HIPAA Compliance Checklist for 2025

Imagine walking into a massive corporate building with hundreds of doors. Some doors lead to sensitive financial records, some to customer data, and others to everyday tools employees use. Now imagine there are no clear rules about who can open which door. Chaos, right?
This is exactly what happens in the digital world when businesses don’t have a proper identity and access management framework. Without structure, users end up with unnecessary access, old accounts remain active, and sensitive information becomes vulnerable.
A framework brings order to this chaos. It acts as the blueprint that defines who gets access, when they get it, and how it’s monitored. Whether you’re a growing startup or a global enterprise, understanding IAM frameworks is essential to protecting data, ensuring compliance, and creating a seamless user experience.
In this guide, you’ll learn what identity and access management is, how frameworks work, why enterprises need them, their core components, challenges, and how CloudEagle.ai helps strengthen your strategy.
TL;DR
- Identity and Access Management (IAM) ensures the right users have the right access to systems, applications, and data.
- An identity and access management framework provides structure, policies, and processes to enforce secure and compliant access.
- Core components of IAM frameworks include identity lifecycle management, access controls, authentication, RBAC/ABAC, SSO/MFA, PAM, and audit trails.
- Common challenges include managing access across SaaS, balancing security with convenience, preventing privilege creep, and staying compliant in dynamic environments.
- CloudEagle.ai enhances IAM frameworks with AI-powered automation, dynamic role management, time-based access, PoLP enforcement, and a self-service app catalog to strengthen security and governance.
What is Identity and Access Management?
Identity and Access Management (IAM) is a security framework designed to manage digital identities and regulate user access to resources. It ensures the right individuals have appropriate access at the right time while preventing unauthorized entry.
IAM covers authentication (verifying identity), authorization (defining permissions), and access control (managing resource access).
Identity and access management (IAM) is the discipline of making sure the right users have the right level of access to the right resources. It ensures that employees, contractors, partners, and even non-human accounts can safely interact with applications and data.
IAM is built on three main principles:
- Identification – Defining who the user or system is.
- Authentication – Verifying the identity through credentials like passwords, tokens, or biometrics.
- Authorization – Determining what the user is allowed to access.
For organizations running multiple SaaS applications, IAM is a lifeline. It prevents security risks like orphaned accounts or excessive permissions while simplifying the user experience with tools like single sign-on (SSO). Without it, companies face unmanaged identities and security blind spots.
What is Identity and Access Management Framework?
An Identity and Access Management (IAM) Framework is a structured system of policies, processes, and technologies designed to manage digital identities and regulate user access within an organization. It ensures the right individuals have proper access at the right time while reducing security risks.
While IAM is the broader concept, the identity and access management framework is the structured model you follow to implement it consistently. Think of it as a set of rules, technologies, and governance policies that make IAM scalable and enforceable.
An effective framework brings together:
- Policies – Who gets access, under what conditions, and how it’s reviewed.
- Technologies – SSO, MFA, and privileged access management (PAM).
- Governance workflows – Access reviews, audits, and compliance checks.
- Lifecycle processes – Onboarding, role transitions, and offboarding.
The framework ensures that every identity, human or machine, is managed properly. When someone joins the company, their access is provisioned based on role. When they leave, access is automatically revoked. This eliminates risks of leftover accounts or privilege creep.
Beyond provisioning, the IAM governance framework also ensures accountability by requiring audits, generating logs, and proving compliance with regulations like GDPR or HIPAA.
What is the Working Mechanism of IAM Frameworks?
The working mechanism of an IAM framework defines how digital identities are created, managed, and monitored. It involves authenticating users, authorizing access, and enforcing policies across systems. This ensures secure, efficient, and compliant access to resources.
IAM frameworks don’t just sit on paper; they operate through a cycle of processes that govern every user identity. Here’s how the mechanism works:
- Identity Creation – User profiles are created from HR or directory systems.
- Authentication – Credentials or MFA verify the identity during login.
- Authorization – Role-based or attribute-based policies determine access.
- Access Enforcement – Policies are applied consistently across all apps.
- Monitoring and Auditing – Activity is logged to detect anomalies and meet compliance.
- De-provisioning – Access is revoked when employees leave or roles change.
This closed-loop approach ensures continuous oversight. Without it, organizations risk fragmented systems where identity management access becomes inconsistent and prone to errors.
