HIPAA Compliance Checklist for 2025

Enterprises today depend on hundreds of SaaS apps for daily work, ranging from email and collaboration to HR, finance, and analytics. Without a central access management system, employees struggle with managing multiple passwords, while IT teams spend countless hours resolving login issues and SaaS security risks.
Single sign-on (SSO) lets users access all apps with one secure login, reducing password fatigue and boosting enterprise security. It’s more than convenience; it creates a unified identity layer that simplifies login for users and IT teams.
However, successful SSO requires following standards, strong identity management, and consistent integration. Done right, SSO reduces breaches, simplifies permissions, and lets IT centrally manage access across cloud, on-premise, and hybrid applications.
Let’s explore the top SSO best practices every enterprise should follow.
TL;DR
- Use Single Sign-On (SSO) to let employees log in once and securely access all their apps, reducing password fatigue and improving productivity.
- Add an extra layer of security by combining SSO with multi-factor authentication (MFA) to prevent unauthorized access.
- Limit users’ permissions to only what they need, reducing risks of accidental or malicious access to sensitive data.
- Ensure your SSO uses trusted protocols like SAML and OAuth with strong encryption to protect authentication data.
- Automate access lifecycle management so users get timely access when joining and are immediately revoked when leaving, preventing orphaned accounts.
What is Single Sign-On?
Single Sign-On (SSO) is an authentication solution that allows users to log in once using a single set of credentials and securely access multiple applications and websites during the same session. This simplifies the login process by eliminating the need to remember and enter different passwords for each service.
SSO enhances security by reducing password fatigue and provides a streamlined user experience. It works through a central identity provider (IdP) that authenticates users and issues tokens, granting access across trusted applications without repeated logins.
In essence, single sign-on creates a unified layer for identity management, making it easier for both users and IT teams to manage access across cloud, on-premise, and hybrid environments.
What are the Different Single Sign-On Types?
There are several types of single sign-on (SSO) solutions tailored to meet different enterprise needs, from modern web-based SSO to legacy support and advanced biometric systems.
Federated Identity Management (FIM)
Federated identity management allows users to use one set of credentials across multiple systems or organizations. It creates trust between identity providers and service providers, enabling seamless access without re-authentication.
Web-Based Single Sign-On Solutions
These SSO solutions use web protocols like SAML, OAuth, and OpenID Connect to let users log in once and access multiple web applications securely. They are widely used for cloud and SaaS app access.
Enterprise SSO for Legacy Applications
These solutions support older, on-premise applications that may not natively support modern SSO standards. They often use credential vaulting or proxy-based authentication to provide single sign-on capabilities for legacy systems.
Smart Card and Biometric-Based SSO
This type leverages hardware tokens, smart cards, or biometric data (like fingerprints or facial recognition) for authentication. It offers high security and is often used in environments requiring strong identity verification.
Why Single-Sign On is Important for Enterprises?
Gartner highlights that organizations implementing SSO reduce password-related helpdesk calls by up to 50%, freeing IT teams to focus on strategic tasks.
Enterprises adopt Single Sign-On (SSO) to boost security, simplify user access, and reduce IT workload. Implementing SSO helps:
Enhance User Experience With Fewer Logins
Single sign-on dramatically improves user experience by allowing employees to access all their applications with just one login. This reduces the frustration of remembering multiple passwords and entering credentials repeatedly, making workflows smoother and boosting productivity across the enterprise.
Strengthen Security Through Centralized Access
SSO provides centralized identity management, ensuring consistent enforcement of security policies. It minimizes risks by reducing weak or reused passwords and supports integration with multifactor authentication. Centralized access control also helps IT teams monitor and respond quickly to suspicious login attempts or breaches.
IDC states that centralized identity management with real-time monitoring and audit trails accelerates threat detection and remediation by up to 30%, as it allows IT teams to quickly identify anomalous login activities and privilege escalations.
Reduce IT Helpdesk Workload From Password Resets
Password reset requests account for a large portion of IT helpdesk tickets. With SSO, employees memorize fewer passwords, drastically cutting down reset requests. This saves IT teams valuable time and reduces operational costs, allowing them to focus on higher-value tasks.
Support Regulatory Compliance Requirements
