HIPAA Compliance Checklist for 2025

You might think giving employees easy access to tools like Slack, Microsoft Teams, and Google Workspace boosts productivity, but what if that same access is silently putting your organization at risk?
Studies show that the majority of data breaches occur due to misused or excessive user permissions, often from insiders who have more access than they truly need. In fact, 74% of enterprise data breaches involved privileged credential abuse, according to Tim Steinkopf, CEO of Centrify.
This is why user access review control is no longer optional. Regularly auditing who can access what ensures sensitive data stays secure, insider threats are minimized, and your organization remains compliant with regulations like SOX, HIPAA, and GDPR.
In this guide, we’ll explore the full user access review process, best practices, common challenges, and how tools like CloudEagle.ai can make reviews simpler and more effective.
TL;DR
- User Access Review Control ensures only authorized users access to critical systems.
- Structured review process reduces security risks, privilege creep, and compliance gaps.
- Best practices include automation, RBAC, least privilege, and periodic certifications.
- Challenges include large user bases, complex SaaS apps, and a lack of integration.
- CloudEagle.ai simplifies reviews with AI, real-time monitoring, and seamless SaaS integrations.
What Is User Access Review Control?
A user access review control is a formal process by which organizations periodically examine who has access to systems, applications, and data, ensuring that each user’s permissions align with their job responsibilities.
It involves evaluating roles, permissions, and access levels, identifying orphaned accounts, and mitigating risks associated with excessive or poor access.
The process is not limited to employees; non-human identities such as service accounts and API integrations also fall under scrutiny. For instance, a Slack bot integrated with sensitive HR data must have access monitored just like any employee account.
Neglecting these reviews can result in over-privileged accounts, creating potential entry points for cyberattacks.
Conducting user access reviews also provides a solid audit trail for compliance purposes. Whether an organization is bound by SOX, HIPAA, or GDPR, regulators increasingly expect evidence that access rights are regularly validated and any anomalies are addressed promptly.
Why User Access Review Matters for Compliance?
User access reviews are critical for compliance, as they ensure that only authorized personnel can access sensitive systems and data. By preventing privilege creep and minimizing insider threats, these reviews help organizations ensure compliance requirements such as HIPAA, GDPR, and SOX.
A well-structured user access review process ensures that employees, contractors, and service accounts have the right level of access, minimizing insider risks and maintaining regulatory compliance.
Preventing Unauthorized Access and Data Breaches
Unauthorized access continues to be a major cause of security breaches. Regular user access review control helps identify accounts with excessive permissions and remove them before they can be exploited.
For instance, a marketing employee retaining admin-level access to a Google Workspace drive could inadvertently expose confidential data if not monitored.
- Identify users with unnecessary permissions
- Revoke access for former employees promptly
- Monitor sensitive SaaS tools like Slack, Teams, and Google Workspace
- Reduce insider threat risks
“Identity remains one of the weakest links in any security ecosystem. Continuous identity validation and access reviews help prevent sensitive data exposure and reduce insider risks.”
— Nick Kathmann, Chief Information Security Officer, LogicGate
Meeting Regulatory Requirements (SOX, HIPAA, GDPR)
Organizations must comply with multiple regulations that mandate controlled access to sensitive data. SOX requires that only authorized personnel access financial reporting systems, HIPAA compliance emphasizes safeguarding patient records, and GDPR mandates strict access control over personal data.
Conducting structured user access reviews demonstrates due diligence and regulatory adherence.
- Ensure access aligns with job roles for compliance
- Limit sensitive data access to authorized personnel
- Maintain audit-ready documentation
- Support SOX, HIPAA, and GDPR requirements
Strengthening Overall Security Posture
Beyond regulatory compliance, periodic user access reviews strengthen the organization’s overall security posture. Excessive permissions, or “permission creep,” in SaaS tools like Slack or Microsoft Teams can create vulnerabilities. Regular reviews reduce the attack surface, enabling faster detection of anomalies and incidents.
- Remove excess permissions to minimize the attack surface
- Prevent “permission creep” over time
- Track roles for faster incident response
- Strengthen security posture with regular user access reviews
80% of data breaches are caused by excessive or outdated user permissions, emphasizing the critical importance of conducting regular user access reviews to prevent unauthorized access and protect sensitive organizational data
What Are the Core Components of an Effective User Access Review?
