HIPAA Compliance Checklist for 2025

Imagine not remembering another password: no reset emails, no sticky notes with credentials, no worry about phishing. For many users, that feels like a security dream.
In 2023, Google reported that security keys and biometric authentication methods reduced account hijack risk by over 90% compared to passwords alone. These advances are part of why WebAuthn (Web Authentication) is being adopted rapidly across browsers and platforms.
This article explains what WebAuthn is, why it matters, and how enterprises can focus on WebAuthn implementation for modern secure, modern web authentication methods.
TL;DR
- WebAuthn replaces passwords with biometrics, security keys, or trusted devices using public-key cryptography.
- Credentials are bound to domains, making it nearly impossible for attackers to reuse stolen information.
- Stronger security, reduced credential theft, improved user experience, and lower IT support costs.
- Start with high-risk users, educate employees, support multiple authenticators, and monitor authentication logs.
- User resistance, hardware dependencies, and integration with legacy systems remain key hurdles.
What is WebAuthn?
WebAuthn is an open global standard for secure, passwordless web authentication using public-key cryptography. It replaces traditional passwords with hardware security keys, biometrics, or mobile device authenticators.
The standard was developed by the W3C and FIDO Alliance for strong, adaptive authentication. WebAuthn works with modern browsers and operating systems to support secure logins.
Websites use WebAuthn authenticator to authenticate users without shared secrets, reducing risks of phishing or credential theft. This approach improves security and helps prevent data breaches caused by stolen passwords. Core Features of WebAuthn authenticator:
- Public-Key Cryptography: Only the public key is stored on the server; the private key remains on the user’s device, improving security.
- Phishing Resistance: Because credentials are bound to the origin (domain), attackers can’t easily trick users into giving away valid credentials on fake sites.
- Device-Based Authenticators: Supports built-in authenticators (e.g. fingerprint sensors, face recognition) and external hardware security keys.
- Cross-Platform Compatibility: Works across major browsers (Chrome, Edge, Safari, Firefox) and operating systems, enabling wide adoption.
A real-world example is GitHub, which rolled out WebAuthn API security key support for developer accounts. This change significantly reduced account takeovers, protecting critical code repositories from credential-stuffing attacks.
How Does WebAuthn Work?
WebAuthn uses public-key cryptography to verify users without password authentication or shared secrets. A private key stays safely on the user’s device or authenticator, while a public key registers with the website.
During login, the website sends a unique challenge to the user’s authenticator. The device signs this challenge using its private key, then returns the signed answer to the server.
Registration Phase
When a user signs up for WebAuthn test, the website requests their authenticator (like a phone, YubiKey, or biometric device) to create a unique public-private key pair. The public key is stored on the server, while the private key never leaves the device.
Authentication Phase
During login, the server challenges the user’s authenticator to sign a unique piece of data with the private key. The authenticator confirms the user’s identity (via fingerprint, PIN, or key press) before generating the signature.
Verification by Server
The server from web authentication methods uses the stored public key to verify the signature. Since the private key never leaves the device, attackers can’t steal or reuse it, even in phishing attempts.
As Jeremy Grant, Managing Director at Venable and former leader of the National Strategy for Trusted Identities in Cyberspace, once stated:
“WebAuthn finally gives us a scalable path to eliminate the password, one of the biggest security weaknesses today.”
This quote proves the importance of eliminating password reuse risks and ensuring only the legitimate device holder can complete authentication.
What are the Limitations of Current Authentication Methods?
Traditional authentication methods (passwords, SMS codes, and basic MFA) have many weaknesses. Cloud security threats exploit human error, reused passwords, and outdated protocols to breach accounts and systems.
Methods like SMS or email codes are vulnerable to phishing, social engineering, and SIM-swapping attacks. Even biometrics have risks, as stolen biometric data can't be reset or changed like passwords.
