat = the same employee downloading and leaking those files.
- Approach:
- Risk requires monitoring and reducing exposure.
- The threat requires an active incident response.
By distinguishing between the two, you ensure your team doesn’t just react to insider threats but also manages insider risk before it escalates into something damaging.
How CloudEagle.ai Can Mitigate Access-Related Insider Threats
Access mismanagement is one of the biggest drivers of insider threats. Without strict visibility and automated controls, employees or third parties may hold onto permissions they don’t need, creating hidden risks. CloudEagle.ai helps CISOs strengthen insider threat prevention with automation, centralized visibility, and continuous access governance.
Centralized Control & Visibility
With CloudEagle.ai, CISOs gain a single dashboard to oversee access across 500+ integrations. This makes insider threat management easier by eliminating blind spots.
- Unified view of “who has access to what.”
- Integrates with HRIS, SSO, and finance systems to sync data.
- Prevents excessive permissions that can evolve into insider threats.
Privileged Access Management
Some accounts require elevated permissions, which can easily be misused. CloudEagle.ai automates privileged access assignments, ensuring strict oversight.
- Automates the granting and revoking of elevated rights.
- Minimizes human error in privilege assignments.
- Reduces the chance of high-risk insider threats.
Role-Based Access Control (RBAC)
Manual access assignment is time-consuming and risky. With CloudEagle.ai, permissions are aligned with job functions, simplifying insider threat prevention.
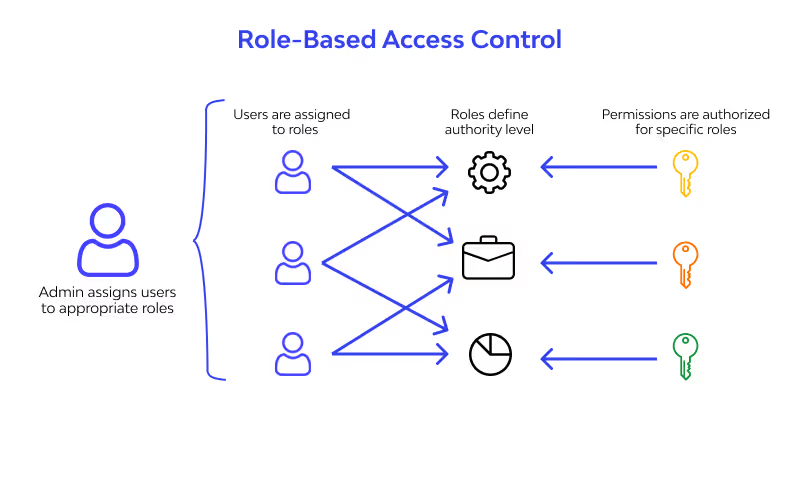
- Groups employees by role and grants necessary access.
- Prevents unnecessary exposure to sensitive apps.
- Scales easily as organizations grow.
Attribute-Based Access Control (ABAC)
CloudEagle.ai adds flexibility by enforcing access based on user attributes, helping CISOs understand how to prevent insider threats in dynamic environments.
- Just-in-time access for temporary needs.
- Location-based access to block risky logins.
- Automatic revocation after time-based access expires.
Principle of Least Privilege (PoLP)
To minimize risks, CloudEagle.ai enforces least privilege access at all times. This reduces exposure even if an account is compromised.
- Adjusts permissions continuously based on roles.
- Ensures employees only access essential systems.
