HIPAA Compliance Checklist for 2025

Are spreadsheets still your first line of defense?
In a world of fast-moving cyber threats, that’s no longer enough.
In today’s hyper-connected world, a single overlooked vulnerability can lead to data breaches, regulatory fines, and operational chaos. According to reports, 4.45 million dollars is the average cost of a data breach.
IT leaders now rely on smart, automated IT risk management software, tools that help spot, sort, and stop risks before they cause damage. These platforms give real-time visibility, better control, and faster response.
Let’s explore the top 10 enterprise-ready IT risk management tools.
TL; DR
- Today’s fast-changing cyber threats require smart, automated IT risk management software that can detect risks early, respond instantly, and keep your business audit-ready without the hassle.
- With the right IT risk management tools in place, companies can prevent costly incidents before they happen, saving time, protecting data, and avoiding major financial losses.
- IT leaders are moving away from outdated systems and choosing platforms that give them a live view of their entire tech stack, complete with predictive insights and seamless integrations.
- These tools help enforce access rules, detect risky shadow IT, manage third-party vendors, and respond to threats before they become serious.
- Top IT risk management software, like CloudEagle.ai, combines AI-powered discovery, automated workflows, and deep SaaS visibility to reduce risk, secure user access, and eliminate waste across your organization.
What is IT Risk Management Software?
IT risk management software is a tool that helps companies find and fix problems in their tech systems before those problems turn into big, expensive issues. Instead of using unorganized spreadsheets or slow manual checks, these tools let IT teams track cyber threats, spot weak points, and stay compliant; all from one place.
They keep everything organized and show what needs attention, fast. These IT risk management tools are built to make risk management smart, fast, and easy.
Key features of IT risk management tools:
Why Enterprises Need IT Risk Management Tools?
From increasing cyber threats to growing compliance demands, enterprises need smarter, faster ways to manage IT risks. IT risk management software helps leaders protect systems, reduce surprises, and keep everything under control.
According to reports, 63% of IT decision makers admitted that high-sensitivity access in their organization is not adequately secured.
Thus, the need for IT risk management tools arises, which:
1. Addresses Evolving Cyber Threats
Cybercriminals are getting more advanced; your defenses need to keep up. IT risk management tools give IT teams the edge with real-time threat detection and early warnings.
With IT risk management tools, you can:
- Stop cyber threats before they break in.
- Get alerted instantly when something looks risky.
- Keep sensitive data safe with smarter threat detection.
- Track vulnerabilities across networks, devices, and cloud environments.
- Use AI to predict threats before they cause harm.
- Respond faster to incidents with automated workflows.
Know how Heath Ceramic's IT and Finance team got 100% SaaS visibility using CloudEagle.ai.
2. Ensures Compliance with Frameworks Like SOC 2 and ISO 27001
Whether it’s ISO 27001, SOC 2, GDPR, or HIPAA; compliance isn’t optional. Security risk management software keeps your company audit-ready all year round.
With IT risk management tools, you can:
- Stay audit-ready with zero last-minute scrambling.
- Avoid fines with always-updated compliance tracking.
- Show auditors a clear, centralized risk history.
- Automatically map risks to multiple frameworks.
- Track audit dates, document changes, and renewal cycles in one place.
- Prove security controls are in place—backed by real data.
3. Centralizes Risk Detection and Response
Manual spreadsheets and scattered systems cause blind spots. Risk management information system software pulls everything together—so teams don’t miss a thing.
With IT risk management tools, you can:
- All your risks in one dashboard, not 10.
- Coordinate faster with connected teams and tools.
- No more lost emails or missed red flags.
- Link incidents, controls, and actions in one traceable thread.
- Use tags and categories to sort risks by type, owner, or urgency.
- Share risk insights across departments to improve alignment.
4. Enables Data-Driven Decision-Making
Smart decisions require smart data. Software for risk analysis gives leaders visual reports, heatmaps, and KPIs to guide strategy.
With IT risk management tools, you can:
- See the big picture at a glance.
- Focus on what matters most, not what screams the loudest.
- Use predictive insights to fix problems before they happen.
- Prioritize risks by impact, likelihood, and business exposure.
- Use data to back budget requests and policy changes.
- Share insights with execs using simple, visual reports.
