HIPAA Compliance Checklist for 2025

A call from your “bank” asking to verify account details may sound harmless, but it could be a trap. This technique, known as vishing (voice phishing), is one of the fastest-growing SaaS security risks targeting individuals and enterprises alike.
According to the FBI’s Internet Crime Report 2023, vishing and related phishing scams led to losses exceeding $2.7 billion. Attackers exploit trust and urgency in phone calls, tricking victims into sharing credentials, financial data, or system access.
In this guide, we’ll break down what vishing is, explore real-world examples, and share practical prevention tips to help both individuals and enterprises stay safe.
TL;DR
- Vishing is voice-based phishing, where attackers use phone calls or voice messages to trick victims into revealing sensitive data.
- Common tactics include impersonation and urgency, such as fake bank alerts, tech support calls, government impersonation, or healthcare scams.
- Attacks exploit human trust and emotion, often bypassing traditional cybersecurity defenses like firewalls or antivirus software.
- Prevention relies on awareness and controls, including security drills, MFA, strict data-sharing policies, and verification protocols.
- CloudEagle.ai helps enterprises reduce vishing risks through automated access control, just-in-time permissions, centralized visibility, and audit-ready compliance tools.
What is Vishing?
Vishing is a social engineering attack where cybercriminals use phone calls or voice messages to trick victims into revealing sensitive information. Unlike other causes of data breaches, which relies on fraudulent emails, vishing leverages the human element of trust in voice communication.
Key characteristics of vishing attacks include:
- Impersonation of trusted entities such as banks, government agencies, or IT departments.
- Urgent requests for action, like verifying account details or resetting passwords immediately.
- Manipulation of emotions, often using fear or authority to pressure victims into compliance.
A common example is a scammer posing as a bank representative claiming suspicious activity on your account. The victim, fearing financial loss, may provide PINs or credentials without verifying the caller’s legitimacy.
Vishing is dangerous because it bypasses many traditional cybersecurity defenses. Firewalls or antivirus software can’t detect a malicious phone call, which makes awareness and vigilance the first line of defense.
How Does Vishing Work?
Vishing works by exploiting trust in voice communication and creating a false sense of urgency. Attackers use convincing scripts and spoofed numbers to appear legitimate. The process typically unfolds in a few key stages:
Target Identification
Attackers may collect information from common causes of data breaches, social media, or public records to personalize the call.
Impersonation of Authority
The scammer poses as a trusted entity, such as a bank officer, IT support, or government representative.
Psychological Manipulation
Victims are pressured with fear (fraud alerts, tax penalties) or incentives (refunds, prize winnings).
Extraction of Sensitive Data
The attacker requests account numbers, passwords, or verification codes under the guise of “helping.”
Exploitation
Once obtained, the information is used for identity theft, fraudulent transactions, or account takeovers.
In 2020, the Twitter Bitcoin Scam exposed how effective vishing can be. Hackers used phone calls to trick Twitter employees into revealing internal credentials.
With this access, they hijacked high-profile accounts (including Barack Obama and Elon Musk) to promote a cryptocurrency scam. The attackers made over $100,000 in Bitcoin within hours.
Common Examples of Vishing Attacks
Vishing attacks don’t follow a single pattern; they adapt depending on the victim and the attacker’s goal. Some scams target individuals for quick financial gain, while others aim at employees inside enterprises to breach sensitive systems.
1. Fake Bank or Credit Card Alerts
Banks often alert customers about suspicious activity via phone calls or messages. Vishing attackers exploit this by pretending to be bank representatives, urging urgent action. Unsuspecting victims may share sensitive account information, believing the call is legitimate.
These calls often leverage fear and urgency, instructing users to “verify” account numbers, authentication methods, or OTPs. Attackers may even spoof official bank numbers to appear authentic.
According to cybersecurity expert Kevin Mitnick,
“Humans are the weakest link in security, and vishing preys on that trust.”
Victims of fake bank alerts can face unauthorized transactions, identity theft, and financial loss. Awareness campaigns, multi-factor authentication, and verifying calls through official channels can help prevent such attacks.
2. Tech Support Scam Calls
Tech support scams have become a significant concern, with attackers impersonating legitimate companies to deceive victims. These scammers often claim that a computer has a virus or other issues and offer to fix them for a fee.
