HIPAA Compliance Checklist for 2025

In today’s complex IT environments, securing access to sensitive systems and data is a top priority for enterprises. Effective access control is essential to protect against unauthorized use while enabling employees to perform their jobs efficiently.
Strong access governance helps uphold security principles such as least privilege and segregation of duties, which are critical to minimizing risk. One widely adopted approach to access management is Role-Based Access Control (RBAC). The global RBAC market is projected to grow at a CAGR of 12.14% reaching USD 21.3 billion by 2030.
Understanding the foundational RBAC rules is key to designing an access control system that is both secure and scalable. But what exactly are these role-based access control rules, and how do they shape the way permissions are granted?
Let’s explore each rule and its role in effective RBAC access control.
TL;DR
- Role-based access control rules define how users, roles, and permissions interact to ensure users access only what their roles allow, supporting key security principles like least privilege and separation of duties.
- Core RBAC rules include role assignment (valid user-role mapping), role authorization (user role approval), and permission authorization (role-permission enforcement).
- Understanding and applying these rules is essential to designing a secure and scalable RBAC model that streamlines access management and enforces organizational policies.
- RBAC roles group permissions by job function, simplifying administration and minimizing errors by assigning permissions collectively instead of individually.
- Effective role-based access control implementation enforces governance around role creation, role assignment, regular access reviews, emergency access handling, and audit logging for compliance and security.
What is RBAC?
Role-based access control (RBAC) is a widely used security model that restricts system and data access based on the roles assigned to individual users within an enterprise. The core idea behind RBAC is to simplify and secure access management by ensuring users have only the minimum permissions needed to perform their work.
RBAC decreases time spent on access requests and troubleshooting by 25-30%, enabling employees with timely access and reducing IT support tickets. Freshworks
For instance, someone in a finance role might be allowed to access accounting software and financial records while being restricted from accessing sensitive IT systems.
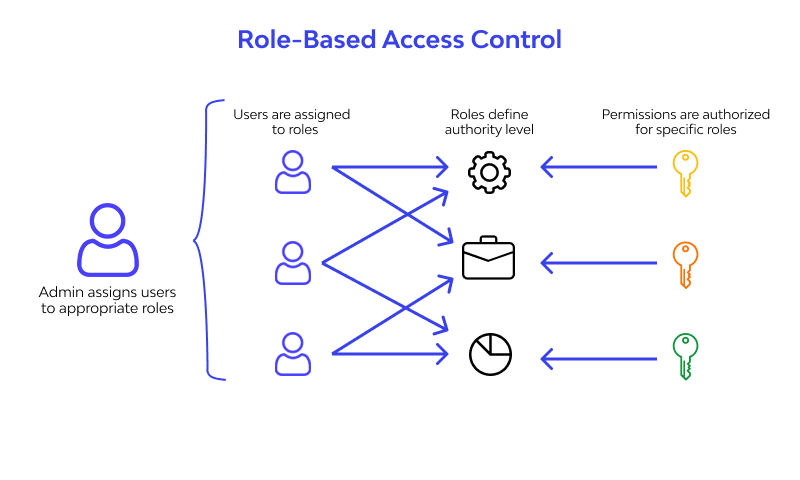
RBAC access simplifies administration by allowing organizations to manage user permissions efficiently. When a user's job changes, administrators only need to update their role rather than manually adjusting individual permissions, greatly reducing the risk of errors and unauthorized access.
From a technical perspective, the RBAC model involves defining:
- Users: The individual identities requiring access.
- Roles: Groups of permissions that represent job functions.
- Permissions: The rights to perform operations on resources.
- Sessions: The active association between users and roles during system access.
Overall, role-based access control provides a scalable, auditable, and policy-driven way to enforce security policies in complex IT environments, making it a foundational element of modern identity and access management (IAM) strategies.
Why Role-Based Access Control is Important for Enterprises?
Role-based access control (RBAC) plays a vital role in making enterprise security and operations efficient and safe. Here are several reasons why RBAC is essential for organizations of all sizes:
1. Reducing Unauthorized Access Risks
RBAC limits access strictly to what a user needs for their role. This means fewer chances for sensitive information to fall into the wrong hands, either accidentally or through malicious attacks. By adhering to the principle of least privilege, RBAC protects valuable data and systems from internal and external threats.
Large - Identity & Access management risks you must know
2. Streamlining User Onboarding and Offboarding
Assigning roles to new employees instantly grants them the right access without manual intervention. When someone leaves or changes jobs, access rights are updated simply by changing or removing roles, reducing errors and security gaps due to lingering permissions.
