HIPAA Compliance Checklist for 2025

While passwords are essential aspects of digital security, they’ve also been the weakest link. In fact, Statista revealed that 94 million records were stolen due to multiple causes of data breaches.
Passkeys offer a new way forward. Instead of relying on passwords that can be guessed, stolen, or phished, they use cryptographic keys stored securely on devices. This makes them far harder for attackers to exploit and far simpler for users to manage.
For enterprises, the challenge is managing passkeys across hundreds of applications. That’s where platforms like CloudEagle.ai help. By centralizing identity governance and access management, CloudEagle.ai ensures IT gains full visibility and control to enforce compliance and reduce risks.
In this article, we’ll break down what passkeys are, how they work, their benefits, limitations, and practical steps to create them.
TL;DR
- Passkeys replace passwords by using cryptographic keys stored on devices, offering stronger security and phishing resistance.
- Authentication is seamless, leveraging biometrics or PINs, reducing login frustration and IT support costs.
- Types of passkeys include device-bound, synced (cloud), and hardware tokens, balancing security and usability.
- Limitations exist, like device dependency, cross-platform issues, and risks if devices are lost or stolen.
- CloudEagle.ai enhances enterprise management by centralizing identity governance, automating access, and securing SaaS environments.
What is a Passkey?
A passkey is a modern, passwordless authentication method used instead of static character strings. Users authenticate with built-in device security, like face recognition, fingerprint, or a secure PIN.
Each passkey leverages public-key cryptography and is unique for every account and device combination. The overall security improves since private data remains safely stored on the user’s personal device.
Here’s a simple breakdown of what defines a passkey:
- Passwordless authentication: Users don’t need to create or remember complex passwords.
- Device-bound security: Passkeys are stored on trusted devices and can’t be stolen through phishing.
- Biometric or PIN-based access: Authentication happens via methods like Face ID, fingerprint, or a local PIN.
- Cross-platform support: Major platforms like Apple, Google, and Microsoft support passkeys across devices.
Passkeys are designed to make digital access both secure and seamless. For everyday users, this means fewer login frustrations and stronger protection against common identity and access management risks. For enterprises, it signals a step toward reducing password-related breaches and support costs.
How Do Passkeys Work?
Passkeys use public-key cryptography to generate unique key pairs for each online account. The public key stays on the server, while the private key remains securely stored on the user's device.
During sign-in, the server sends a challenge for the device to sign with its private key. Authentication happens without ever sharing or transmitting the private key across the internet.
Device unlock methods like fingerprints, face scans, or PIN verify the user before signing the challenge. Passkeys make logins phishing-resistant and safer than traditional passwords. Here’s how the process looks step by step:
- User registers a passkey: The device generates a public and private key pair.
- Public key is stored on the service: Only the public key is shared with the online service.
- Private key stays on the device: It never leaves the user’s phone or computer.
- Authentication via biometric or PIN: The private key is unlocked using Face ID, fingerprint, or PIN.
- Secure login: The service verifies the signed challenge and grants access.
This process significantly reduces the risk of phishing, credential theft, or brute-force attacks. In fact, according to a 2023 FIDO Alliance survey, 57% of consumers abandoned a purchase due to password frustrations, highlighting the need for seamless solutions like passkeys.
What are the Different Types of Passkeys?
Passkeys come in several forms, depending on the device or authentication method used. Each type is designed to balance security and usability, allowing enterprises and users to choose what works best for their needs.
Here are the main types:
Device-Bound Passkeys
These passkeys are tied to a single device, like a phone or laptop. They ensure the private key never leaves that device, providing high security. However, they may be less convenient if a user frequently switches devices.
Synced Passkeys
These passkeys are stored in cloud accounts, like Apple iCloud Keychain or Google Password Manager. They sync across devices for convenience, making it easier for users to log in anywhere. While user-friendly, they rely on the security of the syncing platform.
Hardware Token Passkeys
Security keys such as YubiKeys generate and store private keys in physical form. They provide robust protection against endpoint security risks like phishing and malware but require users to carry the device, which may not be practical in all cases.
What are Some Benefits of Using Passkeys?
