HIPAA Compliance Checklist for 2025

How is your organization's SaaS security holding up with all the applications in use? Does your IT team have a SaaS security strategy to deal with the dangers of data breaches, unauthorized access, and other compliance issues?
Are you constantly worried about these questions?
When SaaS usage grows in organizational settings, the primary challenge often revolves around effectively managing the SaaS platforms while maintaining robust security measures for the organization.
As per a study, companies estimate that 70% of the business apps they use today are SaaS-based, and by 2025, this number will grow to 85%.
As organizations increasingly use cloud-based apps, implementing top SaaS security practices is crucial to safeguarding customer data and financial information stored within these apps.
This article discusses eight SaaS security best practices you should follow in 2024 to secure your SaaS portfolio.
TL;DR
- SaaS dominance raises security stakes:
About 70% of business apps today are SaaS-based, and this will reach 85% by 2025, making effective SaaS security practices mission critical. - Top security risks include unauthorized access, shadow IT, and misconfigurations:
Organizations struggle with ex-employee access, unapproved (shadow IT) apps, and complex setups that often lead to serious data breaches and compliance failures. - Comprehensive SaaS management platforms are essential:
Using automated SaaS management tools provides full visibility, central control over user access, and helps detect vulnerabilities or unauthorized use — vital for both security and compliance. - Strong authentication and vendor compliance are crucial:
Enforce single sign-on (SSO), multi-factor authentication (2FA), and only work with vendors who meet key compliance standards like GDPR and SOC 2 to safeguard sensitive data. - Continuous monitoring and proactive review prevent incidents:
Regularly update security settings, audit user rights, encrypt sensitive data, and implement incident response strategies to minimize the risk of breaches and stay compliant with evolving regulations.
1. What is SaaS security?
SaaS security refers to the practice of safeguarding user privacy and data within subscription-based cloud applications.
SaaS security refers to the practice of safeguarding user privacy and data within subscription-based cloud applications.
These applications host substantial amounts of sensitive data and are accessible from various devices by different users, so they present inherent privacy and data security risks.
SaaS security ensures that the information you store and access through these online applications remains safe from unauthorized access, data breaches, or other cyber threats.
It involves various strategies, such as encryption, user authentication, access controls, and regular security updates, to keep your data and applications secure while using cloud-based services.
2. Key components of SaaS security
Effective SaaS security requires a multi-layered approach that addresses the unique challenges of distributed cloud applications.
Unlike traditional on-premises software, SaaS environments demand specialized security components that can operate across multiple vendors, platforms, and user access points while maintaining visibility and control.
- Identity and Access Management: Controls who can access which applications and with what permissions. Critical for SaaS environments where users access multiple applications from various devices and locations.
- Data Protection and Encryption: Safeguards sensitive information both in transit and at rest across SaaS platforms. Essential because data flows between multiple cloud services and storage locations.
- Configuration and Posture Management: Monitors and maintains secure settings across all SaaS applications. Prevents misconfigurations that commonly lead to data breaches in complex SaaS stacks.
- Monitoring and Logging: Provides continuous visibility into user activities, access patterns, and potential security threats. Enables rapid detection of anomalous behavior across distributed applications.
- Incident Response: Establishes procedures for quickly addressing security events and breaches. Particularly important in SaaS environments where incidents can affect multiple integrated systems.
- Compliance and Governance: Ensures adherence to regulatory requirements and internal security policies across all SaaS applications and data flows.
- Vendor Risk Management: Evaluates and manages security risks associated with third-party SaaS providers and their security practices.
These components work together to create a comprehensive security framework that adapts to the dynamic nature of SaaS environments, providing the foundation for implementing the security best practices detailed in the following sections.
3. Why should you pay attention to SaaS security?
According to BetterCloud, IT professionals' top concerns about using SaaS are data security and protection against cybercrime.
The data carried by SaaS apps - ranging from financial information and client records to intellectual property - is invaluable and must be protected. Failures in security can lead to data breaches, financial losses, and reputational damage.
Companies can limit these risks with proper knowledge of the risks and appropriate security measures for their business.

4. SaaS security architecture: how modern stacks stay protected
Modern SaaS security architecture relies on layered defenses that span identity, data, network, and application domains to create comprehensive protection across distributed tech stacks.
This multi-layered approach ensures no single point of failure can compromise the entire security posture.
