HIPAA Compliance Checklist for 2025

Did you know that 80% of organizations fail to revoke access once a task is complete, leaving their systems vulnerable? As cyber threats evolve, traditional access management methods struggle to keep up. Organizations need a smarter way to control access that minimizes risks while meeting operational needs.
In a survey of 2,300 security decision-makers, 99% of respondents believe they might face an identity-related compromise within the next year. This highlights the urgent need to stay prepared and ahead of such issues.
The old way of managing app access is broken, with lingering permissions, orphaned accounts, and mounting compliance risks. That’s where Just-In-Time (JIT) access changes the game.
It’s not just about tighter control; it’s about securing your SaaS stack without slowing down the business. In this blog, we’ll explore how CloudEagle.ai's JIT solution can safeguard your SaaS stack, optimize spend, and enhance operational efficiency, all while ensuring security without disrupting business operations.
Let’s dive in.
TL;DR
- Restrict your organization’s app access for a limited time to enhance security and operational efficiency.
- Use a solution like CloudEagle.ai to set up and manage just-in-time access with automated workflows tailored to your organization.
- Create workflows to automate app access requests, define approvers, and establish time-based access limits for employees and contractors.
- Define roles, apps, and license types, and set specific access windows to align with your organizational requirements.
- Automatically remove app access after the designated period, ensuring compliance and reducing security risks effectively.
"CloudEagle.ai helped us streamline access governance with advanced features like RBAC, just-in-time access control, and privileged access management (PAM). The platform provided real-time insights into user access and activity, improving visibility, reporting, security, and compliance."
- Mathew Abraham, Senior IT Manager, Treasure Data
What is Just-in-Time Access?
Just-in-time (JIT) access is a security measure that gives users access to apps, systems, or data only when they need it. Instead of granting permanent access, JIT provides temporary access for a specific task or time period.
The most common form of JIT access is:
- Absolute just-in-time access: This grants user privileges for a fixed, one-time period. Once the specified time frame ends, the access expires. It's typically used for short-term tasks or high-stakes projects.
This approach is beneficial for managing access across all users—whether internal employees, contractors, or temporary workers—by ensuring they have the right permissions at the right time. JIT access reduces security risks, prevents over-privileged accounts, and helps organizations stay compliant with regulations while maintaining control over sensitive data.
For instance, a contractor working on a project may only need access to certain tools for a few days. With JIT, they can get the permissions they need, and once their work is done, access is removed to prevent misuse or unnecessary exposure.
Why Your Organization Needs Just-In-Time (JIT) Access?
Many organizations still grant permanent access to employees, contractors, and third-party vendors. This can result in excessive privileges and unnecessary risks. Just-In-Time (JIT) Access changes the game by granting elevated permissions only when necessary, and for a limited time. This means tighter control and better compliance.
Here’s why JIT access is essential:
- Minimizes Excessive Privileges:
Traditional, standing access gives users more permissions than they need, for longer than necessary. JIT access prevents privilege creep by automatically revoking elevated permissions once the task is complete, keeping your system secure. - Meets Compliance Standards:
JIT access is designed to meet the demands of ISO 27001 and SOC 2 by supporting least-privilege access control. With time-bound access and detailed logs, JIT access ensures you stay audit-ready without the hassle of manual tracking. - Reduces the Risk of Data Breaches:
By limiting the window of exposure for sensitive data or admin access, JIT access minimizes the risk of internal threats and accidental misuse, securing your most valuable information. - Prevents Privilege Creep:
Over time, users can accumulate unnecessary access, creating security risks. JIT access ensures that permissions are granted only for the duration needed, avoiding the long-term build-up of permissions that are no longer required. - Enhances Visibility and Accountability:
Every access request is logged with a clear record of who, why, and when. This transparency simplifies audits and ensures that your team can quickly track and resolve access issues.
Adopting Just-In-Time (JIT) access helps organizations reduce risks, stay compliant, and improve efficiency. CloudEagle.ai makes it simple by automating time-bound access, monitoring user activity, and streamlining approvals, ensuring the right people have access at the right time.
Why CloudEagle.ai is Built for Just-in-Time Access, And Why Your Organization Needs It
Traditional IT processes are often slow, relying on manual tracking, delayed deprovisioning, and over-provisioned licenses, which increase security risks and inflate software costs.
