HIPAA Compliance Checklist for 2025

In the digital age, securing access to devices, data, and services is more critical than ever. Traditional methods like passwords and PINs fall short due to vulnerabilities like theft, guessing, and reuse. This is where biometric authentication steps in as a powerful solution.
By using unique physical or behavioral characteristics, such as fingerprints, facial features, or voice patterns, biometric authentication offers a secure and convenient way to verify identity.
Unlike passwords, biometric authentication is nearly impossible to fake or steal, making it a reliable layer of protection against cyber threats. More enterprises are adopting biometric authentication to safeguard sensitive information, streamline access, and reduce security risks.
As technology advances, biometric authentication is becoming the cornerstone of future-proof security strategies. Biometric systems have been proven to reduce fraud and identity theft by up to 70% in different sectors due to their resistance to credential theft and spoofing methods.
Let’s explore what biometric authentication is, how it works, its benefits, common types, challenges, and why it matters in today’s cybersecurity landscape.
TL;DR
- Biometric authentication uses unique physical or behavioral traits like fingerprints and facial features for fast, secure identity verification, replacing passwords and PINs.
- It offers superior security by being nearly impossible to fake or steal, reducing risks from cyberattacks like phishing and credential theft.
- Biometric authentication improves convenience and user experience by eliminating the need to remember passwords or carry tokens.
- It integrates well with multi-factor authentication (MFA), adding a strong extra layer of protection against unauthorized access.
- Widely adopted across industries, biometric authentication secures mobile devices, banking, government IDs, and workplaces, making it key to modern security strategies.
What is Biometric Authentication?
Biometric authentication is a security process that verifies a person’s identity by using unique biological traits or behaviors. Instead of relying on passwords or PINs, biometric authentication looks at fingerprints, facial features, retina patterns, voice, or even how a person types.
These characteristics are incredibly difficult to fake or steal, making biometric authentication a much more secure method of verifying identity. The process begins by capturing a biometric sample during enrollment, such as scanning a fingerprint or taking a face photo.
This data is converted into a digital template that represents the unique features. Later, during authentication, the system compares the live biometric input to the stored template. Access is granted only if there is a close match.
Biometric authentication provides convenience and improved security because people don’t have to remember passwords or carry extra tokens. It is widely used on smartphones, banking apps, workplaces, and airports for secure access. As a result, biometric authentication is rapidly becoming an essential part of modern security strategies.
Types of Biometric Authentication
Biometric authentication comes in many forms, each leveraging unique human characteristics for identity verification. The most common types of biometric authentication include:
1. Fingerprint Recognition
Fingerprint recognition is the most widely used type of biometric authentication. It analyzes the unique ridge patterns on a person’s fingertips. This method is popular because it is quick, accurate, and integrated into many smartphones, laptops, and security systems.
2. Facial Recognition
Facial recognition systems analyze the structure of a person's face—measuring distances between eyes, nose shape, jawline, and other features. This type of biometric authentication is commonly used in mobile phones, airports, and secure facilities for contactless access.
3. Iris and Retina Scanning
Iris and retina scanning involve analyzing the intricate patterns within the eye. Although less common due to the need for special scanners, these methods offer high precision and are used in high-security environments like government buildings and research labs.
4. Voice Recognition
Voice recognition measures unique vocal characteristics such as tone, pitch, and cadence. It is often employed in call centers, banking, and virtual assistants to authenticate users verbally.
5. Vein Recognition
Vein recognition maps the unique patterns of veins beneath the skin, typically in the palm or fingers. This biometric authentication is highly secure because vein patterns are beneath the skin and difficult to replicate or forge.
6. DNA Matching
DNA matching uses a person’s genetic makeup for authentication. Due to its complexity and cost, this type of biometric authentication is generally used in forensic and specialized security scenarios.
How Biometric Authentication Works?
Biometric authentication works by using unique physical or behavioral features of an individual to verify their identity. The process generally follows these key steps:
1. Enrollment: This initial step captures a person’s biometric data, such as a fingerprint scan, facial image, or voice sample. The system converts this data into a digital template—a mathematical representation of the distinctive features. Importantly, the raw biometric data is not stored; only this encrypted template is saved securely.
2. Storage: The biometric template is stored either locally on a device (like a smartphone’s secure area) or on a remote server with strong encryption, ensuring privacy and security.
3. Authentication: When the user tries to access a system or device, they provide a fresh biometric sample. The system captures this input and compares it against the stored template using sophisticated algorithms.
