HIPAA Compliance Checklist for 2025

SaaS applications thrive on data and generate vast amounts in return. With data now being the “new oil,” IT and security teams must protect these apps and their data from vulnerabilities and breaches.
Unfortunately, IT teams often face the reality of frequent data breaches that can originate from common sources.

This puts more emphasis on user provisioning and deprovisioning. Who has access to the applications? On how many devices have you used the credentials? These reports should not
Manual provisioning through spreadsheets or legacy tools is slow and risky. Automating the process with modern SaaS applications ensures speed, accuracy, and security.
A SaaS management platform can reduce the manual workload and simplify user provisioning and deprovisioning for the IT team. You’ll learn more about it in this article.
TL;DR
- Automated user provisioning streamlines IAM by instantly granting user access to necessary applications based on roles, eliminating the need for manual spreadsheets and reducing security gaps.
- Automated deprovisioning revokes user access immediately upon offboarding or role changes, minimizing the risk of unauthorized access and data breaches.
- User provisioning and deprovisioning tools like CloudEagle integrate with SSO and HRIS systems to automate onboarding/offboarding workflows and maintain centralized access control.
- Following best practices like the Principle of Least Privilege (PoLP), Role-Based Access Control (RBAC), and regular access audits helps ensure secure, compliant identity management.
- SaaS management platforms with auto-provisioning workflows improve operational efficiency, reduce IT workload, and prevent shadow IT by managing sanctioned app access effectively.
What is user provisioning?
User provisioning is the process of creating, maintaining, updating, and deleting user accounts and access across multiple applications and systems, whether on-premise, cloud, or hybrid.
Challenges with traditional user provisioning
Traditionally, IT and HR teams used spreadsheets to track which apps belong to which roles. Each new hire meant manually assigning access and sharing credentials over email or chat, an insecure and time-consuming process.
Modern automated user provisioning eliminates this manual work. Platforms like CloudEagle.ai streamline provisioning by connecting to your HRIS and IdP, automatically assigning and revoking app access based on user roles and policies.
Automated user provisioning
Modern automated user provisioning eliminates these challenges. Platforms like CloudEagle.ai connect to your HRIS and IdP to automatically assign and revoke access based on user roles and policies.
When employees join, move between teams, or leave, automated workflows instantly update their access, ensuring accuracy, security, and compliance while reducing IT workload.
What is user deprovisioning?
Automated user deprovisioning helps keep your company secure by ensuring that whenever an employee leaves, their access is automatically removed for all connected applications. In addition, all existing user sessions are removed to reduce security risk.
Challenges with traditional user deprovisioning
When user accounts are tracked using spreadsheets, the IT team will have a hard time revoking access to each application.
- The IT team will have to visit each application to revoke access, which will be time-consuming.
- Ensuring that an employee's access to all applications has been removed will be hard. Sometimes, IT teams might miss revoking access to some applications.
- And once the employee has left, this unrevoked access might get compromised and pave the way to security breaches.
Consider a scenario where you terminate an employee but forget to revoke their access to a critical application. If the former employee is dissatisfied, they might extract sensitive information about your business operations and share it with your competitors.
Automated deprovisioning
Automating deprovisioning enables you to swiftly revoke access and delete a user's account from your system with minimal time and effort.
Automating employee offboarding using a SaaS management platform can ensure that an employee's access to applications is entirely revoked, preventing them from accessing any information.
Alice Park from Remediant had troubles with manual provisioning and deprovisioning; she spent most of her time visiting each app to revoke user access, which was counterproductive.
What is automated provisioning?
Automated provisioning is the IAM practice of creating, updating, and removing user accounts and entitlements across SaaS and internal systems based on policies and lifecycle events—not tickets.
Unlike manual provisioning, which depends on spreadsheets and human steps, it’s policy- and event-driven: the HRIS serves as the source of truth, IdP group memberships define roles, and app connectors (via SCIM or APIs) push least-privilege access to each app.
During onboarding, a new-hire event in the HRIS triggers identity creation in the IdP, group assignment, and auto provisioning of the exact apps and permissions needed for the role, location, and team, aligned to the Principle of Least Privilege.
As users change roles, policies adjust access automatically to prevent privilege creep.
