HIPAA Compliance Checklist for 2025

What if the people who left your company months ago still had access to critical apps today? That’s not just a fear; it’s reality. According to a Wall Street Journal cybersecurity report, 82% of data breaches in 2023 involved data stored in the cloud.
The problem isn’t the cloud itself, but the lack of visibility and control over who can access what.
This guide will walk you through what cloud access governance is, its core disciplines, benefits, challenges, and best practices, plus how modern solutions simplify app access management, so you can secure SaaS access without slowing down your business.
TL;DR
- Cloud Access Governance (CAG) defines and enforces who has access to SaaS apps and cloud resources, ensuring security, compliance, and efficient use of licenses.
- The five key disciplines include cost management, security baselines, identity baseline, resource consistency, and deployment acceleration, create a strong governance framework.
- Core components like centralized visibility, policy enforcement, access reviews, role mapping, and audit trails help organizations reduce risks and maintain control.
- CAG delivers benefits such as stronger security, faster compliance, reduced SaaS waste, and greater accountability, though challenges like shadow IT, misconfigurations, and stale accounts remain.
- Best practices include clear access policies, regular audits, real-time monitoring, automation, and Just-In-Time access. Solutions like CloudEagle.ai streamline provisioning, deprovisioning, reviews, and compliance with automation and centralized visibility.
What is meant by Cloud Access Governance?
Cloud Access Governance is the backbone of securing modern SaaS and cloud environments. At its core, it’s about defining and enforcing who has access to what within your cloud ecosystem, from applications and databases to sensitive customer or financial data.
Without it, unauthorized accounts, orphaned access, and unmanaged superusers can quietly expose your business to risk.
Think of it as a cloud computing governance framework designed to balance productivity with security. Through policies, procedures, and technologies, organizations can control access rights, monitor usage, and ensure compliance with both internal policies and external regulations.
In short, cloud access governance ensures that the right people have the right level of access - no more, no less.
What are the Five Disciplines of Cloud Access Governance?
The five disciplines of Cloud Access Governance are Cost Management, Security Baselines, Identity Baseline, Resource Consistency, and Deployment Acceleration. Together, they create a structured cloud computing governance framework that balances security, efficiency, and scalability.
1. Security Baselines
Security baselines establish standardized controls and configurations across cloud resources. They ensure data protection, compliance with regulations, and a consistent defense against vulnerabilities.
2. Identity Baseline
An identity baseline defines who has access to what within the cloud. It strengthens cloud identity governance by enforcing least-privilege access, managing permissions, and reducing the risk of unauthorized entry.
3. Resource Consistency
This ensures cloud resources are deployed and configured according to predefined standards. It reduces errors, prevents shadow IT, and maintains operational consistency across the environment.
4. Deployment Acceleration
Deployment acceleration streamlines provisioning through automation. It enables teams to move quickly without compromising governance, ensuring agility while keeping access and security under control.
5. Cost Management
This discipline focuses on controlling and optimizing cloud spend. By tracking resource usage and eliminating unnecessary costs, organizations can align budgets with actual business needs and reduce SaaS waste.
What are the Benefits of Cloud Access Governance?
Cloud Access Governance matters in SaaS environments because it protects sensitive data, ensures compliance, and keeps SaaS costs under control. Without it, organizations risk breaches, overspending, and operational inefficiencies.
Here’s why it’s essential:
Enhanced Security
- Prevents Data Breaches: Strict access controls minimize unauthorized entry into critical apps and databases.
- Mitigates Insider Threats: Monitoring access patterns helps detect negligent or malicious insider activity.
- Reduces Attack Surface: Limiting permissions to what’s necessary makes it harder for attackers to exploit accounts.
Improved Compliance
- Meets Regulatory Requirements: Meeting industry requirements like GDPR, HIPAA, or SOC 2 is one of the biggest reasons organizations adopt cloud identity governance. Automating access reviews and enforcing role-based policies not only simplifies audits but also lowers compliance risk. According to CloudEagle’s IGA Report, organizations that adopt strong identity governance frameworks reduce access-related compliance violations by up to 35%.
- Reduces Compliance Costs: Automating access reviews and certifications streamlines audits and reduces manual workloads.
Cost Optimization
- Eliminates Over-Provisioning: Identifies unused licenses or redundant applications to cut SaaS waste.
- Optimizes SaaS Spend: Provides visibility into app usage, so leaders can decide which apps to scale, consolidate, or retire.
Increased Efficiency
- Streamlines Access Management: Automates onboarding, offboarding, and access approvals.
- Improves Productivity: Ensures users always have timely access to the right tools, reducing delays.
Enhanced Visibility and Control
- Centralized Monitoring: Offers a single view of all SaaS apps and user access rights.
- Data-Driven Decisions: Provides usage insights that guide smarter SaaS investments and governance policies.
In short, cloud access governance brings together security, compliance, cost control, and productivity into one unified strategy for managing SaaS.
Key Components of Cloud Access Governance
The key components of cloud access governance create a structured way to manage SaaS access, strengthen compliance, and reduce risk.
Here are the essentials every organization needs in place:
Centralized Visibility
Centralized visibility provides a single source of truth across all cloud applications. It helps you see who has access to which tools, track entitlements, and uncover shadow IT, making access risks easier to spot and control.
Access Reviews & Certifications
Regular access reviews and certifications validate whether users’ permissions are still appropriate. This practice ensures that outdated or unnecessary access is revoked, closing compliance gaps and reducing the chance of insider threats.