3. Supporting Compliance and Audit Readiness
Many laws require businesses to demonstrate controlled and auditable data access, such as GDPR, HIPAA, and SOX. RBAC organizes permissions by roles, creating clear audit trails and making it easier to prove compliance during audits.
4. Increasing Operational Efficiency
RBAC cuts down repetitive work by automating access management. Administrators can assign, modify, or revoke role permissions centrally rather than managing millions of individual access rights, freeing up time for more strategic tasks.
5. Enhancing Security with Least Privilege
RBAC enforces the security principle of least privilege—users get only the minimum access necessary to perform their job. This reduces attack surfaces and limits damage if a user account is compromised.
AI-powered RBAC platforms can detect anomalous role assignments and automate least privilege enforcement, improving risk mitigation by over 45% annually.
6. Reducing Human Error
Manual access assignment often leads to mistakes or overly broad permissions. RBAC’s role-based system minimizes human error by standardizing access policies across user groups.
7. Providing Scalability and Flexibility
As organizations grow, manually managing individual permissions becomes impossible. RBAC scales with the company effortlessly, allowing new roles and permission sets to be defined without overhaul.
8. Supporting Segregation of Duties
RBAC can implement policies that separate responsibilities to prevent conflicts of interest or fraud, essential for financial and critical infrastructure sectors.
9. Simplifying Third-Party and Vendor Access
Temporary or external users can be assigned limited roles quickly, controlling their access and ensuring proper removal when no longer needed.
Overall, RBAC is the foundation of a secure and organized access management strategy that aligns IT controls with business needs, making it indispensable for enterprises.
What are the 4 Models of RBAC?
Role-based access control (RBAC) comes in different models that enterprises can use based on their needs to control access more precisely. The four common RBAC models are:
1. Core RBAC
This is the basic model that defines the fundamental components of RBAC are users, roles, permissions, operations, and objects. Permissions are assigned to roles, and users are assigned roles. It lays the foundation for other RBAC models and sets the three main RBAC rules: role assignment, role authorization, and permission authorization.
2. Hierarchical RBAC
This model builds on core RBAC and introduces role hierarchies. Roles can inherit permissions from other roles, reflecting organizational structures. For example, a senior manager role inherits all permissions of a manager role plus additional ones. This reduces complexity by avoiding duplication of permissions in similar roles.
Role hierarchies reduce administrative overhead by up to 40%, enabling better scalability and easier policy updates in complex organizations.
3. Symmetric RBAC
Symmetric RBAC allows administrators to review and verify permissions assigned to roles and users in a balanced way. It helps in conducting audits to ensure no excessive or conflicting permissions exist, optimizing security by properly balancing access.
4. Constrained RBAC
This model adds constraints, usually to enforce separation of duties (SoD). It prevents users from holding conflicting roles either statically (never allowed) or dynamically (cannot activate conflicting roles in the same session). For example, a user cannot both create and approve invoices, reducing fraud risks.
What are the 10 Most Important RBAC Rules to Consider?
Organizations adopting RBAC report an average of 20-30% reduction in IT security costs due to fewer breaches and simplified access management processes.
Implementing role-based access control (RBAC) effectively requires adherence to key rules that protect organizational resources while enabling smooth business operations. These rules form the backbone of a secure, scalable, and manageable RBAC system.
Let’s explore them in more detail:
1. Principle of Least Privilege
At the core of role-based access control (RBAC) is the principle of least privilege. This means users are given only the permissions absolutely necessary to perform their specific job roles. By limiting access this way, enterprises reduce the chances of sensitive systems and data being exposed, lowering risks from insider threats and external attacks.
When a user's privileges are strictly controlled, it becomes much harder for attackers to move laterally within systems if an account is compromised, helping to contain potential damage quickly and effectively.
2. Role Hierarchies and Inheritance
Roles often represent varying levels of responsibility, from junior employees to senior managers. By structuring roles in hierarchies, inheritance allows higher-level roles to automatically inherit the permissions of lower-level ones, simplifying access management.
For instance, a department head might inherit all access rights granted to team members plus additional managerial privileges. This hierarchical model reduces redundancy and eases permission administration.
3. Role-Based Separation of Duties (SoD)
Separation of Duties (SoD) is a key internal control that helps prevent conflicts of interest and fraud by dividing important responsibilities among different roles. RBAC enforces SoD policies by ensuring users cannot hold conflicting roles at the same time.