An effective user access review clearly defines its scope, assesses users, enforces RBAC and least privilege, follows regular intervals, documents findings, leverages automation, and has a clear remediation process to ensure only authorized access.
Identifying Critical Systems and Applications
Start by identifying which systems and applications are critical for business operations, especially high-risk SaaS tools like Google Workspace, Salesforce, and HR systems. Prioritize sensitive systems to focus review efforts efficiently.
Key Points:
- Classify systems by sensitivity and business impact
- Prioritize high-risk SaaS tools
- Focus on applications with sensitive or regulated data
- Allocate review resources based on system criticality
Assigning Review Owners and Responsibilities
Designate responsible individuals, such as IT security managers or compliance officers, to ensure accountability in each user access review process. Review owners' track actions and report outcomes.
Key Points:
- Assign owners for each system or application
- Ensure owners understand responsibilities and deadlines
- Follow a user access review policy
- Document ownership for audit purposes
Reviewing Roles, Permissions, and Access Levels
Check that users’ access aligns with their current job roles. Include shared, service, and temporary accounts to prevent privilege escalation and maintain proper access control.
Key Points:
- Validate user roles and permissions regularly
- Apply Role-Based Access Controls to simplify access management
- Include shared and service accounts in the review
- Remove unnecessary or outdated permissions
Documenting and Reporting Review Outcomes
Maintain proper records of review findings, corrective actions, and unresolved issues. Use user access review software for automated reporting and audit-ready dashboards.
Key Points:
- Document all findings and actions taken
- Use user access review software for automation
- Maintain audit-ready records for compliance
- Track and remediate outstanding issues
Step-By-Step User Access Review Process
A step-by-step user access review involves inventorying users and assets, collecting current access data, defining review criteria, collaborating with managers and system owners, revoking unnecessary access, and documenting all changes for audits. Reviews should be scheduled and repeated regularly to maintain security and compliance.
Step 1: Define Review Scope and Frequency
Start by deciding which systems, applications, and user groups are included in the review. Critical SaaS tools like Slack, Microsoft Teams, and Google Workspace may require quarterly reviews, while less sensitive systems can be audited annually. Tiered review schedules help focus on high-risk areas first.
Key Points:
- Identify critical systems and sensitive data repositories
- Determine review frequency based on risk level
- Prioritize high-risk SaaS tools first
- Define user groups included in the review
- Document scope for compliance and audit purposes
Step 2: Gather User Access Data
Collect comprehensive access data from all systems, including SaaS tools, internal apps, and shared accounts. Modern user access review software centralizes permissions, enabling a unified view across multiple platforms. Accurate data collection is essential for identifying over-privileged or dormant accounts.
Key Points:
- Aggregate permissions from multiple SaaS applications
- Include shared and service accounts
- Use user access review software for efficiency
- Ensure data is up-to-date before validation
- Maintain a central repository for audit purposes
Step 3: Validate Access Against Job Roles
Compare the collected access data with current job descriptions and roles. Employees moving between departments should have their access updated immediately to prevent unnecessary exposure. Role-based access control (RBAC) simplifies this by aligning permissions with standardized role profiles.
Key Points:
- Cross-check user access against current job roles
- Adjust permissions for role changes promptly
- Use RBAC to standardize access levels
- Identify dormant or inappropriate accounts
- Reduce insider threat risks by aligning access with duties
Step 4: Remove or Modify Excess Permissions
Apply the principle of least privilege by removing unnecessary permissions. Automation tools can flag accounts with excessive access in Slack, Teams, or Google Workspace for immediate remediation, ensuring users only have what they need to perform their job.
Key Points:
- Remove permissions not aligned with current roles
- Modify over-privileged accounts immediately
- Automate detection with user access review software
- Prevent privilege creep in SaaS tools
- Minimize risk of accidental or malicious data exposure
Step 5: Document Findings and Close Gaps
Finally, document all findings, including over-privileged accounts, misaligned roles, and corrective actions taken. Scheduling follow-up reviews ensures that gaps remain closed and controls stay effective over time, supporting ongoing compliance with SOX, HIPAA, and GDPR.