The Major Pitfalls of Traditional Access Management
- Increased Security Vulnerabilities: Users retaining access to sensitive systems long after their tasks are complete expose the organization to internal threats and potential breaches.
- Wasted Software Licenses: Licenses assigned to inactive users result in unnecessary costs, complicating financial forecasting and resource management.
- Lack of Centralized Visibility: IT teams are unable to efficiently track access levels, the duration of access, or whether access is still required, leading to inconsistent security and compliance controls.
How CloudEagle.ai Addresses These Challenges with Time-Based Access
CloudEagle.ai provides a comprehensive solution to these issues by automating time-based access provisioning and license management. This approach ensures that users are granted access only when necessary and for the specific duration required, reducing security risks and eliminating unnecessary costs.
Time-Based Licensing: CloudEagle.ai assigns licenses only for the required time period, automatically revoking access when it expires. This ensures that users no longer have unnecessary access, minimizing security gaps.
Automated Access Requests and Approvals: Access requests are centralized through CloudEagle’s app catalog, automatically routed for approval based on defined roles, departments, or locations. This ensures quick approvals and tighter control over who gets access and when.
Role-Based Access Control: CloudEagle.ai ensures that only relevant applications are visible to each user, limiting unnecessary access and aligning with organizational policies to improve compliance.
Centralized Access Management Dashboard: CloudEagle’s centralized dashboard provides full visibility into who has access, how long it’s valid, and when it should be revoked. This gives IT teams a unified view and better control over access governance.
License Optimization: CloudEagle.ai continuously monitors license activity, automatically flagging inactive licenses and reclaiming them to reduce waste. This helps organizations save on unnecessary SaaS costs and optimize their software spend.
The Outcomes CloudEagle.ai Delivers
Enhanced Security: By automating time-bound access, CloudEagle.ai reduces the risk of lingering access, ensuring users only have the necessary permissions for the required period. This minimizes insider threats and accidental misuse of sensitive systems.
Cost Reduction: CloudEagle.ai eliminates SaaS waste by ensuring that licenses are only allocated when needed and automatically reclaimed once expired. This leads to significant cost savings by reducing over-provisioned licenses.
Streamlined Compliance: CloudEagle’s system provides an audit trail for every access request, approval, and revocation, ensuring your organization is fully compliant with standards
Organizations relying on outdated access management processes are exposing themselves to security risks and inefficiencies. CloudEagle’s time-based access control and automated license management provide a secure, efficient, and cost-effective solution for managing app access.
With CloudEagle.ai, you can ensure compliance, optimize spend, and protect your organization from unnecessary risks.
3-Step process to implement just-in-time access management using Cloudeagle.ai
Implementing just-in-time access for your employees, vendors, or external users is simple and efficient with CloudEagle.ai. To ensure a seamless setup, follow these straightforward steps before getting started:
Step 1: Log in to CloudEagle.ai
To configure just-in-time access rules, log in to your CloudEagle.ai account and navigate to the "Access Management" module.
Step 2: Set up access automation
Go to the “Access Requests” tab and click on “Build Automation” to begin creating your workflows. This feature lets you tailor app access, define approvers, and set up monitoring processes.
