HIPAA Compliance Checklist for 2025

Today, enterprises rely heavily on cloud applications for everything from collaboration to data storage. While the cloud offers speed and flexibility, it also introduces new security challenges. Keeping sensitive information safe and controlling user access has become more complex than ever.
To solve these issues efficiently, a Cloud Access Security Broker (CASB) acts as a gatekeeper between users and cloud services. CASB solutions provide IT teams with visibility and control over cloud usage, helping enforce security policies, monitor activity, and protect data across multiple cloud platforms.
The global CASB market is projected to grow from approximately USD 8.5 billion in 2025 to USD 38.3 billion by 2035, with a CAGR of 16.3% during this period.
Let’s explore what a Cloud Access Security Broker is and how it works, as understanding this can make all the difference in strengthening your enterprise’s security posture.
TL;DR
- A cloud access security broker (CASB) is a security tool that sits between users and cloud services, providing visibility, control, and protection over cloud usage.
- CASBs help enterprises monitor cloud app usage, enforce security policies like data loss prevention (DLP), detect threats, and ensure compliance with regulations.
- CASB solutions come in API-based, proxy-based, or hybrid models, offering different ways to secure cloud environments effectively.
- Key benefits of CASBs include enhanced visibility, improved data security, risk reduction through threat detection, and control over unauthorized shadow IT.
- Following best practices such as aligning CASB with business policies, integrating with IAM and DLP tools, and regularly updating policies maximizes CASB effectiveness.
What is Cloud Access Security Broker?
A cloud access security broker, or CASB, is a security tool that works like a gatekeeper between a company’s internal systems and the cloud services it uses. Its main job is to help enterprises see clearly and control how their cloud services are used. By being between users and cloud apps, a CASB helps monitor cloud activity and enforce security rules to protect important data.
Understanding what a cloud access security broker does is important to see how it improves cloud security and helps enterprises follow regulations. Many vendors offer different CASB solutions, but they all focus on protecting cloud environments effectively.
What does a cloud access security broker do?
A cloud access security broker (CASB) provides key security functions to protect cloud data and users, including:
- Visibility: It gives clear insights into how cloud apps are being used, helping spot any unauthorized or risky activities.
- Policy Enforcement: It enforces security rules like data loss prevention (DLP), encryption, and verifying user identity through authentication.
- Threat Detection: It watches for unusual or suspicious behavior to stop insider threats and external attacks before they cause harm.
- Compliance Support: It helps enterprises meet legal and industry regulations by auditing cloud activities and generating important reports.
- Access Control: It manages who can access specific information across various cloud services, improving security control.
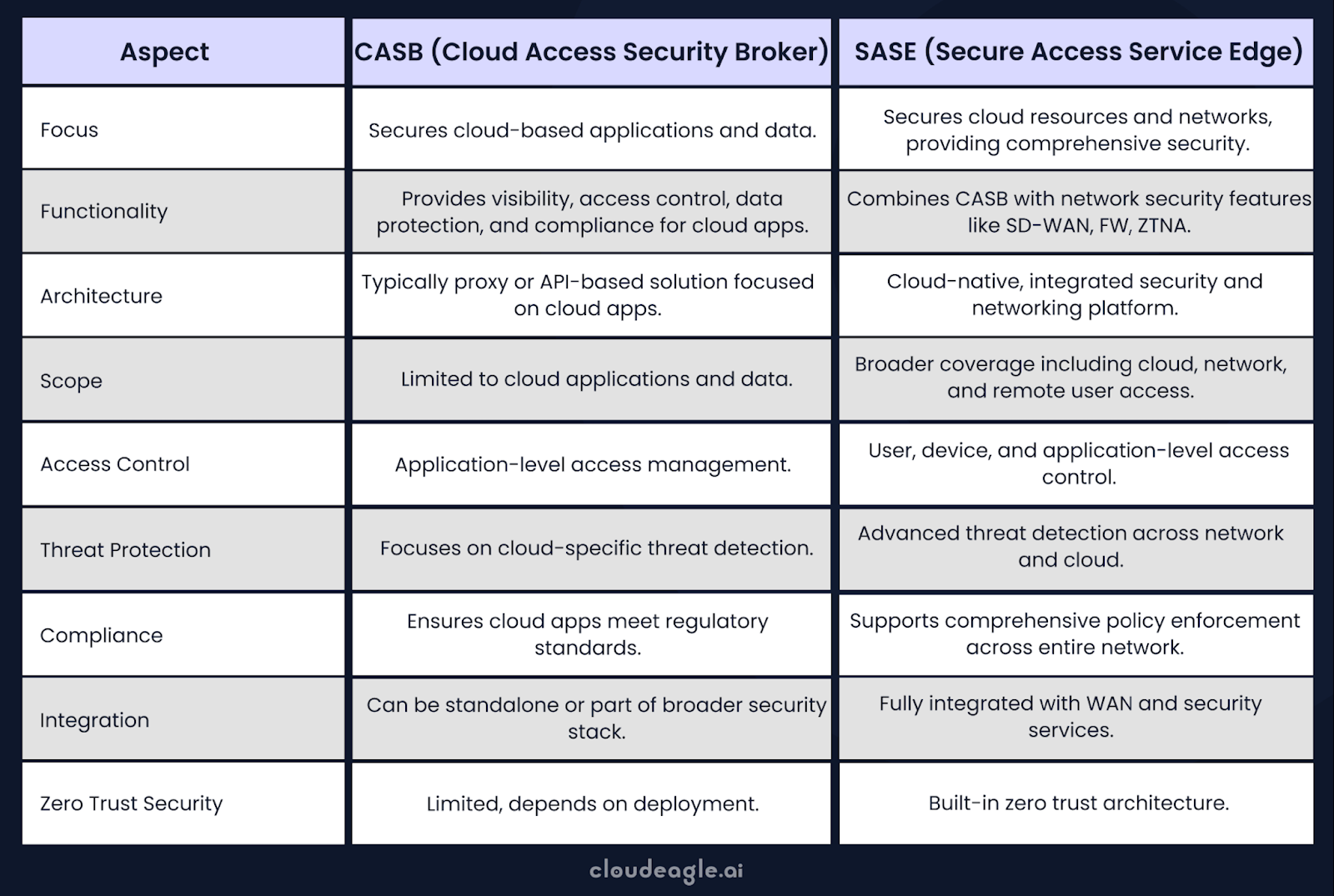
What is the difference between CASB and SASE?
What are the Benefits of Using CASB?
A cloud access security broker (CASB) offers multiple benefits that help enterprises protect their data, manage risks, and ensure compliance in the ever-expanding cloud environment.
Enhanced Visibility into Cloud Usage
One of the biggest benefits of a cloud access security broker (CASB) is its clear visibility into cloud app usage. It monitors how users access cloud services and detects unauthorized or risky actions. This helps enterprises track all cloud activity and respond swiftly when needed.
