HIPAA Compliance Checklist for 2025

Think about how many tools your company uses daily: Salesforce, Slack, Google Workspace, Zoom, and more. Now imagine if a former employee still had access to these systems weeks after leaving. Scary, right?
You’re not alone. According to IBM’s 2024 Cost of a Data Breach Report, 19% of breaches were linked to compromised or mismanaged credentials.
A user access review checklist is your safeguard against such risks. It ensures every account, permission, and privilege is aligned with current roles and compliance needs. By following a structured checklist, you can detect orphaned accounts, prevent privilege creep, and stay audit-ready.
In this blog, we’ll cover why a user access review checklist matters, the challenges enterprises face, and a practical step-by-step guide you can adopt. We’ll also show how CloudEagle.ai makes the entire process easier and more efficient.
TL;DR
- User access reviews ensure only the right people have the right access at the right time.
- A structured user access review checklist helps prevent breaches and meet compliance requirements like SOX, HIPAA, and PCI DSS.
- Common challenges include orphaned accounts, excess privileges, and coordinating reviews across multiple apps.
- Following steps like defining scope, validating approvals, and documenting findings keeps audits smooth and risk-free.
- CloudEagle.ai automates access reviews with AI-driven insights, real-time monitoring, and compliance-ready reports.
What is User Access Review Checklist?
A user access review checklist is a structured, repeatable process for auditing user access across an organization’s systems, applications, and data. Its goal is to verify that every user holds only the permissions required for their role, aligning with the principle of least privilege.
This approach reduces the risk of unauthorized access, supports regulatory compliance, and strengthens accountability. The checklist typically includes steps such as identifying active and inactive accounts, validating access levels, monitoring logs for unusual activity, and recording all changes to maintain a clear audit trail.
Unlike a generic system review checklist, which examines system performance and compliance at a broader level, a user access review checklist specifically focuses on user accounts, roles, and privileges.
In short, the checklist is your blueprint for systematically reviewing who has access, validating approvals, and ensuring that your organization is aligned with regulatory compliance like SOX, HIPAA, and PCI DSS.
Why Are User Access Reviews Important for Enterprises?
User access reviews play a vital role in strengthening enterprise security, meeting compliance standards, and controlling costs. By ensuring employees only have the permissions needed for their roles, organizations can prevent data breaches, privilege creep, and misuse of resources.
According to a report from Check Point’s Cyberint research arm, compromised credentials increased by 160% in 2025 compared to 2024.
A well-structured user access review checklist goes far beyond a compliance exercise. It’s a proactive way to protect sensitive data, enforce least-privilege policies, and maintain full visibility over user activity across the enterprise.
Preventing Unauthorized Access to Critical Systems
Unauthorized access remains one of the leading causes of data breaches. If former employees, vendors, or contractors retain access to critical systems, they could expose your business to major risks. A structured user access review checklist ensures accounts are regularly validated.
- Ensuring ex-employees, contractors, or vendors no longer have active accounts.
- Validating that system privileges match current job roles.
- Identifying accounts with access to sensitive databases, CRMs, or financial systems.
- Use the user access review checklist to regularly disable or remove unnecessary accounts.
- Complementing broader governance tools, like a system review checklist, for added protection.
Reducing Insider Threats and Data Breach Risks
Not every threat comes from hackers. Sometimes employees, unintentionally or deliberately, become the source of a breach. That’s why insider threats are among the hardest to predict, making a user access review critical for detection and prevention.
- Monitoring for excessive privileges granted during temporary projects.
- Detecting dormant or rarely used accounts that could be exploited.
- Enforce the principle of least privilege from your identity and access management checklist.
- Preventing accidental or intentional misuse of sensitive data.
- Lowering the chances of costly insider-driven data breaches.
Meeting Compliance Standards Like SOX, HIPAA, and PCI DSS
Auditors expect to see evidence that your organization regularly reviews access. Regulatory standards like SOX, HIPAA, and PCI DSS mandate these reviews, and failing to comply can result in hefty penalties. That’s where a user access review checklist becomes indispensable.
- Meeting SOX requirements for strict control over financial reporting systems.
- Aligning with HIPAA standards to safeguard patient health records.
- Complying with PCI DSS to secure cardholder payment data.
- Providing documented audit trails to show regulators evidence of periodic reviews.
- Supporting security maturity frameworks like NIST and ISO through documented access control reviews.
