HIPAA Compliance Checklist for 2025

Privilege creep occurs when employees accumulate access rights beyond what they need for their current job roles. This often happens as employees change roles, take on temporary projects, or receive additional permissions that are never revoked.
According to CloudEagle.ai’s IGA Report, 1 in 2 employees have excessive access privileges. This makes it critical for IT teams to regain control before these overprivileged access rights lead to major security or compliance risks.
This unchecked growth of permissions expands an organization’s attack surface, making it easier for insider threats, accidental misuse, or external attackers who compromise accounts to cause damage. It also leads to compliance challenges and operational inefficiencies.
Let’s explore how you can stay ahead of privilege creep and keep your enterprise secure and compliant at all times.
TL;DR
- Privilege creep happens when employees accumulate more access than needed due to role changes, temporary projects, or unrevoked permissions, leading to nearly half of employees being overprivileged.
- Common causes include default broad access at onboarding, failure to revoke old permissions after promotions, lingering temporary access, and overlapping permissions from multiple departments.
- Overprivileged accounts increase security risks by expanding the attack surface, enabling insider threats, causing compliance violations, and complicating access management.
- Fixing privilege creep requires enforcing the Principle of Least Privilege, implementing role-based access control (RBAC), and conducting regular access reviews and audits.
- Automation through privileged access management (PAM), provisioning/deprovisioning integration, and continuous monitoring are key to preventing privilege creep and maintaining secure, compliant access.
What Is Privilege Creep?
Privilege creep happens when an employee keeps getting new access over time, without old, unnecessary permissions being removed. As a result, they end up with more access than they need for their current role.
For example, someone who was promoted or moved between teams might still have access to tools or data from their previous job. This extra access increases the risk of data leaks, insider threats, or accidental misuse. It’s the opposite of following the “least privilege” rule, which says users should only have the minimum access needed to do their jobs.
“Privilege creep happens when employees retain access they no longer need, quietly piling up over time. Without regular access reviews, these outdated permissions become a hidden threat to security and operational integrity.” — Noni Azhar, CIO, ProService Hawaii.
Difference Between Intended Privileges And Privilege Creep
Intended privileges are the exact app access and permissions someone needs to do their job—nothing more. This access is based on their role and is usually reviewed by IT or security to make sure it’s correct.
Privilege creep in cyber security happens when people slowly collect more access than they need. This can happen when they switch roles, help with a project, or are never removed from apps they no longer use. Over time, they end up with too much access, and that can be risky.
The key difference:
- Intended access is planned, limited, and reviewed.
- Privilege creep is accidental, extra, and often missed.
Intended privileges help keep your company safe. Privilege creep can open the door to security problems.
Why Does Privilege Creep Occur?
Privilege creep is often unintentional but creates significant security risks. Here are the main reasons why privilege creep occurs:
1. Default Access Given at Onboarding Without Later Adjustment
When new employees join, they are often granted broad access permissions to enable them to start work quickly. However, as their responsibilities become clearer or more focused, these initial permissions are rarely scaled back. This leads to employees retaining unnecessary access that exceeds their actual needs.
2. Role Changes or Promotions Without Revoking Old Permissions
Employees frequently change roles, get promoted, or transfer to different departments. During these transitions, new access rights are added to support their new responsibilities, but the old permissions from previous roles are often not revoked promptly, or at all. This results in overlapping access rights that accumulate over time.
“I’ve seen it happen too many times: an employee changes roles, yet months later, they still have admin access to systems they no longer need. Manual access reviews are just too slow to catch these issues in time. By the time someone notices, privilege creep has already turned into a serious security risk.” — Nidhi Jain, CEO and Founder, CloudEagle.ai
3. Temporary/Project-Based Access Not Revoked After Use