Top 10 IT Risk Management Software for 2025
With cyber threats growing and compliance demands rising, choosing the right IT risk management software is key to protecting your digital assets
Here are the top 10 solutions for businesses to stay secure, compliant, and ahead of risks.
1. CloudEagle.ai
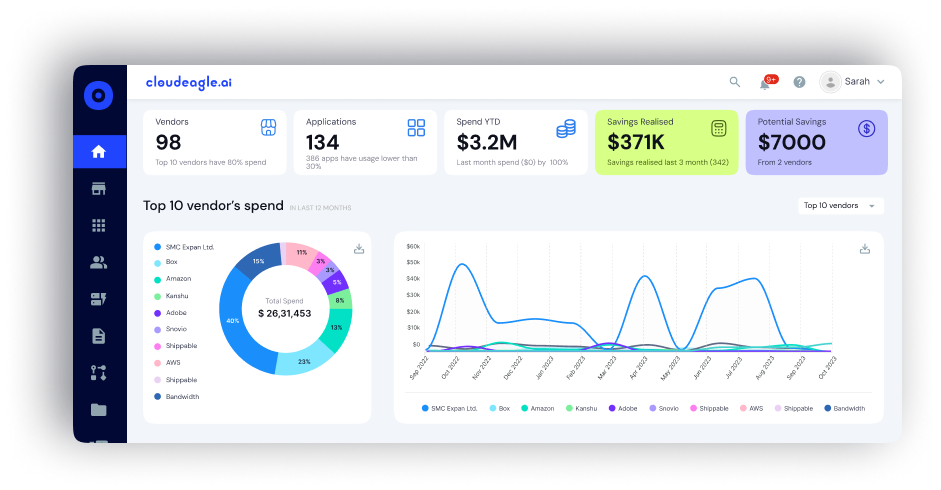
CloudEagle.ai is an advanced SaaS governance platform for IT, security, and procurement teams. It helps enterprises reduce risk by providing complete visibility into their SaaS environment, automating access controls, and ensuring compliance across all apps.
Here’s how it helps protect your organization:
i. Eliminates Shadow IT Risk
One of the biggest threats to enterprise security is what you don’t know. Shadow IT (apps used without IT approval) can expose sensitive data, violate compliance policies, and introduce vulnerabilities.

According to CloudEagle.ai’s IGA report, 60% of AI and SaaS apps operate outside IT visibility.
However, there’s a soution to it; and that’s CloudEagle.ai.
The platform uses advanced AI to scan SSO logs, finance tools, and browser activity to automatically uncover every app being used across the organization, including free trials, duplicates, or rogue installs.
Instead of guessing where risks might exist, IT teams get a complete, real-time SaaS inventory, eliminating blind spots and strengthening the security perimeter across departments.
ii. Strengthens Access Governance
Every active user account is a potential entry point for attackers. CloudEagle.ai brings discipline to access management by automating provisioning, deprovisioning, and periodic access reviews for every app in your stack.
Nidhi Jain, CEO and Founder of CloudEagle.ai, says:
“I’ve seen it happen too many times, an employee changes roles, yet months later, they still have admin access to systems they no longer need. Manual access reviews are just too slow to catch these issues in time. By the time someone notices, privilege creep has already turned into a serious security risk.”

Thus, the need for strong automated access reviews arises. CloudEagle.ai’s IGA report reveals that 95% of organizations still rely on manual access reviews. However, with CloudEagle.ai, you can streamline this process.
Know how Dezerv automated its app access review process with CloudEagle.ai.
iii. Seamless Auto-Provisioning and Deprovisioning
Manual access management is time-consuming and risky. CloudEagle.ai automates both provisioning and deprovisioning to ensure employees get instant, appropriate access when they join, and lose it immediately when they leave or switch roles.
- Auto-Provisioning connects with HRIS tools and identity platforms (like Okta, Google Workspace, or Azure AD) to instantly assign required apps when a user is onboarded, without manual IT intervention.

- Auto-Deprovisioning ensures all access is revoked across all apps when a user offboards or changes departments, eliminating lingering access that could lead to data breaches.
