HIPAA Compliance Checklist for 2025

Protecting your enterprise isn’t just about having the right tools; it’s about giving the right people the right access at the right time. That’s where access control and access management become very useful. Though often used interchangeably, these two concepts play distinct roles in your security strategy.
Access control sets the rules and gates: who can enter which digital doors and interact with sensitive data. Meanwhile, access management is the engine behind the scenes, handling everything from account creation and permissions to monitoring and deactivation.
When you understand the difference between access control and access management, you lay the foundation for a more secure, efficient, and compliant security framework.
Let’s explore in detail access control vs access management; what sets them apart, how each helps safeguard your business, and why mastering both is essential for modern enterprises.
TL;DR
- Access control decides who can access specific resources by enforcing rules like RBAC or mandatory access control.
- Access management is broader; it includes verifying identities, provisioning users, managing permissions, and monitoring access throughout the user’s lifecycle.
- Identity management handles digital identities, while access management controls what those identities can do.
- Access control is part of access management, and combined tools help automate and centralize security.
- Using privileged access management strengthens defense against insider threats, breaches, and compliance risks.
What is Access Control?
Access control is a security practice that determines who is allowed to access or use resources within a system, application, or physical environment. It involves defining and enforcing rules and permissions that restrict or grant access to data, systems, or physical locations based on user identities, roles, or attributes.
The main goal of access control is to ensure that only authorized individuals can interact with sensitive information or critical infrastructure, thereby protecting assets from unauthorized use or breaches.
What are the Benefits of Access Control?
Access control provides several important benefits for enterprises:
- Enhanced Security: Limits access to sensitive data and systems to authorized users only, reducing the risk of data breaches and insider threats.
- Regulatory Compliance: Helps enterprises meet legal and industry requirements by enforcing strict access policies and maintaining audit trails.
- Reduced Risk: Prevents unauthorized actions or data exposure by controlling who can view, modify, or delete information.
- Operational Efficiency: Streamlines access management by automating permissions, reducing manual errors, and simplifying user onboarding and offboarding.
- Granular Permissions: Supports fine-grained control over resources, allowing enterprises to tailor access based on roles, departments, or other attributes.
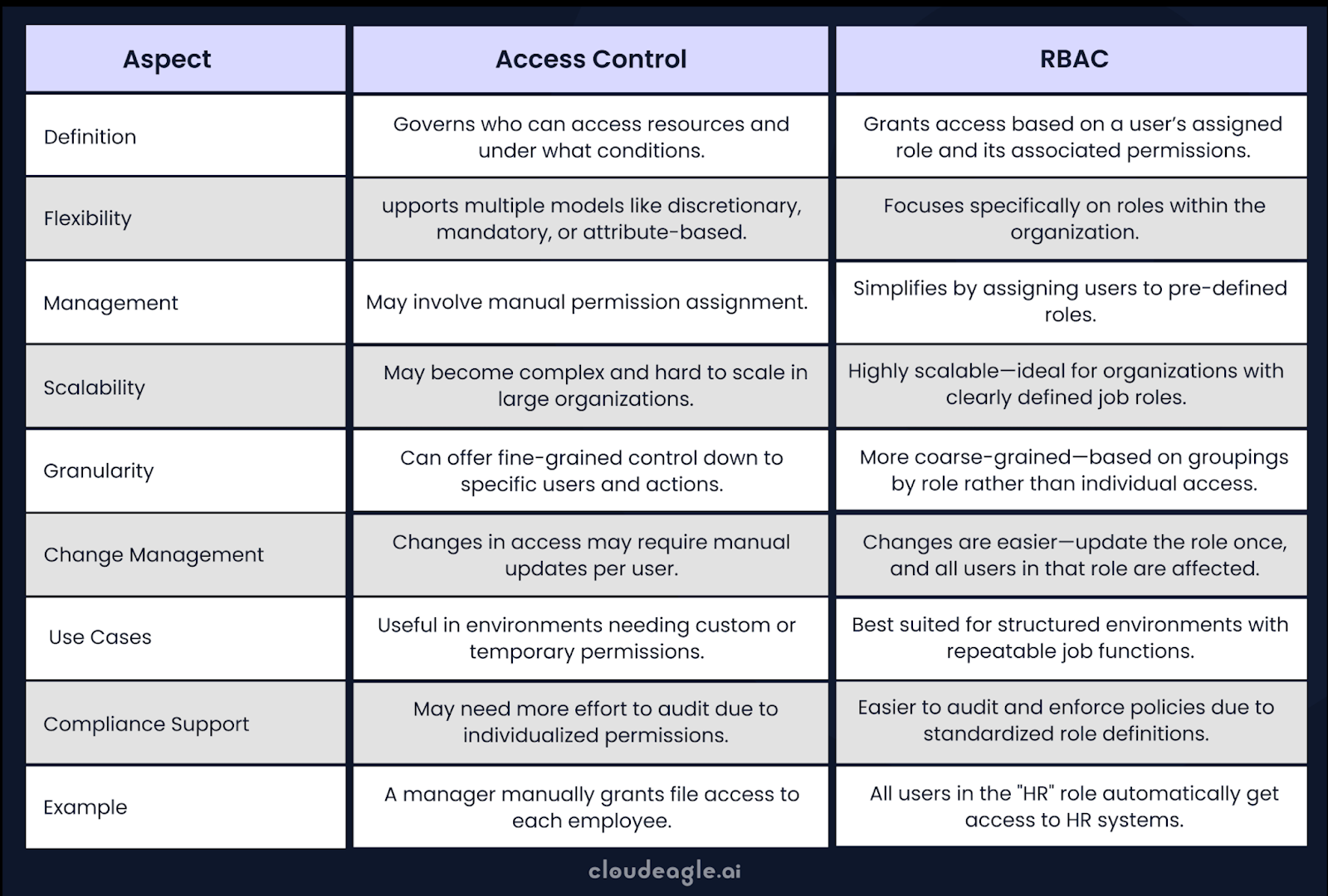
What is the Difference Between Access Control and RBAC?
