HIPAA Compliance Checklist for 2025

Many enterprises rely on IAM platforms like Okta or SailPoint to manage user access, but these tools often struggle with the complexities of modern, identity-first environments. Traditional IAM systems were built for simpler, on-premise infrastructures, focusing primarily on authentication and user management.
What enterprises need is a stronger approach to Identity Governance and Administration (IGA). CloudEagle.ai complements existing IAM tools by enhancing their capabilities, like automating access management, simplifying approval workflows, enforcing policies, and flagging risky access in real-time.
Let’s explore why modern enterprises are choosing CloudEagle.ai to strengthen their IGA practices, working alongside platforms like Okta and SailPoint to drive more comprehensive access governance.
TL;DR
- CloudEagle.ai lets IT leaders manage access effortlessly, ensuring it's granted when needed and revoked when not, improving security and reducing risks.
- With 500+ integrations, CloudEagle.ai automates access management across all apps, saving time and cutting down errors by applying consistent security policies.
- It automates employee access, providing new hires with immediate access while swiftly removing permissions for ex-employees, speeding up the process and enhancing security.
- CloudEagle.ai’s Just-In-Time (JIT) access ensures users only have access as needed, minimizing unnecessary permissions and helping prevent security breaches.
- CloudEagle.ai automates access reviews based on role changes or risks, reducing review time by 80%.
What Is IGA?
Identity Governance and Administration (IGA) is a modern approach to securing access to systems and data. Instead of focusing on network firewalls, IGA ensures that only the right users can access the right resources, at the right time, and for the right duration.
IGA makes it easy for enterprises to maintain compliance, audit user access, and adapt quickly to changes like new employees, role shifts, or project needs. It ensures that only authorized users have access, preventing unauthorized access and minimizing potential security threats.
The Struggles IT Teams Face in Implementing IGA
While IGA is essential, many IT teams struggle to implement it effectively. Here’s why:
1. Data Spread Across Multiple Platforms: IT teams often lack a unified view of who has access to what, as data is dispersed across various systems, including emails, shared folders, collaboration tools, and SaaS apps, making it difficult to consistently manage and control permissions.
2. Fragmented Access Control: Managing access across various platforms that aren’t connected can lead to inconsistent access control policies. Without integration, enforcing a uniform security approach becomes challenging.
3. Legacy Tools: Many enterprises still rely on outdated security tools built for on-premise setups. These tools don’t work well in SaaS environments, leaving IT teams with limited options for automation and real-time monitoring.
4. Managing Identities at Scale: As companies grow, managing more users and apps becomes harder. IT teams often face delays in access provisioning, human errors, and potential security risks due to the lack of efficient systems.
Why is IGA Vital Today?
With employees accessing data from various locations and devices, managing who can access sensitive information is more challenging. SaaS platforms add complexity by storing data across multiple applications. As security shifts from physical boundaries to managing access, enterprises must focus on:
- Who has access? Ensuring only authorized users can access critical resources.
- What can they access? Granting access based on roles and responsibilities.
- How long do they need access? Providing time-bound access to reduce unnecessary permissions.
According to CloudEagle.ai’s IGA report, 85% of enterprises have not updated their identity governance processes. Enterprises that haven't implemented IGA need to do so, as it ensures the right people have the right access at the right time.

