HIPAA Compliance Checklist for 2025

As enterprises use more and more SaaS tools and move to hybrid IT environments, managing user access across all these systems has become harder than ever. Doing it manually takes a lot of time, often leads to mistakes, and increases the chances of security issues.
In fact, CloudEagle.ai’s IGA Report found that 48% of former employees still have access to company apps, which creates a major risk. To fix this, many organizations are now using SCIM (System for Cross-domain Identity Management).
SCIM is a secure, open standard that helps automate how users are added, updated, or removed from different apps. It works using APIs and a standard format (JSON), so everything happens in real time and without manual work.
Let’s explore how SCIM makes it easier for businesses to stay secure, work faster, and meet compliance needs in today’s digital world.
TL;DR
- SCIM is an open standard that automates user account creation, updates, and deactivation across multiple systems using RESTful APIs and JSON.
- Automates user provisioning and deprovisioning by syncing identity providers with SaaS applications, reducing manual errors and speeding up access management.
- Enhances security and compliance by ensuring timely revocation of access, minimizing orphaned accounts, and providing consistent audit trails for regulatory requirements.
- Improves operational efficiency by centralizing identity management, cutting administrative overhead, and enabling real-time synchronization of user data across platforms.
- Supports seamless integration with hundreds of cloud apps, enabling enterprises to scale identity management easily while optimizing user experience and security.
What is SCIM Provisioning?
SCIM Provisioning stands for System for Cross-domain Identity Management. It’s a way for companies to automatically manage user accounts and access across different SaaS apps.
Instead of manually adding or removing users in each app, SCIM lets you do it all from one place—like your identity provider (such as Okta or Azure AD). It uses RESTful APIs and JSON to send updates to connected apps in real time.
This makes it faster and easier to:
- Create new user accounts.
- Update roles or permissions.
- Remove access when someone leaves.
SCIM helps save time, cut down on errors, and keep your company secure, especially if you have lots of apps and users.
Key Features:
- Automated Provisioning & Deprovisioning: Instantly grant or revoke access based on user role changes, onboarding, or offboarding, reducing manual effort and errors.
- Real-Time Sync Across Apps: Keep user permissions updated across all connected SaaS tools as changes happen in your HR or identity system.
- Centralized Access Control: Manage all user access through your identity provider (e.g., Okta, Azure AD) for consistent enforcement and oversight.
- Stronger Security & Compliance: Reduce the risk of privilege creep and unauthorized access while staying audit-ready for standards like SOC 2, HIPAA, and GDPR.
What is the SCIM Protocol?
The System for Cross-domain Identity Management (SCIM) is an open standard protocol that automates exchanging user identity information between different IT systems or identity domains, especially in cloud and SaaS environments.It simplifies managing user accounts by enabling automatic provisioning, updating, and de-provisioning of user identities across multiple platforms such as Google Workspace, Microsoft 365, Salesforce, and others.
Think of SCIM as a bridge that helps apps "talk" to each other about users, like names, emails, roles, or who should have access. Instead of updating user info manually in every app, SCIM allows this to happen automatically and in sync.
What Does SCIM Do?
- Creates users automatically when someone joins your company.
- Updates user details (like job title or department) across all apps at once.
- Removes access when someone leaves, so all their accounts are deactivated instantly.
- Keeps user groups and roles in sync, so permissions are always up to date.
SCIM uses simple, secure web technology (like REST APIs and JSON) to do all of this behind the scenes. It works well with tools like Okta, Azure AD, Google Workspace, Slack, and more.
What Are the Components of SCIM?
SCIM comprises several key components that work together to enable efficient identity management:
Core Schema: The SCIM standard defines a core schema for representing users and groups. The user schema includes attributes like userName, name, emails, and active status, while the group schema covers attributes like displayName and members. These standardized schemas ensure consistent data representation across systems.
Resources: SCIM operates on two primary resource types: Users and Groups. Users represent individual accounts, while Groups define collections of users for access control. Resources are managed through CRUD (Create, Read, Update, Delete) operations.
RESTful API: SCIM uses HTTP-based RESTful APIs for communication, leveraging standard methods like GET, POST, PUT, PATCH, and DELETE. These APIs facilitate interactions between the IdP and SP, enabling actions like provisioning a new user or updating group memberships.