4. Decision: Based on how closely the new sample matches the stored template, the system decides whether to grant or deny access. If the match meets the predefined confidence threshold, authentication succeeds.
This combination of unique biological data and algorithmic matching makes biometric authentication not only convenient but highly secure compared to traditional methods such as passwords.
Why is Biometric Authentication the Future of Security?
Biometric authentication is widely used across industries for fast, secure, and easy identity verification. It is changing how enterprises protect users and improve security.
Enhanced Accuracy and Reliability
In 2025, 16 billion passwords were leaked, making it one of the largest data breaches ever recorded. Biometric authentication uses unique physical or behavioral traits that are highly difficult to duplicate or alter. Unlike passwords or PINs, which can be forgotten, guessed, or stolen, biometric data offers a precise and reliable way to verify identity.
Difficult to Forge or Replicate
One of the biggest advantages of biometric authentication is that it’s nearly impossible to forge or replicate a person’s unique traits, such as fingerprints, iris patterns, or facial structure. This makes biometric authentication far more resistant to cyberattacks like credential theft, phishing, and brute-force hacking.
Convenience and User Experience
Biometric authentication streamlines the user experience by eliminating the need to remember complex passwords or carry physical tokens. Users can simply scan their finger, face, or even authenticate with their voice to quickly and securely gain access.
Integration with Multi-Factor Authentication (MFA)
For even stronger security, biometric authentication is often integrated as one factor within multi-factor authentication (MFA) setups. Combining biometric authentication with other factors such as one-time passcodes or hardware tokens creates layered defenses that are much harder for attackers to penetrate.
Applications of Biometric Authentication
49% of all data breaches involve compromised passwords. Thus, Biometric authentication is essential across industries for providing fast, secure, and easy identity verification. It is transforming how enterprises experience security in key areas.
Mobile Devices and Consumer Electronics
Mobile phones, tablets, and laptops commonly use biometric authentication methods such as fingerprint scanners and facial recognition. This allows users to quickly unlock their devices or authorize payments without needing passwords. Biometric authentication makes device security seamless and personal, reducing the risk of unauthorized access.
Banking and Financial Services
The banking industry has embraced biometric authentication to protect customer accounts and transactions. Fingerprint and facial recognition are used for secure login to mobile apps, ATM access, and transaction approvals. By implementing biometric authentication, banks reduce fraud and identity theft while offering customers a smooth, secure experience.
Border Control and Government ID Verification
Airports and government agencies use biometric authentication extensively for identity verification during immigration and border control. Facial recognition, iris scans, and fingerprint authentication help speed up passenger processing and prevent identity fraud. Government ID verification systems use biometrics to enhance security in issuing passports, driver’s licenses, and social services.
Workplace Access and Time Tracking
Businesses use biometric authentication for secure physical access to buildings and restricted areas, replacing or complementing traditional keycards. Fingerprints or iris scans ensure only authorized personnel enter sensitive zones. Additionally, biometric authentication systems track employee attendance and working hours accurately, eliminating buddy punching and ghost attendance.
Challenges and Considerations in Biometric Authentication
While biometric authentication provides enhanced security and convenience, it also comes with its own set of challenges and important considerations that organizations must address to implement it effectively.
Privacy Concerns and Data Protection
Biometric authentication involves collecting highly sensitive personal data, raising significant privacy issues. Organizations must ensure biometric data is stored securely using strong encryption to prevent theft or misuse.
37% of cyberattacks in 2025 used brute force to guess weak passwords, up from 21% last year. This shows how easily hackers can exploit simple passwords.
Unlike passwords, biometric traits are immutable—once compromised, they cannot be changed. Proper legal and ethical frameworks should govern how biometric data is collected, stored, and used, respecting user consent and privacy rights.
Technology Limitations and False Positives
No biometric system is flawless. False positives (incorrectly granting access to unauthorized users) and false negatives (denying access to authorized users) remain challenges. Environmental conditions, aging, or injuries can affect accuracy.
Implementation Costs and Infrastructure Needs
Deploying biometric authentication requires significant investments in hardware sensors, software platforms, and integration with existing IT infrastructure. Additionally, ongoing maintenance, updates, and staff training add to the total cost of ownership. Organizations must balance these upfront expenses against the long-term benefits of enhanced security.
Data Breach Risks
A breach involving biometric data is far more serious than traditional password leaks since biometric traits cannot be reset. Protecting biometric databases with cutting-edge cybersecurity measures—such as encryption, tokenization, and decentralized storage—is critical to mitigate these risks.