Enterprises often grant temporary access to employees for specific projects, emergencies, or cross-training purposes. Unfortunately, once these projects or tasks are completed, the temporary permissions are not always removed. This leaves employees with lingering elevated access that is no longer necessary.
According to CloudEagle.ai’s IGA report, 40% of organizations said users, including contractors, often retain SaaS access even after their assignments end.
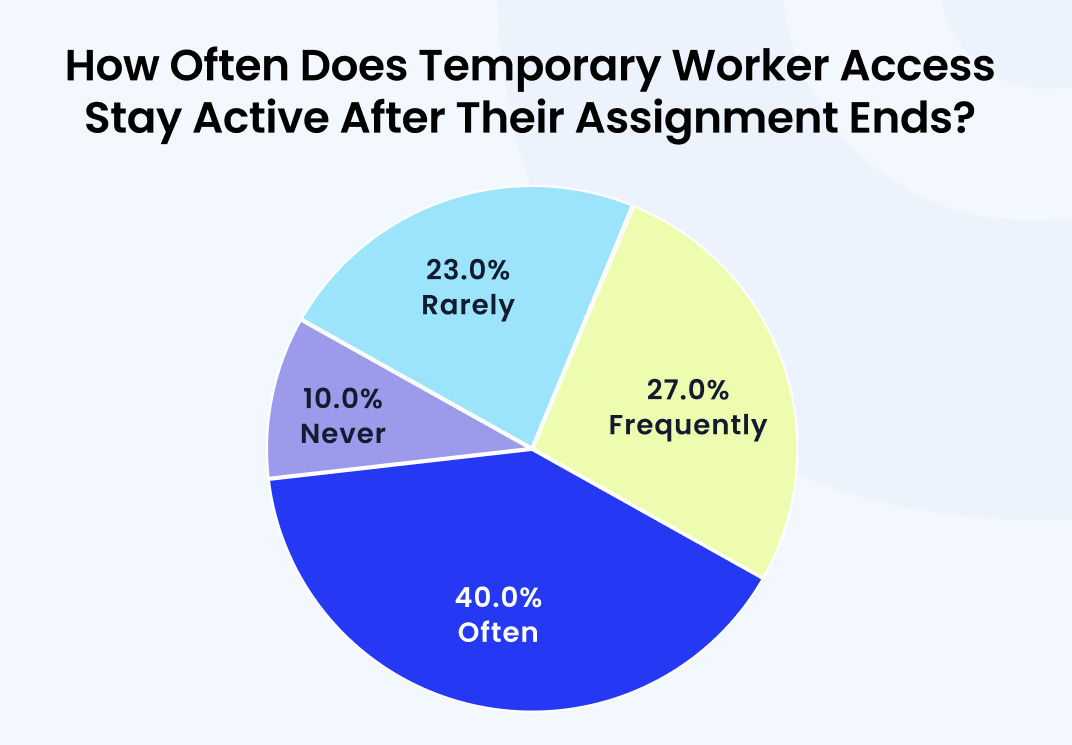
4. Multiple Departments Granting Overlapping Permissions
In larger enterprises, different teams or departments may independently grant access to the same employee without coordination. For example, IT, HR, and Finance might each assign permissions based on their own needs, leading to overlapping and excessive access rights.
What Are The Risks of Privilege Creep?
Privilege creep quietly builds up over time, increasing the risk of data leaks, insider threats, and audit failures if unused or unnecessary access isn’t regularly removed. It leads to the following:
Larger Attack Surface: When employees have more access than needed, attackers who compromise one account can reach multiple systems, making it easier to move across the network and access sensitive data.
Increased Insider Threats: Employees with extra privileges can abuse their access intentionally (e.g., for sabotage or fraud), or unintentionally cause harm by making mistakes or falling victim to phishing attacks.
Harder to Detect Breaches: With many users holding excessive permissions, it becomes difficult to trace, detect, and contain security breaches quickly.
Greater Risk of Data Breaches: Unchecked and unnecessary privileges make it easier for outsiders and insiders to leak, steal, or modify confidential data.
According to CloudEagle.ai’s IGA report, insider threats are responsible for 28% of data breaches, making them one of the most common and dangerous sources of security incidents.
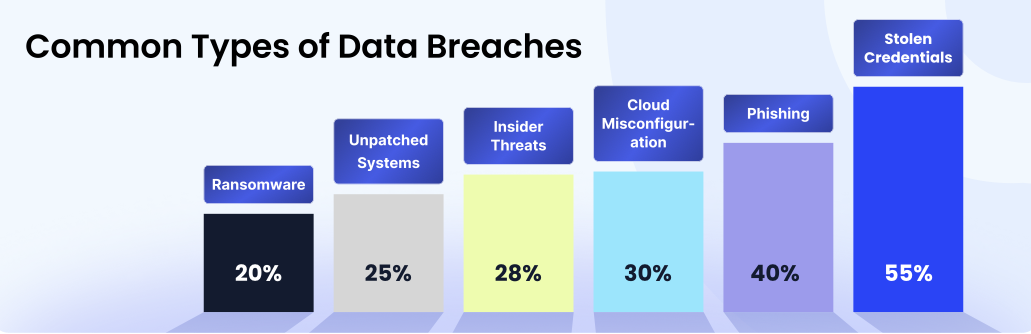
Regulatory Non-compliance: Many regulations (like HIPAA, GDPR, and SOX) require strict access controls; privilege creep makes audits harder and can lead to fines or legal trouble if discovered after a breach.
Operational Problems: Too much access can cause employees to accidentally disrupt workflows, delete or alter important files, and slow down processes thanks to confusion or unauthorized changes.
Higher Costs and Complexity: Excessive privileges create an ever-expanding web of access rights, making permission reviews, compliance management, and security operations more complicated and expensive over time.
Signs Your Enterprise Has a Privilege Creep Problem
Access Audits Don’t Match Roles: Regular audits reveal employees who have access to systems or data unrelated to their current job responsibilities. This is a classic privilege creep warning sign.
Too Many Admins: If people outside of IT, or many long-tenured employees, have admin permissions (or greater access than peers in similar roles), privilege creep is likely present.
Cross-Department Access: Users in one department have access to data or platforms owned by another department without a clear reason.
Long-Time Employees Can “See Everything”: Staff who have changed roles, filled in temporarily, or taken on special projects accumulate access over time. If these permissions aren’t removed, they’re left with a menu of “keys” to the company.
Unexplained or Forgotten Accounts: Orphaned accounts for contractors, former employees, or outdated systems that were never fully deprovisioned often linger with excess privileges.
Audit Trail Gaps: Gaps between intended access policies and what’s actually provisioned, or an inability to quickly answer “who has access to what and why,” highlight privilege creep.
Frequent Compliance Failures: Regular trouble during compliance or security audits points to unaddressed privilege sprawl in the environment.
Why 1 in 2 Employees Have Excess Access?
Many employees retain old permissions after role changes, temporary projects, or due to poor access controls, leading to widespread overprivileged access across enterprises.
Role Changes and Promotions: Whenever employees change departments or are promoted, new access rights are granted, but old permissions are rarely revoked. Over time, this leads to a buildup of unnecessary privileges, known as “privilege creep”.
Onboarding Without Offboarding: New tools and apps are granted as job needs expand, yet no one systematically reviews and prunes access to what’s no longer needed.
Lack of Automation: Manual permission management is error-prone. Enterprises without automated tools are much more likely to forget to revoke or adjust permissions.
Overly Permissive Defaults: Some systems have generous default access settings, granting users more rights than required unless specifically restricted.
No Clear Policy: Without enforcing the “need to know” principle, enterprises allow users to accumulate access over time.
