HIPAA Compliance Checklist for 2025

A clean report can lull teams while risk keeps moving. In 2024, the average breach cost reached $4.88M, and stolen credentials were the top initial action in breaches (24%), a costly reminder that point-in-time IT audits don’t equal ongoing safety.
This guide to IT audit management shows how to build a repeatable, defensible program that reduces findings and speeds remediation across the information technology audit process and IT compliance audit cycles.
We’ll cover the basics and why it matters; best practices (risk-led scope, sampling, evidence, controls); cloud/SaaS/vendor handling; automation with IT audit software; and the metrics that prove it’s working.
TL;DR
- IT audit management reduces repeat findings and speeds audits by turning one-off checks into a steady program tied to real risk.
- Best practices: scope from risk, inventory before evidence, reproducible sampling, clear evidence rules, prioritize identity/change/recovery, handle SaaS and vendors early, automate log-based tests.
- Run on cadence: quarterly privileged recerts, semi-annual sensitive, monthly restore tests, weekly POA&M. Track KPIs like on-time critical closures, unknown-asset rate, evidence rework, TTR revoke, and restore success.
- Make it practical: pre-mortems, scheduled evidence exports, treat SOC reports as tasks with owners, and link renewals to remediation.
- CloudEagle helps with unified SaaS inventory, access reviews, vendor SOC workflows, and scheduled exports so proof is ready when auditors ask.
What is IT Audit Management?
IT audit management is the program and governance layer that makes IT audits repeatable, defensible, and fast. Instead of a one-off IT audit, it runs year-round: planning the information technology audit process, setting evidence standards, designing sampling, coordinating testing, and driving remediation to closure with clear owners and deadlines.
A strong program aligns IT audit and compliance work (e.g., SOX, ITGC, GDPR, HIPAA) with business risk. It maintains an audit universe and control library, defines Evidence Acceptance Criteria, maps audit tests (design vs. operating effectiveness), and tracks issues through a living POA&M. It also connects the stack, such as CMDB, SIEM, IAM, ticketing, and IT audit software / IT auditing software, so evidence is collected once and reused.
Where it shows up daily:
- Assurance & compliance: supports external auditors and IT audit and assurance needs; coordinates SOC 2 audit services and other information technology audit services.
- Vendors: review SOC reports, implement CUECs, and tie results to procurement decisions.
- Operations: prioritizes identity, change, and recovery controls; measures KPIs to prove improvement.
Result: audits you can pass on purpose, not by surprise.
Why IT Audit Management Matters?
1) Breach costs make the business case
Global breach costs fell for the first time in five years, yet still average $4.44M while the U.S. hit a record $10.22M per incident. Programmatic IT audit management reduces exposure by tightening scope, controls, and evidence across every information technology audit process and IT compliance audit cycle.
2) Credentials + web apps are still the front door
In the 2025 Verizon DBIR, 88% of Basic Web Application Attacks involved stolen credentials; exploitation of vulnerabilities climbed to 20% as an initial access vector. Strong access reviews, patch governance, and defensible sampling are core IT audit and assurance priorities, not optional.
3) Third-party exposure doubled
Third-party involvement in breaches jumped from 15% to 30% year over year, underscoring why vendor SOC reviews, implementing CUECs, and continuous monitoring belong in IT audits (and your procurement playbook).
4) Hybrid/cloud sprawl costs more
Breaches touching multiple environments average $5.05M vs. $4.01M on-prem only. Cloud/SaaS scoping, shadow-IT discovery, and OAuth app reviews should be baseline in IT audit management, not afterthoughts.
5) Automation buys you time (and savings)
Organizations with fully deployed security AI/automation identified and contained breaches 77 days faster (247 vs. 324 days). Accelerated detection/containment helped drive the 2025 global cost decline, evidence that IT auditing software/IT audit software and log-level CAATs materially impact outcomes.
6) Compliance, trust, and revenue pressure
Regulatory fines and detection/escalation costs are a key reason U.S. breach costs rose to $10.22M. Mature IT audit management streamlines readiness for buyer demands (e.g., SOC 2 audit services, ISO 27001) and coordinates information technology audit services so audits help revenue instead of stalling it.
IT Audit Management Best Practices
1. Scope from risk, not framework
Start where impact lives: map crown-jewel data, the processes that move it, and every system (including SaaS) that touches it.
Let that risk picture set scope, timing, and tests, then freeze change rules so “one more control” shifts to the next IT audit. When it audit management leads with risk, the information technology audit process stays focused and faster.
2. Inventory before evidence
Proofs collapse without a trustworthy map. Run a short, intense inventory across endpoints, cloud, and SaaS: owners, usage, data classes, and residency.
Retire duplicates and stale access first; collect evidence second. Your IT audit stops being scavenger hunts, and IT compliance audit requests become routine exports. If you already track app/owner/usage centrally, the IT audit management software can surface a clean export you attach to your audit pack.
3. Sampling you can defend
Ad-hoc picks invite debates.
Define the population, choose statistical or judgmental sampling on purpose, and record the method, seed, and size so another auditor could reproduce it. Reproducible sampling shortens reviews in any IT audit and assurance engagement.
4. Evidence acceptance criteria, upfront
Publish what “good evidence” means before testing begins: source-of-truth exports over screenshots, required timestamps and approvers, redaction standards, chain-of-custody, and immutable storage.
Schedule recurring pulls with IT audit software/IT auditing software so you collect once and reuse across cycles.