Many regulations, like GDPR, HIPAA, and others, require strict controls and auditing of user access to sensitive data. SSO simplifies compliance by providing centralized logs of authentication and access events. This improves visibility, accountability and helps enterprises meet compliance and regulatory standards more efficiently.
What are the 7 SSO Best Practices to Consider
Single sign-on (SSO) helps enterprises boost security, simplify user access, and improve efficiency. To maximize the benefits of SSO, companies should adhere to key best practices that ensure robust identity management and seamless integration.
Here are the top SSO best practices every enterprise should consider:
Implement Multi-Factor Authentication Alongside SSO
Adding multi-factor authentication (MFA) to your SSO setup greatly improves security. While SSO lets users log in once to access multiple apps, MFA adds an extra step, like a code or biometric scan to verify identity. This blocks unauthorized access even if passwords are stolen, following strong authentication standards.
Regularly Audit and Monitor Access Logs
Continuous monitoring of access logs is vital to detecting unusual activities or potential data breaches. Auditing helps track who accessed what and when, supporting compliance requirements and fast incident response. Effective SSO integration includes centralized logging to maintain visibility across all connected applications.
Apply the Principle of Least Privilege
Give users the minimum access necessary to perform their roles by implementing the Principle of Least Privilege. Limiting permissions reduces internal risks and helps contain breaches if credentials are compromised. Applying least privilege within your SSO system simplifies permission management and supports compliance and security best practices.
Forrester reports that enterprises enforcing the principle of least privilege in identity and access management reduce insider threat risks by up to 75%.
Ensure Strong Encryption and Secure Protocols
Use industry-standard encryption and protocols such as SAML, OAuth 2.0, or OpenID Connect for authentication and data exchange. Strong encryption protects credentials and tokens from interception during single sign-on implementation, ensuring data privacy and integrity.
Standardize Authentication With SAML or OAuth
Implement widely adopted single sign-on standards like SAML or OAuth to enable interoperability, scalability, and consistent security. These standards support diverse single sign-on types and facilitate smooth SSO integration across cloud and on-premise environments.
NIST’s Digital Identity Guidelines (SP 800-63-3) emphasize use of federated authentication standards such as SAML and OAuth 2.0 for secure and interoperable SSO implementations.
Train Employees on SSO Security Awareness
User awareness is critical to the success of any identity management strategy. Train employees to recognize phishing, handle credentials securely, and understand the importance of MFA. Such training reduces human error and complements technical security measures.
Automate User Provisioning and Deprovisioning
Automate access management so new users are granted correct permissions promptly, and departing users’ access is revoked immediately. This prevents orphaned accounts and reduces security risks, while streamlining lifecycle management as part of your SSO identity management strategy.
Deloitte states that automating user provisioning and deprovisioning can decrease orphaned accounts by 80% and reduce compliance violations.
How CloudEagle.ai Can Help With SSO?
CloudEagle.ai is an advanced SaaS management and access governance platform that complements and enhances your existing Single Sign-On (SSO) infrastructure. The platform improves security, optimizes SaaS spend, and automates identity and access management workflows.
Here’s how it can help your enterprise:
Complete Visibility Across SaaS Applications
CloudEagle.ai provides complete visibility into your SaaS stack with detailed insights into user access, usage patterns, and license allocations. This centralized view ensures nothing is overlooked, allowing IT and security teams to track who has access to what, identify underutilized licenses, and spot potential security risks early.
Role-Based Access Control
With CloudEagle.ai, you can implement role-based access controls, which help define roles and assign permissions tailored to each job function. This ensures users only have access they need to perform their duties.
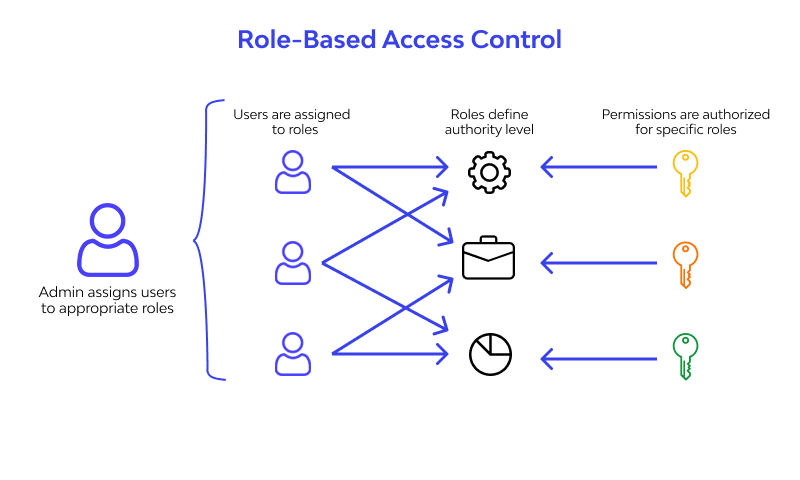
CloudEagle.ai automates role assignments and enforces access control policies smoothly, simplifying management while strengthening security by preventing excessive access.
Eliminate Shadow IT and Reduce Risk
CloudEagle.ai discovers all SaaS applications in use, including unauthorized ones. It can alert you when employees attempt to use unapproved software and enable proactive blocking of these applications, reducing shadow IT risks and improving organizational compliance.
Automated Employee Onboarding
CloudEagle.ai integrates with HR systems, SSO providers, and finance tools to automate user provisioning. When a new employee joins, CloudEagle.ai automatically grants them access to the right applications based on their role, department, and location.