Role-Based Access Control (RBAC) is a specific model within the broader concept of access control. Here’s how they differ:
What is Access Management?
Access management is the comprehensive process of controlling and monitoring user access to digital resources, systems, and data within an organization. It involves authenticating users, authorizing their permissions, provisioning access rights, and continuously managing these permissions throughout the user’s lifecycle.
A recent CloudEagle.ai IGA report reveals a critical issue: 48% of ex-employees retain app access even after termination. This makes it critical for enterprises to take the necessary steps to ensure access is revoked promptly and securely.
Access management ensures that the right individuals have the right access at the right time, while unauthorized users are kept out. This practice relies on technologies such as multi-factor authentication (MFA), single sign-on (SSO), identity providers, and user management software to streamline and secure access.
What are the Benefits of Access Management?
Implementing effective access management delivers multiple advantages:
- Enhanced Security: By verifying identities and enforcing access policies, access management reduces the risk of unauthorized access, insider threats, and data breaches. Features like MFA and adaptive access provide layered defenses.
- Operational Efficiency: Automating user onboarding, provisioning, and offboarding reduces administrative workload and accelerates access changes, enabling teams to focus on core tasks.
- Improved User Experience: Seamless authentication methods such as SSO simplify login processes, reducing password fatigue and support tickets.
- Regulatory Compliance: Access management maintains detailed audit trails and enforces consistent policies across systems, helping enterprises meet data protection regulations like GDPR, HIPAA, and SOC 2.
- Scalable Control: Supports diverse environments—cloud, on-premises, hybrid—and various user types including employees, contractors, and partners.
- Real-Time Monitoring: Detects unusual access patterns and triggers alerts or automated responses to mitigate threats proactively.
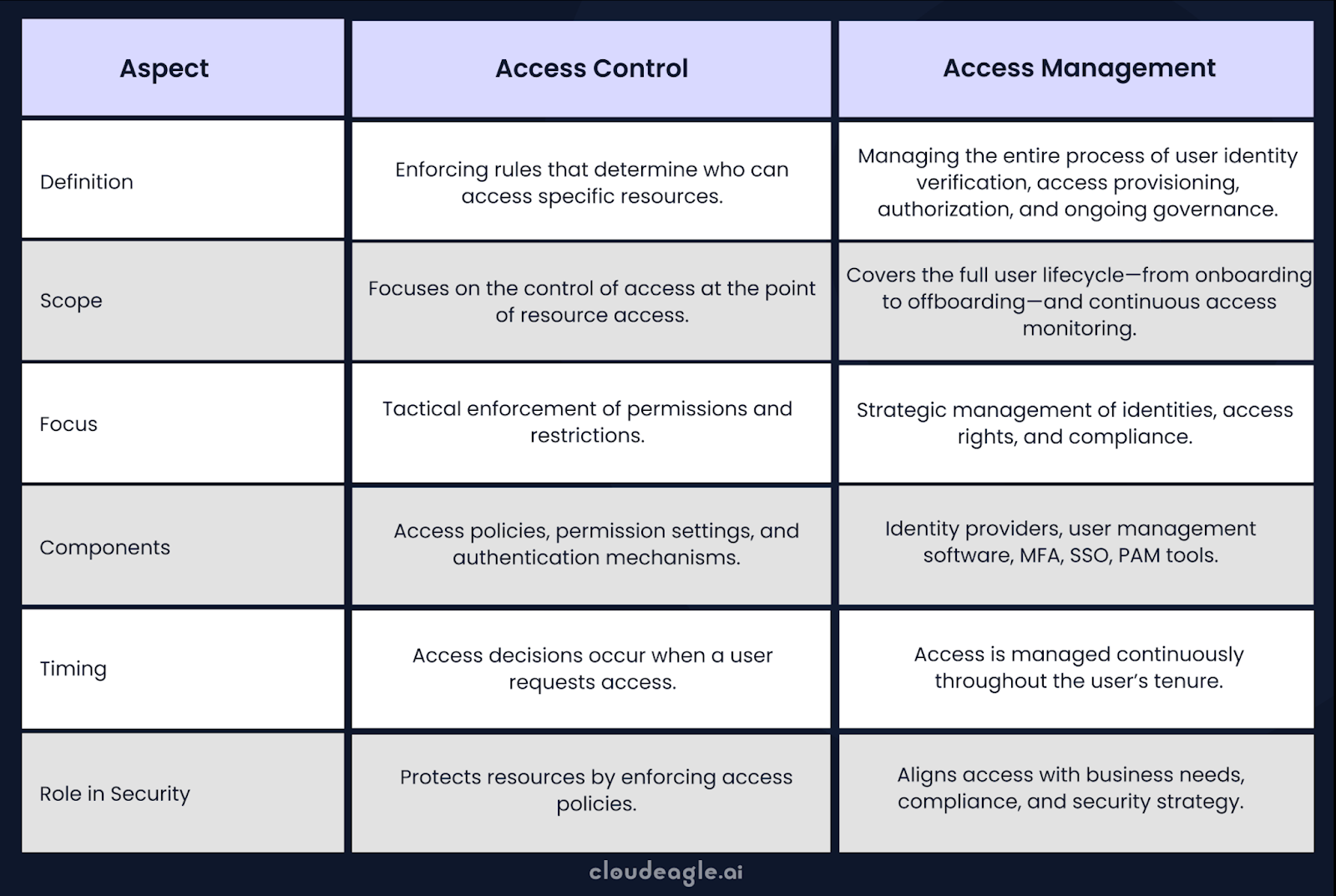
Access Control vs Access Management: What is the Difference?
While related, access control vs access management differ in scope: access control sets access rules, while access management handles the entire access process.
How Access Control and Access Management Work Together?
Access control and access management are two sides of the same coin in securing enterprise resources. While access control focuses on enforcing who can enter or use specific systems or data, access management oversees the entire process of managing user identities and their access rights throughout their lifecycle.
Together, they create a comprehensive security framework:
- Access control enforces permissions at the point of entry, ensuring that only authorized users gain access to resources based on policies such as mandatory access control versus role-based access control.
