HIPAA Compliance Checklist for 2025

For enterprises, protecting shareholder value and customer trust is critical. To achieve this, enterprises must remain compliant and resilient at all times. An IT general controls audit (ITGC audit) supports this by ensuring the tech stack is secure, compliant, and reliable.
These audits review core ITGC controls like access management, change management, and data backups. Strong ITGC compliance prevents financial misstatements, regulatory fines, and security risks. Weak controls can quickly erode confidence.
In a recent PCAOB report, it was found that nearly 39% of audits were flagged for control or evidence deficiencies, indicating persistent gaps in ITGC testing. It’s time to take action and protect enterprises from potential breaches or compliance failures.
Let’s explore what ITGC is, how ITGC testing works, and the steps to achieve compliance.
TL;DR
- An ITGC audit reviews core IT controls such as access, change management, backups, and operations to ensure systems are secure, reliable, and compliant.
- Strong ITGC controls reduce fraud, errors, and compliance risks. Weak controls can result in fines, reputational damage, and failed certifications.
- Audits follow structured steps, including scoping, risk assessment, control identification, testing, reporting, and remediation to verify control effectiveness.
- ITGC audits protect financial data, strengthen security, build investor trust, and confirm compliance with SOX, SOC 2, ISO 27001, and GDPR.
- CloudEagle.ai automates access reviews, centralizes evidence, and enables continuous monitoring, cutting audit time from weeks to hours while ensuring compliance year-round.
What is an ITGC Audit?
An ITGC audit is a formal review of the foundational IT controls that support a company’s financial reporting and compliance obligations. These audits evaluate whether systems and processes around access management, change management, data backup, and IT operations are operating effectively.
Strong ITGC controls reduce risks of fraud, data breaches, and reporting errors, while weak controls can expose an organization to fines, reputational damage, or failed certifications.
Key Steps in an ITGC Audit
1. Planning and Scoping: Define the audit objectives, identify systems in scope, and align with compliance requirements such as SOX or SOC 2.
2. Risk Assessment: Evaluate potential risks across IT processes, including access control, change management, and data protection.
3. Control Identification: Map and document the ITGC controls in place, covering user access, backups, and operational practices.
4. ITGC Testing: Perform detailed ITGC testing to check if controls are designed properly and working as intended.
5. Gap Analysis: Identify control deficiencies, compliance gaps, or risks that may affect financial reporting or security.
6. Reporting and Recommendations: Deliver an audit report highlighting findings, risks, and corrective actions needed for ITGC compliance.
7. Remediation and Certification: Address gaps, strengthen controls, and pursue ITGC certification where required to demonstrate compliance and resilience.
Why is ITGC Audit Important for Enterprises?
An ITGC audit is not just about passing a compliance checklist. An ITGC audit protects systems, financial data, and reputation by strengthening resilience and reducing enterprise risks.
Here’s why it’s important:
1. Strengthening Security and Data Integrity
ITGC audits confirm that controls around system access, backups, and changes are working effectively. This prevents accidental errors or malicious activities from corrupting data and ensures decision-makers can rely on accurate reports.
2. Reducing Fraud and Unauthorized Access Risks
Weak access controls are one of the top causes of fraud and cyberattacks. ITGC testing verifies whether user permissions, role assignments, and approval workflows are enforced properly. By closing these gaps, enterprises reduce the likelihood of insider threats and unauthorized access.
3. Ensuring Compliance With Regulatory Mandates
Frameworks like ISO 27001, SOC 2 Type II, GDPR require strong ITGC controls. An audit confirms compliance with these mandates, helping enterprises avoid financial penalties, lawsuits, and reputational damage. For regulated industries such as finance and healthcare, this is especially critical.
4. Building Trust With Investors and Auditors
Investors and external auditors want proof that governance standards are in place. Independent ITGC certification demonstrates that an enterprise is managing IT risks responsibly. This builds investor confidence, smooths financial audits, and strengthens market credibility.
Core ITGC Domains to Audit
An ITGC audit reviews core IT governance areas that impact security, compliance, and business continuity. It helps identify weaknesses that may cause errors, penalties, or security risks, ensuring the IT environment stays resilient and trustworthy.