- Identity and SSO integration: Deep SaaS & Identity Integrations with 500+ direct integrations allow centralized authentication management, while integrated platforms automatically sync user provisioning and deprovisioning across all applications.
- Access governance and reviews: Automated User Access Governance ensures the right employees have the right access at the right time while minimizing security risks through intelligent access management. Platforms combine with IdPs to enforce least-privilege principles and automate quarterly access certifications.
- Data encryption and classification: End-to-end encryption policies are enforced consistently across SaaS applications, with integrated platforms providing visibility into data flows and classification standards.
- Configuration and posture management: Continuous monitoring of SaaS application configurations ensures security baselines are maintained, with automated remediation workflows triggered through SIEM integrations.
- Monitoring and analytics: No code Slack-enabled workflows enable IT & security teams to streamline employee onboarding/offboarding, access reviews, and renewals while providing centralized visibility into security events across the entire SaaS portfolio.
Integrated SaaS management platforms significantly enhance security architecture maturity by providing unified policy enforcement, automated governance workflows, and comprehensive visibility that traditional point solutions cannot achieve.
5. 6 Common SaaS security threats
You never know when your organization might encounter security threats, so it's crucial to remain vigilant and aware of occurrences within your organization that could create cloud security vulnerabilities, such as:
1. Unauthorized access
Unauthorized personnel, including former employees, having access to SaaS apps could cause data breaches and misuse of sensitive information.
These breaches can lead to theft, manipulation, or exposure of confidential information, potentially causing significant harm to individuals or organizations.
Unauthorized personnel, including former employees, having access to SaaS apps could cause data breaches and misuse of sensitive information.
These breaches can lead to theft, manipulation, or exposure of confidential information, potentially causing significant harm to individuals or organizations.
Also, insider threats can result from malicious actions, negligence, or a lack of awareness about security best practices.
These threats stem from individuals within the organization, such as employees or contractors, who intentionally or accidentally compromise security.
To avoid these security lapses, you must implement SaaS security best practices, such as auto-deprovisioning, to prevent unauthorized access.
2. Shadow IT
Controlling shadow IT is an ongoing struggle for organizations. This is compounded by the common use of SaaS on personal devices or via unsecured networks, further elevating security risks.
Employees using unapproved SaaS apps without authorization from the IT team create security risks, data breaches, and increased app spending.
These unapproved apps can pose security threats like data leaks or malware infections.
3. Scattered platforms and applications
SaaS ecosystems often comprise multiple applications from different SaaS vendors.
This fragmentation complicates the implementation of a cohesive security strategy, leaving potential gaps in defense and making threat monitoring across platforms difficult.
Cybercriminals exploit these vulnerabilities, as evidenced by numerous high-profile data breaches.
4. Intricate custom configurations
While SaaS platforms offer flexibility for organizations to tailor configurations, this customization can increase complexity and the risk of oversight in security settings.
Misconfigurations, a common occurrence, have become a leading cause of data breaches in recent times.
5. Poor compliance and regulation
Using non-compliant SaaS providers can result in compliance violations, legal consequences, and reputational damage.
Compliance violations may result in legal actions, fines, or penalties imposed by regulatory authorities.
Additionally, failing to meet compliance requirements can damage the company's reputation, eroding trust among customers and stakeholders.
6. Cloud misconfiguration and evolving environments
Improper cloud system configuration could pose security risks.
Even minor misconfigurations can have serious implications, compromising the security of your entire infrastructure.
Additionally, in SaaS environments, users have the flexibility to access applications from diverse devices and locations, which creates a challenge for IT security teams.
6. Developing a SaaS security framework
A SaaS security framework provides a structured approach to managing security risks across your organization's cloud application portfolio.
Unlike ad-hoc security controls that react to individual threats, a comprehensive framework proactively addresses vulnerabilities, ensures compliance, and maintains governance at scale as your SaaS stack grows.
Building an effective framework requires a systematic approach:
- Inventory and classify all SaaS applications across departments to eliminate shadow IT and understand your complete attack surface
- Map security risks and regulatory requirements specific to each application and data type, identifying high-risk scenarios
- Define comprehensive policies for user access controls, data protection standards, and procurement approval workflows
- Select and implement governance tools, including SSO, SaaS management platforms, and CASB solutions for policy enforcement
- Establish continuous monitoring and review processes for access rights, security configurations, and compliance status
- Create clear ownership structures and automated workflows that eliminate manual bottlenecks in approval and review processes
Each step directly addresses common challenges: automated discovery prevents shadow IT proliferation, policy-driven access controls reduce manual review overhead, and integrated renewal workflows prevent last-minute scrambling.