- Access management automates provisioning, authentication, and continuous monitoring using user management software and integrates with identity providers to keep access aligned with organizational changes.
This integration improves security by reducing risks such as orphaned accounts and insider threats, while streamlining operations through automation and centralized management.
For example, when an employee leaves, access management ensures their permissions are revoked promptly, and access control management enforces this restriction immediately.
Know this inspiring customer success story of how Treasure Data enhanced access management and reporting with CloudEagle.ai.
Why Understanding the Difference Matters?
Knowing the distinction between access control vs access management isn’t just a technical detail; it’s foundational to a secure and well-governed IT environment. Here's why it matters:
Improved Security Posture: Access control focuses on determining who can access which resources at any given moment. On the contrary, access management looks at the entire process of how access is granted, regularly reviewed, and eventually revoked.
Understanding both ensures you can:
- Prevent unauthorized or lingering access.
- Mitigate privilege creep (users retaining more access than they need).
- Protect sensitive data from internal and external threats.
Operational Efficiency: When you clearly define roles for access control and processes for access management, it allows automation to thrive. This helps your organization:
- Automate onboarding and offboarding of users.
- Set role-based or time-based access policies.
- Reduce manual work and errors across IT and HR workflows.
Regulatory Compliance: Data privacy laws like ISO 27001, SOC 2 Type II, GDPR, HIPAA, and SOC 2 require companies to know and control who accesses sensitive information. A clear separation between access control (enforcing rules) and access management (governing access lifecycles) helps:
- Maintain audit trails.
- Meet compliance checklists with ease.
- Prove proper controls during audits or assessments.
Better Resource Allocation: Without clear policies, IT teams waste time handling repetitive access requests or cleaning up after poor provisioning. When access control and management are well-structured:
- Teams can focus on higher-value initiatives like security enhancements.
- User provisioning and deprovisioning can be automated.
- Access review cycles become faster and less burdensome.
Holistic Security Strategy: Access control is the tactical layer that grants or denies access to systems and resources. Access management is the strategic layer, overseeing how access is handled throughout an employee's journey. Together, they enable:
- End-to-end governance of user access.
- Scalability as your organization grows.
- A defense-in-depth approach, covering both technical enforcement and process control.
How CloudEagle.ai Can Help You Manage Access Control?
CloudEagle.ai provides a single dashboard where you can see all user access across your SaaS applications. This means no more jumping between different tools to check permissions.

