HIPAA Compliance Checklist for 2025

According to CloudEagle.ai's IGA report, 28% of enterprises experienced major security incidents due to overprivileged access. This risk is a growing concern as enterprises continue to rely on identity and access management (IAM) tools to protect sensitive data, simplify user access, and maintain compliance.
Ping Identity has been a reliable choice for IAM, but as businesses grow, they need tools that better match their specific needs. Whether you're looking for better scalability, more features, or stronger security, many Ping Identity alternatives for 2025 can help you reach your goals.
Let’s explore the top Ping Identity competitors to take your identity management to the next level.
TL;DR
- Ping Identity is a top IAM solution offering SSO, MFA, and Identity Governance to secure access across applications.
- Many enterprises seek Ping Identity alternatives for better cost efficiency, customization, integration, and advanced security.
- Key evaluation criteria for competitors include strong security, scalability, easy administration, and flexible pricing models.
- Alternatives often provide enhanced scalability, AI-driven threat detection, and more tailored user access management.
- Selecting the right IAM requires aligning with your security needs, long-term growth, and smooth integration with existing IT systems.
What is Ping Identity?
Ping Identity is a leading provider of Identity and Access Management (IAM) solutions, helping businesses manage and secure user identities across apps and systems. As IT environments become increasingly complex and security threats escalate, Ping Identity ensures that only authorized users can access the right resources, thereby enhancing both security and the user experience.
Key Features of Ping Identity:
1. Single Sign-On (SSO): Users log in once and gain access to multiple applications without needing to re-enter credentials, reducing password fatigue and improving security.
2. Multi-Factor Authentication (MFA): Adds extra security by requiring users to verify their identity with more than one method (e.g., password and one-time passcode).
3. Identity Governance: Helps manage who has access to what by automating workflows, access reviews, and compliance checks, ensuring the right people have the right access.
4. Federated Identity Management: Lets businesses manage identities across different enterprises and platforms, making collaboration easier while keeping access control tight.
5. Adaptive Authentication: Uses machine learning to adjust authentication methods based on factors like user behavior, device, or location, adding extra protection against unusual activities.
6. Access Management: Controls who can access which resources, when, and under what conditions, ensuring compliance with security policies.
Why Look for Ping Identity Alternatives?
While Ping Identity is a trusted IAM solution, many enterprises are exploring alternatives for:
1. Cost Efficiency: Ping Identity's pricing may not always be the most competitive, especially as companies scale. Some alternatives offer more flexible and affordable pricing models without sacrificing essential IAM features.
2. Customization & Flexibility: If your enterprise needs tailored identity management solutions, Ping Identity alternatives may provide greater customization options for user provisioning, access control, and overall configuration, offering more flexibility to suit your specific needs.
3. Integration & Ecosystem Compatibility: Enterprises often rely on a variety of tools and applications. Ping Identity alternatives may offer more seamless integration with a broader range of third-party apps, streamlining workflows and improving operational efficiency.
4. Scalability: As your business grows, so do your IAM needs. Some Ping Identity competitors are better equipped to handle larger volumes of users, devices, and apps, providing a more scalable infrastructure that evolves with your enterprise.
5. User Experience: While Ping Identity offers solid functionality, its user interface and experience may not be ideal for every enterprise. Alternatives might provide more intuitive, easy-to-use interfaces, improving the overall experience for both IT teams and end users.
6. Vendor Support and Service: The level of customer support from Ping Identity may not always meet every enterprise’s needs. Some competitors offer better support models, including personalized services and 24/7 assistance, ensuring that IAM challenges are addressed quickly and efficiently.
Top 10 Ping Identity Competitors
As IAM needs grow, many enterprises look for simple and affordable alternatives to Ping Identity. Here are the top options to consider:
1. CloudEagle.ai
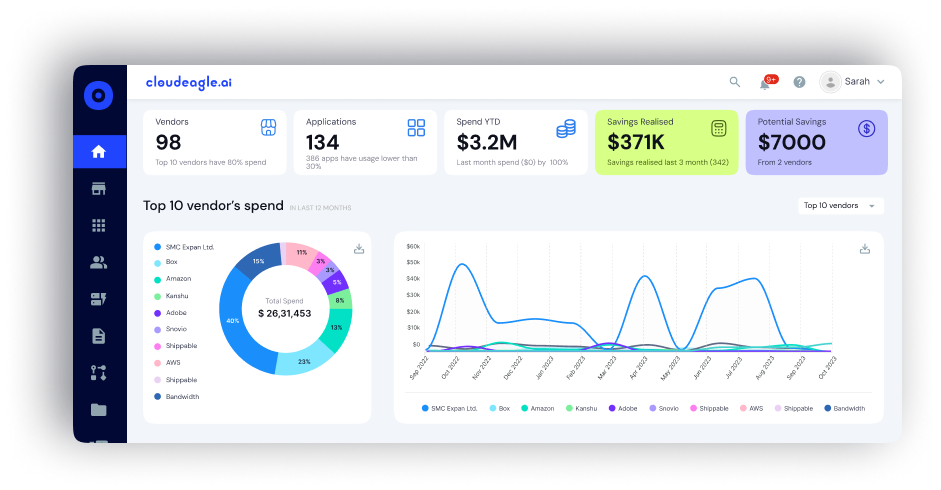
CloudEagle.ai is an advanced SaaS management and access governance platform built for IT, security, and procurement leaders who want more than traditional identity management. It unifies real-time visibility, automated access governance, and streamlined compliance management into a single, powerful solution tailored to meet the complex needs of modern enterprises.