1. Access Controls and Identity Management
Access management is often the first line of defense in IT governance. Auditors review how enterprises assign, modify, and revoke user access to sensitive systems. Strong role-based access and multi-factor authentication ensure that only authorized users perform critical tasks.
For enterprises, weak access controls are both a security risk and a compliance failure. Insider threats, unauthorized privilege escalation, and abandoned accounts from former employees all raise the chances of fraud and breaches. ITGC audits confirm these controls are tested regularly and meet compliance requirements.
2. Change Management and System Updates
Modern enterprises evolve quickly, with frequent system upgrades, patches, and configuration changes. An ITGC audit examines how these changes are tracked, approved, and tested before implementation. The goal is to prevent errors or unauthorized updates that might disrupt operations or create vulnerabilities.
A failure in this domain can lead to system downtime, misaligned financial reporting, or regulatory violations. Strong ITGC controls ensure that every change is documented, tested, and approved by the right stakeholders, reducing operational and reputational risks.
3. Backup, Recovery, and Data Integrity Controls
Data is the backbone of financial and operational reporting. ITGC audits review whether backups are performed consistently, tested for accuracy, and recoverable in case of disaster. They also verify whether data integrity checks are built into operational processes.
Without robust backup and recovery procedures, enterprises risk data loss, downtime, and compliance failures. Regulators often scrutinize this area closely since lapses in ITGC testing around recovery can directly affect business continuity and shareholder confidence.
4. IT Operations and Monitoring Processes
Daily IT operations, including monitoring, logging, and incident response, form the engine room of enterprise technology. Auditors assess whether systems are monitored continuously, alerts are acted upon promptly, and incident response plans are tested.
This ensures that risks are detected early and disruptions are minimized. A strong IT operations framework demonstrates maturity in governance, supports smoother audits, and reduces the likelihood of missed red flags in critical business processes.
5. Vendor and Third-Party ITGC Considerations
With most enterprises relying on cloud and SaaS providers, third-party risks are unavoidable. ITGC audits extend to vendor management practices, ensuring external partners meet security, compliance, and contractual obligations.
Weak oversight in this domain can lead to data breaches, failed certifications, or regulatory penalties due to non-compliant vendors. Enterprises must ensure contracts include audit rights, security standards, and monitoring of vendor controls. This safeguards both compliance and brand reputation.
6. Documentation and Evidence Management
Compliance is not only about having strong controls; it’s about proving they exist. ITGC audits review documentation of policies, procedures, and system configurations, along with evidence from prior control testing.
Proper documentation accelerates audit readiness and reduces disputes with regulators and auditors. For leadership, this translates into cost savings, efficiency, and stronger confidence that the enterprise is prepared for scrutiny at any time.
A Step-by-Step ITGC Audit Process
An ITGC audit follows a structured approach to test whether IT general controls are effective, reliable, and compliant with regulations. Here’s how you can implement it:
1. Planning and Scoping the Audit
The first step is defining the audit scope. Auditors work with IT and compliance leaders to decide which systems, applications, and business processes to review. High-risk systems, like financial reporting tools or HR platforms with sensitive data, get the most attention.
This stage also includes aligning with regulatory requirements such as ISO 27001, SOC 2 Type II, GDPR, and others depending on industry and geography. A well-scoped audit avoids wasted resources on low-risk systems and ensures compliance obligations are addressed directly.
2. Identifying Key ITGC Controls to Test
Next, auditors identify the specific ITGC controls that need evaluation. These include access management, change management, backup and recovery, and IT operations monitoring. The purpose is to confirm that each control area supports accurate reporting and secure operations.
For example, auditors check access controls to ensure former employees lose system access. They also review change management to confirm updates are approved and tested. Focusing on the right controls helps protect business continuity and compliance.
3. Gathering Evidence and Documentation
Auditors then collect documentation to verify whether policies and controls are formally defined and consistently followed. This may include IT policies, system configuration records, audit logs, approval workflows, or backup schedules.
Strong documentation makes compliance easier to prove. Enterprises that maintain evidence proactively reduce audit delays and disputes with external auditors. This stage highlights the importance of governance maturity, clear evidence builds investor and regulator trust.
4. Testing Control Effectiveness
At this stage, ITGC testing is performed to confirm whether controls operate as intended. Testing may involve sampling system access requests, reviewing logs of system changes, or verifying data recovery from backup systems.