For example, one employee may be responsible for creating purchase orders, while another must approve them. This division reduces the risk of unauthorized or fraudulent transactions by making sure no single person has full control over a critical process.
4. Time-Bound Access Restrictions
Access needs can be dynamic; hence, RBAC supports time-limited roles to accommodate temporary assignments such as contract workers, interns, or project-based teams. Time-bound restrictions ensure that access automatically expires after a set period, preventing lingering permissions that could become security liabilities.
5. Role Assignment and Validation
Assigning the correct roles to users is vital for RBAC to function accurately. Automated or administrative processes should ensure that role assignments strictly reflect current job functions. Periodic validation of user roles guards against unnecessary privilege creep, where users accumulate permissions over time without justification.
6. Access Approval Workflows
Changes to user roles and permissions must be governed by structured approval workflows. This governance step helps enforce accountability and ensures that all access modifications are justified, authorized, and properly documented. Workflows allow managers or security officers to vet requests before implementation, preventing unauthorized privilege escalations.
7. Role Modification Controls
Permissions tied to roles should not be altered casually. Robust controls—such as change management policies, versioning, and multi-level approvals—ensure that role modifications are deliberate, transparent, and reversible. This control protects the integrity of the RBAC system and helps prevent mistakes or malicious changes.
8. Regular Access Reviews
Continuous compliance and security depend on regular auditing of roles and permissions. Enterprises should conduct periodic access reviews to identify outdated or excessive privileges and to confirm that users’ access aligns with their current responsibilities. Automation tools can facilitate these reviews and generate audit reports to support compliance efforts.
9. Emergency Access Handling
Sometimes, users may need immediate access to resources outside their standard privileges due to operational emergencies. RBAC systems must define emergency or “break-glass” access procedures that allow temporary elevation of privileges under strict monitoring. After the emergency, such elevated access must be promptly revoked and recorded for audit.
10. Comprehensive Audit Logging
An effective RBAC implementation maintains detailed IT compliance audit logs that capture user role assignments, access events, permission changes, and approval activities. These logs support forensic investigations, regulatory audits, and ongoing security monitoring.
Transparent and tamper-proof logs ensure that any suspicious activity or compliance violation can be quickly detected and addressed.
What is the Difference Between RBAC and ABAC?

How CloudEagle.ai Helps Implement Role-Based Access Control?
CloudEagle.ai offers a cutting-edge SaaS access governance platform designed to simplify and strengthen role-based access control (RBAC) for modern enterprises. Its intelligent and automated approach ensures that organizations can enforce secure access policies consistently across diverse SaaS applications while optimizing operational efficiency.
Here are key ways CloudEagle.ai supports RBAC implementation:
Complete Visibility Across SaaS and AI Applications
Many organizations underestimate the number of tools employees rely on. Beyond officially approved apps, teams often adopt new SaaS and AI tools without notifying IT—a practice known as Shadow IT. This leads to rising costs while creating serious security and compliance risks.
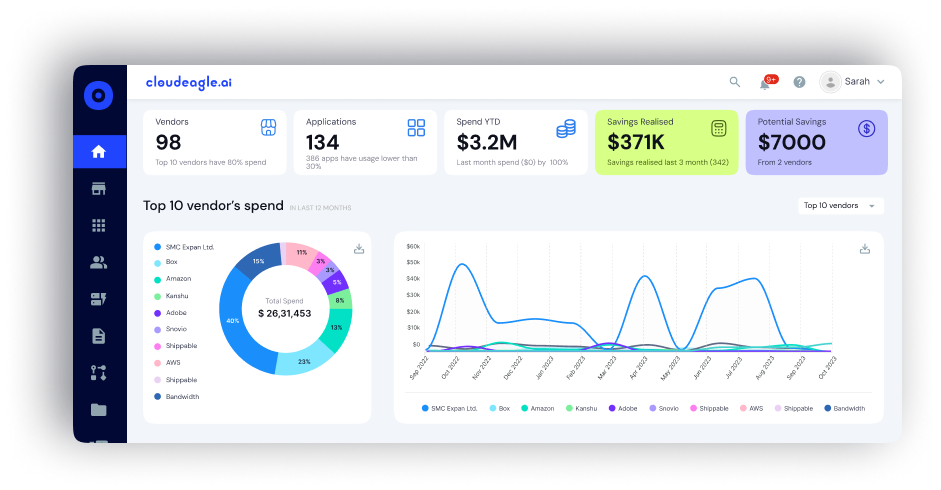
CloudEagle.ai brings all applications into view by automatically identifying every SaaS tool in use. It consolidates usage, spend, and access data into a single dashboard, enabling IT teams to close visibility gaps, eliminate redundancies, and strengthen governance across the application landscape.