Passkeys offer enhanced security by resisting phishing attacks and preventing data breaches for users and organizations. Users benefit from faster authentication methods across devices and platforms, improving the login experience.
1. Elimination of Password-Based Attacks
Passwords remain the weakest link in authentication, often exploited through brute force, credential stuffing, or leaks. Passkeys eliminate these endpoint security issues by replacing passwords with cryptographic keys that cannot be guessed or reused across platforms.
- Resistant to theft: Since private keys never leave the device, attackers cannot compromise them via phishing or breaches.
- No reuse issues: Users no longer rely on the same password across multiple accounts, reducing credential stuffing attempts.
- Future-proof approach: Passkeys align with evolving SaaS security measures, making them a long-term solution against identity fraud.
As Microsoft’s former CEO Bill Gates once said:
“There will always be passwords. But they should be phased out as quickly as possible.”
Passkeys mark a turning point in finally realizing that vision.
2. Faster and Seamless User Login Experience
Passwords slow users down, requiring frequent resets and complex requirements that frustrate employees and customers alike. Passkeys enable login through simple device-based authentication, such as biometrics or a PIN.
This streamlined process reduces login times and eliminates password fatigue, particularly in enterprise environments with multiple apps. By making access quick and effortless, organizations improve both productivity and user satisfaction.
3. Stronger Protection Against Phishing
Phishing is one of the most common cyber threats, tricking users into handing over credentials. Statista revealed that more than 38 million phishing cases were detected in 2024. Passkeys counter this by binding login credentials to the domain they’re created on, ensuring they cannot be reused on fake sites.
- Domain validation: Authentication only works on legitimate websites or apps, blocking phishing redirections.
- No shared secrets: Since no password is exchanged, attackers have nothing to intercept or steal.
- Stronger user trust: Users gain confidence that their login process is inherently more secure.
4. Reduced IT Overhead and Support Costs
Password resets account for a large share of IT helpdesk tickets, draining time and resources. Passkeys drastically reduce these requests by eliminating forgotten or expired passwords altogether.
This not only improves IT efficiency but also frees up teams to focus on more strategic security initiatives. In the long run, enterprises save significantly on both operational costs and workforce productivity losses tied to password management.
How to Create a Passkey from Scratch?
Setting up a passkey is simpler than most people expect, thanks to growing support from browsers, devices, and apps. Instead of memorizing complex passwords, users generate secure cryptographic keys stored directly on their device. This makes the process both user-friendly and highly secure.
1. Creating Passkeys on Mobile Devices
Passkeys on mobile devices are designed to be easy to set up and even easier to use. Both iOS and Android offer native support for passkeys, allowing users to create them during app sign-in or through account settings.
On iPhones and iPads, passkeys can be managed directly through iCloud Keychain. This ensures that once a passkey is created, it automatically syncs across all Apple devices. Android offers a similar experience through Google Password Manager.
For users, this means fewer hurdles during account creation. The process eliminates the need to come up with complex passwords, reduces the likelihood of phishing, and improves overall identity and access security.
2. Setting Up Passkeys on Browsers
Passkeys can also be created and managed directly through web browsers. Modern browsers like Chrome, Safari, and Edge now support passkeys, enabling users to replace traditional passwords with a stronger, phishing-resistant alternative.
The process typically begins when a user visits a website that supports passkeys. Instead of prompting for a password, the site triggers the browser to generate a unique passkey linked to the user’s device.
A real-life example is when Google rolled out passkey support for its Workspace and Cloud Identity users in June 2023. Admins can now enable users to skip passwords and rely on passkeys in their Google accounts.
3. Syncing Passkeys Across Platforms
One of the biggest strengths of passkeys is their ability to sync across devices and platforms. Unlike traditional passwords, passkeys are securely stored in IDP credential managers.
For example, if a user creates a passkey on their iPhone, it can be automatically synced through iCloud Keychain and accessed on their Mac or iPad. Similarly, Google’s Password Manager and Microsoft Authenticator allow seamless syncing across Android and Windows devices.