Gartner recognized CloudEagle.ai in its Light Identity Governance and Administration report for its advanced IGA capabilities.
The Identity Reality That Most It Teams Struggle With
Modern IT teams are under pressure to secure access across hundreds of SaaS apps, but most are still relying on manual identity governance processes. The result is a daily balancing act between security, compliance, and employee productivity, and it rarely works smoothly.
Here are the core issues IT leaders face:
1. Shadow IT: It occurs when employees use unapproved apps without IT’s knowledge. According to CloudEagle’s IGA report, 60% of SaaS and AI tools are used without IT’s oversight, creating major security risks and compliance problems. These hidden apps can expose sensitive data and make it harder to follow security policies.
2. Over-Privileged Access: Many employees keep access to sensitive systems after their roles change or they leave the company. This can lead to insider threats and make it harder to control who sees what data, leaving companies vulnerable to security breaches.
3. Manual Processes: Many companies still use systems that weren’t designed for modern SaaS environments. These slow, error-prone methods make it harder to manage access and ensure compliance, especially as enterprises grow.
4. High Risk of Human Error: With manual provisioning and deprovisioning processes in place, human error is inevitable. Whether it’s over-permissioned accounts, missed offboarding steps, or delayed access changes, these mistakes introduce security gaps that can easily turn into compliance violations or data breaches.
5. Poor Visibility: Lack of visibility is a major issue for IT teams still relying on spreadsheets and ticketing systems to manage access control. These outdated methods fail to provide real-time insights into who has access to what, making it difficult to detect and respond to risks quickly.
How Enterprises Approach IGA And The Challenges Of It?
Currently, many enterprises rely on traditional IAM tools like Okta, SailPoint, and Active Directory to manage user access. While these systems work for some use cases, they were never designed for modern, SaaS-first, and AI-driven environments.
While IDPs are crucial for authenticating users, they offer limited control and visibility over detailed permissions. This can cause over-privileged access and security risks. What works for small setups often fails as SaaS usage grows larger and more complex.
Here’s what a typical setup looks like, and where it falls short:
1. Inefficiency in Access Reviews: Manual access reviews are conducted quarterly or annually. This means enterprises often miss unauthorized or excessive access, increasing the risk of data breaches or compliance violations. Automated access reviews are crucial for faster remediation.