Data Security and Compliance Support
Cloud access security broker solutions protect sensitive data by enforcing security policies like encryption and data loss prevention (DLP). They also help enterprises meet industry and government regulations by providing auditing, reporting, and compliance tools for cloud activities.
Treat Detection and Risk Reduction
A CASB platform continuously monitors cloud environments to detect unusual or malicious behavior. This proactive threat detection helps reduce risks from insider threats, data breaches, and cyberattacks, strengthening the enterprise’s overall security stance.
Improved Control over Shadow IT
Shadow IT refers to employees using unauthorized cloud apps that can introduce security vulnerabilities. CASB solutions identify and manage shadow IT by tracking unsanctioned cloud services and enforcing policies to control access, helping reduce hidden risks.
What are the Four Pillars of Cloud Access Security Broker?
A Cloud Access Security Broker (CASB) is based on four key pillars that together secure cloud environments. These pillars help enterprises control access, protect data, and ensure compliance. Here they are:
1. Visibility
The first pillar is visibility. A cloud access security broker provides comprehensive insight into cloud application usage across the enterprise. This visibility helps identify who is accessing what data and how, allowing IT teams to detect unauthorized or risky behavior in real time.
Know this inspiring success story of how Edge gets complete spend visibility with CloudEagle.ai.
2. Compliance
Compliance is a critical pillar of cloud access security broker solutions. CASBs assist enterprises in meeting regulatory requirements by enforcing policies and generating detailed audit reports. This ensures that cloud usage aligns with industry standards and legal obligations.
3. Data Security
Data security is at the heart of any cloud access security broker CASB platform. By implementing data loss prevention (DLP), encryption, and access controls, a CASB protects sensitive information from accidental leaks or malicious attacks while it moves through the cloud.
4. Threat Protection
Threat protection completes the four pillars. Cloud access security broker CASB solutions continuously monitor for unusual activities or cyber threats within cloud environments. This proactive detection and response significantly reduces the risk of insider threats, data breaches, and external attacks.
What are the Different Types of CASB?
Cloud Access Security Brokers (CASBs) come in different types to meet various business needs. The main types are:
API-based CASB
This type connects directly with cloud services using APIs. It gives deep insight into data and user activities without affecting user traffic. It helps monitor activity, protect data, and ensure compliance across cloud apps.
Proxy-based CASB
This type works by sitting between users and cloud services, monitoring traffic in real time. It can stop unauthorized actions and protect data by enforcing security rules as users interact with the cloud.
Hybrid CASB Models
This combines both API-based and proxy-based methods. It offers the benefits of both: detailed visibility and control through APIs, plus real-time monitoring and enforcement through proxies. This makes it a flexible and strong choice for complex cloud environments.
How Does CASB Work?
A Cloud Access Security Broker (CASB) is a key security layer between users and cloud services. It helps enterprises monitor cloud use, enforce security rules, detect threats, and ensure compliance across cloud apps.
Models: API vs Proxy-Based
