HIPAA Compliance Checklist for 2025

As organizations scale their cloud infrastructure, securing workloads, identities, and data becomes a growing concern.
However, with rising cloud complexity and evolving compliance demands, businesses are exploring Lacework alternatives that offer enhanced features, better pricing, or more seamless integrations.
In this blog, we’ll explore the top 7 Lacework alternatives and what makes them stand out, helping you select the best fit for your cloud security needs.
TL;DR: Top 7 Lacework Alternatives for Cloud Security
- Lacework is a solid cloud security platform, but its pricing, learning curve, and limited SaaS visibility lead many to seek alternatives.
- Top Lacework competitors include CloudEagle, Prisma Cloud, Orca Security, Sysdig Secure, Qualys Cloud Platform, Threat Stack, and Wiz Security.
- These alternatives excel in areas like agentless deployment, full-stack and SaaS security, automated compliance, and more flexible pricing models.
- CloudEagle stands out for SaaS visibility and spend optimization, while Wiz and Orca offer easy, agentless cloud protection with advanced risk prioritization.
- Choosing the right tool depends on your priorities: compliance, cost efficiency, DevSecOps integration, or holistic SaaS management.
Lacework Cloud Security: A Brief Overview
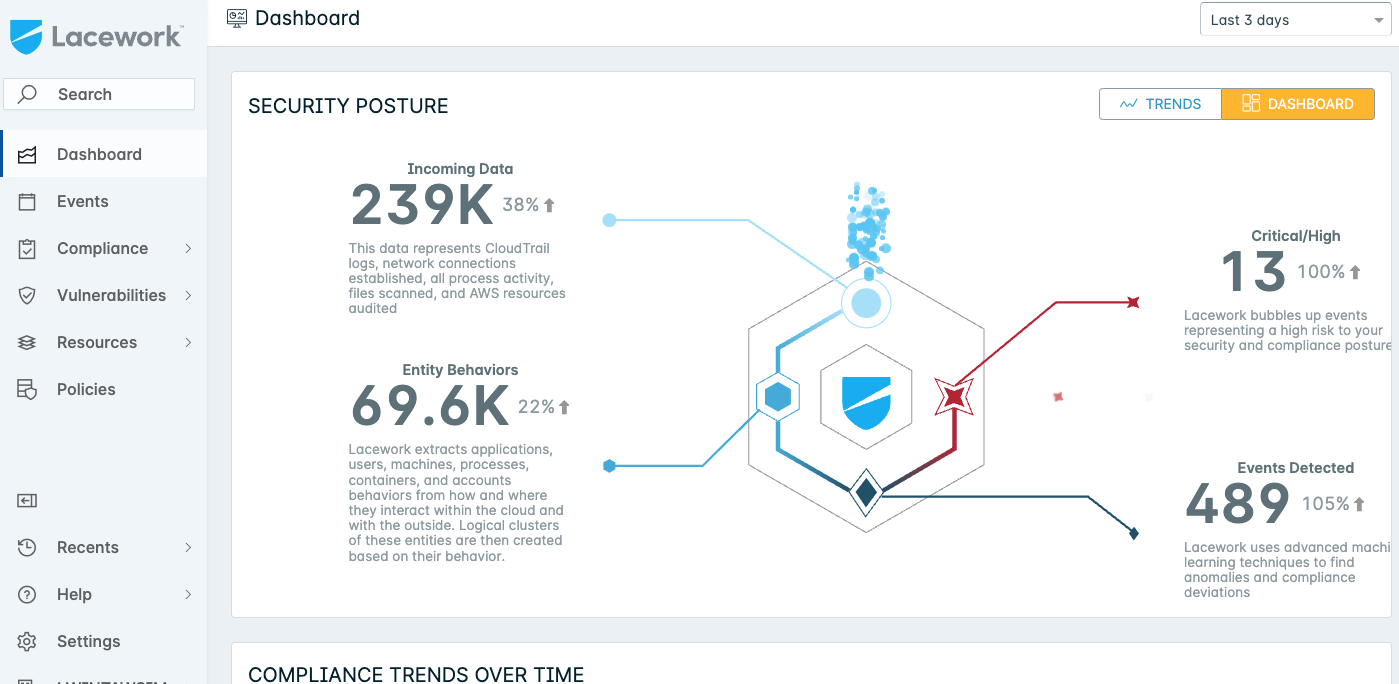
Lacework is a cloud security posture management platform designed to provide comprehensive security and compliance for cloud environments. It offers automated vulnerability detection, threat identification, and cloud compliance across various cloud platforms like AWS, Google Cloud, and Azure, as well as Kubernetes configurations.