- Limits damage from potential insider threats.
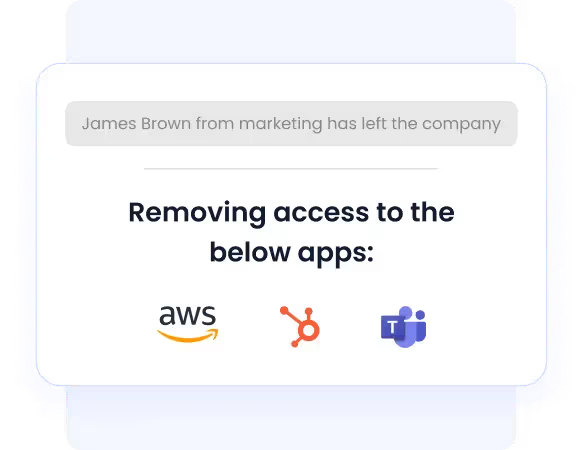
Employee Onboarding & Offboarding
Delayed provisioning or deprovisioning often creates insider risks. CloudEagle.ai automates the entire lifecycle.
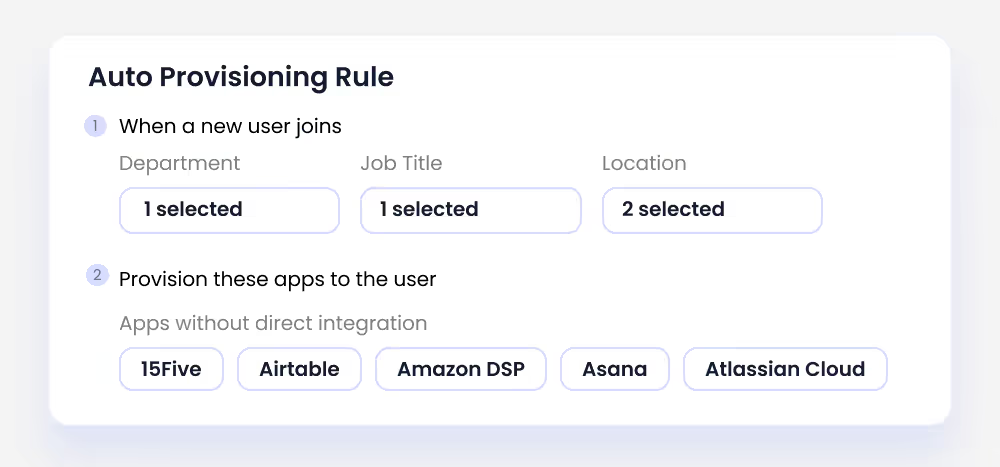
- Instant access provisioning for new employees.
- Swift, automatic deprovisioning when employees leave.
- Prevents ex-employee accounts from turning into insider threats.
Check out this customer success story of Treasure Data to know how they streamlined employee offboarding using CloudEagle.ai.
Final Words
Preventing insider threats is no longer optional, it’s a critical part of enterprise security. Organizations that proactively implement access controls, continuous monitoring, and employee training significantly reduce the risk of data breaches and operational disruption.
By understanding what is an insider threat is and adopting structured insider threat prevention strategies, enterprises can safeguard sensitive information while maintaining employee trust. Regular audits, behavioral analytics, and zero-trust principles are key to comprehensive insider threat management.
CloudEagle.ai simplifies how to prevent insider threats by automating access management, enforcing least privilege, and providing centralized visibility across all SaaS applications. This ensures CISOs can manage risks efficiently, stay compliant, and secure critical data.
Book a free demo to see how CloudEagle.ai can strengthen your insider threat prevention strategy.
Frequently Asked Questions
- Which is an example of an insider threat?
An employee stealing sensitive data, a negligent worker exposing passwords, or a contractor misusing access are all examples of insider threats. - What best describes an insider threat?
An insider threat is a risk posed by someone within the organization who can intentionally or accidentally harm systems, data, or operations. - How many insider threat indicators are there?
There are typically four main insider threat indicators: malicious, negligent, compromised, and third-party insiders. - Who can you report an insider threat to?
Report insider threats to your security team, IT department, HR, or through internal whistleblowing channels. - How can you minimize the ability of an insider threat?
Minimize insider threats with access controls, monitoring, least privilege, MFA, zero-trust policies, and regular employee training.

%201.svg)









.avif)




.avif)
.avif)




.png)









