HIPAA Compliance Checklist for 2025

Nearly 1 in 2 employees still hold excessive privileges, a risk that opens the door to insider threats, failed audits, and costly breaches. Manual reviews and spreadsheets simply can’t keep pace with today’s dynamic access sprawl.
That’s why access certification matters.
According to CloudEagle’s 2025 IGA Report, privilege creep remains one of the most overlooked identity governance challenges.
In this guide, we’ll break down the benefits, process, components, and best practices of user access certification, and how enterprise platforms make governance scalable and audit-ready.
TL;DR
- Access certification is the process of reviewing and validating user permissions to ensure they’re still appropriate, secure, and compliant with policies and regulations.
- Key benefits include audit readiness, stronger security through least privilege, reduced insider threats, and better visibility into user access across the enterprise.
- The process involves mapping entitlements, assigning reviewers, validating access, remediating issues, and documenting decisions, often supported by IAM/IGA platforms.
- Best practices: automate recurring reviews, involve business managers, apply risk-based certification, track remediation, and continuously improve.
- CloudEagle.ai simplifies enterprise-level user access with automation, dashboards, audit-ready reporting, and least-privilege enforcement, making access governance scalable and audit-friendly.
What is an Access Certification?
Access certification is the formal process of periodically reviewing user permissions to confirm they’re still appropriate for current roles and responsibilities. It’s not a one-time exercise but an ongoing control that keeps access aligned with business needs and security policies.
During these reviews, managers or auditors examine who has access to critical systems, identify unnecessary or outdated permissions, revoke what’s no longer needed, and document the decisions. This reduces risks like privilege creep, insider misuse, and compliance violations, while ensuring the organization can demonstrate control during audits.
At its core, access certification is a safeguard, making sure that the right people maintain the right level of access, and no one else does.
What are the Key Benefits of Access Certification?
The main benefits of access certification are improved compliance, stronger security, reduced insider risk, and greater visibility into user access. Together, these outcomes make it a cornerstone of identity governance.
1. Improved Compliance and Audit Readiness
Regular certifications create a documented record of who has access to what, helping organizations meet regulations like GDPR, HIPAA, and SOX. During audits, this evidence shows that controls are in place and working as intended.
2. Stronger Security Through Least Privilege
By enforcing the principle of least privilege, access certification ensures users only have the permissions required for their roles. This reduces unnecessary exposure and strengthens defenses against breaches.
3. Reduced Insider Threat and Privilege Creep
Unchecked access often leads to privilege creep, employees accumulating permissions as they move through roles. Certification helps detect and remove these excess rights, minimizing the risk of insider misuse or accidental data leaks.
4. Increased Visibility into User Access
Access reviews provide managers and security teams with a clear, up-to-date view of who can access sensitive systems and data. This visibility supports better decision-making and improves accountability across the organization.
How Does User Access Certification Works?
User access certification works as a systematic review cycle where organizations confirm that each employee, contractor, or third-party still has the right level of access.
The goal is simple: remove what’s unnecessary, keep what’s essential, and document the decisions to stay compliant and secure.
How the process works:
- Identification of access rights: The process begins by pulling a complete inventory of access rights across systems, apps, and databases. Every entitlement, no matter how small, is cataloged for review.
- Review and validation: Managers, application owners, or designated reviewers examine each user’s access.
They ask: Does this access still match the person’s role? Is it aligned with policy?
This step stops permission creep before it becomes a problem.
- Issue detection: Reviews often uncover problems such as:
- Overprivileged users with more access than necessary
- Orphaned accounts left behind after role changes or departures
- Access no longer required for a job function
- Certification and Remediation: Reviewers formally approve or revoke access. If issues are found, corrections are made, whether that’s revoking outdated rights, reducing privileges, or granting missing permissions.
- Documentation and Audit Trail: Every decision is logged. This creates a clear audit trail to prove compliance during internal and external audits.
What is the Access Certification Process?
