HIPAA Compliance Checklist for 2025

Access governance helps enterprises control who can access their systems, apps, and data. In today’s cloud-first world, teams use lots of different tools, which makes it hard to keep track of app access.
Without proper access governance, the wrong people might access sensitive information, leading to security risks and compliance problems. According to CloudEagle.ai’s IGA report, 28% of enterprises experienced major security incidents due to overprivileged access.
Therefore, organizations need to take action. That’s why it’s important to have a system in place to ensure only the right users get the right access at the right time.
Access governance includes managing user identities, assigning the right permissions, and regularly reviewing access. It also covers special controls for users with higher privileges.
Let’s break down what access governance is, why it matters, and how it helps reduce risk while improving access management.
TL;DR
- Access governance is a process that controls who can access an enterprise’s systems, applications, and sensitive data, ensuring secure and compliant access based on roles.
- Data access governance focuses on protecting sensitive data by setting policies on who can view or edit it, helping enterprises meet compliance requirements.
- Identity governance manages user identities and permissions throughout their lifecycle, automating access reviews and enforcing least privilege to reduce risks.
- Privileged access governance controls and monitors special permissions granted to users with elevated rights, preventing misuse and insider threats.
- SaaS identity governance addresses access control challenges in cloud environments by integrating governance with cloud platforms and SaaS tools for centralized, automated security.
What Is Access Governance?
Access governance is the process enterprises use to control and manage who can access their systems, applications, and sensitive data. It ensures that only authorized users have the right permissions to access specific resources based on their roles. This helps prevent unauthorized access, reduces security risks, and ensures compliance with regulations.
Access governance involves defining access policies, assigning permissions, regularly reviewing user rights, and removing unnecessary access as roles change or users leave. Effective access governance strengthens security, protects critical data, and supports smooth business operations.
What Is The Difference Between Access Management And Access Governance?
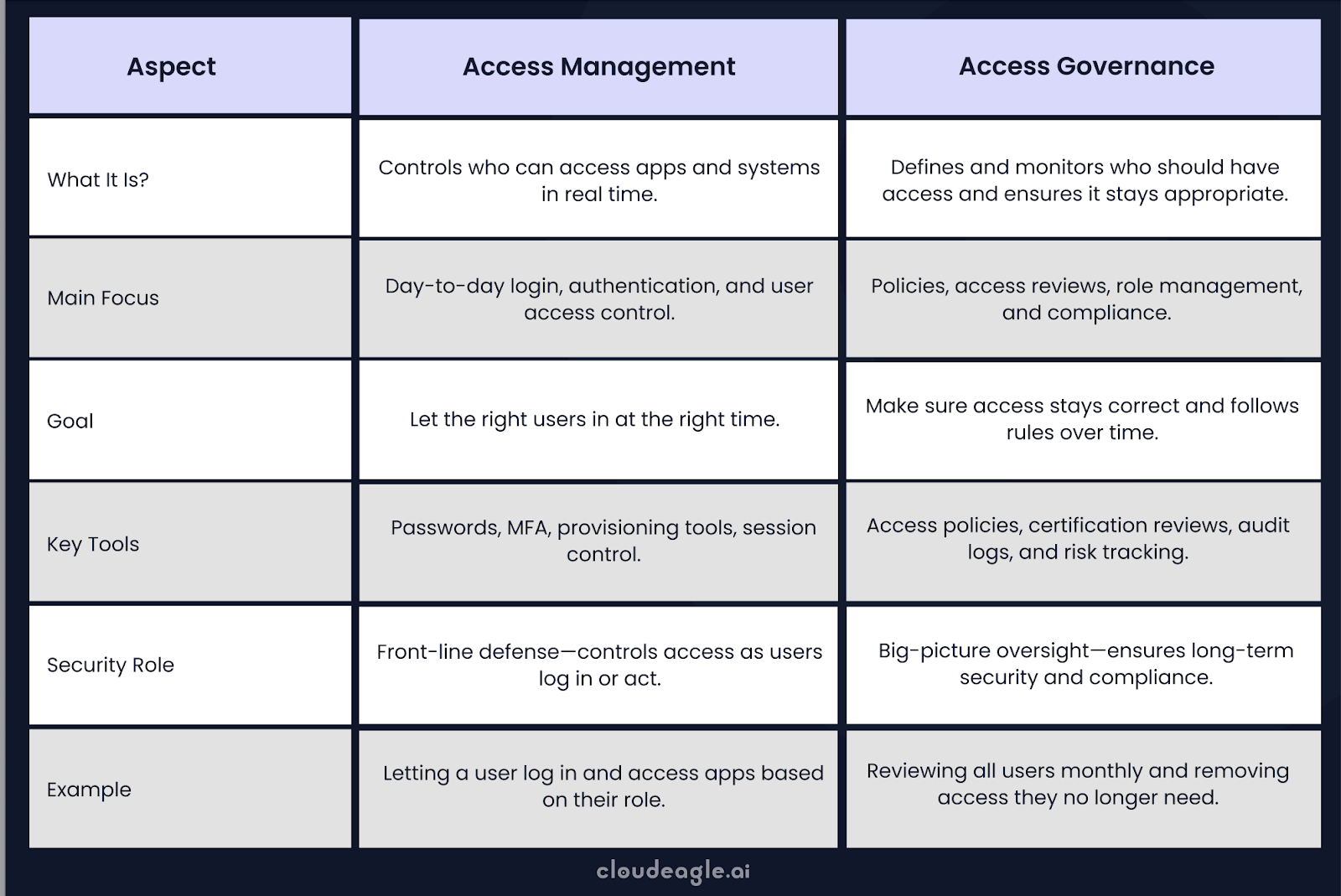
Why Access Governance Matters?
In a world of growing SaaS adoption and remote work, managing who can access what is more important than ever. It:
Reduces Security Risks by Controlling Access: Access governance helps enterprises make sure only the right people can access important systems and sensitive data. By giving access based on each person’s job role, it lowers the chance of unauthorized users causing data leaks or security problems.
Helps Enterprises Follow Rules and Laws: Many laws require enterprises to control and record who can access sensitive information. Access governance gives clear rules and tracks access, helping enterprises meet these legal requirements and avoid fines or penalties.
Gives a Central View of Access Across Systems: Enterprises use many different apps and cloud services. Access governance tools let IT teams see and manage all user access from one place. This helps find and fix any access problems quickly.
Automates Access Processes: Manually managing access can be slow and prone to mistakes. Access governance automates tasks like giving new users access, checking who still needs access, and removing unneeded permissions. This saves time and reduces errors.
Prevents Users from Having Too Much Access: Sometimes users get access to more systems than they really need—called “privilege creep.” Access governance regularly reviews and removes unnecessary access, which keeps systems safer.
Protects Against Insider Risks: Not all security problems come from outside; sometimes, employees accidentally or intentionally misuse access. Access governance limits people’s access to only what they need, reducing these insider risks.
Provides Detailed Reports for Audits: Access governance tracks who accessed what and when. These reports help enterprises show regulators that they are following security rules and also help investigate any security incidents.
What are the Key Components of Access Governance?
Effective access governance is built on several core parts that work together to secure your systems. It includes:
Access Reviews & Certifications
Enterprises regularly review and certify who has access to what systems and data. This means checking if users still need their permissions and removing any unnecessary access. These regular reviews help keep access clean, up to date, and secure.
Policy-Based Controls