Growth and Organizational Change: As enterprises scale, managing and auditing access across hundreds of apps and systems becomes exponentially harder, leading to more cases of excess access.
How to Fix and Prevent Privilege Creep?
Privilege creep in cyber security can quietly expose your organization to serious security and compliance risks.
Here’s how to spot it early and fix it fast.
Enforce the Principle of Least Privilege (PoLP)
The Principle of Least Privilege means giving every user, app, or system only the access they need—nothing more. This simple rule helps stop both mistakes and malicious use of access, making your systems more secure.
Start by creating different account types for everyday users, privileged users like IT admins, and services. For example, an IT admin should use one account for daily tasks like email and a separate one for jobs needing high-level access.
Next, really think about what each person or application needs. Don’t give access “just in case”—this is how too much access builds up. Give only what’s required for that role, and regularly check and remove access that’s no longer needed.
Organizations that consistently use PoLP see several benefits: a smaller attack surface (fewer ways for hackers to get in), less risk if someone’s account gets compromised, more system stability, and easier compliance with security rules. Even high-security agencies like the NSA rely on PoLP to keep their systems safe.
Implement Role-Based Access Control (RBAC)
Role-based access control (RBAC) helps manage access by assigning permissions based on job roles. For example, roles like “Finance Analyst” or “IT Support” come with preset permissions.
Instead of giving permissions to each person manually, just assign them to the right role. This keeps access accurate and avoids giving more than needed. When someone changes jobs, simply update their role to adjust their access; this helps prevent privilege creep and keeps your system secure.
Conduct Regular Access Reviews and Audits
It’s important to regularly check who has access to what, so outdated or excessive permissions don’t build up unnoticed. Set a routine schedule, like every few months, to review permissions for each system, user, or job role.
Automated tools can help by flagging dormant accounts, unused permissions, or conflicts. After each review, act quickly to remove any permissions people no longer need.
Doing these reviews not only strengthens security but also helps you meet regulations like ISO 27001, GDPR, HIPAA, or SOX, since you’ll have clear records for auditors and can quickly show that you’re controlling access as required by law.
Use Privileged Access Management (PAM) Solutions
Privileged Access Management, or PAM, is a way to control and protect your most sensitive user accounts, like those used by IT admins or anyone with high-level access. These accounts can do much more than regular ones, so they need tighter security.
PAM tools store all privileged account credentials (like passwords and keys) in a secure digital vault that only authorized users can access. This helps keep those credentials safe from hackers or misuse by insiders.
Modern PAM systems also support Just-in-Time (JIT) access, which means users get admin access only when they need it, and only for a short period. After the task is finished, the access is automatically removed. This greatly limits how long elevated access is available, reducing the chance it gets misused or forgotten.
Automate Provisioning and Deprovisioning
Automation makes user access management faster and safer. By connecting access controls with HR and IT systems, permissions are updated automatically when someone joins, leaves, or changes roles. This helps avoid mistakes and ensures no one keeps access they shouldn’t have.
This prevents “orphaned accounts” from lingering after staff departures, which are a common source of unauthorized access. Automation brings faster onboarding, seamless offboarding, and consistent security enforcement across all applications and platforms.
Monitor and Log Access Activity
Ongoing access monitoring helps you see how accounts and permissions are being used. By tracking user activity, you can spot unusual behavior, like someone accessing sensitive data at odd hours. Automated tools can detect these risks, send alerts, and help your team respond quickly.
Maintaining comprehensive audit logs is also critical for meeting compliance requirements and providing evidence during investigations. Continuous monitoring transforms access management from a reactive to a proactive defense, helping you identify and mitigate threats early.
How CloudEagle.ai Can Help Reduce Overprivilege?
CloudEagle.ai helps solve the problem of creeping privileges by giving enterprises the tools to enforce the Principle of Least Privilege (PoLP) across all SaaS and cloud applications.