A notable statistic highlights the severity of this issue: In 2024, Forbes revealed that losses attributable to tech support scams amounted to $1.464 billion, marking a $500 million increase from 2023. This alarming rise underscores the growing sophistication and impact of such scams.
To protect oneself, it's crucial to be cautious of unsolicited tech support calls. Always verify the identity of the caller through official channels and avoid granting remote access to your computer unless you're certain of the person's legitimacy.
3. IRS or Government Agency Impersonation
Vishing attacks often exploit fear and urgency by impersonating government agencies, particularly tax authorities. Attackers call individuals claiming unpaid taxes or legal action, pressuring them to act immediately. Common tactics used by scammers include:
- Threatening legal consequences: Claiming lawsuits, arrest warrants, or heavy fines for non-compliance.
- Requesting immediate payment: Asking for payment via gift cards, wire transfers, or prepaid debit cards.
- Requesting sensitive personal data: Asking for Social Security numbers, bank details, or login credentials.
These calls are highly manipulative and can create panic, causing victims to act without verification. Always confirm through official government channels and never share personal information over unsolicited calls.
4. Healthcare and Insurance Scams
Vishing attackers often target individuals by impersonating healthcare providers, insurance companies, or Medicare representatives. They exploit the urgency of medical needs or insurance claims to trick victims into revealing sensitive information.
According to Brian Krebs, cybersecurity journalist,
“Healthcare data is gold to attackers because it’s permanent and uniquely identifies individuals.”
Attackers can sell this information on the dark web or use it for identity theft and fraudulent claims. This makes healthcare vishing one of the most damaging social engineering schemes.
Why is Vishing a Growing Threat?
Vishing attacks are on the rise as cybercriminals exploit the human element of security. Vishing targets users through voice calls, creating a sense of urgency and trust that emails often fail to replicate. The sophistication of these attacks makes even cautious employees vulnerable.
1. Increasing Sophistication of Scammers
Vishing attackers are becoming more advanced, using technology and psychological tricks to deceive victims. They often research targets to make their calls more convincing and tailored.
- Caller ID spoofing: Scammers manipulate phone numbers to appear as legitimate institutions.
- Social engineering scripts: Well-crafted scripts mimic authentic communication patterns.
- Automated calling systems: Bots increase call volume while maintaining personalized touches.
As these tactics evolve, enterprises and individuals must stay vigilant and implement strong verification practices.
2. Vulnerability of Remote and Hybrid Workers
Remote and hybrid work environments have expanded the attack surface for cybercriminals, making employees more susceptible to vishing attacks. Unlike traditional office settings, remote workers often use personal devices and unsecured networks, which can be easily exploited by attackers.
A significant concern is the increased reliance on voice communication for authentication and support. Attackers can impersonate IT support or HR departments, leading to unauthorized access to sensitive information.
For instance, in 2024, Cisco was a victim of a Vishing attack. The attacker convinced the employee to grant remote access, compromising the company's network,
3. Exploiting Human Fear and Urgency
Vishers often manipulate emotions like fear, anxiety, or urgency to trick victims into divulging sensitive information. They create a sense of immediate threat, making rational decision-making difficult.
Impersonating Authorities
Attackers may pose as IRS agents, bank officials, or law enforcement, pressuring targets to act quickly without verification.
Urgent Security Alerts
Fake warnings about account breaches or overdue payments prompt hasty responses, increasing the success rate of attacks.
Time-Sensitive Consequences
Vishing scripts often threaten severe consequences, like account suspension or legal action, exploiting natural human reactions to urgency.
Vishing Prevention Best Practices for Enterprises
Enterprises face rising risks from vishing attacks targeting employees, customers, and partners. Implementing structured prevention measures can reduce exposure, strengthen security awareness, and protect sensitive data from social engineering exploits.
1. Regular Security Drills and Awareness Campaigns
Regular security drills and awareness campaigns are essential in preparing employees to recognize and respond effectively to vishing attacks. These initiatives help cultivate a security-conscious culture within the organization.
According to a 2025 report by KnowBe4, organizations that conducted regular simulated phishing exercises saw a significant reduction in phishing susceptibility. The report revealed that the global Phish-prone Percentage (PPP) decreased by 86% over 12 months of security training.
