HIPAA Compliance Checklist for 2025

These days, companies are relying more on SaaS tools than legacy applications. The widespread use of SaaS has completely changed how organizations operate. According to reports, 80% of companies already use at least one SaaS solution.
But, as you consider adopting SaaS, you must focus on establishing strong security measures right from the start. Even a minor issue can expose your organization's data to breaches or unauthorized access, triggering serious SaaS security issues.
Therefore, you should carefully evaluate the security risks associated with the solution. This proactive approach can help you make informed SaaS purchasing decisions and safeguard your data without compromising your organization's integrity.
This article is for you if you're unaware of the common SaaS security risks. It covers the top six SaaS security risks and practical tips for securing your organization's SaaS stack.
What is SaaS Security?
SaaS security refers to the practices, technologies, and controls used to protect data, users, and applications within Software-as-a-Service environments. It focuses on ensuring that all information stored and processed in SaaS apps remains confidential, available, and tamper-proof.
Key components of SaaS security include:
- Data protection: Securing data at rest and in transit through encryption and secure storage.
- Identity & access management: Ensuring the right users have the right access using provisioning, deprovisioning, MFA, SSO, and least-privilege controls.
- Configuration management: Preventing misconfigurations that expose sensitive data or permissions.
- Visibility & monitoring: Tracking user activity, unusual behavior, and Shadow IT usage across SaaS apps.
- Compliance & governance: Meeting standards like SOC 2, HIPAA, ISO 27001, and GDPR through continuous monitoring and policy enforcement.
SaaS Security Architecture
A modern SaaS security architecture focuses on securing what the customer controls: identity, access, configurations, data, and usage across SaaS apps.
1. Identity & Access Controls (Primary Layer)
Identity is the strongest control you own in SaaS. A secure access layer includes:
- Enforcing SSO through an IdP (Okta, Azure AD, Ping).
- Requiring MFA for all high-risk apps.
- Applying least-privilege access using RBAC/GBAC.
- Enabling time-bound access for contractors or temporary roles.
- Automating provisioning & deprovisioning to prevent missed access revocations.
2. Data Protection & Privacy Controls
Protect data across storage, transport, and usage:
- Encryption at rest and in transit.
- Tokenization/redaction for sensitive fields.
- Configurable retention policies for compliance.
- Validated backup and restore procedures.
3. SaaS Security Posture Management (SSPM)
Misconfigurations drive a large portion of SaaS security incidents. SSPM helps by:
- Enforcing secure default settings.
- Detecting configuration drift.
- Monitoring risky sharing behaviors (public links, external access).
- Standardizing security policies across SaaS apps.
4. Monitoring, Detection & Response
Visibility is essential for detecting abnormal behavior. Key capabilities include:
- Centralized activity logging.
- Behavioral analytics for risky events.
- Real-time alerts on suspicious actions.
- SIEM/SOAR integration for automated response.
What Do You Mean by SaaS Risks?
SaaS risks are the security threats and vulnerabilities that arise when organizations use cloud-based applications.
Common SaaS Security Risks
- Unauthorized access due to weak IAM, poor provisioning, or delayed deprovisioning
- Misconfigurations in sharing settings, permissions, or security defaults
- Data breaches caused by exposed data, poor encryption, or compromised accounts
- Insider threats from employees or contractors with excessive or unused privileges
- Unsecured APIs & integrations that can be exploited by attackers
- Shadow IT from employees using unapproved SaaS apps
- Compliance violations (SOC 2, HIPAA, GDPR, ISO 27001) due to missing controls or audit gaps
- Vendor-side vulnerabilities in the SaaS provider’s infrastructure
Why SaaS Risks Matter
- Lead to data loss or exposure of sensitive information
- Create operational disruption and unplanned downtime
- Result in compliance penalties or legal exposure
- Damage brand reputation and customer trust
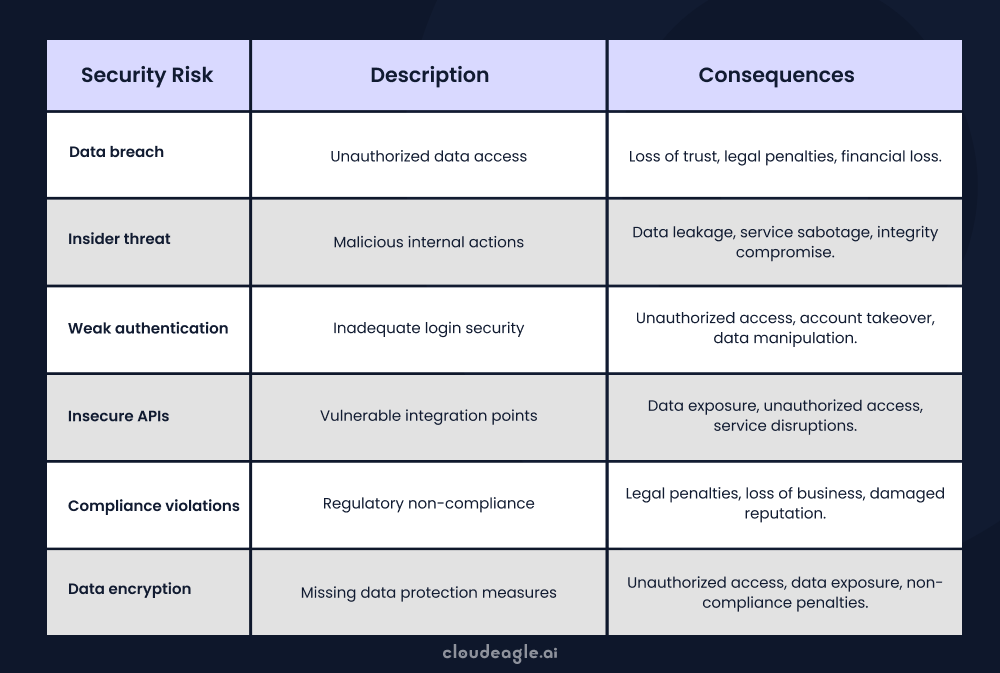
6 Common SaaS Security Risks Organizations Should Know
Common SaaS security issues include data breaches, misconfigurations, unauthorized access, and compliance violations. These are among the top risks organizations must monitor when using SaaS platforms.
