HIPAA Compliance Checklist for 2025

As enterprises increasingly rely on SaaS platforms, it’s more important than ever to ensure that only authorized users can access sensitive company data.
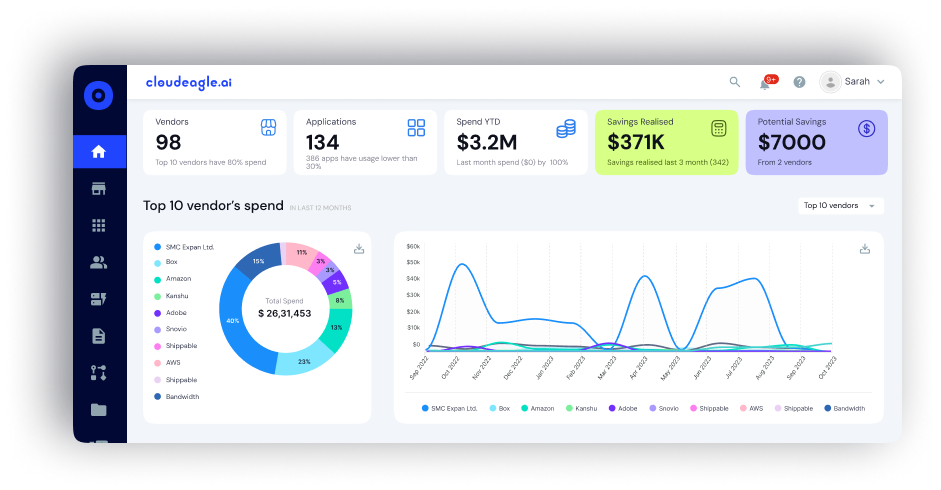
According to CloudEagle.ai's IGA report, 60% of AI and SaaS apps operate outside IT visibility.
User authentication is the key to this, verifying identities before granting access to SaaS applications, internal systems, or company resources.
So, what exactly is user authentication?
In simple terms, user authentication is the process of verifying someone’s identity using methods like passwords, biometrics, or SSO systems. As cyber threats increase, choosing the right authentication methods is crucial for enterprises using SaaS tools.
Let’s explore how user authentication works, the different methods available, and how CloudEagle.ai helps enterprises secure and manage access effectively.
TL;DR
- User Authentication verifies a person’s identity before granting access, protecting sensitive data, and preventing unauthorized access to systems and applications.
- Multi-Factor Authentication (MFA) and SSO provide stronger security by requiring multiple credentials or allowing access through a single login across multiple apps.
- Privileged User Authentication is crucial for controlling access to high-risk admin accounts and sensitive resources in a SaaS environment.
- User Authentication Services ensure compliance with regulations such as SOC 2, GDPR, and HIPAA, helping businesses meet data privacy standards.
- CloudEagle.ai automates access reviews, tracks risky behavior, and provides detailed audit logs, enhancing authentication governance for secure SaaS management.
What is User Authentication?
User authentication is the process of confirming a person’s identity before they can access a system, app, or network. In simple terms, it’s how enterprises make sure users are who they say they are. Without it, unauthorized people could access sensitive data or internal tools.
Key Aspects:
- Verifying Identity: Ensures only the right people can access your system.
- More Than Just Passwords: Uses a mix of passwords, security tokens, biometrics, or multi-factor authentication for extra protection.
- Prevents Unauthorized Access: Stops attackers from getting in by impersonating users.
Today, user authentication involves more than just passwords. It includes methods like SSO (Single Sign-On) and privileged user authentication for higher-risk accounts. These processes make sure that every action is tied to a verified user.
Modern user authentication services work across cloud and on-premise systems, balancing strong security with a smooth user experience. It’s not just a login process; it’s an important part of keeping your enterprise secure and trustworthy.
Why is User Authentication Important?
User authentication is the first line of defense against unauthorized access in any enterprise.
Veteran CIO & Technology Advisor, Paul Heard, says:
“AI tools boost productivity and are becoming like digital workers, but need oversight to prevent security and rule-breaking issues. The main challenge is making sure employees protect sensitive information when using AI, with proper controls and training in place. With the right safeguards, companies can get AI benefits while keeping data safe and following regulations.”
Proper user authentication helps:
1. Protect Sensitive Data and Systems