Policy Enforcement
Policy enforcement turns governance into action. From enforcing least-privilege access to requiring MFA for sensitive apps, policies ensure that security standards are consistently applied across the SaaS stack, regardless of scale.
Role Mapping
Role mapping aligns user access with job functions. By defining clear roles and mapping permissions accordingly, organizations prevent over-provisioning, simplify onboarding, and maintain control without slowing down productivity.
Audit Trails
Audit trails provide documented proof of every access decision, request, and approval. This transparency is vital for passing audits, meeting regulatory requirements, and demonstrating strong governance to stakeholders.
Together, these components form the backbone of an effective cloud identity governance strategy - one that balances security, compliance, and efficiency in SaaS-first environments.
Challenges in Governing Cloud and SaaS Access
Governing cloud and SaaS access is complex because environments are dynamic, decentralized, and constantly evolving. Without the right cloud governance solutions, organizations face visibility gaps, compliance risks, and mounting security threats. Here are the biggest hurdles:
Visibility and Control
Cloud adoption often fragments oversight.
- Limited Infrastructure Visibility: Multi-tenant and hybrid environments make it difficult to see who has access to what.
- Data Silos: Information scattered across apps creates blind spots that weaken cloud data access governance.
- Lack of Centralized Management: Monitoring multiple SaaS platforms without unified controls leads to inconsistent access decisions.
Identity and Access Management
Managing user lifecycles in SaaS is an ongoing struggle.
- Orphan or Stale Accounts: Old accounts remain active, exposing organizations to security risks.
- Excessive Privileges: Users often retain entitlements beyond their role, increasing exposure.
- Lack of Reviews: Access certifications are skipped or delayed, breaking compliance.
- Integration Challenges: Aligning SaaS apps with SSO, federation, or MFA is difficult at scale.
Security Risks
Cloud access errors frequently translate into breaches.
- Cloud Misconfigurations: Small setup mistakes can leave data exposed.
- Unauthorized Access: Public-facing SaaS apps are vulnerable to account takeovers.
- Insider Threats: Employees or contractors may misuse legitimate access.
- Data Breaches: Sensitive SaaS data is a prime target for attackers.
Compliance and Governance
Regulatory and operational demands add pressure.
- Meeting Requirements: Regulations like GDPR, HIPAA, and PCI DSS require strict cloud identity governance.
- Shadow IT: Unauthorized SaaS apps bypass governance controls.
- Cloud Complexity: Diverse services require consistent, enforceable policies.
Other Challenges
- Vendor Lock-In: Over-reliance on one provider reduces flexibility.
- Cost Management: SaaS costs rise quickly without oversight.
- Lack of Expertise: Skilled governance professionals are in short supply.
- Rapid Change: Constant SaaS updates make policies hard to keep current.
In short, effective cloud identity access governance requires balancing agility with control, solving these challenges before they spiral into risks that threaten both compliance and financial health.
Cloud Access Governance Best Practices
Strong Cloud Access Governance relies on consistent policies, real-time monitoring, and automation to balance security with productivity.
The following best practices help organizations build a resilient cloud governance solution that safeguards SaaS environments while ensuring compliance.
1. Define Clear Access Policies and Procedures
Establish well-documented policies that specify who can access which systems, apps, and data. Align them with both business objectives and compliance requirements, and make them easily accessible to stakeholders.
2. Implement Robust Identity and Access Management (IAM)
Adopt cloud identity governance tools with multi-factor authentication (MFA) and role-based access control (RBAC). Enforce least-privilege principles to ensure users only get the permissions necessary for their role.
3. Conduct Regular Access Audits and Reviews
Schedule frequent access reviews and certifications to identify stale or excessive permissions. Automating these reviews strengthens compliance while reducing manual overhead.
4. Monitor Access Events in Real-Time
Use SIEM tools or behavior analytics to monitor user activity continuously. Real-time alerts allow faster detection of unauthorized access attempts and potential insider threats.
5. Mitigate Security and Compliance Gaps
Continuously scan for misconfigurations or outdated policies that weaken cloud data access governance. Automated compliance checks and remediation workflows help maintain alignment with regulations like GDPR or HIPAA.
6. Implement Just-In-Time (JIT) Access
Provide temporary, task-specific access instead of standing privileges. Automating JIT provisioning with PAM solutions reduces the attack surface and limits exposure from privileged accounts.
7. Automate Policy Enforcement
Leverage automation and Infrastructure as Code (IaC) to consistently apply governance controls. Automated workflows ensure policies are enforced across all SaaS applications without manual intervention.
8. Foster a Culture of Cloud Accountability
Assign clear governance responsibilities across teams, provide training, and reinforce a culture where access governance is seen as part of productivity, not just a compliance checkbox.
9. Regularly Review and Update Governance Policies
Cloud environments evolve quickly, as do compliance standards. Regularly revisit governance frameworks to stay current with new threats, tools, and industry regulations.
By following these best practices, organizations create a cloud computing governance framework that enhances security, keeps SaaS costs in check, and ensures compliance without slowing down operations.
Using CloudEagle.ai for Superior Access Governance
Managing SaaS access manually often creates delays, errors, and compliance gaps.
CloudEagle.ai streamlines this entire lifecycle with automation, visibility, and policy-driven controls, making governance seamless instead of stressful.
Automated Provisioning and Deprovisioning
Onboarding new employees or revoking access for those who leave can be time-consuming, and missed deprovisioning leaves accounts vulnerable.
CloudEagle.ai connects directly with HR systems and identity providers to automate access updates as roles change, ensuring no account is left unmanaged.

