HIPAA Compliance Checklist for 2025

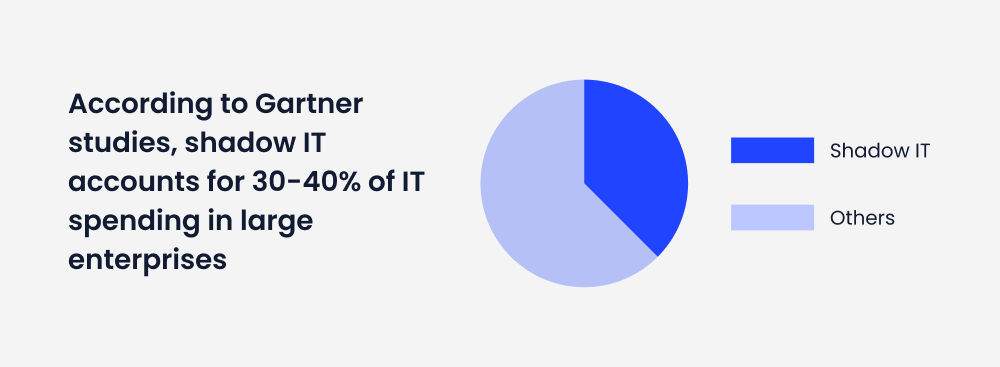
The technology sector is rapidly evolving, with the SaaS industry projected to reach $1.2 trillion by 2032. Another report revealed that 99% of companies will adopt at least one SaaS solution by 2024.
However, this explosive growth comes with significant security challenges. Over 80% of businesses rely on SaaS applications, yet 58% of IT professionals report data leakage as one of their primary SaaS security issues.
To keep SaaS secure, your organization must understand and mitigate these risks. A robust SaaS risk assessment strategy is your shield against potential data breaches, and this article will arm you with the key strategies for mitigating these SaaS security issues through smart SaaS risk management.
TLDR
- 99% of companies are expected to adopt at least one SaaS solution by 2024, highlighting the critical need for robust risk assessment SaaS and application risk management strategies in the digital transformation era.
- SaaS risk assessment is critical for protecting business continuity, enhancing compliance, safeguarding sensitive data, optimizing costs, and preventing unauthorized software adoption (Shadow IT).
- Key risk domains include data security, compliance, access control, and financial risks, which require a comprehensive SaaS assessment approach to identifying, evaluating, and mitigating potential vulnerabilities.
- Proven strategies for effective SaaS risk management include maintaining a detailed SaaS inventory, implementing risk scoring frameworks, conducting vendor due diligence, and using robust Identity and Access Management (IAM) solutions.
- CloudEagle.ai offers a comprehensive solution for SaaS risk assessment, providing complete app visibility, centralized user management, shadow IT prevention, and automated compliance tracking to transform app risk management from reactive to proactive.
What is SaaS Risk Assessment?
A SaaS risk assessment is the process of identifying, evaluating, and addressing potential security and operational threats tied to the use of SaaS applications. It enables organizations to safeguard data, stay compliant, and ensure business continuity by proactively managing vulnerabilities in their SaaS ecosystem.
Four critical domains are involved in SaaS risk assessment. Each demands careful attention and strategic application risk management. These domains include data security and privacy breaches, compliance and regulatory obligations, operational challenges, and vendor dependency risks.
You need to systematically address these risks to transform assessment SaaS efforts from a defensive strategy into a proactive business enabler. When approached effectively, SaaS risk management not only strengthens your security posture but also supports operational efficiency and cost control.
Common Risks Associated with SaaS Applications
Common risks tied to SaaS applications include data breaches, unauthorized access, compliance failures, and third-party vulnerabilities, often caused by misconfigurations, weak authentication, and insecure APIs. These threats can result in financial loss, reputational harm, and business disruption.
Data Security Risks
Your sensitive information faces constant threats from cybercriminals. Unauthorized data access, potential breaches, and cloud vulnerabilities can expose critical business intelligence, highlighting the urgency of managing SaaS security issues with comprehensive application risk management.
Compliance Challenges
Navigating regulations requires meticulous attention. Different industries demand specific SaaS compliance standards like GDPR, HIPAA, or PCI-DSS. Non-compliance can trigger substantial financial penalties and legal repercussions. A proactive SaaS assessment framework helps you stay aligned and ready for audits.