Improving Visibility Into User Roles and Permissions
Roles evolve as employees switch departments, earn promotions, or move projects. Without structured checks, these role changes often leave employees with more access than they need. Regular user access reviews solve this by restoring visibility and alignment.
- Mapping employees’ current roles to their actual system permissions.
- Highlighting mismatches between job functions and assigned access rights.
- Allowing IT and managers to identify unused or risky privileges.
- Leveraging a system review checklist to cross-reference accounts across multiple platforms.
- Giving leadership confidence that the right people hold the right permissions.
What Are the Common Challenges in User Access Reviews?
Common challenges in user access reviews include slow, manual processes that are prone to human error and limited visibility across disconnected systems. Privilege creep, where users collect excessive privileges over time, is another frequent issue. Organizations also struggle with disengaged stakeholders, certification fatigue, and maintaining accurate access data.
“As the entry point to companies' infrastructure and consumers' most important data, identity is a critical pillar of security.” — Todd McKinnon, CEO & Co-Founder, Okta
Therefore, even with a detailed user access review checklist, enterprises face challenges when executing reviews at scale. Identifying risks, consolidating data, and balancing security with productivity are recurring pain points.
Identifying Orphaned Accounts and Excess Privileges
When employees leave or contractors finish projects, their accounts sometimes remain active. These orphaned accounts become ticking time bombs for attackers. A user access review checklist helps clean up these security gaps before they’re exploited.
- Detecting accounts that belong to departed employees or contractors.
- Reviewing temporary accounts created for projects or external partners.
- Removing privileges that linger after role changes.
- Aligning with the identity and access management checklist to catch hidden access points.
- Preventing attackers from exploiting forgotten accounts.
Managing Large Volumes of User Data
Enterprises deal with thousands of user identities across multiple platforms. Manually tracking them can be overwhelming and prone to human error. That’s why a system review checklist combined with automation is essential.
- Consolidating identity data across HR systems, SaaS apps, and cloud environments.
- Automating reporting to avoid manual spreadsheet errors.
- Prioritizing critical systems where risks are highest.
- Enabling IT teams to filter and flag unusual access activity.
- Making large-scale reviews practical and less overwhelming.
Coordinating Reviews Across Multiple Applications
With dozens of SaaS apps in use, consistency becomes a major challenge. Each platform has different access structures and approval workflows, making coordination complex. A repeatable user access review process solves this.
- Ensuring consistency of permissions across Salesforce, Slack, Microsoft 365, and others.
- Creating standardized workflows using an identity and access management checklist.
- Involving system owners and managers in the review process.
- Tracking approvals across multiple stakeholders without losing accountability.
- Using automation tools to reduce manual review fatigue.
Balancing Security With Employee Productivity
Overly strict reviews can frustrate employees, while too much leniency creates security risks. Finding the right balance is one of the hardest parts of a user access review checklist.
- Enforcing least-privilege access while ensuring employees can do their jobs.
- Avoiding “over-restriction” that slows down workflows.
- Reviewing access at logical intervals rather than over-policing.
- Consider user feedback when adjusting permissions.
- Using a system review checklist to find the sweet spot between productivity and security.
How Can Enterprises Build an Effective User Access Review Checklist?
To create an effective User Access Review (UAR) Checklist, start by clearly defining its scope and aligning it with organizational needs. Apply Role-Based Access Control (RBAC) and the principle of least privilege to ensure users only have the access they need. Involve key stakeholders, such as IT, managers, and HR, for accuracy and accountability.
Strengthen the process with automation and maintain thorough documentation and reporting. The checklist should confirm permissions match job roles and HR records, flag inactive or orphaned accounts, and validate privileged account access to minimize risk.
Here’s a step-by-step breakdown of how enterprises can implement an effective checklist:
Step 1: Define Scope and Access Review Objectives
Every successful review starts with clarity. If you don’t know what you’re reviewing and why, the process quickly spirals into busywork. That’s why this first step is about setting boundaries and goals.
- Identify which systems and applications will be included in the review (finance, HR, SaaS, cloud apps).
- Define the frequency of reviews (quarterly, biannually, or continuous monitoring).
- Align objectives with compliance requirements like SOX, HIPAA, or PCI DSS.
- Document risk priorities, for example, protecting financial records or customer data.
