HIPAA Compliance Checklist for 2025

Without proper identity and access management strategies, enterprises face significant risks. According to CloudEagle.ai’s IGA report, 28% of enterprises have experienced major security incidents due to overprivileged access.
This highlights the importance of implementing a robust identity and access management tool that helps prevent such vulnerabilities. However, with so many options on the market, what is the most efficient way to select the right identity and access management tool?
Choosing the right identity and access management tool is important for your enterprise’s security, efficiency, and compliance. The best IAM platforms provide real-time access monitoring, automatic user setup, and smart policies that match access to job roles and changing needs.
Let’s explore the top 10 tips to help you pick a scalable, secure, and future-ready IAM strategy.
TL;DR
- Understand your organization’s rules and regulations (like GDPR, HIPAA). Pick IAM tools that offer strong login protection, clear audit logs, and help you meet those requirements easily.
- Choose IAM platforms that connect smoothly with your current systems (cloud, on-premises, SaaS) and can grow with your business, keeping everything managed in one place.
- Go for IAM solutions that let you set exact access rules based on roles and user details, ensuring people only get the access they need — nothing more, nothing less.
- Look for tools that automatically handle user setup, access removal, and regular access checks. Also, make sure the system is simple for employees and managers to request and approve access.
- Pick identity and access management tools that tracks access activity all the time, alert you to unusual actions quickly, and come with strong vendor support to keep your system running smoothly long-term.
What are Identity and Access Management Tools?
Identity and Access Management tools are advanced software platforms that secure and manage digital identities and control user access to IT systems, applications, and resources within an enterprise.
Essentially, these tools ensure that the right users, whether employees, contractors, machines, or IoT devices, have the right access to the right resources at the right time for the right reasons, enabling them to do their tasks securely and efficiently.
The Four Key Components of IAM
1. Authentication
Authentication is the process of confirming the identity of a user or system trying to access resources. It ensures that the person or entity is who they claim to be before granting access. Common authentication methods include:
- Passwords or PINs
- Biometric verification (fingerprints, facial recognition)
- Multi-factor authentication (MFA), combining multiple proofs such as a password plus a mobile verification code
- Security tokens or smart cards
Robust authentication acts as the first security gate to protect sensitive applications and data.
2. Authorization
After successful authentication, authorization determines what resources and actions the authenticated user can access or perform. Authorization enforces policies based on user roles and attributes to:
- Grant or deny access to applications, systems, or data
- Apply fine-grained controls like Role-Based Access Control (RBAC) or Attribute-Based Access Control (ABAC)
- Enforce the principle of least privilege, giving users only the access necessary for their job functions and minimizing security risks.
3. User Management (Identity Lifecycle Management)
This component manages the entire lifecycle of a user identity, including:
- Onboarding: Creating accounts and assigning access when a user joins the enterprise.
- Modification: Updating access rights when roles or responsibilities change.
- Offboarding: Removing access promptly when the user leaves.
Effective user management reduces orphaned accounts and unauthorized access by automating provisioning and deprovisioning processes.
4. Centralized Monitoring and Auditing
Continuous monitoring and auditing track who accessed what, when, and how. This enables:
- Detection of suspicious or unauthorized activities in real time
- Maintenance of audit logs for compliance reporting and forensic investigations
- Automated alerts for policy violations or security incidents
Centralized monitoring provides transparency and enforces accountability across the enterprise’s systems.
Why Do You Need Identity and Access Management Software?
Identity and Access Management (IAM) tools provide several key benefits that are critical for enterprises. Here are the main points:
Strengthened Security: IAM ensures only authorized users can access sensitive data and systems by enforcing strong authentication methods such as multi-factor authentication (MFA) and single sign-on (SSO). It reduces risks of data breaches, insider threats, and identity theft by applying the principle of least privilege and monitoring user activity to detect anomalies early.
According to CloudEagle.ai’s IGA report, Chetna Mahajan, Global CDO & CIO, Webflow, believes:
“IAM is often the most underfunded yet mission-critical part of security. But those taking a proactive approach, starting with automation and AI-driven governance, are not just reducing risk, they’re unlocking efficiency and long-term cost savings.”
Improved Regulatory Compliance: IAM systems help enterprises comply with industry regulations by maintaining detailed access logs, generating audit-ready reports, and enforcing consistent security policies across all systems. This reduces the risk of penalties and simplifies audits.
Enhanced User Experience and Productivity: Features like SSO and self-service password reset portals make it easier for users to access resources securely without repetitive logins or IT helpdesk dependencies, improving satisfaction and operational efficiency.
Centralized Access Control and Governance: An Identity and access management tool gives IT centralized management of user roles, permissions, and lifecycle events (onboarding, offboarding), which streamlines administration and ensures access remains in alignment with current business needs and security policies.
Reduction in Insider Threat Risks: By monitoring user behavior, promptly revoking access when needed, and enforcing granular access controls, IAM minimizes risks posed by internal actors or compromised accounts.
Operational Efficiency and Automation: Automation of user provisioning, deprovisioning, license, and access reviews saves time, reduces human errors, and allows IT staff to focus on strategic tasks.