Such issues often result from weak access controls, poor authentication practices, a lack of visibility into SaaS usage, and vulnerabilities introduced by third-party integrations.
To address these SaaS risks, businesses should implement strong authentication protocols, encrypt sensitive data, conduct regular security audits, and monitor SaaS activity continuously.
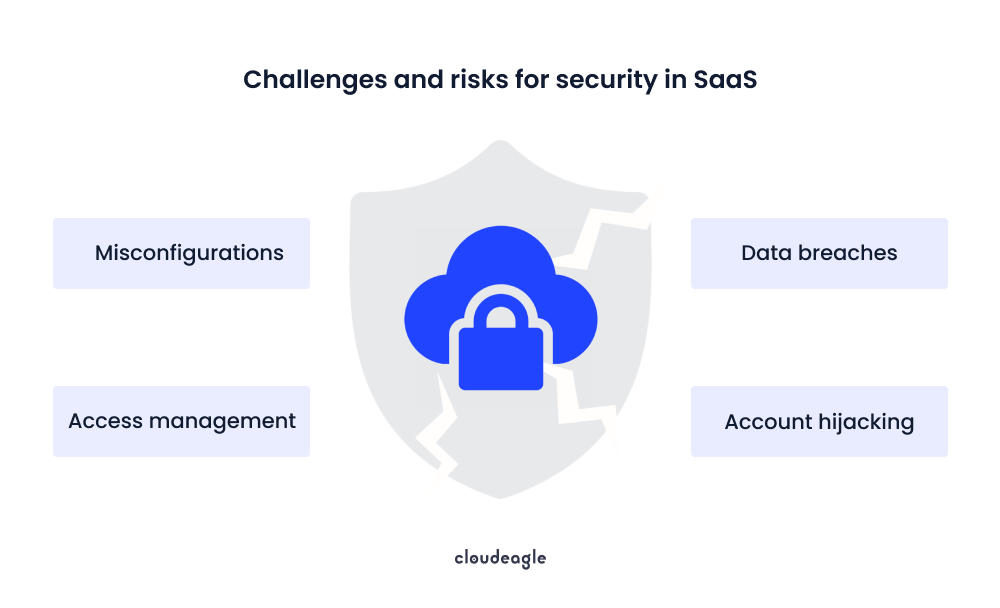
As SaaS usage continues to soar in 2025, it's crucial to understand the top security risks. From unauthorized access to insider threats, here are seven common SaaS security risks you need to know to keep your SaaS stack safe.
1. Unauthorized access & insider threats
Unauthorized access often happens due to poor provisioning, weak authentication, or delayed deprovisioning.
When ex-employees retain access, it can lead to data breaches, IP theft, and insider threats.
Fix: Enforce SSO, MFA, least privilege, and automated offboarding.
Key points:
- 36% of employees retain access after leaving without proper deprovisioning
- Password sharing in chats/emails increases the risk of unauthorized access
- Manual revocation often leaves orphaned accounts active
- Insider threats arise when former employees misuse leftover access
Check this table to understand the different unauthorized access methods you should know.