Here are some limitations of current authentication methods that WebAuthn can solve:
Password Fatigue and Reuse Across Platforms
Employees today juggle dozens of accounts, which often leads to password fatigue. Many reuse the same credentials across multiple platforms, making it easier for attackers to compromise several accounts once one password is exposed. WebAuthn authenticator can address this issue effectively.
Phishing and Social Engineering Vulnerabilities
Phishing emails and social engineering tricks remain among the most effective ways to steal login credentials. Even with basic identity security in place, attackers exploit human trust and urgency, bypassing traditional authentication methods.
Weaknesses of SMS and Email OTPs
One-time passwords sent via SMS or email may seem secure but are increasingly vulnerable to interception. As per ABCNews, the FBI reported that SIM-swapping attacks caused over $68 million in losses in the U.S. alone in 2021.
What are the Benefits of WebAuthn for Enterprises?
WebAuthn delivers stronger, passwordless security that resists phishing, credential theft, and replay attacks for enterprises. Users enjoy faster, more convenient logins across platforms and devices, improving their experience daily.
1. Strong Defense Against Credential-Based Attacks
Every day, enterprises face waves of cyberattacks targeting weak or stolen credentials. Traditional passwords are often reused, forgotten, or stolen, leaving systems vulnerable. WebAuthn test removes this weak link, offering a robust, phishing-resistant way to secure identity & access.
- Phishing-resistant authentication: Users no longer rely solely on passwords, drastically reducing the risk of credential theft.
- Hardware-backed security keys: WebAuthn authenticator uses cryptographic keys stored securely on devices, preventing attackers from easily replicating credentials.
- Adaptive authentication: It integrates seamlessly with enterprise systems to ensure strong verification without disrupting workflows.
2. Improved User Experience With Passwordless Access
Managing multiple passwords is a constant headache for users, often leading to frustration and login delays. WebAuthn API simplifies access by eliminating the need for passwords, letting users authenticate quickly and securely with just their authentication methods or biometric verification.
- Faster logins: Users can consider application access management instantly without typing complex passwords.
- Fewer login errors: Passwordless methods reduce failed login attempts caused by forgotten or mistyped credentials.
- Consistent experience: Works uniformly across devices and platforms, providing smooth access for employees and partners.
3. Reduced IT and Helpdesk Burden
Enterprises often spend hours addressing reset requests and troubleshooting login problems, diverting attention from strategic initiatives. WebAuthn reduces these repetitive tasks by enabling passwordless or application access protocols that are more reliable and easier to manage.
With fewer password-related incidents, IT teams can focus on proactive security measures rather than reactive support. Employees experience fewer interruptions, and helpdesk queues shrink, improving overall operational efficiency.
Adopting WebAuthn also decreases security risks tied to human error. Mismanaged passwords or insecure resets are common entry points for attackers. By automating secure authentication, enterprises minimize vulnerabilities.
4. Enhanced Compliance With Security Standards
Enterprises face increasing pressure to meet regulatory and security standards, from GDPR to ISO 27001. WebAuthn helps enterprises align with these frameworks by enforcing strong, passwordless authentication that reduces security risks.
As Satya Nadella once said,
“Our industry does not respect tradition — it only respects innovation.”
Adopting modern authentication like WebAuthn is part of that innovation. Here are some ways it can help:
Regulatory Alignment
By implementing WebAuthn, companies can demonstrate adherence to compliance requirements, reducing the risk of fines and audits.
Audit Readiness
WebAuthn provides clear logs of authentication events, simplifying audit processes and reporting.
Reduced Liability
Stronger authentication practices lower the causes of data breaches, minimizing potential legal and financial repercussions.
WebAuthn Implementation Best Practices
Implement WebAuthn only over secure HTTPS to protect client-side communications and prevent exposure. Verify server-side challenge responses and check application origin to ensure requests are valid and trusted.