2. Fragmented Systems: Most enterprises use a patchwork of systems to manage identities, including spreadsheets, manual ticketing, and multiple IAM platforms. This leads to confusion, inefficiency, and difficulty in tracking who has access to what.
3. Slow Response Times: With manual processes, onboarding and offboarding employees can take days or even weeks. This results in delayed access for employees and, more critically, prolonged access for former employees, increasing the risk of unauthorized data access.
4. Shadow IT and Compliance Risks: Without centralized visibility, employees often bypass IT to use unauthorized apps, creating security risks. It becomes hard to track this manually and control which apps are in use, leading to compliance violations and potential breaches.
5. Spreadsheet-Driven Tracking: App access rights are often tracked in spreadsheets or ticketing systems. These static records can’t provide real-time visibility, making it difficult to know who has access to what at any given moment.
6. Hidden Costs with IDPs: Identity Providers like Okta or Azure AD help with authentication, but pushing every app behind them often requires expensive enterprise plans. Even then, IDPs don’t cover non-SSO apps, license reclamation, or shadow IT.
This patchwork approach leaves enterprises exposed to security risks, wasted spend, and compliance failures. As SaaS adoption accelerates, manual IGA simply can’t keep up, making automation a necessity, not a luxury.
Why Relying Solely on IAM Platform Isn't Feasible for IGA?
IAM platforms like Okta and SailPoint are great for user management, but they fall short when it comes to handling modern Identity Governance at scale.
Here’s why:
1. Different Focus Areas: IAM primarily focuses on managing who can access what systems and apps, handling authentication and authorization. IGA goes beyond this by enforcing access control policies on whether users should have access, ensuring compliance, and managing risk.
2. Limited to SSO and Authentication: IAM systems focus primarily on SSO and authentication, not on the broader needs of IGA. While they are great for access management, they lack robust features for managing access reviews, governance workflows, and automated compliance.
3. Disconnected from SaaS Ecosystems: IAM platforms are often disconnected from SaaS tools, making it hard for IT teams to gain visibility into shadow IT or unauthorized app usage. CloudEagle.ai’s deep integrations with SaaS apps provide a more comprehensive view, while also automating governance tasks in real time.
4. Manual Workflow Integration: IAM tools typically can’t automate entire workflows (like access reviews, license harvesting, and renewals). CloudEagle.ai seamlessly integrates these workflows and uses AI to optimize access controls across the enterprise, while IAM platforms are largely static and require significant manual effort to manage.