JSON Payloads: Data in SCIM is exchanged in JSON format, providing a lightweight and flexible structure for transmitting user and group information. JSON payloads ensure compatibility and ease of integration across diverse platforms.
Endpoints: SCIM defines specific API endpoints, such as /Users, /Groups, and /Schemas, for managing resources. These endpoints allow systems to query, create, or modify identity data systematically.
Authentication and Authorization: SCIM relies on secure authentication mechanisms, typically OAuth 2.0 or API tokens, to ensure that only authorized systems can perform provisioning tasks, safeguarding sensitive identity data.
Service Provider Configuration: The SP exposes a /ServiceProviderConfig endpoint, which details its SCIM capabilities, such as supported operations, authentication methods, and bulk processing limits, ensuring compatibility with the IdP.
How Does SCIM Provisioning Work?
SCIM (System for Cross-domain Identity Management) provisioning automates the management of user identities across systems by enabling seamless communication between an identity provider (IdP) and service providers (SPs).
The process leverages RESTful APIs and JSON payloads to perform CRUD (Create, Read, Update, Delete) operations on user and group resources. Here’s how it works:
- Initiation: The IdP, such as Okta or Azure AD, initiates a provisioning request based on predefined policies or triggers (e.g., a new employee is added to HR systems).
- API Communication: The IdP sends HTTP requests (e.g., POST to create a user, PUT to update) to the SP’s SCIM endpoints (e.g., /Users or /Groups).
- Data Exchange: User or group data, formatted in JSON per SCIM’s core schema, is transmitted securely, often using OAuth 2.0 for authentication.
- Action Execution: The SP processes the request, creating, updating, or deactivating user accounts or group memberships as instructed.
- Synchronization: SCIM supports real-time or scheduled synchronization to ensure user data remains consistent across systems.
- Error Handling: The SP returns status codes and error messages (if any) to the IdP, ensuring reliable operation and troubleshooting.
This automation reduces manual effort, minimizes errors, and ensures timely access control, enhancing security and efficiency.
What Is The Difference Between SAML and SCIM Provisioning?
- Purpose: SAML (Security Assertion Markup Language) focuses on authentication, enabling single sign-on (SSO) by allowing users to log in once and access multiple applications.
SCIM user provisioning focuses on user identity management, automating the creation, updating, and deletion of user accounts and group memberships across systems.
- Functionality: SAML exchanges authentication and authorization data (e.g., user identity and roles) via XML assertions, while SCIM uses RESTful APIs and JSON to manage user and group data.
- Use Case: SAML is used for seamless login experiences, whereas SCIM ensures user accounts are provisioned and deprovisioned efficiently across platforms.
- Protocol: SAML relies on XML-based messages, typically over HTTPS, while SCIM uses lightweight JSON over REST APIs.
What Is The Difference Between SCIM and ADFS?
- Purpose: SCIM automates user provisioning and deprovisioning across systems, managing user accounts and group memberships. ADFS (Active Directory Federation Services) enables federated authentication, providing SSO across trusted domains and applications.
- Functionality: SCIM uses RESTful APIs and JSON to manage user data, while ADFS uses SAML or WS-Federation protocols to exchange authentication and authorization data.
- Integration: SCIM integrates with cloud and on-premises systems for identity synchronization, often complementing directories like Active Directory. ADFS integrates Active Directory with external applications for SSO, relying on federation trusts.
- Use Case: SCIM is ideal for automating user lifecycle management (e.g., onboarding/offboarding), while ADFS is suited for enabling secure, seamless login experiences across trusted systems.
What Is The Difference Between SCIM and SSO?
Single Sign-On (SSO) and SCIM (System for Cross-domain Identity Management) are both tools used in identity management, but they serve different purposes.
Purpose: SSO lets users log in once through a tool like Okta and access many apps without logging in again. SCIM automatically creates, updates, or removes user accounts across apps, helping manage users through their entire journey.
Functionality: SSO handles authentication; it checks who the user is and gives them access using secure protocols like SAML or OAuth. SCIM manages user details like names, emails, and roles using REST APIs, keeping all systems in sync.
Use Case: SSO is great for making login easier. For example, one login gives access to Gmail, Slack, and Salesforce. SCIM is perfect for onboarding or offboarding—when someone joins or leaves, their access is added or removed automatically.
Data Shared: SSO sends login tokens to apps to confirm identity. SCIM shares user information like email, department, or group to make sure the right accounts are created.
Example: With SSO, a user logs into Okta and gets access to all their tools. With SCIM, Okta also automatically sets up or removes their accounts in tools like Slack or Zoom.
What are the Benefits of SCIM Provisioning?