- Ensure your user access review checklist connects with broader governance efforts, like an identity and access management checklist.
Step 2: Identify All Active Users and Accounts
Once the scope is set, the next step is building a clean list of everyone who has access. This includes employees, contractors, and third-party vendors.
- Pull user data from HR systems, identity providers, and SaaS platforms.
- Cross-check active accounts against HR records to find mismatches.
- Don’t forget temporary project accounts and external vendor access.
- Use automation to reduce human error in compiling the list.
- This step bridges your user access review with your system review checklist to ensure nothing slips through.
Step 3: Review Roles, Permissions, and Access Levels
Now that you have a full inventory, it’s time to check whether permissions align with actual job roles. This is where most access creep hides.
- Evaluate if each user’s access is still relevant to their current responsibilities.
- Apply role-based access control (RBAC) or attribute-based access control (ABAC).
- Flag accounts with “admin” or “superuser” privileges for extra scrutiny.
- Check for employees with overlapping roles that may grant redundant access.
- Leverage your identity and access management checklist to ensure alignment with least-privilege principles.
Step 4: Detect Orphaned and Dormant Accounts
Inactive or orphaned accounts are ticking time bombs. They often remain unnoticed but can be exploited by attackers.
- Identify accounts belonging to employees or contractors who have left the company.
- Look for dormant accounts that haven’t logged in for weeks or months.
- Review accounts tied to former projects or test environments.
- Disable or delete accounts promptly to minimize attack surfaces.
- A recurring user access review checklist ensures these gaps don’t accumulate.
Step 5: Validate Approvals With Managers and Owners
Access shouldn’t be decided by IT alone; business managers must weigh in on whether employees still need access. This introduces accountability into the process.
- Send review requests to managers or system owners for each employee’s access.
- Require managers to confirm if access is still necessary for current projects.
- Track responses and follow up with non-responding managers.
- Ensure approvals are documented to satisfy audit requirements.
- By embedding this into your user access review checklist, you avoid blind IT-driven decisions.
Step 6: Remove or Adjust Excessive Privileges
Excessive privileges are one of the biggest drivers of insider threats. Employees often accumulate access they no longer need as they switch roles or projects.
- Downgrade permissions to match the employee’s current role.
- Remove admin or elevated access unless necessary.
- Use Just-in-time access where temporary privileges expire automatically.
- Document every adjustment to support compliance evidence.
- This ties back to your identity and access management checklist, ensuring least-privilege is enforced.
Step 7: Document Review Findings for Audit Readiness
If you can’t prove you performed a review, regulators will assume you didn’t. That’s why documentation is as important as the review itself.
- Log every action taken, including approvals, revocations, and role changes.
- Maintain time-stamped reports for audit readiness.
- Store documentation in a centralized, secure location for easy access.
- Use dashboards or reporting tools to generate compliance reports quickly.
- A thorough user access review checklist always ends with documentation, which also strengthens your system review checklist.
How CloudEagle.ai Can Simplify User Access Reviews
Manual user access reviews across dozens of SaaS applications can feel like a nightmare, with spreadsheets, email approvals, and endless reminders. The result? Delays, human errors, and compliance gaps.
This is where CloudEagle.ai becomes a game-changer. By combining automation, AI-driven insights, and seamless integrations, it transforms your user access review checklist into a streamlined, audit-ready process.
In fact, CloudEagle.ai was recently recognized in the 2024 Gartner Magic Quadrant for SaaS Management Platforms for its innovative AI/ML capabilities, reinforcing its position as a trusted leader in simplifying access governance.
Automating Access Reviews for Efficiency
Traditional reviews often involve manual tracking and endless back-and-forth emails. CloudEagle.ai eliminates inefficiencies by:
- Automating review cycles – Scheduled periodic access reviews without manual triggers.
- Automated approval workflows – Send managers timely reminders to validate or revoke access.
- Centralized dashboard – One view of all SaaS applications, users, and permissions.
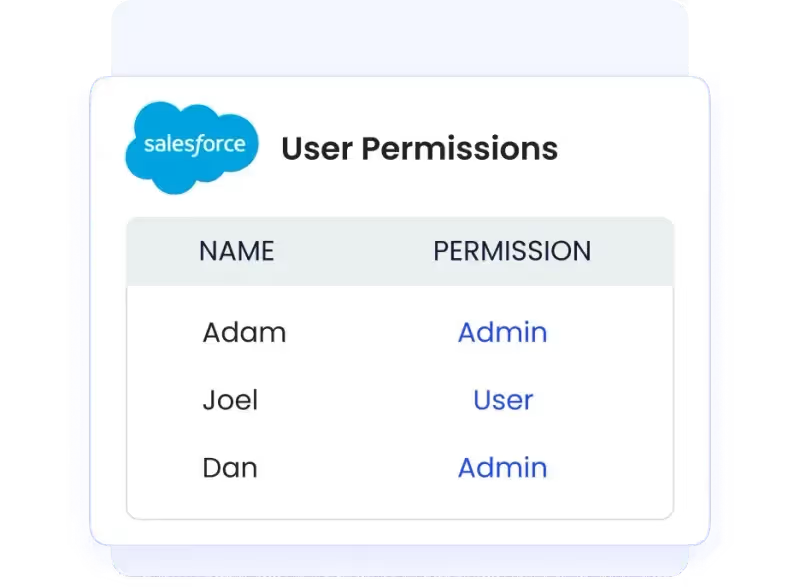
Automation ensures your user access review checklist is completed accurately and on time, reducing both administrative burden and risk.
AI-Driven Insights for Smarter Decisions
One of the biggest challenges in identity and access management checklists is spotting excessive permissions or unusual activity. CloudEagle.ai uses AI to:
- Detect anomalies in access patterns – Identifies accounts with risky, unnecessary, or duplicate access.
- Enforce least-privilege access – Recommends removing over-provisioned roles to strengthen security.
- Reduce insider threat exposure – Flags suspicious access requests before they escalate.