4. Testing Passkeys for Proper Functionality
After creating and syncing passkeys, the next critical step is testing them to ensure they function as intended. Testing verifies that users can authenticate smoothly across devices, browsers, and applications without errors or compatibility issues.
As Google’s product manager Christiaan Brand once noted,
“Passkeys must be tested in real-world conditions to build trust. Reliability in authentication isn’t optional, it’s essential for adoption.”
This highlights that successful implementation depends on more than deployment; it requires thorough validation to ensure a seamless user experience.
How Can You Delete Passkeys?
Just as important as creating passkeys is knowing how to delete them. Users may need to remove passkeys when switching devices or simply resetting login credentials for security reasons. The process is straightforward, and here are some common ways to delete them:
On Mobile Devices
Both iOS and Android allow users to manage passkeys in settings. For example, on iPhones, you can navigate to Settings → Passwords → Passkeys and delete the selected entry. Android users can find similar options under Google Password Manager.
On Web Browsers
Browsers like Chrome, Safari, and Edge provide built-in passkey management. Users can open the password manager, locate the passkey tied to a specific service, and remove it with a few clicks.
From Cloud Accounts
Since many passkeys sync via cloud services, removing them from accounts like iCloud Keychain or Google Password Manager ensures they disappear across all linked devices.
Deleting passkeys ensures that outdated or unnecessary login credentials do not remain active. This reduces the risk of accidental account access from old devices or users who should no longer have permissions.
What are Some Limitations of a Passkey?
While passkeys are a major leap forward in authentication, they are not without challenges. Businesses and individuals adopting them must be aware of certain drawbacks. These limitations do not undermine the security benefits of passkeys but highlight areas where they are still maturing.
1. Dependence on Hardware and Devices
Passkeys rely heavily on the devices they are stored on, which can create challenges for users. If a device is lost, damaged, or stolen, access to accounts can be disrupted.
- Device-Specific Limitation: A passkey generated on one smartphone or hardware token often cannot be directly transferred to another device.
- Operational Impact: Enterprises must invest in backup solutions or multi-device support to mitigate downtime and maintain seamless access.
Teledataslect revealed that more than 50% of data breaches involve SaaS systems. With a proper backup, it can be mitigated to a great extent.
2. Limited Cross-Platform Compatibility
While passkeys offer enhanced security, their effectiveness can be limited by cross-platform compatibility issues. Users may encounter difficulties when attempting to use passkeys across different operating systems or devices that do not support the same authentication standards.
- Platform-Specific Limitations: Some platforms may not support passkeys, requiring users to revert to traditional password-based authentication methods.
- Inconsistent User Experience: The lack of universal support can lead to a fragmented user experience, where users must remember and manage multiple authentication methods.
- Enterprise Challenges: Organizations with diverse IT environments may face challenges in implementing passkeys uniformly across all systems and devices.
3. Risk of Losing Device Access
While passkeys offer enhanced security, they are not immune to risks associated with device loss or theft. If a device containing a passkey is lost or stolen, access to associated accounts can be compromised, especially if the device is not adequately protected.
- Device Dependency: Passkeys are stored locally on devices, and without proper backup or synchronization, losing the device can result in the loss of access to accounts.
- Security Concerns: If a device is not secured with strong authentication methods like biometrics or a PIN, unauthorized users may gain access to the passkeys stored on it.
- Recovery Challenges: Recovering access to accounts protected by passkeys can be more complex than traditional passwords, often requiring assistance from service providers.
For instance, a study by Nuke From Orbit found that 29% of UK adults have experienced mobile phone theft, a significant increase from 17% in 2023. This surge in thefts has heightened concerns over digital security, particularly regarding unauthorized access to bank accounts and digital wallets.
Passkey vs Password: What are the Differences?
Enterprises and users are moving toward passkeys because they address many security and usability challenges of traditional passwords. Understanding the key differences helps organizations make informed decisions for digital authentication.
Security
- Passkeys: Rely on cryptographic keys stored locally or on devices, making them nearly impossible to guess or phish.
- Passwords: Can be reused, stolen, or cracked, leaving accounts vulnerable to attacks like credential stuffing.
User Experience
- Passkeys: Offer seamless login with biometrics or device authentication, reducing login friction.