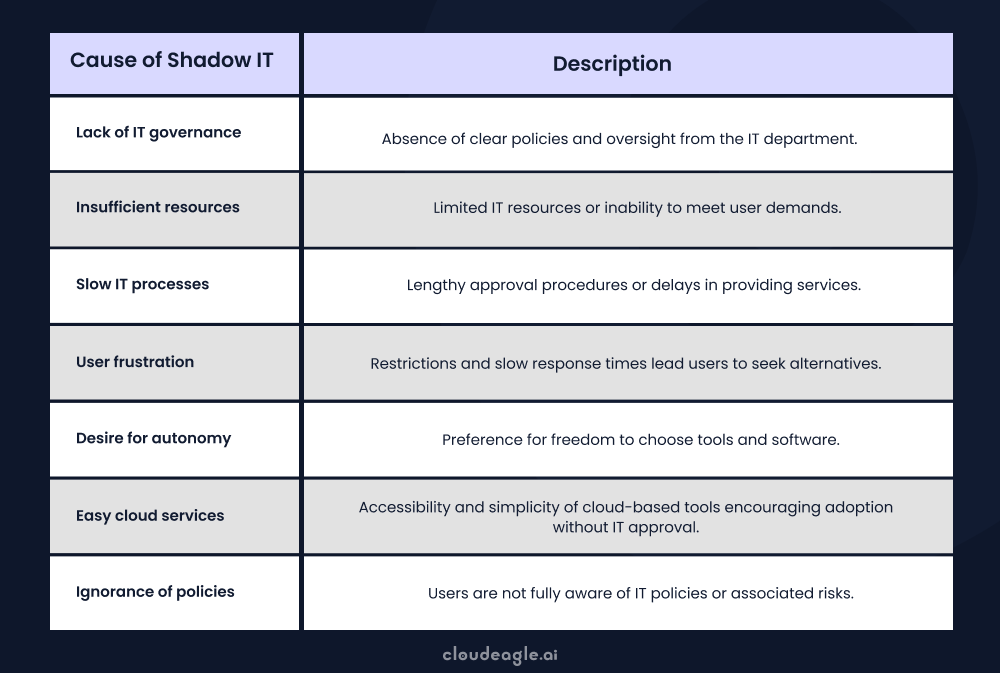
2. Shadow IT
Employees frequently use unapproved SaaS apps without IT’s knowledge, creating blind spots and compliance risks.
Unvetted apps may lack proper security controls or regulatory compliance.
Fix: Enable Shadow IT detection, set usage policies, and monitor third-party apps.
Key points:
- 80% of employees use unapproved SaaS tools at work
- Shadow purchases increase third-party risk and hidden costs
- Unmonitored apps often bypass security controls
- Free-tier apps may lack compliance or data protection standards

Organizations must educate workers on the dangers of using unapproved apps. They must also establish rules and processes to oversee and monitor the use of third-party apps.
This table will help you understand the causes of shadow IT, enabling you to know how to stay protected from this risk.
3. Poor Compliance & Regulation Issues
Using SaaS vendors that don’t meet standards like SOC 2, ISO 27001, GDPR, HIPAA, or PCI DSS exposes the business to legal and saas risks.
Non-compliant vendors introduce gaps that your internal controls cannot cover.
Fix: Continuously evaluate vendor compliance and review certifications.
Key points:
- Choosing non-compliant vendors leads to regulatory penalties
- PCI DSS requires vendors to meet specific SaaS risk controls
- Many vendors falsely claim compliance without audits
- Third-party non-compliance creates hidden SaaS risks
4. Misconfigurations
Complex SaaS apps often have insecure default settings, risky sharing permissions, or disabled MFA.
Small configuration errors can expose data or expand attack surfaces.
Fix: Use SSPM to enforce secure configurations and detect drift.
Key points:
- Misconfigured SaaS settings cause long-term exposure
- Multi-layer cloud designs increase configuration complexity
- Lack of SaaS security knowledge leads to recurring issues
- SSPM provides full application visibility into app-level security posture
5. Storage and data loss

Storing sensitive data in cloud apps introduces risks such as breaches, corruption, accidental exposure, or vendor outages.
Poor backup controls increase the impact of data loss.
Fix: Use encryption, strong retention rules, and validated backup/restore processes.
Key points:
- Vendor-owned servers increase dependency & third-party risk
- Outages or device failures can trigger data loss events
- Data may be exposed through poor retention or storage practices
- Regular data backups are essential for continuity
6. Non-Compliance by SaaS Vendors
Some SaaS providers may falsify compliance claims or skip required audits. Shadow IT makes it harder to monitor these vendors, increasing risk exposure.
Fix: Vet all vendors thoroughly and block non-compliant apps.
Key points:
- Non-compliant SaaS vendors put your sensitive data at risk
- Missing certifications (SOC 2, ISO 27001, GDPR) increases liability
- Shadow IT introduces hidden vendors that bypass IT review
- Vendor compliance must be validated regularly

Key Factors Contributing to SaaS Security Risks
Excessive permissions and admin sprawl expand the attack surface, enabling unauthorized access and amplifying insider threats.
Weak deprovisioning and JML processes leave orphaned accounts active, a persistent SaaS risk when employees change roles or leave.
Shadow IT and unmanaged integrations connect sensitive systems without oversight, bypassing centralized policies and exposing saas data security to hidden data flows.
- Over-permissioned roles/admin sprawl → unauthorized access and lateral movement.
- Broken JML/deprovisioning → insider threats via lingering credentials and tokens.
- Shadow IT, marketplace apps, and unmanaged integrations → unvetted scopes and silent data exfiltration.
- Misconfigurations, cross-tenant sharing, poor audit trails, and uneven controls → breaches and compliance failures.