Why Enterprises Need Identity and Access Management Framework
Enterprises rely on an Identity and Access Management (IAM) framework to secure and streamline access to their resources. IAM enables organizations to manage digital identities, enforce access controls, and maintain regulatory compliance, protecting sensitive data and critical systems from unauthorized access and cyber threats.
Let’s break down the main reasons enterprises implement iam frameworks and how they deliver measurable value.
Preventing Unauthorized Access and Data Breaches
Unauthorized access remains one of the most significant enterprise risks. Attackers often exploit weak credentials, orphaned accounts, or excessive permissions to move deeper into systems. A robust identity and access management framework acts as the first line of defense by enforcing strict authentication and authorization controls.
With proper identity management access, enterprises can:
- Enforce strong authentication protocols like MFA and biometrics to verify user identities.
- Automate access de-provisioning to immediately revoke rights when employees or contractors leave.
- Limit privilege escalation by ensuring users only have the minimum permissions required for their roles.
- Monitor and log access activities for early detection of suspicious behavior.
By combining these measures, organizations significantly reduce the risk of unauthorized data exposure and build stronger trust with stakeholders.
Improving Compliance with Regulatory Standards
Modern businesses face intense regulatory scrutiny. Whether it’s GDPR in Europe, HIPAA in healthcare, or SOX in finance, companies must demonstrate full control over user identities and access rights. This is where an IAM governance framework becomes essential.
With structured identity and access governance, you can:
- Generate automated audit logs showing who accessed which resources and when.
- Apply role-based access controls (RBAC) that align directly with regulatory requirements.
- Perform regular access reviews to ensure only authorized individuals maintain access to sensitive systems.
- Standardize compliance processes across all SaaS and on-premise environments.
By embedding compliance directly into your identity and access management framework, you minimize audit failures, reduce the risk of penalties, and maintain customer confidence in your security posture.
Enhancing Operational Efficiency and User Experience
While compliance and security are top priorities, enterprises also want IAM systems that don’t frustrate employees. A properly designed identity and access management framework improves both productivity and satisfaction by streamlining the way users interact with enterprise applications.
Through efficient identity management access, organizations can:
- Implement Single Sign-On (SSO) so employees log in once to access all authorized applications.
- Use adaptive authentication methods that balance user convenience with risk-based verification.
- Reduce IT helpdesk overhead by automating password resets and access provisioning.
- Enable role-based onboarding so new employees get the right access immediately without delays.
The result is an environment where employees spend less time managing credentials and more time focusing on meaningful work, while IT teams gain efficiency through automation.
What are the Core Components of an Identity and Access Management Framework?
The core components of an Identity and Access Management (IAM) framework include Authentication, Authorization, Administration, and Auditing/Reporting. Together, these elements manage user access, enforce security policies, and ensure compliance across the organization.
Identity Lifecycle Management
One of the most critical pillars of any identity and access management framework is lifecycle management. This governs the entire journey of a digital identity, from creation to deactivation.
- Automates the process of onboarding and offboarding employees.
- Ensures identities are regularly updated when users change roles.
- Prevents orphaned accounts that hackers often exploit.
- Eliminates excessive permissions by enforcing least privilege access.
Access Management and Control Policies
Without clear rules, access quickly spirals into chaos. IAM frameworks establish control policies that determine who can access what resources and when.
- Defines policies for role-based or attribute-based access.
- Enforces time-bound or conditional access restrictions.
- Standardizes rules across cloud, on-premises, and hybrid systems.
- Supports identity and access governance by ensuring only authorized use.
Authentication and Authorization Protocols
At the core of an iam governance framework are authentication and authorization. They serve as the gatekeepers that validate identities and determine permissions.
- Authentication verifies identity using methods such as passwords, MFA, or biometrics.
- Authorization decides the access level based on predefined policies.
- Strong protocols prevent credential theft and minimize insider threats.
- Integrating adaptive authentication adds real-time intelligence.
Role-Based and Attribute-Based Access Controls
Identity and access governance requires precision, which is why RBAC (Role-Based Access Control) and ABAC (Attribute-Based Access Control) are vital.
- RBAC assigns permissions based on job roles (e.g., HR, finance, IT).
- ABAC adds contextual attributes like device type, time, or location.
