HIPAA Compliance Checklist for 2025

How sure are you that your organization’s user access is secure and compliant?
Managing user access reviews is becoming increasingly crucial with the growing number of apps, frequent role changes, and ever-evolving compliance requirements. CIOs must ensure that every access privilege is justified and reviewed regularly to protect sensitive data and maintain security.
A clear user access review process helps CIOs identify over-privileged accounts, prevent data breaches, and ensure compliance with standards like SOC 2, GDPR, ISO 27001, and HIPAA.
CloudEagle.ai’s IGA report shows that 95% of organizations still use manual app access reviews, which is no longer efficient. It's time to automate the user access review process.
Let’s explore how to automate the user access reviews process with best practices and tools to reduce risks.
TL;DR
- A regular check to ensure user access aligns with job roles. It includes identifying active users, reviewing permissions, getting approvals, and documenting for audits.
- Regular access reviews reduce security risks, ensure compliance with regulations like SOC 2, GDPR, and HIPAA, and help avoid audit failures.
- Schedule reviews based on events like role changes, offboarding, compliance cycles, new SaaS tools, and updated regulations.
- Lack of visibility, fragmented data, manual reviews, and missed deadlines can make the user access review process inefficient, increasing risks.
- Align stakeholders, define ownership, automate reviews, track progress, and keep audit logs to improve the efficiency and compliance of access governance.
What is a User Access Review?
A user access review is the process of regularly checking who has access to your organization’s systems and data to ensure their permissions are still appropriate for their job. For CIOs and IT leaders, this is key to following the principle of least privilege, ensuring that employees only have access to what they truly need for their roles.
The user access review process usually involves these simple steps:
1. Identify Active Users: Start by making sure you have an up-to-date list of everyone with access to your systems, including full-time employees, contractors, and third-party vendors. This step helps you know exactly who can access what.
2. Review Permissions: Check that each user’s access is appropriate for their current role. For example, if someone has changed roles or left the company, their access may still need to be updated or removed.
3. Get Approvals: After reviewing the permissions, ask managers or app owners to confirm that the access is still needed. This ensures that the right people are approving the access.
4. Document for Audits: Make sure to keep detailed records of the user access review process, including who reviewed the access, what changes were made, and when. This documentation is important for audits and compliance purposes.
Why Should CIOs Care About Access Reviews?
CIOs play a critical role in establishing the governance framework for user access reviews. Neglecting them can lead to security incidents, regulatory penalties, or reputational harm.
Key reasons include:
1. Increasing Cyber Threats and Insider Risk: When employees have more access than necessary, it creates security risks. Hackers or insiders can misuse these overprivileged accounts. Regular reviews help remove unnecessary access and reduce these risks.
2. Compliance Requirements: Regulations like SOC 2, ISO 27001, GDPR, and HIPAA require companies to review user access regularly. Skipping these reviews can lead to non-compliance, resulting in fines or legal problems.
3. Employee Role Changes: Employees frequently change roles or leave the company, which can affect their system access. If access isn’t updated, they may retain permissions they no longer need. Regular reviews ensure access matches their current role.
4. Audit Risks: If access reviews are missed or not done consistently, it can lead to problems during audits. Auditors expect to see that user access is being properly managed. Missing reviews can result in failed audits and damage to the company’s reputation.
What Are The Key Triggers for Access Reviews?
CIOs should schedule user access reviews based on specific events and governance cycles to ensure proper access management. Key triggers for user access review process include:
1. Employee Role Change, Promotion, or Department Shift: When an employee changes roles or moves to a different department, their access needs may change. This is a crucial time to review and adjust their permissions accordingly.
Reflecting on her journey, Nidhi Jain, CEO and Founder of CloudEagle.ai, shares:
“I’ve seen it happen too many times, an employee changes roles, yet months later, they still have admin access to systems they no longer need. Manual access reviews are just too slow to catch these issues in time. By the time someone notices, privilege creep has already turned into a serious security risk.”
