HIPAA Compliance Checklist for 2025

As organizations adopt hybrid work, multi-cloud, and SaaS-first environments, identity becomes the new security perimeter. Yet, identities are increasingly exploited in cyberattacks, making Identity Security Posture Management (ISPM) critical for modern risk reduction.
But knowing your security posture isn’t enough. You need to assess it rigorously. That’s where security risk assessment in ISPM plays a vital role. It helps uncover hidden vulnerabilities, gauge exposure to threats, and prioritize mitigation before attackers strike.
In this blog, we’ll explore:
- What ISPM is
- Why security risk assessments are essential
- The step-by-step assessment process
- Common vulnerabilities to watch out for
- How CloudEagle helps organizations secure their identity fabric
TL;DR
- As organizations move to hybrid, multi-cloud, and SaaS-first models, identity becomes the primary attack surface, making ISPM essential for securing access and managing identity-related risks.
- Even the best ISPM tools need regular security risk assessments to uncover hidden vulnerabilities like orphaned accounts, privilege creep, and misconfigurations that attackers exploit.
- Effective ISPM risk assessment involves mapping all identities, classifying vulnerabilities, analyzing threat paths, evaluating existing controls, and prioritizing mitigation based on risk scores.
- Risk assessments support compliance with SOX, HIPAA, ISO, and NIST while embedding identity governance into daily operations like onboarding, role changes, and M&A activities.
- CloudEagle.ai enhances ISPM with real-time visibility, AI-powered risk scoring, orphaned account cleanup, automated access reviews, and compliance reporting, helping organizations reduce identity threats at scale.
What is Security Risks Assessment?
A security risk assessment is a process to identify, analyze, and evaluate potential threats and vulnerabilities that could negatively impact an organization's assets, including information, technology, personnel, and physical infrastructure. It involves systematically measuring the probability and consequences of these risks to develop strategies for mitigation or management.
What is Identity Security Posture Management (ISPM)?
Identity Security Posture Management (ISPM) is a cybersecurity framework that continuously monitors and manages the risk associated with identity and access across an organization’s digital ecosystem.
Unlike traditional IAM, which focuses on who can access what, ISPM focuses on how risky that access is, by factoring in misconfigurations, overprovisioning, privilege escalation, and more.
ISPM combines:
- Identity context (who/what)
- Access patterns (when/where)
- Risk analytics (how/why)
- Policy enforcement (control)
The goal? To provide real-time visibility into the identity landscape and proactively remediate vulnerabilities before they become breaches.
Why Security Risk Assessment Matters in ISPM?
While Identity Security Posture Management (ISPM) tools offer automated visibility and control over your identity environment, they’re not enough on their own. Without a strategic and continuous security risk assessment, even the most advanced ISPM system can fall short. Here’s why risk assessments remain critical:
- Evolving Threat Landscape: Today’s attackers don’t just target endpoints, they exploit identity-based vulnerabilities like stale credentials, misconfigured roles, and inactive accounts. Risk assessments help surface these blind spots before they’re exploited.
- Rising Regulatory Demands: Frameworks such as NIST, ISO 27001, and SOC 2 mandate continuous identity and access monitoring, making risk assessments not just a best practice, but a compliance automation.
- Shadow IT Expansion: Employees often adopt unsanctioned tools without security oversight. These unmanaged apps and orphaned accounts can become hidden entry points for attackers, unless identified and assessed.
- Privilege Creep: Over time, users accumulate excessive access rights they no longer need. Without periodic reviews and risk scoring, these unnecessary privileges can turn into major breach vectors.
- Exploding SaaS Ecosystems: With modern organizations using dozens or even hundreds of SaaS tools, identity management becomes fragmented. Risk assessments help prioritize remediation by identifying where the greatest identity threats lie.
Bottom line? ISPM without continuous risk assessment is like flying blind: you may sense something’s wrong, but you won’t know where you're heading or how close you are to disaster.