Modern AI-driven platforms can automate user access governance and significantly reduce security risks while minimizing manual effort.
7. Getting SaaS secure: turning best practices into action
Moving from understanding SaaS security risks to actually implementing secure saas practices requires a systematic approach that addresses the root causes: scattered visibility, manual access management, and uncontrolled shadow IT.
IT and security teams need quick wins that immediately strengthen their security posture while reducing operational overhead.
The key is transforming reactive security management into proactive governance through automation and centralized control.
Here's your tactical action plan to secure saas applications:
- Run a comprehensive SaaS discovery - Identify all applications across SSO, finance systems, and browser data to establish your complete inventory
- Prioritize high-risk applications - Focus first on apps with sensitive data access, admin privileges, or compliance requirements
- Enable SSO and MFA - Implement single sign-on and multi-factor authentication for critical applications immediately
- Centralize access requests - Create approval workflows that eliminate scattered email and Slack requests
- Automate user provisioning/deprovisioning - Set up rules-based access management tied to your HRIS system
- Schedule recurring access reviews - Automate quarterly reviews to identify and remove unnecessary permissions
- Implement renewal workflows - Automate contract tracking and approval processes to prevent last-minute renewals and optimize licensing
8. 8 Essential SaaS security best practices
To stay ahead of emerging threats, ensure you have built a robust security framework with SaaS security best practices in place. This SaaS security checklist includes:
1. Use a SaaS management platform for complete app visibility
A study by Resmo notes that only 26% of organizations have embraced automation for monitoring SaaS application security.
Implementing a SaaS management platform helps you centralize and manage all your SaaS apps on a single dashboard. It gives a 360-degree overview of your SaaS environment, including application use, spending, user access, and security.

Constant surveillance helps you detect and manage possible vulnerabilities and unauthorized SaaS usage and shadow IT within your firm.
Streamlined SaaS application management gives you the insight to make cost-optimization decisions and ensure that your business adheres to security guidelines and standards.
Streamlined SaaS application management gives you the insight to make cost-optimization decisions and ensure that your business adheres to security guidelines and standards.
Using a SaaS management platform has become an organization's go-to SaaS security standard strategy to prevent users from purchasing unsanctioned applications.
2. Enhance your authentication with SSO and 2FA
Integrating single sign-on (SSO) and two-factor authentication (2FA) significantly reduces the risks of using weak or repeated passwords and unauthorized access to your SaaS applications.
SSO requires users to provide one-time authentication to enable access to multiple apps.
2FA provides an extra layer of protection by requiring users to provide additional verification, like a one-time password or biometric authentication.
3. Ensure that your vendors comply with security regulations
A Superoffice study claims that 60% of organizations believe that governance and compliance are their major concerns when dealing with cloud services.
Before implementing a SaaS app, assessing the vendor's security standards is critical. Before implementing a SaaS app, assessing the vendor's security standards is critical.
Check that they adhere to industry-standard security measures and laws such as the General Data Protection Regulation (GDPR), the Health Insurance Portability and Accountability Act (HIPAA), or the International Organization for Standardization (ISO) 27001.

Assess the vendor's security policies, data handling methods, and certifications to guarantee that your data will be safeguarded in accordance with your organization's security standards.
Do not sign a contract with a vendor lacking common SaaS compliance certifications like GDPR and SOC 2. Otherwise, you might put your SaaS data security at risk, lose valuable customer and financial data, and lose revenue.
4. Encrypt your data
Encryption is critical to ensuring the security of sensitive data handled or transmitted through SaaS applications. As per Statista, 38 percent of businesses are specifically concerned about encrypting their organizations' data.
Encryption turns data into an unreadable format that can only be accessed by authorized individuals with the decryption key. Encrypting your data adds an extra layer of security, even if there is a breach.

Ensure your data is encrypted during transit and at rest. The channels connected with SaaS apps often use Transport Layer Security (TLS) to safeguard data in transit. Some SaaS providers provide additional encryption features for data protection at rest.
Check each SaaS service to see whether data encryption is possible by default and, if so, activate it.
5. Prevent shadow IT with centralized procurement
G2 research shows that, by 2025, three in four people believe that shadow IT will be a bigger security issue at their companies.