Shadow IT
Unauthorized software adoption by employees creates significant organizational risks. When teams independently select and use SaaS applications without IT department approval, you expose your network to unvetted SaaS security issues and compliance gaps.
These unmonitored applications can bypass critical security protocols, create integration challenges, and increase potential breach points. Addressing this risk is a vital part of any successful SaaS assessment or SaaS risk management program.
Access Control Risks
Inadequate user authentication and permission management can devastate your organizational security. Weak password policies, lack of multi-factor authentication, and improper access permissions are key Identity and Access Management concerns that lead to SaaS security issues.
Financial Risks
SaaS adoption introduces complex financial considerations. Unexpected licensing costs, inefficient software utilization, vendor lock-in, and unpredictable pricing models can strain your budget.
You also reduce risks associated with overprovisioned software licenses, often revealed through thorough assessment, SaaS reporting, and insights.
Why SaaS Risk Assessment is a Strategic Priority
SaaS risk assessment has become a strategic priority as organizations increasingly rely on cloud-based software. It’s essential for protecting sensitive data, maintaining compliance, and ensuring business continuity. By proactively managing SaaS-related risks, businesses can prevent costly disruptions, preserve customer trust, and secure their operations.
Protecting Business Continuity
Unmitigated SaaS risks can disrupt your entire operational ecosystem. Service interruptions, data losses, and system vulnerabilities can halt critical business processes.
Your SaaS risk assessment strategy creates robust contingency plans to ensure minimal downtime and rapid recovery. These controls are a key part of both SaaS risk management and long-term application risk management practices.
Enhancing Compliance Posture
Regulations continue to evolve rapidly. A sound SaaS assessment becomes a proactive compliance shield as it helps you navigate complex legal requirements.
Systematically evaluating applications within your enterprise risk management SaaS framework reduces the risk of SaaS compliance failures and supports regulatory readiness during audits.
Protecting Sensitive Data
Data is your organization's most valuable asset. Comprehensive risk assessment provides multiple layers of protection against potential breaches. You implement advanced encryption, multi-factor authentication, and stringent access controls.
When you understand potential vulnerabilities, you create a robust defense mechanism that safeguards customer information, intellectual property, and critical business intelligence.
Optimizing Costs
Unmanaged SaaS investments can rapidly escalate unnecessary expenses. SaaS risk assessment helps identify redundant applications, optimize licensing, and eliminate inefficient software subscriptions.
You gain granular visibility into software utilization, which enables strategic budget allocation and prevents financial waste. This approach transforms risk management into a cost-optimization strategy.
Preventing Shadow IT and Sprawl Escalations
Uncontrolled software adoption creates significant organizational risks. SaaS risk assessment strategy establishes clear governance frameworks, preventing unauthorized software acquisitions.
You create centralized procurement processes, implement comprehensive approval workflows, and maintain complete visibility into your organization's software stack.
This approach prevents potential security vulnerabilities and ensures consistent technology standards.
Strengthening Vendor Relationships
Strategic risk assessment transforms vendor interactions from transactional to collaborative partnerships. You establish clear expectations, define performance metrics, and create transparent communication channels.
By holding vendors accountable and establishing mutually beneficial risk management frameworks, you cultivate stronger, more reliable technology partnerships that drive organizational innovation and growth.
Tools and Frameworks for SaaS Risk Assessment
SaaS risk assessments can be efficiently streamlined using a mix of tools and frameworks designed to detect, analyze, and address threats in cloud-based applications. Risk matrices, decision trees, and automated vulnerability scanners assist in evaluating and prioritizing risks.
Frameworks like ISO 27001 and the NIST Cybersecurity Framework (CSF) offer structured methodologies for managing information security and cybersecurity challenges. In addition, specialized SaaS security tools such as Centraleyes, Netskope, and BetterCloud help organizations handle compliance, enforce data protection, and control user access more effectively.
NIST
The NIST Cybersecurity Framework is a trusted model for structuring assessment SaaS processes. It focuses on five pillars: Identify, Protect, Detect, Respond, and Recover, guiding teams through every stage of application risk management. NIST works especially well for organizations building scalable and compliant enterprise risk management SaaS programs.