Key Points:
- Record review outcomes and corrective actions
- Maintain audit-ready documentation for compliance
- Schedule follow-up reviews for gap closure
- Track progress in user access review software
- Ensure continuous improvement of access controls
What Are the Best Practices for Access Review Controls?
Best practices for access review controls include using role-based access control (RBAC), enforcing least privilege, automating reviews when possible, and holding managers accountable for team access.
Additional actions include setting a regular review schedule, keeping detailed audit trails, continuously improving documentation, and educating employees on their security responsibilities.
Automate With Identity Management Tools
Automation streamlines the user access review process, enabling centralized collection of access data, real-time alerts for over-privileged accounts, and audit-ready reporting. Modern user access review software integrates with SaaS platforms like Slack, Microsoft Teams, and Google Workspace, reducing human errors and manual workload.
Actionable Tips:
- Use software to automate data aggregation
- Generate real-time alerts for unusual access patterns
- Integrate multiple SaaS tools for centralized monitoring
- Save time and improve review accuracy
- Ensure documentation aligns with your user access review policy
Organizations that automate their user access reviews can save up to 70% of the time compared to manual spreadsheet-based processes, reducing errors, improving efficiency, and ensuring compliance with regulatory standards.
“Automating user access reviews can reduce audit preparation time by up to 70%,” according to SafePaaS, highlighting how AI-driven user access review software can streamline processes, minimize errors, and strengthen compliance.
Adopt Role-Based Access Control (RBAC)
RBAC standardizes access permissions based on job roles, simplifying the user access review process. By mapping roles to predefined access levels, organizations can ensure users have only the access necessary to perform their duties, reducing the risk of insider threats.
Actionable Tips:
- Map all user roles to standard access levels
- Apply RBAC across SaaS apps like Teams, Slack, and Google Workspace
- Simplify access audits by aligning roles and permissions
- Reduce administrative complexity in large enterprises
- Support compliance with the internal user access review policy
Enforce the Principle of Least Privilege
Granting minimal access necessary for job responsibilities is key to reducing security risks. Regular user access reviews ensure employees, contractors, and service accounts do not retain unnecessary permissions.
Actionable Tips:
- Review and remove excess permissions regularly
- Adjust temporary access immediately after project completion
- Monitor SaaS accounts for privilege creep
- Limit admin-level access to sensitive applications
- Strengthen overall organizational security posture
Conduct Periodic Access Certifications
Access certifications validate that permissions remain appropriate over time. Scheduling regular reviews helps identify outdated or misaligned permissions, ensuring compliance with SOX, HIPAA, GDPR, and internal policies.
Actionable Tips:
- Schedule quarterly or annual access certifications
- Verify user access for critical SaaS applications
- Document certification outcomes for audits
- Update roles and permissions as business needs evolve
- Track trends to improve future user access review control cycles
Integrate SaaS Tools Into Reviews
Integrating all enterprise SaaS tools into your user access review process ensures comprehensive visibility. Platforms like Slack, Teams, and Google Workspace often contain sensitive data, making it essential to track permissions consistently.
Actionable Tips:
- Connect all SaaS tools to the review process
- Maintain a unified dashboard for access monitoring
- Identify high-risk accounts and take corrective action
- Reduce the likelihood of accidental or malicious data exposure
- Streamline user access review software, reporting, and documentation
What Are the Common Challenges in User Access Reviews?
Common challenges in user access reviews include the time and effort of manual processes, human errors, limited visibility across disconnected systems, and a lack of stakeholder buy-in. High employee turnover can lead to “rubber-stamped” approvals, while certification fatigue and the administrative burden of maintaining detailed documentation further complicate compliance.
Handling Large Enterprise User Bases
- Problem: Managing thousands of users across multiple SaaS platforms like Slack, Microsoft Teams, and Google Workspace can be overwhelming.
- Impact: Manual reviews become slow, error-prone, and incomplete, increasing the risk of insider threats.
- Solution: Use user access review software to automate large-scale reviews, segment users by roles, and maintain audit-ready reports.
Tips:
- Prioritize critical roles and high-risk users
- Break down reviews into manageable segments
- Automate repetitive tasks to reduce errors
- Maintain continuous visibility across SaaS tools
- Ensure all actions are logged for compliance
Dealing With Complex Application Environments
- Problem: Organizations often use multiple SaaS apps, legacy systems, and internal platforms, each with different access models.
