HIPAA Compliance Checklist for 2025

Identity security is the foundation of strong enterprise protection in today’s fast-changing digital world. With more than half of organizations experiencing identity-related breaches that lead to financial losses, the risks are greater than ever.
In fact, 82% of businesses are increasing their investments in identity security in 2025 to combat these escalating risks. Identity security goes beyond just safeguarding passwords; it involves creating a comprehensive, identity-driven security framework that continuously verifies and manages access to sensitive data and systems.
This approach lowers the chance of costly data breaches and helps businesses follow strict rules like GDPR and HIPAA. As cyberattacks become increasingly advanced, particularly with the aid of AI, having a robust identity security program is crucial to safeguard critical assets and maintain customer trust.
Let’s explore the top identity security best practices that help enterprises boost their cybersecurity and protect enterprise access from unauthorized users.
TL;DR
- Using multi-factor authentication (MFA) adds an extra verification step to logins, which greatly blocks hackers even if passwords are stolen.
- Giving users only the access they need helps keep your systems safer by reducing unnecessary permissions and preventing misuse.
- Automating user access when employees join or leave ensures people get the right access quickly and stops former employees from keeping access.
- Switching to passwordless login with biometrics or security keys makes signing in safer and easier while cutting down on password theft risks.
- Protecting sensitive accounts with special tools keeps a close watch on admin access, stopping misuse and securing your most important systems.
What is Identity Security?
Identity security is the practice of protecting digital identities, such as employees, devices, and applications, from unauthorized access and misuse. It ensures that only the right people or systems can access sensitive data and resources, helping businesses defend against cyber threats.
By continuously verifying who is requesting access and managing permissions, identity security prevents breaches caused by stolen credentials or insider threats. It’s a crucial part of modern cybersecurity strategies, especially important as workforces become remote and cloud services expand.
Why Enterprises Should Consider Identity Security?
With cyber threats evolving rapidly, identity-based attacks are a growing risk that can threaten critical data and systems. By 2025, the global cost of cybercrime is projected to reach $10.5 trillion, growing 15% annually, making identity security a critical investment.
Prioritizing identity security helps businesses stay compliant with regulations while protecting customer trust and safeguarding their brand.
Growing Risks From Identity-Based Attacks
Identity-focused cyberattacks are rapidly increasing, with attackers targeting user credentials, cloud identities, and authentication systems through phishing, credential stuffing, and AI-powered deception. These breaches cause severe data loss and disruption, making identity protection the critical first line of defense
Meeting Compliance And Regulatory Requirements
Regulatory frameworks like GDPR, HIPAA, and SOX are tightening access control and data protection requirements globally. Robust identity security helps organizations enforce strict access policies, maintain complete audit trails, and avoid hefty fines and legal repercussions.
Protecting Customer Trust And Brand Reputation
Security incidents exposing customer data can irreparably harm trust and reputation. Proactively securing identities prevents unauthorized access and fraud, reinforcing customer confidence and preserving brand integrity in competitive markets.
Reducing Insider Threats And Access Misuse
Insider threats, accidental or malicious, pose significant risks by exploiting excessive or inappropriate access. Effective identity security enforces least privilege access, continuously monitors user activity, and detects anomalies early to protect against both internal misuse and external credential compromise.
Top 10 Identity Security Best Practices to Follow
In June 2025, over 16 billion stolen credentials were exposed globally, illustrating the massive scale of identity-related cyber risk.
To build a truly identity-secure environment, enterprises must follow a clear set of best practices that protect digital identities, reduce risks, and ensure compliance with regulations.
Here are the top 10 best practices that help enterprises strengthen their identity-driven security and defend against identity-based cyber threats.
1. Enforce Multi-Factor Authentication (MFA)
MFA is a cornerstone of modern identity security. It requires users to verify themselves with two or more methods, like a password and a fingerprint or a one-time code. This greatly reduces unauthorized access, even if passwords get stolen. For better protection, enterprises should use phishing-resistant MFA, like security keys or certificates, instead of less secure SMS codes.
2. Apply the Principle of Least Privilege
Implementing strict access controls ensures users only have the minimum permissions necessary for their roles. This identification security strategy reduces the attack surface by limiting opportunities for insiders or compromised accounts to misuse privileges. Regularly review user permissions and adjust access based on role changes or business needs.