Core Principles of Security Risk Assessment
Understanding Threats vs. Vulnerabilities
- Threat: An external actor or event that can cause harm (e.g., hacker, malware, insider).
- Vulnerability: A weakness in your system that a threat can exploit (e.g., misconfigured admin access).
Security risk assessment focuses on identifying vulnerabilities in your identity posture that increase the likelihood of threats succeeding.
Risk = Likelihood × Impact: The Assessment Formula
This foundational formula helps quantify risk:
Risk Score = Likelihood of Exploit × Business Impact
For example:
- An unused admin account with MFA disabled (high likelihood)
- Connected to sensitive data stores (high impact)
= Critical Identity Risk
Compliance and Regulatory Drivers
Risk assessments help meet compliance goals for:
- SOX: Validate user access to financial systems
- HIPAA: Protect healthcare data from unauthorized access
- GDPR/CCPA: Ensure identity governance and access transparency
- ISO 27001: Demonstrate systematic risk evaluation
- NIST CSF: Align with Identify-Protect-Detect-Respond-Recover principles
Key Steps to Conduct a Security Risk Assessment in ISPM
1. Define Scope and Objectives
Start by clearly outlining the boundaries and intent of your assessment:
- Identity Types: Determine whether you're assessing human identities (employees, contractors) or non-human identities (bots, service accounts, APIs).
- Systems in Scope: Identify which environments and applications (on-prem, cloud, SaaS) will be included.
- Risk Tolerance: Establish what constitutes acceptable vs. unacceptable identity-related risk.
- Stakeholders: Involve key teams, IT, security, HR, compliance, to align on priorities and responsibilities.
This ensures your risk assessment is purpose-driven, cross-functional, and aligned with governance standards.
2. Inventory and Map Identity Assets
Create a centralized identity map to gain visibility across your organization:
- Entities: Catalog all user accounts (employees, contractors), service identities, bots, and federated users (SSO, third parties).
- Access Mapping: List entitlements, group memberships, and roles associated with each identity.
- System Integration: Use ISPM tools to pull data from IAMs, IdPs (Okta, Azure AD), HRMS platforms, and SaaS environments. This forms the foundation for detecting overprovisioned accounts, inconsistencies, and rogue access.
3. Identify and Classify Vulnerabilities
Pinpoint identity-related exposures that may lead to compromise:
- Common Findings:
- Orphaned accounts (employees who’ve left)
- Admin or privileged accounts with weak or default credentials
- Dormant access privileges that haven't been used in months
- Role redundancies or overlapping permissions that violate least privilege.
- Classification: Rank each finding using a criticality matrix (Low, Medium, High, Critical), based on business impact and exploitability. Prioritizing vulnerabilities this way helps drive faster, targeted remediation.
4. Analyze Threat Vectors and Attack Surfaces
Identify how malicious actors could exploit identity gaps to compromise your environment:
Tactics to Watch:
- Credential stuffing attacks on exposed login portals
- Privilege escalation through unused admin rights
- Exploitation of stale OAuth tokens or unrevoked API keys
- Phishing campaigns targeting SSO logins
- Inactive accounts used for lateral movement
Attack Path Mapping:
Correlate these tactics with identified vulnerabilities to visualize your threat exposure. This helps quantify the real-world risk of each issue and guides mitigation strategies.
5. Evaluate Current Controls and Gaps
Assess whether existing identity controls are sufficient and properly enforced:
- Key Areas to Review:
- MFA deployment (coverage, enforcement policies)
- Role-based access control (RBAC) implementation fidelity
- Audit and activity logging for identity events
- Least privilege access enforcement
- Conditional access policies (geo, device, network-aware)
- Gap Analysis: Document areas where controls are missing, misconfigured, or unenforced. This step reveals whether your identity infrastructure supports proactive threat defense or requires hardening.
6. Assess Risk Levels and Prioritize Mitigation
Assign risk scores by combining threat likelihood, impact severity, and control effectiveness:
- Scoring Framework: Use a standard like FAIR or CVSS-like internal rubric to grade identity risks.