- Passwords: Require memorization and frequent updates, which often leads to password fatigue and reuse.
Recovery and Management
- Passkeys: Require device-based recovery or cloud sync options, which may be new for users.
- Passwords: Can be reset through email or SMS, but these methods are also vulnerable to attacks.
Adoption and Compatibility
- Passkeys: Supported across most modern devices and platforms, but older systems may lack compatibility.
- Passwords: Universally compatible but weaker in security and prone to human error.
How CloudEagle.ai Can Manage Access and Secure Data Easily?
CloudEagle.ai helps IT, procurement, and security teams take full control of their SaaS ecosystem. The platform connects with 500+ integrations, from finance to SSO to HRIS, giving you complete visibility into applications, licenses, vendors, and spend.
CloudEagle.ai also streamlines identity and access management. Through a centralized dashboard and Slack-enabled workflows, IT can automate onboarding, offboarding, access reviews, and license assignments, saving time while reducing security risk.
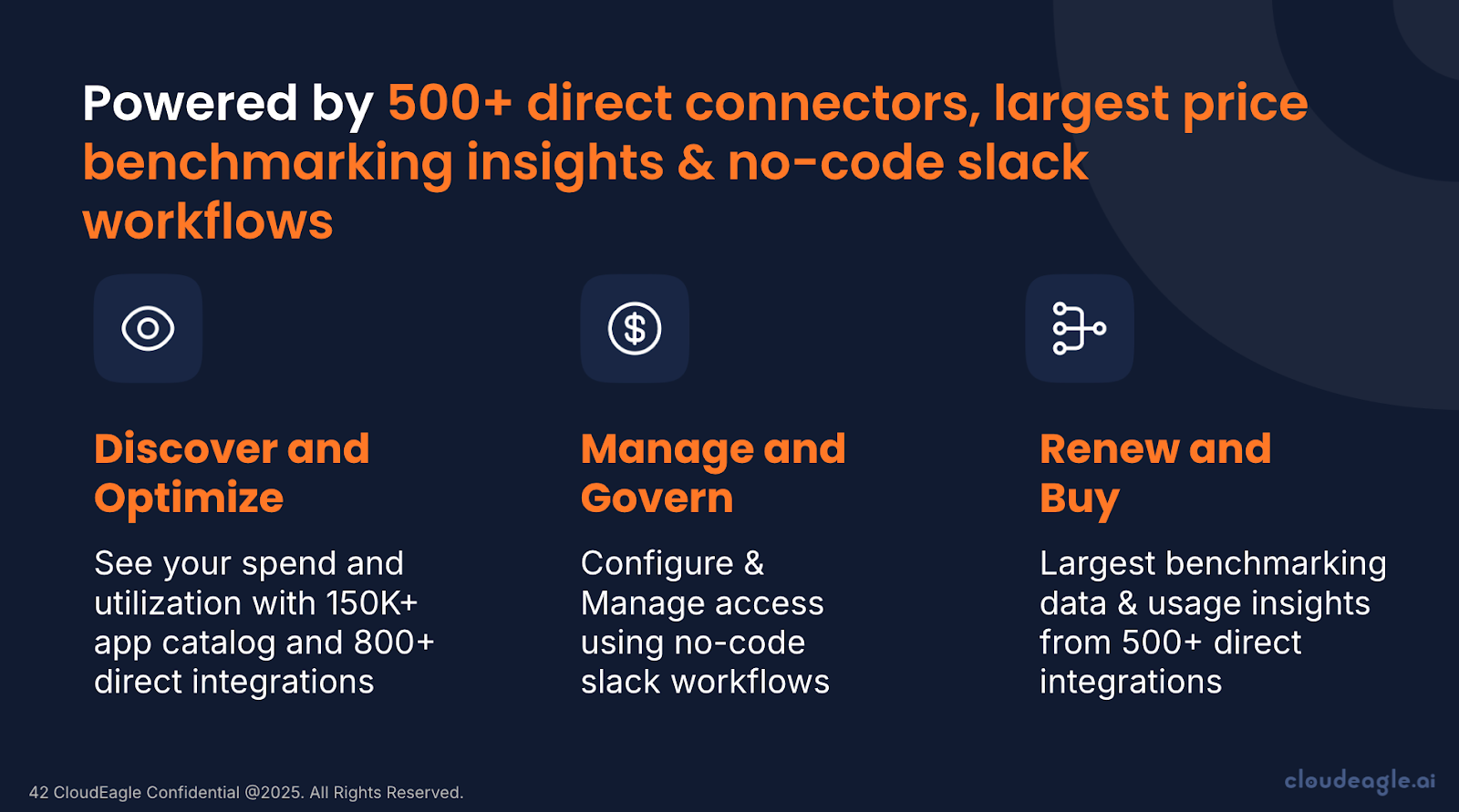
Enterprises like RingCentral, Shiji, and Rec Room already rely on CloudEagle.ai to cut SaaS costs by 10-30%. With $3.5B in processed spend and $250M+ in customer savings delivered, the platform proves its impact. And thanks to 30-minute onboarding, enterprises such as Rec Room see governance improvements and cost savings from day one.