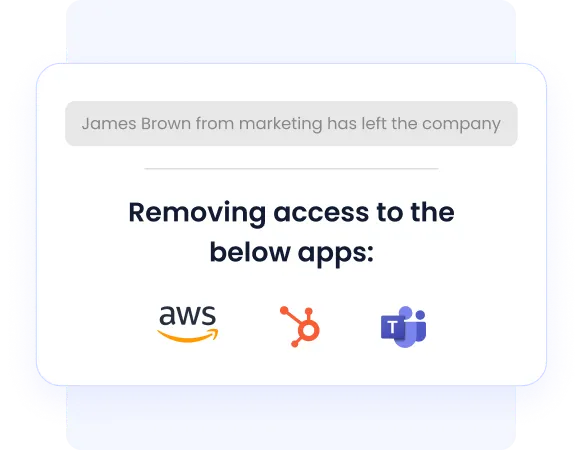
This not only reduces IT workload but also ensures compliance with access control frameworks like ISO 27001, SOC 2, and HIPAA.
Know this story of how Recroom automated employee offboarding and saved $200k annually with CloudEagle.ai.
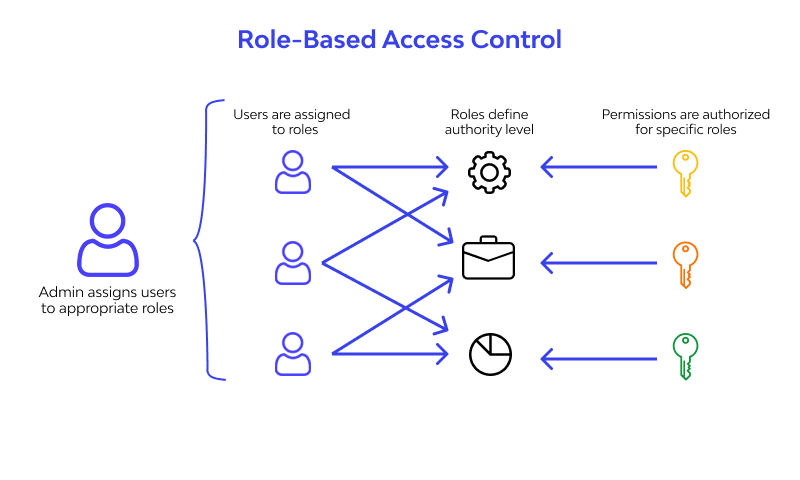
iv. Strong Access Controls
Controlling who can access which apps—and when—is a cornerstone of any effective IT risk management strategy. CloudEagle.ai offers multiple layers of access governance to minimize identity-based risks and enforce security policies across your entire SaaS stack.
- Role-Based Access Control (RBAC): CloudEagle.ai lets admins assign access based on roles (e.g., HR, Finance, Engineering). This ensures users only have access to the apps and data they need, reducing security risks.
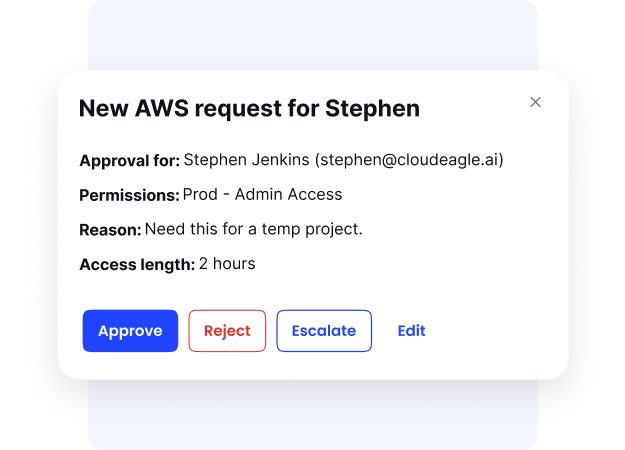
- Just-In-Time (JIT) Access: JIT access gives temporary permissions when needed and automatically revokes them after a set time. This limits unnecessary access and helps meet compliance requirements.
- Attribute-Based Access Control (ABAC): Access is controlled based on user attributes like department, location, or job role. For example, a Sales employee in NY gets access to Salesforce, but not to HR tools—providing precise control without extra admin work.
v. Automates Risk & Compliance Workflows
Manual compliance processes are time-consuming and prone to human error. With CloudEagle.ai’s no-code workflow automation, IT teams can build rule-based flows for approvals, user access, vendor onboarding, and even renewal decisions.