2. Terminations and Offboarding: When an employee leaves the company, it’s essential to immediately revoke access to prevent unauthorized access to systems and data.
3. Quarterly or Semi-Annual Compliance Reviews: Many compliance standards, like SOC 2, ISO 27001, HIPAA, and GDPR, require regular access reviews to ensure that only authorized users have access to sensitive information.
4. Introduction of New SaaS or AI Platforms: When new software or tools are introduced to your organization, it's important to review who will have access to them and ensure they are only accessible to the appropriate users.
5. New or Updated Regulatory Mandates: Changes in regulations may require adjustments to user access policies. Regular reviews help ensure your organization stays compliant with the latest rules and guidelines.
What Are The Key Challenges CIOs Face in Access Reviews?
Despite the critical importance of user access reviews, many CIOs face significant challenges that make the user access review process inefficient and incomplete.
Some of the common challenges include:
1. Incomplete Visibility Across Apps: Many organizations lack full visibility into all applications, particularly non-SSO or free-tier tools. These tools often fall outside IT’s control, making it difficult to track who has access and whether it’s still needed.
2. Disconnected Access Data: Access data often exists in silos, separated across IT, HR, and security systems. This fragmentation makes it harder to get a clear, unified view of who has access to what, increasing the risk of oversight.
3. Manual “Rubber-Stamping” Reviews: In some cases, access reviews are conducted manually with little real validation. Managers may simply approve or renew access without thoroughly checking whether it’s still necessary or appropriate, leading to over-privileged accounts.
4. Missed Review Deadlines and Lack of Audit Documentation: Without proper automation, access reviews can be delayed or forgotten, and the documentation needed for audits may be incomplete or not properly tracked. This makes it difficult to prove compliance during an audit.
Essential Components of a Modern Access Review Process
A modern user access review process ensures security, compliance, and efficiency. Here are the key components:
1. Identity + App Mapping
Centralize all users and their access across both SaaS tools and internal systems. This provides a comprehensive view of who has access to what, making it easier to track and manage permissions across the organization.
2. Contextual Insights
Provide data such as the last login, usage frequency, and reasons for access. This contextual information helps reviewers make informed decisions on whether users still need access to specific tools or systems.
3. Reviewer Assignment
Assign app owners, team managers, or department leads to handle the review and approval process. These individuals are best suited to assess whether a user still requires access based on their role and responsibilities.
4. Approval Workflows
Automate the user access review process with rule-based, time-bound workflows. This ensures reviews are done consistently and on schedule, reducing manual errors and delays in the approval process.
Know how Treasure data enhanced access management and reporting with CloudEagle.ai.
5. Evidence & Logs
Maintain exportable, timestamped logs of all user access reviews. These logs serve as proof for audits, ensuring that your organization can demonstrate compliance with industry regulations like SOC 2, ISO 27001, and GDPR.
How to Structure Access Reviews by Risk Level?
Access reviews should be risk-based, not one-size-fits-all.
Best Practices for CIO-Led Access Governance
To make user access reviews both effective and sustainable, CIOs should:
1. Align Stakeholders
Bringing together key teams like IT, Security, HR, and Compliance ensures that everyone is on the same page. Collaboration among these teams helps ensure a thorough and efficient review process, while also making sure access decisions align with company policies and regulations.
2. Define Clear Ownership
Assign clear responsibilities for who reviews access to what. For instance, app owners review access to their specific tools, managers review access for their teams, and compliance leads oversee the entire user access review process. This way, there’s no confusion about who is responsible for what, and the reviews happen promptly.
3. Automate Where Possible
Using user access review tools can automate many aspects of the process, such as data collection, sending reminders, and generating reports. This reduces manual work, minimizes human error, and speeds up the user access review process, making it much more efficient.
4. Track Participation and Fixes
Monitoring who is completing the reviews and how quickly they’re being done helps ensure accountability. If issues are found, track how quickly they are resolved. This ensures the reviews are thorough and that any problems, like over-privileged access, are fixed promptly.