ISO 27001
ISO/IEC 27001 provides a formalized standard for managing security controls across SaaS environments. It strengthens SaaS risk management by requiring documented policies, audits, and controls, key to keeping SaaS assessment repeatable and compliant.
CSA CCM
The Cloud Security Alliance (CSA) Cloud Controls Matrix focuses specifically on cloud-based environments. It helps identify common SaaS security issues like data residency risks, access misuse, and vendor non-compliance. It’s widely used for structuring app risk management across decentralized SaaS ecosystems.
Automation Tools
Tools like CloudEagle.ai, Drata, and Vanta automate tasks such as app discovery, vendor evaluations, risk scoring, and access reviews. These platforms form the operational layer of SaaS risk assessment, making it easier to monitor your entire SaaS stack without manual effort.
GRC Platforms
For mature companies, integrating SaaS risk management into broader GRC (Governance, Risk, and Compliance) platforms creates a centralized, policy-driven model. This improves visibility and aligns application risk management with business-wide compliance goals.
By combining these frameworks and tools, your team can enforce a continuous, auditable, and scalable SaaS assessment process, one that keeps up with your expanding app ecosystem and evolving risks.
Proven SaaS Risk Assessment Strategies
Proven SaaS risk assessment strategies take a comprehensive approach, covering vendor risk management, data protection, access control, and real-time monitoring. Core practices include performing detailed risk assessments, enforcing strict access controls, and creating strong incident response plans.
Additionally, organizations should invest in employee security awareness training and continuously update their security protocols to adapt to evolving threats.
Comprehensive SaaS Inventory
A detailed SaaS inventory is the first step toward effective SaaS risk assessment. You map out every application across your organization, capturing its usage, integration points, and security vulnerabilities. This visibility helps prevent SaaS security issues and shadow IT from taking root.
A well-structured SaaS assessment uncovers redundant tools, shadow apps, and unused licenses, enabling stronger application risk management and informed budget decisions. It's a critical foundation of any successful enterprise risk management SaaS strategy.
Risk Scoring Frameworks
Quantitative risk assessment empowers strategic decision-making. You develop a structured scoring system that evaluates each SaaS application against multiple risk parameters.
These parameters include data sensitivity, compliance requirements, vendor reliability, and potential business impact. By assigning numerical values to different risk factors, you create a standardized approach to prioritizing and addressing potential vulnerabilities.
Vendor Due Diligence
Thorough vendor evaluation prevents potential security breaches. You conduct comprehensive background checks on functionality, assess the vendor's financial stability, review their security certifications, and analyze their data protection mechanisms.
This process includes examining their historical performance, understanding their incident response protocols, and verifying their compliance with industry standards. Rigorous due diligence ensures you partner with reliable and secure SaaS providers.
Streamlining Access Controls
Robust access management minimizes unauthorized system entry. You implement multi-factor authentication, develop role-based access protocols, and create granular permission structures.
Regular access audits help you identify and remove unnecessary user privileges. It helps reduce potential internal and external security risks. This strategy ensures that only authorized personnel can access critical business applications.
Continuous Monitoring
Real-time risk tracking becomes your defense mechanism. You deploy advanced monitoring tools that provide instant alerts about potential security incidents, performance issues, or compliance deviations.
Continuous monitoring allows rapid response to emerging threats. This is to ensure minimal disruption to your business operations.
Using a Robust IAM Solution
Identity and Access Management (IAM) solutions like CloudEagle.ai transform your risk management approach. These platforms provide centralized control over user access, automate compliance processes, and offer comprehensive visibility into your SaaS stack.
You gain real-time insights, streamline procurement, and implement consistent security standards across your entire SaaS portfolio.
Best Practices to Mitigate SaaS Risks
To mitigate SaaS risks, organizations should adopt a multi-layered strategy that includes strong authentication, strict access controls, routine security audits, and continuous monitoring. These measures help prevent data breaches, unauthorized access, and compliance failures, strengthening the overall security of SaaS applications.
Enforce Zero Trust Access Controls
Zero Trust is essential for modern app risk management. Instead of assuming that internal users or devices are safe, this model verifies every access attempt based on user identity, location, device health, and role.
Enforcing Zero Trust with tools like Okta or Microsoft Entra ID can reduce excessive permissions and prevent lateral movement during breaches.