This zero-touch provisioning ensures new hires can start working productively from day one, with all necessary tools ready, without waiting for manual IT approvals.
Streamlined Employee Offboarding
When employees leave or change roles, CloudEagle.ai promptly revokes their access across all connected SaaS applications. This automated deprovisioning eliminates orphaned accounts that can lead to security risks.
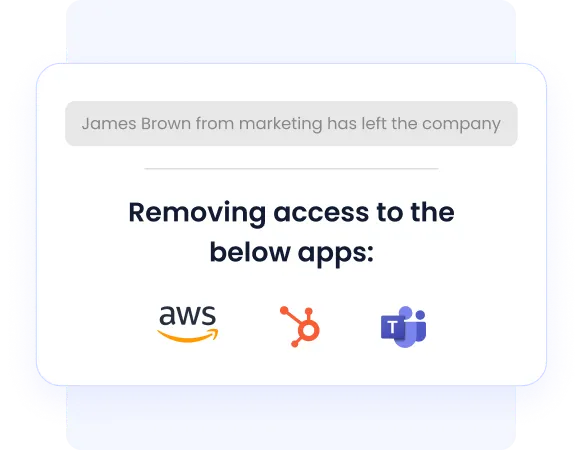
By centralizing offboarding workflows, CloudEagle.ai reduces manual errors, enhances security, mitigates insider threats, and ensures compliance with company policies and regulations.
Know how Treasure Data streamlined employee offboarding using CloudEagle.ai.
Robust Policy Enforcement and Access Reviews
CloudEagle.ai simplifies compliance by automating regular access reviews and certification processes. It helps maintain policies around least privilege access and highlights anomalous access for remediation, supporting regulatory mandates such as GDPR, HIPAA, and SOC 2.
Seamless Integrations and APIs
The platform connects easily with popular identity providers, HR systems, and cloud applications, unifying disparate systems into one cohesive SaaS management solution. Custom APIs enable provisioning and governance even for less common or internally built applications.
AI-Driven Automation for Proactive Management
CloudEagle.ai leverages AI insights to identify potential security issues before they become problems. It optimizes license assignments, predicts SaaS spend trends, and recommends access changes, helping enterprises stay agile and cost-efficient.
Enhanced Security with Just-in-Time and Privileged Access Controls
The platform supports granting just-in-time access to sensitive applications, ensuring temporary permissions automatically expire. Privileged access management capabilities restrict high-level permissions to only authorized users, reducing attack surfaces.
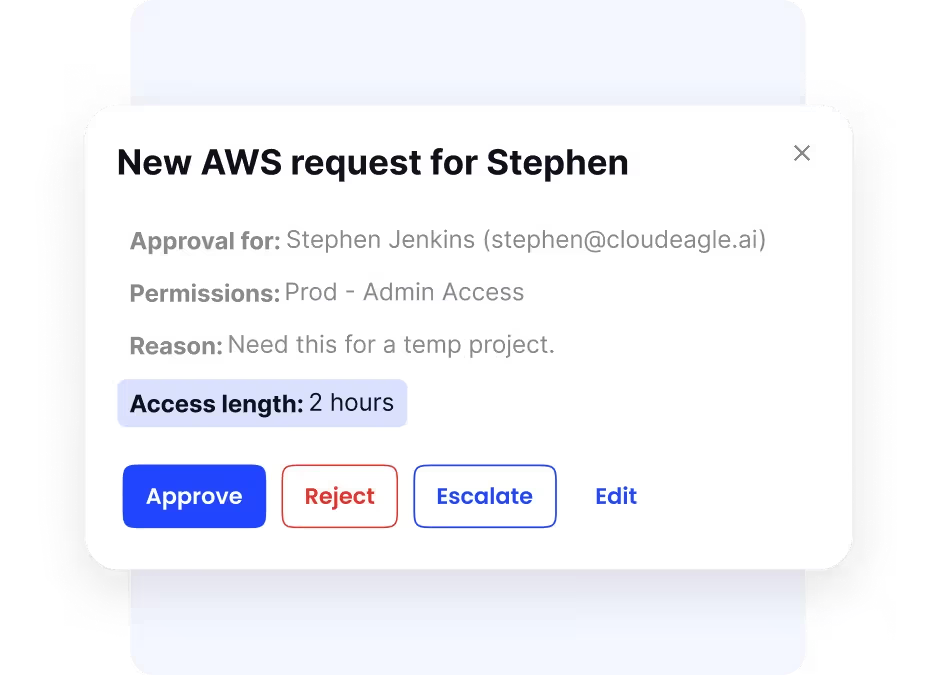
Real-Time Monitoring and Compliance Reporting
The platform maintains comprehensive compliance audit trails and continuously monitors all access activities. CloudEagle.ai leverages AI-driven alerts to promptly notify security teams of unusual events such as unexpected privilege escalations or unauthorized access attempts, enabling swift action against potential threats.