3. Automate User Provisioning and Deprovisioning
Automation of identity lifecycle management strengthens identification cybersecurity by ensuring timely access for new hires and immediate revocation for departing employees or contractors. Automating these processes reduces human error and prevents stale or unauthorized accounts that can be exploited by attackers.
4. Use Strong Password Policies and Passwordless Options
Strong passwords still matter, but modern identity security favors passwordless options like biometrics, security tokens, or cryptographic keys. These improve safety and user experience. When passwords are used, they should be complex, long, and changed regularly.
5. Secure Privileged Accounts With PAM Tools
Privileged Access Management (PAM) is critical for protecting accounts with elevated rights. PAM solutions monitor, control, and audit privileged access, preventing abuse that could lead to significant breaches. Integrating PAM into the identity-driven security framework adds an important layer of control over the most sensitive data and systems.
6. Regularly Review and Audit Access Rights
Regular access reviews and audits are essential to maintain a secure identity environment. Continuous monitoring, combined with periodic certification processes, helps identify and remove excessive or inappropriate privileges, supporting compliance and reducing insider risk.
7. Implement Robust Identity Verification Methods
Strengthen identification security by adopting advanced authentication methods like behavioral biometrics, contextual risk assessments (e.g., location, device posture), and adaptive authentication mechanisms. These techniques go beyond simple password checks, providing continuous identity verification throughout a session.
8. Adopt Zero Trust Principles
The Zero Trust security model assumes no user or device should be trusted by default. Every access request is verified rigorously before granting entry, enhancing identity-driven security by minimizing implicit trust and reducing potential attack vectors across cloud, on-premises, and hybrid environments.
9. Educate Employees on Identity Security
Employees are often the weakest link in identity security. Providing regular training on phishing awareness, password hygiene, and secure access practices empowers users to become active defenders against cyber threats, reinforcing the organization’s overall identification cyber cybersecurity posture.
10. Integrate Identity Security with Broader Cybersecurity Strategies
A siloed approach to identity security is insufficient. Enterprises must weave identity security practices into wider security programs, network defenses, endpoint protections, and application security to create a seamless and layered defense against sophisticated cyberattacks.
How Identity Security is Used in Enterprises?
Enterprises depend on strong identity security to protect important assets, ensure smooth operations, and handle growing cyber risks.
According to CloudEagle.ai’s IGA report, Chetna Mahajan, Global CDO & CIO at Webflow, believes:
“IAM is often the most underfunded yet mission-critical part of security. But those taking a proactive approach, starting with automation and AI-driven governance, are not just reducing risk, they’re unlocking efficiency and long-term cost savings.”
Here’s how identity security works in real-world businesses:
Securing Employee And Contractor Access
One main use is managing access for employees, contractors, and third-party vendors. Centralized identity systems enforce strict login and permission rules. Multi-factor authentication (MFA) and automated access provisioning make sure everyone only accesses what they need. This reduces insider threats and blocks unauthorized access.
Protecting Customer-facing Applications
Customer-facing platforms are common targets for attacks. Identity security solutions help billions of users log in safely with tools like single sign-on (SSO) and adaptive authentication. These strong controls prevent account takeovers and fraud while protecting customer data and meeting privacy laws.
Enabling Secure Remote And Hybrid Work
With more remote and hybrid jobs, identity security must go beyond traditional network access. Zero Trust frameworks verify every access request continuously, no matter the user’s location or device. This stops risks from stolen credentials or unmanaged devices, keeping remote work secure and efficient.
Supporting Compliance Audits And Certifications
Regulations like GDPR and HIPAA require strict identity controls and audit trails. Identity security tools provide detailed logs, automated checks, and reports that simplify audits. Having clear records of who accessed what and when helps companies prove compliance and respond quickly to investigations.