Implement Identity and Access Management (IAM)
A strong IAM framework helps ensure that only the right people access the right applications at the right time. This prevents privilege creep and supports automated access reviews, key components of a well-governed SaaS assessment process.
IAM tools also integrate seamlessly with SSO (Single Sign-On), enhancing both security and user experience in platforms like Google Workspace or Slack.
Monitor Shadow IT and SaaS Sprawl
Shadow IT is one of the most overlooked SaaS security issues. Employees often sign up for new tools without IT’s approval, leading to security blind spots. Use tools like CloudEagle.ai or Torii to monitor app usage, flag unauthorized software, and align purchases with procurement policy.
This approach strengthens enterprise risk management SaaS efforts and ensures consistent enforcement across departments.
Automate Vendor Risk Assessments
Vendor security is a core part of SaaS risk assessment. Automate the review of vendor SOC 2 reports, compliance certifications, and breach history before onboarding. Platforms like TrustCloud or SecurityScorecard streamline third-party reviews and integrate well with procurement workflows, helping reduce the workload on security teams.
Train Employees on SaaS Security
Even the best technology can’t compensate for uninformed users. Regularly educate your workforce on secure SaaS usage, how to spot phishing links, avoid unsafe integrations, and follow approval processes.
Employee awareness is a powerful layer in SaaS risk management, especially when combined with continuous monitoring and alerts.
By putting these best practices in place, you'll transform your application risk management process from reactive to strategic.
Steps to Build an Effective SaaS Risk Assessment Program
To build an effective SaaS risk assessment program, organizations should take a structured approach that starts with identifying SaaS usage, evaluating data sensitivity, and assessing vendor security. It’s essential to involve a cross-functional team, define clear assessment criteria, and implement ongoing monitoring and improvement to stay ahead of evolving risks.
Step 1: Assemble a Cross-functional Risk Management Team
You need a team that understands risk assessment SaaS from all angles. Include stakeholders from IT, security, legal, finance, and procurement to form a well-rounded application risk management unit.
This cross-functional team ensures technical security concerns, compliance mandates, and business risks are all addressed during your SaaS risk assessment planning phase.
Step 2: Conduct a SaaS Inventory and Classify Risks
This step is key to preventing SaaS security issues before they spread. Audit all applications, log access levels, and classify risks based on sensitivity and impact.
By categorizing tools through your assessment SaaS lens, you can prioritize mitigation efforts and allocate resources smartly, a central goal of effective app risk management.
Step 3: Define and Implement Risk Assessment Criteria
Establish standardized scoring models to rank SaaS tools by risk. Include factors like encryption, data privacy, and vendor certifications in your risk assessment SaaS matrix.
These criteria help your team apply SaaS risk management principles uniformly across the portfolio, ensuring every app is evaluated against consistent, measurable standards.
Step 4: Monitor and Refine Policies Based on Real-time Insights
Real-time risk visibility is non-negotiable. Use platforms like CloudEagle.ai to automate tracking, flag SaaS security issues, and surface anomalies.
Continuous improvement is a key pillar of enterprise risk management SaaS. You refine policies as insights evolve, turning your SaaS assessment strategy into a proactive defense system.
Step 5: Foster a Culture of Compliance and Security Awareness
Risk management is everyone’s job. Embed app risk management awareness into your organization’s culture. Conduct training, share updates, and reward secure behavior.
Clear communication and role-specific education transform SaaS risk assessment from a security function into a company-wide mission.=
How CloudEagle.ai Can Assist with SaaS Risk Assessment
CloudEagle.ai is built to eliminate blind spots in your SaaS ecosystem. It brings together app risk management, license optimization, compliance readiness, and access control into one smart platform.
Complete App and Spend Visibility
CloudEagle.ai transforms your SaaS portfolio management by delivering comprehensive visibility within 30 minutes. You gain instant insights into department-level spending and detailed usage metrics.

The platform reveals crucial data points, from Zoom meeting recordings to Salesforce opportunity creation.
Furthermore, the system intelligently identifies duplicate and redundant applications through direct API integrations. You leverage feature-level usage insights to eliminate unnecessary costs.
One case study is how CloudEagle.ai helped speed up M&A Diligence and saved them a lot of money on duplicate apps. It helped them reduce 70% of the time spent on app management and saved 630 hours yearly on reporting.