This statistic underscores the effectiveness of continuous training and simulation in enhancing employee awareness and reducing the risk of successful vishing attacks.
2. Implementing Multi-Factor Authentication (MFA)
Multi-Factor Authentication (MFA) adds an extra layer of security, ensuring that even if attackers gain credentials, unauthorized access is prevented. By combining something users know (password), something they have (security token), or something they are (biometric), enterprises drastically reduce the risk of vishing-related breaches.
Layered Protection
MFA requires multiple verification steps, making it harder for attackers to compromise accounts. This protects sensitive systems from unauthorized access.
Adaptive Authentication
Organizations can apply MFA selectively for high-risk actions or users, improving usability without sacrificing security.
Integration With Existing Systems
MFA can be integrated with enterprise applications, VPNs, and cloud platforms to create consistent security coverage.
User Education
Employees should understand how MFA works and why it’s critical, reducing resistance and encouraging proper usage.
Implementing MFA is especially effective against vishing because attackers often rely on stolen credentials. MFA ensures that a password alone is insufficient, significantly lowering the success rate of such attacks.
3. Limiting Sensitive Data Sharing Over Calls
Enterprises must establish strict policies to prevent employees from sharing sensitive information over phone calls. Attackers often impersonate trusted entities, and restricting what can be disclosed reduces the risk of successful vishing attempts. Here are some best practices:
- Verification Protocols: Always verify the caller’s identity using official channels before sharing any confidential data.