Policy-based controls require enterprises to set clear rules and policies about who can access different resources. For example, certain information might only be accessible by managers or IT staff. These policies help automate and enforce good security practices across the enterprise.
Role Management
Role management means defining different user roles, like “employee,” “manager,” or “contractor,” and giving each role the right access needed for their job. Instead of giving permissions one by one, enterprises use roles to make sure users get only the access they need—nothing more, nothing less.
Audit & Reporting
Audit and reporting tools keep records of who accessed what, when, and what actions they took. These logs and reports help enterprises track activity, spot any problems, and prove to auditors or regulators that access policies are followed.
What are the Benefits of Strong Access Governance?
A well-implemented access governance program delivers both security and operational efficiency. With effective access governance, enterprises achieve:
Improved Security Posture: Access governance limits access to sensitive data and critical systems to only authorized users. This reduces the chances of data breaches, insider threats, and unauthorized misuse, strengthening the enterprise’s overall security.
Operational Efficiency: By automating user access requests, approvals, and reviews, access governance reduces the manual workload for IT teams. This speeds up onboarding, offboarding, and access changes, allowing enterprises to operate more smoothly and respond faster to business needs.
Better Compliance: Access governance helps enterprises meet legal and regulatory requirements by maintaining clear access policies, audit trails, and detailed reports. This makes it easier to pass audits, avoid fines, and prove compliance with regulations like GDPR, HIPAA, and SOX.
Risk Reduction: Regular access reviews and strict access controls prevent “privilege creep” where users accumulate unnecessary permissions over time. This minimizes insider risk and potential external attack surfaces, lowering the chance of costly security incidents.
Common Access Governance Challenges
Despite its value, access governance can be hard to implement and scale for the following reasons:
Lack of Centralized Visibility: Enterprises often find it hard to see who has access to what across all their systems and apps. This makes it easier for unauthorized people to get access without being noticed and harder to enforce rules or respond to problems quickly.
Complex User Lifecycle Management: Managing access for new hires, changes in roles, or people leaving is tricky. If access rights aren’t updated right away, old or too much access can create security risks and compliance issues.
Keeping Up with Technology Changes: As enterprises adopt new cloud services and SaaS applications, integrating them efficiently into the existing access governance framework can be challenging. The rapid pace of technology change requires governance systems to be flexible and scalable to avoid gaps in access control across new platforms.
Maintaining Compliance and Audit Readiness: Enterprises must always track and report who accesses what to follow laws and regulations. This requires ongoing effort, and missing reports or non-compliance can lead to fines and damage to reputation.
Policy Misalignment and Outdated Access Controls: If access rules are unclear or not updated regularly, people might have more access than they should. Frequent policy reviews are needed to keep access appropriate and secure.
Resource Constraints: Limited budgets, tools, and skilled personnel can hinder effective access governance implementation and ongoing management. Many enterprises struggle to balance the cost of governance with the growing complexity of their IT environments.
User Resistance and Workarounds: When access controls are complex or slow, users may look for shortcuts or bypass procedures to get their work done quickly. This undermines governance efforts and can lead to unintended security gaps or policy violations.
Access Governance Best Practices
Following a few proven strategies can make your governance program far more effective and efficient. It includes:
Enforce Least Privilege by Default: Grant users only the minimum access needed to complete their tasks. This reduces the risk of unauthorized access or damage from compromised accounts. Consistently applying least privilege limits exposure and helps contain potential breaches.
Automate Access Reviews: Automate the process of periodically reviewing user access rights to identify and remove unnecessary permissions quickly. Automated access reviews save time, reduce human error, and ensure access stays aligned with current roles and responsibilities.
Set Clear Role Definitions: Create well-defined user roles based on job functions with assigned access privileges. Clear role definitions simplify access assignment and help prevent errors and privilege creep by ensuring users only get the permissions relevant to their position.