The platform's smart categorization engine automatically organizes applications by department, enabling precise resource allocation and cost tracking.
Centralized App and User Management
CloudEagle.ai streamlines your employee onboarding and offboarding processes through automation.

New employees receive immediate access to essential tools, eliminating productivity delays. The platform's automated workflows ensure precise access level assignments from day one.
The system also provides intelligent app recommendations based on employee roles and departments.
You maintain security through automated access revocation when employees leave. Most importantly, CloudEagle.ai offers unified control over both SCIM and non-SCIM applications through a single dashboard.
Shadow IT Prevention
CloudEagle.ai proactively identifies and prevents unauthorized application usage. You receive instant alerts when employees purchase unsanctioned apps using company credit cards.
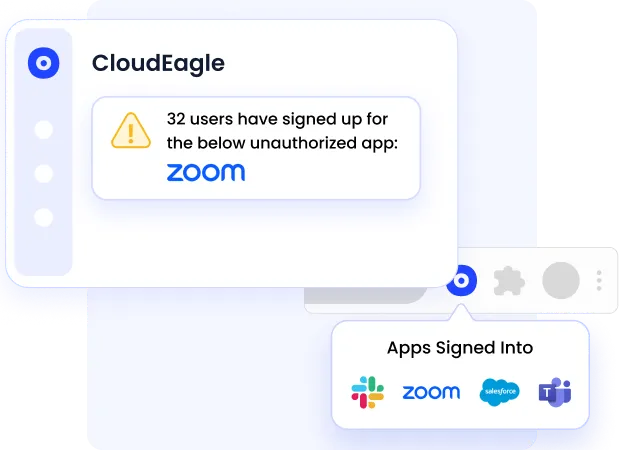
This early detection system prevents potential security risks and unnecessary cost escalation. The platform excels in license management through:
- Automatic license reclamation based on usage thresholds.
- Precise usage monitoring through 500+ integrations.
- Intelligent license downgrade recommendations.
- Employee self-service app catalogs via Slack integration.
Privileged and Role-Based Access Controls
CloudEagle.ai enhances your security posture through sophisticated access management. You maintain precise control over application privileges, ensuring users receive appropriate access levels.
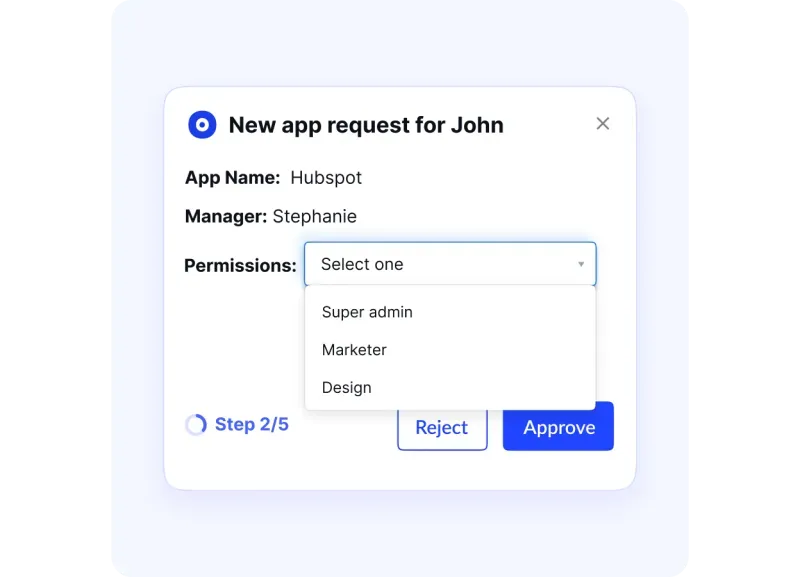
The platform automatically manages critical system access, including AWS and NetSuite privileges.
A user-friendly application catalog enables streamlined access requests and approvals. You assign dedicated app administrators to review and manage access requests, maintaining security while improving efficiency.
Time-Based Access Management
CloudEagle.ai introduces innovative time-based access controls. You grant temporary access to privileged systems, like AWS root acces,s for specific durations.