- Remediation Strategy:
- Target quick wins (e.g., disabling orphaned privileged accounts).
- Address high-risk blind spots (e.g., critical SaaS apps with no access logging or RBAC).
- Schedule longer-term fixes (e.g., role redesign, automation via ISPM).This ensures your resources go toward the most impactful actions first, driving real security posture improvement.
Addressing Common Vulnerabilities in Identity Security
Over-Provisioned Access Rights
Employees often have more access than needed. This violates least privilege principles and increases insider risk. Audit roles and rights regularly.
Orphaned Accounts and Shadow IT
Accounts left behind by offboarded users or discovered in unsanctioned SaaS apps pose a major risk. Use discovery tools to identify and remove them.
Weak Credential Policies
Passwords without complexity or MFA expose identities to brute-force or phishing attacks. Enforce strong authentication and password rotation policies.
Misconfigurations in Identity Systems
Open roles, default admin settings, or insecure SAML configurations can serve as backdoors for attackers. Audit IdP and IAM settings often.
Insufficient Monitoring and Alerts
Lack of real-time monitoring allows attackers to stay hidden. Integrate identity logs with SIEM/SOAR platforms and set behavior-based alerts.
Best Practices to Strengthen Identity Security Posture
Implement Least Privilege Access
Ensure that every user, whether human or machine, only has the minimum level of access required to perform their role. Leverage Role-Based Access Control (RBAC) and Just-in-Time (JIT) access provisioning to prevent standing privileges. This not only limits exposure but also reduces the blast radius in case of a breach.
Regularly Review and Update Access Rights
Access rights aren’t static, neither are users' roles. Conduct quarterly access reviews to validate that permissions still align with job functions. Remove outdated entitlements, revoke access for departed employees, and tighten overly permissive roles. Automating this process with identity governance tools can streamline compliance.
Educate Teams on Identity Security Risks
Your strongest technical defenses can be undone by human error. Deliver regular security awareness training focused on:
- Recognizing phishing attempts
- Practicing credential hygiene
- Understanding the importance of MFA and secure password usage
Equip your workforce to be the first line of defense against identity-related threats.
Integrate Risk Assessment into Routine Operations
Identity risk management shouldn’t be an afterthought or only activated during audits. Embed it into your day-to-day processes, including:
- Quarterly security reviews
- New app/vendor onboarding
- Mergers & acquisitions (M&A)
- Employee role changes or terminations
This proactive approach ensures continuous risk mitigation rather than reactive firefighting.
Foster Cross-Functional Collaboration
Identity risk is an enterprise-wide responsibility. Encourage collaboration between IT, HR, compliance, procurement, and security teams.
- HR can flag role/title changes early
- Procurement can validate vendor access needs
- Compliance can ensure regulatory requirements are met
Working in silos causes gaps. A united front enables faster detection and resolution of identity risks.
How CloudEagle.ai Helps Organizations Improve Identity Security Posture Management (ISPM)
CloudEagle.ai enables IT and security teams to proactively strengthen identity governance across their SaaS environments. In a landscape where over 60% of AI and SaaS apps operate outside IT’s oversight, CloudEagle provides the visibility, automation, and control needed to reduce access-related risks and enforce security policies at scale.