Here’s how CloudEagle.ai transforms IAM:
1. Real-Time Comprehensive Visibility
Many enterprises struggle with shadow IT, where applications and services operate outside the control of the IT team, leading to security risks and wasted resources. CloudEagle.ai provides IT and security teams with real-time visibility into all SaaS apps, users, and access levels across the enterprise.

How it Helps:
- Detects unauthorized and shadow SaaS apps automatically.
- Maps app usage and user access across all departments.
- Helps identify cost leaks and compliance issues instantly.
Learn how CloudEagle.ai helped Rec Room gain complete visibility into free apps used by its teams.
2. Enhanced Access Governance for Stronger Security
CloudEagle.ai automates user access management, from provisioning and deprovisioning to periodic access reviews. It ensures that only the right people have the right access at the right time, with least-privilege access policies in place to reduce over-permissioning risks.
How it Helps:
- Automates user onboarding and offboarding.
- Enforces least-privilege and just-in-time access controls.
- Automatically generates detailed access review reports.
Learn how CloudEagle.ai helped Dezerv automate its app access review process.
3. Effortless Automated Provisioning & Deprovisioning
Manual access management is time-consuming and prone to errors. CloudEagle.ai integrates seamlessly with HRIS tools like Workday and identity providers like Okta and Azure AD to automatically update or revoke access when users join, change roles, or leave the company. This integration ensures compliance while reducing human error.
How it Helps:
- Syncs access updates automatically with HR and identity tools.

- Automatically revokes access when users exit or change roles.
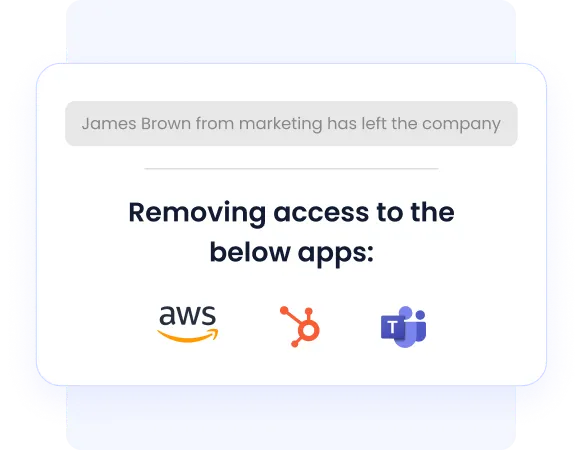
- Prevents unauthorized access to sensitive data.
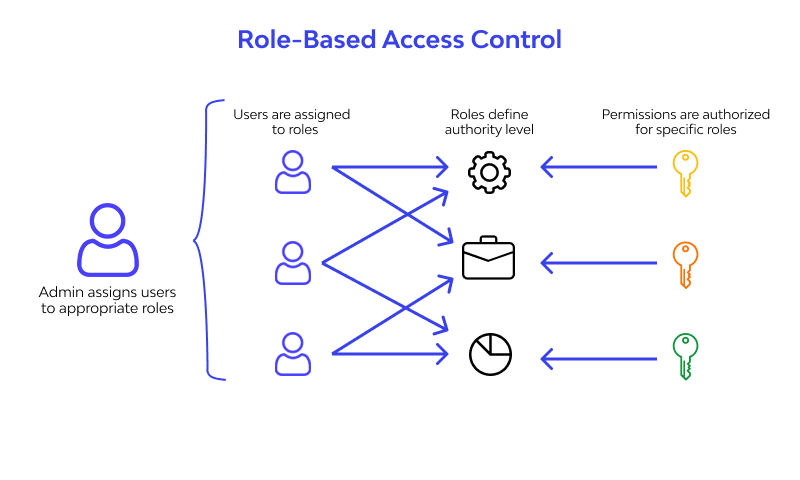
4. Granular Role-Based Access Control (RBAC)
CloudEagle.ai allows IT administrators to assign and manage permissions based on specific job roles and departments. For example, an HR user may have access to Workday and BambooHR, while a finance user can access NetSuite and Expensify. This ensures that users have access to only the resources they need.
How it Helps:
- Assigns access based on job roles and departments.
- Simplifies policy enforcement for compliance frameworks.
- Reduces over-permissioning risks and internal threats.
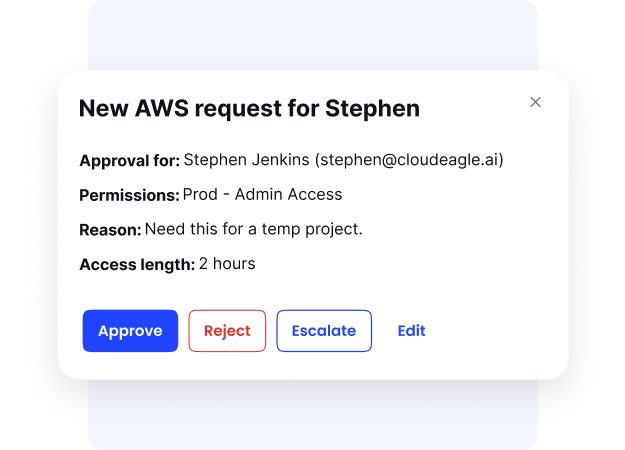
5. Just-In-Time (JIT) Access for Temporary Permissions
Standing access (permanent access) is a security risk. CloudEagle.ai addresses this with Just-In-Time (JIT) access, which provides temporary access only when needed and automatically revokes it once the task is complete. This minimizes exposure to insider threats and accidental data breaches.