Lacework's approach is cloud-native and delivered as-a-Service, focusing on automating security tasks to help organizations innovate with speed and safety.
With deep visibility into AWS, Azure, and GCP, Lacework helps organizations detect anomalies, misconfigurations, and vulnerabilities using a data-driven behavioral approach.
Key Features of the Lacework tool:
- Cloud workload protection (CWPP)
- Container and Kubernetes security
- Compliance assessments (e.g., SOC 2, PCI-DSS)
- Runtime threat detection
- Risk-based prioritization
Despite its powerful capabilities, many organizations find the Lacework pricing model restrictive or seek more flexibility, integrations, or usability, leading them to explore alternatives.
Limitations of Lacework
While Lacework remains a solid solution, it does present certain drawbacks:
- Pricing complexity: Lacework’s pricing is not transparent and can be steep for growing teams or SMBs.
- Steep learning curve: While powerful, the platform can be overwhelming for security teams new to behavioral analytics or agent-based solutions.
- Limited SaaS visibility: Lacework focuses heavily on cloud infrastructure but offers minimal SaaS-specific visibility or license management.
These challenges open the door for Lacework competitors who provide more holistic SaaS security, FinOps visibility, and tailored user experiences.
Top 7 Lacework Alternatives for Cloud Security
Some businesses find Lacework’s pricing high or seek tools that better support SaaS visibility, easier deployment, or deeper DevOps integrations. Top Lacework competitors include CloudEagle, Prisma Cloud, Orca Security, Wiz, Sysdig Secure, Threat Stack, and Qualys Cloud Platform. The Alternates are:
1. CloudEagle.ai

CloudEagle is more than just a cloud security tool; it's a unified platform that offers complete visibility into your SaaS ecosystem, security compliance, and spend optimization. For businesses dealing with dozens or hundreds of SaaS applications, CloudEagle.ai provides centralized control that Lacework cloud security tools often miss.
Features:
Discover Shadow IT & Uncover Hidden Risks
CloudEagle gives you 100% visibility into your SaaS and AI landscape—including unsanctioned tools that bypass your IDP or firewall. By combining login behavior, browser activity, and finance system data, the platform identifies unauthorized usage, flags duplicate tools, and helps you eliminate shadow IT before it becomes a compliance or budget risk.
Identity & Access Management Reinvented
CloudEagle goes beyond traditional IAM tools, offering automated onboarding/offboarding and continuous access governance across all your SaaS and AI apps—even those not behind Okta or SailPoint.
- Zero-touch provisioning: Automatically assigns apps based on role, department, and location.
- Automated offboarding: Instantly revokes access when employees leave, even for tools outside the IDP.
- Audit-ready access reviews: Run on-demand or scheduled, with full logs and anomaly detection.
48% of former employees still retain access to business-critical tools—CloudEagle ends that risk.
Just-in-Time & Privileged Access Management
Stop privilege creep before it becomes a breach. CloudEagle enforces least privilege by granting time-bound access for contractors and temporary users, and revoking it automatically.
- Time-based, self-expiring access for high-risk roles.
- Alerts for excessive admin access or unusual behavior.
- SOC 2 and HIPAA-ready audit trails for every provisioning action.
AI-Powered Access Reviews & Security Compliance
Modern security requires more than quarterly audits. CloudEagle runs continuous, AI-driven access reviews that detect stale permissions, flag overprivileged users, and automate deprovisioning.
- Risk scoring of user access and app usage.
- Workflow automation to remediate issues instantly.
- Coverage for AI tools like ChatGPT, DeepSeek, and beyond.

Reclaim unused licenses and eliminate wasteful spend automatically
CloudEagle tracks feature-level usage, not just logins, allowing IT and finance teams to right-size license allocations and remove idle accounts.
- Weekly license harvesting workflows reclaim and recycle unused seats.
- Identify overlapping tools and downgrade plans before your next renewal.
- Automate license downgrades and reallocations with zero manual effort.