Modern enterprises rely on cloud apps, SaaS platforms, and internal systems that store vast amounts of confidential information. Robust user authentication methods safeguard these assets by confirming user identities before granting access, reducing the risk of data theft or misuse.
2. Prevent Unauthorized Access
User authentication blocks intruders from exploiting weak or shared credentials. Whether through passwords, MFA, or SSO user authentication, it ensures that every login attempt is verified, preventing unauthorized users from infiltrating sensitive environments.
3. Enable Compliance
Regulatory frameworks like SOC2, ISO 27001, GDPR, and HIPAA require strong access control and user authentication services to protect data privacy. Implementing secure user authentication helps enterprises stay compliant and avoid costly penalties.
4. Support Zero-Trust Architecture
Zero-trust security models rely on continuous user authentication, never assuming trust, even within internal networks. By verifying identity at every access point, enterprises strengthen privileged and user authentication policies that align with zero-trust principles.
What Are The Types of User Authentication?
Enterprises use various user authentication methods to verify identity and secure access. Each method balances security and convenience, helping teams select the best approach for their needs.
What Are The Modern Authentication Protocols?
As digital ecosystems expand, enterprises require user authentication methods beyond passwords. Here are the key frameworks and tools used in modern IT and SaaS environments:
1. OAuth 2.0 and OpenID Connect
OAuth 2.0 is a widely used authorization framework that allows users to grant limited access to their data without sharing passwords. OpenID Connect extends OAuth 2.0 to include identity verification, enabling SSO user authentication across multiple apps. Together, they power secure logins for Google, Microsoft, and enterprise systems.
2. SAML (Security Assertion Markup Language)
SAML is a standard protocol used for exchanging authentication and authorization data between identity providers (IDPs) and service providers (SPs). It’s one of the core technologies behind SSO user authentication, allowing employees to log in once and access multiple business applications securely.
3. SCIM (System for Cross-domain Identity Management)
SCIM automates user provisioning and deprovisioning across systems. It’s a critical part of user authentication services, ensuring that user access is automatically updated when employees join, change roles, or leave an enterprise; essential for managing privileged user authentication securely.
4. JWT (JSON Web Tokens)
JWT is a compact token format that securely transmits user identity information between systems. It’s commonly used in modern user authentication workflows, API security, and session management, helping ensure trust and integrity without storing credentials directly.
5. FIDO2 / WebAuthn
FIDO2 and WebAuthn enable passwordless user authentication using biometrics or hardware security keys. These standards support phishing-resistant authentication, making them key components of modern user authentication methods focused on convenience and high security.
What Are The Risks of Weak Authentication?
Weak user authentication exposes enterprises to security and compliance risks. In SaaS environments, a single compromised login can lead to data breaches, compliance issues, and financial loss. Here are common threats caused by poor authentication.