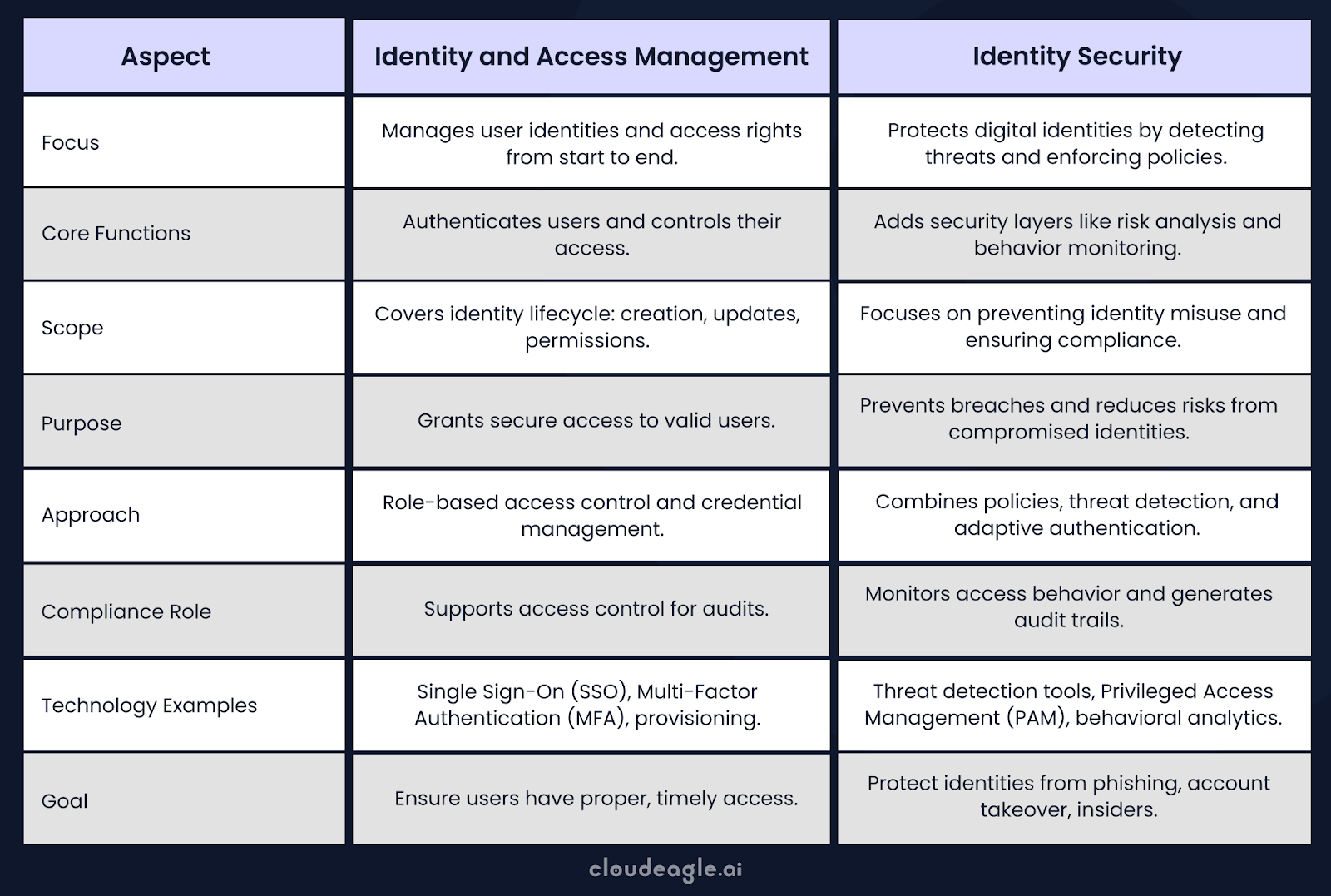
Key Differences Between Identity and Access Management vs. Identity Security
How CloudEagle.ai Can Improve Security and Access Management?
CloudEagle.ai is an AI-powered SaaS management and access governance platform that simplifies the process of securing and managing your cloud environment. It seamlessly integrates with over 500 SaaS applications and your existing IAM, SSO, and security tools, so you can enhance security without disrupting your current setup.
Here’s how CloudEagle.ai strengthens and supports your conditional access strategy:
Real-Time Identity Activity Tracking
CloudEagle.ai continuously monitors user activity across your SaaS applications, capturing logins, access attempts, and unusual behaviors. It identifies risk signals such as logins from unfamiliar locations, repeated failed access attempts, or usage outside normal hours.