When employees leave, automated workflows revoke access, disable sessions, reclaim licenses, and log every action for audits, closing gaps faster than manual processes.
How automated provisioning works
Automated provisioning starts with a system-of-record event: a new hire or change in the HRIS triggers automatic identity creation or updates in the IdP. Attributes like role, department, location, and manager are mapped, then policies evaluate RBAC/GBAC rules to determine least-privilege access.
No-code workflow orchestration routes required approvals (manager, app owner, security) before auto provisioning continues.
- SSO/IdP group assignments are applied, aligning the user to standardized access profiles.
- App-level provisioning executes via native connectors or SCIM, creating accounts, assigning roles, and setting time-bound entitlements for sensitive apps.
- Conditional logic (e.g., location or employment type) refines access and duration to enforce the Principle of Least Privilege.
- Every step is logged for auditability, with immutable records supporting compliance and periodic access reviews.
Automated user provisioning is mirrored by deprovisioning: termination or HRIS status changes immediately revoke SSO groups, disable sessions, and deprovision app accounts through connectors.
Licenses, seats, and API tokens are reclaimed automatically to cut spend and eliminate orphaned access.
End-to-end logging, alerts, and scheduled certifications validate that automated provisioning and deprovisioning remain correct over time, while approval workflows and break-glass requests provide governed exceptions without compromising security.
Best Practices for Automated User Provisioning and Deprovisioning
Integrating with HR and other systems
You first need the user's data to provision users to applications automatically. Without a clear view of users accessing your applications, you cannot manage onboarding and offboarding effectively.
Two integrations will make this possible,
- SSO integration
- HRIS integrations
SaaS management tools can integrate with SSO systems to discover all your SaaS applications within your infrastructure. HRIS integrations will reveal the user data and how they use the applications.

By using a SaaS management system, you can collect user information and organize it in one location for easier onboarding and offboarding. This ensures consistency and minimizes the likelihood of errors.
Use the Principle of least privilege(PoLP)
Instead of granting access to all the applications, the principle of least privilege necessitates that a user only be granted access to the applications required to do the work, not more than that.
Previously, organizations provided one common credential to a user; they could access all the applications within their SaaS stack using the credential. This is an unsecured practice and one of the most common security breach vectors.
If you are doing this in your organization, stop it now. Leverage PoLP and grant access to only specific applications based on the roles using an identity and access management system.
IAM, or identity and access management, is a set of processes and standards used to track and manage the digital identity of users. User provisioning falls under the umbrella of IAM, ensuring that only the right people get access to the right solutions.
Implement GBAC and RBAC
Group-based access contracts and role-based access control are two common levels of access controls that most businesses use. User provisioning must be done based on these access controls.
Grant application access to users based on their departments and roles; this will prevent users from accessing applications their roles don’t require. It’ll also provide better control for IT teams to prevent unauthorized application access.
You can use the HRIS and SSO integrations to group users and applications based on their roles and departments. For example, if you have ten licenses for Mailchimp, only the marketing team should have access to the application.
Constantly review user access and activity
Regularly reviewing your user access permissions will ensure that the right users are accessing your applications and also help prevent potential security breaches.
Monitoring user activity will reveal how users access your applications; you can identify a pattern in each interaction.
Once the patterns become erratic, it indicates that the user account may have some unwanted activity, and appropriate measures can be taken to prevent unauthorized individuals from gaining access to the application using compromised credentials.
Stay on top of shadow IT
Using identity and access management tools, you can manage user access to applications sanctioned and purchased by the admin and IT teams. What about the apps that were purchased without the approval of IT?
Shadow IT is the act of purchasing applications without IT’s knowledge, and it occurs in almost all organizations. Applications from unauthorized third-party vendors can lead to compliance issues and security breaches.
SSO integrations will reveal all the applications in your tech stack, and your IT teams can quickly identify the apps resulting from shadow IT and eliminate them to keep the stack optimized.
Communicate with the users, understand their requirements, and purchase the applications they need to avoid shadow IT. This will keep your user accounts and applications secure.
Automated provisioning and deprovisioning tools
Automated provisioning and deprovisioning tools streamline the entire user lifecycle, from onboarding to offboarding, by integrating with your HRIS, IdP, and SaaS apps.