The access certification process is a structured security practice where managers or designated reviewers regularly check if users’ access rights still make sense for their current roles. If permissions are outdated, unnecessary, or excessive, they’re revoked. This prevents misuse, reduces security gaps, and ensures compliance with regulations.
Also known as access attestation or recertification, this process is a core part of Identity Governance and Administration (IGA).
Enforcing the principle of least privilege stops employees from accumulating unchecked access over time and lowers the risk of insider threats or unauthorized data exposure.
In short, the access certification process ensures that permissions are not static; they evolve with the user’s responsibilities, business needs, and security requirements.
What are the Major Components of Access Certification Process?
An effective access certification process relies on a few core components that ensure reviews are consistent, compliant, and audit-ready.
1. User Entitlement Mapping
The foundation of certification is a clear inventory of entitlements who has access to which applications, systems, and data.
Mapping these rights makes it possible to spot overprivileged accounts, dormant access, or permissions that no longer align with a user’s role.
2. Reviewer Assignment Logic
Each access review must be assigned to the right person.
Typically, managers, application owners, or department heads are chosen because they understand the context of their team’s responsibilities. This ensures access decisions are accurate and business-aligned.
3. Policy-Driven Controls
Policies define the rules: how often reviews occur, what thresholds trigger revocation, and how exceptions are handled.
These controls keep certifications consistent across the organization and enforce security models such as least privilege and separation of duties.
4. Integration with IAM and HR Systems
For certifications to stay accurate, they must reflect real-time changes in user roles and employment status.
Integration with IAM and HR systems ensures that when someone changes departments or leaves the company, their access is automatically flagged for review.
5. Audit Logging and Evidence Collection
Every approval, rejection, and remediation step must be logged.
Detailed records not only create accountability but also make it easier to demonstrate compliance during audits, reducing the risk of penalties or failed assessments.
Access Certification Best Practices to Consider
The best way to strengthen access certification is by following proven practices that make reviews accurate, efficient, and business-focused.
Automate Recurring Reviews
Automating recurring reviews eliminates the delays and errors of manual tracking.
IAM and IGA tools can schedule certifications, send reminders, and generate reports automatically, reducing reviewer fatigue and ensuring deadlines aren’t missed.
Involve Business Owners, Not Just IT
Business managers and application owners understand how their teams use systems day-to-day.
Involving them in reviews ensures access decisions reflect real needs, not just technical permissions.
Apply Risk-Based Certification
High-risk accounts like privileged admin roles or systems holding sensitive customer data need more frequent, detailed reviews.
Risk-based certification helps prioritize effort where the potential impact of misuse is greatest.
Ensure Access Is Tied to Business Justification
Access rights should always have a clear reason tied to job responsibilities.
If a reviewer can’t justify why someone needs certain access, it’s a sign those permissions should be revoked.
Track Completion Rates and Remediation Times
Monitoring how quickly reviews are completed and how long it takes to fix identified issues keeps the process accountable.
These metrics highlight bottlenecks and show whether certifications are actually reducing risk.
Audit, Measure, and Continuously Improve
Certification isn’t a one-and-done exercise.
Regular audits, performance reviews, and policy updates help organizations refine their process, adapt to new risks, and improve compliance over time.
How CloudEagle.ai Can Manage Enterprise-Level User Access?
CloudEagle.ai simplifies enterprise access management by combining automation, visibility, compliance, and security into one platform.
It helps organizations reduce manual work, enforce least privilege, and stay audit-ready across all SaaS applications.
Automated Provisioning and Deprovisioning
- Assign access from day 1: New hires are automatically granted the right access based on HR system triggers, while departing employees or role changes trigger instant deprovisioning, closing security gaps, and cutting delays.

- Custom workflows: Sensitive roles can be routed through multi-level approvals, ensuring no access is granted without proper oversight.
