HIPAA Compliance Checklist for 2025

In today’s SaaS-first world, enterprises rely on a wide array of applications, cloud services, and data systems. Safely managing who has access to these resources presents a significant challenge.
Without a strong identity governance framework, enterprises struggle to effectively manage access risks, leaving them vulnerable to unauthorized activity, data breaches, and compliance violations.
According to CloudEagle.ai’s latest IGA report, 28% of enterprises have suffered major security incidents caused by overprivileged access.
Thus, it becomes essential for enterprises to adopt an identity governance framework. This framework determines who can access which resources, enforces security policies, and regularly reviews access to prevent issues like unauthorized use or data leaks.
Let’s explore what an Identity Governance Framework is and how it can help you build strong security measures in your enterprise.
TL;DR
- An Identity Governance Framework sets rules and tools to manage digital identities and control access to company resources securely.
- It handles the full lifecycle of identities, from creation and role updates to timely removal, while enforcing security policies.
- Enterprises use it to comply with laws like GDPR and HIPAA, protect data, and reduce risks from excessive or outdated access.
- Key components include managing user lifecycles, role-based permissions, access reviews, policy enforcement, and automation.
- Best practices involve aligning governance with business goals, applying least privilege and Zero Trust, automating workflows, auditing regularly, and training employees.
What is an Identity Governance Framework?
An identity governance framework is a structured set of policies, processes, and technologies designed to manage and control digital identities and their access rights within an enterprise. It ensures that the right individuals have the appropriate access to the right systems and data at the right time, and for the right reasons.
This framework is sometimes known as an identity and access management governance framework, as it overlaps with IAM strategies but places a stronger emphasis on governance, compliance, and policy enforcement.
At its core, an identity governance framework aims to provide an enterprise with better visibility and control over who can access critical resources, reducing risks related to unauthorized access, insider threats, and data breaches.
It automates key functions such as user provisioning, role management, access certifications, privileged access controls, and audit reporting. By doing so, it supports regulatory compliance requirements and strengthens cybersecurity.
Why Enterprises Need an Identity Governance Framework?
Enterprises face increasing challenges in managing access to sensitive data and critical systems. An identity governance framework is essential because it helps enterprises control, monitor, and secure access efficiently while meeting regulatory demands. Here’s why it’s vital:
Compliance With Regulations And Industry Standards
Laws like GDPR, HIPAA, and SOX require strict control over who can access sensitive information. An identity governance framework enforces policies that help companies meet these legal requirements and provide clear audit trails to demonstrate compliance, avoiding penalties and reputational harm.
Protecting Sensitive Data From Insider And External Threats
Overprivileged users or dormant accounts present risks that attackers may exploit. The framework applies the principle of least privilege, ensuring users only get access needed for their roles, and continuous monitoring to reduce insider threats and data breaches significantly.
Reducing Risks Tied To Excessive Or Orphaned Accounts
Without governance, users accumulate unnecessary permissions, or accounts remain active after they leave, increasing security risk. The framework automates access reviews, deactivates unused permissions, and regularly certifies access, keeping rights accurate and safe.
Enabling Scalability In Large Enterprises
In a large enterprise, manual management of thousands of users and frequent role changes is impossible. Identity governance frameworks automate onboarding, offboarding, access changes, and audits, making it easier to manage access securely and effectively at scale.
Improving Operational Efficiency And Security Posture
Automation reduces manual errors and IT workloads by handling access requests, certifications, and policy enforcement. This boosts productivity and sharpens the enterprise's ability to detect and respond to risky access activities promptly.
Core Components of an Identity Governance Framework
An effective identity governance framework consists of several core components working together to secure and manage digital identities throughout their lifecycle. These components ensure that access is granted appropriately, policies are enforced, and compliance is maintained.
Identity Lifecycle Management (Provisioning And Deprovisioning)
This component manages the entire lifecycle of user identities, from onboarding and provisioning access to modifying permissions during role changes, to timely deprovisioning when users exit. Automating these processes minimizes risks from orphaned or excessive accounts.
Learn how Bloom & Wild streamlined employee onboarding and offboarding with the help of CloudEagle.ai.
Role-based And Attribute-based Access Control
Access permissions are granted based on predefined user roles (RBAC) or attributes (ABAC) such as department, location, or job function. This helps enforce least privilege and align access rights with business needs securely and efficiently.
Access Reviews And Certifications
Regular reviews and certifications validate that users’ access rights are still appropriate. This continuous monitoring helps detect and remediate excessive access, ensuring compliance with policies and regulations.
Policy And Workflow Management
Defines and automates the business rules and approval processes that govern identity and access operations—such as access requests, role assignments, and segregation of duties—to maintain governance and reduce manual errors.
Audit And Compliance Reporting
Provides detailed records and reports of identity and access activities to support compliance audits, demonstrate regulatory compliance, and identify potential security risks through continuous monitoring.
How an Identity Governance Framework Works
Managing who can access enterprise resources requires a structured and automated approach to identity and access control. An IGA Framework achieves this by:
Establishing Policies And Access Rules
Enterprise begins by defining clear policies about who should have access to specific systems and data. These policies are based on user roles, attributes like department or location, and risk profiles to ensure only authorized users gain the right level of access aligned with business needs and security requirements.
Automating User Lifecycle Events
The framework automates identity provisioning, role changes, and deprovisioning to eliminate delays and human errors common in manual processes. Automation ensures users get timely access when they join or change roles and that unauthorized access is promptly revoked when users leave.
Monitoring And Detecting Risky Access Behavior
Continuous monitoring tools flag unusual or high-risk behaviors such as privilege escalations, dormant or orphaned accounts, and policy violations. This proactive detection enables security teams to respond swiftly and prevent potential breaches or misuse.
Integrating With Iam, Pam, And Hr Systems
Seamless connection with Identity and Access Management (IAM), Privileged Access Management (PAM), and Human Resources (HR) systems ensures identity data accuracy. This integration guarantees that access rights remain correctly aligned with employee status and enterprise roles, supporting consistent governance and compliance.
What is the Difference Between IAM and IAG?