1. Credential Theft
When user authentication relies solely on passwords, stolen or reused credentials can easily be exploited. Attackers use credential stuffing or brute-force attacks to gain unauthorized access, making strong user authentication services and MFA essential for protection.
2. Phishing
Phishing attacks trick users into revealing login details through fake links or messages. Without robust user authentication protocols, these attacks succeed easily. Adding MFA or SSO user authentication helps verify identity and stop credential-based breaches.
3. Session Hijacking
Weak user authentication or poor session management allows attackers to hijack valid sessions and impersonate legitimate users. Tokens, cookies, or unencrypted traffic can be exploited, making token-based user authentication methods like JWT crucial for security.
4. Shadow IT from Unsanctioned Logins
Employees often sign up for SaaS tools without IT approval, creating shadow IT. These unmonitored logins bypass user authentication services, increasing risk and reducing visibility. Centralized SSO user authentication helps regain control and prevent data exposure.
5. Ex-Employee Access and Privilege Creep
Without automated offboarding and privileged user authentication controls, ex-employees may retain access to corporate systems. Over time, this leads to privilege creep, where users accumulate unnecessary permissions. Strong user authentication tied to role-based access and automated reviews prevents such risks.
Authentication vs. Authorization
How CloudEagle.ai Helps in User Authentication?
CloudEagle.ai is a SaaS management and access governance platform that augments traditional identity providers like Okta and Azure AD. It provides continuous, automated governance for user authentication and access across your entire SaaS environment, including non-SSO and shadow apps.
Here’s how the tool helps:
1. Contextual Governance Beyond IDP
CloudEagle.ai augments traditional IDPs like Okta or Azure AD by discovering and managing access to all apps, even those not linked to SSO (like free-tier tools, AI apps, and apps paid via cards). It gathers data from finance, browser, HRIS, and authentication sources, helping IT and Security teams manage user access across the entire enterprise.
How it helps:
- Delivers complete visibility into authenticated users across all SaaS.
- Reduces blind spots from unmanaged or shadow apps.
- Enhances security posture by closing governance gaps.
- Lets IT enforce consistent access policies across all tools.
- Simplifies audits by capturing access changes across IDP + non‑IDP apps.
2. Zero‑Touch Provisioning & Deprovisioning
CloudEagle.ai automates access provisioning and removal using HRIS + IT workflows. Whether or not apps sit behind your IDP, access is automatically granted based on role and instantly revoked when needed, preventing lingering access and reducing security exposure.
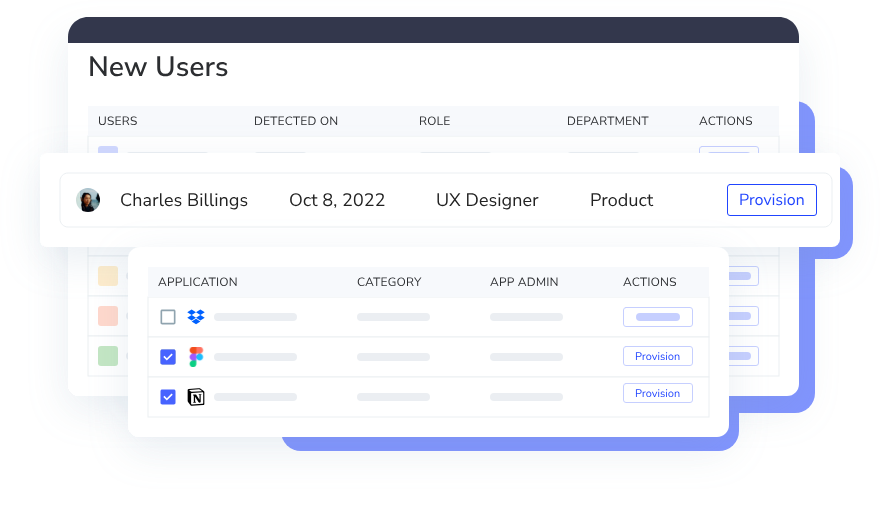
How it helps:
- Eliminates manual onboarding/offboarding effort.
- Prevents ex‑employees from retaining access.
- Reduces provisioning time from days to minutes.
- Keeps license pools accurate to avoid waste.
- Boosts employee productivity from day 1.
3. Automated Access Reviews
CloudEagle.ai centralizes access reviews across SaaS apps. including those not tied to IDP. Usage‑based insights and role context make certifications fast and accurate, reducing dependence on spreadsheets or ticketing systems.