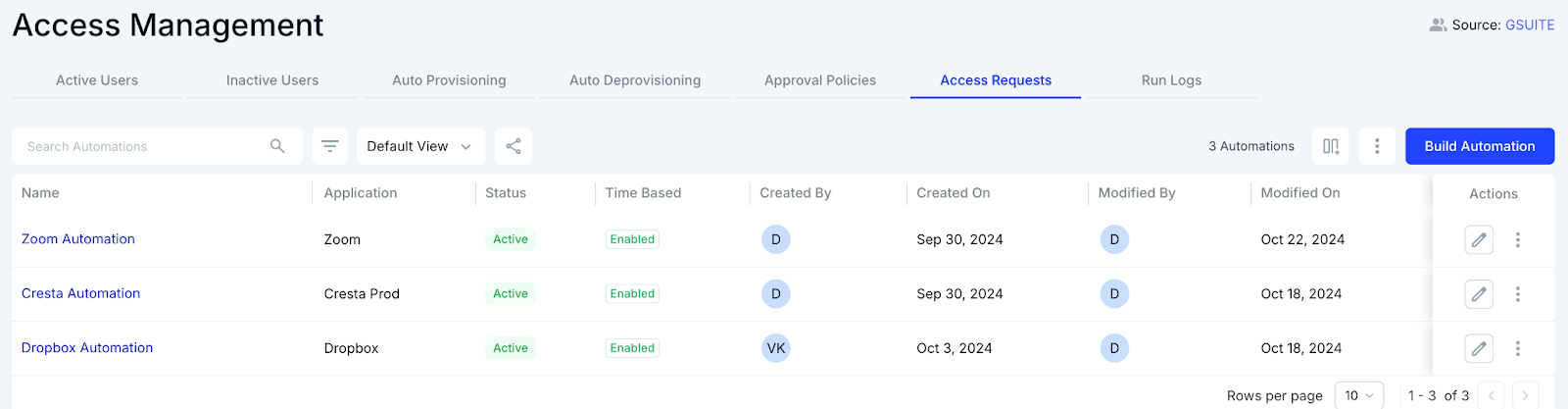
Step 3: Configure access settings
In this step, you’ll customize just-in-time app access by defining applications and entitlements. You can set license types like Basic, Pro, or Enterprise, and roles such as regular users, privileged users, or admins.
You can also establish visibility rules to ensure that only authorized individuals, such as team leads or IT admins. For instance, if Jira is selected as the app, we can set visibility based on departments and restrict access to only the Engineering and Product teams. As a result, Jira will not be visible to the Sales department, preventing them from requesting unnecessary access.
Now comes the most crucial step in setting up just-in-time app access: defining just-in-time access limits.
In this step, you can set time limits for different users based on your organizational needs. For instance, when assigning licenses, you can grant users access to a particular app for a specific duration, whether it's hours, days, months, or even years.

Once the designated period ends, access is automatically revoked, ensuring no unnecessary or prolonged access to sensitive apps.
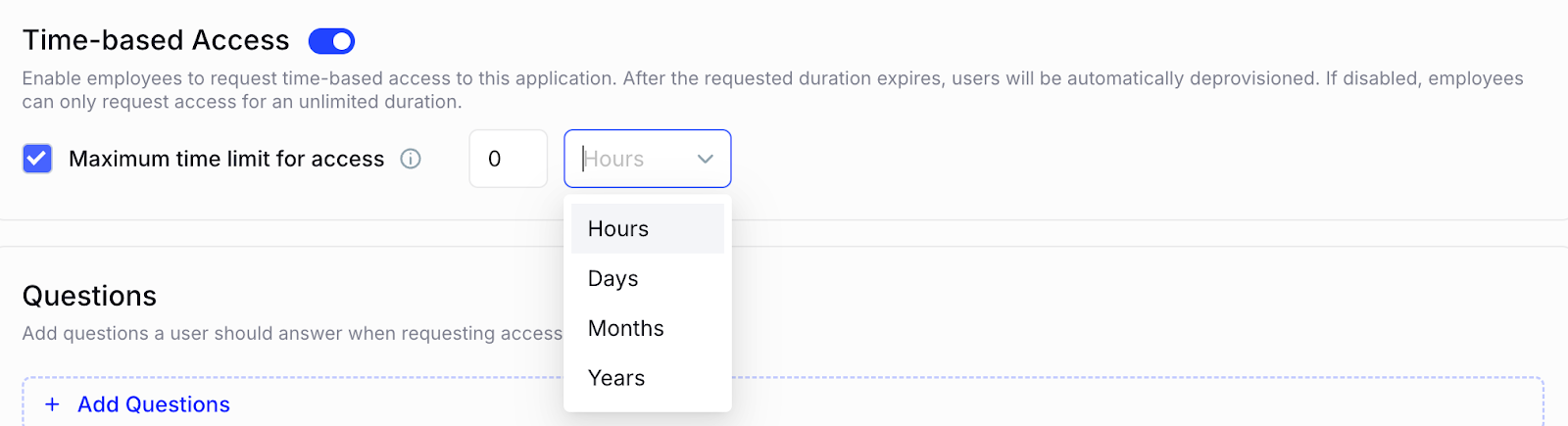
This feature boosts security by reducing access risks and makes managing temporary users easier. It ensures app access matches business needs and is removed when no longer needed.