360° Identity Visibility
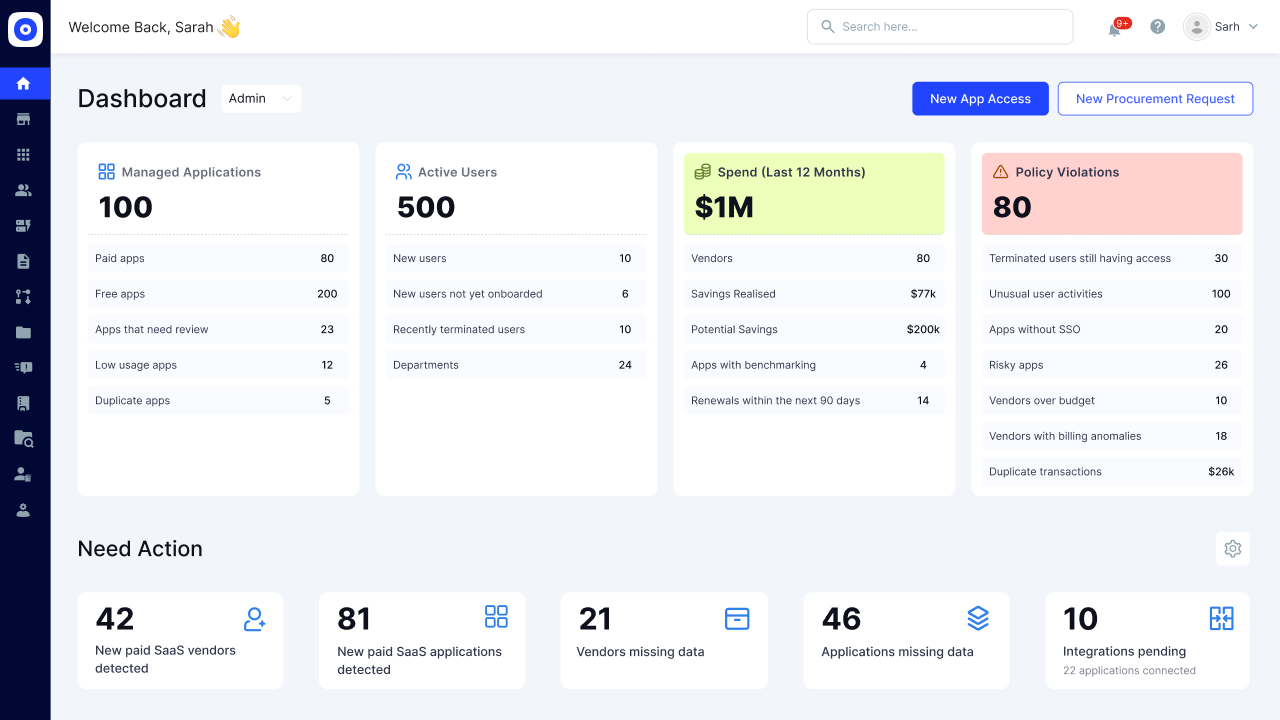
Achieve a unified, real-time view of all users, access levels, and entitlements across every application, including those outside your SSO or IDP. Eliminate access blind spots and reduce the surface area for insider threats and non-compliance.
AI-Powered Risk Scoring
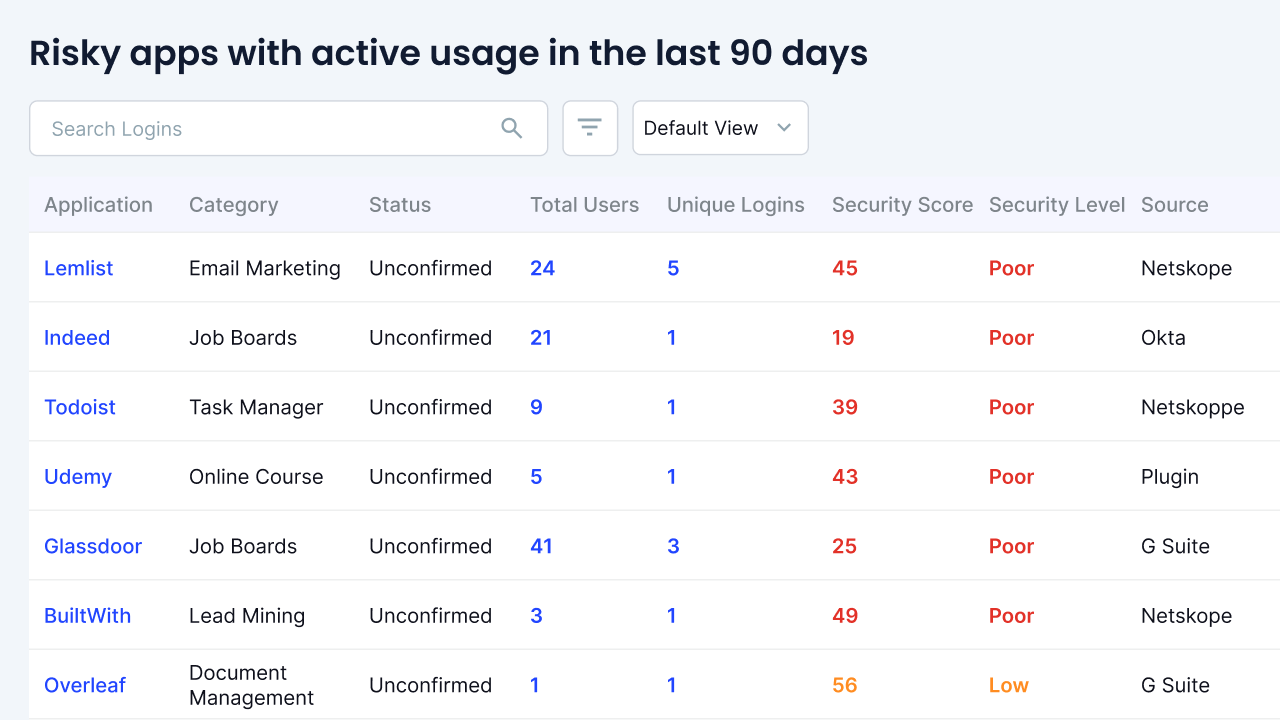
Continuously assess identity-related risks by evaluating user privileges, app usage behavior, and access anomalies. CloudEagle highlights high-risk accounts and access combinations to enable early intervention and stronger security posture.
Orphaned Account Detection