5. Keep Audit Records
Documenting every step of the user access review process is important for compliance purposes. Keeping clear, exportable logs of each review, including who reviewed what, when, and what changes were made, ensures you’re ready for audits and can prove that the user access review process was followed correctly.
6. Have an Escalation Process
Sometimes issues arise that need immediate attention. Having a clear escalation user access review process ensures that any critical access problems are dealt with quickly, without causing delays in the user access review process.
7. Review Third-Party Access
Third-party vendors often need access to your systems, so their permissions should be reviewed just like those of employees. Regularly checking their access helps prevent unauthorized use and ensures that vendors are following the same security protocols as your internal teams.
8. Set a Review Schedule
Create a regular schedule for access reviews, whether they’re done quarterly, semi-annually, or annually. Scheduling them ensures that reviews don’t get forgotten and keeps your access governance consistent.
How CloudEagle.ai Streamlines the Access Review Process?
CloudEagle.ai is an advanced SaaS management and access governance platform that transforms the outdated, manual user access review process into an automated, scalable, and audit-ready workflow that CIOs can rely on.
Here’s how the platform automates access reviews:
1. Centralized Access Review Hub
CloudEagle.ai aggregates all user access data from both IDP-connected and unmanaged SaaS apps into one centralized dashboard. This eliminates the need for manual logins to each app, saving time and reducing complexity for reviewers.
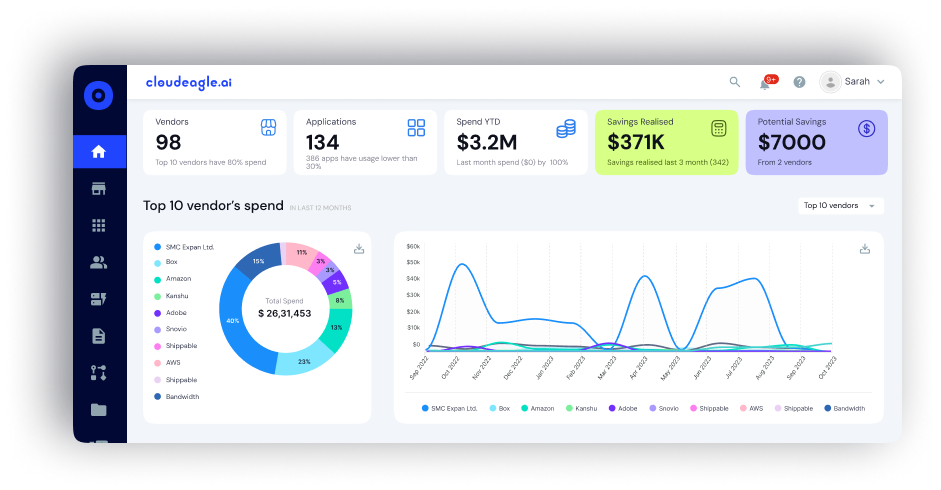
How it helps:
- Saves CIOs and IT leaders hours of manual work.
- Delivers full visibility into who has access to what.
- Supports both SSO and non-SSO tools.
- Provides a real-time inventory of entitlements.
- Speeds up review initiation and certification cycles.
2. Automated Review Scheduling
With CloudEagle.ai, access reviews can be scheduled on a quarterly, semi-annual, or custom cadence. The platform automatically sends notifications to reviewers, tracks their progress, and enforces deadlines, ensuring reviews are completed on time and bottlenecks are avoided.

How it helps:
- Ensures compliance with SOC2, ISO 27001, HIPAA, etc.
- Improves accountability with reviewer reminders.
- Reduces time-to-completion across business units.
- Keeps reviews on track without micromanagement.
- Eliminates email chasing for review sign-offs.
Explore how Dezerv automated its app access review process with CloudEagle.ai.
3. Usage-Based Certification
Rather than asking reviewers to guess if access is still needed, CloudEagle.ai provides key insights such as app usage, last login, access history, and license tiers. This data enables reviewers to make informed decisions based on real usage patterns.