- Minimizes risk by granting only relevant permissions.
- Simplifies compliance audits by making access rules transparent.
Single Sign-On (SSO) and Multi-Factor Authentication (MFA)
Convenience and security often clash, but SSO and MFA bring balance within an identity and access management framework.
- SSO lets users log in once to access multiple applications seamlessly.
- Reduces password fatigue and IT helpdesk costs.
- MFA strengthens verification by requiring multiple factors (e.g., SMS codes, biometrics).
- Shields against phishing and credential-stuffing attacks.
Privileged Access Management (PAM)
Not all accounts are equal. Privileged users, like admins, hold the keys to critical systems. That’s why PAM is a cornerstone of any iam governance framework.
- Monitors privileged sessions to detect unusual activity.
- Enforces just-in-time access for critical systems.
- Stores and rotates privileged credentials securely.
- Reduces insider threat risks by limiting overprivileged accounts.
Audit Trails and Activity Monitoring
To enforce compliance, organizations must know who accessed what and when. That’s where audit trails become essential in an identity and access management framework.
- Records all login attempts, successful or failed.
- Tracks privileged user activity in real time.
- Generates reports to meet industry regulations (HIPAA, GDPR, SOX).
- Helps security teams investigate incidents faster.
Challenges of IAM Governance Framework
IAM (Identity and Access Management) governance frameworks face challenges such as integrating with diverse systems, managing user lifecycles, ensuring compliance, and balancing security with user experience. Additional hurdles include securing management support, handling complex access permissions, and managing implementation and maintenance costs.
Managing Access Across SaaS Environments
Enterprises often use dozens of SaaS applications, each with its own unique access controls. This fragmentation makes managing identity management access across platforms extremely complex.
- Each SaaS app has a distinct permission model that must be mapped to enterprise roles.
- Maintaining consistency requires a centralized view of all users, roles, and privileges.
- Integration challenges arise when connecting legacy systems with cloud applications.
- Automation and policy enforcement tools within iam frameworks help mitigate human errors and gaps.
Balancing User Convenience and Security
A common challenge in identity and access management is ensuring robust security without frustrating users. Overly strict access controls can slow workflows, while lax controls expose sensitive data.
- Too many authentication steps can reduce productivity and increase helpdesk tickets.
- Minimal security controls increase the risk of credential theft or data breaches.
- Adaptive authentication methods in identity and access management frameworks balance security with convenience.
- SSO and MFA integration reduces password fatigue while maintaining strong identity and access governance.
Maintaining Role Accuracy and Preventing Privilege Creep
Over time, employees may accumulate permissions that are no longer relevant. Without regular oversight, this leads to privilege creep, putting sensitive data at risk.
- Employees changing roles can retain outdated permissions if identity management access isn’t updated promptly.
- Periodic access reviews within IAM governance frameworks ensure roles remain accurate.
- Role-based and attribute-based access controls help reduce the likelihood of unnecessary privileges.
- Automation tools within iam frameworks can flag and revoke excessive access automatically.
Handling Compliance in Dynamic Environments
Regulatory requirements evolve rapidly. Enterprises must ensure their identity and access management framework adapts without disrupting business operations.
- Compliance obligations (like GDPR, HIPAA, SOX) require continuous monitoring and reporting.
- Dynamic cloud and hybrid environments complicate the enforcement of identity and access governance.
- Policies must be flexible to accommodate new regulations while remaining aligned with organizational risk tolerance.
- Automated auditing tools within iam frameworks simplify compliance reporting and reduce manual errors.
Using CloudEagle.ai to Improve IAM Framework
While an identity and access management framework provides the foundation for secure access, CloudEagle.ai takes it further by operationalizing and optimizing IAM across complex SaaS ecosystems.
Automated Provisioning & Deprovisioning
CloudEagle.ai automates user provisioning and deprovisioning, ensuring employees receive the correct identity management access from day one. When a user leaves the organization, access is automatically revoked, reducing risks associated with orphaned accounts.