How it Helps:
- Grants temporary, time-bound access to apps.
- Supports secure project-based or vendor access.
- Removes standing privileges to reduce security exposure.
6. Intelligent Attribute-Based Access Control (ABAC)
CloudEagle.ai enhances access control by using ABAC, which is based on user attributes like department, location, and job title. For example, a marketing user in New York may get access to HubSpot, while one in London can access Salesforce. This provides flexible, scalable access management for global teams.
How it Helps:
- Automates access based on user attributes.
- Supports hybrid and multi-department environments.
- Reduces manual admin work and errors.
7. Automated Risk & Compliance Workflow Management
Compliance audits can be time-consuming when done manually. CloudEagle.ai automates the process by mapping risks to compliance frameworks, generating audit-ready reports, and tracking remediation efforts in real time. This ensures continuous compliance with standards like ISO 27001, SOC 2, GDPR, and HIPAA.
How it Helps:
- Automatically maps risks to multiple compliance frameworks.
- Continuously generates audit evidence in real time.
- Simplifies the compliance process with automation.
8. Detailed Audit-Ready Reports and Insights
With CloudEagle.ai, IT teams are always ready for audits. The platform logs every access request, change, and approval, providing detailed audit trails. Custom dashboards display key metrics such as access activity, compliance posture, and risk exposure, simplifying the audit process.
How it Helps:
- Centralizes audit reports for easy access.
- Tracks every access action for full transparency.
- Makes compliance verification simple during audits.
9. User-Friendly Self-Service Application Catalog
CloudEagle.ai empowers employees with a self-service app catalog, allowing them to securely request access to approved apps. The platform then triggers automated approval workflows, which reduces IT’s workload, prevents shadow IT, and boosts productivity without compromising governance.

How it Helps:
- Allows employees to securely request app access.
- Automates approval processes via pre-set workflows.
- Prevents unapproved app usage and shadow IT growth.
Know how a Gen AI company streamlined saas access provisioning with CloudEagle.ai’s self‑service app catalog.
2. Microsoft Entra ID (Azure AD)

Microsoft Entra ID, formerly known as Azure AD, is a cloud-based IAM solution that enables enterprises to manage user identities and secure access to apps, including those within the Microsoft ecosystem.
Key Features
- Single Sign-On (SSO): Simplifies user access across multiple applications with a single login.
- Conditional Access: Applies security policies based on user conditions, such as location or device health, ensuring secure access.
Pros
- Seamless integration with Microsoft products.
- Scalable solution for large enterprises.
Cons
- Complex setup and configuration for non-Microsoft environments.
- High cost for advanced enterprise features.
3. Duo Security
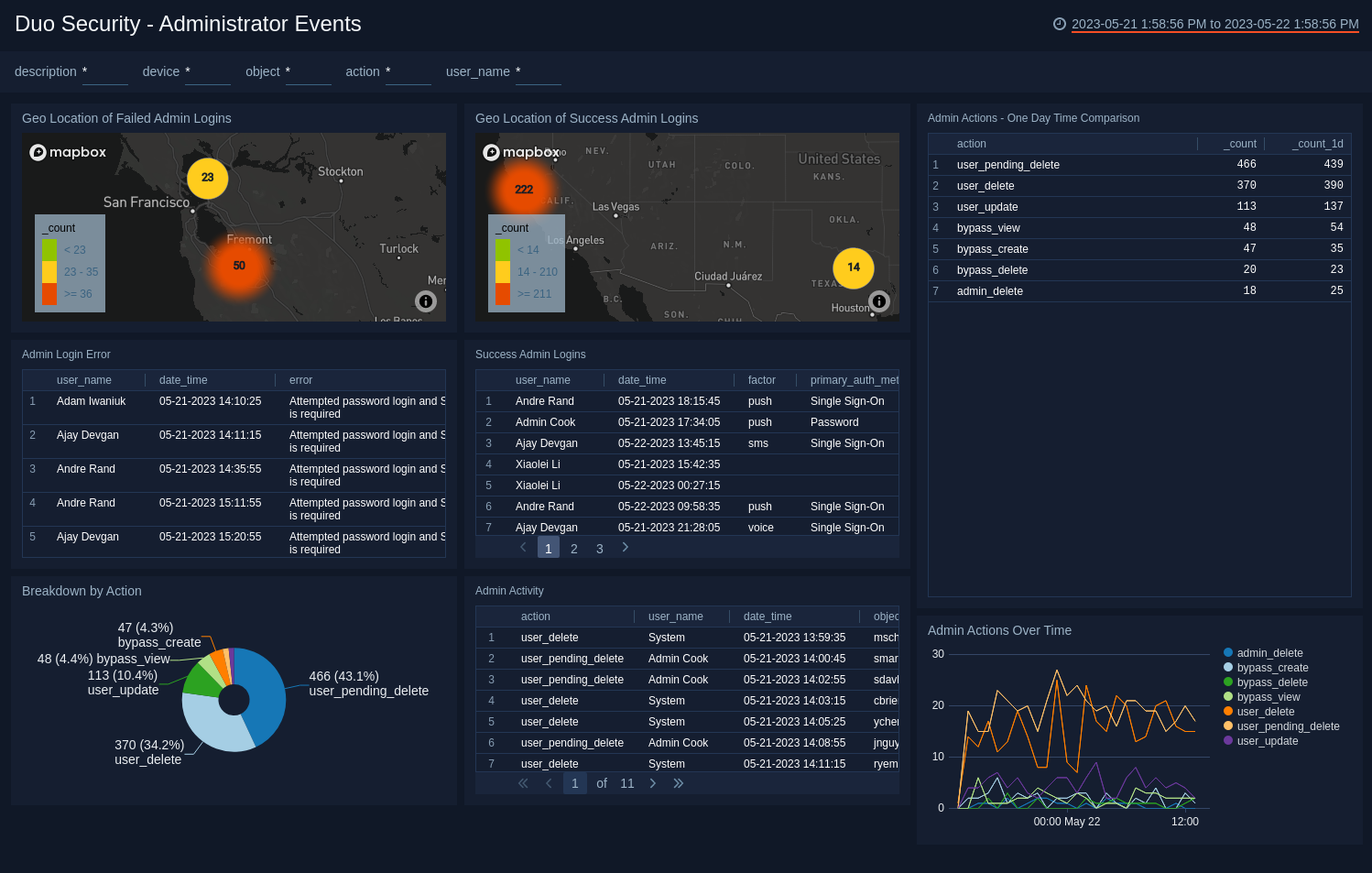
Duo Security offers a simple yet powerful authentication solution, with a focus on providing two-factor authentication (2FA) and securing access to cloud and on-premise applications.