Why Is It Important to Address SaaS Security Concerns in Organizations?
SaaS security concerns must be addressed because businesses entrust critical data to third-party providers. Misconfigurations, unauthorized access, and data breaches can easily arise due to the shared responsibility model.
Impact of Ignoring SaaS Risks
- Compliance violations
- Data loss or exposure
- Reputational damage
- Financial penalties
How to Protect Your Organization
- Enforce strong identity and access controls
- Conduct regular audits and access reviews
- Continuously monitor usage across all SaaS applications
Key SaaS Security Concerns
- Security of sensitive data:
SaaS apps store customer data, financial records, and IP. Strong security prevents unauthorized access, breaches, and data leaks. - Operational continuity:
Breaches can disrupt workflows, cause downtime, and reduce productivity. Prioritizing SaaS security helps maintain smooth business operations. - Reputation protection:
Security incidents damage trust with customers, partners, and stakeholders. Strong SaaS security safeguards your brand reputation. - Regulatory compliance:
Industries must meet standards like GDPR, SOC 2, PCI DSS, ISO, and HIPAA. Security controls help avoid penalties and ensure compliance. - Financial resilience:
Breaches lead to recovery costs, legal fees, and fines. Prioritizing SaaS security reduces financial exposure and strengthens your defenses.
How SaaS security risks impact your business
SaaS security risks translate directly into financial, operational, and brand damage when controls fail inside apps. Here’s how gaps in SaaS data security and governance show up in the business.
- Data exposure and breach costs: Unapproved AI plugin pulls customer records from a helpdesk; you incur incident response, legal notifications, and credit monitoring fees.
- Operational disruption: Account takeover of a marketing platform pauses campaigns and breaks single sign-on; misconfigurations disable webhooks, halting order fulfillment.
- Audit failures and fines: Missing access reviews in a CRM and excessive admin roles lead to SOC 2 findings or GDPR penalties due to poor evidence trails.
- Reputational damage: Leaked sales forecasts from shared links erode partner trust and elongate sales cycles, increasing churn risk.
- Vendor lock-in: Poor offboarding and no export plan trap data; you pay for extensions and custom scripts to migrate critical records.
- Budget waste: Ex-employee retains access to CRM and paid seats remain active; over‑permissioned users drive premium license creep and duplicate tools.
Addressing each SaaS risk with least privilege, continuous configuration monitoring, and a modern SaaS security solution in your security SaaS stack reduces exposure while improving governance and spend efficiency.
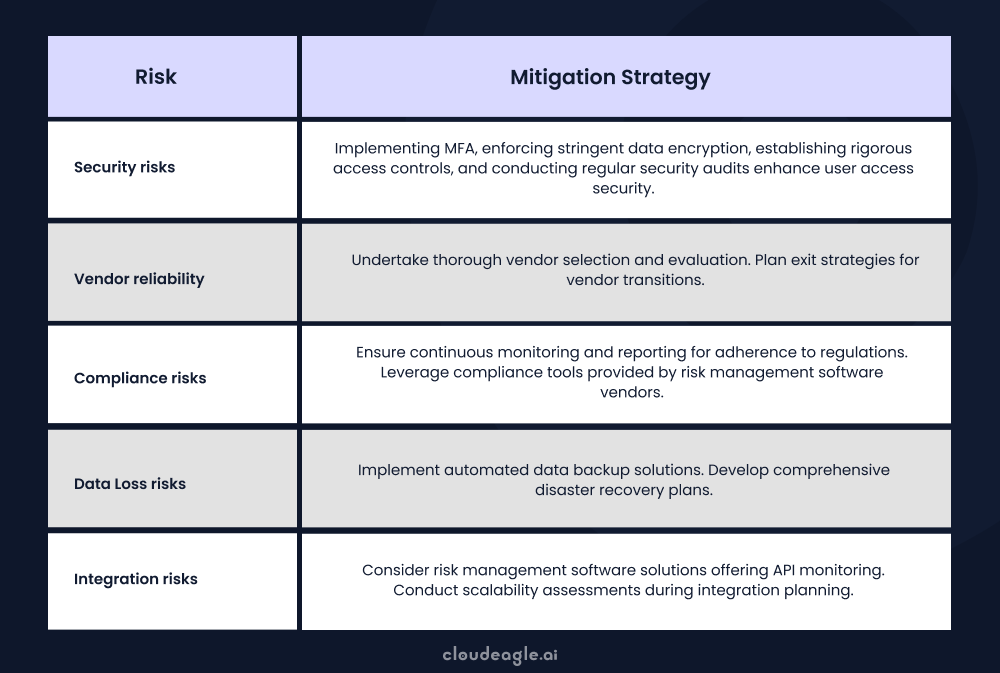
How Can Organizations Mitigate SaaS Security Risks?
To mitigate SaaS security risks effectively, organizations must adopt a comprehensive strategy. This includes strong authentication, data encryption, regular security assessments, and ongoing employee training.