For example, auditors may check if administrator access requests were properly approved or if backup files can be restored without errors. Failures here pose risks to compliance and security. Regular testing helps enterprises find weaknesses before regulators or attackers do.
5. Reporting Audit Findings and Recommendations
Once testing is complete, findings are compiled into an audit report. This document outlines strengths, weaknesses, and areas of non-compliance. Risks are typically classified by severity, helping leadership understand which issues require immediate remediation.
Recommendations are then provided, guiding enterprises on how to strengthen weak controls, align processes with compliance frameworks, and improve operational efficiency. For executives, this report becomes a roadmap to enhance IT governance while protecting shareholder value.
6. Continuous Monitoring and Remediation
An audit is not a one-time exercise. Enterprises must act on findings, remediate gaps, and implement continuous monitoring practices to maintain strong controls year-round. This includes automating control checks, using monitoring dashboards, and scheduling interim reviews.
By improving IT operations continuously, enterprises reduce repeat audit issues and show resilience to regulators. This leads to fewer audit surprises and stronger confidence that compliance and governance risks are managed well.
Common ITGC Audit Challenges
Even large enterprises face obstacles during an ITGC audit. These challenges often come from fragmented processes, complex systems, or limited resources. Left unaddressed, they can delay compliance, increase costs, and expose the business to security or regulatory risks.
Here are the challenges you must stay aware of:
1. Lack of Centralized Control Documentation
A major ITGC challenge is poor documentation. Policies, procedures, and evidence are often scattered across teams, making it difficult for auditors to confirm if controls work effectively. This slows audits, drives up costs, and raises concerns about governance maturity.
2. Complex IT Environments With Multiple Systems
Most enterprises run many systems, from ERP and HR tools to SaaS apps. Each requires proper ITGC controls, but complexity makes full coverage difficult. Missing even one high-risk system can cause audit gaps. Mergers, acquisitions, or rapid tech adoption add to the challenge, making audits more resource-heavy.
3. Insufficient User Access Reviews
User access reviews are among the most common points of failure in ITGC testing. If terminated employees retain access, or if role changes are not updated promptly, the enterprise risks unauthorized activity or fraud. Regulators often cite this as a leading compliance weakness.
According to reports, 95% of enterprises still rely on manual access reviews.

Beyond compliance, poor access reviews create real business risk. Insider threats, data leakage, and operational disruption all stem from weak access governance. Regular, automated access reviews are essential to avoid repeat findings in audits.
4. Ineffective Change Management Processes
Enterprises regularly apply patches, updates, and system changes. Without structured approvals and testing, these changes may go live unchecked, causing downtime, data corruption, or security risks. Weak change management is a serious compliance issue since auditors expect clear approvals and testing records.
5. Resource Constraints and Manual Testing
ITGC audits need skilled IT, audit, and compliance teams to gather evidence and test controls. Many enterprises lack resources and rely on manual processes that are slow and error-prone. This extends audit timelines, raises costs, and lowers accuracy. Without automation, enterprises face recurring audit gaps and higher compliance risks.
Best Practices for a Successful ITGC Audit
Preparing for an ITGC audit can be complex, but following best practices makes the process smoother and more effective. Here’s how you can achieve a successful ITGC audit:
1. Automate User Access Reviews and Monitoring
Manual access checks are slow and prone to errors. Automation makes sure former employees lose access quickly and that permissions always match job roles. Continuous monitoring tools flag unusual activity early, reducing risk. For auditors, automated logs prove that ITGC controls work effectively, cutting delays and building trust.
2. Standardize Change Management Procedures
Uncontrolled system changes often cause audit failures. Standardizing updates, patches, and configuration changes ensures every change is approved, tested, and reviewed before going live. This reduces errors, prevents downtime, and shows auditors that strong IT audit general controls are in place. A consistent process also avoids surprises during testing.
3. Maintain Strong Evidence and Audit Trails
Auditors rely on clear evidence to confirm compliance. Enterprises should keep updated policies, approval records, and system logs in one centralized lo`cation. Strong audit trails prove that processes were followed consistently. This not only speeds up the audit but also demonstrates maturity in governance, making it easier to achieve ITGC certification.
