HIPAA Compliance Checklist for 2025

Managing digital identities has become a cornerstone of cybersecurity in today’s cloud-driven world. As organizations adopt more SaaS tools, remote access policies, and hybrid infrastructures, the need for secure, centralized authentication has never been greater.
That’s where an identity provider, commonly referred to as an IdP, comes in. Acting as a trusted source for verifying user identities, IDPs streamline access across multiple applications while improving both security and user experience.
But what exactly is an IdP, Identity provider? How do they work, and why are they essential for modern businesses? This guide explores everything you need to know about IdP authentication, its role in SaaS security, and how to choose the right provider for your organization.
You’ll also see how combining CloudEagle.ai with your IdP can streamline and automate access governance.
TL;DR
- An identity provider (IdP) authenticates users and enables secure, centralized access to SaaS apps.
- IdPs support SSO, MFA, and token-based authentication for better security and user experience.
- Key benefits include reduced credential theft, streamlined provisioning, and cost savings.
- Choose an IdP with features like centralized directories, audit trails, and federation capabilities.
- CloudEagle.ai complements your IdP by automating access reviews, provisioning, and SaaS usage tracking.
What is an Identity Provider (IdP)?
An Identity Provider (IdP) is a trusted service that handles the verification and management of user identities. It authenticates users through a single set of credentials and grants access to various applications and services based on their assigned permissions.
In simpler terms, the IdP identity provider is the system that confirms whether users are who they claim to be before granting them access to an application or service.
When you log in to a website using your Google or Microsoft account, you’re using an idp. These platforms act as centralized identity sources, reducing the need for separate usernames and passwords for every app.
The terms IdP meaning or IdP mean are often used to describe the same concept: an authentication authority that verifies users’ identities securely and consistently.
How Identity Providers (IdPs) Work
An Identity Provider (IdP) authenticates user identities and shares that verification with other services, enabling Single Sign-On (SSO). This allows users to log in once through the IdP and seamlessly access multiple connected applications without repeated logins.
Authentication Flows Explained
Authentication flows are the series of steps an IdP uses to confirm a user’s identity. The flow typically includes credential verification, token issuance, and application access.
Once a user tries to log in:
- The app redirects them to the IdP.
- The IdP asks for credentials (or uses a pre-established session).
- Upon verification, it returns an authentication token.
- The app then uses this token to grant access.
These flows vary depending on the method, SAML, OAuth, or OpenID Connect, but the core process remains the same.
What Happens During Login? (Step-by-Step)
Here’s a step-by-step of what typically occurs during an IdP authentication event:
- User attempts to access an application.
- The application redirects the request to the identity provider.
- The IdP checks if the user is already authenticated.
- If not, the user is prompted for credentials.
- Once verified, the IdP issues an authentication token.
- The token is sent to the app, which grants access.
This ensures that all login attempts are vetted centrally, making the process more secure and traceable.
Role of Authentication Tokens (SAML, OAuth, etc.)
Tokens are a critical part of how IdP identity providers function. Once the IdP authenticates a user, it issues a secure token, usually in the form of SAML, OAuth 2.0, or OpenID Connect.
- SAML (Security Assertion Markup Language) is often used in enterprise environments.
- OAuth 2.0 is preferred for mobile and cloud apps.
- OpenID Connect builds on OAuth 2.0 to enable authentication and user profile sharing.
These tokens are tamper-proof, time-bound, and encrypted, providing a secure way for applications to trust the identity of the user without managing passwords locally.
What Are the Benefits of IdPs?
Identity Providers (IdPs) deliver major advantages by centralizing authentication and access control. They strengthen security with multi-factor authentication, simplify logins through single sign-on (SSO), and reduce IT overhead, improving compliance, efficiency, and the user experience.
Enhanced Security for User Access
IdP cybersecurity ensures that user authentication happens through a secure, centralized gateway. This reduces the risk of data breaches caused by phishing, brute-force attacks, and unauthorized access attempts
Because all access requests are filtered through the identity provider, it’s easier to monitor, detect anomalies, and apply uniform security policies.