Alice Park shares that CloudEagle.ai transformed her team’s workflow by automating user onboarding and offboarding. Previously, significant time was lost on manual provisioning and deprovisioning tasks. With CloudEagle.ai, these processes are now fully automated, minimizing errors and significantly enhancing overall security.
Conclusion
Implementing these key SSO best practices helps your enterprise improve security, increase efficiency, and enhance user experience. When done right, SSO reduces password fatigue, lowers security risks, and allows IT teams to manage user access centrally across cloud, on-premise, and hybrid environments.
To make the most of these benefits and simplify identity governance, CloudEagle.ai offers a powerful SaaS management and access governance platform. With CloudEagle.ai, you get clear visibility into application usage and spending, automate user provisioning and deprovisioning, and enforce strong policies to protect your enterprise.
Don’t let complex access controls slow your business down or expose you to unnecessary risk.
Schedule a demo with CloudEagle.ai to see how AI-powered automation and governance can transform your single sign-on strategy and elevate your enterprise security posture effortlessly.
FAQs
1. How do I use single sign-on?
Use SSO by logging in once with your credentials. After authentication, you gain access to connected apps without reentering your password, simplifying access across multiple services securely.
2. What is the difference between SSO and AD?
SSO lets you access many apps with one login. Active Directory (AD) manages user identities and access in a network. AD can work with SSO to authenticate users and control permissions centrally.
3. When to use single sign-on?
Use SSO to streamline access when users need multiple apps, reduce password hassles, and improve security by centralizing authentication in corporate environments, especially with cloud or hybrid setups.
4. Does SSO require a license?
Most SSO solutions require licenses, which vary by provider. Licensing models include per-user, per-application, or enterprise-wide, depending on features and organizational needs.
5. What makes a good SSO?
Good SSO supports secure protocols like SAML or OAuth, integrates with existing systems, provides smooth login experiences, supports multi-factor authentication, and scales with your enterprise’s growth.

%201.svg)








.avif)




.avif)
.avif)




.png)