These workflows run inside tools like Slack and Teams, making risk response faster and more collaborative. Whether you're managing compliance checklists, routing access requests, or enforcing separation of duties, CloudEagle.ai ensures consistency, traceability, and speed.
vi. Monitors Vendor & Contract Risk
SaaS vendors are often the weakest link in your security chain. CloudEagle.ai gives you a central dashboard to manage every third-party relationship, tracking access certifications (like SOC 2 or ISO 27001), renewal terms, pricing benchmarks, and vendor risk scores.
The platform flags high-risk vendors, missing compliance docs, or contracts nearing expiration. This lets teams take action early, before a risky vendor leads to a breach, or a forgotten contract leads to renewal waste.
vii. Provides Audit-Ready Insights
When audit season comes around, the last thing you want is to scramble for evidence. CloudEagle.ai keeps detailed logs of all user access, app activity, deprovisioning timelines, and workflow approvals. Dashboards turn raw data into insights, helping IT leaders demonstrate policy enforcement and risk posture with confidence.
viii. Prevents License Misuse & Overexposure
Licenses that go unused or over-allocated don’t just waste money; they increase your attack surface. CloudEagle.ai continuously monitors app usage and flags inactive or underutilized accounts.
With license harvesting workflows, you can reassign unused seats, enforce access policies, and ensure each license adds real value. This not only tightens security but also significantly reduces SaaS spending by up to 30%.
ix. Self-Service App Catalog
CloudEagle.ai’s self-service app catalog helps IT teams stay in control by giving employees a safer way to request software. Instead of going around IT and signing up for unapproved tools (shadow IT), users choose from a list of pre-vetted, compliant apps.
Each request follows an automated, policy-based approval workflow, ensuring that the right people approve access, and usage is logged for visibility. This keeps SaaS adoption secure, reduces risk from untracked tools, and improves compliance without slowing anyone down.
Know how A gen ai company streamlined saas access provisioning with CloudEagle.ai’s self‑service app catalog.
Pros
- Immediate ROI with 30-minute onboarding.
- Reduces SaaS spend by 10–30%.
- Automates tedious IT and procurement workflows.
- Robust access controls and compliance reporting.
- AI-driven benchmarking and vendor negotiation support.
- Centralized dashboard for renewals and SaaS visibility.
2. ServiceNow Risk Management

Part of the ServiceNow GRC suite, the Risk Management module helps enterprises continuously identify, assess, and mitigate risks across IT and business operations—unifying risk data and processes on the one ServiceNow platform.
Key Features
- Continuous Risk Identification & Prioritization: Tracks risks in real time and highlights high-impact vulnerabilities so teams respond quickly.
- Cross-Platform Workflow Automation: Leverages ServiceNow’s automation to connect risk tasks to ITSM, SecOps, and other modules for seamless remediation.
Pros
- Tight integration with other ServiceNow modules (ITSM, SecOps, etc.).
- Strong automation of risk workflows and remediation.
Cons
- Expensive licensing and complex cost structure.
- Steep learning curve and lengthy implementation.
3. LogicGate Risk Cloud

A no-code GRC platform built for flexibility, LogicGate Risk Cloud allows organizations to build workflows, connect risks with controls, automate evidence collection, and scale with their compliance needs.
Key Features
- No-Code Workflow Builder & Applications: Create custom risk management apps and workflows without writing code.
- Automated Evidence Collection & Controls Mapping: Automatically gather control evidence and map it to compliance frameworks to reduce manual work.
Pros
- Highly flexible and configurable.
- Supports multiple risk & compliance use cases.
Cons
- Pricing can be opaque and variable.
- Some complexity in getting started or customizing advanced workflows.