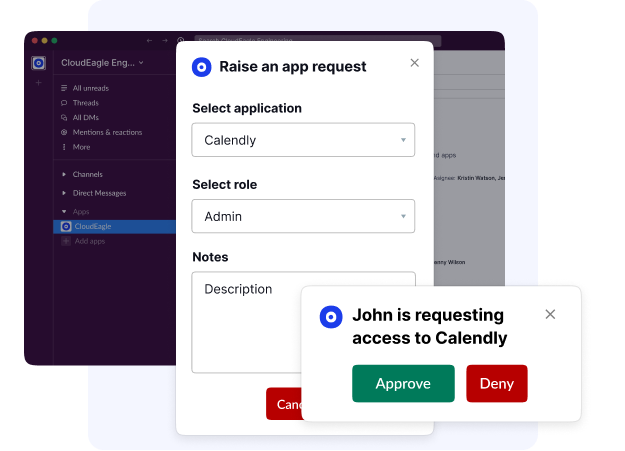
Self-Service App Catalog
Waiting on IT for every access request slows down productivity and overloads IT teams with repetitive tickets.
With CloudEagle.ai’s self-service app catalog, employees can request the apps they need while managers approve access through automated workflows, giving users speed without sacrificing governance.
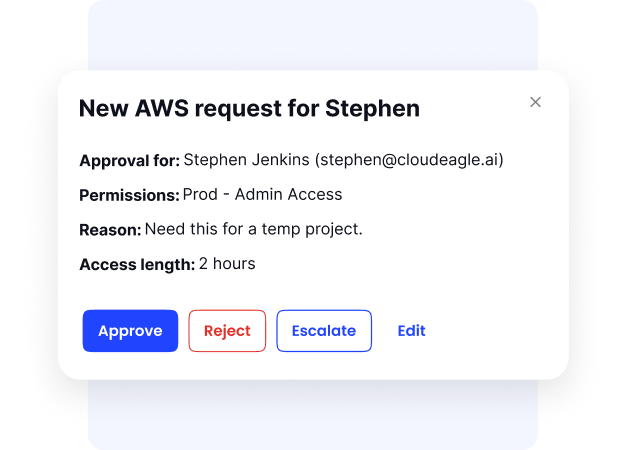
Time-Based Access Management
Temporary projects or contractors often end up with permanent entitlements they no longer need.
CloudEagle.ai solves this by offering time-bound access that automatically expires, reducing unnecessary exposure while supporting short-term work.
Automated Access Reviews
Access reviews are critical for compliance, but are often skipped because of how tedious they are.
CloudEagle.ai automates these reviews, sending periodic reminders to managers and generating audit-ready reports that make certifications effortless.