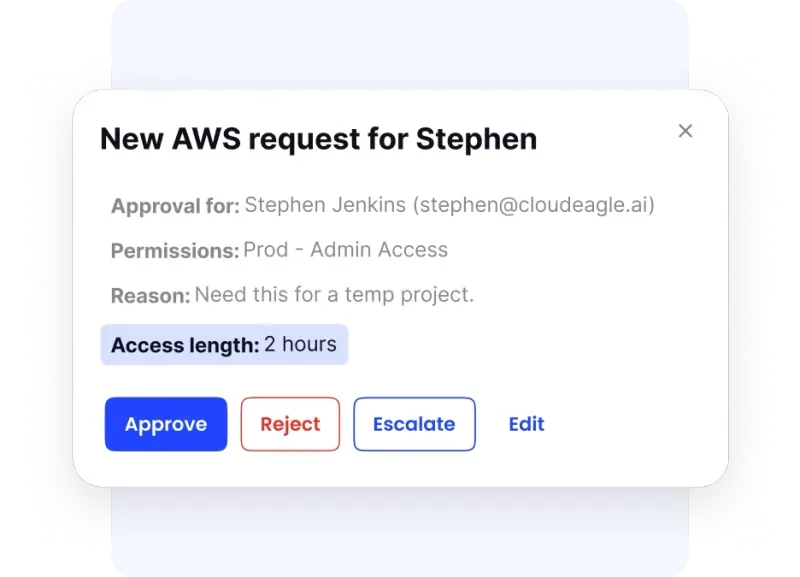
The platform automatically revokes access after completion, enhancing security for temporary workers while optimizing license costs.
Compliance Management
CloudEagle.ai transforms compliance management into an automated, efficient process. The platform streamlines SOC 2 and ISO 27001 access reviews through:
- Automated compliance verification.
- Centralized deprovisioning logs.
- Comprehensive audit trails.
- Real-time vulnerability testing.
- External audit management.
- Certification tracking.

Most importantly, CloudEagle.ai protects your organization from compliance-related penalties and data breaches. You maintain continuous compliance through automated monitoring and comprehensive documentation.
The platform's centralized dashboard provides complete visibility into your compliance status, enabling proactive risk management and regulatory adherence.
CloudEagle.ai is a complete solution for modern SaaS risk assessment challenges through these sophisticated capabilities. You gain control over your SaaS stack while ensuring security, efficiency, and compliance.
Conclusion
SaaS risk assessment is your primary defense against evolving digital threats. With the SaaS sector expanding rapidly, your organization faces increasing security challenges, compliance requirements, and operational risks.
A proactive risk assessment strategy protects your valuable data, ensures regulatory compliance, and optimizes your software investments.
Take control of your SaaS stack today. CloudEagle.ai empowers you with comprehensive visibility, automated risk management, and intelligent insights. Transform your SaaS security from reactive to proactive.
Ready to strengthen your SaaS security posture? Book a demo with CloudEagle.ai now and discover how we can revolutionize your SaaS risk management strategy.
Frequently Asked Questions
1. What are the 5 main steps of risk assessment?
Identify hazards, assess risks, control risks, document findings, and review regularly. This structured approach ensures consistent risk evaluation and mitigation.
2. What are the 4 C's of risk assessment?
The 4 C’s are Communication, Consultation, Coordination, and Cooperation. These ensure collaborative risk assessment and effective implementation of safety measures.
3. What is the SA 8000 risk assessment?
SA 8000 risk assessment evaluates workplace practices like child labor, safety, and wages. It ensures compliance with social accountability standards for ethical working conditions.
4. What is the risk management of SaaS?
SaaS risk management involves identifying, assessing, and mitigating security, compliance, and operational risks across all cloud-based software applications in use.
5. What is application risk management?
Application risk management focuses on identifying, evaluating, and mitigating security and compliance risks related to software applications within an organization.
6. What are the 5 components of ERM?
The five components are Governance and Culture, Strategy and Objective-Setting, Performance, Review and Revision, and Information, Communication, and Reporting.
7. What are the security issues with SaaS?
Common SaaS security issues include data breaches, shadow IT, poor access controls, weak encryption, insecure APIs, and lack of compliance with industry standards.

%201.svg)







.avif)




.avif)
.avif)




.png)