Key Features
- Adaptive Authentication: Adjusts the authentication requirements based on real-time risk assessments.
- Secure Single Sign-On (SSO): Provides a unified access point for all your applications.
Pros
- Simple to deploy and use.
- Works across a variety of devices and apps.
Cons
- Lacks deep identity governance features.
- Limited customization options for advanced workflows.
4. OneLogin
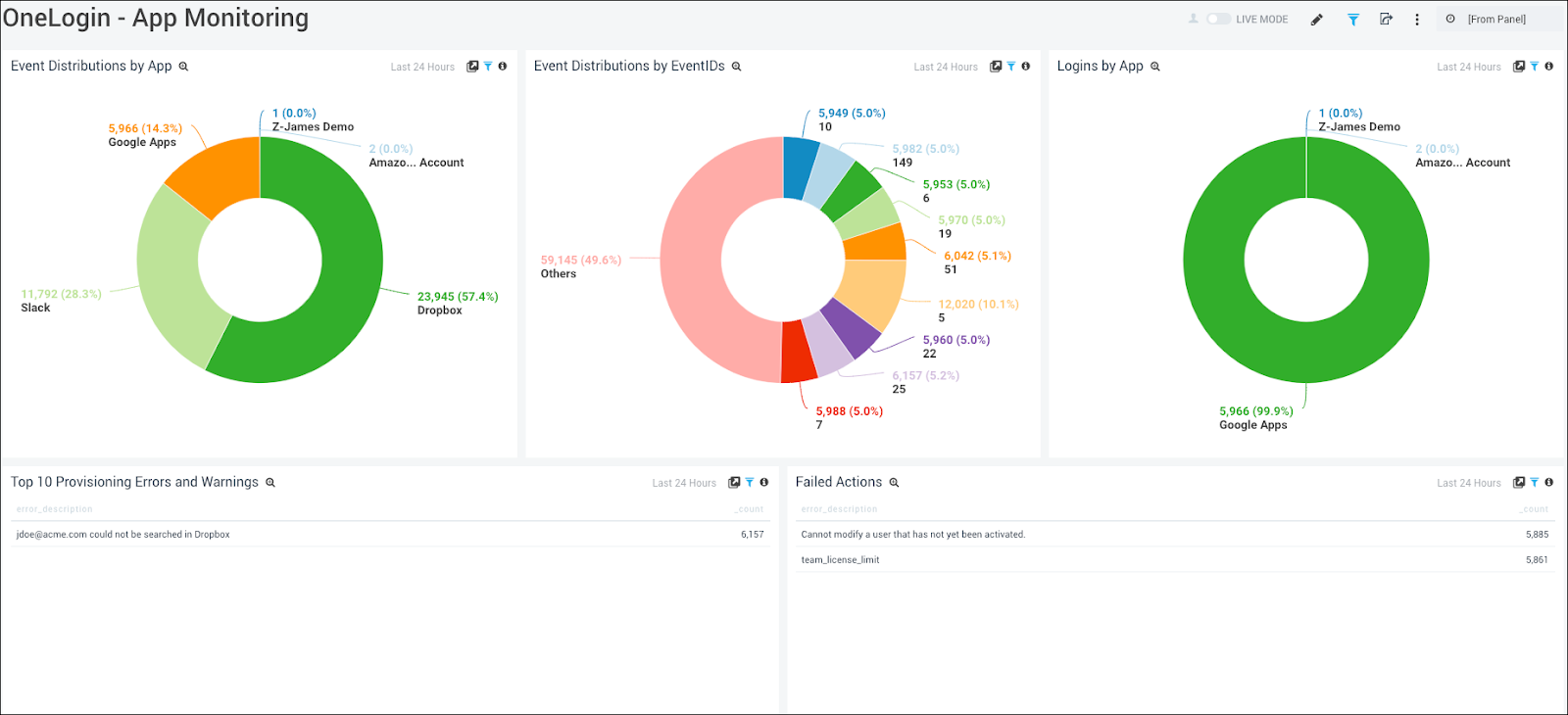
OneLogin is an intuitive cloud-based IAM solution that offers SSO, MFA, and user lifecycle management to ensure secure and seamless access across applications and systems.