4. Perform Regular Internal ITGC Assessments
Waiting for the annual audit increases the risk of surprises. Regular internal reviews help detect gaps early, giving teams time to fix issues before external auditors arrive. These proactive assessments show regulators and investors that the enterprise takes ITGC compliance seriously and maintains strong oversight year-round.
5. Leverage Technology Platforms for Compliance
Managing controls through spreadsheets and emails is inefficient. Modern compliance and SaaS management platforms automate monitoring, centralize evidence, and simplify reporting. This means fewer manual errors, lower audit costs, and stronger assurance that ITGC testing and compliance are handled consistently throughout the year.
How CloudEagle.ai Helps With ITGC Compliance
Traditional ITGC audits are slowed by manual reviews, scattered documentation, and poor visibility. CloudEagle.ai solves these issues with automation, centralized governance, and AI-driven insights; helping enterprises achieve audit readiness in hours, not weeks.
Unlike legacy platforms that take months to deploy, CloudEagle.ai is fully operational in just 30 minutes. See how Rec Room was fully onboarded in just 30 minutes with CloudEagle.ai, proving that compliance and efficiency don’t have to wait.
Enterprises can start governing SaaS usage, improving compliance, and saving money right away. Let’s explore all these capabilities in detail:
1. Complete Access Discovery
CloudEagle.ai integrates with over 500 SaaS applications and identity providers to give enterprises full visibility into accounts, entitlements, and permissions. Hidden or abandoned accounts, which are a frequent cause of failed ITGC audits, are surfaced immediately.
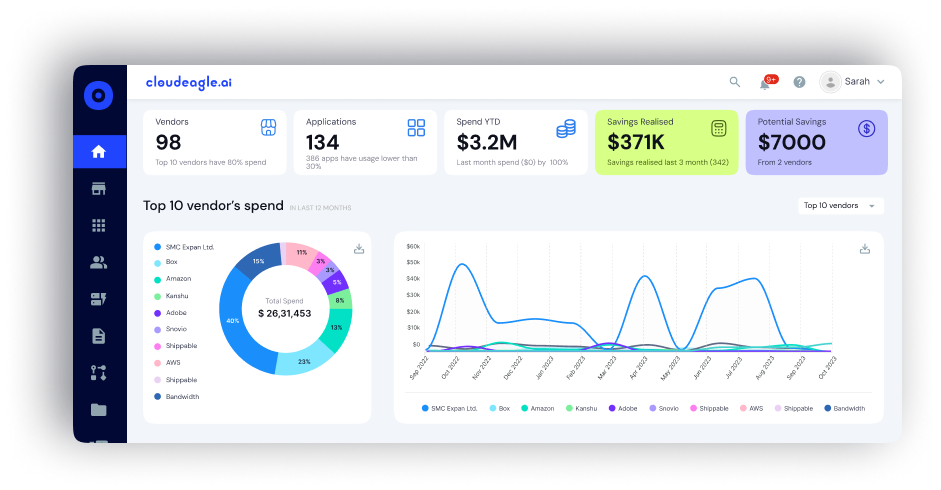
CIOs and CISOs no longer need to rely on fragmented reports; instead, they gain a single, consolidated dashboard that provides actionable insights on access governance across SaaS, AI apps, and IT systems. This visibility ensures compliance risks are detected before they escalate.
2. Automated User Access Reviews
These processes are slow, error-prone, and costly. CloudEagle.ai transforms this by automating the entire access review process. Within minutes, IT leaders can view role-based permissions, terminated employee accounts, and risky entitlements across the enterprise.

Customers have reported an 80% reduction in review time, shrinking cycles that once took weeks into hours. This not only reduces audit fatigue but also provides audit-ready reports on demand, cutting costs while improving accuracy.
Learn how Dezerv automated its app access review process with CloudEagle.ai, reducing manual work and strengthening compliance.
3. Continuous Monitoring and Alerts
Static, point-in-time audits leave enterprises vulnerable to ongoing risks. CloudEagle.ai enables continuous monitoring of user activity across SaaS and IT systems, detecting anomalies like ex-employees retaining access.
Real-time alerts allow IT and audit teams to close compliance gaps immediately, reducing fraud, insider risk, and regulatory exposure. In one case, a customer used the platform to deprovision 30+ ex-employees, optimize 75 apps, and save 1,354 hours annually.