Best Practices for Implementing an Identity Governance Framework
Implementing a successful Identity Governance Framework requires aligning it closely with business needs, security objectives, and regulatory compliance. To build a strong, scalable, and effective identity governance system, enterprises should follow these best practices:
Align Governance Policies With Business Goals And Compliance Needs
Successful identity governance starts by aligning policies with the broader business objectives and regulatory requirements like GDPR, HIPAA, and SOX. Engaging stakeholders across departments such as IT, HR, legal, and business units ensures that policies reflect real-world roles, workflows, and risk areas.
By incorporating compliance mandates early in the governance strategy, enterprises reduce the risk of penalties and reputational damage. Clear, adaptable policies also help maintain trust with customers and partners. This foundation supports ongoing governance that grows with the company’s evolving needs and regulatory landscape.
Apply Least Privilege And Zero Trust Principles
The principle of least privilege is essential: users must have the minimum access necessary to perform their roles, reducing exposure to insider threats and data breaches. Implementing Zero Trust means continuously validating every access request, regardless of a user’s location or past behavior, and monitoring user activities for anomalies.
Together, these principles enhance security by shrinking the attack surface and preventing privilege creep—users gradually accumulating excessive permissions. Zero Trust also strengthens cybersecurity posture with layers of verification, making unauthorized access more difficult for attackers and malicious insiders.
Automate Access Provisioning And Certification Processes
Automated access provisioning and deprovisioning speed up user onboarding and ensure timely removal of access when roles change or employees leave. Automated access certification campaigns regularly verify and update user permissions, keeping access rights accurate and aligned with current roles.
This automation not only improves operational efficiency but also supports compliance by generating audit-ready records that document access rights over time. It frees up IT and security teams to focus on strategic tasks while minimizing manual errors and reducing risks from outdated permissions.
Conduct Periodic Audits And Role Reviews
Regular audits and access role reviews are necessary to identify excessive privileges, orphaned accounts, and violations of access policies early on. These reviews help maintain least privilege, reduce risk, and demonstrate compliance with internal policies and external regulations.
Using identity analytics during audits can provide deeper insight into access trends, helping identify potential risks faster. Timely remediation of issues uncovered during reviews strengthens governance and improves the enterprise’s overall security posture.
Train Employees On Governance And Access Policies
Employee education is a key pillar of successful identity governance. Providing clear training programs ensures users understand governance policies, their own responsibilities, and best security practices. Educated employees are more aware of the risks associated with improper access and more likely to follow protocols.
Common Challenges in Identity Governance
Managing identity governance is critical but complex. Enterprises face several common challenges, especially in today’s hybrid IT environments combining on-premises and cloud systems:
Complexity In Managing Hybrid It Environments
Hybrid environments mix traditional on-premises directories with multiple cloud identity services (like Azure AD, Okta, Salesforce). This creates fragmented identity silos, inconsistent access controls, and difficulty enforcing unified policies. Managing identities and access consistently across diverse systems and clouds is a major challenge.
Balancing Security With User Productivity
Strict security can slow users down or cause frustration, but lax policies increase risk. Finding the right balance between strong access controls and seamless user experience, including single sign-on and quick onboarding/offboarding, requires careful planning and effective tools.
Handling Role Explosion And Policy Conflicts
As enterprises grow, the number of roles and permissions can explode, creating complex policy overlaps and conflicts. This leads to access sprawl and difficulties in ensuring least privilege access. Managing and simplifying roles, entitlements, and policies is an ongoing challenge.
Ensuring Continuous Compliance Across Jurisdictions
Enterprises operating globally must comply with varying regulations (GDPR, HIPAA, etc.) that demand different access control and auditing requirements. Maintaining continuous compliance with these diverse rules while managing access at scale requires automation and comprehensive monitoring.
Role of CloudEagle.ai in Identity and Access Management
CloudEagle.ai is an advanced SaaS management and access governance platform that helps IT and security teams easily see, control, and automate user access across hundreds of SaaS apps.
It connects with over 500 apps and works smoothly with your current IAM, SSO, and security tools, so you can secure your cloud environment without big changes.
The platform automates tasks like onboarding and offboarding users, access reviews, and license management, ensuring that the right people have the right access at the right time. With clear insights and real-time monitoring, CloudEagle.ai makes access governance simple, keeps your data safe, and helps maintain compliance.
Here’s how the platform simplifies IAM:
Comprehensive Visibility into SaaS and AI Applications
Many enterprises don’t have the exact number of applications used by their employees. While some of these applications are officially approved by IT, a significant number are adopted independently by teams or individuals without formal supervision.
This phenomenon is known as “Shadow IT,” which introduces serious security vulnerabilities and compliance risks, in addition to driving up operational costs.

