HIPAA Compliance Checklist for 2025

When employees log into corporate systems, countless security checks happen behind the scenes. These rules, called access management protocols, decide who can enter, what they can see, and how long access lasts.
The risks of weak IAM protocols are very real. In 2021, Colonial Pipeline suffered a major ransomware attack. The breach disrupted fuel supply across the East Coast, showing how fragile systems become without strong access controls.
As remote work and cloud adoption accelerate, securing access has never been more critical. This article explains what access management protocols are, their key types, and the best benefits of identity federation protocols for enterprises to stay protected.
TL;DR
- Access management protocols are technical standards that authenticate, authorize, and manage user sessions, ensuring secure entry to enterprise systems.
- Strong IAM protocols safeguard sensitive data, support compliance, and reduce risks from identity-based cyberattacks.
- Authentication, authorization, session management, audit logging, and policy enforcement form the backbone of effective access controls.
- Commonly used protocols include SAML, OAuth 2.0, OpenID Connect, LDAP, Kerberos, and RADIUS.
- CloudEagle.ai automates provisioning, deprovisioning, access reviews, and compliance—helping enterprises strengthen IAM and reduce audit burdens.
What Are Access Management Protocols?
Access management protocols are technical standards that control how users are authenticated and authorized to access digital resources. They define rules for identity verification and ensure only authorized individuals reach sensitive systems and data.
Serving as digital gatekeepers, these entry authorization protocols help prevent misuse and causes of data breaches across enterprise applications, networks, and the cloud. Key elements of access management protocols include:
- Authentication: Verifies user identity, often through passwords, biometrics, or multi-factor authentication methods.
- Authorization: Determines what a verified user can access, based on assigned roles or permissions.
- Session management: Tracks user activity during a session to prevent misuse or unauthorized extensions.
- Audit logging: Records access events, enabling enterprises to detect anomalies and meet SaaS compliance requirements.
- Policy enforcement: Applies predefined rules to maintain consistency in access across users and devices.
Why Are IAM Protocols of Utmost Importance?
IAM protocols are essential SaaS security best practices that control who can access data, reducing the risk of data breaches. They protect sensitive data and mitigate threats from both internal and external sources.
1. Safeguarding Sensitive Data and Applications
Every enterprise handles data that could damage trust or business continuity if exposed. Access management protocols ensure only authorized users access sensitive applications, minimizing the risk of leaks or misuse. They also help IT teams enforce strict security without slowing legitimate workflows.
Key safeguards include:
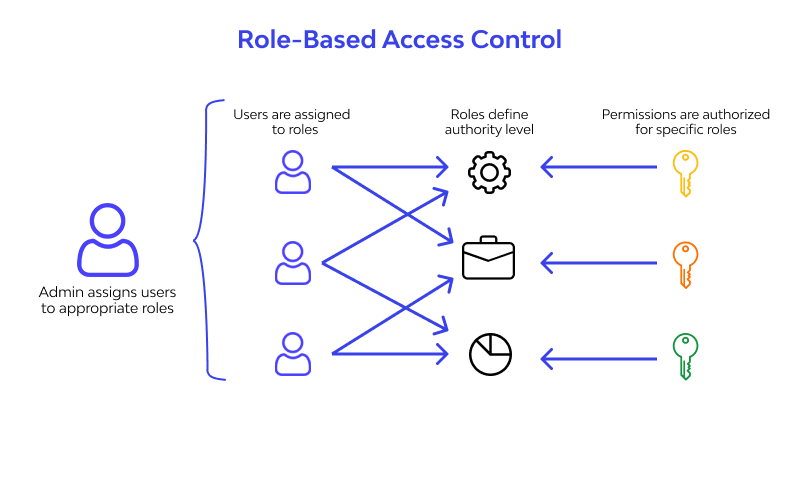
Role-Based Access Control (RBAC)
Assign role-based access control strictly based on job roles, ensuring employees access only what they need.
Multi-Factor Authentication (MFA)
Adds essential identity checks that block attackers, even if credentials are compromised.
Least Privilege Principle
The entry authorization protocols grant minimal access required for tasks to mitigate insider misuse or accidental exposure.
Session Management Controls
Closes idle sessions to prevent unauthorized use after termination or vacancy.
A real-world breach in 2024 demonstrates why this matters: during the Snowflake incident, attackers exploited stolen credentials, lacking MFA, to access over 160 customer environments. That compromised organizational trust and highlighted the danger of weak access management protocols.
2. Supporting Regulatory and Compliance Standards
Regulatory frameworks like GDPR, HIPAA, and SOX compliance require enterprises to prove that access to sensitive systems is tightly controlled. IAM protocols provide the foundation for demonstrating compliance by enforcing consistent rules.