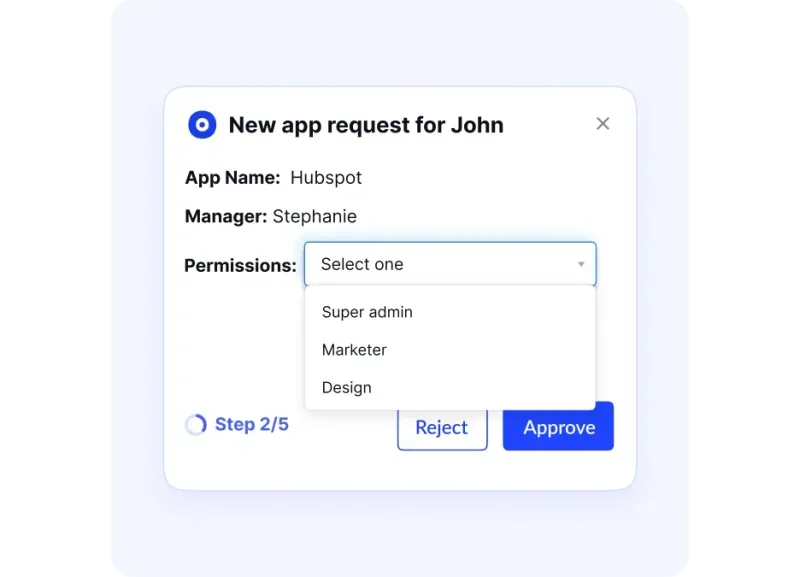
Unified Platform and Visibility
- Centralized dashboard: A single view of all user access across SaaS apps makes it easier for IT and business owners to spot overprivileged accounts or compliance gaps.
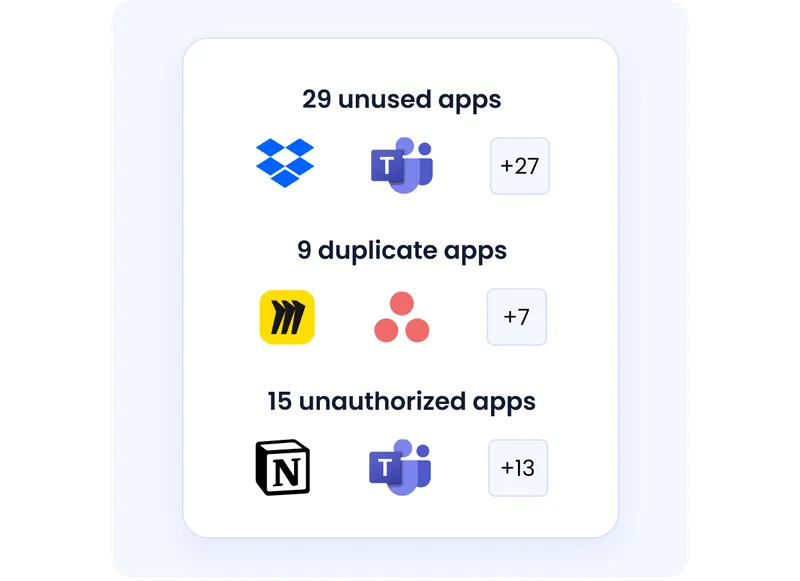
- Identity analytics: Built-in tools track entitlements, highlight risky access patterns, and simplify ongoing policy enforcement.
Compliance and Auditing
- Audit-ready reports: Pre-built templates and automated trails map directly to frameworks like SOC 2, ISO 27001, GDPR, and HIPAA. Audits that once took weeks can be completed in hours.

- Automated access reviews: CloudEagle.ai runs certification campaigns automatically, saving teams from logging into every individual app.
Self-Service and Efficiency
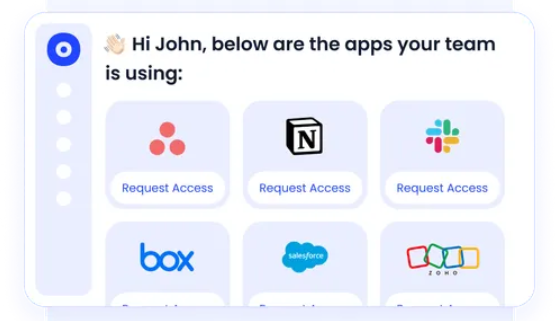
- App catalog: Employees request access through a self-service app catalog, which routes approvals to the right manager. This removes IT bottlenecks while preserving governance.