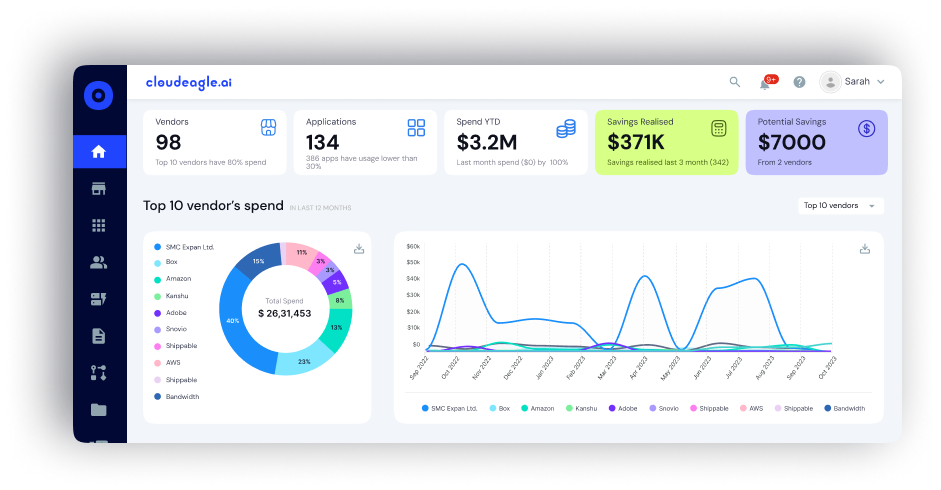
This real-time visibility enables early detection of potential threats, allowing your security team to respond swiftly and prevent incidents from escalating. By adding this proactive layer of monitoring, CloudEagle.ai significantly strengthens your conditional access policies and overall security posture.
Automated User Access Management
Managing user access manually often leads to delays and errors. CloudEagle.ai automates this process by aligning access rights with users' roles and changes in their employment status.

When someone's role shifts or they leave the company, CloudEagle.ai automatically updates or removes their access, reducing the risk of lingering over-privileged accounts and easing administrative workloads. This ensures your access policies are consistently enforced.
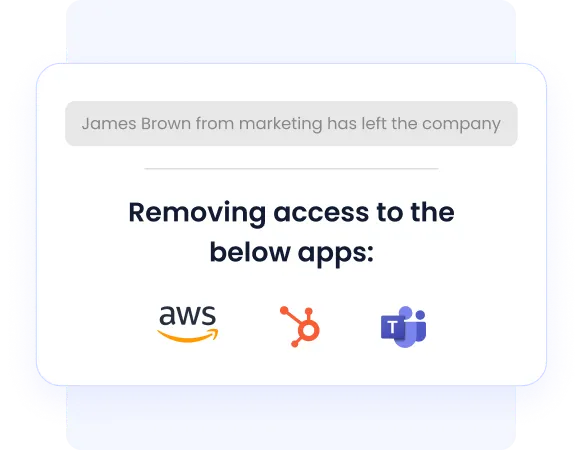
Discover how Treasure Data Streamlined Employee Offboarding using CloudEagle.ai
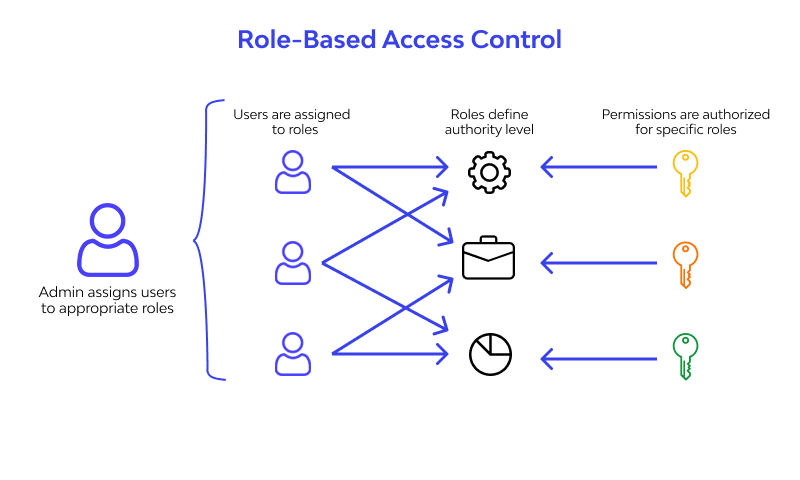
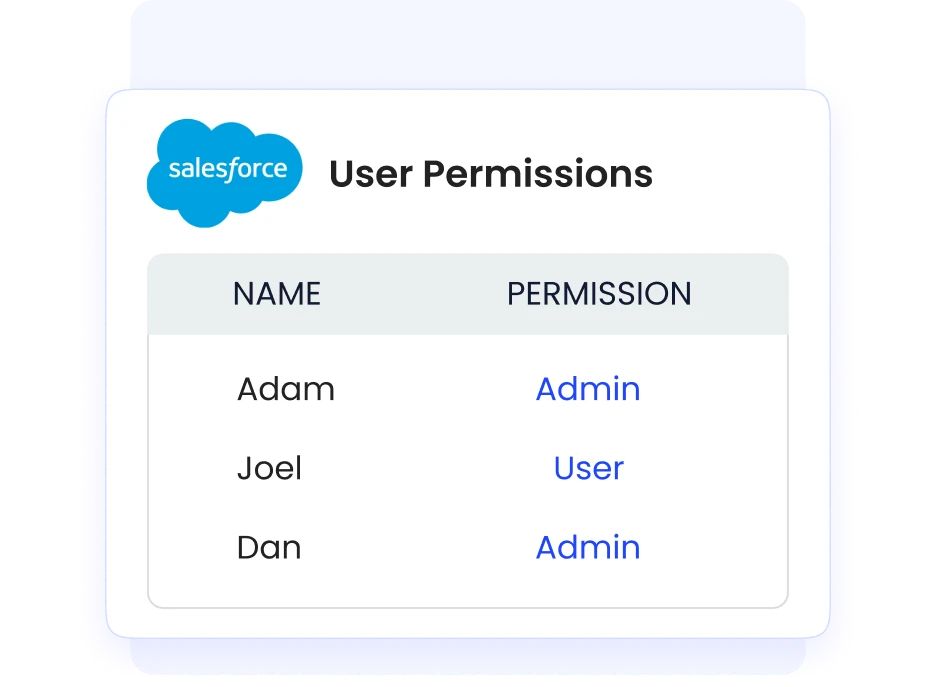
Role-Based Access Controls