4. Automated Onboarding and Offboarding
Employee lifecycle management is a critical ITGC domain, and manual onboarding/offboarding processes are error-prone and costly. CloudEagle.ai provisions all approved apps within 30 minutes of a new hire’s start date, ensuring productivity from day one.
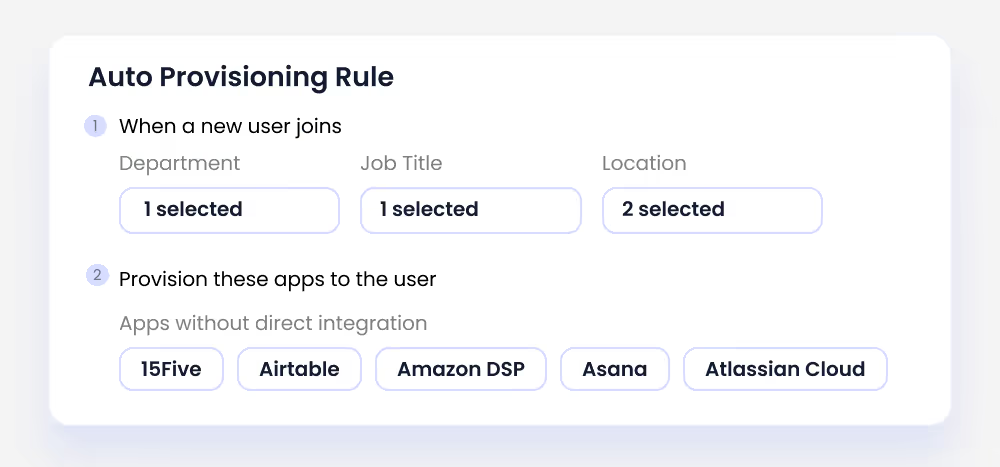
When employees leave, access is revoked, licenses are reclaimed, and costs are reduced automatically. By automating these workflows, CloudEagle.ai ensures no gaps exist between HR systems, IT operations, and compliance mandates.
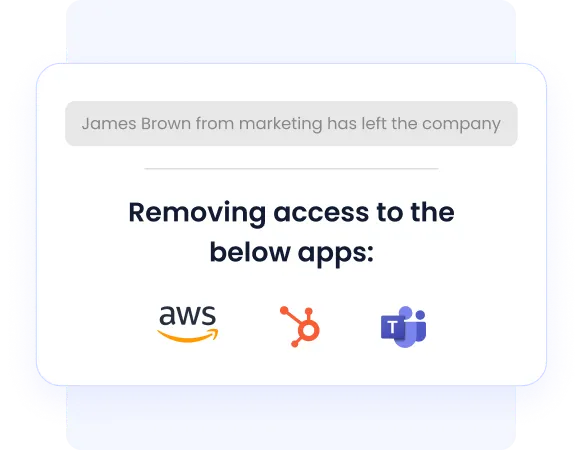
Know how JoVe streamlined employee onboarding and offboarding with CloudEagle.ai, saving countless hours while boosting productivity and compliance.
See how Alice Park from Remediant describes the impact of streamlining employee onboarding and offboarding with CloudEagle.ai. She explains how automation saved significant time while keeping their SaaS ecosystem secure.
5. AI-Powered Identity Governance (IGA)
Legacy IAM and IGA platforms are rigid and costly, often requiring additional enterprise add-ons like SAML. CloudEagle.ai’s Gen AI engine, Eagle Eye (Ai-powered ChatBot), modernizes identity governance by recommending least-privilege access, detecting redundant licenses, and enforcing time-based entitlements.
6. Just-in-Time (JIT) Access
In many enterprises, IT teams issue perpetual licenses for tasks that should only require temporary access. Even after the assignment ends, the access often stays active, leading to unnecessary license costs and compliance risks. According to CloudEagle.ai’s IGA report, only 10% of enterprises have implemented JIT controls.