Key Features
- Cloud-based SSO: Allows users to access multiple apps with one set of credentials.
- Automated User Provisioning: Automates the process of adding or removing users across systems, reducing manual effort.
Pros
- Easy-to-use interface for IT admins and end-users.
- Strong integrations with third-party applications.
Cons
- Lacks comprehensive governance and audit features.
- Some customization options may require advanced technical expertise.
5. CyberArk
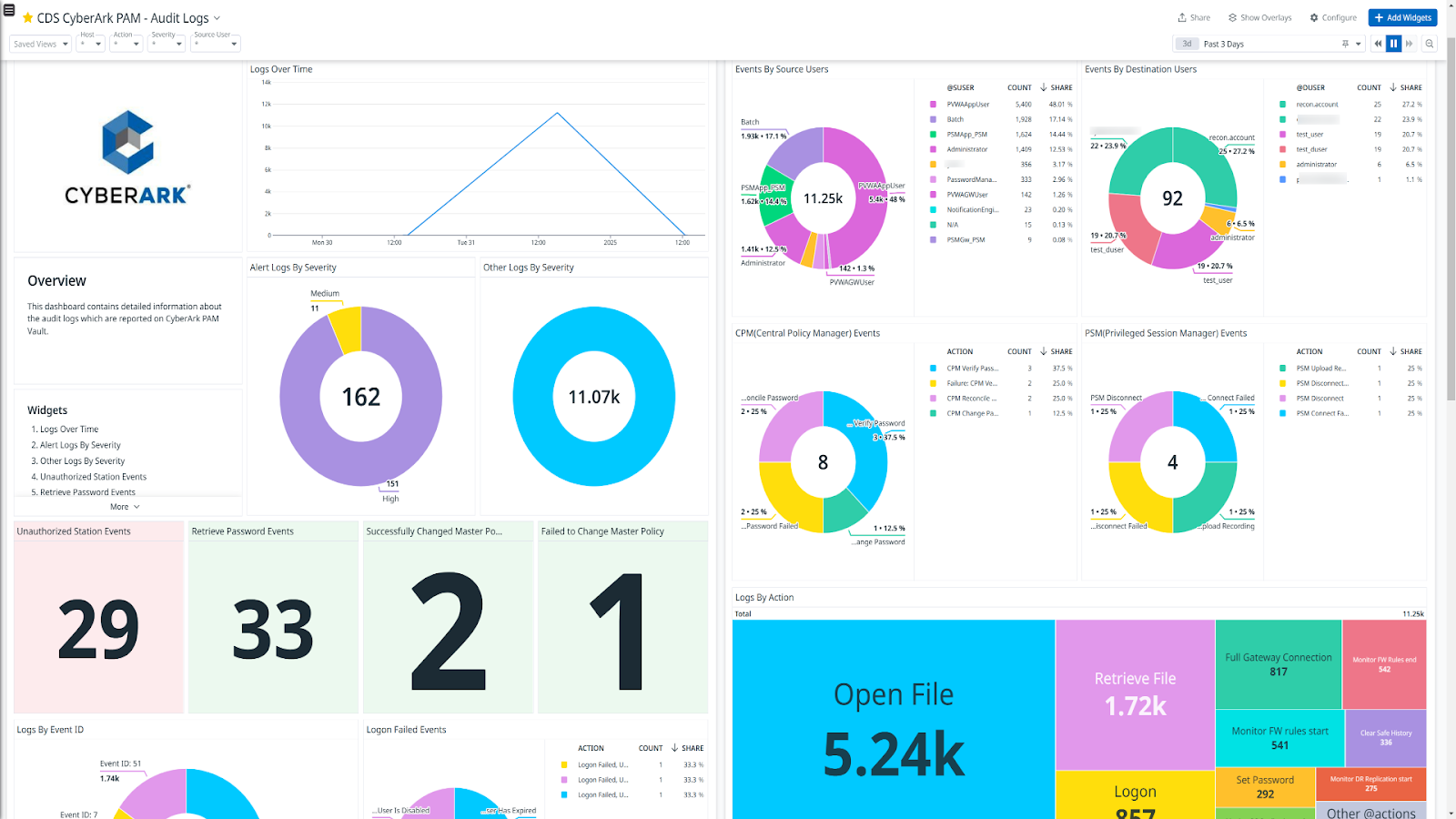
CyberArk focuses on securing privileged access, offering IAM solutions tailored to protect high-value assets and critical systems from internal and external threats.
Key Features
- Privileged Access Management (PAM): Controls access to high-level accounts to minimize risk.
- Session Monitoring: Records and monitors user sessions to ensure compliance and security.
Pros
- Strong focus on securing privileged accounts.
- Comprehensive audit and session monitoring capabilities.
Cons
- High cost for small and medium-sized businesses.
- Setup can be complex, requiring specialized resources.
6. JumpCloud

JumpCloud is a cloud directory service offering IAM, device management, and secure access control, designed to simplify IT management in a single platform.
Key Features
- Universal Directory: Centralizes user, device, and application management in one platform.
- Device Management: Ensures all devices are securely managed and compliant.
Pros
- Simple interface, easy to set up.
- Effective for multi-platform environments.
Cons
- Lacks advanced integration options for complex IT environments.
- Advanced features may require additional configuration.