Shadow IT is common in organizations with a disorganized procurement process. SaaS management platforms now have procurement workflows to automate the process and provide 100% transparency with real-time progress updates.
Implement a centralized procurement process and completely eradicate the risks of shadow IT .
6. Manage user access effectively
Security Magazine says 31% of former employees still have access to an organization's SaaS applications and other sensitive information.
Another report from TechRepublic reveals that around 20% of organizations experienced data breaches by ex-employees.
This indicates the need for a streamlined user access management system. Users should be provisioned appropriately for suitable applications and deprovisioned right after they leave your organization.

SaaS management platforms with user provisioning and deprovisioning modules can be integrated with your HRIS systems to collect user data, access, and permission levels in each application.
With a centralized access dashboard, you can easily provision the right apps to users when they join and revoke their access when they quit, preventing security breaches by former employees.
7. Implement strong IAM policies
Implementing strong identity and access management (IAM) policies is the most fundamental aspect of SaaS security best practices. IAM policies govern user access to SaaS applications and resources, ensuring only authorized individuals can view, modify, or interact with sensitive data.
By implementing robust IAM policies, organizations can enforce principles of least privilege, granting users access to the resources necessary for their roles and responsibilities. This reduces the risk of unauthorized access, data breaches, and insider threats.
Additionally, IAM policies enable organizations to streamline user provisioning and deprovisioning processes, ensuring that access rights are promptly revoked when employees leave the company or change roles.
8. Don't overlook SaaS security posture management
One critical SaaS security standard practice is not to overlook SaaS security posture management. It involves continuously assessing and monitoring the security configuration of SaaS applications and services to promptly identify and address vulnerabilities or misconfigurations.
Regularly reviewing and updating security settings, permissions, and configurations ensures that SaaS environments remain resilient against evolving threats.
By staying vigilant and proactive in managing the security posture of SaaS platforms, organizations can mitigate risks, safeguard sensitive data, and maintain compliance with industry regulations.
Ignoring this aspect of SaaS security best practices could leave businesses vulnerable to cyberattacks, data breaches, and other security incidents, emphasizing the importance of prioritizing security posture management in SaaS environments.
9. 5 Challenges you might face while using security SaaS platforms
Securing SaaS platforms involves addressing various challenges:
1. Data privacy and compliance
SaaS platforms often handle sensitive user data, making data privacy a paramount concern. Ensuring compliance with regulations such as GDPR, CCPA, HIPAA, or industry-specific standards adds complexity to security measures.
Implementing robust data encryption, access controls, and auditing mechanisms to maintain compliance while preserving user privacy can be challenging.
2. Multi-tenancy risks
SaaS platforms typically serve multiple tenants (organizations or users) on shared infrastructure. This shared environment introduces the risk of data leakage between tenants, especially in misconfiguration or inadequate isolation cases.
Implementing strong access controls, secure authentication mechanisms, and proper data segregation techniques is essential to mitigating these risks.
3. Third-party integration security
SaaS platforms often integrate with third-party services and APIs to extend functionality. However, each integration introduces potential security vulnerabilities, such as inadequate authentication mechanisms or data validation.
Verifying the security practices of third-party providers, conducting regular security assessments, and implementing secure integration protocols are vital to preventing the exploitation of these vulnerabilities.
4. User access management
Securely managing user access is crucial in SaaS environments, where users access services remotely from various devices and locations.
Challenges include enforcing strong password policies, implementing multi-factor authentication (MFA), and managing user permissions effectively to prevent unauthorized access.
Additionally, ensuring timely revocation of access for terminated users or compromised accounts is essential to maintaining security.
5. Continuous monitoring and incident response
SaaS platforms require continuous monitoring to detect and respond to security threats promptly.
Challenges arise in identifying anomalous behavior, detecting unauthorized access attempts, and correlating security events across distributed environments.
Implementing 2FA, intrusion detection systems (IDS), security information and event management (SIEM) solutions, and establishing well-defined incident response procedures are critical to mitigating risks and minimizing the impact of security incidents.
10. How to choose the right SaaS security solution for your business
Selecting the right SaaS security solution is critical for establishing comprehensive visibility, automating governance, and optimizing costs across your tech stack.
The wrong choice can leave security gaps, create operational inefficiencies, and result in wasted spending on tools that don't integrate well with your existing infrastructure.