When enterprises implement these identity federation protocols, audits become smoother and less resource-intensive. Instead of scrambling for documentation, teams can rely on automated access reports and activity records to meet auditor expectations.
Beyond avoiding fines, compliance strengthens trust with regulators, partners, and customers. Enterprises that align access management protocols with global standards show they value data privacy and operational integrity.
3. Reducing Risk of Identity-Based Cyberattacks
Identity-based cyberattacks, where malicious actors exploit stolen credentials, are among the most dangerous threats facing organizations today. Robust IAM protocols, like multi-factor authentication, least-privilege access, and continuous monitoring, are essential to breaking the “Identity Attack Chain” before threats can escalate.
Richard Clarke, former U.S. national security advisor, said.
“If you spend more on coffee than on IT security, you will be hacked.”
This quote highlights the importance of prioritizing security investments, reminding enterprises that identity protection must be central to their defense strategy.
What are the Top Access Management Protocols?
Enterprises use top access management protocols to authenticate users, authorize actions, and manage sessions across systems and networks. These access management protocols create a consistent security layer and are chosen based on application environment, business needs, and SaaS compliance demands.
1. Security Assertion Markup Language (SAML)
SAML is an XML-based open standard widely used for federated identity and single sign-on (SSO). It enables users to authenticate once with an identity provider and securely access multiple applications across domains.
SAML continues to dominate enterprise environments due to its maturity and interoperability. As of 2025, Gartner reveals that approximately 82% of enterprises implement SAML-based SSO, particularly in regulated sectors like finance and healthcare.
This widespread adoption ensures a robust ecosystem of tools, vendor support, and proven resilience. For enterprises aiming to centralize authentication protocol and comply with complex security policies, SAML remains a foundational and trusted choice.
2. OAuth 2.0 for Authorization
OAuth 2.0 or is an industry-standard authentication protocol designed to allow secure delegated access. Instead of sharing passwords, this access management protocol enables identity federation protocols to obtain limited access tokens on behalf of users, protecting both credentials and data.
Token-Based Access
Users grant application tokens with limited permissions, avoiding unnecessary exposure of sensitive credentials. This authentication protocol ensures higher security across connected platforms.
Granular Permissions
OAuth IAM protocol allows precise control over what applications can and cannot access, strengthening compliance and reducing unauthorized exposure.
Its flexibility and scalability make OAuth 2.0 essential for securing APIs, mobile apps, and multi-cloud systems. Enterprises implementing it not only enhance security but also improve user experience by reducing friction during authentication.
3. OpenID Connect for Authentication
OpenID Connect (OIDC) builds on top of OAuth 2.0, providing a standardized way to verify user identities. This authentication method simplifies authentication for web, mobile, and API-driven applications by enabling single sign-on across platforms.
Streamlined User Experience
OIDC access management protocol reduces login friction by letting users authenticate once and access multiple services seamlessly.
Verified Identity Layer
It introduces an identity layer, ensuring that applications not only authorize but also confirm user identities securely.
Developer Friendly
With support for JSON Web Tokens (JWT), OIDC makes integration with modern applications more flexible and lightweight.
For example, Microsoft uses OIDC in Azure Active Directory for enterprise single sign-on. This allows employees to log in once and securely access Microsoft 365, Teams, and third-party apps without managing separate credentials.
4. Lightweight Directory Access Protocol (LDAP)
LDAP is a widely used access protocol that enables applications to query and manage user information stored in directory services. LDAP access management protocol plays a critical role in centralizing identity data, making authorization and authentication protocol more efficient across enterprise systems.
Enterprises rely on LDAP to unify identity and access management, especially in environments where users need to log into multiple internal applications. Its hierarchical structure allows administrators to manage credentials, roles, and permissions in a standardized way.
Despite being an older protocol, LDAP continues to be relevant, particularly in hybrid IT environments. It remains a foundation for enterprise identity solutions, often integrated with tools like Active Directory for broader security management.
5. Kerberos Authentication Protocol
Kerberos is a time-tested protocol designed to verify user identities through secure tickets instead of passwords. These access protocols reduce the risk of credential theft by minimizing repeated password exchanges across networks.
As Benjamin Franklin once said, “An ounce of prevention is worth a pound of cure.”
- Ticket-Based Authentication: Kerberos issues time-bound tickets, which grant access securely without repeatedly entering passwords. This minimizes risks of interception.
- Mutual Verification: Both the user and the service validate each other, ensuring attackers cannot impersonate either side.