Here’s how it does:
Detect and Control Shadow IT
One major cause of overprivileged access is shadow IT, where employees use apps and tools without IT team approval. CloudEagle.ai uses a powerful AI-enabled discovery engine to monitor SaaS usage and detect unauthorized or high-risk apps across the organization.

By identifying these tools early, IT teams can take action to review who’s using them, reduce unnecessary access, and stop data from flowing into insecure, unmanaged systems. This is a critical step in enforcing least privilege and reducing potential exposure.
Centralized Access Visibility and Compliance
Monitoring access across hundreds of apps can quickly become overwhelming. CloudEagle.ai brings everything into one centralized platform where IT and security teams can view all user permissions in one place.

The system connects with identity and access management (IAM) tools and automatically logs user activity, making it easier to stay compliant with regulations like GDPR, HIPAA, and SOX. At any point, you’ll be able to answer questions like: “Who has access to this app?” or “Is this user’s access still necessary?”
“Overprivileged access is a compliance nightmare waiting to happen. If employees keep unnecessary permissions, it’s only a matter of time before sensitive data ends up in the wrong hands. Regulations like SOC 2 and GDPR demand strict access controls, but without regular reviews, companies are flying blind, and that’s a costly risk to take.” — Datta Junarkar, CIO, Maritime, Boeing.
Automated Provisioning, Deprovisioning, and Access Reviews
Manual processes like onboarding, offboarding, or reviewing user permissions often lead to mistakes or overlooked accounts. CloudEagle.ai automates these tasks:
Auto-Provisioning: New employees get the right access on Day 1 based on their role.

Auto-Deprovisioning: Departing users have their app access revoked immediately.

Access Reviews: Scheduled access reviews regularly check whether users still need the access they have.