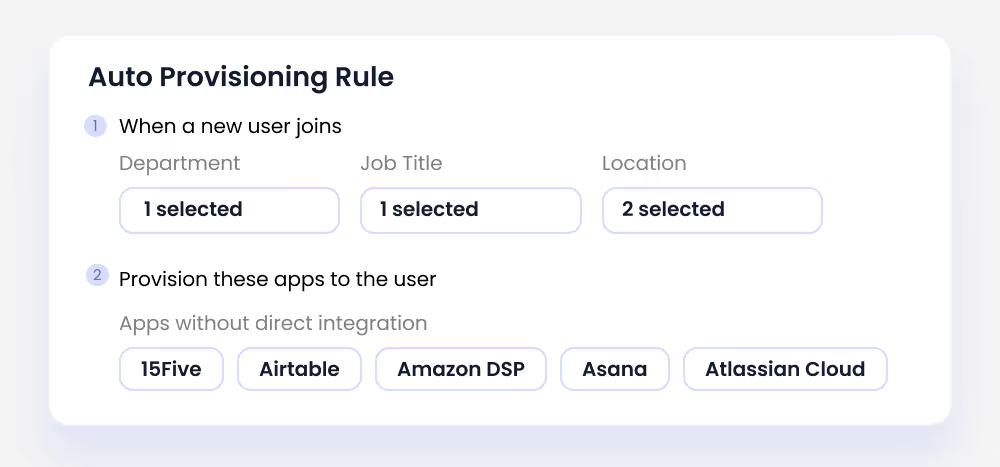
- Automated User Provisioning – Streamlines account creation across multiple systems and SaaS applications.
- Access Revocation – Automatically removes app access when roles change or employees exit.
- Compliance Enforcement – Ensures policies meet internal and external standards, supporting an effective IAM governance framework.
Dynamic Role Management with RBAC
Traditional IAM systems often require manual updates when a user changes roles. CloudEagle.ai enhances role-based access control (RBAC) by dynamically adjusting privileges in real time.
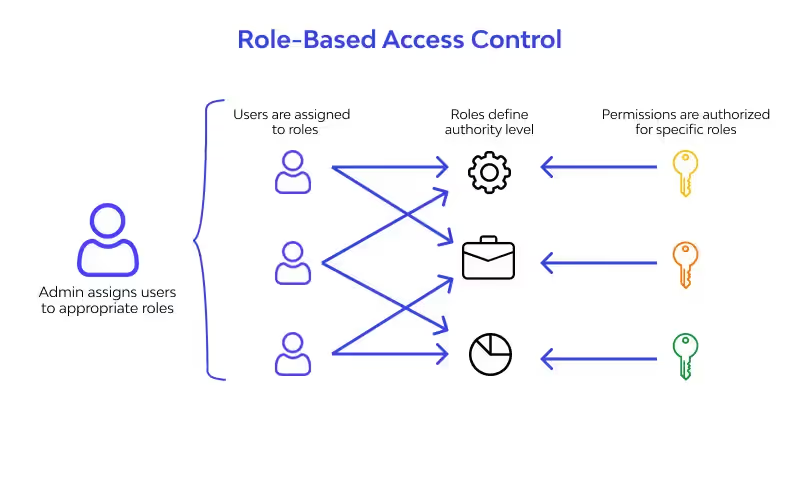
- Real-Time Role Updates – Automatically modifies permissions when a user changes position.
- Least Privilege Enforcement – Ensures employees access only what is necessary for their roles.
- Risk Reduction – Limits over-permissioning and potential security gaps in your identity and access management framework.
Dynamic role management ensures flexibility while maintaining strict control over identity management access across all SaaS tools.
Time-Based Access Management
Some users, like contractors or temporary collaborators, require access for limited periods. CloudEagle.ai introduces time-based access management to enforce temporary access policies effectively.