- Role-Based Restrictions: Only employees with specific roles should have access to sensitive information, limiting exposure.
- Predefined Scripts: Use approved scripts for phone interactions to avoid accidental disclosure of critical information.
- Employee Training: Regularly train staff on recognizing social engineering tactics and understanding what information is off-limits.
Limiting sensitive data sharing over calls strengthens an enterprise’s overall security posture. When combined with other preventive measures like MFA, the likelihood of vishing success is significantly reduced.
How CloudEagle.ai Can Help Secure Enterprise Access
CloudEagle.ai empowers IT, procurement, and security teams to gain complete control over their SaaS ecosystem. With over 500 integrations spanning finance, SSO, and HRIS, the platform delivers full visibility into applications, licenses, vendors, and spending.
It also streamlines identity and access management. Through a unified dashboard and Slack-enabled workflows, IT teams can automate onboarding, offboarding, access reviews, and license assignments, saving time and reducing security risks.
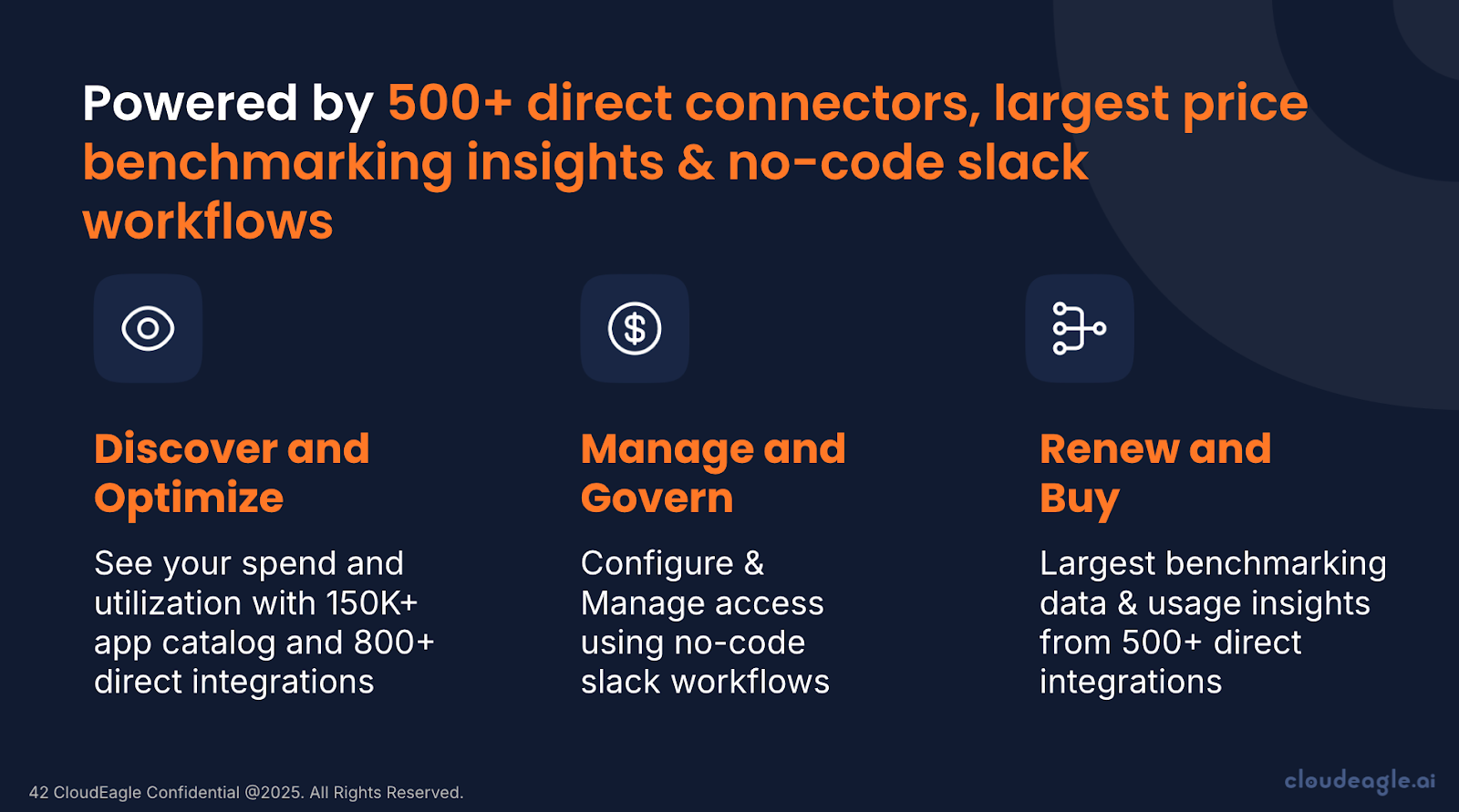
Enterprises like RingCentral, Shiji, and Rec Room rely on CloudEagle.ai to cut SaaS costs by 10–30%. With $3.5B in processed spend and over $250M in customer savings, the platform demonstrates measurable impact. Rapid 30-minute onboarding ensures immediate governance improvements and cost savings.
Just-in-Time Access
Temporary licenses often remain after tasks are completed, creating security risks and unnecessary costs. CloudEagle.ai addresses this by granting just-in-time access only for the required duration and automatically revoking it afterward.
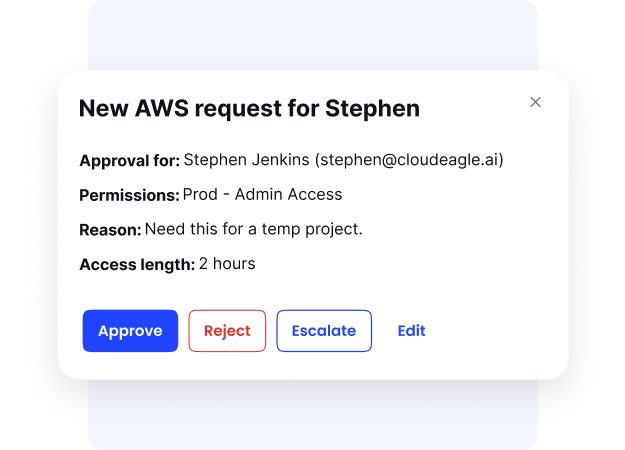
This reduces unauthorized access, cuts license waste, and simplifies governance through automated controls.