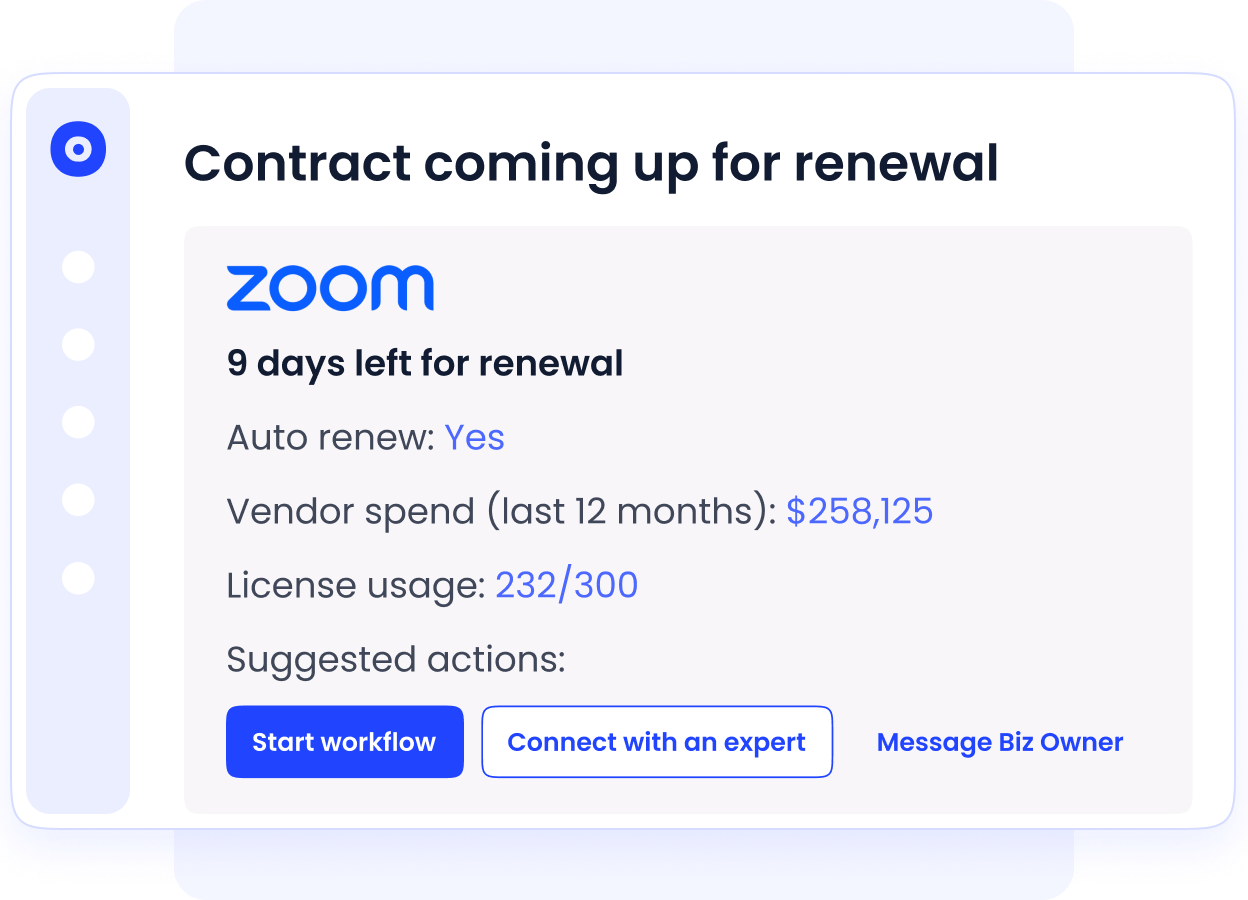
Contract Intelligence & Renewal Management
Never miss a renewal or overpay again. CloudEagle’s AI-powered contract repository centralizes all vendor agreements, extracts critical metadata, and builds a proactive renewal calendar.
- Auto-detects renewal dates, license counts, SKUs, and opt-out windows.
- Sends renewal alerts and automates Slack/Jira approval workflows.
- Benchmarks pricing to help you renegotiate smarter.

The Procurement Intelligence and Price Benchmarking engine equips buyers with vendor-specific insights, pre-negotiated discounts, and cost benchmarks by license tier. This empowers procurement teams to confidently negotiate renewals or new purchases based on usage trends and peer comparisons.

CloudEagle also supports strong Security and IT Compliance by enabling identity hygiene, continuous access reviews, and privileged access reporting. It aligns with SOC 2, HIPAA, ISO 27001 frameworks and supports risk scoring and alerts for unauthorized tools or excessive permissions, offering complete SaaS governance.
Pros:
- CloudEagle delivers true end-to-end visibility, covering not only approved tools behind SSO but also Shadow IT, browser logins, and free-tier AI tools, which most platforms miss. This is especially valuable in today’s decentralized and fast-moving SaaS environments.
- Its automation-first design drastically reduces the workload for IT and procurement teams. From onboarding workflows to license harvesting and access reviews, CloudEagle eliminates dozens of manual steps and replaces spreadsheets with real-time intelligence and triggers.
