HIPAA Compliance Checklist for 2025

When employees switch roles, leave the company, or gain new responsibilities, their access privileges often change. But without proper oversight, unused or privilege creep can linger, becoming a hidden security risk.
This is where User Access Review audits step in, ensuring that access rights align with business needs. The importance of these audits is underscored by the numbers. According to a 2023 Ponemon Institute report, 62% of organizations experienced data breaches caused by misuse of employee access rights.
This highlights how critical is to automate user access reviews to prevent unauthorized exposure of sensitive information. In this guide, we’ll explore what user access review audits are, why they matter for compliance, how they work, and best practices to implement them effectively.
TL;DR
- User Access Review (UAR) audits validate that employee permissions align with current roles, reducing security risks and privilege creep.
- Critical for compliance, UARs help organizations meet SOX, HIPAA, PCI DSS, and other regulatory requirements while providing audit-ready documentation.
- Enhances security, preventing insider threats, unauthorized access, and potential data breaches by continuously monitoring and revoking excessive privileges.
- Improves visibility and operational efficiency, giving IT and management clear insight into who has access to which systems and why.
- Automation tools like CloudEagle.ai streamline audits, provisioning, deprovisioning, and privileged access management, saving time and ensuring consistent, secure access governance.
What is a User Access Review Audit?
A User Access Review audit is a structured process where organizations evaluate who has access to which systems, applications, and data. The goal is to confirm that each user’s permissions match their current job responsibilities, reducing unnecessary exposure and strengthening SaaS compliance.
Key elements of a UAR audit include:
- Access Validation: Ensuring users only have access to the applications, databases, and files required for their roles.
- Role Alignment: Reviewing whether access rights are consistent with job functions and updated after promotions, transfers, or exits.
- Risk Identification: Spotting excessive privileges, dormant accounts, or unauthorized access attempts that could be exploited.
- Regulatory Compliance: Meeting frameworks with user access review software such as SOX, HIPAA, or GDPR that mandate regular access reviews.
- Documentation & Reporting: Maintaining detailed logs and reports to demonstrate compliance during internal or external audits.
For example, in 2024, a U.S. healthcare provider discovered that over 300 inactive employee accounts still had access to patient records. A UAR audit helped revoke those permissions before regulators flagged the issue, avoiding potential HIPAA violations and heavy fines.
Why Are User Access Review Audits Important?
User access review audits safeguard against hidden risks. When employees accumulate unnecessary access, they create openings for both internal misuse and cloud security threats. Regular reviews close these gaps before they escalate into threats.
1. Strengthening Identity and Access Management (IAM)
User access review audits reinforce IAM by ensuring accounts align with business needs and compliance standards. These audits not only verify permissions but also highlight areas where controls can be strengthened for long-term resilience.
Eliminating Excessive Privileges
Reviews uncover users with access rights beyond their roles, reducing the attack surface significantly. They also help enforce least privilege access, a core IAM principle.
Validating Role Assignments
By checking if role-based permissions remain accurate, audits prevent outdated access from persisting. This avoids gaps that hackers or insiders could exploit.
Ensuring Lifecycle Consistency
Access is aligned with employee lifecycle events, such as onboarding, promotions, or offboarding. User access review software prevents dormant accounts from becoming backdoors.
2. Preventing Insider Threats and Unauthorized Access
Not all risks come from external attackers; insiders often pose greater dangers because they already have legitimate access. User access review audits detect anomalies early, ensuring that employees and contractors do not retain access they no longer need.
When reviews are neglected, terminated employees or role-shifters may retain sensitive access, creating hidden entry points. Detecting and revoking these rights is critical for SaaS data loss prevention or misuse.
As cybersecurity expert Bruce Schneier once said,
“The user is going to pick dancing pigs over security every time.”
This highlights why ongoing checks are essential, where trusting users alone isn’t enough; controls must enforce security.
3. Meeting SOX, HIPAA, and PCI DSS Requirements
User access review audits are also compliance enablers. Frameworks like SOX, HIPAA, and PCI DSS all mandate periodic verification of user privileges. Failing to conduct reviews can result in fines, audits, and reputational damage.
Audits demonstrate accountability by showing that organizations actively manage and document user access. This builds confidence with regulators and external auditors.
According to Journalwjaets, 67% of organizations face significant gaps in privileged access management. Regular reviews directly address this issue, reducing risks of non-compliance.
4. Enhancing Visibility Into Access Privileges
Access reviews give enterprises a clear picture of who has access to what, a view that many organizations lack. With this visibility, security teams can act decisively rather than reactively, reducing blind spots across critical systems.