Monitor Access Continuously: Implement continuous monitoring of user access and activities to detect any suspicious or abnormal behavior. Early detection enables rapid response to potential security threats, minimizing damage and data loss.
Document and Update Policies: Keep detailed, updated documentation of access governance policies, roles, and procedures. Regular policy reviews and updates ensure that governance keeps pace with evolving business needs, technology changes, and regulatory requirements.
Integrate Access Governance with IAM & IGA Systems: Ensure access governance is tightly integrated with identity and access management (IAM) and IGA identity governance and administration (IGA) tools. This integration provides a comprehensive approach to managing identities and access efficiently.
Use Risk-Based Access Controls: Apply risk-based policies that adjust access controls based on the sensitivity of data, user behavior, location, or device. This approach adds an extra layer of security for high-risk situations and critical data access.
How to Implement Effective Access Governance?
Starting small and scaling with the right framework ensures long-term success. To do so:
Centralize Access Data: Bring all access data into a single system or dashboard. This helps IT and security teams see and control who has access to every app, file, and system in one place, making it easier to spot problems or risks across your entire enterprise.
Automate Reviews: Set up automated tools that regularly check and review user access. Automation saves time, reduces human errors, and quickly identifies users with permissions they no longer need, keeping your environment secure and up to date.
Define Roles Clearly: Design clear and specific roles for different jobs, like “HR staff,” “manager,” or “contractor.” By assigning access based on these roles, you make sure people only get the permissions they truly need, which simplifies management and cuts down on mistakes.
Integrate with IAM Tools: Connect access governance with your Identity and Access Management (IAM) systems. This integration ensures that user identities, access requests, and changes are managed smoothly and consistently everywhere, from onboarding to offboarding.
Establish Governance Policies: Develop clear, documented policies that outline who can access what, under which conditions, and how approvals work. Regularly review and update these policies as your business, regulations, or systems change to ensure continued compliance and security.
How to Choose the Best Access Governance System?
Choosing the right tool is key to ensuring your access governance is scalable, secure, and user-friendly. While choosing the right tool, ensure it has:
User-Friendly Interface: Pick a system with an intuitive, easy-to-use interface that lets business users and IT teams clearly see access rights, roles, and responsibilities. A simple interface encourages better adoption and faster decision-making.
Support for All Data Types: Choose a solution that manages access not just for structured data like databases but also for unstructured data such as documents, media files, and cloud storage. This ensures comprehensive protection across all enterprise data.
Clear Accountability and Ownership: The system should allow assigning data owners who understand business needs and can approve or deny access requests appropriately. Strong accountability helps maintain proper access controls.
Compliance-Driven Features: Look for features that support regulatory requirements like GDPR, HIPAA, and SOX, including audit logging, reporting, and identity analytics. These help simplify compliance and prepare for audits.
Advanced Security Capabilities: Ensure the solution supports multi-factor authentication (MFA), automatic user provisioning and deprovisioning, and self-service access requests. Such features enhance security while improving operational efficiency.
Seamless Integrations: Choose a system that integrates smoothly with your existing IAM tools, user directories, cloud platforms, and other IT systems. Good integration ensures scalability and reduces management complexity.
Scalability and Flexibility: Pick a solution that can scale as your enterprise grows and adapts to changing IT environments, including hybrid and multi-cloud setups.
Using CloudEagle.ai to Automate Access Control
CloudEagle.ai is an advanced SaaS management and access governance platform that helps enterprises automate and streamline access control for their SaaS apps.
Here's how CloudEagle.ai facilitates automated access control in detail:
Centralized Visibility and Monitoring: CloudEagle.ai provides a centralized dashboard where administrators can monitor all application access in real-time. This unified visibility helps enterprises track who has access to what, detect unusual behavior, and maintain comprehensive audit trails for compliance and security reviews.