How it helps:
- Ensures compliance without manual effort.
- Saves time with auto‑generated audit‑ready reports.
- Reduces human error during periodic reviews.
- Simplifies workflows for managers & app owners.
- Provides a clean audit trail for SOC2/ISO.
Explore how Dezerv Automated Its App Access Review Process with CloudEagle.ai.
4. Just‑In‑Time Access
CloudEagle.ai allows just-in-time access granting for temporary users, contractors, interns, or employees needing short‑lived privileges. Access automatically expires, reducing the risk of privilege creep.

How it helps:
- Eliminates always‑on admin or excess permissions.
- Reduces insider threat exposure.
- Minimizes license waste.
- Adds a layer of guardrails for temporary access.
- Simplifies enforcement of least‑privilege principles.
5. Shadow IT Discovery
CloudEagle.ai tracks app usage through SSO, browser, HRIS, and finance data to detect apps accessed outside IT-approved channels (Shadow IT). IT can then identify unmanaged logins and bring them under control.

How it helps:
- Exposes unauthorized tools instantly.
- Reduces risk of data leakage via unknown vendors.
- Helps IT enforce authentication + compliance policies.
- Prevents duplicate or unnecessary tools.
- Improves spend tracking and consolidation.
6. SOC2‑Ready Audit Logs
CloudEagle.ai maintains complete logs of authentication‑related activity across SaaS, including provisioning, approvals, revocation, temporary access, and usage. Reports can be exported on demand for audits.
How it helps:
- Makes passing SOC2/ISO audits faster.
- Eliminates manual evidence collection.
- Ensures full traceability of user access.
- Helps proactively identify risky permissions.
- Simplifies collaboration with auditors & GRC teams.
7. Policy Enforcement & Risk Scoring
CloudEagle.ai evaluates user access posture across apps and assigns risk scores based on role, authentication method, and usage. Non‑compliant apps or permissions can be flagged for review.

How it helps:
- Enforces consistent authentication standards.
- Highlights high‑risk user access instantly.
- Helps prioritize remediation efforts.
- Reduces manual investigation work.
- Supports proactive governance instead of reactive fixes.
Tune in to this insightful episode of CloudEagle.ai's SaaS Masterminds podcast, featuring Karl Haviland as he shares expert insights on AI, governance, and scaling innovation responsibly.
Conclusion
User authentication is key to digital security, ensuring that only authorized users access sensitive data and systems. The right methods, like SSO user authentication and biometrics, reduce risks and improve user experience.
Strong authentication helps with compliance, supports zero-trust security, and boosts efficiency. As businesses grow, managing privileged user authentication is essential to prevent misuse.
In short, effective user authentication is crucial for every enterprise. With CloudEagle.ai, teams can automate access reviews and strengthen security for the future.
Reflecting on her experiences, Nidhi Jain, CEO and Founder of CloudEagle.ai, shares:
“I’ve seen it happen too many times, an employee changes roles, yet months later, they still have admin access to systems they no longer need. Manual access reviews are just too slow to catch these issues in time. By the time someone notices, privilege creep has already turned into a serious security risk.”
Schedule a demo with CloudEagle.ai to see how it streamlines access governance and ensures secure SaaS management.
FAQ
1. Why is user authentication important?
User authentication is important because it verifies identity, protects sensitive data, and prevents unauthorized access. It ensures that only trusted users can log into systems, applications, and SaaS platforms securely.
2. How can I manage user authentication effectively?
You can manage user authentication effectively by using centralized user authentication services such as Okta, Azure AD, or CloudEagle.ai. Automate access reviews, enable SSO user authentication, and enforce multi-factor authentication for better control and security.
3. What are the three types of authentication?
The three main user authentication methods are:
- Knowledge-based (something you know – passwords)
- Possession-based (something you have – OTPs or tokens)
- Inherence-based (something you are – biometrics)
4. What is user authentication OTP?
A user authentication OTP (One-Time Password) is a temporary, single-use code used to verify identity during login. It adds an extra security layer beyond passwords, helping prevent credential theft and unauthorized access.
5. What is the difference between user authentication and verification?
User authentication confirms a user’s identity before granting access, while verification checks if the provided credentials are valid. Authentication is part of the access process; verification is one of its key steps.

%201.svg)








.avif)




.avif)
.avif)




.png)