After setting up the just-in-time access, you can include a brief questionnaire for requesters to capture key details, such as the reason for access and the required duration. This helps make approvals faster and more informed.
Additionally, you can define specific actions for each request, like routing it to a manager for approval or automating provisioning. Integrating with tools like Okta further streamlines the process, making it seamless and efficient.
With these capabilities, CloudEagle.ai guarantees that just-in-time app access remains secure, streamlined, and tailored to your organization's unique requirements.
Why are leading organizations implementing just-in-time access?
Leading organizations are implementing just-in-time (JIT) access as a proactive security and efficiency measure to address evolving challenges in IT and access management. Here’s why JIT access is becoming a priority:
1. Enhanced security: Just-in-Time (JIT) access reduces risks by granting access only when necessary, minimizing exposure to sensitive data. This approach limits the attack surface and prevents privilege abuse, ensuring users can’t misuse elevated rights. By restricting access to critical systems, JIT also mitigates insider threats and reduces accidental errors.
2. Regulatory compliance: JIT access ensures compliance with global standards like ISO 27001, NIST, and GDPR by limiting access to essential personnel and times. It simplifies audit processes with detailed logs showing who accessed what and when. This transparency not only ensures accountability but also makes your organization audit-ready.
3. Operational efficiency: JIT access automates workflows, reducing the time IT teams spend on manual provisioning and deprovisioning. This eliminates the burden of managing access manually and streamlines role-based permission assignments. By providing temporary access, JIT ensures resources are allocated efficiently without administrative overhead.
4. Cost optimization: JIT access optimizes license use by providing temporary access to occasional users, avoiding the need for extra licenses. It identifies underused resources, helping to cut unnecessary costs. Limiting access also reduces the risk of costly data breaches, saving organizations from significant financial losses.
5. Improved user experience: JIT access makes requests quick and simple, integrating with tools like Slack or Teams for seamless approvals. Employees and contractors receive access exactly when they need it, avoiding delays and overprovisioning. This streamlined process keeps workflows smooth, minimizes frustrations, and boosts overall productivity.
6. Scalability for dynamic workforces: JIT access supports remote and hybrid teams by adapting to their evolving needs. It provides timely access to systems, ensuring productivity regardless of location. This approach scales easily to manage dynamic workforce changes without compromising security.
Adopting Just-In-Time (JIT) access helps organizations reduce risks, stay compliant, and improve efficiency. CloudEagle.ai makes it simple by automating time-bound access, monitoring user activity, and streamlining approvals, ensuring the right people have access at the right time
Considerations while implementing just-in-time access
Implementing just-in-time access can bring many benefits, but there are some challenges like:
1. Integration challenges: Implementing just-in-time access can be tricky when integrating it with existing apps. Sometimes, platforms are incompatible, or custom integrations are needed, which can slow down the process and cause issues in setting up smooth access control.
2. Complex configurations: Setting up the rules for just-in-time access can get complicated, especially when dealing with different user groups, roles, and applications. It requires careful planning and might take more time and resources than you initially expect to define the right access windows and adjust permissions.
3. Monitoring and reporting challenges: Tracking and reporting on just-in-time access can be difficult, especially without the right monitoring tools. Ensuring that users follow the access rules and report their behavior accurately can be challenging, especially if data is scattered across different systems.
4. Inconsistent policies across departments: Different departments or teams may have different access needs, leading to inconsistent implementation of just-in-time access. Ensuring that all departments follow the same rules and time frames is tough without a unified approach.
5. User resistance: Some users may not be happy with just-in-time access, especially if they’re used to having open access all the time. This can lead to frustration and pushback, making it harder to enforce time restrictions effectively across the organization.
Conclusion
Just-in-time access is an easy and effective way to improve your organization's security. Limiting access to specific hours reduces the risk of unauthorized use and ensures that only the right people have access when needed.
With CloudEagle.ai, managing just-in-time access is simple and easy. It gives you complete control over who can access what, when, and for how long. The tool also helps you comply with security policies and industry regulations, making it a trusted and efficient solution for any organization.
Are you ready to improve security with just-in-time access?
Schedule a demo with CloudEagle.ai to see how simply you can implement just-in-time access.

%201.svg)







.avif)




.avif)
.avif)




.png)