7. SailPoint
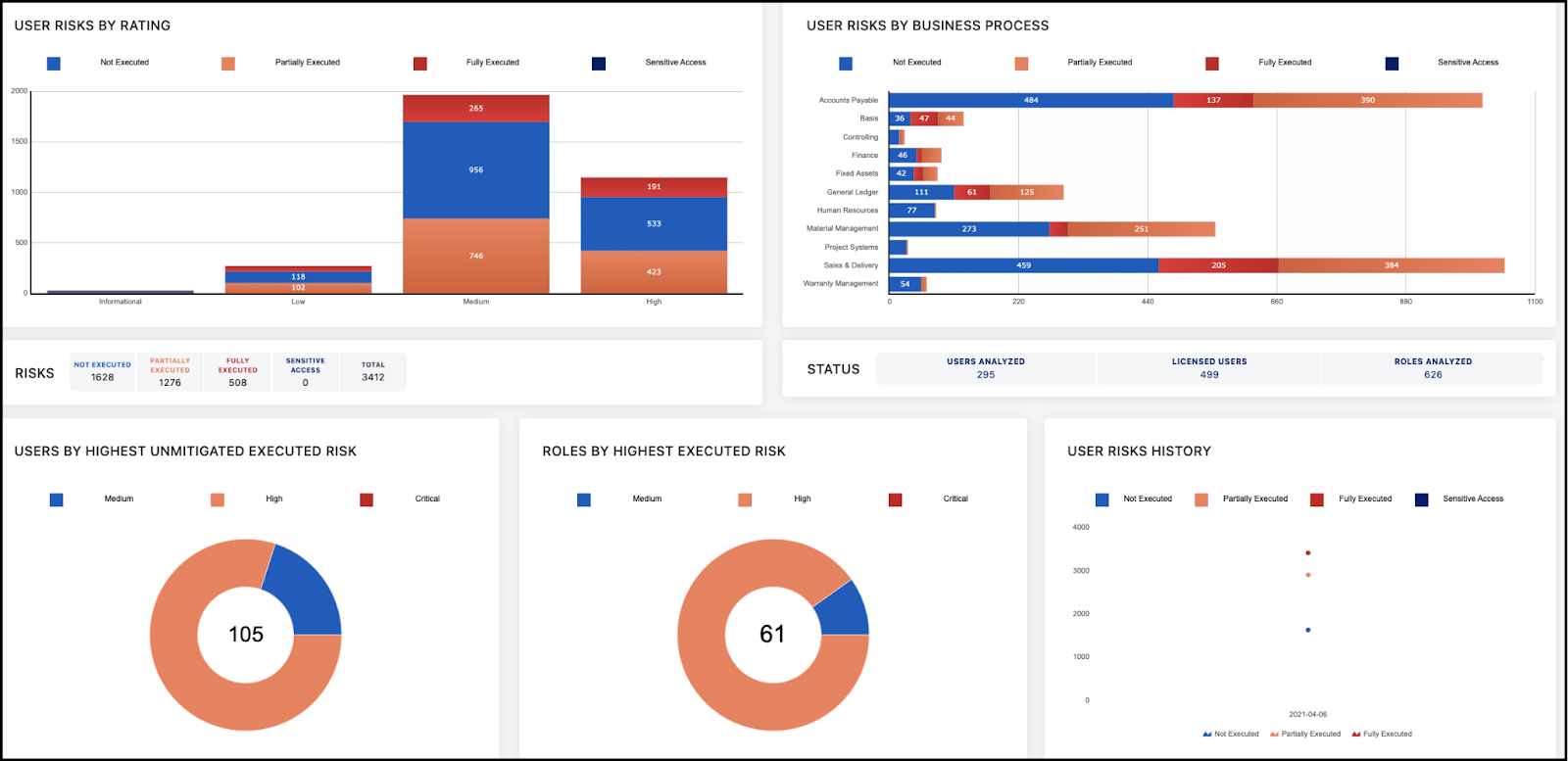
SailPoint provides a robust IAM solution focused on identity governance, compliance, and automating identity lifecycle management for large enterprises.
Key Features
- Identity Governance: Ensures compliance by managing user access and entitlements across applications.
- Automated Access Reviews: Simplifies the process of auditing and verifying user access to systems.
Pros
- Strong governance and compliance features.
- Deep integration capabilities with major enterprise applications.
Cons
- High cost, making it less suitable for smaller businesses.
- Requires specialized expertise to fully utilize its capabilities.
8. Omada Identity
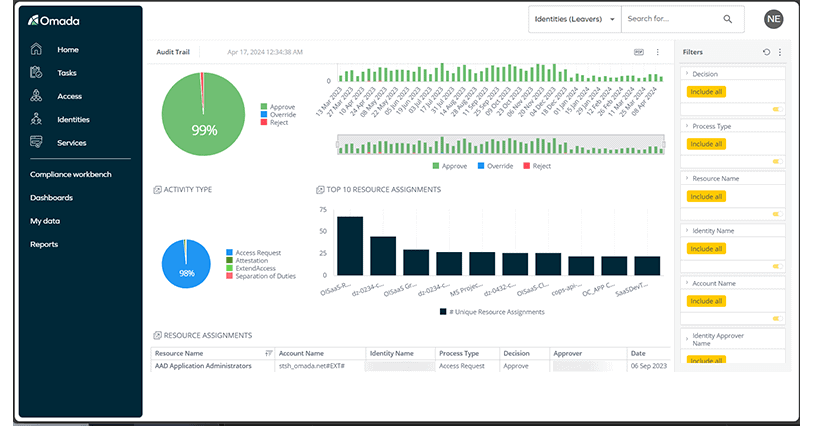
Omada Identity is an IAM solution designed to provide robust identity governance, access management, and compliance controls for enterprises.