Support for Scalable, Hybrid Environments: Modern IAM solutions integrate well with cloud, on-premises, and hybrid IT environments, providing seamless identity and access management across diverse infrastructures.
10 Expert Tips to Choose the Right Identity and Access Management Tool
Choosing the right identity and access management platform is key to protecting your business and ensuring smooth, compliant user access. To decide well, look beyond basic features and focus on security, scalability, integration, and how well it improves operations.
1. Define Your Security and Compliance Requirements
Start by clearly outlining your organization’s security policies, regulatory requirements, and compliance standards such as GDPR, HIPAA, or SOX. The ideal identity and access management software should provide detailed audit trails and reporting features to help your enterprise demonstrate compliance easily.
Understanding what regulations apply to your business ensures the identity and access management tools supports necessary controls. Look for tools with built-in compliance automation and strong identity lifecycle management features to keep audits straightforward and reduce manual overhead.
2. Evaluate Integration Capabilities
Choose identity and access management tools that seamlessly integrate with your existing IT ecosystem, including cloud services, on-premises systems, SaaS applications, and identity directories like Active Directory or LDAP. Support for open standards such as SAML, OAuth, OIDC, and SCIM ensures smoother implementation and interoperability.
Good integration reduces complexity and avoids creating security gaps. Platforms with broad connectivity enable centralized identity governance and unify management across various environments, improving operational efficiency.
3. Prioritize Role-Based and Attribute-Based Access Control
Look for identity and access management platforms offering fine-grained policy models like Role-Based Access Control (RBAC) and Attribute-Based Access Control (ABAC). These allow precise access assignments tailored to user roles, attributes, or context, reducing overprovisioning and minimizing security risks.
Granular access control helps enforce the principle of least privilege, ensuring users get only the permissions needed to perform their duties. This flexibility is critical in dynamic business environments to address evolving access needs securely.
4. Ensure Multi-Factor Authentication (MFA) Is Included
Multi-factor authentication is a vital security layer provided by advanced identity and access management security tools. MFA combines passwords with biometrics, one-time codes, or push notifications to confirm user identities dynamically.
Including MFA drastically lowers the risk of unauthorized access by requiring multiple proofs of identity. When evaluating identity and access management tools, ensure MFA options are easy to use and support diverse authentication methods to fit your enterprise’s needs.
5. Look for Centralized Identity Governance
Effective user access management tools unify all identity-related processes like authentication, authorization, and governance into one cohesive platform. Automation of user lifecycle events like onboarding, role changes, and offboarding prevents orphaned accounts and enforces least privilege access.
Centralized governance improves visibility into who has access to what, streamlines compliance workflows, and reduces risks related to access sprawl. This strategic control supports both security and operational efficiency.
6. Assess Usability for IT and End Users
The best identity and access management tools balance robust security with simplicity. They offer intuitive portals for both administrators and end users, supporting features like Single Sign-On (SSO), self-service password resets, and convenient access requests.
Good usability drives wider adoption, reduces IT support requests, and accelerates access approvals. Platforms that integrate with collaboration tools (e.g., Slack) improve user experience and streamline administrative workflows.
7. Consider Automation Features
Advanced identity lifecycle management tools automate key tasks such as provisioning, deprovisioning, and periodic access certification. Automation helps minimize human errors, accelerates access changes, and frees IT teams to focus on critical strategic initiatives.
Look for identity and access management tools that allow policy-driven automation aligned with your security goals. This capability enhances governance, reduces administrative burden, and improves overall security posture.
Know how Remediant streamlined user provisioning & deprovisioning with CloudEagle.ai and saved hundreds of employee hours.
8. Validate Real-Time Monitoring and Auditing Tools
Visibility is key for secure access management. Identity and access management tools with real-time monitoring and AI-driven alerting identify anomalous user behavior early—such as unusual login locations or access patterns—helping prevent breaches.
Comprehensive audit logs support compliance reporting and forensic investigations. Real-time insights enable rapid response to risks while maintaining transparency across the enterprise’s access environment.
9. Review Scalability and Cloud Readiness
Given today’s hybrid and multi-cloud environments, choose IAM platforms that scale seamlessly across global user populations and support various deployment models. Cloud readiness ensures future-proof infrastructure that can grow as your enterprise expands or adopts new technologies.
Scalable identity and access management tools maintain performance and security without complicated rearchitecture. This flexibility is essential for enterprises with dynamic needs and geographically distributed users.
10. Analyze Vendor Support and SLA Commitments
Select a vendor with a strong reputation for reliable support and clear Service Level Agreements (SLAs). Responsive customer service and ongoing product updates aligned with emerging security trends are vital for long-term IAM success.
A good vendor partnership ensures smooth deployment, helps navigate evolving compliance landscapes, and supports continuous improvement of your identity and access management security tools.
How CloudEagle.ai Can Help Enterprises Manage Access?
CloudEagle.ai is an advanced SaaS management and governance platform that helps enterprises manage app access. Here’s how it helps:
See Everything in One Place
CloudEagle.ai gives you a complete and clear view of who has access to which applications, why they have that access, and how they are utilizing those apps.