- Enterprise-Wide Use: Kerberos is widely deployed in corporate networks, integrated with systems like Active Directory for single sign-on.
- Strong Encryption: It uses cryptographic techniques to secure communication, protecting identities even across unsecured networks.
6. RADIUS for Network Access Control
Remote Authentication Dial-In User Service (RADIUS) is a protocol enterprises rely on to control network access. This auth protocol validates users before granting entry, often used in Wi-Fi, VPNs, and enterprise networks.
- Centralized Authentication: RADIUS connects to a single server, streamlining user verification across multiple access points and devices.
- Policy Enforcement: This access management protocol applies role-based access control policies, ensuring only the right users access critical systems or data.
- Scalability for Enterprises: RADIUS supports thousands of users, making it suitable for enterprises with distributed networks.
- Integration with MFA: It pairs with modern multi-factor authentication to add extra layers of security.
- Strong Use Cases: Enterprises often deploy RADIUS to protect wireless networks, VPNs, and remote workforce connections.
How CloudEagle.ai Can Help Enterprises Manage Access?
CloudEagle.ai simplifies how you manage and optimize SaaS tools from discovery to renewal, while keeping license spend and governance in check.
Its built-in identity and access management capabilities give you full visibility into user roles, permissions, and app access from one centralized dashboard.
With 500+ integrations across SSO, HRIS, and finance systems, you can take control of SaaS access, monitor usage patterns, and enforce the right permissions, all without switching platforms.
Automated App Access Reviews
CloudEagle.ai access management solutions takes the manual work out of SOC 2 and ISO 27001 audit reviews. Thus, no more scrambling to audit apps or prove deprovisioning.
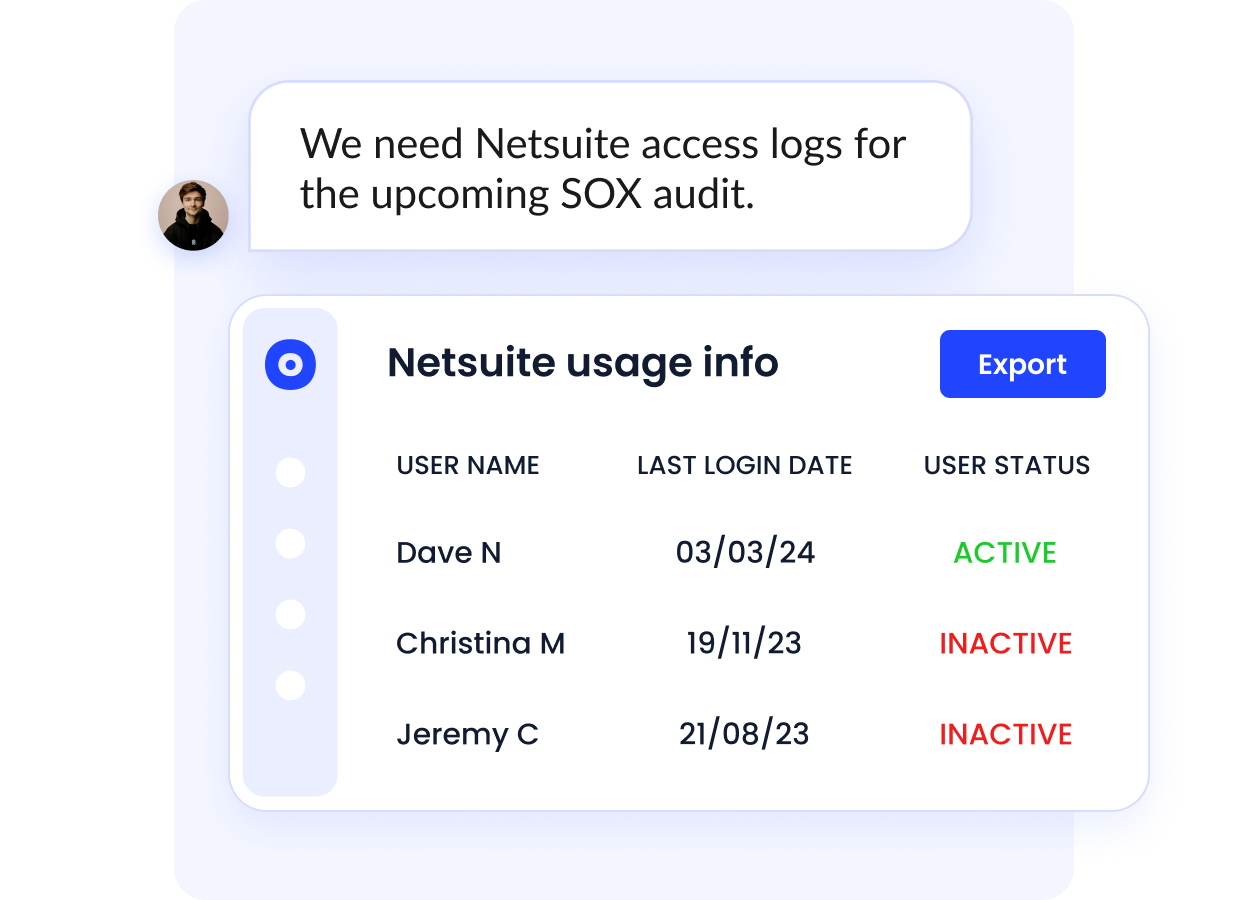
By centralizing key systems into a single, easy-to-navigate dashboard, it simplifies compliance and helps you stay audit-ready without the last-minute chaos.