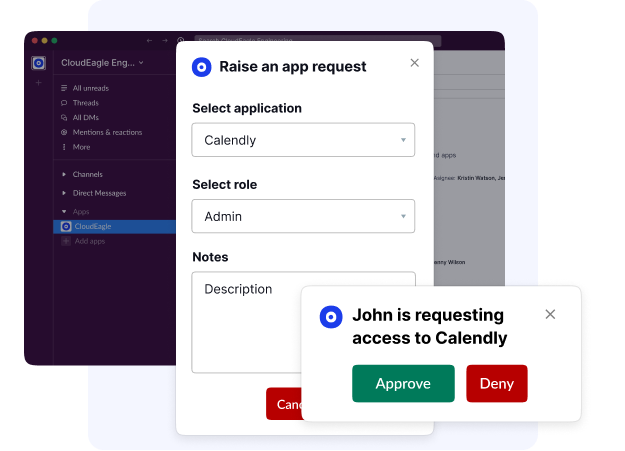
Employee App Access Catalog
Most employees don’t know which tools they can request, and IT spends hours piecing approvals together from emails, Slack, or tickets. This slows onboarding, creates compliance gaps, and forces IT into repetitive access request work.
Even with tools like JIRA or ServiceNow, app lists require manual updates and can’t restrict visibility by department, leading to shadow IT, redundant purchases, and security risks.
CloudEagle.ai solves this by centralizing app access in a dynamic self-service app catalog that updates automatically through 500+ integrations. Employees see only relevant apps: Sales sees Salesforce, Engineering sees AWS, and requests flow through automated approval workflows with complete audit trails.

The result? IT resolves access requests up to 80% faster, employees onboard in minutes, shadow IT shrinks, and compliance reporting becomes effortless, all while improving security and cutting redundant SaaS applications.
Just-in-Time Access
IT teams often grant perpetual licenses for short-term tasks, leaving unused access that increases security risks and wastes spend. Contractors, freelancers, and temporary staff frequently end up with permissions long after their work is done.
CloudEagle.ai solves this with time-based access. It grants licenses or permissions only for the required duration and automatically revokes them once the task is complete. No manual follow-up needed.
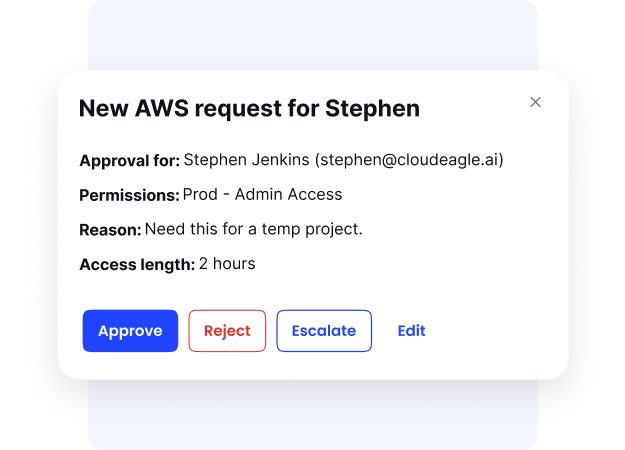
Enterprises will get stronger security by reducing unauthorized access, lower costs by eliminating wasted licenses, and simpler governance through automated oversight.