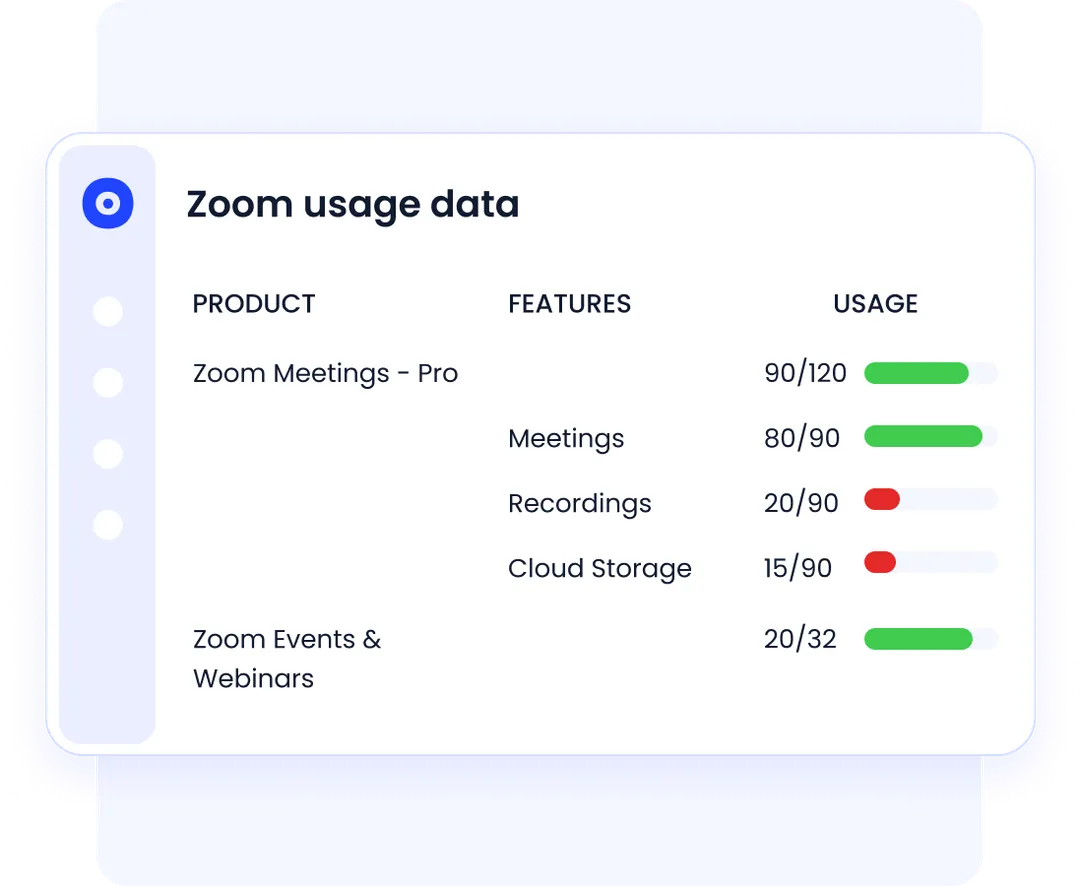
How it helps:
- Minimizes overprovisioned access.
- Flags unused or dormant accounts.
- Reduces risk from inactive entitlements.
- Optimizes license usage and cost control.
- Aligns review decisions with actual behavior.
4. Intelligent Reviewer Routing
CloudEagle.ai assigns reviews to the appropriate owners, such as people managers, app owners, or department heads, based on role mapping and system integrations. This ensures the right people are reviewing the right access, speeding up the user access review process and increasing accuracy.