Identify and flag inactive, unused, or shadow accounts including those belonging to former employees or contractors. Automate the cleanup process by deprovisioning these accounts directly through integrations with Okta, Azure AD, Microsoft, and other identity systems.
Automated Access Reviews and Certifications
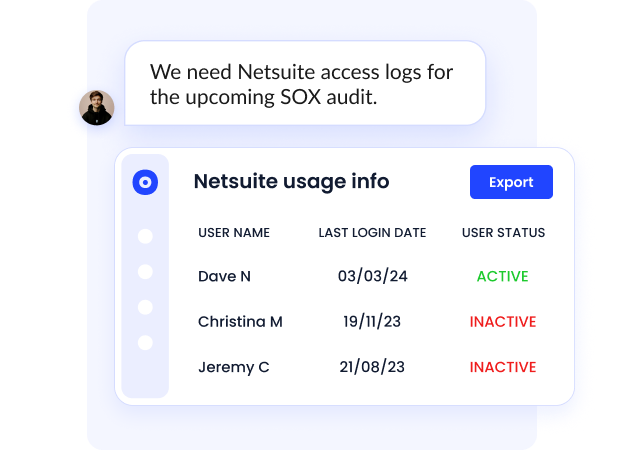
Replace slow, manual quarterly reviews with continuous, risk-based access governance. CloudEagle’s workflows surface context-rich insights for approvers, streamline access decisions, and generate SOC2-ready audit trails.
Audit and Compliance Reporting
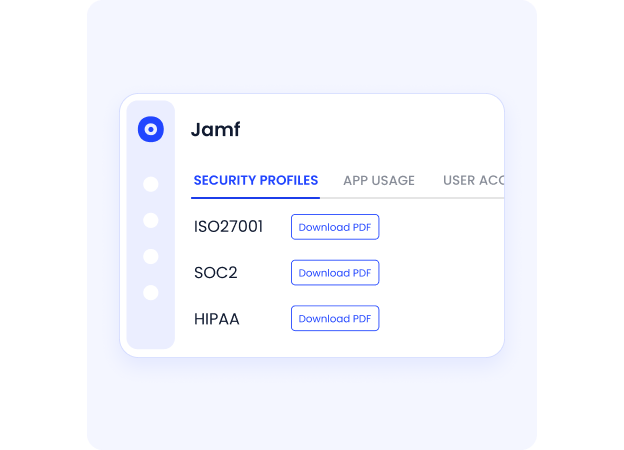
Create detailed reports for compliance frameworks like SOX, GDPR, ISO, and HIPAA. Maintain an automated record of all identity and access changes, approvals, and provisioning actions to support audit readiness.