User Acceptance and Accessibility
Not all users may be comfortable or able to provide biometric data due to personal, cultural, or religious reasons. Disabilities or age-related changes can also impact the effectiveness of certain biometric modalities, potentially excluding some individuals. Considerations for accessibility and alternative authentication options are essential.
Ethical and Legal Challenges
The growing use of biometric authentication has sparked debates over surveillance, consent, and individual rights. Without clear regulation, there is a risk of misuse or overreach by governments or organizations. Transparent policies and compliance with data protection laws are vital.
Standardization and Interoperability
The lack of universal standards for biometric authentication can lead to compatibility and integration issues across different systems and devices. This fragmentation may reduce security and user convenience.
How Emerging Technologies are Shaping Biometric Authentication?
The landscape of biometric authentication is rapidly evolving, driven by continuous advancements in technology that enhance security, accuracy, and user experience.
The biometrics market overall is estimated at $52.64 billion in 2025, with expectations to reach $93.57 billion by 2029, growing at a CAGR of 15.5%.
These emerging technologies are reshaping how biometric authentication is implemented and adopted across industries.
Contactless Biometrics
With hygiene concerns and convenience in mind, contactless biometric authentication methods like facial recognition and palm scanning are becoming increasingly popular. These systems allow users to authenticate without physical contact, reducing friction in access processes while maintaining high security.
Multi-Modal Biometrics
Next-generation biometric authentication combines multiple biometric traits—such as fingerprint, face, and voice recognition—into a single system. This multi-modal approach increases security by requiring various forms of identity verification, making unauthorized access significantly more difficult.
Artificial Intelligence (AI) and Machine Learning
AI powers the intelligence behind modern biometric authentication. It improves the accuracy of recognition by continuously learning from vast datasets and detecting anomalies that indicate potential fraud. AI-driven biometric authentication also enhances liveness detection, ensuring that biometric inputs come from real users rather than photos or deepfakes.
Behavioral Biometrics
Behavioral biometric authentication analyzes unique user interactions such as typing rhythms, mouse movements, and gait patterns. These subtle behaviors create an additional layer of security and allow continuous, passive authentication during a user’s session.
Cloud-Based Solutions and IoT Integration
Cloud computing enables scalable and efficient biometric authentication services accessible from anywhere. Integration with Internet of Things (IoT) devices expands biometric authentication to smart homes, wearable technology, and connected environments, providing seamless security across various touchpoints.
Blockchain for Biometric Security
Blockchain technology is being explored to enhance the privacy and integrity of biometric data. Decentralized storage and verifiable chains of custody reduce the risks of data tampering and unauthorized access, bolstering trust in biometric authentication systems.
Continuous and Adaptive Authentication
Emerging biometric authentication systems no longer rely on one-time verification. Continuous authentication monitors user behavior in real-time, adjusting the level of security dynamically based on risk factors like location, device health, and network security status.
How CloudEagle Supports Access Governance?
CloudEagle.ai is an advanced SaaS management and access governance platform that helps enterprises manage and secure access to applications quickly and efficiently. It integrates with over 500 SaaS apps, including popular identity providers such as Okta and Azure AD, syncing data to maintain consistent and secure access across systems.
Here’s how CloudEagle helps streamline access governance in enterprises:
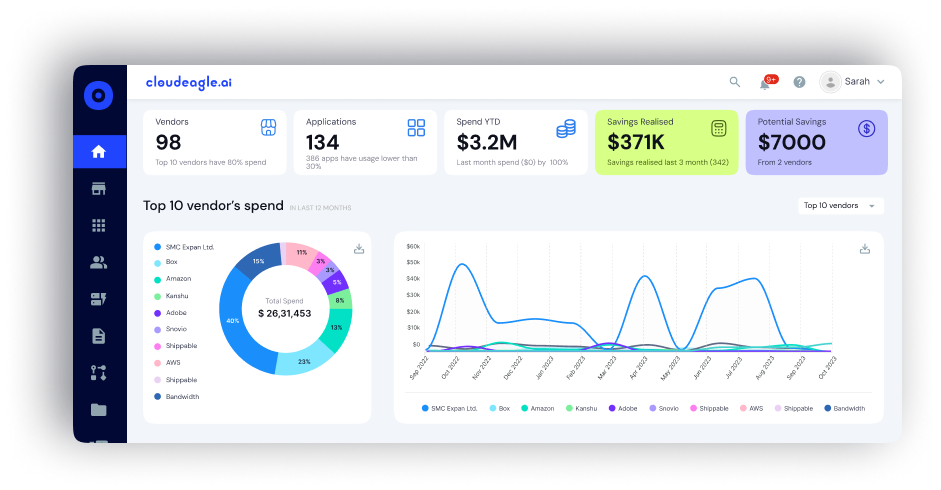
1. Centralized Access Visibility
CloudEagle provides a unified dashboard where administrators get real-time insights into who has access to which applications. This centralized visibility helps monitor permissions, detect anomalies, and maintain audit trails for compliance and security audits.