- Impact: Risk of outdated or misaligned access increases, creating security gaps.
- Solution: Consolidate access data, standardize review procedures, and prioritize high-risk applications in your user access review process.
Tips:
- Map permissions consistently across all applications
- Focus on sensitive or high-risk systems first
- Use dashboards for centralized monitoring
- Reduce discrepancies caused by different access models
- Ensure all SaaS tools are included in periodic reviews
Ensuring Stakeholder Accountability
- Problem: Undefined ownership leads to delayed or incomplete reviews.
- Impact: Security gaps persist, and compliance with internal policies and regulations is compromised.
- Solution: Assign clear review owners, track their actions, and document responsibilities in a user access review policy.
Tips:
- Assign owners for each system and SaaS application
- Set deadlines and escalation procedures
- Document ownership and accountability
- Encourage collaboration between IT and business teams
- Track review completion and remediate gaps
Lack of Automation and Integration
- Problem: Manual processes and disconnected SaaS tools make reviews inefficient and error-prone.
- Impact: Accounts may be overlooked, permissions may be outdated, and insider threat risks rise.
- Solution: Implement automated user access review software and integrate all critical SaaS tools for centralized monitoring.
Tips:
- Use automation to track changes in permissions
- Integrate multiple platforms for unified reporting
- Reduce human errors and missed accounts
- Maintain dashboards for real-time visibility
- Ensure audit-ready documentation for compliance
How CloudEagle.ai Can Simplify Access Reviews
Managing SaaS access manually is time-consuming, error-prone, and inefficient. CloudEagle.ai streamlines user access review control with AI-driven automation, real-time monitoring, and seamless integrations, helping organizations maintain security and compliance effortlessly.
Automating Access Reviews for Improved Efficiency
Many organizations still rely on spreadsheets and manual approval chains for user access reviews, which can cause delays and create security gaps. CloudEagle.ai eliminates these inefficiencies by:
- Automating Review Cycles – Triggers periodic user access reviews automatically and sends approval requests to managers, reducing administrative overhead.
- Centralized Dashboard – Provides IT teams with a single view to track, approve, or revoke user access across multiple SaaS applications like Slack, Microsoft Teams, and Google Workspace.
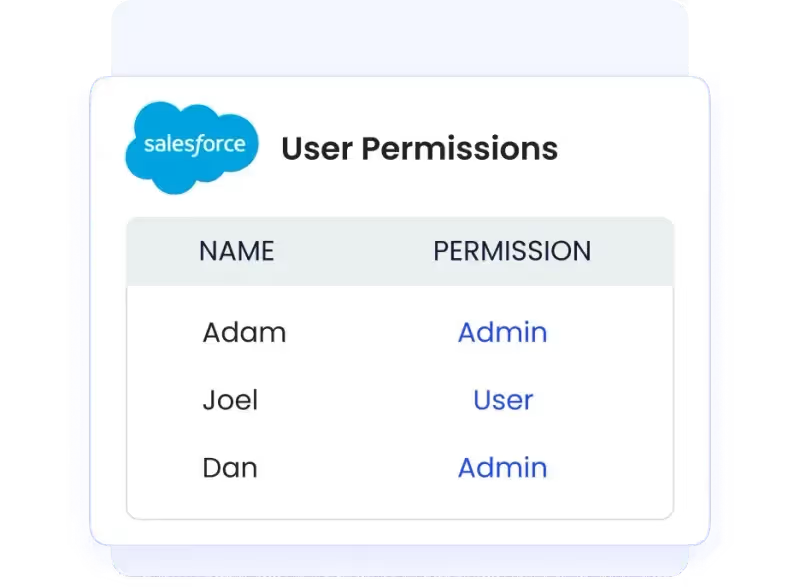
Automation ensures user access review processes are conducted consistently, accurately, and on schedule.
AI-Driven Insights to Identify Risky Access and Over-Provisioning
Traditional access reviews often miss over-privileged accounts or abnormal user behavior. CloudEagle.ai leverages AI and machine learning to enhance user access review software capabilities:
- Detect Anomalies in Access Patterns – Flags users with excessive or unnecessary access, highlighting high-risk permissions.
- Enforce Least Privilege Access – Recommends corrective actions to reduce over-provisioning and ensure security best practices are followed.