4. Resolver
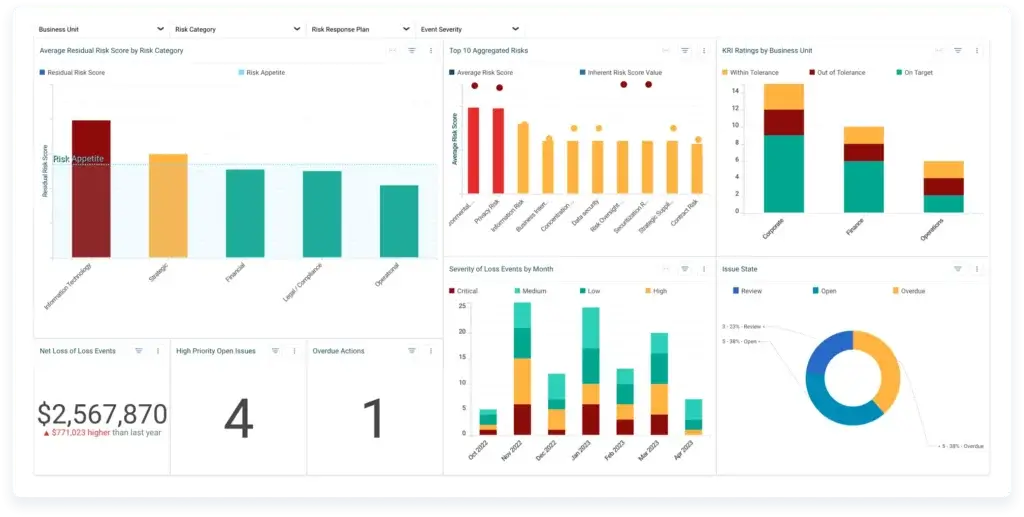
Resolver offers a modular approach to risk, audit, compliance, and security—allowing organizations to piece together the modules they need to manage IT risk within a broader risk ecosystem.
Key Features
- Integrated Risk, Audit, and Incident Modules: Connect risk events, audits, and security incidents in one platform.
- Risk Scenario Modeling & What-If Analysis: Simulate risk impacts and test “what-if” scenarios to plan responses.
Pros
- Modular – you choose the parts you need.
- Good synergy between audit, risk, and incident management.
Cons
- Adding more modules can escalate cost.
- Users report steeper learning for advanced modules.
5. OneTrust GRC
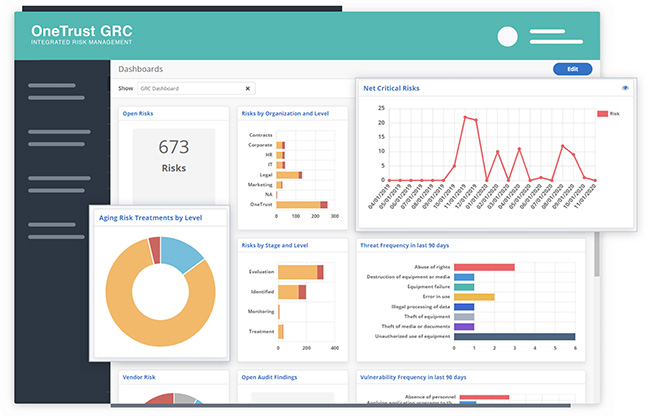
OneTrust’s GRC solution integrates compliance, risk, and privacy modules into one platform—offering real-time oversight of IT risk and compliance across environments.
Key Features
- Policy & Control Management: Maintain and enforce policies aligned with risks.
- Risk & Compliance Assessments: Conduct assessments and gap analyses across systems.
Pros
- Strong privacy and GRC capabilities.
- Well-suited for regulated industries.
Cons
- It can be costly at an enterprise scale.
- Complexity may require dedicated admin resources.