Scalable SaaS Access Governance
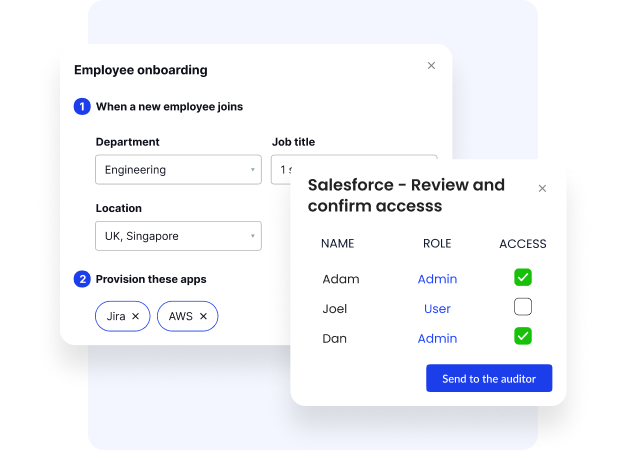
Enforce access policies across your SaaS stack, including apps not covered by your IDP. CloudEagle integrates with HRIS, ITSM, and security systems to manage provisioning, approvals, and deprovisioning workflows from one centralized platform.
CloudEagle = Risk Reduction + Operational Efficiency + Compliance Peace of Mind
Conclusion
In an era where identities are the new endpoints, organizations can’t afford to manage access blindly. Security risk assessments in ISPM help uncover identity weaknesses that traditional security tools miss, before they lead to breaches, fines, or reputational damage.
Whether you’re a fast-growing startup or a global enterprise, adopting a proactive ISPM strategy, powered by regular risk assessments, sets the foundation for scalable, secure, and compliant operations.
And with tools like CloudEagle.ai, the path to a mature identity security posture is clearer than ever.
FAQs
1. What is posture management security?
Posture management security refers to the process of continuously monitoring and improving the security configuration of IT environments including identities, applications, and networks, to reduce exposure and meet compliance.
2. What is the difference between ITDR and ISPM?
ITDR (Identity Threat Detection and Response) focuses on detecting and responding to identity-based attacks in real-time. ISPM (Identity Security Posture Management) focuses on proactively reducing risk by fixing misconfigurations, access gaps, and compliance issues before attacks happen.
3. What is security posture in information security?
Security posture describes an organization’s overall readiness to detect, respond to, and recover from cyber threats. It includes tools, policies, processes, and risk assessments across the IT environment.
4. What is ISPM in cybersecurity?
ISPM stands for Identity Security Posture Management. It involves monitoring, analyzing, and managing identity-related risks and misconfigurations across digital systems to strengthen an organization’s security.
5. What is the ISPM treatment?
In cybersecurity, the “ISPM treatment” refers to applying continuous assessment, risk scoring, access optimization, and automated remediation to identity systems and policies.
6. What does ISPM 15 certified mean?
ISPM 15 relates to international shipping and packaging standards (not cybersecurity). In the context of identity security, ISPM refers to Identity Security Posture Management, which is unrelated.
7. What is the difference between ITDR and ISPM?
To reiterate:
- ITDR = Real-time detection and response to identity threats
- ISPM = Proactive posture management and risk prevention
Both are complementary in a layered identity security strategy.

%201.svg)








.avif)




.avif)
.avif)




.png)