- Mapping Access Across Systems: Audits consolidate data from multiple platforms, revealing permissions that are often siloed. This unified perspective enables faster remediation.
- Spotting Anomalies Early: When unusual privileges are identified quickly, risks of misuse or data exposure drop dramatically. This proactive stance strengthens defenses before causes of data breaches occur.
- Enabling Transparent Oversight: Executives and auditors gain confidence when clear reports show justified access. This transparency builds trust internally and externally.
5. Reducing Operational and Security Risks
Unchecked access permissions create operational inefficiencies and serious security vulnerabilities. Access reviews provide assurance that employees only retain what they need, keeping sensitive systems protected.
Operational risks also decrease because fewer unauthorized users access critical tools, which minimizes downtime and accidental misconfigurations. Reviews therefore reduce both security and business continuity risks.
What is the User Access Review Audit Process?
The user access review audit process is a structured approach to validating whether employees have appropriate system permissions. It ensures that access rights match job responsibilities and regulatory requirements.
1. Defining Scope and Objectives for the Audit
Every access review begins with a clear scope and defined objectives. Enterprises must decide which systems, applications, and users fall under review.
- Establishing boundaries: Decide if the audit covers enterprise-wide access or focuses on high-risk systems.
- Clarifying objectives: Align the user access review software goals with security and compliance or internal policy requirements.
- Stakeholder alignment: Involve IT, compliance officers, and business leaders to ensure goals are practical and measurable.
2. Gathering and Validating Access Data
Accurate data collection ensures that access reviews are meaningful. This step involves consolidating permissions from multiple sources and validating their accuracy.
The process starts with pulling information from HR systems, identity providers, and application-level logs. Each dataset must be cleaned and standardized for consistency. Without this, reviewers may miss critical red flags.
“In my experience, 60% of access errors stem from outdated records not being cleaned up,”
said Alex Simons, Corporate VP at Microsoft Identity. This highlights why validation is as important as collection.
Finally, enterprises should run automated tools to spot anomalies such as duplicate accounts or inactive users with active privileges. The combination of manual oversight and automation significantly reduces data errors.
3. Reviewing Access Against Roles and Policies
Once data is validated, managers and compliance teams compare user permissions with established access policies. This ensures employees only have access tied to their role and failing to do so can lead to chaos. In 2024, Security Magazine revealed that 90% of organizations experienced at least one identity-related incident
First, the audit compares current access rights to role-based models. Any excess access is flagged for review. For example, a sales executive having database admin rights would be considered a violation.
Next, policies tied to regulatory frameworks like SOX or HIPAA compliance are applied. This double-check ensures compliance beyond internal rules. Automated alerts can streamline this process for recurring audits.
Finally, stakeholder reviews play a role. Department heads must approve or reject flagged permissions, ensuring business context is considered before changes are enforced.
4. Remediation of Access Violations
When issues are found, remediation ensures risks are immediately addressed. This may involve revoking unnecessary access, restructuring permissions, or tightening approval workflows.
Organizations should also document corrective actions to track progress and prevent recurrence. In many cases, automation tools accelerate remediation by automatically disabling orphaned accounts or escalating high-risk issues.
5. Documenting Results and Reporting to Management
Transparency is vital, and every finding must be documented for audit readiness. Reports help management take informed action and demonstrate compliance to regulators.
A good report doesn’t just state violations; it categorizes them by severity and impact. This allows executives to prioritize remediation and allocate resources efficiently. Clear evidence trails also build regulator confidence.
Business Standard revealed that 74% of enterprises prefer real-time auditing and reporting. Addressing this weakness with structured reporting tools can drastically improve audit outcomes.
6. Scheduling Regular Audit Cycles
Audits aren’t one-time events. Scheduling them regularly ensures ongoing compliance and proactive risk management.
- Quarterly reviews: Common for financial and healthcare organizations.
- Annual audits: Suitable for organizations with lower compliance requirements but still needing oversight.
- Ad-hoc checks: Triggered after major security incidents or organizational changes.
- Policy alignment: Each cycle should adapt to evolving regulatory requirements.
- Continuous monitoring: Modern identity and access management tools allow near-real-time detection between cycles.
Common Challenges in User Access Review Audits
Even well-planned access review audits come with obstacles that can slow progress or weaken outcomes. These challenges often arise from the complexity of modern IT environments and the scale of user access data.
- Data Overload: Large enterprises may have thousands of users and apps, making it difficult to consolidate access records.