Cloud Access Security Broker solutions mainly use two models: API-based and proxy-based. In the API-based model, the CASB connects directly with cloud service providers through their APIs. This allows for continuous, deep visibility without disrupting user traffic.
In contrast, the proxy-based model routes user traffic through the CASB, either as a forward or reverse proxy. This provides real-time control over data flow, user access, and security policy enforcement. Some solutions combine both models in hybrid setups for fuller protection.
Data Monitoring and Control
Cloud Access Security Broker solutions primarily use two models: API-based and proxy-based. The API-based model connects directly with cloud service providers through their APIs, allowing continuous and deep visibility without affecting user traffic.
The proxy-based model routes user traffic through the CASB, acting as either a forward or reverse proxy. This enables real-time control over data flows, user access, and policy enforcement. Some CASBs combine both models in hybrid setups for broader security coverage.
User Behavior Analytics and Policy Enforcement
CASBs watch the data traveling to and from cloud apps, checking for sensitive info or rule-breaking. They use tools like data loss prevention (DLP), encryption, and access controls to keep data safe from unauthorized access or leaks. This helps enterprises make sure only the right people can use the data, while stopping risky actions and sharing right away.
What is the Best Practice of CASB?
To make the most of a Cloud Access Security Broker (CASB), enterprises should follow simple best practices. These help ensure strong cloud security and fit well with their overall IT plans. By doing this, enterprises can protect data better and manage risks more effectively.
Align CASB with Business Security Policies
First, make sure the CASB matches your enterprise’s security rules. Customize the controls and settings to fit your specific compliance needs, risk levels, and daily operations. This keeps your cloud environment safely protected all the time.
Integrate CASB with IAM and DLP Tools
Connect the CASB with identity and access management (IAM) and data loss prevention (DLP) tools. This improves security by making it easier to manage user access and protect sensitive data across all cloud apps in one unified system.
Monitor and Control Shadow IT
Shadow IT is when employees use cloud apps without approval, which can create hidden risks. A CASB helps find and manage these unknown apps, enforcing rules to block or control unauthorized use and reduce security gaps.
Regularly Update Policies for New Threats
Cyber threats constantly change, so it’s important to update your security policies often. Regular policy reviews keep your CASB ready to protect against the latest risks and stay ahead of cyberattacks.
How CloudEagle.ai Can Assist in Enhancing Access Control?
CloudEagle.ai is an advanced SaaS management and access governance platform that keeps your enterprise’s cloud environment safe and easy to manage. It connects with over 500 cloud apps, including tools like identity and access management (IAM) and single sign-on (SSO).
This lets you control user access to all your cloud apps from one place, removing security gaps caused by unconnected systems. The platform works with all types of apps, whether they use SCIM or not, helping you manage access smoothly across your entire cloud environment.
Here’s a detailed look at how CloudEagle.ai helps keep your systems safe and secure:
Real-Time User Activity Monitoring
CloudEagle.ai continuously tracks what users do across all connected cloud apps. It tracks all actions like logging in, downloading files, sharing documents, or making API calls. The platform uses smart analytics to spot unusual or suspicious behavior, like a user logging in from a new or unexpected location, working at strange hours, or downloading large amounts of data quickly.