CloudEagle.ai addresses this challenge by automatically discovering every SaaS application being used across the enterprise. It aggregates critical data, such as login patterns, spending details, and user activity, into a unified, easy-to-navigate dashboard.
This level of visibility enables IT teams to identify hidden or redundant applications, remove blind spots in security, and consolidate software tools, all of which contribute to stronger governance over the company’s entire software portfolio.
Seamless Automated Onboarding and Offboarding
Manual onboarding and offboarding processes are often slow, prone to errors, and introduce security risks. CloudEagle.ai automates these identity touchpoints, guaranteeing that new employees receive access to all necessary applications and tools immediately on their first day.

Equally critical, CloudEagle.ai handles offboarding by promptly revoking access to all resources as soon as an employee departs. This automatic access removal eliminates security gaps, prevents data leaks from former employees, and ensures the enterprise remains audit-ready at all times.

Know this inspiring story of how JoVe streamlined employee onboarding and offboarding with CloudEagle.ai.
Continuous Access Reviews and Compliance-Ready Reporting
Regulations such as SOC 2, GDPR, and ISO require enterprises to perform regular reviews of user access to sensitive systems. Traditional manual access reviews can be inefficient, error-prone, and usually occur infrequently, leaving security gaps in the interim.

CloudEagle.ai provides an AI-powered, continuous access review system that automates this critical function. The platform generates audit-ready reports instantly, reducing compliance preparation time and ensuring that permissions remain current without outdated or excessive access. As a result, organizations can confidently demonstrate compliance and reduce the risk of security breaches.
Enforcement of Least Privilege Access Principles
Over time, employees often accumulate more access privileges than necessary, including sensitive admin or super-admin rights. This “privilege creep” elevates the risk of insider threats, accidental data exposure, and compliance failures. CloudEagle.ai continuously monitors user permissions and dynamically adjusts access to ensure employees retain only the rights needed for their roles.
According to CloudEagle.ai’s IGA report, Datta Junarkar, CIO, Maritime, Boeing, says:
“Overprivileged access is a compliance nightmare waiting to happen. If employees keep unnecessary permissions, it’s only a matter of time before sensitive data ends up in the wrong hands. Regulations like SOC 2 and GDPR demand strict access controls, but without regular reviews, companies are flying blind, and that’s a costly risk to take.”
By enforcing strict least-privilege access policies, CloudEagle.ai helps organizations safeguard confidential information, reduce the potential for malicious activity or mistakes by internal users, and maintain compliance with various security and regulatory standards. This approach balances security with usability, keeping access minimal yet sufficient.
Simplified and Centralized Compliance Management
Compliance management across hundreds of SaaS applications is a complex undertaking, especially when approvals and policies are scattered across emails, spreadsheets, and ticketing systems. CloudEagle.ai simplifies this by centralizing governance policies, approval workflows, and audit logs in a single, intuitive platform.