Automated App Access Management: CloudEagle.ai allows enterprises to automate the entire app access lifecycle. You can define rules that specify which employees can request access to specific applications based on their role, department, or project.
When a user requests access, whether through the platform or integrated tools like Slack, the request is automatically routed to the appropriate approver, speeding up the process and reducing delays.
Role-Based and Context-Aware Access Controls: The platform supports granular, role-based access policies, ensuring that users receive only the permissions necessary for their job functions.

Additionally, access can be restricted based on context, such as user location, department, or job title, adding an extra layer of security.
Time-Based Access: CloudEagle.ai provides just-in-time access control, granting temporary permissions for specific projects or tasks and automatically revoking them once the defined period expires. This eliminates the risk of lingering access for former employees or contractors, reducing potential security vulnerabilities.
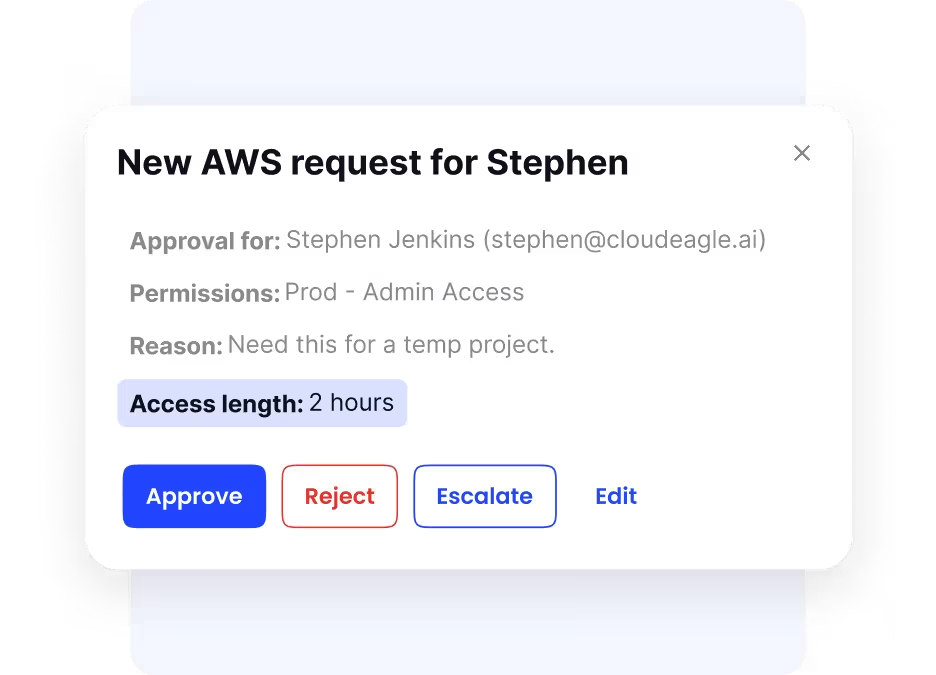
Automated Provisioning and Deprovisioning: CloudEagle.ai simplifies and secures the way enterprises manage user access through automated provisioning and deprovisioning. When a new employee joins, CloudEagle.ai automatically assigns them the right SaaS app access based on their role, department, and location without any manual steps required.