By leveraging AI, organizations can proactively mitigate risks, prevent unauthorized access, and maintain robust user access r
eview controls.
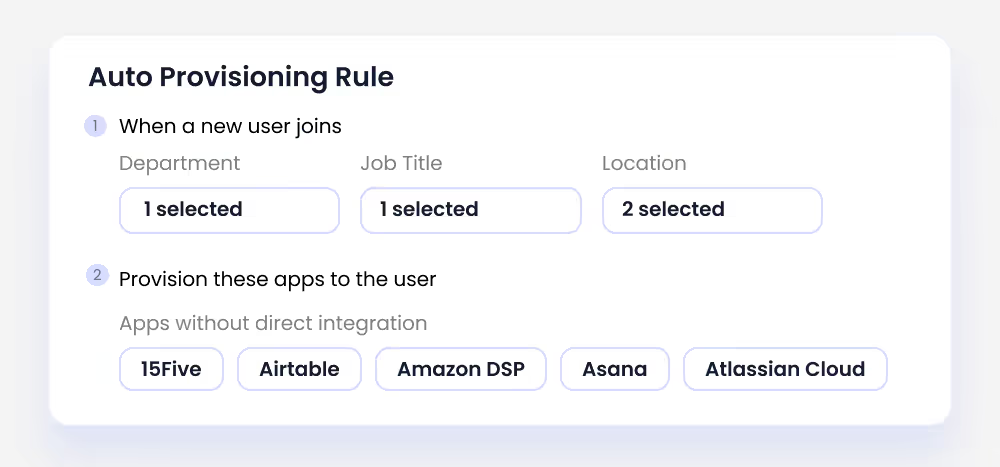
Seamless Integration With SaaS Applications for Real-Time Monitoring
Gaining visibility across multiple SaaS platforms can be challenging. CloudEagle.ai integrates with leading applications to:
- Monitor Access in Real Time – Tracks who has access to what across all platforms, ensuring continuous governance.
- Automate Permission Revocation – Automatically removes unnecessary permissions when employees change roles or leave, reducing security exposure.
These integrations strengthen the user access review process by ensuring timely and accurate access management.
Compliance Enforcement With Automated Workflows
Meeting regulatory requirements can be overwhelming without proper tools. CloudEagle.ai simplifies compliance by:
- Pre-Configured Compliance Policies – Aligns with SOX, HIPAA, GDPR, and other frameworks to ensure audits are always up to date.
- Audit-Ready Reports – Generates detailed logs and reports for internal assessments and external compliance audits, eliminating manual effort.

With CloudEagle.ai, organizations can maintain continuous compliance, minimize security risks, and optimize user access reviews across all SaaS applications with minimal effort.
Final Words
A strong user access review control ensures only authorized users access to critical systems, reducing security risks and helping maintain compliance with SOX, HIPAA, and GDPR. Following a structured user access review process keeps access aligned with job roles and responsibilities.
Best practices like automation, RBAC, least privilege enforcement, and periodic certifications streamline reviews and improve accountability. Overcoming challenges like large user bases and complex SaaS environments ensures robust and effective access governance.
When managing SaaS access becomes overwhelming, this is where CloudEagle.ai steps in. It simplifies user access review control, automates reviews, detects risky permissions, and integrates seamlessly with tools like Slack and Microsoft Teams.
Book a free demo today and stay compliant, reduce security risks, and streamline access management.
Frequently Asked Questions
- What type of control is a user access review?
A user access review is a preventive and detective control that ensures users have appropriate permissions, helping reduce security risks and maintain compliance. - What is a UAR in compliance?
A UAR (User Access Review) is a compliance process that validates user permissions, ensuring access aligns with roles and regulatory requirements like SOX, HIPAA, or GDPR. - What are user access controls?
User access controls are security measures that define who can access systems, apps, or data, ensuring only authorized users perform specific actions. - How to audit user access?
Audit user access by collecting permissions data, comparing it with roles, checking for anomalies, and documenting findings for compliance and security reviews. - How to do a user access review?
Perform a user access review by defining the scope, gathering access data, validating against roles, removing excess permissions, and documenting outcomes for audit readiness.

%201.svg)










.avif)




.avif)
.avif)




.png)