Centralized Control and Visibility
With SaaS spread across dozens of applications, most organizations lack a single view of who has access to what.
CloudEagle.ai consolidates all access into one dashboard, providing real-time insights, detailed activity logs, and full visibility across the SaaS stack.

RBAC and ABAC Support
Manually assigning permissions can result in excessive or inconsistent entitlements.
CloudEagle.ai enforces Role-Based and Attribute-Based Access Controls, ensuring users get the right access based on their role or attributes - nothing more, nothing less.

Compliance Management
Preparing for audits is one of the biggest drains on IT teams.
CloudEagle.ai automates compliance tracking, captures certifications, and generates ready-to-submit reports, making it easier to stay ahead of regulations like ISO 27001, SOC 2, and GDPR.
By addressing the everyday struggles of access governance, delayed provisioning, unmanaged accounts, shadow IT, and compliance stress, CloudEagle.ai empowers organizations to secure SaaS access without slowing down their business.
What is the Difference Between Identity Governance and IAM?
Identity Governance and Identity and Access Management (IAM) are closely related, but they serve different purposes in managing cloud access. IAM handles the mechanics of granting access, while identity governance cloud frameworks focus on whether that access is appropriate, compliant, and aligned with business goals.
Identity and Access Management (IAM)
IAM provides the technical foundation for managing digital identities.
- Focus: Authentication (verifying who a user is) and authorization (deciding what they can access).
- Key Functions: Single Sign-On (SSO), Multi-Factor Authentication (MFA), and account provisioning or deprovisioning.
- Scope: Deals with the “who” and “how” of access, ensuring users can log in and perform approved actions.
Identity Governance (IGA)
Identity governance builds oversight and compliance on top of IAM.
- Focus: Ensuring access rights follow policies, regulations, and risk controls.
- Key Functions: Access certifications, periodic reviews, role-based access control (RBAC), segregation of duties (SoD), and audit reporting.
- Scope: Deals with the “why” and “what” of access, making sure permissions are justified, compliant, and not excessive.
How They Work Together
Think of IAM as the engine that controls user access, and cloud identity access governance (IGA) as the guardrails ensuring the engine runs safely and within policy.
IAM answers “Who gets access?”, while IGA ensures “Should they have it in the first place?”
Together, they create a complete framework for secure, compliant cloud access management.
Ready to Simplify SaaS Access?
Cloud Access Governance gives you the visibility, control, and compliance needed to keep SaaS environments secure and efficient.
By now, you know the disciplines, challenges, and best practices that make it work.
If managing access still feels complex, CloudEagle.ai helps cut through the noise. With automated provisioning, reviews, and centralized visibility, it’s built to solve the exact challenges you’re facing today.
FAQs
1. What is cloud identity management?
Cloud identity management is the process of controlling user identities in the cloud. It authenticates users, manages credentials, and ensures secure access to SaaS apps, data, and resources through policies and automation.
2. Which is an example of cloud access?
A common example of cloud access is logging into Google Workspace or Microsoft 365 with a single set of credentials. Through IAM or SSO, users securely access apps and data without separate logins.
3. What are the four pillars of data governance?
The four pillars of data governance are accountability, integrity, protection, and compliance. Together, they ensure data is reliable, secure, and used in line with business policies and regulations.
4. What is the data access governance model?
The data access governance model defines who can access, use, and share data. It involves classifying sensitive information, setting roles and policies, and enforcing least-privilege access to reduce risk and ensure compliance.
5. What is identity governance used for?
Identity governance is used to ensure access rights are appropriate, compliant, and secure. It manages access reviews, enforces role-based controls, and prevents excessive permissions that could create risks or compliance violations.
👉 Want to see how this works in practice? Book a free demo with CloudEagle.ai and explore automated identity governance in action.
.avif)
%201.svg)







.avif)




.avif)
.avif)




.png)