With these AI-powered insights, your system review checklist doesn’t just cover compliance; it proactively strengthens security.
Seamless SaaS Integrations & Real-Time Monitoring
With dozens of SaaS tools in use, visibility is often scattered. CloudEagle.ai integrates directly with leading applications like Slack, Google Workspace, Salesforce, and Microsoft Teams to:
- Monitor access in real time – Track changes as they happen.
- Automate permission revocation – Instantly adjust or revoke access when employees change roles or exit.
- Ensure continuous governance – Maintain ongoing oversight instead of relying on point-in-time reviews.
This makes your user access review checklist dynamic, reducing blind spots across multiple applications.
Compliance Enforcement Made Simple
Regulatory frameworks like SOX, HIPAA, and PCI DSS require strict user access reviews. CloudEagle.ai helps enterprises stay compliant by:
- Pre-configured compliance templates – Built-in alignment with industry regulations.
- Audit-ready reports – Instantly generate logs for auditors, cutting down preparation time.
- Automated evidence collection – No more scrambling for documentation during reviews.

By embedding compliance directly into workflows, CloudEagle.ai ensures your identity and access management checklist is always up to date and audit-ready.
Final Words
Conducting regular user access reviews is no longer optional; it’s a necessity. With SaaS adoption rising and compliance requirements tightening, enterprises need a reliable user access review checklist to ensure that only the right people have the right access at the right time.
By following a structured user access review checklist, enterprises can quickly identify orphaned accounts, minimize insider threats, and maintain visibility into user roles and permissions. Even with challenges like large data volumes or multi-app coordination, consistent reviews deliver lasting security and compliance benefits.
This is where CloudEagle.ai makes a difference. With automation, AI-driven insights, and real-time SaaS integrations, it transforms manual reviews into seamless, audit-ready workflows. Enterprises can save time, reduce risks, and confidently meet compliance demands, all from a centralized dashboard.
Book a free demo with CloudEagle.ai today and simplify your user access reviews.
Frequently Asked Questions
1. What is the purpose of an access review?
To ensure users have only the access they need, reducing risks of unauthorized use, insider threats, and compliance violations.
2. How to test user access review?
Test by sampling user accounts, verifying roles match job functions, checking approvals, and ensuring revoked accounts are deactivated.
3. Who should perform user access reviews?
Typically, IT admins and managers, with input from compliance officers, should review and approve user access across systems and apps.
4. How to automate user access review?
Use IAM or SaaS management tools like CloudEagle.ai that trigger review cycles, flag risky access, and generate audit-ready reports automatically.
5. How to audit user access?
Audit by documenting access rights, comparing them with role requirements, checking removal of excess privileges, and generating compliance logs.

%201.svg)








.avif)




.avif)
.avif)




.png)