Simplified User Experience with SSO
Identity provider SSO (Single Sign-On) allows users to log in once and access all connected apps without re-entering credentials. This reduces friction, improves productivity, and eliminates the need to remember multiple passwords.
From an IT perspective, IdPs eliminate password reset requests and enhance usability across platforms.
Streamlined User Lifecycle Management
As users join, move within, or leave an organization, their access needs evolve. A centralized IdP identity provider simplifies provisioning and deprovisioning by automatically assigning or revoking access across multiple systems with just a few clicks.
This reduces the risk of orphaned accounts and strengthens your identity governance framework.
Cost Savings from Centralized Control
Managing authentication and access separately in every system increases administrative overhead. A centralized IdP reduces the need for redundant tools and manual processes.
With fewer service desk calls, reduced password resets, and automated provisioning, organizations often see significant operational cost savings.
Reduced Risk of Credential Theft and Breaches
Stolen credentials are one of the leading causes of data breaches. By implementing an IdP authentication system with MFA and centralized access controls, companies can drastically reduce this risk.
You can enforce stronger policies (like device trust and geofencing) through the identity provider, keeping your sensitive data safer.
According to CSO Online, centralized identity systems have been proven to reduce attack surfaces and improve security posture across industries.
Key Features to Look for in an Identity Provider
When choosing an Identity Provider (IdP), look for key features like multi-factor authentication (MFA), single sign-on (SSO), and detailed access controls. Prioritize seamless integration, audit logs, strong encryption, scalability, and support for standard authentication protocols and compliance needs.
Here’s a deeper look at the must-have features you should expect from a modern identity provider.
Centralized User Directory
A centralized user directory acts as the single source of truth for all user identities. An effective IdP should offer its user directory or integrate easily with services like Active Directory, LDAP, or cloud-based HR systems.
This ensures consistent identity data across your organization, reduces duplication, and makes user lifecycle management far more efficient.
Whether you're managing hundreds or thousands of users, this feature allows your IdP identity provider to maintain up-to-date identity attributes, like roles, departments, and permissions, in one place.
Single Sign-On (SSO) Capabilities
Identity provider SSO allows users to log in once and gain access to all authorized systems without multiple passwords. This drastically improves user experience and eliminates login fatigue while also strengthening security by reducing attack surfaces.
For IT and security teams, SSO centralizes session control and simplifies compliance tracking. Whether your users need access to Google Workspace, Slack, Salesforce, or internal tools, IdP authentication with SSO ensures consistent, secure entry points.
Multi-Factor Authentication (MFA)
MFA is now a standard requirement, not an optional feature. A robust IdP cybersecurity system must support flexible, context-aware MFA policies, including biometrics, time-based tokens, push notifications, or device-based trust.
Look for IdPs that allow you to enforce MFA during high-risk scenarios, such as logins from unfamiliar devices, sensitive app access, or geographic anomalies. This added layer drastically reduces the risk of unauthorized access due to compromised credentials.
API Access Management
Modern organizations rely on microservices, APIs, and cloud-native workflows. A capable IdP should allow fine-grained API access management, enabling developers to assign, monitor, and revoke permissions through programmatic interfaces.
This is especially critical for DevOps and IT teams managing non-human identities, such as service accounts, bots, or third-party integrations. Controlling API-level authentication ensures your environment stays secure without slowing down development workflows.
Federation Capabilities
A federated IdP allows identity sharing across different organizations, business units, or domains. Federation is vital when collaborating with partners, managing subsidiaries, or onboarding external users who authenticate via their home organization.
Instead of creating and managing separate accounts, federation lets users log in through their existing credentials, using protocols like SAML or OpenID Connect. This enables seamless trust between systems and simplifies compliance by keeping authentication within a known domain.
If your business operates globally or in a multi-tenant model, federated IdP functionality is a game-changer.
Audit Trails and Reporting
Visibility is non-negotiable when it comes to access management. A strong IdP identity provider should generate detailed audit logs that capture login events, permission changes, access attempts, and system anomalies.
These reports help meet regulatory requirements like GDPR, HIPAA, and SOC 2, while also enabling internal investigations and risk analysis. The more granular and customizable the reporting, the easier it is for teams to monitor suspicious behavior and respond in real time.