Automated Role Management and Optimization
Managing roles and permissions manually can lead to errors, privilege creep, and security risks. CloudEagle.ai automates role provisioning by dynamically mapping user roles to the right permissions across multiple SaaS platforms.
It uses AI-driven analytics to optimize roles, reduce redundant permissions, and maintain compliance with security frameworks like HIPAA, GDPR, and SOC 2.
Just-In-Time (JIT) Access for Enhanced Security
One standout feature of modern access control is Just-In-Time (JIT) Access. It gives users temporary, time-limited access only when they need it to complete specific tasks. By avoiding permanent or excessive permissions, JIT Access reduces the risk of unauthorized use and limits the attack surface.
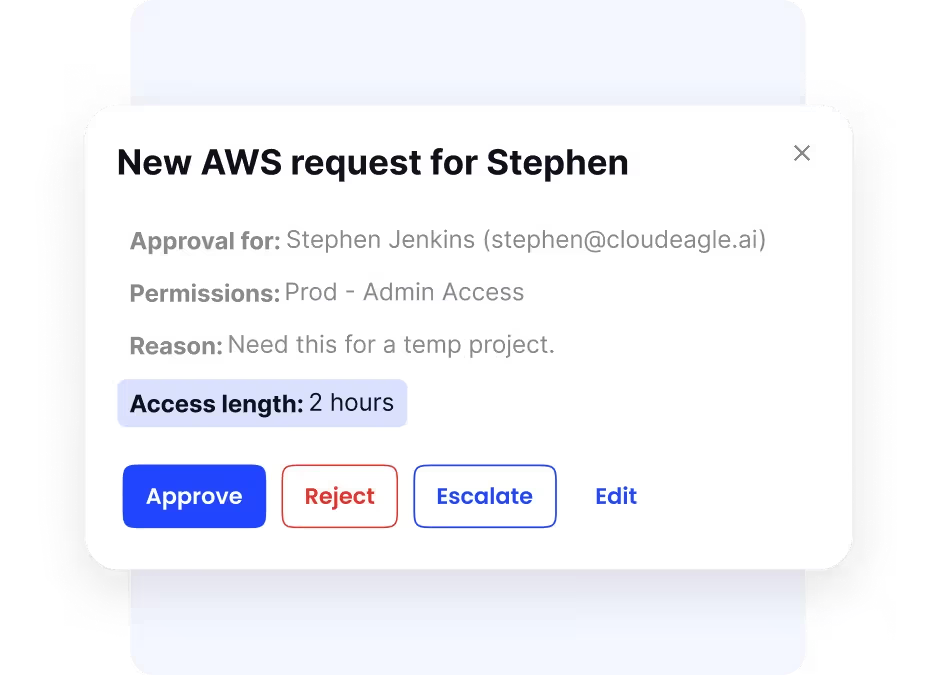
Once the allowed access time expires, permissions are automatically revoked, ensuring strict control over sensitive systems and data. This approach helps protect against insider threats and external attacks by granting the minimum access necessary, only for as long as needed.
JIT Access reduces standing privileges by 60-70%, drastically lowering attack surfaces and enabling fast revocation of elevated permissions to reduce identity-based attacks.
Enforcing the Principle of Least Privilege (PoLP)
CloudEagle.ai enforces the Principle of Least Privilege, ensuring users only have the minimum permissions necessary for their roles. This reduces the risk of unauthorized access and potential insider threats. Continuous monitoring detects and removes unnecessary permissions, addressing privilege creep proactively.
Time-Bound and Context-Aware Access
The platform supports time-bound access restrictions and dynamically adjusts permissions based on context, such as location, device, or risk signals. This granular control further tightens security by adapting to changing conditions and organizational policies.
Policy-Based Access Control Integration
CloudEagle.ai combines RBAC with Policy-Based Access Control (PBAC) by allowing organizations to define detailed, context-aware policies. These policies are centrally managed and enforced in real-time across hybrid and multi-cloud environments, providing flexibility and strong governance.
Streamlined Access Reviews and Compliance
Regular access reviews and certifications are automated, simplifying compliance with standards and audits. CloudEagle.ai generates comprehensive audit logs and reports, providing transparent visibility into who has access, for how long, and why. This capability supports faster audits and continuous regulatory compliance.