- Inconsistent Records: Outdated or mismatched data across HR, IAM, and app systems lead to incomplete reviews.
- Lack of Business Context: Reviewers often struggle to decide if access is truly justified without knowing job-specific needs.
- Employee Pushback: Users may resist access revocations, especially if they believe it impacts productivity.
- Audit Fatigue: Teams conducting frequent reviews risk treating them as checkbox exercises rather than meaningful security controls.
These challenges highlight why automation, clear policies, and cross-team collaboration are essential to make access reviews both accurate and efficient.
Using CloudEagle.ai to Automate User Access Management
CloudEagle.ai simplifies how you manage and optimize SaaS tools from discovery to renewal, while keeping license spend and governance in check.
Its built-in identity and access management capabilities give you full visibility into user roles, permissions, and app access from one centralized dashboard.
With 500+ integrations across SSO, HRIS, and finance systems, you can take control of SaaS access, monitor usage patterns, and enforce the right permissions, all without switching platforms.
Automated App Access Reviews
CloudEagle.ai access management solutions takes the manual work out of SOC 2 and ISO 27001 audit reviews. Thus, no more scrambling to audit apps or prove deprovisioning.

By centralizing key systems into a single, easy-to-navigate dashboard, it simplifies compliance and helps you stay audit-ready without the last-minute chaos.
Just-in-Time Access
CloudEagle.ai lets you grant time-based access to critical systems, automatically revoking permissions when the job’s done.
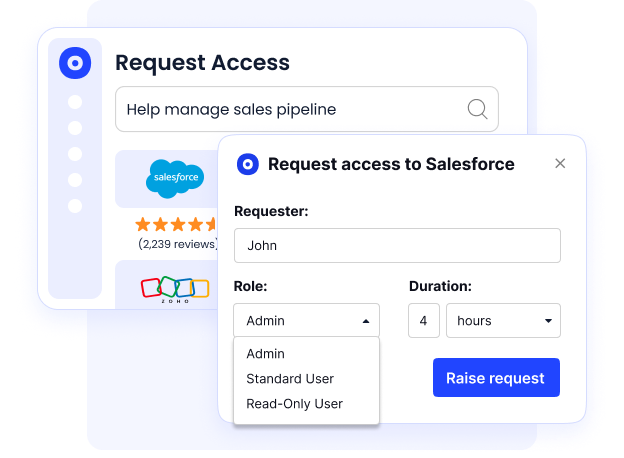
It’s a smart way to reduce access creep, perfect for contractors, freelancers, and temporary staff, giving them exactly what they need for exactly as long as they need it without constant manual intervention.
Access Control
CloudEagle.ai provides identity and access, which gives you complete visibility into who has access to what, why they have it, and how it’s being used, all from one place.
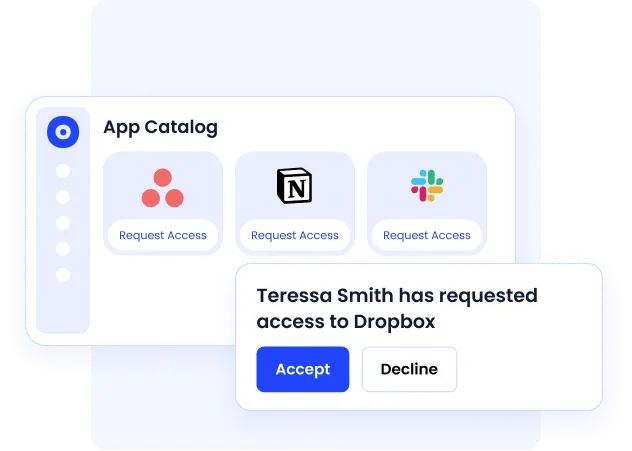
From intake to provisioning to deprovisioning, you can manage the entire access lifecycle through a centralized system. And when audit time rolls around, exporting detailed access logs is fast without delays.
Privileged Access Management
CloudEagle.ai simplifies privileged access management by automating how elevated access is granted sothat only the right people reach critical systems like AWS and NetSuite.