Look for solutions that allow exporting logs, setting automated alerts, and integrating with SIEM platforms for real-time monitoring. Referencing NIST’s identity guidelines can help ensure your chosen IdP meets best practices for access governance.
Choosing the Right Identity Provider for Your Business
Selecting the right identity provider (IdP) is vital for ensuring secure and efficient access management. Consider factors like security capabilities, scalability, SaaS vendor support, and cost. Also evaluate your organization’s needs, such as lifecycle management, cloud support, and integration flexibility.
Here’s a simple guide to help you choose:
Know Your Environment
Start by listing the SaaS tools your teams use: Slack, Google Workspace, Salesforce, and more. Your identity provider should integrate seamlessly with all of them and support IdP authentication across devices and networks.
Set Access Requirements
Do you need identity provider SSO for employees? Do external partners need access? If so, a federated IdP with SAML or OpenID Connect support will help manage identities across domains securely.
Evaluate Compliance Readiness
If you’re in a regulated industry, choose an IdP with robust auditing, role-based access, and MFA. These are essential for meeting SaaS compliance standards like HIPAA, GDPR, and SOC 2.
Think Scalability
Your IdP identity provider should grow with you. Look for automation features like user provisioning and real-time IdP authentication to avoid bottlenecks as your workforce expands.
Test Before You Buy
Always run a pilot. Connect a few apps, test login flows, review audit logs, and validate support response times. This ensures the IdP fits both your tech stack and user expectations.
A good identity provider should be secure, flexible, and future-proof, so choose one that checks every box, not just the basics.
CloudEagle.ai’s Approach to Identity and Access Management
CloudEagle.ai enhances your existing identity and access management by integrating with SSO, HRIS, and other enterprise systems. It’s built to give IT, procurement, and security teams complete control over SaaS usage, spend, and user access, all from a centralized platform.
Rather than replacing your identity systems, CloudEagle.ai extends their value by automating provisioning, simplifying reviews, and streamlining access governance across your entire SaaS stack.
Monitor App Access & Usage
Track employee logins and feature-level app usage in real time. CloudEagle.ai goes beyond surface-level data to give you full visibility into which applications are being used, by whom, and how often.
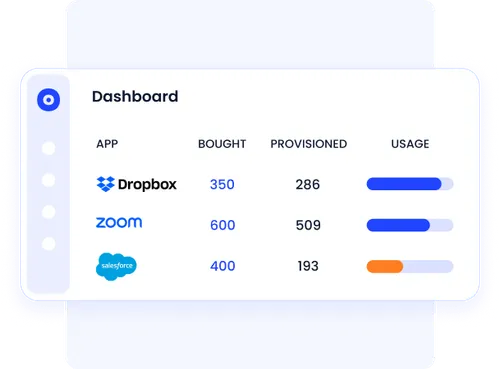
This helps IT and procurement teams eliminate redundant tools, improve license utilization, and maintain a secure SaaS environment.
Automate Provisioning & Deprovisioning
Provisioning and revoking access manually wastes time and increases risk. CloudEagle.ai enables workflow-based automation for both user provisioning and deprovisioning processes.
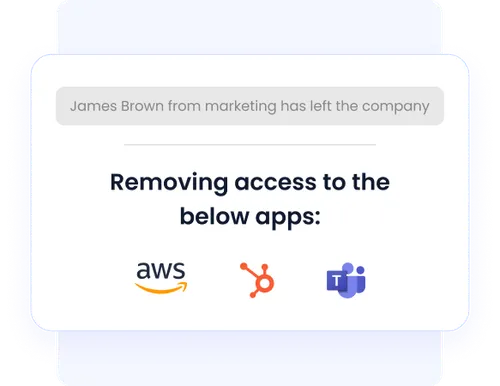
Your team can set up rules to assign apps based on role or department, and automatically revoke access when employees leave. That’s faster provisioning, cleaner access, and fewer mistakes.
Alice Park from Remediant shares how CloudEagle.ai helped streamline operations by managing user access, tracking contracts, and simplifying license renewals.