- The depth of optimization insights stands out — feature-level usage (not just logins) enables accurate license downgrading, reclamation, and app rationalization. This leads to immediate and recurring cost savings, which are often realized within weeks of implementation.
- CloudEagle’s integration ecosystem and flexibility is unmatched, supporting out-of-the-box connections with apps like Slack, Jira, Coupa, Ironclad, and both IDP and non-IDP environments. It’s designed to adapt to real-world toolsets, not just theoretical best practices.
Cons
- Organizations with extensive on-premise legacy applications may find the platform less applicable, as it focuses primarily on SaaS and browser-based tools rather than server-based or non-cloud systems.
- While pricing benchmarks and negotiation insights are powerful, actual vendor negotiation execution (e.g., managed procurement services) may still require customer action or additional advisory help unless bundled as a service.
Pricing
- SaaS Management module starts at $2,500/month – includes license tracking, usage monitoring, renewals, and budgeting.
- SaaS Governance module starts at $2,000/month – covers onboarding/offboarding, access controls, and compliance workflows.
- SaaS Procurement module starts at $2,500/month – offers vendor negotiation support, price benchmarking, and procurement automation.
Bundle options:
- Management + Governance: $4,500/month
- Management + Procurement: $5,000/month
- Full suite (Governance + Management + Procurement): $7,000/month
Free trial available; onboarding support included in packages. Designed for mid-to-large enterprises with scalable, modular pricing.
2. Prisma Cloud by Palo Alto Networks
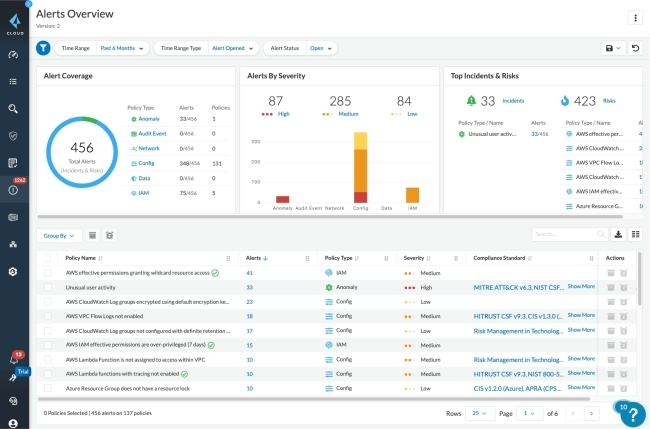
Prisma Cloud is Palo Alto’s flagship cloud-native security platform offering full-stack protection from code to cloud. It is widely adopted by large enterprises for its deep coverage and unified approach.
Features:
Prisma Cloud supports CSPM, CWPP, CIEM, and container security, making it ideal for hybrid and multi-cloud environments. It secures infrastructure as code (IaC), provides real-time monitoring, and enforces policies across CI/CD pipelines. The platform also includes rich compliance capabilities for standards like PCI-DSS, NIST, and GDPR.
Pros:
- Offers end-to-end security coverage, spanning from code development to production deployment, ensuring comprehensive protection across the entire software lifecycle.
- Provides deep and seamless integrations with popular CI/CD tools, cloud service providers, and DevOps pipelines, enabling continuous monitoring and automated remediation.
- Features robust compliance management capabilities with built-in policy automation, audit readiness tools, and support for frameworks like SOC 2, HIPAA, and ISO 27001.
Cons:
- The platform can be complex to set up and configure, especially for smaller teams or organizations without a dedicated DevSecOps function.
- Comes with premium pricing that may be prohibitive for startups or budget-conscious businesses, and users often face a steep learning curve due to the platform’s breadth of features.
Pricing:
Pricing typically starts at $1,000/month or more, depending on the number of cloud accounts, integrations, and required compliance modules. Custom enterprise pricing is available for larger deployments.