The platform integrates with over 500 SaaS apps, bringing everything into one centralized place. This helps your IT team quickly understand who has access to what and easily spot any unusual or risky permissions.
Here’s how the CloudEagle.ai helps you manage access to different apps:
Real-Time Monitoring and Instant Alerts
Security threats can happen anytime. CloudEagle.ai keeps an eye on access activity in real time. If someone tries to access a system they shouldn’t, or if there’s any suspicious behavior, the platform sends immediate alerts. This helps your security team act quickly before a small issue turns into a big problem.
Automated Provisioning and Deprovisioning
Onboarding new employees or contractors often means giving lots of access across many apps. And when someone leaves, you need to make sure their access is removed right away.

CloudEagle.ai automates these processes, granting access to the right tools when people join, and instantly removing permissions when they leave or change roles. This reduces human error and keeps your access list clean.

Know how JoVe Streamlined Employee Onboarding and Offboarding With CloudEagle.ai.
Principle of Least Privilege (PoLP)
CloudEagle.ai helps you apply the principle of least privilege, which means users only get the minimum access they need to do their job. This limits the chances of unauthorized data exposure. If an account is compromised, the damage is much smaller because the attacker’s access is limited.
Just-in-Time (JIT) Access for Temporary Needs
Sometimes, users require temporary access for a limited period, such as contractors or temporary staff working on specific projects. CloudEagle.ai’s IGA report reveals that 40% of organizations report users, especially contractors, continue to have access to SaaS applications even after their assignments have ended.
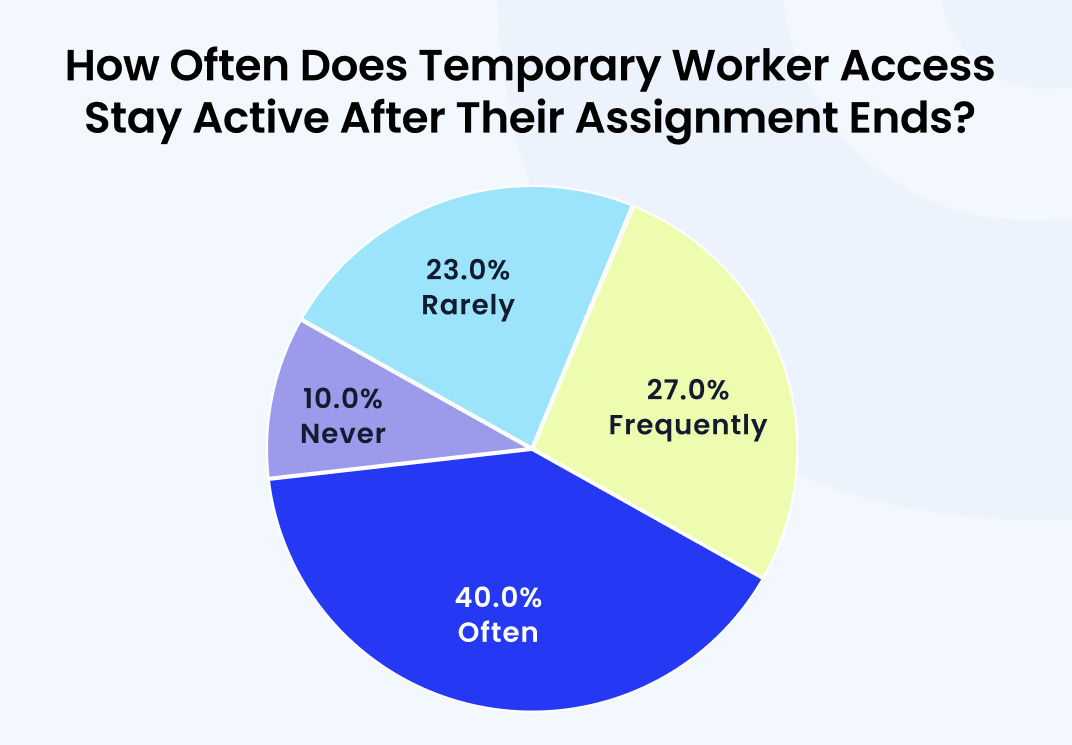
CloudEagle.ai offers Just-in-Time access, granting temporary permissions that automatically expire after the task is done. This helps prevent unnecessary long-term access which can be a security risk.
Role-Based Access Control (RBAC) for Efficient Management
Instead of managing access for each person individually, CloudEagle.ai lets you assign permissions based on roles like marketing, finance, or IT.