1. Start With High-Risk User Groups First
Before rolling out WebAuthn across the enterprise, it’s crucial to focus on high-risk user groups first. These users often have access to sensitive data or privileged accounts, making them prime targets for credential-based attacks. Prioritizing privileged access management ensures the organization mitigates its most critical risks early.
- Executives and C-Level Employees: These users are frequent phishing targets due to access to strategic and financial data. Protecting their accounts first reduces high-stakes exposure.
- Finance and HR Teams: They handle sensitive personal and financial information. Implementing WebAuthn here safeguards employee and customer data.
- IT and Security Administrators: With broad system privileges, a compromised account here can cascade risks across the enterprise. Securing them early prevents large-scale breaches.
2. Educate Employees About Passwordless Authentication
Employee awareness is critical for a successful WebAuthn API rollout. Without proper training, even the most secure systems can fail due to user error or misunderstanding. Enterprises must explain how passwordless authentication works, its benefits, and how it fits into daily workflows.
For example, Microsoft’s implementation of passwordless authentication across its workforce in 2021 involved extensive employee training. This initiative resulted in a significant drop in phishing-related incidents.
3. Use Multiple Authenticator Options (Hardware, Biometric, Device-Based)
Implementing multiple authenticator options ensures flexibility and accessibility while maintaining strong access control. Enterprises can cater to diverse user needs and device types without compromising protection.
Key authenticator options to consider:
- Hardware Security Keys: Devices like YubiKeys provide FIDO2-compliant, phishing-resistant authentication. They are ideal for high-risk roles and critical systems.
- Biometric Authentication: Fingerprint and facial recognition add convenience while keeping credentials private and secure.
- Device-Based Authentication: Leveraging trusted corporate devices ensures seamless login and eliminates password dependence.
3. Ensure Compatibility With Enterprise Systems
Ensuring WebAuthn compatibility with existing enterprise systems is crucial for a smooth rollout. Legacy applications, internal portals, and third-party SaaS management platforms must all support modern authentication standards to prevent access disruptions.
Enterprises should conduct thorough testing across critical systems before full deployment. IT teams need to evaluate single sign-on solutions, identity providers, and endpoint devices to ensure seamless interaction with WebAuthn.
4. Monitor Authentication Logs for Anomalies
Monitoring authentication logs is a critical practice for identifying unusual login activity and potential security threats. By continuously analyzing access patterns, enterprises can detect suspicious behavior, such as repeated failed logins or logins from unusual locations, before incidents escalate.
According to RSA, Nearly half of Americans (about 45%) have experienced a data breach that exposed their personal information in the past five years. This highlights the importance of proactive monitoring to prevent unauthorized access.
Regularly reviewing authentication logs enables IT teams to respond quickly to anomalies, reducing the risk of credential-based attacks.
What are Some Major Challenges of WebAuthn?
WebAuthn faces challenges including complex implementation across diverse systems and devices in enterprises. User adoption remains low due to unfamiliarity with passwordless authentication methods.
1. User Resistance to New Authentication Models
Introducing WebAuthn API often meets resistance from employees accustomed to passwords. Change management is crucial to ease adoption and build confidence in the new system.
- Familiarity Bias: Users may prefer traditional passwords despite the security risks.
- Learning Curve: Initial setup of authenticators or biometric devices can feel cumbersome.
- Support Demand: IT helpdesks may see a spike in queries during rollout periods.
2. Hardware Dependency and Device Limitations
WebAuthn test relies on compatible hardware, such as biometric sensors or security keys. Enterprises must account for device diversity across employees.
- Limited Device Support: Not all laptops, smartphones, or tablets support required authenticators.
- Replacement Costs: Procuring security keys for every employee can be costly.
- Adoption Gap: According to a 2023 survey by Statista, 38% of enterprises cite device compatibility as a major barrier.
3. Integration With Legacy Applications
Legacy enterprise applications may not support modern authentication protocols. WebAuthn implementation often requires significant integration work.
- Custom Development: Older systems may need API or connector development.