3. Orca Security
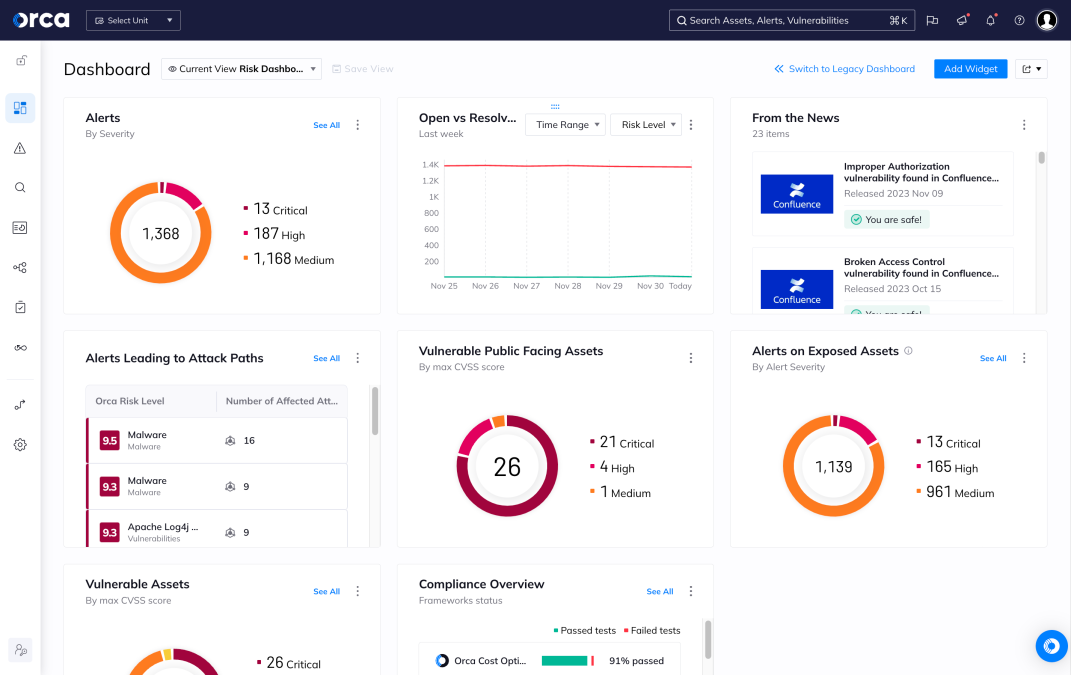
Orca Security is a leading cloud security platform known for its agentless architecture and lightning-fast deployment. It delivers prioritized, contextual alerts with zero disruption to workloads.
Features:
It scans the entire cloud environment without deploying agents, identifying misconfigurations, malware, and exposed secrets. Orca provides asset inventory, risk prioritization, and lateral movement detection using context-aware analysis. Its attack path analysis helps organizations focus on the most critical risks.
Pros:
- Utilizes agentless scanning technology, allowing for fast and efficient security assessments without placing a heavy load on system performance or requiring invasive installations.
- Delivers rapid time-to-value through enriched contextual insights across cloud assets, enabling security teams to identify and address risks quickly.
- Features strong alert prioritization capabilities that significantly reduce noise and false positives, helping teams focus only on high-impact threats.
Cons:
- Does not offer comprehensive runtime protection capabilities, which may leave gaps in monitoring live, in-production environments.
- May require integration with third-party tools or platforms to achieve complete compliance coverage and meet advanced governance requirements.
Pricing:
Pricing generally starts at $500–$1,500/month, depending on the size of the environment and number of assets scanned. Enterprise pricing is available for larger, more complex deployments with premium support and integrations.
4. Sysdig Secure
Sysdig Secure is built for containerized environments and DevOps teams looking to secure their Kubernetes clusters and cloud-native workloads. It emphasizes runtime security and observability.
Features:
Sysdig delivers real-time threat detection using syscall-level data and behavioral profiling of container activity. It includes Kubernetes posture management and compliance enforcement tools. The platform integrates with CI/CD pipelines to shift security left in the development lifecycle.
Pros:
- Purpose-built for modern containerized and microservices-based architectures, making it highly suitable for cloud-native environments running on platforms like Kubernetes and Docker.
- Provides advanced runtime visibility and threat detection, allowing security teams to monitor container activity in real time and respond quickly to anomalous behavior.
- DevSecOps-friendly with robust automation support, enabling security to be seamlessly integrated into CI/CD pipelines for continuous security enforcement without slowing down development cycles.
Cons:
- Primarily focused on container security, which limits its usefulness in traditional or non-Kubernetes environments where broader infrastructure monitoring is needed.
- The platform's depth and complexity can require significant training and onboarding time, especially in organizations with complex multi-cloud or hybrid setups.
Pricing:
Pricing typically starts at $2,000–$3,000/month based on the number of nodes or containers monitored. Enterprise pricing and custom packages are available for large-scale or mission-critical deployments.