- IdP/SSO Platforms:
Enable group-based access (GBAC/RBAC) and auto-provision/deprovision users through SCIM or direct app integrations. - HRIS Systems:
Act as the source of truth to trigger joiner–mover–leaver events for automated provisioning and deprovisioning. - SaaS Management Platforms (SMPs):
Extend automation with no-code workflows, license optimization, app connectors, and centralized visibility across all SaaS tools. - IGA/IAM Suites:
Add governance controls, policy-based entitlements, time-bound access, and certification to enforce least privilege and maintain compliance.
Key capabilities to look for:
- Integration coverage: Broad, reliable app connectors (SSO, HRIS, SCIM, API).
- No-code workflows: Event-driven onboarding and offboarding with approval flows.
- Audit trails: Immutable activity logs for compliance and forensics.
- Governance controls: Automated access reviews and time-limited permissions.
- License reclamation: Reclaim and resize licenses during offboarding.
Prioritize platforms that unify provisioning, deprovisioning, access governance, and SaaS license management. A single system of record cuts handoffs, centralizes audits, automates renewals, and strengthens compliance, all while reducing SaaS spend.
Automate onboarding and offboarding with CloudEagle.ai
CloudEagle.ai is an all-in-one SaaS management and identity automation platform designed to simplify onboarding, offboarding, and access governance, without the need for manual effort or spreadsheets.
Zero-Touch Onboarding
CloudEagle’s Zero-Touch Onboarding automatically detects new employees through your existing HRIS or IdP (e.g., Okta, Microsoft AD). It provisions users into the right applications instantly, using role-based access rules defined by department, job title, and location.

With no-code workflows, IT teams can configure access in minutes, ensuring every new hire gets secure, immediate access to the tools they need from day one.
Automated Deprovisioning
When an employee leaves, CloudEagle automatically identifies all applications the user has access to and revokes permissions in real time.
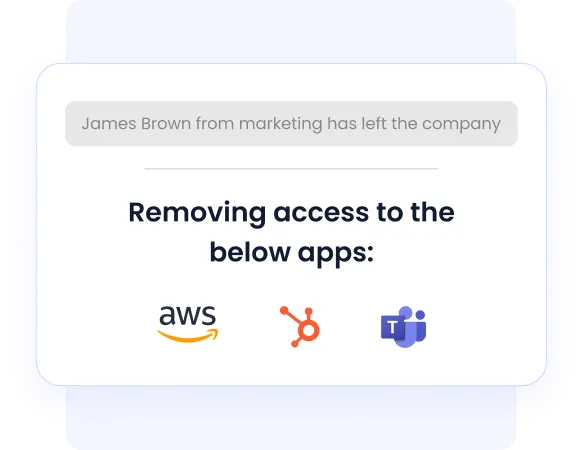
It syncs with your identity systems to deactivate user accounts across all apps simultaneously, closing access gaps instantly and eliminating the risk of lingering credentials.
Enhanced Shadow IT Detection
CloudEagle now delivers advanced visibility into unauthorized or unmanaged apps. It pulls usage data from over 500+ pre-built connectors, even detecting apps outside your IdP or in free-tier versions.
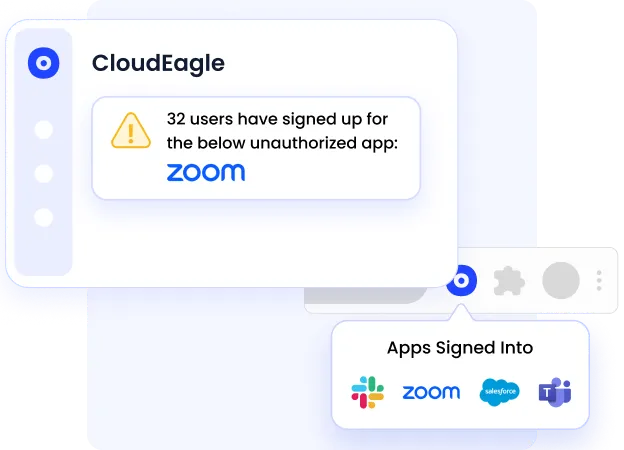
This allows IT and procurement teams to identify, assess, and secure all SaaS usage across the organization, reducing hidden spend and security blind spots.
AI-Powered Access Governance
With AI-driven insights, CloudEagle continuously monitors access across your SaaS ecosystem.