When evaluating SaaS security and management platforms, consider these key criteria:
- Integration depth: Look for 500+ direct app and identity provider integrations to ensure comprehensive coverage without manual data entry
- Discovery capabilities: Automated detection of shadow IT, unused licenses, and duplicate applications across your entire tech stack
- Access governance: Real-time user provisioning/deprovisioning, automated access reviews, and role-based permissions management
- Renewal automation: Contract tracking, renewal alerts, and automated approval workflows with benchmarking data for negotiations
- Spend optimization: AI-driven recommendations for license right-sizing, duplicate app consolidation, and cost reduction opportunities
- Workflow automation: No-code workflows for onboarding, offboarding, and compliance reporting
- Multi-stakeholder usability: Intuitive dashboards accessible to IT, security, finance, and procurement teams
- Fast deployment: Platforms offering rapid onboarding (30 minutes or less) for immediate value realization
Aligning these capabilities with your specific risk profile and operational processes ensures you maintain a secure, cost-efficient SaaS environment.
11. Why CloudEagle.ai Is the Ideal Partner for SaaS Security
CloudEagle.ai is uniquely positioned to help organizations secure their rapidly growing SaaS and AI environments. As identity becomes the new security perimeter, traditional tools, SSO, IAM, CLM, and procurement suites cannot manage the explosion of shadow IT, privilege creep, and unmanaged access.
CloudEagle.ai closes this gap with automated, AI-driven SaaS governance built specifically for modern IT and security teams.
1. Unmatched Visibility Into All SaaS & AI Tools (Approved + Unapproved)
Modern organizations run hundreds of SaaS apps, yet 60% operate outside IT’s visibility, creating compliance and breach risk.
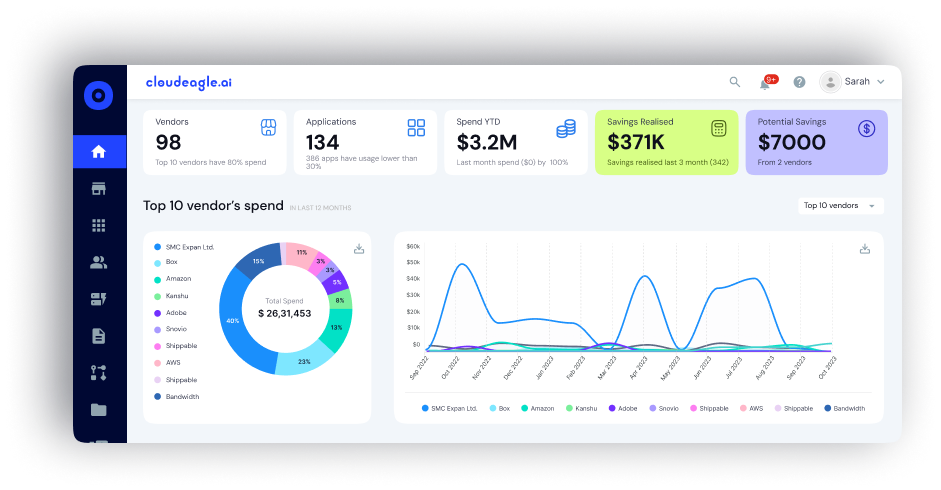
CloudEagle provides 100% visibility into your SaaS and AI footprint by combining:
- SSO login data
- App directory connectors
- Browser login signals
- Finance/card spend data
- HRIS + ITSM context
No other platform correlates login + usage + spend + contract metadata this deeply.
2. Automated Provisioning & Deprovisioning, Even for Apps Outside the IDP
Traditional IAM tools like Okta manage only the apps integrated with SSO. But most SaaS tools and AI apps do not sit behind an IDP.
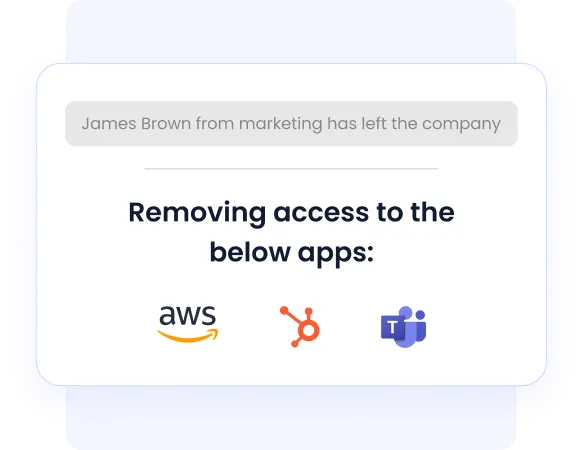
CloudEagle fills this gap with:
- Zero-touch onboarding/offboarding
- Rules-based auto-provisioning
- Automated license harvesting
- Deprovisioning across IDP and non-IDP apps
- Full audit trails for compliance

This eliminates the biggest SaaS security gap: ex-employees retaining access to tools, a problem affecting 48% of organizations.