5. Access Lifecycle Management: While IAM handles user provisioning and deprovisioning, IGA continuously reviews and certifies access rights to prevent privilege creep and enforce segregation of duties, reducing insider threat risks.
Let’s check out what Nidhi Jain, CEO and Founder, CloudEagle.ai, shared from her experience:
“I’ve seen it happen too many times: an employee changes roles, yet months later, they still have admin access to systems they no longer need. Manual access reviews are just too slow to catch these issues in time. By the time someone notices, privilege creep has already turned into a serious security risk.”
6. Complementary Technologies: IAM forms the operational foundation for identity management, while IGA builds on it by adding essential governance and compliance functions. Enterprises need both to achieve a secure, compliant, and well-governed identity environment.
We can conclude, IAM ensures "who can access," but IGA ensures "who should access," making sole reliance on IAM inadequate for full identity governance and administration needs.
Why Choose CloudEagle.ai for Automating IGA End-to-End?
More than 50% of organizations consider automation capabilities a critical factor when selecting new IGA solutions. If you’re adopting a new solution, it's essential to know that CloudEagle.ai leverages automation to simplify Identity Governance.
Further, CloudEagle.ai doesn’t replace your Identity Provider (Okta, Azure AD, or Ping); it enhances it by covering the entire identity lifecycle. With Generative AI, SaaSPilot, and 500+ SaaS integrations, it turns identity governance into a zero-touch, automated process.
According to CloudEagle.ai’s IGA report, Chetna Mahajan, Global CDO & CIO, Webflow, shares:
“IAM is often the most underfunded yet mission-critical part of security. But those taking a proactive approach, starting with automation and AI-driven governance, are not just reducing risk, they’re unlocking efficiency and long-term cost savings.”
Here’s how the platform automates IGA:
1. Full SaaS Discovery
CloudEagle.ai automatically detects every application in use, including unmanaged SaaS and Shadow AI tools that never touch your IDP. CIOs and CISOs gain total visibility into the SaaS stack, closing blind spots that introduce security and compliance risks.
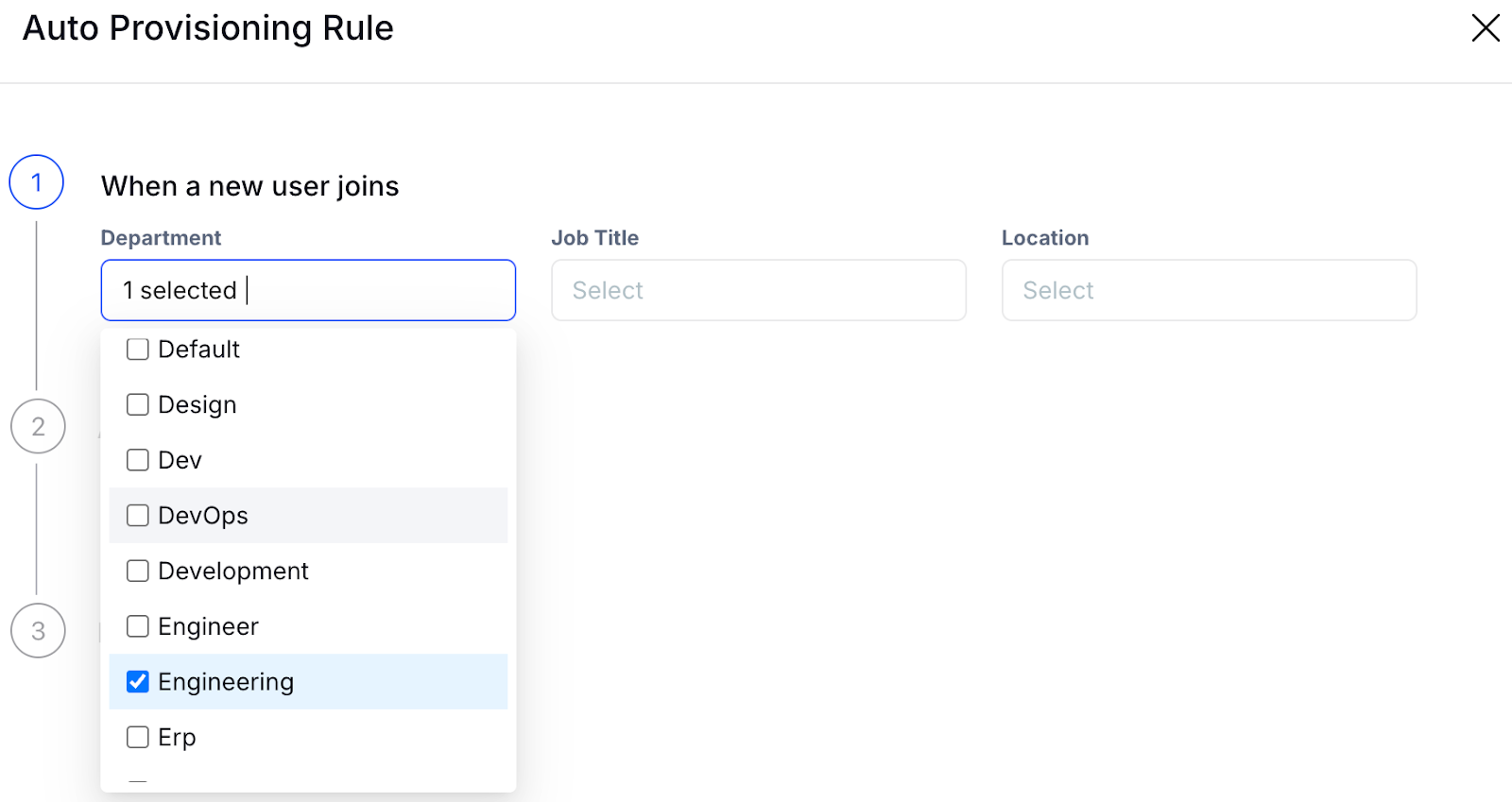
2. Automated User Provisioning And Deprovisioning
CloudEagle.ai automates the entire user lifecycle management, from onboarding to offboarding. When a new employee is added or an existing employee changes roles, CloudEagle.ai automatically provisions or deprovisions access across various systems and applications.
How CloudEagle.ai does this:
- Automates onboarding and offboarding workflows with zero manual effort.