Key Features
- Access Management: Provides granular control over user access to applications and systems.
- Identity Governance: Automates compliance tasks, such as access certifications and audits.
Pros
- Highly customizable to suit unique business needs.
- Strong security features with audit logs.
Cons:
- Time-consuming implementation process.
- Requires skilled resources to operate effectively.
9. MiniOrange
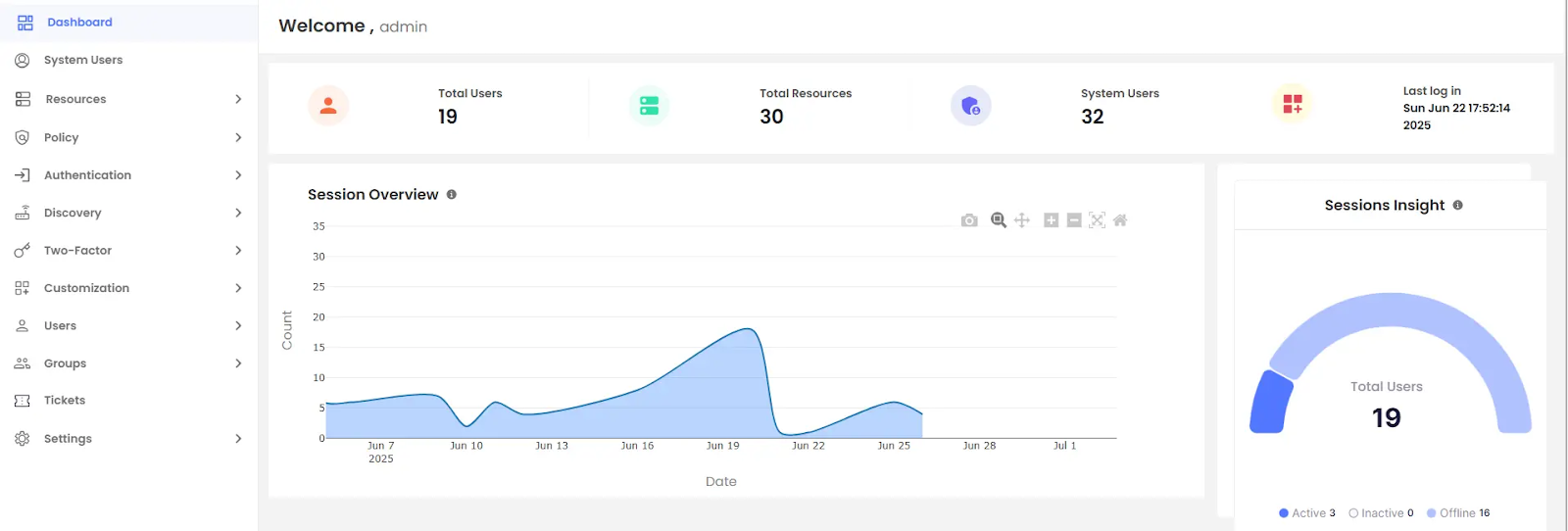
MiniOrange is an affordable IAM solution providing flexible SSO, MFA, and user provisioning capabilities for small to medium-sized businesses.
Key Features
- SSO: Allows users to access multiple applications using a single set of credentials.
- MFA: Enhances login security with multi-factor authentication.
Pros
- Budget-friendly solution for smaller enterprises.
- Easy to configure and deploy.
Cons
- Limited scalability for large enterprises.
- Some integrations require additional setup effort.
10. Keycloak
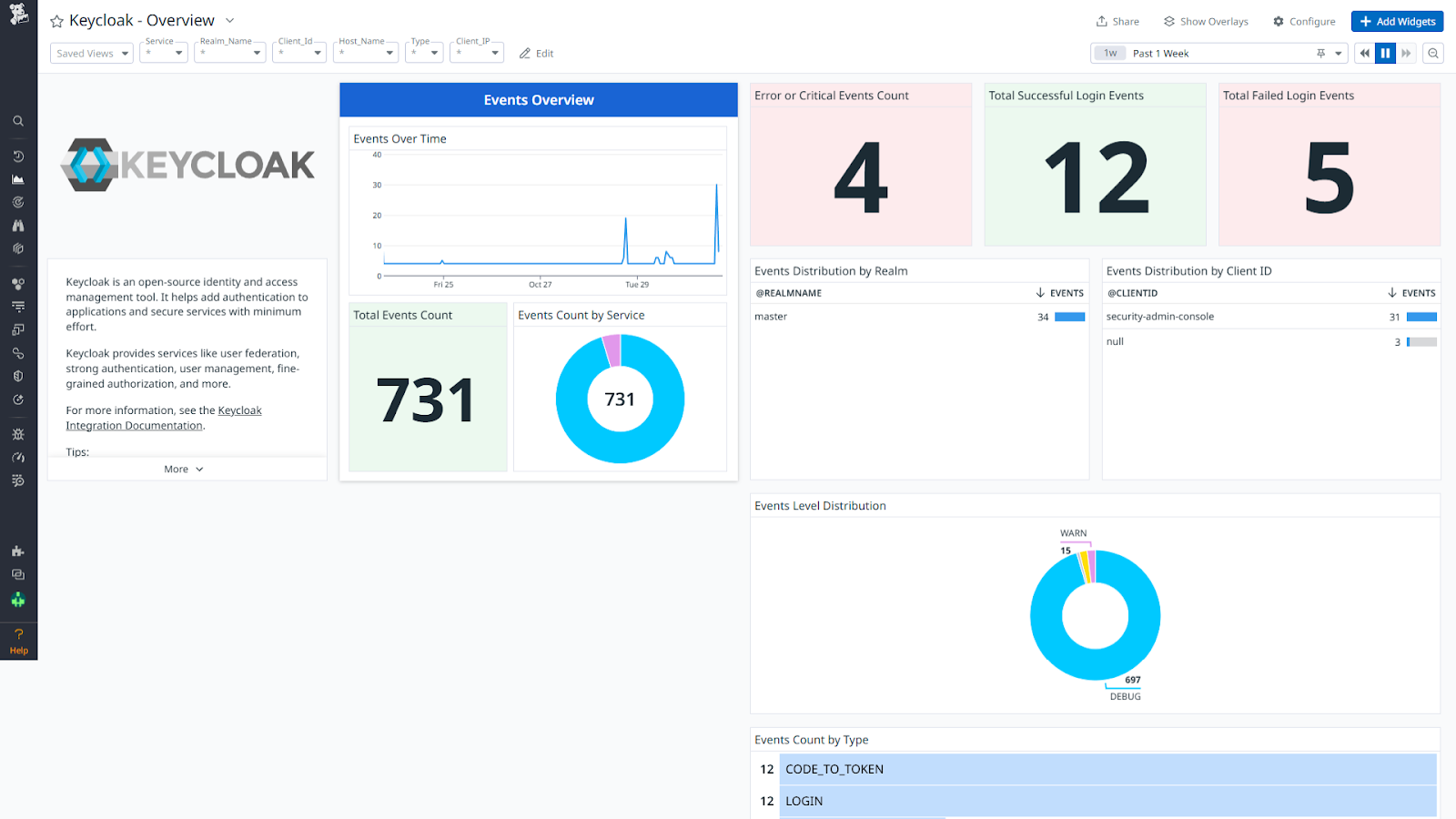
Keycloak is an open-source IAM solution that provides customizable authentication and authorization features, particularly for modern applications.
Key Features
- OpenID Connect and OAuth2 Support: Enables secure authentication and authorization protocols.
- Social Login: Allows users to log in with third-party accounts like Google or Facebook.
Pros
- Free and open-source.
- Highly customizable for developers.
Cons
- Requires technical expertise for setup and maintenance.
- Limited out-of-the-box integrations.
Choosing the Right Identity Management Solution
Choosing the best identity management solution for your enterprise is essential for ensuring security, efficiency, and compliance. Here’s what to consider:
1. Assess Your Needs: Identify whether you need basic authentication or advanced features like SaaS integration, real-time access control, and identity governance. This will help determine if Ping Identity or an alternative is right for your business.
2. Security and Compliance: Check if the solution meets your industry’s compliance standards (e.g., ISO 27001, SOC 2, GDPR, or HIPAA). Ensure the solution offers the security protocols necessary to protect your data and meet regulatory requirements.
3. Scalability: As your organization grows, your IAM needs will change. Choose a solution that can scale with your enterprise, handling more users, devices, and apps efficiently over time.
4. User Experience: Look for a solution that offers a simple and intuitive interface for both admins and end-users. Easy-to-manage dashboards and self-service features will save time and increase productivity.