Automated access reviews are linked to 35% fewer excessive access privileges and stronger audit compliance, essential for frameworks like SOX and HIPAA. Dataversity
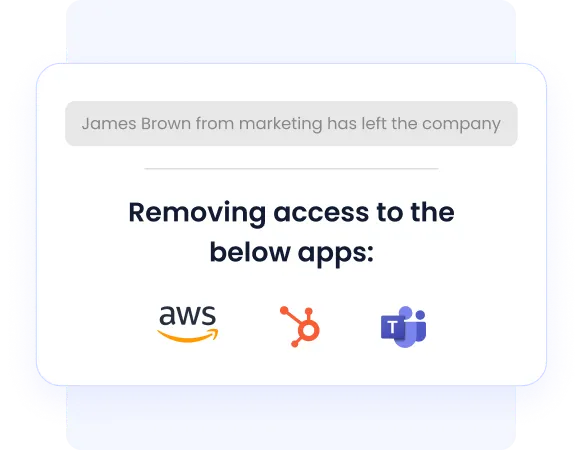
Zero-Touch Offboarding and Access Revocation
CloudEagle.ai’s automated offboarding workflows automatically revoke rights when needed, without any manual intervention. This zero-touch offboarding capability prevents orphaned accounts and significantly reduces insider risk, ensuring secure and seamless access management throughout the employee lifecycle.
Employee Self-Service App Catalog
Employees often don’t know which apps are available or how to request access. CloudEagle.ai solves this with a centralized self-service app catalog where users can easily search for and request access. Approvals are handled through automated workflows, giving IT full visibility and providing faster access for employees.

Integration with Collaboration and Identity Platforms
CloudEagle.ai seamlessly integrates with over 500 SaaS applications, including key identity providers like Okta and Azure AD, as well as popular collaboration tools like Slack and Microsoft Teams. This ensures that RBAC policies aren’t limited to traditional IT systems—they extend to communication platforms and wherever access is needed.
Hear from Alice Park at Remediant, who shares her firsthand experience with CloudEagle.ai. She highlights how the platform simplified access management and significantly enhanced their overall security posture.
Conclusion
Role-Based Access Control (RBAC) is crucial for securing enterprise systems by assigning access rights based on users’ job roles. It strengthens security through the principle of least privilege, ensuring users have access only to what they need.
RBAC simplifies onboarding and offboarding, while helping organizations meet strict compliance requirements such as GDPR, HIPAA, and SOX. RBAC’s flexibility allows it to adapt to various business needs via role hierarchies, separation of duties, and time-bound access.
Implementing RBAC is not a one-time task but a continuous process that evolves with the organization. Studies show 94.7% of surveyed organizations have used RBAC, with 86.6% actively adopting it as their primary access control model, highlighting RBAC’s industry dominance.
When done right, RBAC significantly reduces unauthorized access risks, lowers administrative burdens, and offers a transparent, auditable system for access governance.
Are you ready to advance your access security?
Schedule a demo with CloudEagle.ai today to see how RBAC can fortify your enterprise.
FAQs
1. What is the difference between RBAC and ABAC?
RBAC (Role-Based Access Control) grants access based on predefined roles assigned to users, making it simpler to manage but less flexible. ABAC (Attribute-Based Access Control) evaluates attributes like user details, resource type, and environment dynamically for more fine-grained and context-aware access decisions.
2. What is an example of an RBAC?
An example of RBAC is a company where employees are assigned roles like "Admin," "Manager," or "HR." Each role has specific permissions, such as admins having full system access, managers having access to team reports, and HR able to view employee data. Users gain permissions by their role.
3. What is the difference between rule-based and role-based?
Role-based access control assigns permissions based on users' roles within an organization. Rule-based access control grants or denies access based on a set of rules or policies, which might consider conditions like time of day or IP address, often used alongside RBAC or ABAC systems.
4. What is the RBAC policy rule?
RBAC policy rules define how roles are created, how users are assigned to roles, and what permissions those roles confer. They enforce principles like least privilege, role assignment, role authorization, and permission authorization to ensure secure and managed access.
5. What are role-based access rules?
Role-based access rules are guidelines that determine which roles can perform which actions on specific resources. They ensure users access only what is necessary per their roles and help maintain organizational security and compliance.

%201.svg)








.avif)




.avif)
.avif)




.png)