5. Qualys Cloud Platform
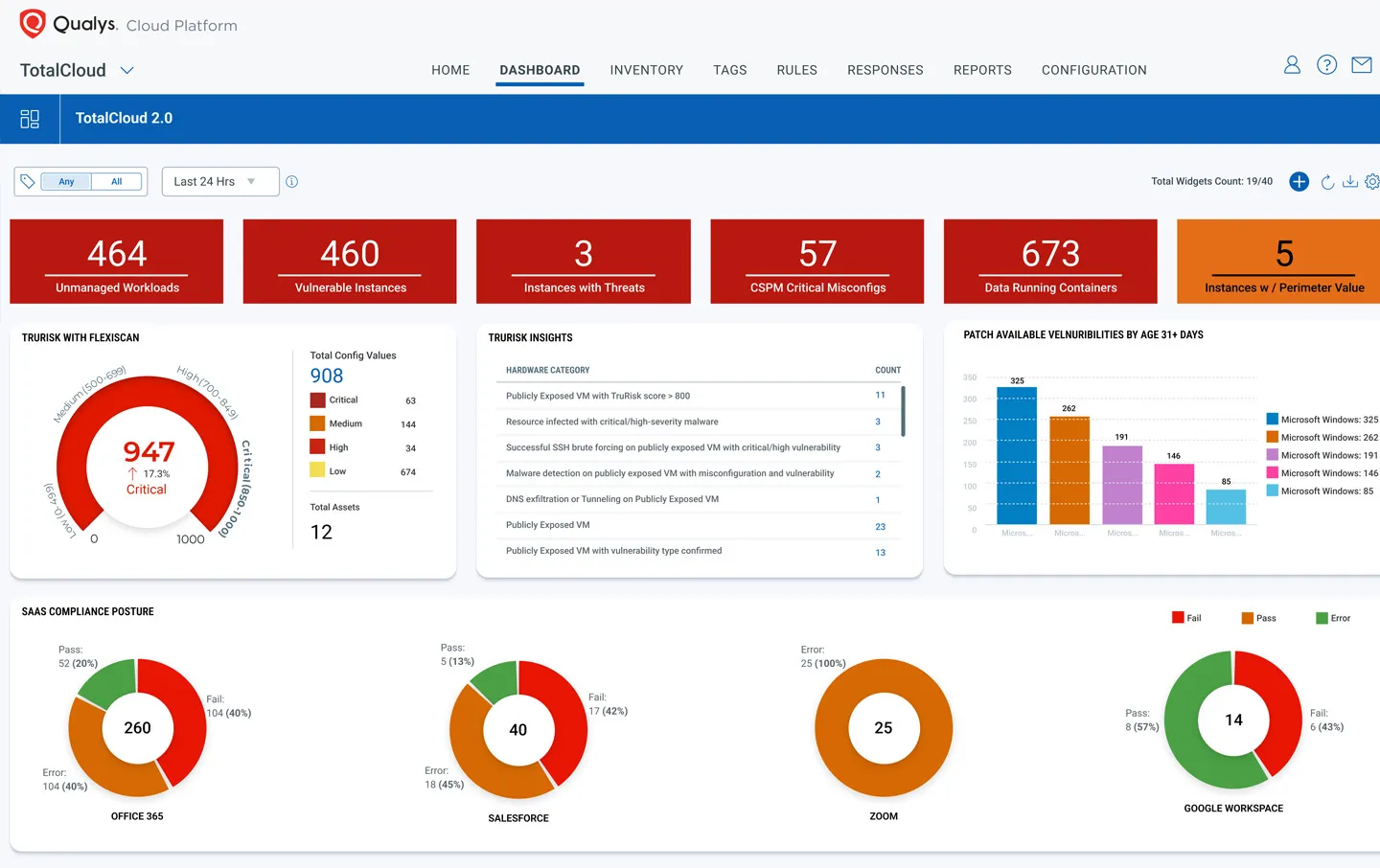
Qualys is a pioneer in vulnerability management, and its Cloud Platform extends these capabilities to hybrid and cloud-native environments. It combines security, compliance, and asset management under one roof.
Features:
Qualys scans your infrastructure for vulnerabilities, configuration issues, and unauthorized changes. It provides continuous visibility across devices, VMs, containers, and apps. The platform is also equipped with real-time threat indicators and patch management capabilities.
Pros:
- Backed by an established and trusted brand in the cybersecurity space, offering mature vulnerability management and compliance capabilities that align well with industry standards.
- Highly scalable for large enterprises with complex, global infrastructures, making it a strong choice for multinational organizations needing centralized security oversight.
- Offers continuous and automated scanning that helps maintain strong security hygiene by identifying vulnerabilities and misconfigurations in real time.