Just-in-Time Access
CloudEagle.ai lets you grant time-based access to critical systems, automatically revoking permissions when the job’s done.
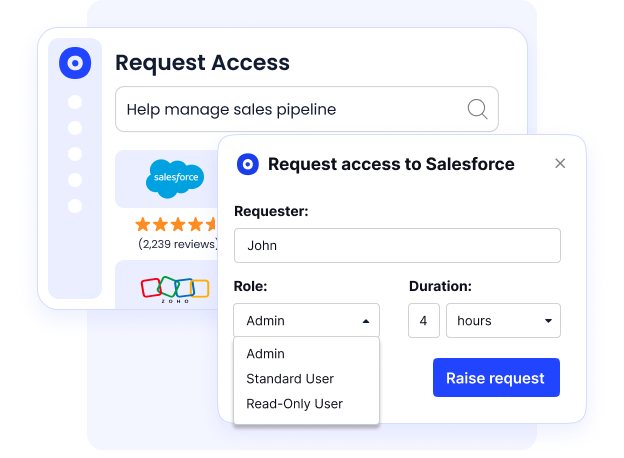
It’s a smart way to reduce access creep, perfect for contractors, freelancers, and temporary staff, giving them exactly what they need for exactly as long as they need it without constant manual intervention.
Access Control
CloudEagle.ai provides identity and access, which gives you complete visibility into who has access to what, why they have it, and how it’s being used, all from one place.
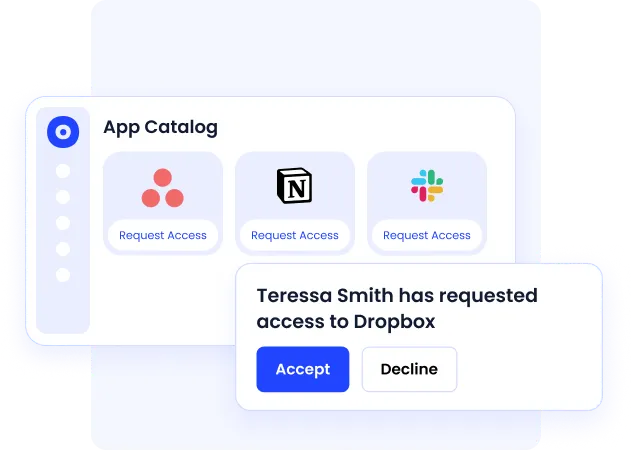
From intake to provisioning to deprovisioning, you can manage the entire access lifecycle through a centralized system. And when audit time rolls around, exporting detailed access logs is fast without delays.
Privileged Access Management
CloudEagle.ai simplifies privileged access management by automating how elevated access is granted sothat only the right people reach critical systems like AWS and NetSuite.