By integrating with over 500 systems such as SSO solutions, HRIS, and financial platforms, it creates a unified dashboard that lets you manage all user permissions easily. This centralized visibility helps prevent excess or inappropriate access and supports better decision-making.
Watch Access in Real Time
The platform continuously monitors user access activities in real time. Using advanced AI and machine learning, it detects unusual behaviors, such as access from unexpected locations, times, or devices, and immediately alerts security teams.
This early warning system helps enterprises quickly respond to potential threats, reducing the risk of security breaches and insider attacks before damage occurs.
CEO of CloudEagle.ai, Nidhi Jain, believes that the most successful IAM implementations leverage AI to accelerate human decision-making. Organizations that embrace this partnership model see both enhanced security and improved operational efficiency.
Role-Based and Context-Aware Access Controls: The platform enables detailed role-based access policies, making sure users get only the permissions needed for their specific job roles.

Moreover, access can be tailored and limited according to contextual factors like user location, department, or job title, providing an additional security layer.
Automate User Access
CloudEagle.ai automates the entire identity lifecycle process. When an employee joins, changes roles, or leaves the company, the platform automatically grants or revokes access based on predefined role permissions.

This zero-touch provisioning eliminates manual errors, reduces security risks from orphaned accounts, and accelerates onboarding and offboarding processes, making IT operations more efficient and secure.