This makes permission management easier and scales well as your company grows. When someone changes jobs or teams, their access automatically updates to match their new role.
Privileged Access Management (PAM) for Sensitive Accounts
Some accounts have powerful permissions and need extra protection, like system administrators. CloudEagle.ai includes privileged access management features that put special controls on these accounts, monitor their use closely, and keep detailed logs. This reduces the risk of misuse or attacks involving powerful accounts.
Compliance Support with Automated Reporting
Meeting legal and industry requirements is easier with CloudEagle.ai. The platform automatically logs all access changes and activities, generating reports to support audits. This helps ensure you stay compliant with regulations like GDPR, HIPAA, or SOC 2, without the usual manual work and stress.

Conclusion
Think of access control and access management as two sides of the same coin. Access control focuses on the “who can access what,” while access management focuses on how access is granted, monitored, adjusted, and removed throughout a user’s time with the enterprise.
When you understand how they work together, you can build a security system that’s not just strong but also efficient that keeps threats out, supports day-to-day operations, and meets compliance standards without creating bottlenecks.
That’s where you need an access management tool like CloudEagle.ai. It simplifies access management by automating tasks such as provisioning and deprovisioning, enforcing role- and time-based access, and providing real-time visibility.
Ready to simplify and secure your access control and management?
Schedule a demo with CloudEagle.ai to streamline identity governance, boost SaaS security, and ensure compliance.
FAQs
1. What are the 4 types of access control?
The four main types are:
- MAC (Mandatory Access Control): Strict, centralized control for high-security environments.
- DAC (Discretionary Access Control): Access granted by data owners, more flexible.
- RBAC (Role-Based Access Control): Access based on user roles.
- ABAC (Attribute-Based Access Control): Access based on multiple attributes like location, time, or device.
2. What is user management and access control?
User management is creating and maintaining user accounts, while access control enforces what resources those users can access, protecting sensitive data and systems.
3. What are the 5 Ds of access control?
The 5 Ds are:
- Deter: Discourage unauthorized access.
- Detect: Identify suspicious activity.
- Deny: Block unauthorized access.
- Delay: Slow down intruders.
- Defend: Respond to security incidents.
4. What are the 3 A's of access control?
The 3 A's are:
- Authentication: Verifying user identity.
- Authorization: Granting access rights.
- Auditing: Tracking and reviewing access activities.
5. What is the difference between PBAC and RBAC?
- Policy-Based Access Control (PBAC): Uses dynamic policies considering multiple factors for access decisions.
- Role-Based Access Control (RBAC): Assigns access based on predefined user roles, simpler but less flexible.

%201.svg)







.avif)




.avif)
.avif)




.png)