5. Cost and ROI: Evaluate the overall cost and how quickly the solution will provide a return on investment by reducing administrative work, improving security, and ensuring compliance.
6. Support: Ensure the solution offers strong customer support, including 24/7 assistance and dedicated resources for troubleshooting, implementation, and training.
Check out this insightful episode of CloudEagle.ai’s SaaS Masterminds podcast, where Karl Haviland offers expert perspectives on AI, governance, and how to scale innovation responsibly.
Conclusion
When evaluating Ping Identity alternatives, you must look beyond just pricing and basic features. You should consider factors like security features, scalability, user experience, and long-term ROI to ensure the solution aligns with your enterprise’s unique needs. The best choice will depend on your enterprise’s size, security priorities, and future growth plans.
By carefully weighing the pros and cons of each alternative, you can select the ideal identity management platform that not only strengthens security but also boosts operational efficiency and scales with your business.
If you’re considering a solution like CloudEagle.ai, you’re on the right path to a smarter, more secure identity management system.
Are you ready to elevate your enterprise's identity governance?
Schedule a demo with CloudEagle.ai to see how it can reduce risk, optimize spending, and keep you ahead of emerging cyber threats.
FAQs
1. Who competes with Ping Identity?
Ping Identity faces competition from Okta, Microsoft Azure AD, OneLogin, Duo Security, and ForgeRock, all offering similar identity and access management solutions.
2. Which is better, Okta or Ping?
Okta is easier to use and great for cloud environments, while Ping Identity is better for complex, hybrid setups and large enterprises with advanced security needs.
3. What is the difference between Ping Identity and ForgeRock?
Ping Identity is focused on secure access management with cloud and hybrid solutions. ForgeRock offers stronger consumer identity management and more customization, supporting both on-premise and cloud.
4. What are the MFA options for Ping Identity?
Ping Identity supports SMS OTP, push notifications, biometrics, and email OTP for multi-factor authentication to strengthen security.
5. What is the difference between PingOne and Ping Identity?
PingOne is a simplified, cloud-based solution for smaller businesses, while Ping Identity offers more advanced features for large enterprises and hybrid environments.

%201.svg)








.avif)




.avif)
.avif)




.png)