2. Automated Access Lifecycle Management
When employees leave, CloudEagle instantly revokes their access to all company apps and systems. This automatic offboarding helps prevent security risks like unauthorized access from former staff. It eliminates the need for IT to track exit dates manually and speeds up compliance with security policies.

By automating offboarding, CloudEagle protects sensitive data and reduces the risks of data breaches, keeping the organization secure at all times.
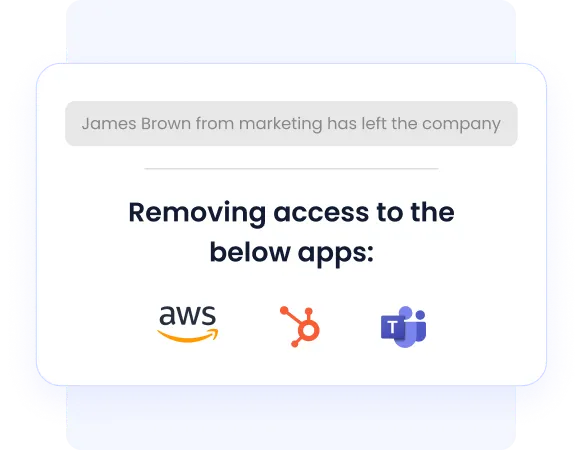
Know how Treasure Data Streamlined Employee Offboarding using CloudEagle.ai.
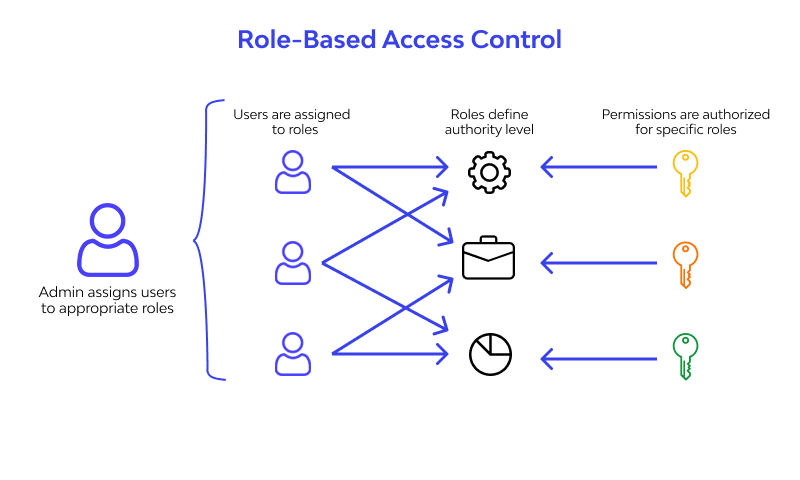
3. Role-Based Access Controls
The platform supports granular, role-based access control policies that ensure users only get the permissions they need. Additional context, like location, department, or projec,t can be factored in to tighten security and reduce overprovisioning.