Tools like Cloud Access Security Brokers (CASBs), Data Loss Prevention (DLP) solutions, and Zero Trust architectures play a key role in protecting data and controlling access.
Here’s how you can protect your organization from SaaS security risks.
1. Using a SaaS management tool
A SaaS management platform provides visibility into your apps so you can manage usage, monitor access, and enforce security standards. By centralizing administration, you can detect unwanted access or possible vulnerabilities and take immediate action.
A bird's-eye view of the SaaS portfolio provided by these platforms can help IT teams detect and eliminate shadow IT applications immediately. It’ll also make verifying a vendor’s compliance with security regulations easier for the security team.
For example, you can use a SaaS management platform like CloudEagle.ai to prevent shadow IT and mitigate the saas security concerns of third-party applications. This tool simplifies and centralizes your organization's SaaS management with various features and automated workflows.
With CloudEagle.ai, you can oversee all your SaaS applications through one dashboard. This lets you comprehensively overview your SaaS environment, including usage, expenses, user access, and security.
With CloudEagle.ai's automated workflows, you can automate tasks such as provisioning and deprovisioning, simplify user provisioning, and minimize your IT team's manual workload. This tool removes time-consuming tasks like user provisioning and deprovisioning, potentially saving up to 500 hours per year.
Here's a testimonial from Alice Park at Remediant. She spent a significant amount of time manually provisioning and deprovisioning users across different applications. However, by integrating with CloudEagle.ai's HRIS system, user management was streamlined through automated provisioning and deprovisioning workflows, saving Alice valuable time.
You can use a SaaS management platform like CloudEagle.ai to strengthen your Application Portfolio Management strategy. It helps prevent shadow IT and reduce SaaS security risks by offering a centralized view of all third-party applications in use. This visibility ensures your team can manage, monitor, and optimize the entire SaaS stack effectively.
2. Implementing robust authentication and authorization
Strong authentication and authorization processes are critical for protecting sensitive data and preventing unwanted access to SaaS apps.
Access controls restrict access to resources, such as SaaS apps, to only authorized users. Strong access restrictions may be implemented in your SaaS system in various ways, including:
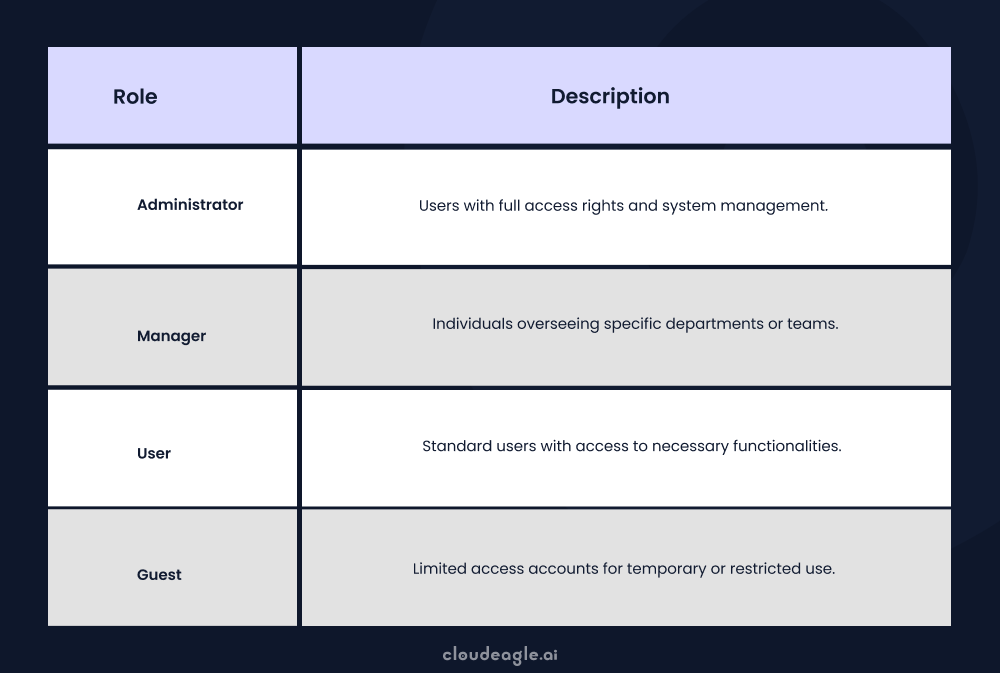
3. Role-based Access Controls (RBAC)
RBAC simplifies access management by tying permissions to user roles, not individual identities. This enhances security by limiting access to only what's necessary, reducing the risk of breaches and other saas security issues.