6. RiskWatch
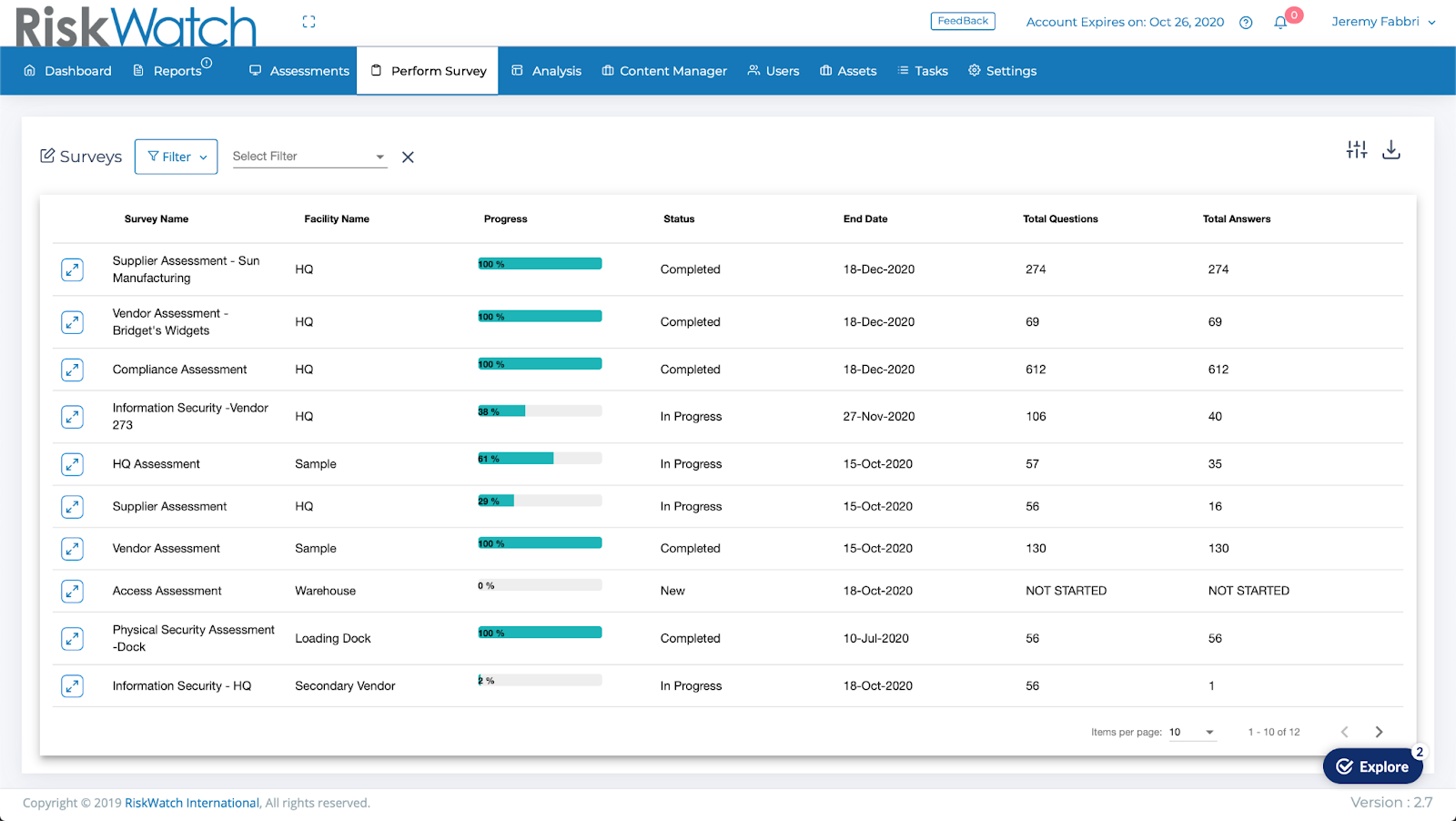
RiskWatch provides risk and compliance assessment software focused on security, safety, and compliance, enabling organizations to evaluate risks and maintain regulatory standards.
Key Features
- Assessment & Questionnaire Engine: Run risk assessments via questionnaires and scoring.
- Risk Analytics & Scoring: Measure and score risks to prioritize mitigation.
Pros
- Focused assessment tooling.
- Good for security & compliance teams.
Cons
- May lack deep integrations with enterprise tools.
- Scalability may be limited for very large organizations.
7. Archer Integrated Risk Management

Archer (by RSA) is a mature, enterprise-grade risk, audit, and compliance platform that supports multiple domains—IT risk, third-party risk, audit, business continuity, and more.
Key Features
- Configurable Risk Frameworks: Tailor risk models to your business, framework, and regulatory needs.
- Reporting & Heatmaps for Board-Level Visibility: Provide executive dashboards and drill-down tools.
Pros
- Very mature and widely used in large enterprises.
- Strong support for multiple risk domains.
Cons
- High cost and implementation effort.
- Requires skilled resources to manage customizations.