Cons:
- The user interface can feel outdated and less intuitive compared to newer, modern platforms, which may hinder usability for first-time users or non-technical stakeholders
- While reporting capabilities are powerful, they often require significant customization to produce executive-level dashboards and compliance-ready summaries.
Pricing:
Pricing typically begins at $2,000/month or more, depending on the number of assets, scanning frequency, and modules selected. Volume discounts and enterprise packages are available for large organizations.
6. Threat Stack (Acquired by F5)
Threat Stack offers cloud-native intrusion detection and workload security. It’s particularly popular in regulated industries like healthcare, finance, and SaaS, where runtime monitoring and compliance are essential.
Features:
It monitors users, processes, and network behavior in real-time to detect threats. The platform offers built-in compliance reporting for HIPAA, SOC 2, and PCI-DSS. Threat Stack provides deep observability with lightweight agents across Linux and Windows environments.
Pros:
- An excellent choice for compliance-driven organizations, offering built-in support for major regulatory frameworks such as PCI DSS, HIPAA, and SOC 2, with detailed audit and reporting tools.
- Utilizes lightweight agents to deliver effective runtime protection without significantly impacting system performance, ensuring secure operations in dynamic cloud environments.
- Provides robust behavioral monitoring to detect anomalies and suspicious activities based on real-time user and system behavior, enhancing threat detection accuracy.
Cons:
- Primarily focuses on detection capabilities rather than proactive prevention, which may necessitate integration with other tools to close the security loop.
- Limited in terms of cloud coverage and multi-environment support when compared to broader Cloud-Native Application Protection Platforms (CNAPPs), which offer more unified visibility across hybrid and multi-cloud infrastructures.
Pricing:
Pricing starts around $1,500–$3,000/month, varying by the number of workloads, cloud accounts, and compliance modules. Enterprise pricing is available for larger deployments with custom compliance needs.
7. Wiz Security
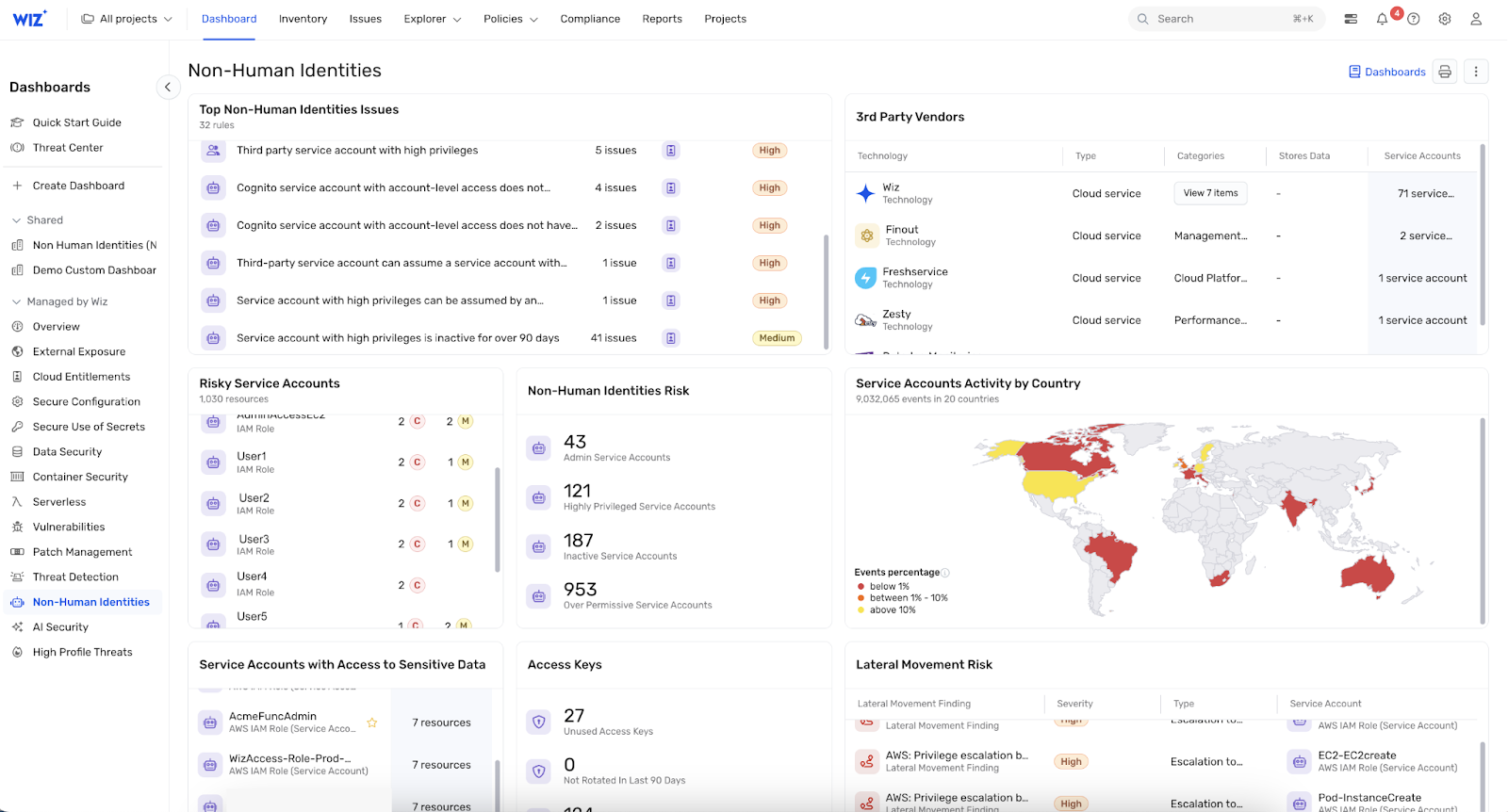
Wiz has emerged as a fast-growing Lacework competitor, offering agentless cloud security that provides full-stack visibility into your cloud environment. It is widely used for its simplicity, speed, and advanced risk correlation.
Features:
Wiz scans across VMs, containers, databases, identities, and workloads without requiring agents. It uses a graph-based analysis engine to detect toxic combinations and exposure paths that could lead to breaches. The platform integrates seamlessly into cloud-native DevOps workflows.
Pros:
- Extremely easy to deploy thanks to its agentless architecture, enabling rapid onboarding and minimal disruption to existing cloud operations.