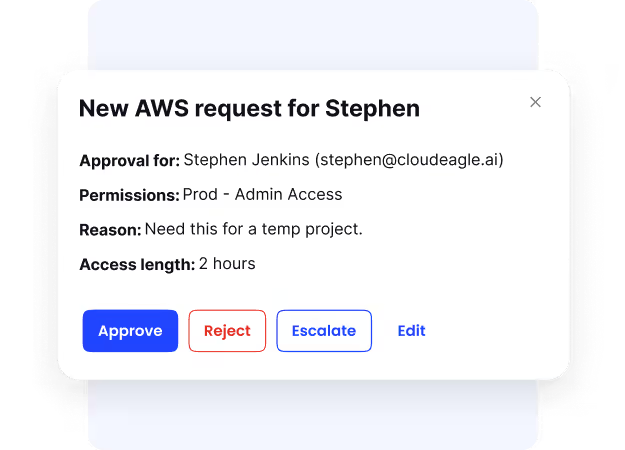
CloudEagle.ai solves this with just-in-time (JIT) access, granting elevated permissions only when needed and for a fixed duration. This eliminates permanent high-risk entitlements, reduces insider threats, and ensures that every privileged action is time-bound, traceable, and audit-ready by default.
7. Attribute-Based Access Control (ABAC)
CloudEagle.ai further enhances governance with attribute-based access control (ABAC). Policies can be applied dynamically based on user role, department, geography, or project context, ensuring employees receive only the access they truly need.
This fine-grained control helps global enterprises maintain compliance across diverse teams and jurisdictions. ABAC enforces least-privilege principles automatically, making ITGC audits smoother and more defensible.
8. Centralized Evidence and Audit Trails
In most enterprises, audit evidence is scattered across spreadsheets, email chains, and ticketing systems, making audits lengthy and painful. CloudEagle.ai consolidates policies, logs, and approvals into a centralized evidence repository.
This reduces the effort required to gather documentation, often cutting hundreds of hours from audit preparation. For CIOs and CISOs, this means less time chasing evidence and more time focusing on proactive compliance strategies.
Atul Tulshibagwale, Cloud Identity Pioneer, advises:
“Dynamic enforcement ensures every access decision is logged, justified, and auditable in real-time—this not only strengthens security but also transforms compliance management.”
9. Self-Service App Catalog
Uncontrolled app requests often lead to shadow IT and audit failures. CloudEagle.ai eliminates this with a governed self-service app catalog where employees can request approved apps. Approvals are routed through Slack or directly within the platform, ensuring every request follows proper chains of command.

Every transaction is logged automatically, creating audit-proof records that strengthen ITGC compliance. This balances productivity and governance, employees get faster access while IT teams retain full oversight.
Conclusion
An ITGC audit protects your systems, financial data, and reputation. It lowers risks, keeps you compliant, and builds trust with regulators and investors. In today’s fast-changing environment, strong ITGC controls are a must for every enterprise.
With CloudEagle.ai, audits become easier and faster. The platform automates access reviews, streamlines access management, and centralizes audit evidence. This means fewer surprises, lower costs, and continuous compliance all year long.
Are you ready to streamline your ITGC audit?
Schedule a demo with CloudEagle.ai and see how easily you can simplify ITGC compliance.
FAQs
1. What are the 4 domains of ITGC?
The four core domains are access controls, change management, backup and recovery, and IT operations. These areas cover who can access systems, how updates are managed, how data is protected, and how daily IT processes are monitored.
2. What is the scope of an ITGC audit?
The scope includes all systems and processes that affect financial reporting, compliance, and security. This often covers user access, system changes, data backup, IT monitoring, and sometimes vendor and third-party services.
3. What is the difference between ISO 27001 and ITGC?
ISO 27001 is a broad information security standard covering an organization’s entire security management system. ITGC audits, on the other hand, focus specifically on IT controls that support financial reporting and compliance with regulations like SOX or SOC 2.
4. What does ITGC mean in audit?
In audit, ITGC stands for IT General Controls. These are the basic IT policies and procedures that ensure systems are secure, reliable, and compliant. Without them, financial and compliance audits may not be trusted.
5. How are ITGCs tested?
Auditors test ITGCs by reviewing documentation, sampling transactions, and checking system logs. For example, they might verify if terminated employees lost system access on time, or test whether backups can be restored successfully.

%201.svg)








.avif)




.avif)
.avif)




.png)