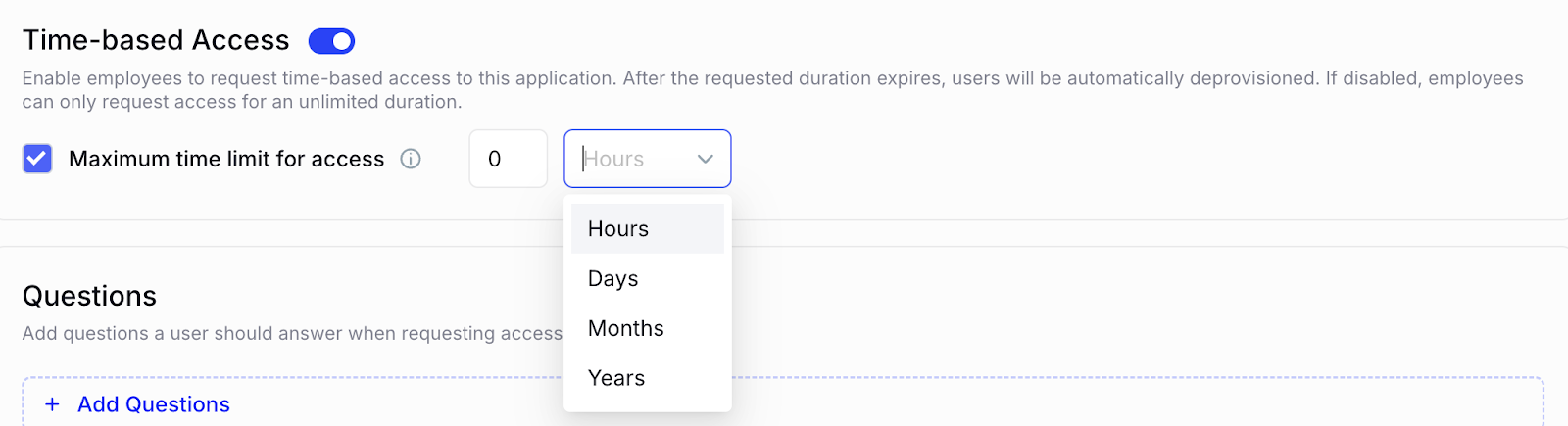
- Temporary Permissions – Grant access for defined periods to reduce unnecessary exposure.
- Automatic Expiration – Access is revoked once the time window ends.
- Compliance Alignment – Supports identity and access governance by applying consistent time-bound policies.
Enforce the Principle of Least Privilege (PoLP)
CloudEagle.ai enforces least privilege principles, ensuring users can only access resources necessary for their roles. Regular automated reviews minimize risks and enhance the overall IAM governance framework.
- Automated Access Reviews – Schedule recurring reviews with notifications for managers.
- Automatic Revocation – If no action is taken, excess privileges are automatically removed.
- Regulatory Compliance – Supports ISO 27001, GDPR, HIPAA, and other standards.
Self-Service App Catalog
CloudEagle.ai empowers employees to request access through a self-service app catalog, reducing IT workload while maintaining oversight.
- Intuitive Portal – Employees can request necessary applications without manual IT intervention.
- Access Approval Workflows – Managers approve or reject requests with audit logs.
- Streamlined Governance – Maintains identity and access governance while improving operational efficiency.
Self-service access simplifies workflows and ensures that the identity and access management framework is consistently enforced across the organization.
Final Words
Securing digital identities is no longer optional; it’s foundational. A strong identity and access management framework helps enterprises safeguard data, meet compliance standards, and streamline user access.
From identity lifecycle management to privileged access controls, every part of the framework contributes to security and efficiency. Yet, challenges like SaaS sprawl, evolving regulations, and privilege creep remain.
That’s why solutions like CloudEagle.ai are critical. By providing automation, visibility, and governance, CloudEagle.ai ensures your IAM framework isn’t just theory but a living, effective security practice.
Book a free demo and see how CloudEagle.ai can transform your identity and access management framework
Frequently Asked Questions
- What are the 4 pillars of IAM?
Identification, Authentication, Authorization, and Accountability – the core elements that ensure secure access and proper identity management. - What is the main goal of IAM?
To ensure the right users have the right access to the right resources at the right time, securely and efficiently. - What are the 3 A's of IAM?
Authentication, Authorization, and Accounting – verifying identity, granting permissions, and tracking activity. - What are the IAM standards of governance?
Policies, role definitions, access reviews, audits, and compliance procedures that guide secure identity and access management. - What is the role of IAM governance?
To enforce policies, manage risk, ensure compliance, and maintain accountability over user access across systems. - Is IAM a framework?
IAM itself is a discipline, while an identity and access management framework is a structured approach to implement it effectively. - Is IAM RBAC or ABAC?
IAM supports both; RBAC assigns permissions based on roles, while ABAC uses attributes like time, location, and device for access control.

%201.svg)







.avif)




.avif)
.avif)




.png)