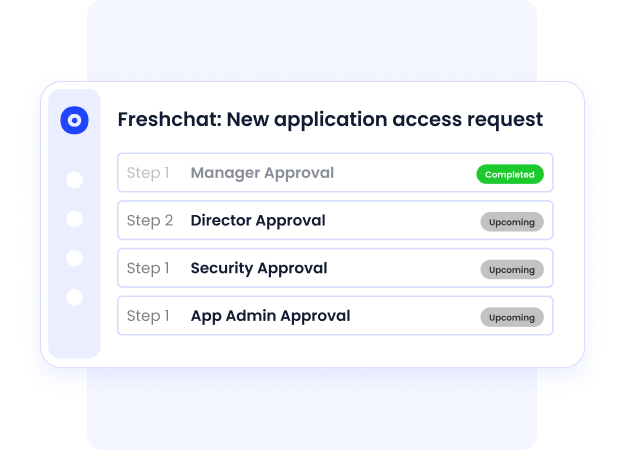
- Reduced IT workload: Automated provisioning, deprovisioning, and reviews free IT teams from repetitive admin tasks, letting them focus on higher-value security initiatives.
Enhanced Security
- Least privilege enforcement: Access rights are tied tightly to job roles, ensuring users only get what they need to perform their duties.
- Privileged access management: High-risk accounts are tightly controlled, with visibility into who has elevated permissions and for how long.
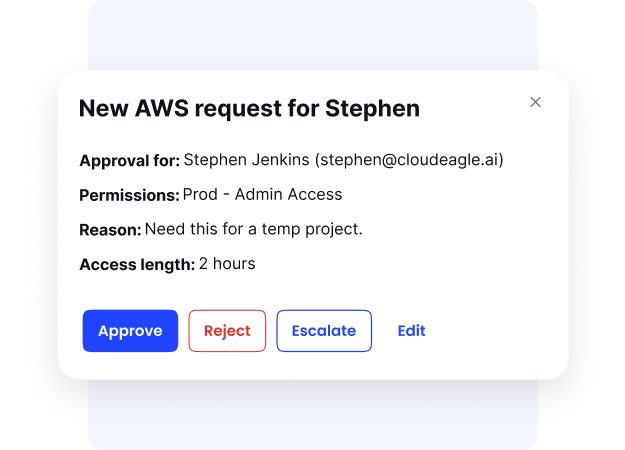
Ready to Certify Smarter, Not Harder?
Access certification helps cut privilege creep, tighten compliance, and make audits less painful. Done right, it’s a win for both security and efficiency.
CloudEagle.ai makes that win scalable, such as automating reviews, syncing with HR systems, and keeping you audit-ready without the spreadsheet chaos.
If access management has been a burden, this is where it finally gets easier.
Request a demo today to see it in action or start your free trial and experience the difference firsthand.
FAQs
1. What is access approval?
Access approval is the process of granting a user permission to specific systems, apps, or data after review. It ensures access is justified, aligned with policies, and limited to what’s needed for the role.
2. What is a user access audit?
A user access audit is a formal review of all user permissions across systems. It verifies whether access rights match job responsibilities, identifies risks, and ensures compliance with regulations and internal policies.
3. What is access accreditation?
Access accreditation is the validation that an organization’s access control policies meet industry standards or regulatory requirements. It confirms that processes for granting, reviewing, and revoking access are secure and compliant.
4. What is an access audit certificate?
An access audit certificate is an official record showing an organization has reviewed and validated user access rights. It provides evidence for regulators and auditors that access is controlled and compliant.
.avif)
%201.svg)







.avif)




.avif)
.avif)




.png)