With CloudEagle.ai, you can create precise roles and assign specific permissions based on job functions. This ensures users have only the access they need to do their work. CloudEagle.ai automates role assignments and policy enforcement, making management simpler while enhancing security by preventing excessive permissions.
Securing Privileged Accounts
CloudEagle.ai puts strong controls around high-level admin accounts. The platform monitors privileged access, applies the principle of least privilege, and can require extra verification steps for sensitive systems. This safeguards powerful accounts from misuse or compromise within your environment.
Temporary Just-in-Time Access
CloudEagle.ai supports just-in-time access, granting users temporary permissions only when needed and for a specified duration. This reduces standing privileges, which are tempting targets for attackers. JIT access minimizes exposure to sensitive resources, reinforcing a zero-trust security model by granting access only as necessary.
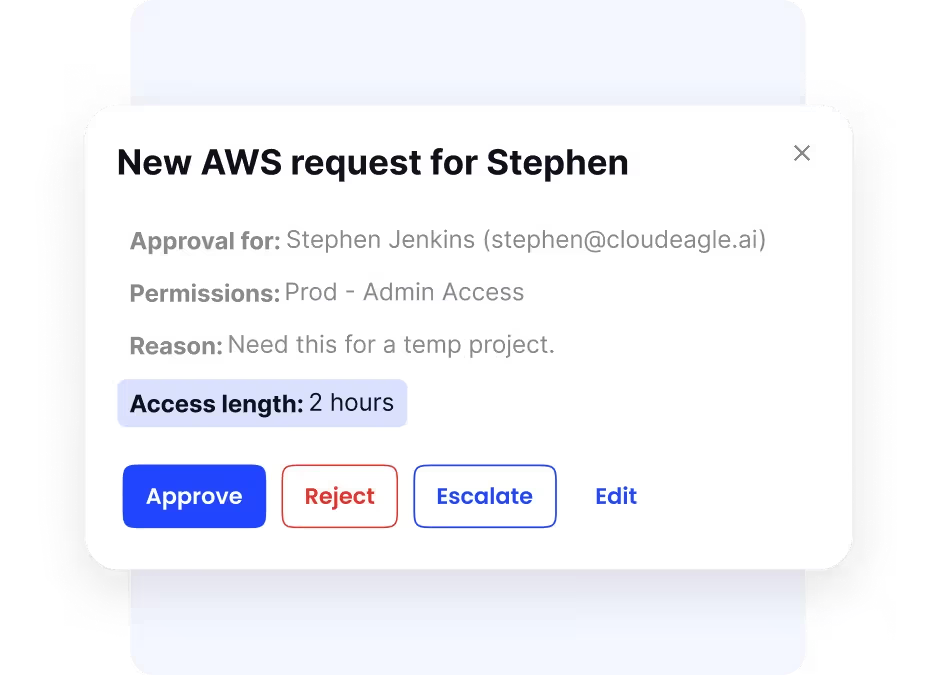
Regular Access Audits
To keep tight control over access, CloudEagle.ai automates scheduled access reviews. Reviewers receive reminders to certify user permissions regularly, helping spot outdated or redundant access rights. This keeps your environment compliant with policies and regulations.