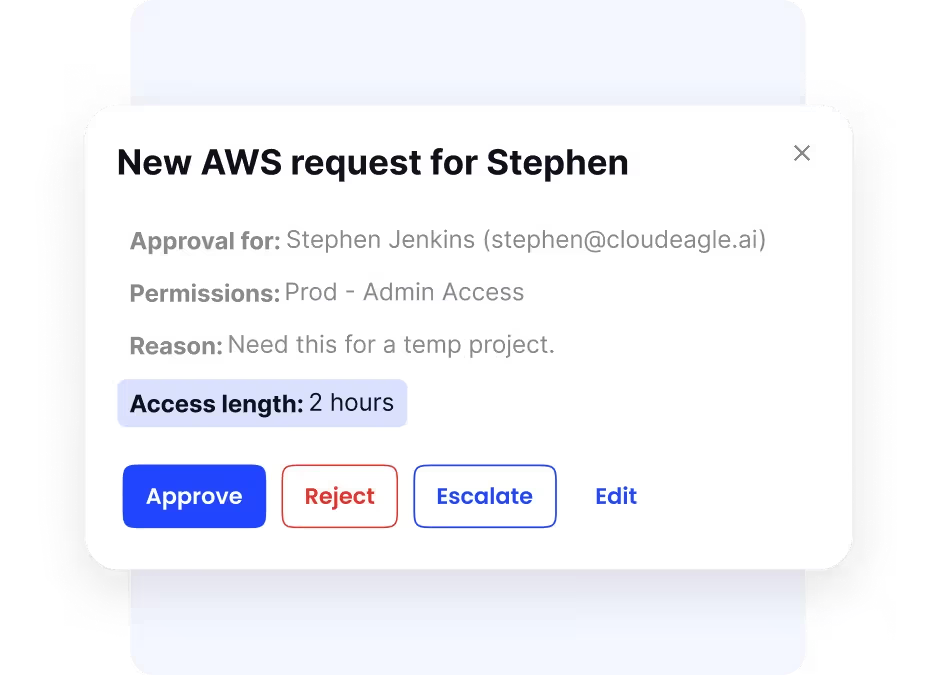
4. Just-In-Time Access Control
CloudEagle enables just-in-time access by granting temporary permissions for specific tasks or projects. Access automatically expires after the set period, reducing the risk of lingering access for contractors or temporary roles.
5. Simplified Access Reviews and Compliance
Manual access reviews are slow, error-prone, and often miss compliance requirements. In fact, about 95% of organizations still rely on manual reviews, which can leave security gaps.
CloudEagle.ai automates access reviews with AI-powered monitoring, instantly generating audit-ready reports. This saves time, reduces errors, and helps quickly remove outdated or excessive permissions, ensuring stronger security and easier compliance.
6. Continuous Monitoring and Compliance Reporting
The platform continuously monitors access events and user behavior to flag unusual activity. It also generates detailed audit reports aligned with standards such as SOC 2, ISO 27001, HIPAA, and GDPR, simplifying compliance audits.

7. Self-Service App Catalog
CloudEagle.ai’s self-service app catalog lets employees easily find and request access to the SaaS apps they need. Instead of waiting for IT approval, users can quickly browse approved apps and request access themselves, speeding up the process and boosting productivity.

The catalog also helps prevent shadow IT by promoting the use of approved apps and limiting unauthorized software. Employees can even request apps and get approvals directly through Slack or Microsoft Teams, making it simple and fast.
Take a moment to hear from Alice Park at Remediant, who shares her experience using CloudEagle.ai. She describes how the platform simplified their access management and significantly enhanced their security posture.
Conclusion
Biometric authentication is quickly changing the future of digital security. It offers better accuracy, ease of use, and strong protection against fraud, making it the preferred choice for people and businesses worldwide.
As technologies like artificial intelligence, multi-modal biometrics, and cloud computing improve, biometric systems will become even more secure, adaptable, and easy to use.
Though there are challenges around privacy, cost, and technology, the benefits far outweigh the risks when managed responsibly. From smartphones to government security, biometrics play a key role in protecting digital identities in today’s connected world.
Looking forward, the use of biometric authentication will grow as the demand for stronger security and smoother user experiences rises. Enterprises adopting biometrics now are not only protecting assets but also preparing for the future of security.
Are you ready to strengthen your enterprise security with cutting-edge biometric authentication?
Schedule a demo with CloudEagle.ai today and take your identity security to the next level.
FAQs
1. How secure is biometric authentication compared to passwords?
Biometric authentication is generally more secure than passwords because it relies on traits that are unique to each person and very difficult to steal, guess, or replicate.
2. Where is biometric authentication commonly used?
Biometric authentication is widely used in mobile devices, banking, government ID verification, workplace access, and border control to enhance security and user convenience.
3. Can biometric authentication be fooled by fake fingerprints or photos?
Modern biometric authentication systems use liveness detection and anti-spoofing technologies to detect and block fake biometrics like masks, photos, or replicas.
4. Is biometric authentication accessible to everyone?
Some users may face difficulties using certain biometric authentication methods due to physical disabilities, age, or environmental factors. Alternative authentication options are important for inclusivity.
5. Does biometric authentication slow down the login process?
No, biometric authentication typically speeds up access by allowing quick, contactless verification without the need to type or remember passwords.

%201.svg)








.avif)




.avif)
.avif)




.png)