8. AuditBoard
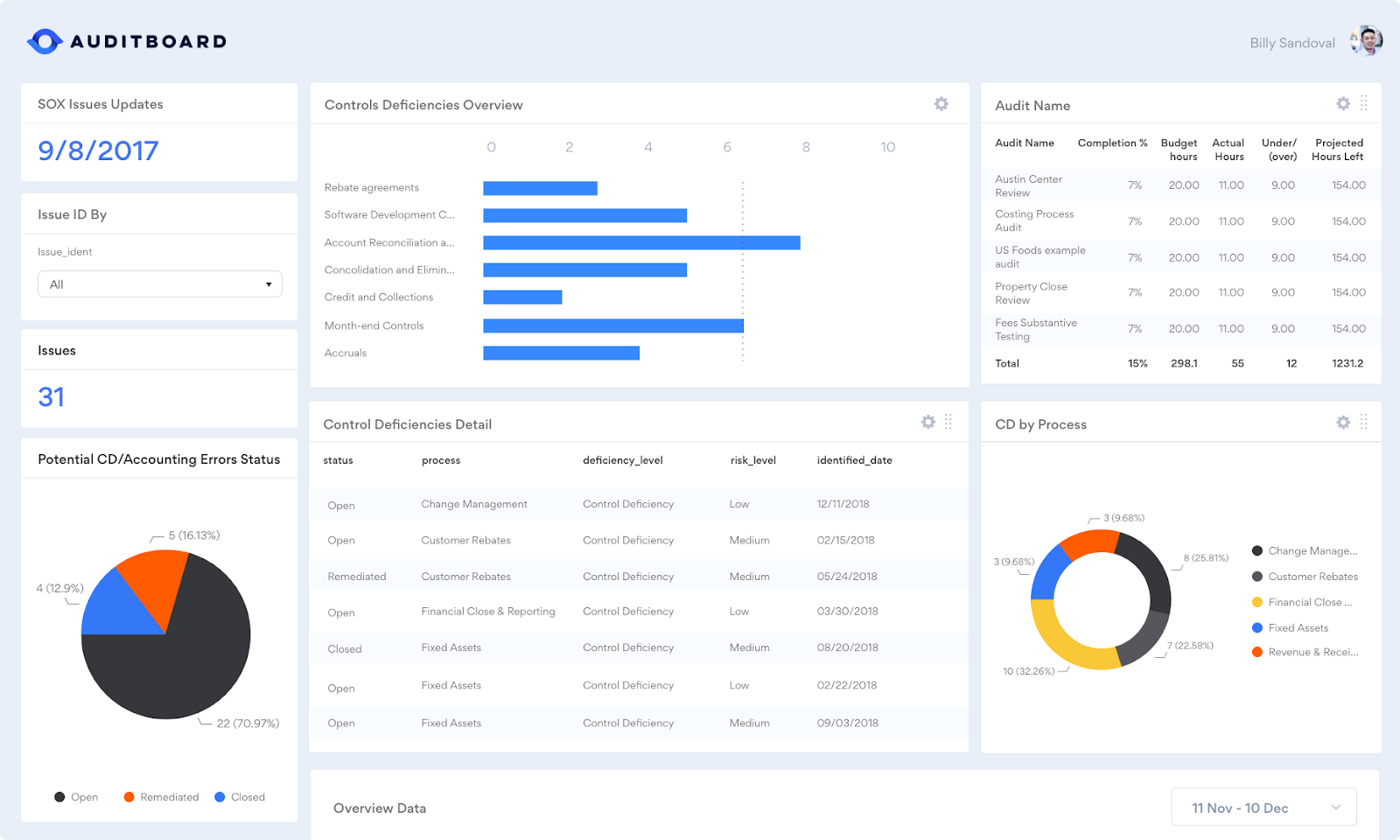
AuditBoard is a cloud-based auditing and compliance platform that also supports risk management—helping teams integrate audit, compliance, and risk into one platform.
Key Features
- Integrated Risk & Audit Workflows: Link risk assessment to audit planning and execution.
- Real-Time Dashboards & Risk Monitoring: Visualize risk trends and key metrics in real time.
Pros
- Excellent for organizations that tie risk to internal audit.
- Clear UI and fast adoption.
Cons
- May lack depth in pure IT risk capability compared to specialized tools.
- Some customization limits for advanced use cases.
9. ZenGRC
ZenGRC is a governance, risk, and compliance tool designed for mid to large enterprises, focusing on simplicity, compliance readiness, and audit performance.
Key Features
- Risk Assessments & Control Management: Conduct risk assessments and manage control effectiveness.
- Audit & Compliance Workflow Automation: Automate audit plans, workflows, and evidence collection.
Pros
- User-friendly and easier onboarding.
- Suitable for organizations that want a balance between power and simplicity.
Cons
- It may not scale as well for extremely large enterprises.
- Fewer advanced analytics compared to high-end tools.
10. MetricStream

MetricStream is a major GRC and risk management platform used in large organizations. It offers broad coverage across compliance, audit, risk, vendor management, and more.