Employee App Access Catalog
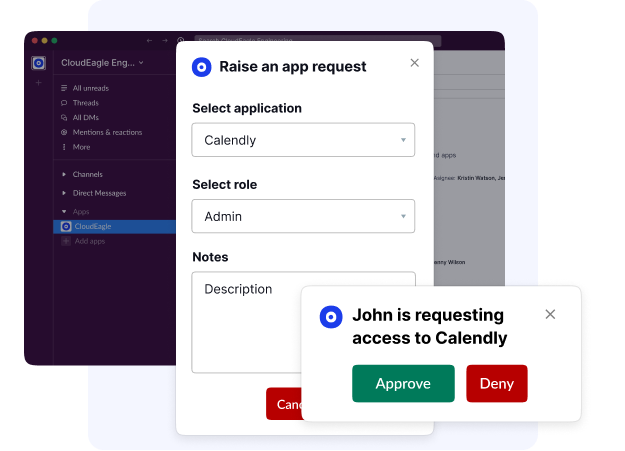
Many employees don’t know which tools they can request, while IT spends hours handling approvals via emails, Slack, or tickets. Even with JIRA or ServiceNow, maintaining accurate app lists is manual, incomplete, and can lead to shadow IT, redundant purchases, and security gaps.
CloudEagle.ai centralizes app access in a dynamic self-service catalog, automatically updated through 500+ integrations. Employees see only relevant tools, Sales accesses Salesforce, Engineering accesses AWS, and requests flow through automated approvals with full audit trails.

The result: IT resolves requests up to 80% faster, onboarding happens in minutes, shadow IT shrinks, compliance reporting is effortless, security improves, and SaaS waste decreases.
Automated App Access Reviews
Traditional access reviews are slow, error-prone, and often infrequent, leaving former employees or risky users with prolonged access.
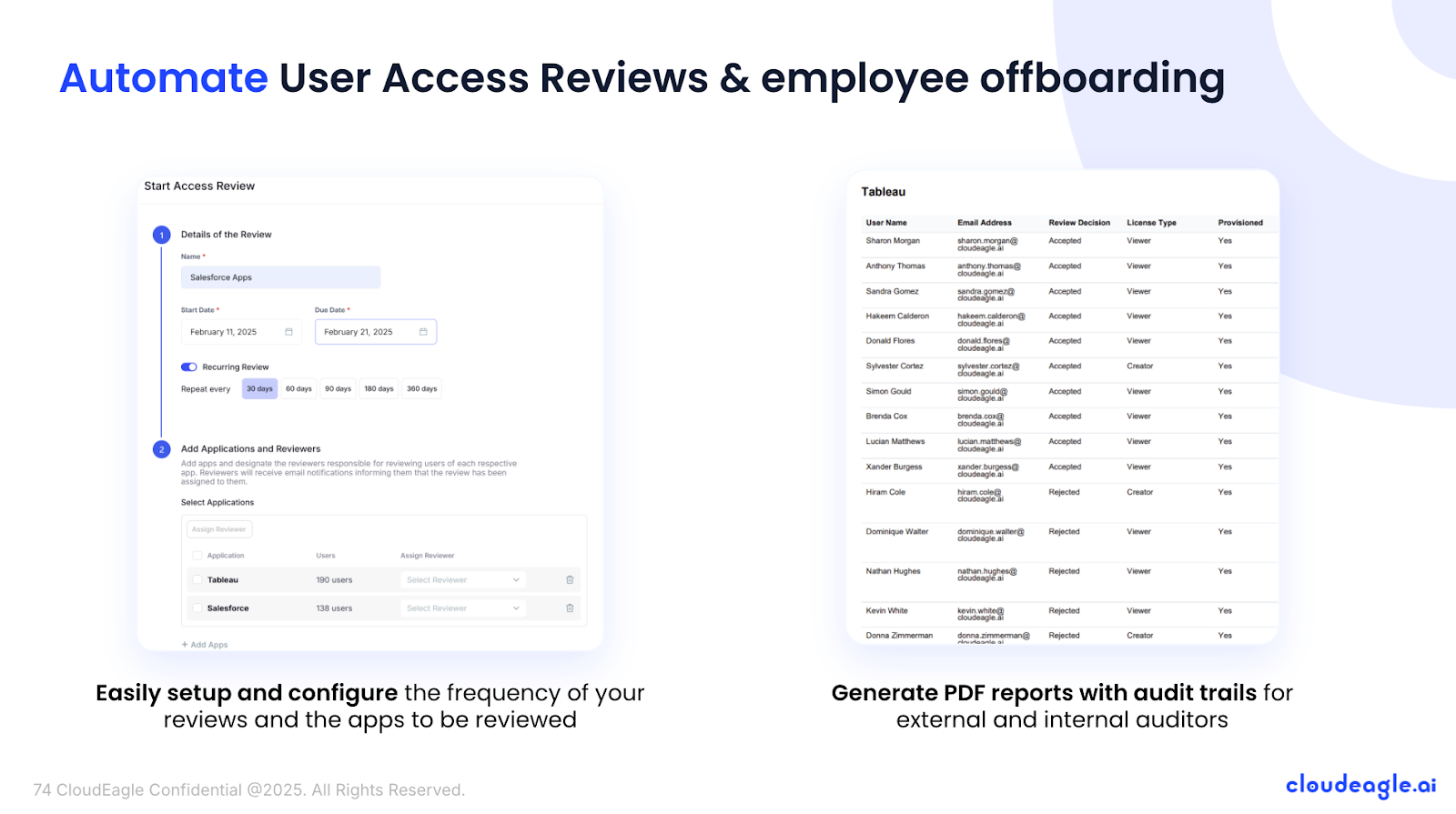
CloudEagle.ai automates these reviews, providing a centralized dashboard for IT and app owners to track roles, schedule reviews, and stay SOC 2 compliant.