It detects overprivileged users, expired permissions, or policy violations, and triggers real-time alerts for proactive remediation.
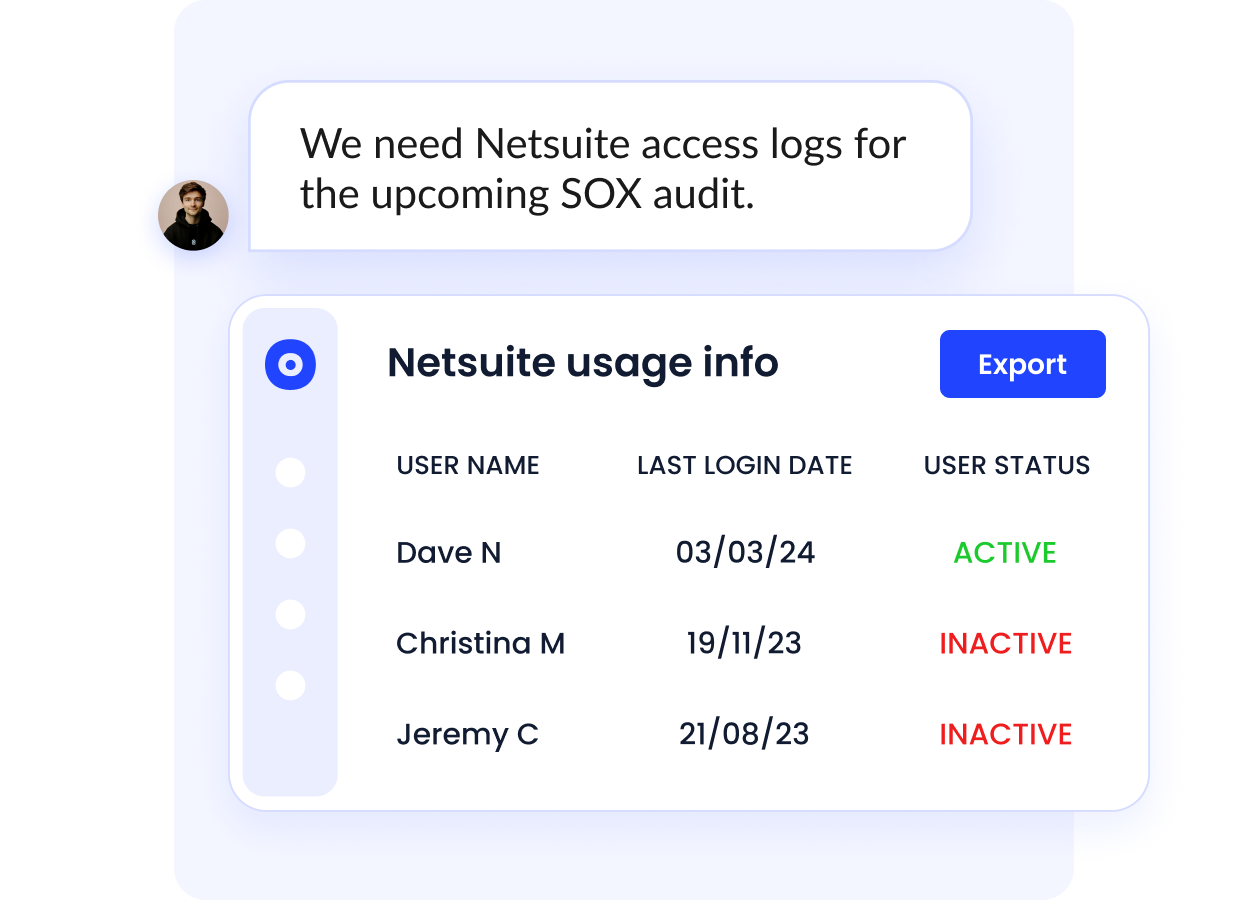
This continuous governance layer ensures compliance with frameworks like SOC 2, ISO 27001, and GDPR, without manual audits.
Time-Based Access Control
For contractors, vendors, or temporary staff, CloudEagle enables time-bound access that automatically expires after a set period.