- Testing Requirements: Ensuring seamless authentication across platforms demands rigorous testing.
- Operational Overhead: Continuous monitoring and updates are needed to maintain compatibility.
How CloudEagle.ai Helps With Access Control and Authentication?
CloudEagle.ai is a SaaS management and procurement platform designed to help you discover, govern, renew, and optimize SaaS licenses.
With robust identity and access management features, it offers a centralized dashboard to manage user permissions, roles, and access effortlessly.
With over 500 integrations, including finance, SSO, and HRIS systems, CloudEagle.ai simplifies managing your tech stack by enabling granular access control and providing deep insights into user activity, all from one platform.
Application Discovery Without the Guesswork
Within 30 minutes, CloudEagle.ai can surface your entire SaaS portfolio with spend and application discovery. This visibility allows you to flag redundant or unused tools and reduce wasteful spend.

Direct API connections bring all your apps into one view. You’ll see feature-level usage, spot overlaps, and consolidate tools effortlessly.
Set up alerts to catch shadow IT like unsanctioned applications with company credit cards, before they become compliance risks. You can block these tools before they’re ever added to your paid stack.
Just-in-Time Access for Temporary Needs
Grant access only when it’s needed and take it away automatically when it’s not. CloudEagle.ai’s time-based access feature is perfect for managing vendors, contractors, or new teams that need short-term access without compromising long-term security.
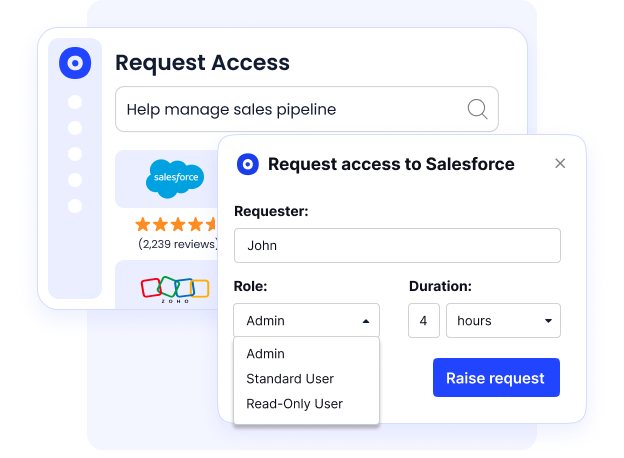
No more manual tracking. Permissions expire on schedule, reducing risk and oversight workload.
Automated Access Reviews for Compliance
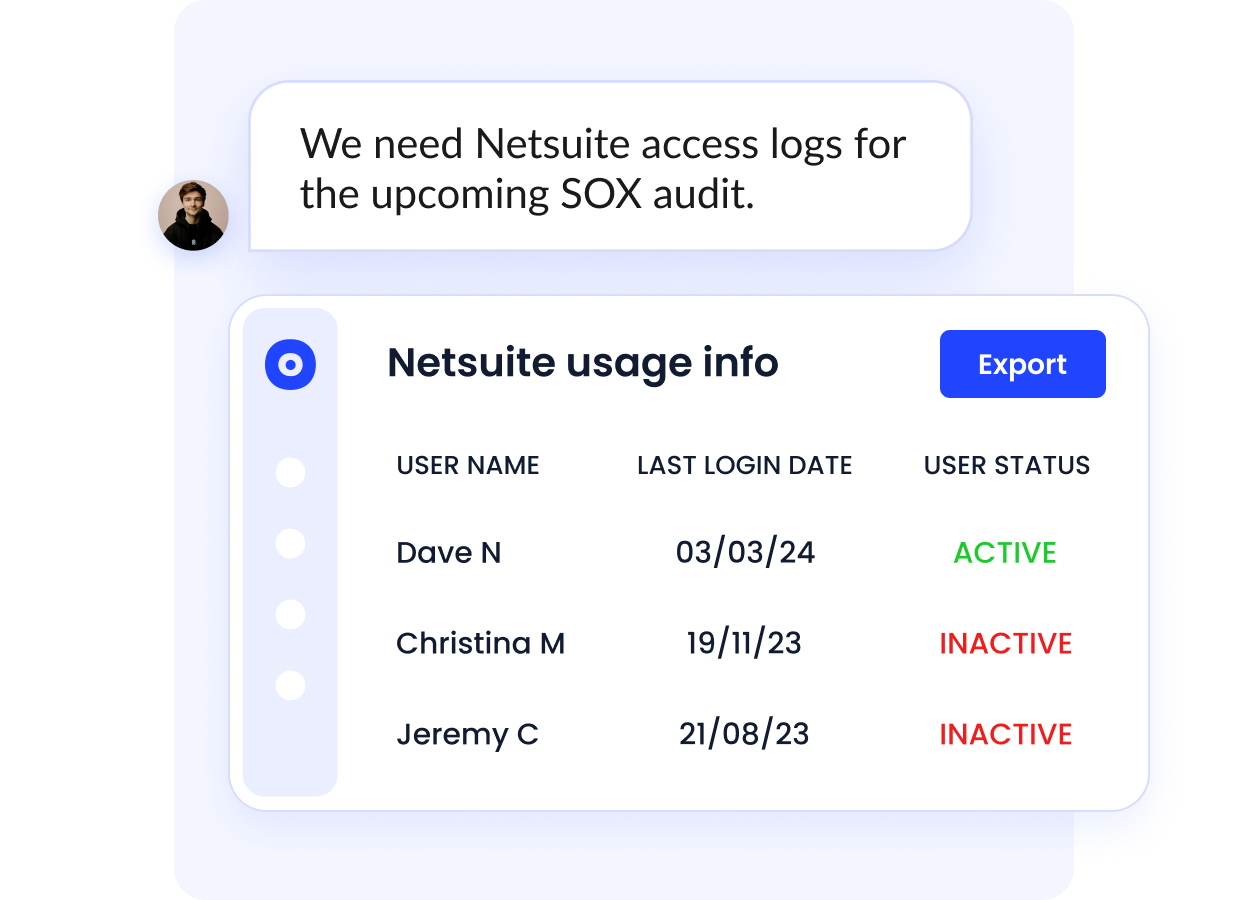
Preparing for SOC 2, ISO 27001, or HIPAA reviews no longer requires spreadsheets and last-minute scrambles. CloudEagle.ai automates access reviews and keeps a live record of provisioning actions. Everything lives in one dashboard—clean, audit-ready, and easy to export.
Access Control that Covers the Full Lifecycle
From the moment access is requested to the point it’s revoked, CloudEagle.ai oversees every step. You’ll know exactly who has access, why they were granted it, and how they’re using it.