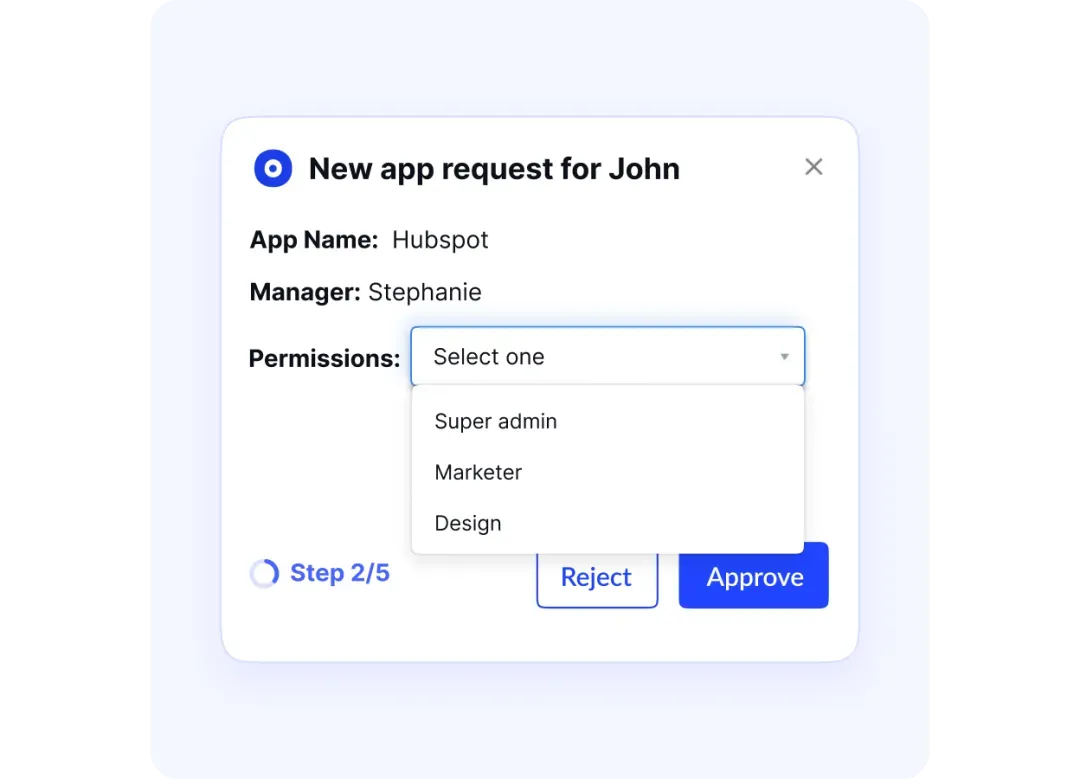
With real-time monitoring and built-in safeguards, you can strengthen security and compliance without adding to your team’s workload—or leaving room for manual mistakes.
Automated User Provisioning and Deprovisioning
Managing access manually opens the door to errors, delays, and security risks, especially during onboarding and offboarding. Users may end up with too much access or not enough to do their jobs effectively. And if accounts aren’t deprovisioned properly, former employees could retain access to sensitive systems.
CloudEagle.ai automates access throughout the employee lifecycle, assigning the right permissions from day one and revoking them instantly when someone leaves or goes inactive. It speeds up onboarding, reduces manual work, and keeps your environment secure and compliant.
Alice Park from Remediant saw this firsthand. What used to take hours of app-by-app deprovisioning is now handled in minutes through CloudEagle’s automated workflows.
Conclusion
User access review audits are more than just a compliance requirement. By regularly validating who has access to what, enterprises can reduce risk, improve visibility, and maintain strong cloud access governance across all systems.
But manual audits are time-consuming and error-prone. That’s where automation comes in. Platforms like CloudEagle.ai streamline the entire review cycle. This helps security and compliance teams save time while ensuring no risky access slips through.
FAQs
1. What is the user access review process?
The user access review process involves verifying employee access rights to ensure they align with job roles and responsibilities. It includes reviewing access logs, removing unnecessary privileges, and documenting compliance findings.
2. What is the difference between SAR and UAR?
SAR (System Access Review) focuses on access to specific systems or applications, while UAR (User Access Review) evaluates all access privileges a user has across systems. UAR is broader, ensuring no excessive or conflicting rights exist.
3. What is the purpose of the access review audit?
The primary purpose is to prevent unauthorized access, reduce security risks, and comply with regulations like SOX, HIPAA, or PCI DSS. It ensures that users only have the access they need, and nothing more.
4. How often should user access reviews be performed?
Best practice suggests quarterly reviews, though frequency can vary depending on industry regulations and organizational risk appetite. High-risk industries, such as finance and healthcare, may require monthly or even continuous monitoring.
5. Is a user access review a detective control?
Yes. User access reviews are considered a detective control because they identify inappropriate access after it occurs. Combined with preventive controls, they help strengthen overall identity and access management.

%201.svg)









.avif)




.avif)
.avif)




.png)