Automation ensures that access controls are consistently applied according to corporate policies, while detailed logs provide transparent evidence for auditors. This centralized approach reduces workload for IT and compliance teams and ensures the business remains fully prepared for regulatory reviews without last-minute scrambles.
Effective Management of Privileged Access
Excessive privileged access poses one of the most significant security challenges for modern enterprises. CloudEagle.ai gives IT teams full visibility into who has administrative or elevated access across all SaaS applications.
The platform flags unusual or excessive privilege assignments and automatically removes unnecessary rights. By tightening control over privileged accounts, CloudEagle.ai helps organizations mitigate insider threats, prevent accidental data exposure, and pass rigorous compliance audits with ease.
Role-Based Access Control and Management
Rather than managing application access on a case-by-case basis, CloudEagle.ai enables enterprises to define role-based access policies aligned with departments, seniority levels, or job functions. For example, a sales manager might automatically receive access to Salesforce, Gong, and Zoom, while a new engineer gets development tools right from day one.

Once these role-based policies are defined, CloudEagle.ai enforces them consistently across the organization, eliminating errors, reducing IT workload, and improving the employee experience with faster access to the tools they need.
Just-in-Time Temporary Access Provisioning
Temporary workers, contractors, and project-based staff often have access that extends beyond the duration of their engagement, creating needless security risks. CloudEagle.ai addresses this by enabling just-in-time access, a system where permissions are granted only when necessary and expire automatically once the task or contract concludes.
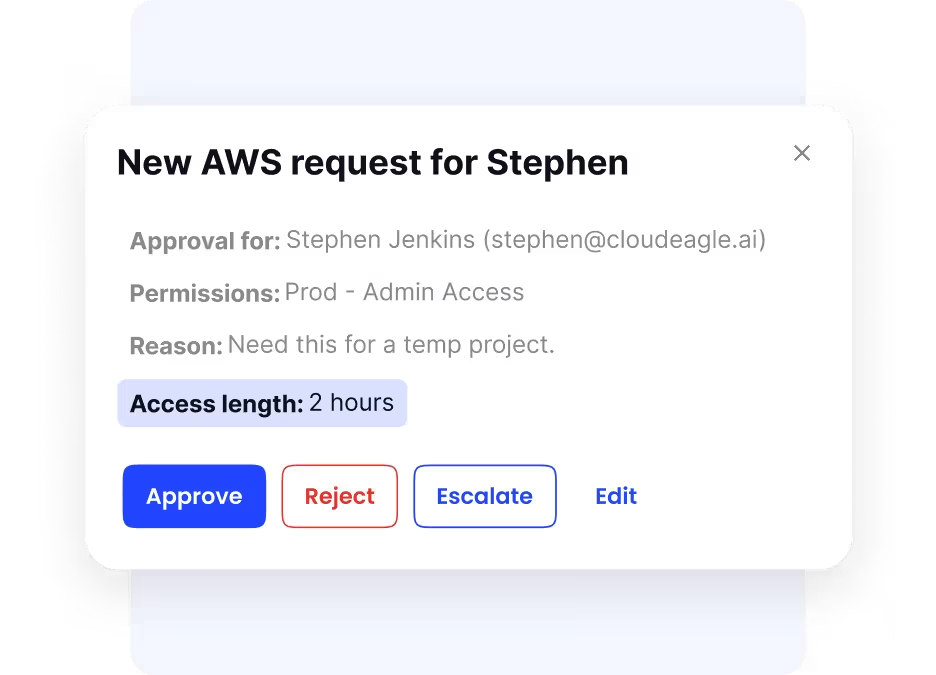
Unified Employee Application Catalog and Self-Service Portal
Employees frequently face challenges discovering which applications are available and how to request them, resulting in scattered requests through emails, chats, and ticketing systems. CloudEagle.ai resolves this by offering a centralized, self-service app catalog where employees can easily browse approved tools and submit access requests.
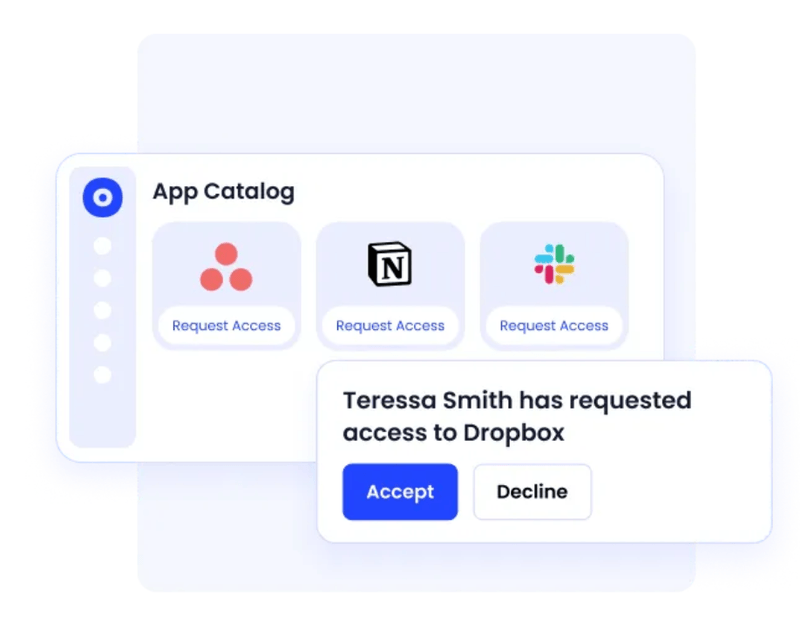
The platform automates approval workflows, routing requests appropriately while providing IT teams with clear visibility into access decisions. This results in faster access fulfillment, happier employees, and a standardized, compliance-supporting access management process.
Hear from Alice Park at Remediant, who shares her firsthand experience with CloudEagle.ai. She highlights how the platform transformed their access management by streamlining onboarding and offboarding processes, resulting in enhanced security and operational efficiency for their team.