Similarly, when someone changes roles or leaves the company, CloudEagle.ai instantly revokes unnecessary access or fully deprovisions accounts across all connected apps. This real-time automation reduces the risk of unauthorized access, closes security gaps, and eliminates the common issue of orphaned accounts.

Know how CloudEagle.ai helped Bloom & Wild streamline employee onboarding and offboarding.
Automated Access Reviews: CloudEagle.ai makes access reviews simple and automatic. It connects with your SaaS tools to track who has access to what and sends review reminders to managers. They can approve or remove access with just a few clicks. This helps prevent over-access, keeps your data safe, and ensures you stay compliant.

Customizable Approval Workflows: The platform allows enterprises to build tailored approval processes for different apps or teams. You can add extra steps for sensitive tools and ask specific questions to ensure access is properly reviewed before it's granted.
Ensuring Compliance: Ensuring compliance is easy with CloudEagle.ai. The platform automates access reviews, continuously monitors user activities, and maintains detailed audit logs to meet regulations like SOC 2, ISO 27001, HIPAA, and GDPR.

It also automates provisioning and deprovisioning of access, protecting sensitive data and simplifying audit preparation. With CloudEagle.ai, enterprises can confidently stay compliant while reducing manual effort and security risks.
To strengthen enterprise access governance, streamlining user provisioning and deprovisioning is key. See how Alice Park from Remediant improved onboarding and offboarding with CloudEagle’s automated workflows in her testimonial.
Conclusion
Effective access governance is essential for enterprises to safeguard sensitive data, strengthen security, and maintain regulatory compliance. By establishing clear policies, automating access reviews, and enforcing the principle of least privilege, enterprises can significantly reduce risks and prevent unauthorized access.
Nidhi Jain, CEO of CloudEagle.ai, believes that the most successful IAM implementations leverage AI to accelerate human decision-making. Organizations that embrace this partnership model see both enhanced security and improved operational efficiency.
A robust access governance system not only improves operational efficiency but also ensures audit readiness and creates a secure, compliant business environment in today’s fast-evolving digital world.
Are you ready to strengthen your enterprise’s access governance?
Schedule a demo with CloudEagle.ai today and take the first step toward smarter, automated access control.
FAQs
1. What is data access governance?
Data access governance manages who can access an organization’s data and their permissions. It ensures only authorized users access sensitive data, helping protect security, maintain privacy, and comply with regulations by setting policies, monitoring access, and regularly reviewing permissions.
2. What is the principle of identity governance?
The principle of identity governance is to control and manage user identities and their access rights. It ensures that users only have access to what they need based on their roles, reducing security risks and improving compliance.
3. What is the identity governance strategy?
An identity governance strategy involves defining policies and processes for managing user access throughout their lifecycle, including onboarding, permission assignment, regular reviews, and offboarding to maintain secure and compliant access.
4. What is the major role of IGA?
The major role of IGA (Identity Governance and Administration) is to provide centralized control over user identities and access permissions, helping enterprises enforce access policies, prevent unauthorized access, and reduce risk.
5. What is meant by data governance?
Data governance refers to the overall management of data availability, usability, integrity, and security within an organization. It includes policies and procedures to ensure data is accurate, accessible, and protected from misuse.

%201.svg)







.avif)




.avif)
.avif)




.png)