These could be signs of unauthorized access or potential security threats. When something looks suspicious, CloudEagle.ai quickly alerts your security team so they can respond immediately, which helps prevent data breaches and keeps your information safe.
Automated User Access Management
When a new employee joins your company, CloudEagle.ai automatically sets up their access to the apps they need based on their job role. This means they can start working right away without waiting for manual approvals or setups, saving time and avoiding mistakes.

When someone leaves the company or changes their job, CloudEagle.ai automatically removes their access. This stops old accounts from being misused by former employees or hackers and keeps your environment secure.

Know how Bloom & Wild streamlines employee onboarding and offboarding with CloudEagle.ai.
Just-In-Time (JIT) Access
Instead of giving users full access all the time, CloudEagle.ai offers Just-In-Time access. This means users get access only when they need it for a limited time, such as for a specific task or project. After that time, the access expires automatically. This reduces the chances of users having unnecessary access that could be abused or stolen.
Role-Based Access Control (RBAC)
CloudEagle.ai uses role-based access control to give people access only to what they need for their job. For example, someone in finance won’t see tech team files, and vice versa. This “least privilege” approach means your sensitive data is better protected by limiting unnecessary access and reducing the risk of accidental data leaks or intentional misuse.

Regular Access Reviews
As people change roles or finish projects, their access needs to be updated. CloudEagle.ai makes it easy to set up regular reviews where security and IT teams check if users still need the permissions they have. This keeps access tight and compliant with security rules, avoiding the problem of users collecting too many permissions over time.

Detailed Audit Trails and Compliance Reporting
CloudEagle.ai carefully records everything related to user access, such as logins, changes, and security alerts. These records help your team investigate any security problems and prove to auditors that your company follows important rules like GDPR or HIPAA. It also creates simple and clear reports to easily show your security efforts to regulators and stakeholders.

Shadow IT Detection and Control
Sometimes employees use cloud apps without approval, which is called shadow IT. These unauthorized apps can introduce security risks because they aren’t monitored or controlled.

CloudEagle.ai scans your cloud environment continuously to find these apps and user activities that aren’t officially allowed. Once found, you can block or manage these apps to reduce security risks and keep everything under control.
Self-Service App Catalog
To make life easier for employees and IT teams, CloudEagle.ai offers a self-service app catalog. Employees can independently browse the approved cloud apps and request access when they need it.
This reduces the number of access-related requests to IT helpdesks, speeds up access approvals, and improves user satisfaction. IT teams still stay in control by setting up approval processes so every access request follows company policies.
Privileged Access Management
CloudEagle.ai makes managing privileged accounts easier by automating the assignment of elevated access, ensuring that only authorized users can access critical systems such as AWS and NetSuite. This automation helps lower the risk of unauthorized activities.
With continuous monitoring and automated management, CloudEagle.ai strengthens security and compliance while easing administrative tasks and reducing human errors.
Flexible Policy Enforcement and Risk-Based Controls
CloudEagle.ai lets you create smart access policies that adjust based on the situation. For example, if someone tries to access sensitive data from a new device or from outside the office network, the platform can require extra verification steps or block access altogether. This helps protect your cloud data without making normal work harder for employees.
To know how to automate employee onboarding and offboarding with streamlined provisioning and deprovisioning workflows, take a look at this testimonial from Alice Park at Remediant. She shares how CloudEagle.ai helped her simplify and improve these processes.
Conclusion
A Cloud Access Security Broker (CASB) is crucial for securing the cloud-driven environments that enterprises rely on today. By delivering enhanced visibility, ensuring compliance, safeguarding data, and detecting threats, CASB solutions empower enterprises to confidently embrace cloud technology while effectively managing risks.
Platforms like CloudEagle.ai exemplify how modern CASB solutions can simplify complex cloud security challenges by providing comprehensive access management and real-time monitoring across hundreds of cloud applications.
As cloud adoption continues to accelerate, having a dependable CASB becomes essential for maintaining a secure, compliant, and well-managed cloud infrastructure.
Ready to elevate your cloud security?
Schedule a demo with CloudEagle.ai and discover how to strengthen your enterprise’s security posture.
FAQs
1. Is CASB a firewall?
No, a cloud access security broker (CASB) is not a firewall. While both enhance security, a CASB specifically focuses on securing cloud applications and data by providing visibility, control, and threat protection. Firewalls mostly protect traditional network traffic.
2. Which is an example of CASB?
Examples of cloud access security broker (CASB) vendors include Microsoft Defender for Cloud Apps, Netskope, McAfee MVISION Cloud, and Cisco Cloudlock. These cloud access security broker solutions help enterprises monitor and secure their cloud environments.
3. What is the best practice of CASB?
Best practices for CASB include aligning CASB with business security policies, integrating it with identity and access management (IAM) and data loss prevention (DLP) tools, monitoring and controlling shadow IT, and regularly updating policies to address new threats.
4. What is the difference between DLP and CASB?
Data loss prevention (DLP) focuses on protecting sensitive data from being lost or leaked anywhere in the network. A cloud access security broker (CASB), on the other hand, extends security specifically to cloud applications by providing visibility, access control, and threat protection for cloud data.
5. What is the difference between a secure web gateway and CASB?
A secure web gateway (SWG) protects users from internet-based threats by filtering web traffic, while a cloud access security broker (CASB) focuses on securing cloud applications and data. CASBs provide granular controls over cloud services, whereas SWGs manage broader internet traffic risks.

%201.svg)








.avif)




.avif)
.avif)




.png)