High-risk users are flagged, and deprovisioning takes just a few clicks. Access reviews become faster, security more proactive, and compliance always audit-ready.
Access Control
CloudEagle.ai provides full transparency into application access control, including who has access, the reasons behind it, and how they utilize it. With centralized access control, it oversees the entire access lifecycle, from request to provisioning and deprovisioning, all within a single platform.
Additionally, the platform simplifies compliance and security audits by offering instant access to application logs. Detailed access records can be exported directly, making audit preparation seamless and hassle-free.
Privileged Access Management
CloudEagle.ai streamlines privileged access management by automating the assignment of elevated access, ensuring that only authorized users can access critical systems like AWS and NetSuite, thereby reducing the risk of unauthorized activity.
With continuous monitoring and automated controls, the platform strengthens security and compliance while easing administrative workloads and minimizing human error.
Employee Onboarding and Offboarding
Manual onboarding and offboarding are slow and error-prone, leaving lingering access and wasting licenses. CloudEagle.ai automates the process with zero-touch workflows, using role-based rules to provision or revoke access instantly across all applications.

Freed licenses automatically return to the pool, maximizing resource efficiency. Companies like Health Ceramics have significantly improved operational efficiency using CloudEagle.ai for deprovisioning.
For instance, Health Ceramics leveraged CloudEagle.ai to automate deprovisioning, significantly boosting operational efficiency.
Compliance Management
CloudEagle.ai centralizes SaaS compliance oversight, continuously scanning for vulnerabilities, managing certifications, facilitating audits, and monitoring account activity for full visibility.
With CloudEagle.ai, enterprises can protect sensitive data, streamline access management, and maintain compliance across all SaaS applications.
Conclusion
Vishing remains one of the most effective social engineering attacks, exploiting human trust and urgency. Enterprises that fail to train employees, enforce verification protocols, and limit sensitive data sharing face substantial financial and reputational risks.
Platforms like CloudEagle.ai help enterprises gain centralized visibility into access controls and security protocols, making it easier to safeguard sensitive data across systems. Book a demo today to see how CloudEagle.ai can strengthen your organization’s defenses against vishing and other social engineering threats.
FAQs
1. Why is it called vishing?
Vishing is short for “voice phishing.” It involves scammers using phone calls to steal sensitive personal or financial information.
2. When did vishing start?
Vishing emerged in the early 2000s, evolving from traditional phishing scams. It exploits voice communication to trick victims.
3. Who is often targeted by vishing calls?
Individuals with access to sensitive financial accounts or corporate systems are common targets. Scammers also focus on older adults.
4. What are the four P's of vishing?
The four P’s are Preparation, Persuasion, Pressure, and Personalization. Scammers plan carefully and pressure victims to disclose information.
5. What is the main objective of a vishing scammer?
The main goal is to obtain personal, financial, or account credentials. Scammers then commit fraud or identity theft.

%201.svg)









.avif)




.avif)
.avif)




.png)