- Equipped with a powerful risk prioritization engine that leverages context from workloads, configurations, and identities to surface the most critical threats first.
- Offers broad support for all major cloud providers — including AWS, Azure, and Google Cloud — delivering unified visibility and control across multi-cloud environments from a single dashboard.
Cons:
- Positioned as a premium enterprise solution with pricing that may not be suitable for smaller businesses or budget-constrained teams.
- While effective in real-time monitoring, the platform has limitations in providing deep historical trend analysis or advanced reporting features out of the box.
Pricing:
Pricing generally starts at $3,000/month or higher, depending on cloud footprint, number of resources, and advanced feature requirements. Enterprise licensing and volume-based discounts are typically available.
Conclusion
Lacework continues to be a solid player in the cloud security space, but it’s not a one-size-fits-all solution. Whether you need stronger SaaS oversight, better cost efficiency, or a more developer-friendly toolset, these
Lacework competitors offer excellent alternatives. From deep container insights with Sysdig to holistic SaaS security with CloudEagle, there’s a solution for every cloud security challenge.
If your stack is becoming SaaS-heavy and you’re aiming for centralized security and cost governance, CloudEagle provides the modern alternative Lacework doesn’t fully cover.
FAQs
1. Is Wiz better than Lacework?
Wiz offers a faster agentless approach with deep risk context and prioritization. It may be a better fit for teams seeking agility and full cloud stack visibility.
2. What are the top Lacework alternatives for cloud security?
The leading Lacework alternatives include CloudEagle, Prisma Cloud, Orca Security, Sysdig Secure, Qualys Cloud Platform, Threat Stack, and Wiz Security. These platforms offer various advantages such as agentless security, stronger SaaS visibility, end-to-end compliance, and cost governance capabilities.
3. What key features set Lacework competitors apart?
Lacework competitors frequently offer transparent pricing, faster deployment (thanks to agentless or API-driven architectures), robust SaaS discovery, automated compliance workflows, and unified dashboards for managing security, spend, and access.
4. Is Lacework pricing suitable for small businesses?
Lacework pricing is generally aimed at mid-market and enterprise customers. Its lack of transparent, simple pricing and potentially higher minimums can make it less accessible for small businesses, who might benefit from alternatives like Orca Security or CloudEagle that offer scalable or tailored pricing models.
5. What are the main limitations of the Lacework tool?
The main drawbacks of Lacework include complex pricing, a steep learning curve, and limited SaaS application visibility. Organizations seeking broader SaaS coverage or easier usability often explore other cloud security tools that complement or replace Lacework for their specific security needs.

%201.svg)







.avif)




.avif)
.avif)




.png)