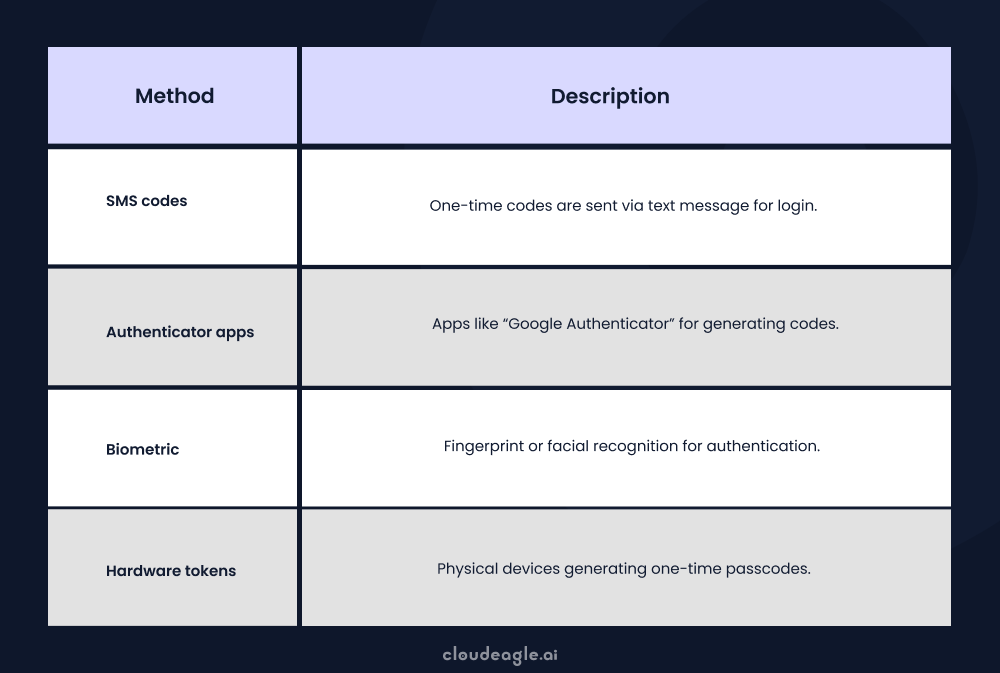
4. Multi-factor Authentication (MFA)
MFA provides an extra layer of protection by asking users to give other credentials along with their login and password, such as a one-time password or a biometric scan. Proper authorization restrictions guarantee that users only get access to the required features and data for their roles and responsibilities.
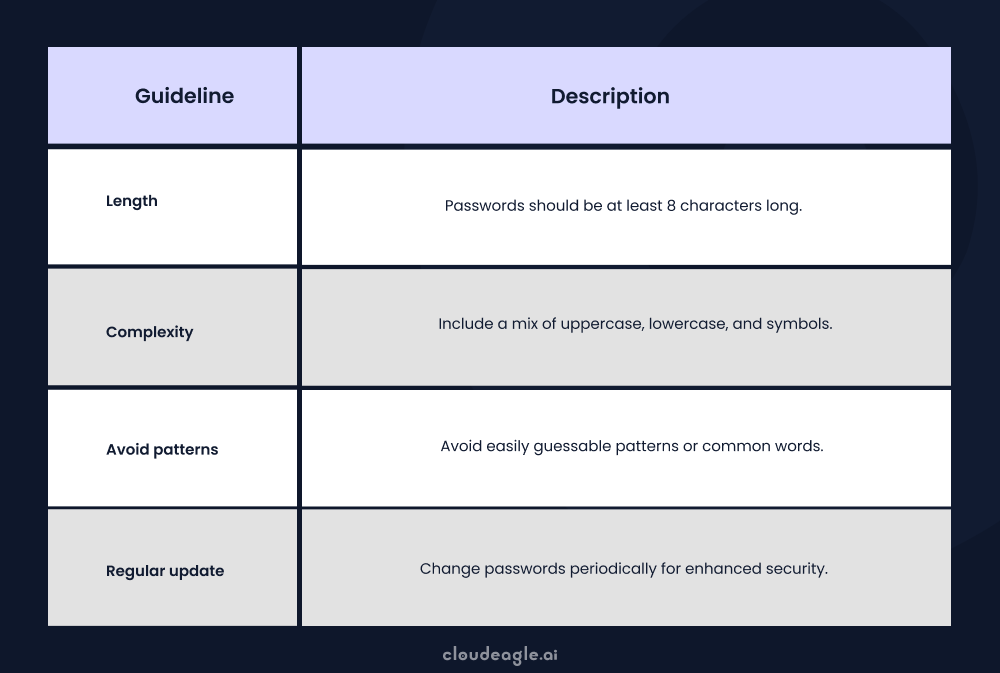
5. Password Guidelines
Password guidelines enforce strong password practices, including complexity and regular changes, to prevent unauthorized access and minimize SaaS risks.