3. AI-Powered Access Reviews Reduce Risk by 80%
Most companies conduct access reviews quarterly or annually, leaving long periods where excessive permissions go unnoticed.
And 95% do not use AI for reviews.
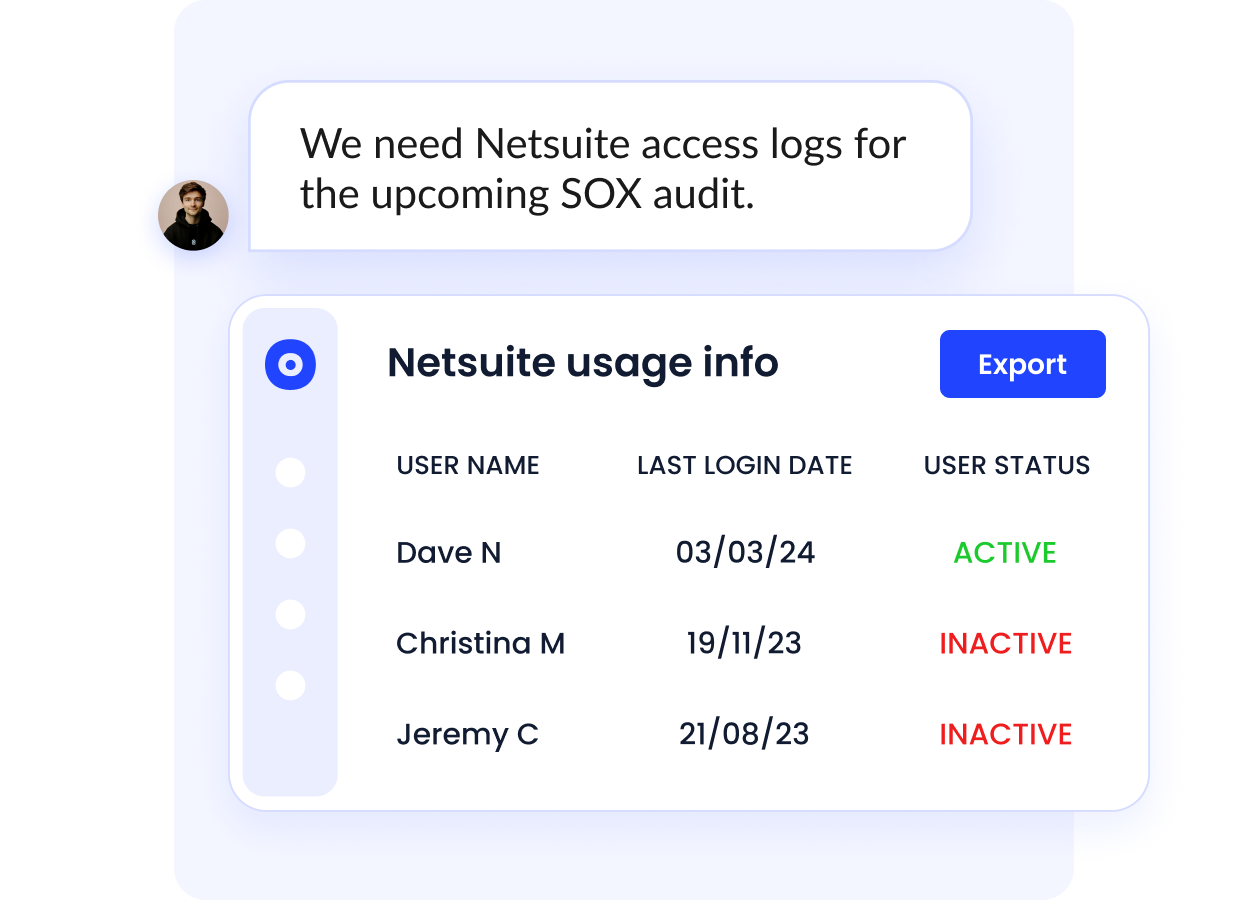
CloudEagle automates:
- Continuous access reviews
- Risk scoring of privileged users
- Excess-access detection
- Department-level privilege creep insights
- Auto-remediation and revocation workflows
This reduces compliance effort and strengthens SOC2 / ISO audit readiness.