Detailed Audit Logs & Compliance
CloudEagle.ai maintains detailed logs of all access actions, policy changes, and enforcement activities. These audit trails support transparent reporting and help you meet compliance requirements for standards like GDPR, HIPAA, and SOX. Generating reports to show policy adherence and pass security audits is easy and efficient.

Self-Service Access Requests
Users can easily request access to SaaS applications through CloudEagle.ai’s intuitive self-service portal. This reduces the workload on IT teams and speeds up the approval process while ensuring requests follow proper approval workflows aligned with conditional access policies.

Adaptive Risk-Based Access Policies
CloudEagle.ai strengthens conditional access by applying flexible, risk-aware controls. It dynamically adjusts security requirements based on factors like device health, user location, and unusual behavior. This approach raises security barriers when risks are high while allowing smooth access in safer contexts, enhancing both security and user experience.
Alice Park shares how CloudEagle.ai helped her team save hundreds of hours by automating user onboarding and offboarding. Before using CloudEagle.ai, they spent a lot of time manually provisioning and deprovisioning users. With CloudEagle.ai, these workflows are streamlined, reducing errors and significantly improving security.
Conclusion
Identity security is the foundation of modern enterprise protection. As cyber threats continue to evolve, organizations must adopt a strong identity driven security approach to safeguard digital identities, control access efficiently, and ensure compliance.
Recent studies show that 91% of enterprises experienced at least one identity-related cyber incident in the past year, highlighting the critical need to prioritize identity-first defenses.
To reduce risks from identity-based attacks and insider threats, enterprises should implement proven best practices such as multi-factor authentication, least privilege access, and automated user management.
Businesses can reduce risks from identity-based attacks and insider threats. Protecting employee access, securing customer-facing applications, and enabling safe remote work all start with strong identity security.
Enterprises that prioritize identity security build trust with customers and maintain business continuity in an increasingly complex digital world.
Are you ready to strengthen your organization's security with cutting-edge identity protection?
Schedule a demo with CloudEagle and see how our innovative platform can secure your enterprise access seamlessly and efficiently.
FAQs
1. What are the 5 C's of cyber security?
The 5 C's of cyber security are Change, Compliance, Cost, Continuity, and Coverage. They guide businesses in adapting to new threats, meeting regulations, controlling expenses, ensuring operations during attacks, and protecting all digital assets.
2. What is the purpose of identity security?
The purpose of identity security is to protect digital identities from misuse by verifying user access and blocking unauthorized entry, keeping sensitive data safe.
3. What are the levels of identity security?
Levels include basic passwords, multi-factor authentication (MFA), adaptive verification, behavioral biometrics, and privileged access management (PAM) for stronger identity protection.
4. What is the meaning of identity security?
Identity security means protecting user identities online by verifying who they are and controlling their access to keep systems safe from attacks.
5. What is an identity security platform?
An identity security platform is a system that combines tools like authentication, access management, and threat detection to protect digital identities and control access.

%201.svg)







.avif)




.avif)
.avif)




.png)