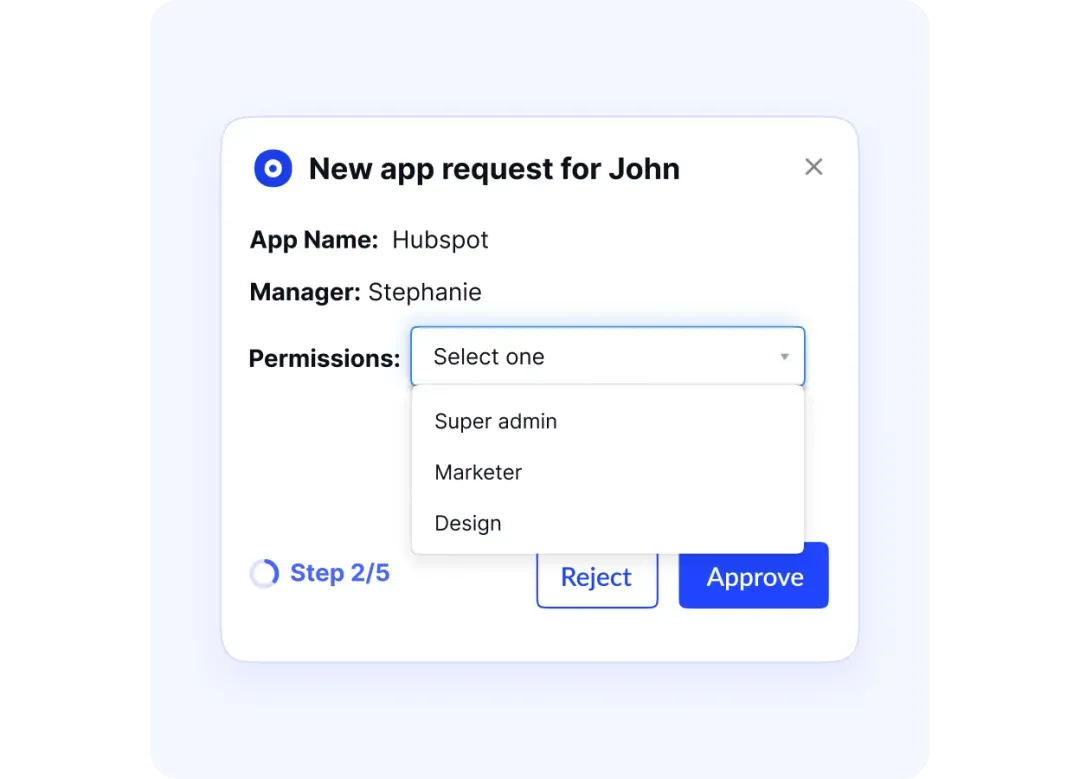
Centralized control makes it easier to stay compliant. Application logs are instantly accessible and exportable, saving hours during audits.
Managing Privileged Access Without Manual Errors
Assigning elevated access to AWS or NetSuite carries risk. CloudEagle.ai reduces that risk by automating privileged access management. Only the right users get elevated permissions, and only for the right systems.
Real-time monitoring and rule-based controls ensure that access stays within policy, easing administrative pressure and improving compliance.
Faster Onboarding, Secure Offboarding
CloudEagle.ai provides automated user provisioning based on department and role, so new hires have everything they need on day one without waiting on IT.

On the other side, access is revoked when users leave or become inactive, protecting your systems from lingering accounts.
Remediant used CloudEagle.ai to automate this process, significantly improving operational efficiency and reducing overhead.
Conclusion
WebAuthn offers enterprises a modern, passwordless authentication framework that significantly reduces security risks. By implementing best practices, enterprises can improve user experience, strengthen compliance, and lower IT support overhead.
To simplify implementation and ensure seamless access management, CloudEagle.ai provides expert guidance, monitoring, and solutions tailored for enterprise-scale. Explore how CloudEagle.ai can help your enterprise strengthen security and streamline authentication workflows today.
FAQs
1. What is WebAuthn used for?
WebAuthn is used for passwordless authentication, replacing passwords with cryptographic credentials for secure user login. It enhances enterprise security and prevents credential theft.
2. Is WebAuthn free?
Yes, WebAuthn is an open web standard available to developers and enterprises without licensing fees. Implementation costs depend on infrastructure and authenticator devices.
3. What is the difference between FIDO2 and WebAuthn?
WebAuthn is a web API standard enabling secure authentication. FIDO2 includes WebAuthn and CTAP, providing complete passwordless login across devices.
4. Is WebAuthn better than 2FA?
WebAuthn offers stronger security than traditional 2FA because it uses public-key cryptography and resists phishing and replay attacks.
5. Is WebAuthn safe?
Yes, WebAuthn is highly secure, storing credentials locally on user devices and preventing phishing, credential reuse, and server-side breaches.

%201.svg)









.avif)




.avif)
.avif)




.png)