Key Features
- Enterprise Risk & Control Frameworks: Build risk and control models aligned with your frameworks.
- Vendor & Third-Party Risk Management: Comprehensive tools to assess supplier risks.
Pros
- Strong enterprise-grade features and scale.
- Multi-domain GRC support.
Cons
- High cost and complexity.
- Implementation timelines are long.
Key Features to Look for in IT Risk Management Software
In today’s digital world, risk doesn’t wait, and neither should your response. The best IT risk management tools give you more than alerts and dashboards. They integrate deeply, scale effortlessly, and help you make smarter decisions backed by data.
Here’s what enterprise IT leaders should look for:
1. Automated Risk and Compliance Reporting
Manual reporting takes too long and often misses critical details. A strong security risk management software should automatically:
- Generate risk reports instantly, using real-time data from across your tech stack.
- Track compliance with frameworks like SOC 2, ISO 27001, NIST, and HIPAA.
- Save hours of manual effort and improve audit readiness.
- Help teams identify what needs attention—before auditors do.
2. Integration with IAM and Security Systems
An IT risk management tool ensures real-time visibility into who’s accessing what, and allows you to enforce access policies automatically, closing security gaps fast. A disconnected tool adds risk, not value. The best IT risk management solutions:
- Connects directly with your Identity and Access Management (IAM) tools, firewalls, SIEMs, and other security systems.
- Syncs with SIEMs, firewalls, and endpoint tools for full visibility.
- Flags unauthorized access or risky behavior in real time.
- Automates access reviews and user deprovisioning across systems.
3. Scalable Frameworks for Enterprise-Level Use
Enterprises grow, and your IT risk management platform should grow, too. Effective risk management information system software can handle large volumes of users, apps, and data without slowing down. These tools:
- Supports thousands of users and a growing infrastructure without breaking.
- Handles global compliance needs with flexible policy mapping.
- Integrates with diverse tools across departments and locations.
- Adapts to changing risk models and regulatory requirements with ease.
4. Data-Driven Insights and Predictive Risk Scoring
Not all risks are the same; some are more serious than others. That’s why your team needs software for risk analysis that shows which problems matter most. The best tools utilize AI to analyze patterns, assess each risk, and even alert you to potential future issues. This helps your team fix the biggest problems first—before they turn into bigger trouble.
Ensure these tools:
- Uses real-time metrics to assign risk scores to users, assets, or vendors.
- Employs AI or machine learning to identify patterns and predict threats.
- Helps prioritize what to fix first based on potential business impact.
- Visualizes trends through dashboards, risk heatmaps, and scorecards.
Let’s check out this insightful episode of CloudEagle.ai’s SaaS Masterminds podcast, where Karl Haviland shares practical perspectives on AI, governance, and how to scale innovation responsibly.
Conclusion
IT risk management software is no longer a nice-to-have; it’s a must-have. Whether you're securing sensitive data, meeting compliance standards, or trying to prevent the next major cyber incident, these tools help your team work smarter, faster, and safer.
By automating risk detection, integrating with your security systems, and centralizing control, IT risk management tools reduce manual errors, speed up response times, and give leaders the insights they need to stay ahead.
Ready to strengthen your enterprise security?
Schedule a demo with CloudEagle.ai to see how your team can reduce risk, control costs, and stay ahead of cyber threats.
FAQs
1. What is the best risk management software?
There are many good risk management software available in the market. Some popular ones are CloudEagle.ai, ServiceNow, LogicGate, OneTrust, and MetricStream. The best choice depends on your company's needs.
2. Which tool is commonly used for risk management?
ServiceNow is widely used by many companies because it connects well with IT and security systems. CloudEagle.ai is popular for managing SaaS risks.
3. Which is the most famous tool of risk management?
CloudEagle.ai is one of the most recognized names in risk management, widely used by large enterprises for its comprehensive GRC (governance, risk, and compliance) capabilities. It supports complex regulatory needs and scales well across industries.
4. What is FMEA in risk management?
FMEA means Failure Modes and Effects Analysis. It helps find where things might fail and how that could cause problems, so you can fix them early.
5. What technology is used in risk management?
Modern tools use AI, automation, and data analysis to find risks quickly and help teams fix them before they cause harm.

%201.svg)








.avif)




.avif)
.avif)




.png)