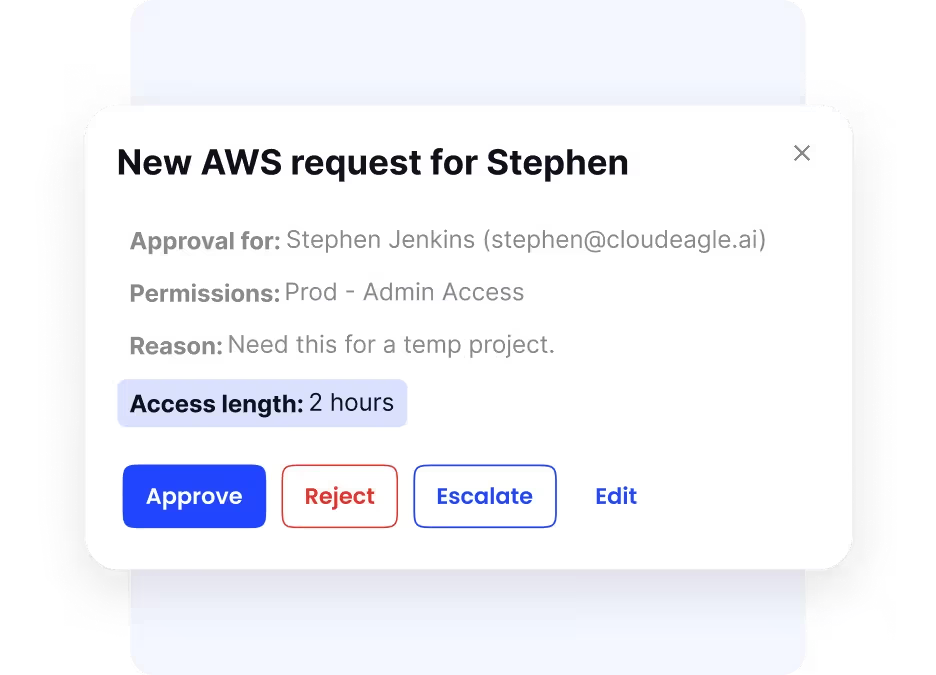
This prevents unnecessary access retention and ensures external users can only access resources for as long as they need them, minimizing risk and improving compliance.
Discover how Joshua Peskay, a 3CPO (CIO, CISO, and CPO) at RoundTable Technology, navigates Shadow IT complexities in remote work environments. Learn his strategies to optimize Shadow IT and uncover an ROI score for SaaS tools that boosts efficiency and maximizes ROI through effective management.
Wrapping up
User provisioning and deprovisioning are the processes of granting and revoking user access to applications. Doing it manually will take time, and tracking user accounts and applications on spreadsheets will lead to unauthorized access and data breaches.
This article emphasized the importance of automated provisioning and deprovisioning and how it can help IT and HR teams streamline employee onboarding and offboarding. It saves time and will enable your team to focus on more strategic tasks.
User provisioning software like CloudEagle.ai will make the identity and access management process easier for the IT teams with its auto-provisioning and deprovisioning modules.
Book a free demo and keep your application stack secure and free of unauthorized access, compromised passwords, and security breaches using CloudEagle.ai.
FAQs
1. What is automated user provisioning in Identity & Access Management?
Automated user provisioning is the IAM process of instantly granting or removing access to apps and systems based on user roles or events, reducing manual tasks and improving onboarding speed and security.
2. How does automated user provisioning benefit large organizations?
Automated user provisioning speeds up user onboarding, minimizes human error, and ensures consistent access rights. It's essential for scaling IAM while maintaining compliance and reducing IT workload.
3. Why is automated provisioning and deprovisioning important for IAM?
Automated provisioning ensures timely, secure access, while automated deprovisioning prevents orphaned accounts and security gaps. Together, they strengthen identity governance and compliance.
4. What’s the difference between provisioning and deprovisioning?
Provisioning gives users access to required systems, while deprovisioning revokes access when users leave or change roles. Automated provisioning and deprovisioning enhance IAM efficiency and reduce risk.
5. How do IAM tools automate access provisioning and deprovisioning?
IAM tools use workflows, rules, and integrations with HR or IT systems to trigger access changes automatically. This auto-provisioning ensures access is always aligned with roles and lifecycle events.

%201.svg)







.avif)




.avif)
.avif)




.png)