Automated App Access Reviews
Traditional access reviews force IT to pull data from multiple systems, log into apps, and manually check user roles. This process is slow, error-prone, and usually happens only once a quarter, leaving ex-employees or risky users with access far too long, creating compliance and security risks.
CloudEagle.ai automates and streamlines app access reviews. Through a centralized dashboard, IT and app owners can instantly see user roles and permissions, schedule periodic reviews, and stay compliant with standards like SOC 2. The platform flags high-risk users and ex-employees automatically, and deprovisioning is handled in just a few clicks.
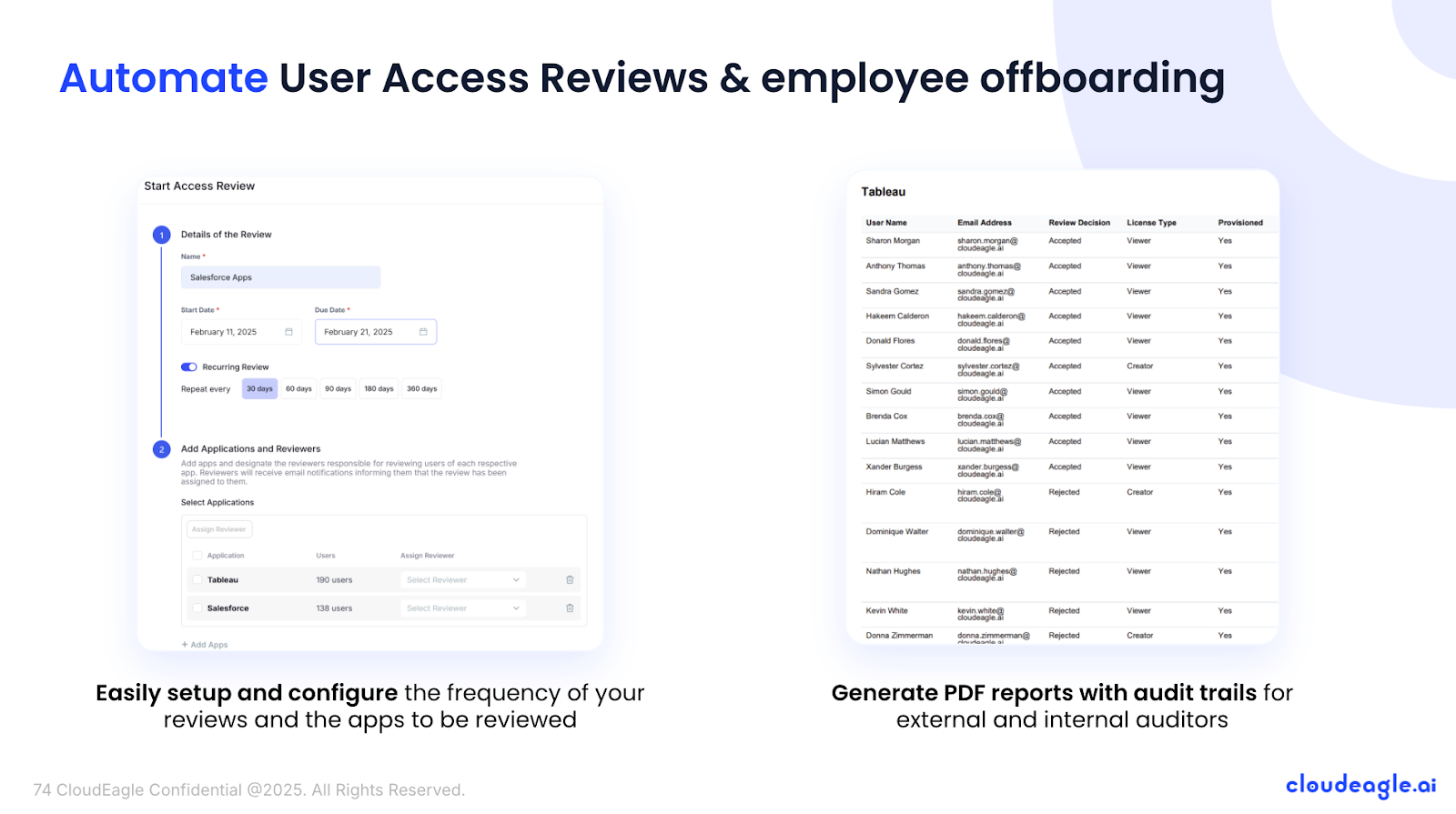
Now, access reviews that take hours instead of weeks, proactive security that prevents excessive privileged access, and compliance that’s always audit-ready.