SCIM (System for Cross-domain Identity Management) provisioning streamlines user identity management across systems, offering significant advantages for enterprises. Below are the key benefits, aligned with the specified aspects:
Automated User Provisioning and Deprovisioning
SCIM automates the creation, updating, and deletion of user accounts and group memberships across multiple systems. By integrating identity providers (IdPs) like Okta or Azure AD with service providers (SPs), SCIM eliminates manual account management, ensuring rapid onboarding and offboarding.
For example, when an employee joins or leaves, SCIM instantly provisions or deprovisions access, reducing administrative overhead and delays.
Centralized Identity Management
SCIM enables a single point of control for user identities across cloud and on-premises applications. It synchronizes user data, such as usernames, emails, and group memberships, ensuring consistency across platforms.
This centralization simplifies administration, allowing IT teams to manage identities from one IdP, reducing complexity in multi-system environments.
Improved Security and Compliance
By automating provisioning and deprovisioning, SCIM minimizes the risk of unauthorized access from outdated or orphaned accounts. It ensures the timely deactivation of accounts when users leave or change roles, enhancing security.
Additionally, SCIM’s standardized approach supports audit trails and consistent data handling, aiding compliance with regulations like GDPR, HIPAA, or SOC 2.
Time and Cost Efficiency
SCIM reduces the time and resources spent on manual identity management tasks. Automation eliminates repetitive administrative work, allowing IT teams to focus on strategic initiatives. By streamlining provisioning processes, SCIM lowers operational costs, particularly for enterprises managing large user bases or numerous applications.
Enhanced User Experience
SCIM ensures users gain timely access to the tools and applications they need, improving productivity and reducing onboarding friction. Seamless synchronization of user attributes and group memberships across systems provides a consistent and efficient experience, enabling employees to focus on their work without access-related delays.
Challenges of SCIM Identity Management
While SCIM user provisioning streamlines user identity management, enterprises may encounter the following challenges when implementing and maintaining it.
Integration Complexity: Integrating SCIM with diverse systems, especially legacy or non-SCIM-compliant applications, can be complex. Some platforms may lack full SCIM support or require custom configurations, leading to additional development effort and potential compatibility issues.
Schema Mismatch: SCIM relies on standardized schemas for user and group data, but different applications may use custom attributes or non-standard data formats. Aligning these schemas between identity providers (IdPs) and service providers (SPs) can be time-consuming and may require manual mapping.
Scalability and Performance: In large enterprises with thousands of users or numerous applications, SCIM provisioning can strain system resources. High volumes of API calls for real-time synchronization may lead to performance bottlenecks or rate-limiting issues on the SP side.
Security and Authentication: SCIM protocol requires secure authentication (e.g., OAuth 2.0 or API tokens) to protect sensitive user data. Misconfigured security settings or weak authentication mechanisms can expose vulnerabilities, risking unauthorized access or data breaches.
Error Handling and Monitoring: SCIM operations can fail due to network issues, incorrect data, or SP-specific constraints. Without robust error handling and monitoring tools, diagnosing and resolving these failures can be challenging, leading to delays in provisioning or data inconsistencies.
Compliance and Governance: While SCIM aids compliance, ensuring that all provisioning actions align with regulations like GDPR, HIPAA, or SOC 2 requires careful configuration. Enterprises must maintain audit trails and ensure that deprovisioning is timely to avoid non-compliance with data protection laws.
Vendor Lock-in and Support Variability: Not all SPs implement SCIM consistently, and some may only support specific versions (e.g., SCIM 2.0) or subsets of features. This variability can limit interoperability and create dependency on specific vendors, complicating multi-vendor environments.
How CloudEagle.ai Can Help You With SCIM Provisioning?
CloudEagle.ai enhances SCIM user provisioning by addressing common challenges around integration, security, and compliance, making it easier for organizations to manage SaaS licenses and user access at scale.
Here’s how CloudEagle.ai supports SaaS license management software through SCIM provisioning:
1. Seamless Integrations with 500+ SCIM-Compliant Apps
CloudEagle.ai connects effortlessly with over 500 apps with SCIM integrations capabilities, including popular platforms like Salesforce, Slack, and Microsoft 365. This extensive integration library reduces the complexity of managing multiple SaaS licenses and user accounts across different systems.
2. Real-Time Visibility and Centralized Monitoring
CloudEagle.ai provides a centralized dashboard that offers real-time visibility into user access across all integrated SaaS applications.