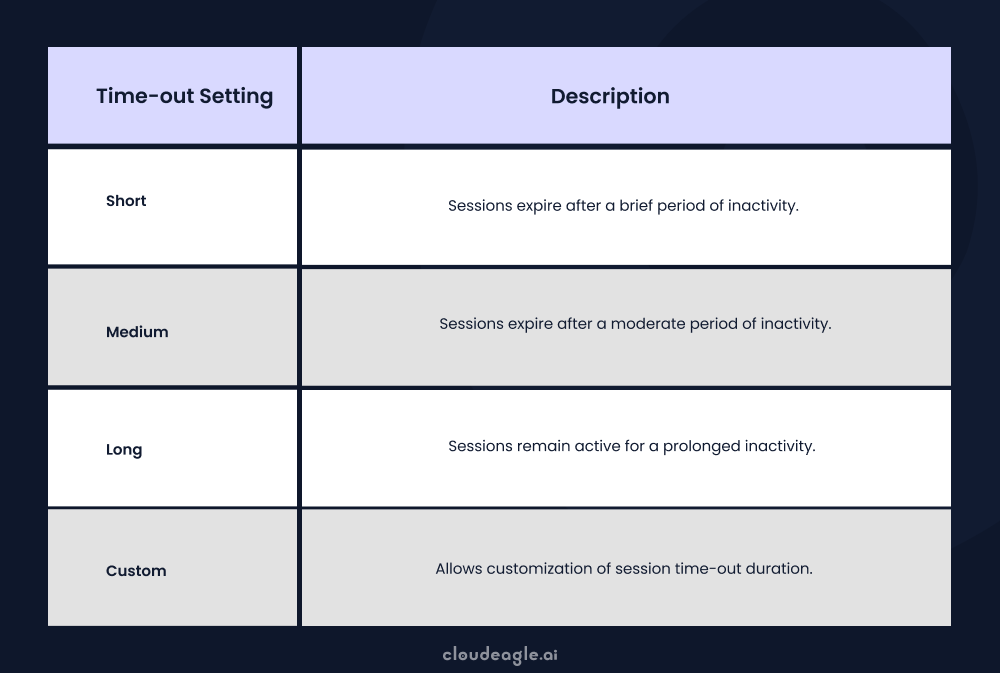
6. Session Time-outs
Session timeouts automatically log users out after inactivity, mitigating risks from unattended devices or shared networks.
If you need a tool to enforce robust authentication and authorization, look no further than CloudEagle.ai in the realm of Identity and Access Management (IAM). CloudEagle.ai stands out with its comprehensive features for managing identities and access, providing a groundbreaking approach to security.
With features such as real-time monitoring, robust authentication, and seamless integration, Cloudeagle.ai’s integration library ensures accuracy and efficiency throughout the identity and access lifecycle. Its automation capabilities, customizable workflows, and user-friendly interfaces empower IT and HR teams, streamlining operations and boosting productivity.
7. Conducting consistent compliance and regulatory audits
Ensuring SaaS compliance requires an ongoing process. Thus, you should constantly monitor and audit user activity and vendors to mitigate SaaS security risks. These audits assist businesses in identifying redundancies in their security measures.
Security teams must frequently monitor and assess their SaaS providers' compliance with industry standards to identify any SaaS security issues that must be addressed.
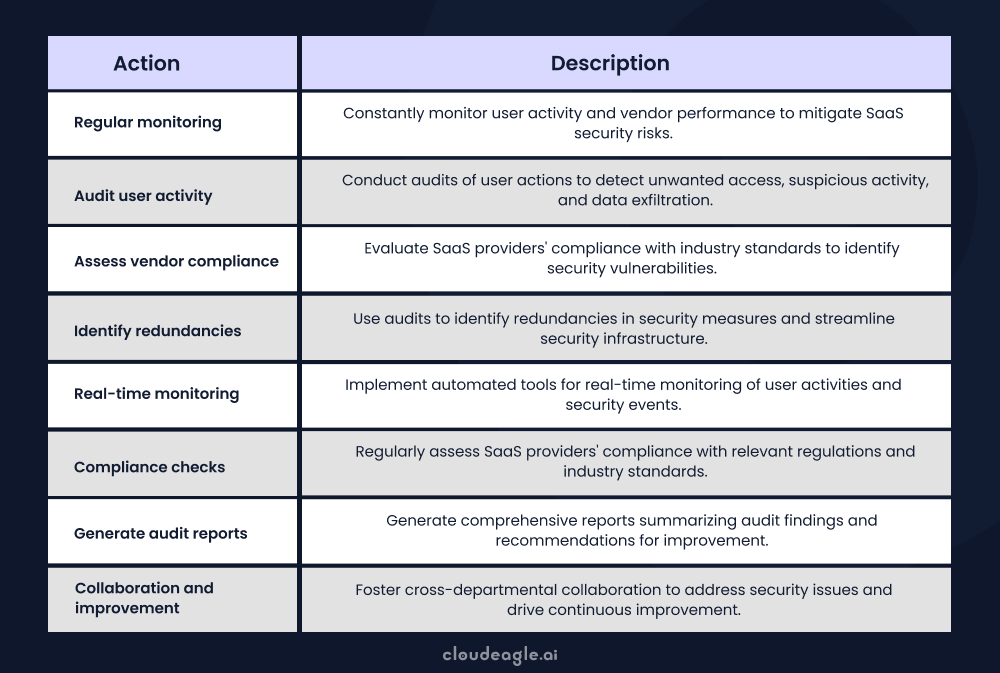
Also, thoroughly checking vendors is crucial. Knowing their compliance practices well is key, as any issues could cause problems for your organization. Organizations can confidently handle compliance and lower compliance-related risks by paying attention to these aspects.