Know this inspiring customer success story of how CloudEagle.ai helped Bloom & Wild streamline employee onboarding and offboarding.
Temporary Access When Needed
To enhance security and flexibility, CloudEagle.ai supports just-in-time (JIT) or temporary access controls. This means you can grant elevated or sensitive access to users only for the specific time they need it, such as for a project or a contract.
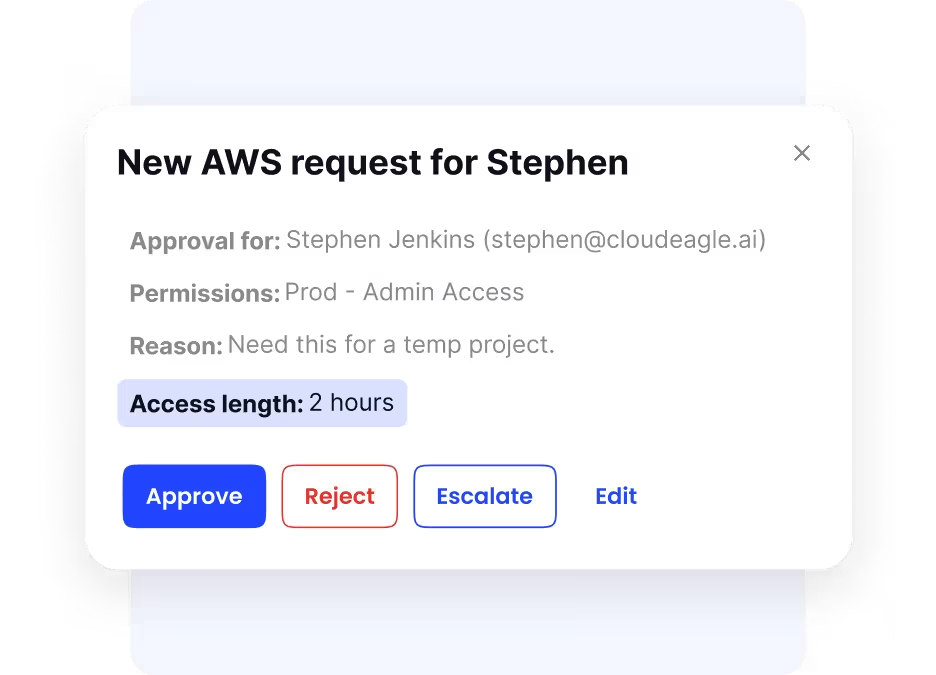
After that period, the access automatically expires, preventing “access creep” where permissions remain longer than necessary and pose security risks.
Help with Compliance and Audits
CloudEagle.ai simplifies meeting regulatory requirements like SOC 2, ISO 27001, GDPR, and others by automating periodic access reviews and certifications. It maintains centralized, audit-ready logs and generates compliance reports quickly, greatly reducing the time and effort required during audit seasons.

Control Privileged Accounts
Privileged accounts hold powerful access rights and can pose significant risks if misused. CloudEagle.ai provides different access control features that decide who gets elevated permissions, for how long, and monitors their activities continuously. This helps prevent insider threats and limits the potential damage from compromised privileged accounts.
Simple Access Requests and Approvals
The platform offers a user-friendly, self-service portal where employees can request access to the apps they need, integrated seamlessly with tools like Slack for convenience. Managers and administrators receive instant notifications for approval or denial of these requests.

Approvals can follow customized workflows, incorporating multi-step and context-based policies (e.g., based on job role or department), ensuring strong governance without slowing down business operations.
Regular Automated Access Reviews
CloudEagle.ai checks regularly if users still need their access. If someone has access they don’t need, it alerts you so you can remove it quickly. This keeps your systems safe by making sure people only have the access they really need.

To enhance enterprise access governance, simplifying the processes of user provisioning and deprovisioning is essential. Discover how Alice Park from Remediant improved onboarding and offboarding using CloudEagle’s automated workflows in her testimonial.
Conclusion
Effective identity and access management is essential for securing today’s complex enterprise environments. By using the right IAM tools and platforms, businesses can protect digital assets, automate user access, and stay compliant with regulations.
CloudEagle.ai provide real-time visibility, automated provisioning, and robust security controls, enabling enterprises to reduce risk while enhancing efficiency. Investing in smart, scalable IAM is not just about technology; it’s a strategic advantage that empowers secure growth and better user experiences.
Ready to elevate your enterprise security and streamline access management?
Schedule a demo with CloudEagle.ai to see how our IAM solutions protect your business and boost your digital transformation.
FAQs
1. What is the IAM toolkit?
The IAM toolkit comprises a set of user access management tools, processes, and policies designed to securely manage digital identities and control user access across various systems.
2. What is an IAM framework?
An IAM framework is a structured set of guidelines and best practices enterprises use to govern identity and access management policies, processes, and technology implementations.
3. What is identity and access management software?
IAM software securely manages user identities and access permissions to IT resources, automating tasks like authentication, authorization, provisioning, and compliance reporting.
4. What are IGA tools?
Identity Governance and Administration (IGA) tools automate access certifications, reviews, policy enforcement, and lifecycle management to maintain secure and compliant identity governance.
5. Which of the following is an IAM security tool?
CyberArk, SailPoint, ForgeRock, and CloudEagle.ai are leading examples of IAM security tools, offering advanced features for access control, risk management, and compliance.

%201.svg)








.avif)




.avif)
.avif)




.png)