This transparency helps IT and security teams monitor compliance with regulations like GDPR and HIPAA, ensuring that access policies are consistently enforced. The platform’s audit-ready logs and customizable reports simplify compliance audits and ongoing monitoring.
3. Automated Role-Based Provisioning
With CloudEagle.ai, user provisioning is automated based on predefined roles and departments. When a new employee joins, the platform instantly grants access to all necessary applications aligned with their job functions.

This role-based provisioning ensures that new hires are productive from day one, while also simplifying license allocation and reducing administrative overhead.
4. Rapid and Reliable Deprovisioning
One of the biggest security risks is orphaned accounts—user accounts that remain active after employees leave the organization.

CloudEagle automatically revokes access for departing employees or those who change roles, significantly reducing this risk. Automated deprovisioning ensures that no unauthorized access persists, protecting your sensitive data and systems.
5. Just In Time Provisioning
CloudEagle.ai helps enterprises implement Just-in-Time (JIT) provisioning as a smarter way to enforce least-privilege access and reduce security risks in complex SaaS environments.
This approach is becoming more important because, according to the CloudEagle.ai IGA Report, only 15% of enterprises currently use JIT provisioning fully, even though many more should adopt it to stay secure and compliant.
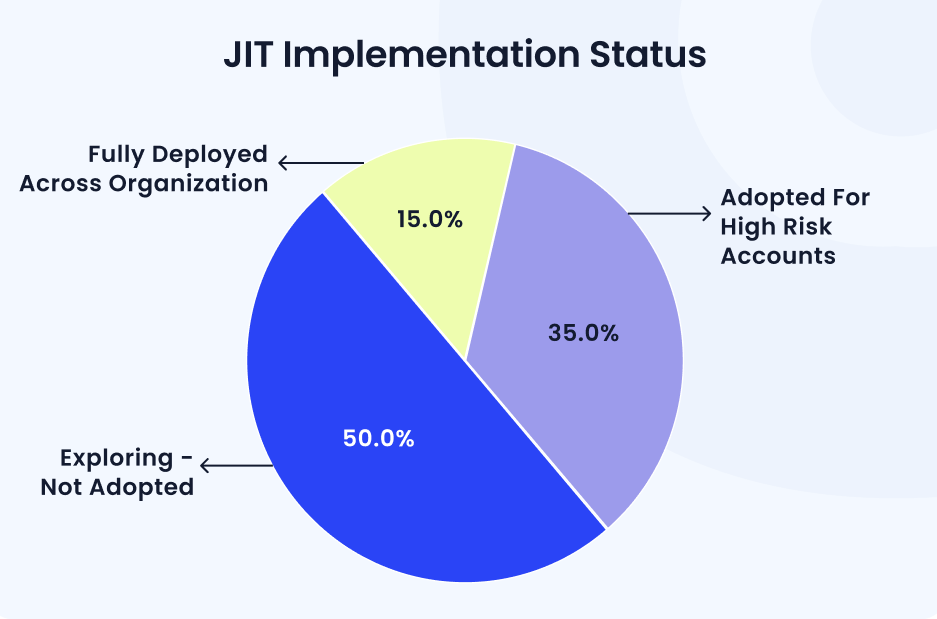
JIT provisioning ensures that users and contractors receive access only when needed, for a limited duration, and automatically revokes it once the task is completed, eliminating the risk of excessive or lingering access.
Instead of granting users permanent access to applications or systems, JIT provisioning allows access only when needed, for a specific duration and purpose. Through our automated request workflows, users can initiate access requests tied to tasks or roles.
CloudEagle.ai checks who the user is, what they need access to, and their role, such as their job, department, and risk level, before giving temporary access. Once the task is done or the session ends, the platform automatically removes access, so there is no need to do it manually.
6. Compliance Support with Audit-Ready Logs
Maintaining compliance with industry regulations requires detailed records of who accessed what and when. CloudEagle automatically logs every provisioning and deprovisioning action, along with access requests and approvals.

These immutable audit trails are essential for demonstrating compliance during regulatory reviews and reducing risks associated with unauthorized access.
To see how streamlining provisioning and deprovisioning can benefit your enterprise, check out Alice Park’s testimonial from Remediant, where she shares how CloudEagle.ai simplified onboarding and offboarding.
Conclusion
CloudEagle.ai simplifies SCIM provisioning by automating identity management across your SaaS ecosystem. With powerful integrations, real-time insights, and a centralized dashboard, it helps streamline user onboarding, offboarding, and access governance.
By leveraging SCIM’s automation potential, CloudEagle.ai minimizes security risks, reduces administrative overhead, and enhances operational efficiency, making it an invaluable tool for modern IT and HR teams managing dynamic, multi-application environments.
Are You Ready to optimize your identity management?
Schedule a demo with CloudEagle.ai to explore how you can streamline your SCIM user provisioning and boost your SaaS efficiency.
FAQs
1. What does SCIM stand for?
SCIM stands for System for Cross-domain Identity Management.
2. What is the purpose of SCIM?
SCIM aims to standardize and simplify user identity management across different systems and applications, enabling secure and efficient user provisioning and deprovisioning.
3. Does SCIM use LDAP?
SCIM does not use LDAP directly but can complement or replace LDAP systems by providing a modern, REST-based protocol for identity management, often integrating with LDAP directories.
4. What is the difference between SCIM and ADFS?
SCIM focuses on user provisioning and identity management across systems, while ADFS (Active Directory Federation Services) enables single sign-on (SSO) and federated authentication between trusted domains.
5. What is the alternative to SCIM?
Alternatives to SCIM include LDAP, SAML for identity federation, custom API-based provisioning, or proprietary identity management solutions like Okta or SailPoint.

%201.svg)










.avif)




.avif)
.avif)




.png)