4. Eliminates Shadow IT Before It Becomes a Security Incident
CloudEagle automatically detects:
- Free AI tools (ChatGPT, Midjourney, DeepSeek)
- SaaS trials started by employees
- Apps purchased on credit cards
- Unapproved or duplicate tools
- Personal-account logins are not visible to IT
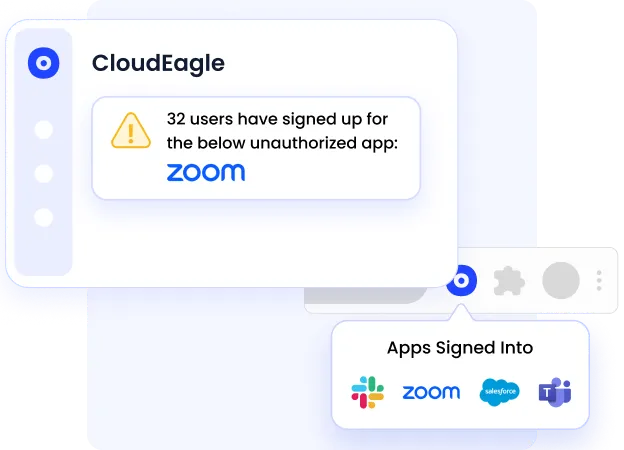
It then triggers:
- Auto-notifications to users
- Slack/email workflows
- Policy enforcement
- Consolidation or removal workflows
This is critical because Shadow IT and AI sprawl are now top enterprise risks, flagged by 70% of CIOs.
5. Stronger Security + Lower Spend (10–30% Savings)
Security and cost optimization are interconnected:
- Removing excessive access prevents breaches
- Reclaiming unused licenses prevents unnecessary spending
- Identifying duplicate apps reduces the attack surface
- Benchmarking ensures secure, compliant vendor choices
CloudEagle is the only platform combining security + procurement + optimization, saving customers 10–30% while reducing risk.
6. Deepest Integration Ecosystem (500+ Connectors)
CloudEagle provides the richest integration library for:
- SaaS apps
- AI tools
- HRIS
- SSO/IDP
- ITSM
- Finance systems
- CLMs
This ensures security teams get real-time, unified identity and usage intelligence across the entire stack.
7. SOC2-Ready Audit Logs & Compliance Dashboards
CloudEagle consolidates and automates:
- User role histories
- Approval trails
- Provisioning/deprovisioning logs
- Access review decisions
- Contract metadata (renewals, SKUs, notice periods)
This accelerates compliance prep by up to 80% and eliminates manual spreadsheets.
12. Conclusion
SaaS security is no longer optional; it’s essential for protecting operations, customer trust, and long-term business growth.
When managing apps, access, compliance, and risk becomes overwhelming, establishing a standard SaaS security best-practices framework supported by automation is the clearest way forward.
Modern SSPM and SaaS management platforms simplify security by eliminating shadow IT, reducing sprawl, enforcing compliance, and continuously monitoring risk. They provide real-time insights and proactive alerts, helping teams act faster and prevent threats before they escalate.
If you're ready to improve SaaS security maturity and gain full control over your SaaS stack, CloudEagle.ai is the right platform to support you.
Book a demo with CloudEagle today and transform the way you secure and manage your SaaS environment.
13. Frequently asked questions
1. What are the most important security features of the SaaS model?
Software as a service (SaaS) security is the umbrella term for the policies and procedures to safeguard the information and programs a SaaS provider hosts. Encryption, authentication, access restrictions, network security, and data backup and recovery are crucial security elements of a SaaS model.
2. What are the key SaaS security concerns with the SaaS model?
One of the primary concerns with SaaS app security is the safety of sensitive data that the service provider stores and processes. Data breaches, leaks, theft, or loss can result in legal, financial, or reputational implications for users.
3. Why should enterprises follow SaaS security best practices?
SaaS security best practices are critical for safeguarding sensitive data, ensuring regulatory compliance, and limiting potential risks. They assist businesses in strengthening their level of security posture by maintaining the integrity and confidentiality of information in SaaS environments. And protect sensitive data against unauthorized access.

%201.svg)







.avif)




.avif)
.avif)




.png)