Conclusion
An effective identity governance framework is crucial for enterprises to secure digital assets and comply with industry regulations. It provides a clear system to manage user identities, control access, and enforce rules tied to business goals.
By automating the identity lifecycle, access reviews, and continuous monitoring, enterprises significantly reduce the risks of unauthorized access and insider threats. Automation ensures that user access is granted based on current roles and is promptly revoked when no longer necessary, minimizing security gaps.
While challenges like managing hybrid IT environments and balancing security with productivity exist, a robust identity governance framework enables enterprises to address these complexities confidently.
CloudEagle.ai supports this journey by providing innovative solutions that simplify and streamline identity and access governance, helping businesses maintain secure, compliant, and efficient operations in today’s dynamic digital landscape.
Nidhi Jain, CEO of CloudEagle.ai, believes that “The most successful IAM implementations leverage AI to accelerate human decision-making. Enterprises that embrace this partnership model see both enhanced security and improved operational efficiency.”
Are you ready to enhance your governance process?
Schedule a demo with CloudEagle.ai and learn how to strengthen access control and compliance smoothly in your enterprise.
FAQs
1. What is the identity governance model?
The identity governance model is a structured approach sets policies, processes, and tools to manage digital identities and their access, ensuring the right people have the right access at the right time for security and compliance.
2. What are the 4 pillars of the data governance framework?
The four pillars of a data governance framework are:
- Data Quality: Ensuring data is accurate and reliable.
- Data Management: Organizing and handling data efficiently.
- Data Policies & Compliance: Following rules and regulations.
- Data Security & Privacy: Protecting data from misuse.
3. What are the three models of governance?
The three models are:
- Centralized: One central authority makes decisions.
- Decentralized: Multiple units share authority.
- Federated: A mix of central control with local execution.
4. What is the identity and access governance framework?
The identity and access governance framework manages who can use systems and data. It combines tools to handle user accounts, control access, check compliance, and automate workflows to keep data safe and provide proper access across the enterprise.
5. What are the 4 C's of governance?
The 4 C’s of governance refer to:
- Control: Setting rules to guide activities.
- Compliance: Following laws and standards.
- Culture: Promoting values and ethics.
- Communication: Sharing clear and open information.

%201.svg)








.avif)




.avif)
.avif)




.png)