Enable Self-Service with Smart Controls
CloudEagle.ai offers a self-service portal where employees can request app access. Admins are instantly notified through Slack or email and can approve requests with one click.
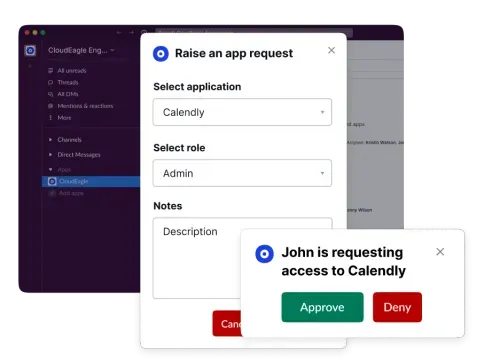
The platform even suggests relevant apps based on user roles, helping new employees get the tools they need without the back-and-forth.
Role-Based & Just-In-Time Access
Assign permissions based on user roles with Role-Based Access Control (RBAC). That means employees only get the access they need, nothing more, nothing less.

For sensitive tools, you can also enable Just-in-Time (JIT) access, allowing temporary access for a set duration. Once expired, access is automatically revoked, minimizing risk without slowing down work.
Automate Access Reviews
Conducting access reviews manually is tedious and error-prone. CloudEagle.ai automates this process by scheduling regular review cycles and prompting approvers to certify or remove access.
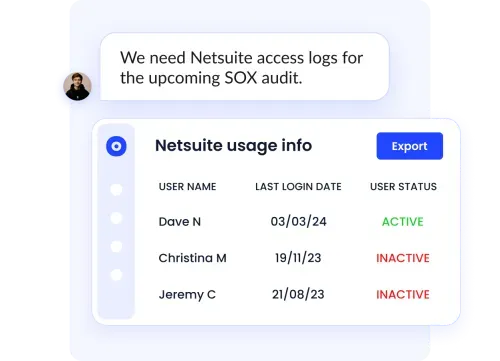
Everything is tracked, audited, and report-ready, helping your organization stay compliant and reduce excessive privileges over time.
Enterprise-Grade Integration & Compliance
CloudEagle.ai has an integration library with 300+ platforms, including SSO tools, HR systems, and financial software. Once connected, it gives you a complete view of your app stack, vendor contracts, users, and spend data, all in one place.
No more switching between tools to get the full picture. You can manage users, licenses, and app usage from a single dashboard and maintain tighter governance across the board.
Final Thoughts
An identity provider (IdP) is essential for managing secure and seamless user access across modern SaaS environments. It centralizes authentication, simplifies login experiences, and reduces the risk of breaches.
Choosing the right IdP means looking beyond basic access control. Features like SSO, MFA, and user lifecycle management are key to strengthening your security framework.
CloudEagle.ai works alongside your existing IdP to automate provisioning, monitor app usage, and enforce access policies. It helps you save time, reduce manual effort, and improve SaaS governance.
Book a free demo today to see how CloudEagle.ai can simplify identity and access management for your business.
Frequently Asked Questions
- What is federated IdP?
A federated IdP allows users to access multiple systems across organizations using one identity, enabling cross-domain authentication through trust relationships. - What is the difference between SSO and federated identity?
SSO lets users access multiple apps within one organization using a single login. Federated identity allows access across different organizations or domains using linked identities. - What is the difference between IdP and SSO?
An IdP verifies user identities and handles authentication. SSO is a feature often provided by IdPs that lets users access multiple apps with one login. - Is there a difference between IdP and IAM provider?
Yes. An IdP handles user authentication, while an IAM provider manages broader access controls, policies, user roles, and compliance across systems. - What is a Single Sign-On provider?
An SSO provider enables users to log in once and access multiple apps or systems without re-authenticating each time. Often, the SSO provider is part of an IdP. - Who is the identity provider in SSO?
The identity provider (IdP) in SSO is the system that authenticates the user and issues access tokens to other connected applications after a successful login.

%201.svg)







.avif)




.avif)
.avif)




.png)