- Role- and location-based automation ensures correct access.
- Integrates with 500+ SaaS apps, keeping license pools updated.
- Speeds up employee productivity with instant access or deprovisioning.
- Reduces security risks and compliance gaps with timely access revocation.
When a new employee joins, CloudEagle.ai automatically creates user accounts and assigns appropriate access permissions across multiple SaaS applications based on the role defined.
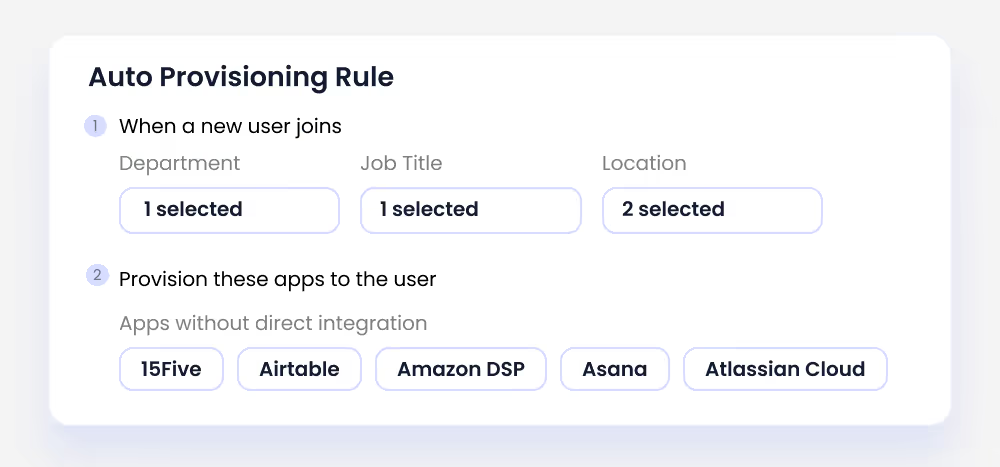
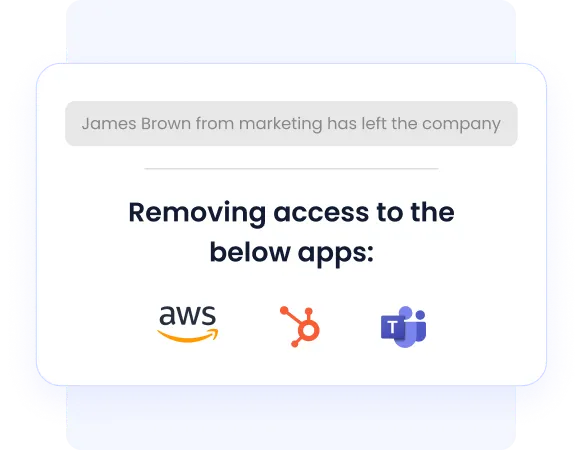
Similarly, upon an employee’s exit, their access is instantly revoked, ensuring no lingering permissions.
Listen to Alice Park at Remediant, where she explains how the company streamlined onboarding and offboarding using CloudEagle.ai.
3. Role-Based Access Control (RBAC)
With CloudEagle.ai, you can implement role-based access control (RBAC) to manage user access based on their job functions, rather than assigning permissions individually.
How CloudEagle.ai does this:
- Centralizes role-based permissions for streamlined governance.
- Assigns access dynamically based on role, team, division, or location.
- Prevents over-provisioning via granular role definitions.
- Supports hybrid IT and SaaS environments with consistent controls.
- Simplifies audit and compliance with enforced RBAC policies.
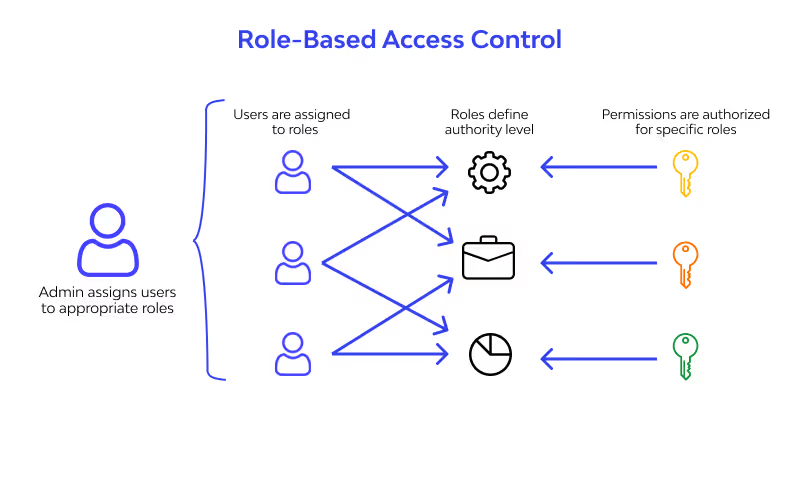
This approach simplifies access management and ensures users have only the minimum permissions necessary for their tasks.
4. Policy-Driven Access Management
With CloudEagle.ai, access permissions are governed by enterprise policies. These policies can be dynamically adjusted to meet security, compliance, and operational needs.
How CloudEagle.ai does this:
- Enforces enterprise access policies automatically and continuously.
- Adapts to changes in business needs and security requirements.
- Provides transparency and audit trails for policy enforcement.
- Minimizes manual errors and governance bottlenecks.
- Supports complex policy workflows across SaaS ecosystems.
Know how Treasure Data enhanced access management and reporting with CloudEagle.ai.
5. Real-time Monitoring And Reports
CloudEagle.ai provides real-time monitoring and detailed reporting on user activities, making it easy for enterprises to track access and detect anomalies immediately.
How CloudEagle.ai does this:
- Offers unified dashboards with real-time SaaS application metrics.
- Alerts for unauthorized access, orphaned accounts, or policy breaches.
- Simplifies audit with detailed logs and automated report generation.
- Enables proactive risk management and incident response.
- Provides actionable insights for identity and access teams.
Continuous monitoring helps identify unauthorized access attempts, over-provisioning, or other suspicious behavior, allowing enterprises to act quickly to mitigate risks.