Access Control
CloudEagle.ai provides full transparency into application access control, including who has access, the reasons behind it, and how they utilize it. With centralized access control, it oversees the entire access lifecycle, from request to provisioning and deprovisioning, all within a single platform.
Additionally, the platform simplifies compliance and security audits by offering instant access to application logs. Detailed access records can be exported directly, making audit preparation seamless and hassle-free.
Privileged Access Management
CloudEagle.ai streamlines privileged access management by automating the assignment of elevated access, ensuring that only authorized users can access critical systems like AWS and NetSuite, thereby reducing the risk of unauthorized activity.
With continuous monitoring and automated controls, the platform strengthens security and compliance while easing administrative workloads and minimizing human error.
Employee Onboarding and Offboarding
Employee onboarding and offboarding are often slow and error-prone. IT teams spend hours logging into dozens of apps, manually provisioning or removing access, and tracking licenses across scattered dashboards. This not only delays employee productivity but also leaves ex-employees with lingering access.
CloudEagle.ai automates the entire process with zero-touch workflows. IT teams set role-based rules, by function, location, or privilege level, and CloudEagle.ai provisions the right apps immediately when employees join, then revokes access as soon as they leave.

Freed licenses automatically return to the pool, ensuring resources are never wasted. Unlike relying solely on costly IdPs, CloudEagle orchestrates onboarding and offboarding across all apps, whether integrated with an IdP or not.
For instance, Health Ceramics leveraged CloudEagle.ai to automate deprovisioning, significantly boosting operational efficiency.
Compliance Management
CloudEagle.ai centralizes SaaS compliance verification across all your SaaS applications, offering full visibility and access to critical data. It continuously scans for vulnerabilities, facilitates external audits, manages certifications, and monitors account logs to ensure comprehensive compliance oversight.
Now that you know how CloudEagle.ai can protect your company’s data, let’s see the top 10 data recovery software for enterprises.
Conclusion
Passkeys represent the future of authentication, offering stronger security and a smoother login experience compared to traditional passwords. While limitations like device reliance and compatibility exist, the benefits far outweigh the challenges.
If your organization is considering a shift toward passwordless authentication, CloudEagle.ai can help. Our platform simplifies identity management, improves SaaS operations management, and ensures secure access across all tools. Explore how CloudEagle.ai can help your enterprise secure data today.
FAQs
1. What is a passkey for?
A passkey is designed to replace traditional passwords. It’s used for secure logins, protecting accounts from phishing, credential theft, and weak password practices.
2. How do I find my passkey?
Passkeys are stored in your device’s secure keychain. On iOS and macOS, you’ll find them in iCloud Keychain, while Android users can access them via Google Password Manager.
3. Can passkeys be hacked?
Passkeys are highly resistant to common attacks like phishing or credential stuffing. However, device theft or malware could still pose risks, making strong device security essential.
4. Can I use a passkey on my phone?
Yes, most modern smartphones support passkeys. They can be set up and synced across devices using cloud services like iCloud Keychain or Google Password Manager.
5. What happens if I lose my device with a passkey?
If your device is lost, you can still recover your passkeys by logging into your cloud account (Apple ID or Google account) on a new device. It’s important to have backup options enabled for seamless recovery.

%201.svg)









.avif)




.avif)
.avif)




.png)