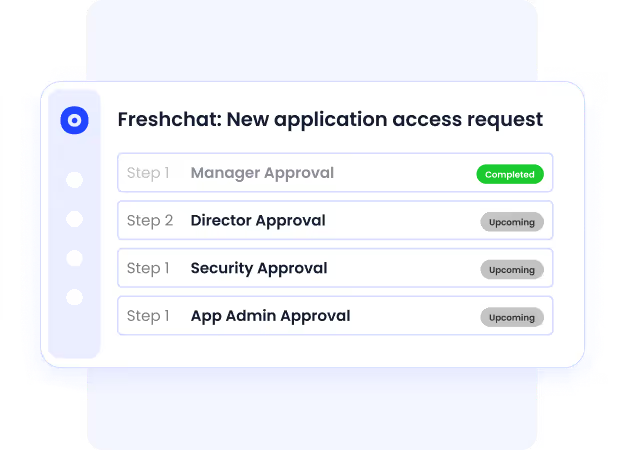
How it helps:
- Ensures high-quality, context-aware decisions.
- Reduces back-and-forth and manual assignments.
- Improves organizational accountability.
- Helps IT avoid acting as the bottleneck.
- Supports decentralized but controlled governance.
5. Automatic Remediation & Revokes
When a reviewer denies access, CloudEagle.ai instantly triggers automated revocation across both IDP and direct app integrations. This ensures that any unapproved access is promptly removed, closing any security gaps immediately.
How it helps:
- Improves time-to-remediation.
- Reduces orphaned or lingering access.
- Strengthens least-privilege posture.
- Avoids security gaps due to delayed IT action.
- Makes offboarding processes seamless.
6. Full Audit Trail & Exportable Reports
Every action, approval, revocation, comment, and timestamp is logged in real-time. CloudEagle.ai’s detailed logs and exportable reports are ready for audits at any time, ensuring your organization remains compliant and prepared for any review.
How it helps:
- Eliminates manual evidence collection.
- Simplifies compliance audits and assessments.
- Supports internal GRC reporting workflows.
- Provides clear accountability by the user and reviewer.
- Builds long-term audit readiness.
7. Non-SSO & Shadow App Coverage
CloudEagle.ai goes beyond just IDP-connected apps, offering coverage for non-SSO and shadow apps discovered through integrations with finance, browsers, or custom sources. This ensures access reviews are comprehensive, even for apps that may not be connected to your IDP.

How it helps:
- Covers the full spectrum of user access.
- Helps CIOs reduce shadow IT risk.
- Delivers complete control over distributed SaaS.
- Improves review completeness.
- Makes governance extensible beyond core tools.
Check out this insightful episode of CloudEagle.ai's SaaS Masterminds podcast, featuring Karl Haviland as he shares expert insights on AI, governance, and scaling innovation responsibly.
Conclusion
User access reviews are no longer optional; they are essential for safeguarding security, ensuring compliance, and building trust within your organization. CIOs who implement a streamlined, automated access review process not only mitigate the risk of data breaches but also stay confidently audit-ready at all times.
Platforms like CloudEagle.ai make the user access review processes seamless by consolidating app access visibility, optimizing workflows, and ensuring that every user privilege is thoroughly validated. With automation, access governance becomes a strategic asset, reducing risks, improving efficiency, and freeing up valuable time for other critical tasks.
Are you ready to automate your user access reviews?
Schedule a demo with CloudEagle.ai and start transforming your user access review process.
FAQ
1. What is a UAR in compliance?
A user access review process (UAR) is a compliance process that verifies user permissions against job roles to ensure security and regulatory alignment.
2. What is the UAR review process?
It’s the structured user access review process where managers or app owners periodically verify, approve, or revoke access.
3. How to audit user access?
A user access review audit involves reviewing logs, approvals, and reports to confirm that access reviews were completed accurately and on time.
4. What are the 4 A’s of IAM?
Authentication, Authorization, Administration, and Audit are the foundational principles of access governance.
5. What is the UAR process in GRC?
In Governance, Risk, and Compliance frameworks, the user access review process ensures access controls align with corporate policies and external regulations.

%201.svg)








.avif)




.avif)
.avif)




.png)