6. Self-Service App Catalog
CloudEagle.ai includes a self-service app catalog, using which users can request access to the applications they need based on their role and job requirements.
How CloudEagle.ai does this:
- Centralized catalog for employees to request and gain app access.
- Automated approvals with built-in compliance and security checks.
- Role-based visibility reduces shadow IT and unauthorized usage.
- Speeds up provisioning while maintaining control and scalability.
- Provides audit-ready logs, simplifying compliance reporting.

This reduces the administrative burden on IT teams and ensures that users have immediate access to the tools they need while maintaining security and compliance standards.
Know how a Gen AI company streamlined SaaS access provisioning using CloudEagle.ai's self-service app catalog.
6. Automated Access Reviews
According to CloudEagle.ai’s IGA report, 95% of organizations are still using manual approaches for access reviews.

However, there is a better solution. When you use CloudEagle.ai, automating regular access reviews becomes a breeze.
How CloudEagle.ai does this:
- Automates scheduled and event-triggered access reviews.
- Flags high-risk, orphaned, or over-privileged accounts instantly.
- Helps maintain least privilege access continuously.
- Reduces audit preparation time significantly.
- Enables a proactive security governance posture.

This helps ensure users retain only the access they need. App access reviews can be scheduled at defined intervals or triggered by significant changes in user roles or permissions. It helps maintain compliance, prevents over-provisioning, and reduces the risk of unauthorized access.
5. Self-Service App Access Requests: Instead of waiting on IT tickets, employees can request apps directly in Slack or Teams. CloudEagle.ai validates policies, automates approvals, provisions access, and logs every action for compliance, turning access into a fast, seamless experience.

6. Compliance Automation
According to reports, organizations that use automated IGA see up to a 60% reduction in audit preparation time and experience significantly lower compliance penalties.
To keep your enterprise compliant, CloudEagle.ai helps automate compliance reporting and auditing. It supports standards like SOC 2, ISO 27001, GDPR, and more by providing built-in reports and audit trails, ensuring your IGA policies are aligned with regulatory requirements.
How CloudEagle.ai does this:
- Automates compliance reporting aligned with leading frameworks.
- Accelerates audit readiness with AI-driven evidence collection.
- Ensures continuous policy adherence and automated enforcement.
- Provides transparency to stakeholders with real-time compliance dashboards.
- Reduces risks of penalties through up-to-date governance.
7. Complete SaaS Stack Integration for Total Visibility
As enterprises use over 400 SaaS applications on average, it becomes harder to track who has access to what. CloudEagle.ai simplifies this by seamlessly connecting with over 500+ SaaS applications, so you get a complete view of user access across all platforms, whether they are integrated with your Identity Provider (IdP) or not.
The platform eliminates the need for manual data entry by automatically syncing your tech stack. This ensures your access control policies are applied consistently across your enterprise, making it easier to manage security without any blind spots.
8. Scalable to Meet Your Growing Needs
As your enterprise grows, managing user access becomes more complex. CloudEagle.ai scales with your business, whether you're a small company or a large enterprise. From hundreds of employees to thousands of non-human identities like bots and APIs, CloudEagle.ai keeps your identity governance efficient and secure.
Sebastian Rohr, Senior Advisor, KuppingerCole Analysts, points out:
“As GenAI agents and machine-to-machine interactions become more prominent, enterprises must move beyond human-centered security frameworks to tackle the risks posed by non-human identities.”
Discover how automating employee onboarding and offboarding with CloudEagle.ai can benefit your enterprise in this testimonial from Alice Park at Remediant.
Conclusion: Embrace Identity-First Security with CloudEagle.ai
As enterprises grow and their IT systems become more complex, managing identity and access manually isn’t enough. To tackle the challenges of modern identity governance, IT leaders are turning to automation, with CloudEagle.ai leading the way.
CloudEagle.ai automates Identity and Governance Administration (IGA), improving security, ensuring compliance, and easing the workload for IT teams. With real-time monitoring, AI-driven insights, and automated user access management, it keeps things secure and streamlined.
By automating IGA, IT leaders can keep their enterprise secure, efficient, and compliant, freeing up time to focus on strategic initiatives rather than getting bogged down by manual processes.
Ready to optimize your IGA? Schedule a demo with CloudEagle.ai today.

%201.svg)









.avif)




.avif)
.avif)




.png)