8. Conducting thorough risk assessment and due diligence
BBefore implementing a SaaS application, it is necessary to perform a complete SaaS risk management assessment. Consider the possible SaaS security concerns connected with the SaaS application, such as data handling procedures, encryption mechanisms, vulnerability management processes, and troubleshooting SSL errors.
SSL (Secure Socket Layer) errors can occur for multiple reasons, including a mismatch of domain names, outdated SSL certificates, and an untrusted Certificate Authority. These can hinder a web server and browser's ability to establish a secure connection, leading to potential risks for data security.
Conduct due diligence on the SaaS vendor. Learn about their security handling capabilities, compliance, incident response abilities, and data protection measures, including their ease in managing and fixing SSL certification errors. This thorough assessment gives enterprises the information they need to make informed decisions.
They can select SaaS providers who satisfy their security standards, thus reducing the risk of security breaches or data exposures.
9.Maintaining a SaaS security checklist
Creating a detailed SaaS security checklist tailored to your organization's SaaS usage is one of the core Saas security best practices. The checklist must include data encryption, frequent backups, safe API integrations, incident response methods, and staff security awareness programs.
You must also ensure that sufficient tools are available to meet the requirements laid out in your checklist. Having an essential API security scanner available is a good example. Review and update the checklist regularly to keep up with developing saas security concerns and emerging risks.

To assess security risks in your organization and optimize Shadow IT for increased ROI, listen to Joshua Peskay, 3CPO (CIO, CISO, and CPO) at RoundTable Technology. He discusses managing Shadow IT and introduces an ROI scoring system for SaaS tools to optimize technology investments.
What Goes into a SaaS Security Risk Assessment?
- Inventory all SaaS apps, third‑party integrations, and connected identities to baseline saas risk.
- Map data flows, classify sensitivity, and note storage locations for saas data security.
- Assess identity model: SSO coverage, enforced MFA, RBAC design, least‑privilege, and external sharing.
- Review configuration baselines and SSPM findings; document misconfigurations and drift.
- Evaluate vendor compliance posture (SOC 2, ISO 27001, GDPR) and incident response processes.
- Analyze audit logs and alerts for anomalies, failed auths, data exfiltration, and API abuse.
- Rate threat likelihood and business impact to quantify saas security risks.
- Prioritize remediation, assign owners, budgets, and timelines; define success metrics.
- Track progress and validate fixes; integrate learnings into your security saas program and saas security solution.
What Are the Most Important SaaS Security Best Practices?
Reduce SaaS security risks by standardizing identity, tightening access, and continuously validating posture and vendors—ideally automated by a security SaaS or SaaS security solution—to protect SaaS data security.
- Enforce SSO across apps and require MFA for all privileged and external users.
- Apply least privilege with role-based access; run periodic access reviews and capture evidence.
- Use time-bound, just-in-time access for admins and sensitive scopes; auto-expire shared links.
- Automate JML provisioning/deprovisioning via HRIS to eliminate orphaned accounts.
- Continuously monitor configurations with SSPM; encrypt sensitive data at rest and in transit.
- Restrict external sharing, third-party marketplace apps, and high-risk integrations by policy.
- Maintain up-to-date vendor due diligence and compliance artifacts (e.g., SOC 2, ISO, DPIAs).
- Run ongoing phishing simulations and security awareness training to lower human-driven SaaS risk.
Conclusion
SaaS security risks, including data breaches, insider threats, and compliance challenges, are a major concern. To ensure safety, prioritize strong security measures, train your team, and adhere to regulations.
However, robust SaaS security solutions can help businesses safeguard critical data by ensuring proper access controls, user provisioning, and application visibility.
If you need assistance selecting the right tool to enhance your organization’s SaaS stack, we recommend CloudEagle.ai, a comprehensive SaaS management and procurement platform with robust security management features.
If you need assistance implementing a SaaS governance framework, consider scheduling a demo with CloudEagle.ai.
Frequently asked questions
1. What are the risks of using SaaS?
SaaS risks include data breaches, lack of visibility, poor access control, vendor lock-in, and compliance issues.
2. What is considered the biggest risk area for the SaaS service model?
Data security is the biggest risk, as sensitive information is stored off-site and may be vulnerable to breaches or unauthorized access.
3. What is the risk management of SaaS?
SaaS risk management involves identifying threats, assessing vulnerabilities, and implementing controls to protect data and ensure compliance.
4. What are the 5 key security elements of the SaaS model?
The 5 key security elements are data encryption, access control, secure APIs, regular audits, and compliance with standards.
5. What should you look for in SaaS security Checklist?
A SaaS Security Checklist should focus on existing security rules, level of compliance, employee authentication methods, data encryption and tokenization, and automatic backups.

%201.svg)










.avif)




.avif)
.avif)




.png)