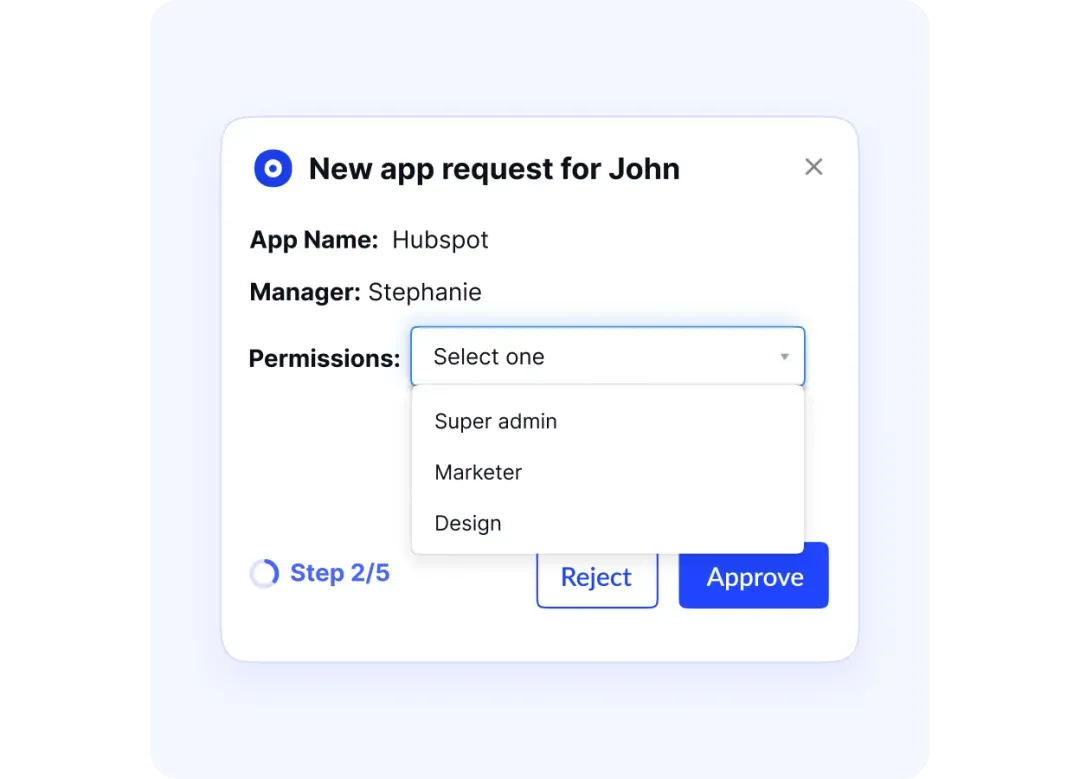
With real-time monitoring and built-in safeguards, you can strengthen security and compliance without adding to your team’s workload—or leaving room for manual mistakes.
Automated User Provisioning and Deprovisioning
Managing access manually opens the door to errors, delays, and security risks, especially during onboarding and offboarding. Users may end up with too much access or not enough to do their jobs effectively. And if accounts aren’t deprovisioned properly, former employees could retain access to sensitive systems.
CloudEagle.ai automates access throughout the employee lifecycle, assigning the right permissions from day one and revoking them instantly when someone leaves or goes inactive. It speeds up onboarding, reduces manual work, and keeps your environment secure and compliant.
Alice Park from Remediant saw this firsthand. What used to take hours of app-by-app deprovisioning is now handled in minutes through CloudEagle’s automated workflows.
Compliance Management
CloudEagle.ai gives you a centralized view of compliance in SaaS contracts without any spreadsheets or blind spots. It continuously scans for risks, tracks certifications, monitors account activity, and simplifies external audits, so you can stay ahead of compliance requirements without the usual chaos.
Conclusion
Access management protocols are the backbone of enterprise security, ensuring users access only what they’re authorized to. They not only safeguard sensitive data but also streamline compliance, improve risk management framework, and user experience.
Adopting the right auth protocols is essential for protecting digital assets in today’s hybrid IT landscape. Enterprises that modernize their access management strategy build stronger defenses and maintain trust with customers and stakeholders.
With CloudEagle.ai, you can simplify access governance, automate user provisioning, and enforce security at scale. Schedule a demo today to see how we help enterprises secure and optimize access.
FAQs
1. What are the protocols used in access control systems?
Access control systems commonly use SAML, OAuth 2.0, OpenID Connect, LDAP, Kerberos, and RADIUS. These protocols enable secure authentication, authorization, and role-based access across applications, networks, and enterprise systems.
2. What are the 4 pillars of IAM?
The four pillars of IAM are authentication, authorization, user management, and central policy enforcement. Together, they define how organizations manage identities, secure access, and maintain compliance across multiple environments.
3. What are the 4 A's of IAM?
The 4 A’s of IAM are authentication, authorization, administration, and auditing. These components ensure users are verified, given proper access, managed effectively, and continuously monitored for compliance and security.
4. Which protocols are related to IAM and SSO?
Protocols like SAML, OAuth 2.0, OpenID Connect, LDAP, and Kerberos are related to IAM and SSO. They work together to manage secure sign-ins, enable single sign-on, and streamline enterprise user access.
5. What protocol is used for SSO?
Single sign-on is most commonly enabled using SAML and OpenID Connect. SAML is often used in enterprises, while OpenID Connect provides lightweight, modern authentication for mobile and cloud-based applications.

%201.svg)









.avif)




.avif)
.avif)




.png)