The system also flags overprivileged users, inactive accounts, and unused licenses, so permissions are always kept in sync with job roles, removing excess access before it becomes a risk.
Just-in-Time (JIT) Access
Some users only need admin-level access for specific tasks and short periods. Instead of giving them full-time elevated privileges, CloudEagle.ai supports Just-in-Time (JIT) Access.
According to CloudEagle.ai’s IGA Report, different departments are widely using the JIT access mechanism. Below is a graphical representation showing which departments use these features for specific environments.
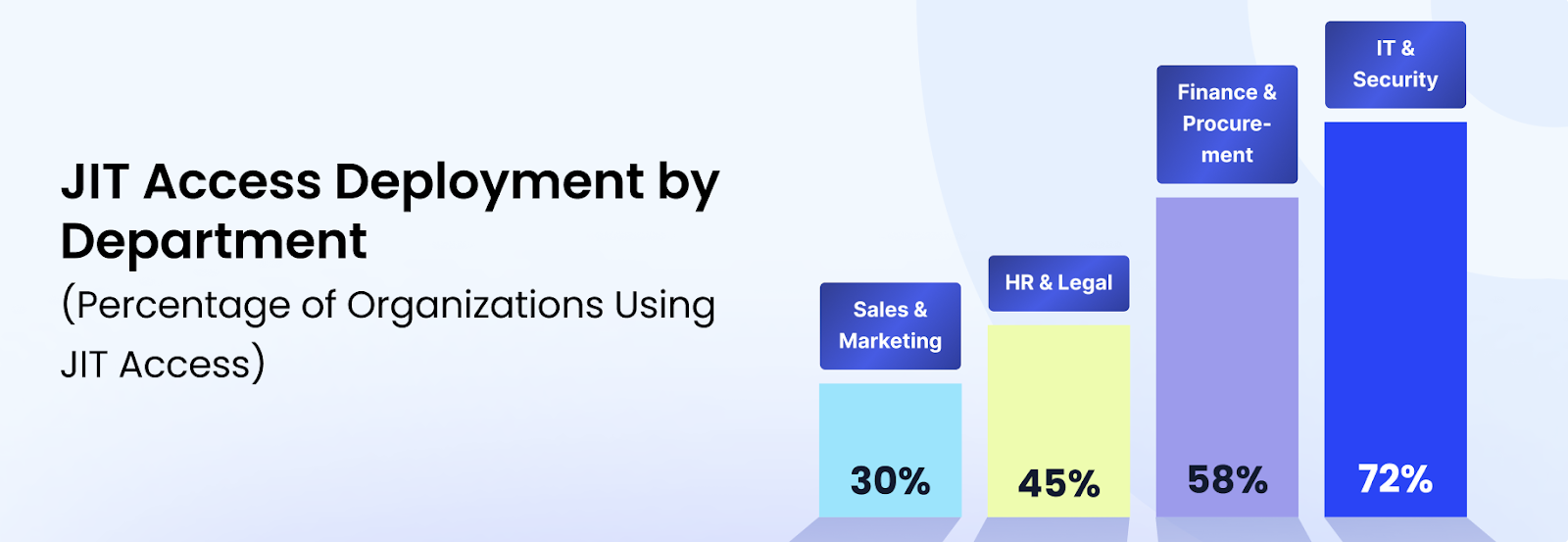
This lets users request temporary access that automatically expires after the task is done. It’s a great way to reduce risks while still giving employees what they need, when they need it, without compromising security.
“Adopting just-in-time access is the closest thing to a 'never trust, always verify' model for user permissions. If you’re still leaving standing privileges unchecked, you’re giving attackers exactly what they need to exploit your systems.” — Jim Palermo, CIO, Red Hat.
Role-Based Access Control (RBAC)
CloudEagle.ai makes it easy to set up and enforce role-based access control (RBAC). You define roles (like “Sales Manager” or “Finance Analyst”) and assign users to those roles. This ensures everyone gets the right access for their job; no more, no less.

When roles change, access is updated automatically, avoiding permission clutter over time. It also makes managing access faster and more scalable across large teams.
Conclusion
Many employees today have more access than they need. This often happens when people change roles, work on short-term projects, or when access is given but never removed. Over time, unused or excessive access builds up a problem called privilege creep.
This not only increases security risks but also makes it easier for insider threats and accidental data leaks. To fix creeping privileges, enterprises need to follow the Principle of Least Privilege, where users are given only the access they truly need.
This can be done by setting up role-based access, automating access reviews, removing unused permissions, and using tools like Just-in-Time (JIT) access so elevated access is temporary.
Doing this manually is hard, especially if your company uses many SaaS or cloud apps. That’s where automation comes in.
Do you want to reduce risk, save time, and make access management easy?
Schedule a demo with CloudEagle.ai to see how you can detect overprivileged users, automate cleanups, and keep your data safe.

%201.svg)







.avif)




.avif)
.avif)




.png)