5. Prioritize IAM, change, recovery
Most costly incidents begin with access and end with fragile recovery.
Tighten join/move/leave, enforce SoD/PAM where needed, make ticket → commit → deploy traceable, and prove backup-to-restore monthly. Do these well, and repeat findings drop across the information technology audit process.
6. Tame cloud/SaaS early
In week one, sweep SSO/CASB/expense data for shadow apps, review OAuth scopes, confirm data location, assign owners, and add apps to a risk-tiered recertification cadence.
Modern IT auditing treats this as table stakes, not a late add.
7. Treat vendor SOC reports like code
A SOC 2 isn’t a PDF to file; it’s a to-do list. Parse complementary user entity controls, translate them into your tasks, track them to closure, and link results to renewals.
That discipline is what buyers expect when they ask for SOC 2 audit services or other information technology audit services. Teams storing vendor profiles and SOC reports in CloudEagle often wire CUECs into renewal workflows to ensure they’re implemented before contracts roll.
8. Automate 100% where logs exist
If logs exist, stop hand-sampling.
Use CAATs to continuously test privileged changes, join/move/leave events, sensitive-data access, and restore outcomes; schedule exports into your IT audit software. Automation turns periodic IT audits into continuous assurance.
9. Pre-mortem tabletop per domain
Before auditors call, run a 60–90-minute dry-run with control owners.
Tell the story, open the consoles, pull the evidence live, and capture every wobble. Fixing gaps now is cheap; discovering them in interviews is not.
10. Close the loop like ops
Findings shouldn’t live in spreadsheets. Track each issue in a living POA&M with owners, due dates, and expiring risk acceptances.
Review progress weekly and watch a few sharp KPIs on-time critical closures, time-to-revoke access, repeat-finding rate to steer the next IT audit management cycl, and keep IT audit and compliance predictable.
Metrics, Cadence, Ownership
Metrics that prove it’s working
Track a handful of sharp KPIs and wire them to your IT audit management dashboard (pulling from HRIS, SSO/IAM, CMDB/SaaS inventory, backup tools, ticketing, and your IT audit software).
1. % Critical findings closed on time
It includes the share of P1/P2 issues closed by the due date.
Formula: closed on/before due ÷ total critical × 100.
Target: ≥90% (quarterly).
Why: Shows the information technology audit process drives real risk reduction.
2. Unknown-asset rate
Assets/apps seen in logs but not in your inventory.
Formula: unknown items ÷ total items × 100.
Target: ≤5%.
Why: Lowers surprises during IT audits and evidence collection.
3. Evidence rework rate
It covers the evidence rejected for format/timestamp/source issues.
Formula: reworked items ÷ total submitted × 100.
Target: ≤10%.
Why: Tests whether Evidence Acceptance Criteria are understood and your IT auditing software automation is paying off.
4. Time-to-revoke (TTR) access
It includes hours from HR termination (or role change) to access removal.
Target: ≤24h for standard; ≤4h for privileged.
Why: Directly reduces breach blast radius.
5. Restore success & RTO/RPO attainment
Successful restores / total restore tests; % meeting RTO/RPO.
Target: ≥99% success; 100% within RTO/RPO.
Why: “Backups succeeded” proves recoverability.
6. Repeat finding rate
Findings that recur across cycles.
Formula: repeats ÷ total findings × 100.
Target: ↓ quarter-over-quarter; aim <10%.
Why: Measures whether fixes stick.
7. Automation coverage
Controls with automated evidence or continuous testing.
Target: 40%+ in year one, 60%+ as the program matures.
Why: Converts periodic IT compliance audit prep into continuous assurance.
Cadence (time-boxed and event-driven)
- Access recertifications: privileged quarterly; sensitive semi-annual; low-risk annual (close each wave within 15 business days).
- Restore tests: monthly for critical systems/SaaS; quarterly for the rest (log artifacts and runbooks).POA&M reviews: weekly stand-ups until all critical items close; monthly exec read-out.
- Shadow-IT sweep: quarterly (SSO logs, CASB, expense data).
- Sampling plans & Evidence Acceptance Criteria: refresh each audit cycle and after any major tooling change.
- Event triggers (immediate): M&A, new critical SaaS go-live, P1 incident, material org or role changes.
Ownership & RACI (keep it simple)
- Executive Sponsor (CIO/CISO/CFO): Accountable: approves scope, risk acceptance, and timelines.
- Audit Lead / Compliance Manager: Responsible: runs the information technology audit process, sets Evidence Acceptance Criteria, designs sampling, coordinates testing, tracks POA&M.
- Control Owners (IT, SecOps, Eng, App Owners): Responsible: operate controls, produce evidence, remediate findings.
- Process Partners (HR, Finance/Procurement, Legal, Privacy): Consulted/Responsible where applicable: JML events, vendor diligence/SOC reviews, contractual and regulatory constraints.
- Systems Owners (IAM/SSO, CMDB/Asset, Backup/DR, SIEM, Ticketing, GRC/IT audit software): Responsible: data accuracy, scheduled exports, and immutable evidence stores.
- External Auditors/Assessors: Consulted: scoping clarifications, testing approach, and evidence sufficiency; Informed on remediation progress.
Practical tip: tie governance to spend, e.g., Procurement won’t renew a high-risk vendor until related POA&M items or CUECs are closed (a control you can implement with your vendor and SaaS management tooling when needed).
Quick-Start Checklist (One Sprint)
1. Map the top 10 business risks & data flows
Run a 60-minute workshop with process owners; diagram data flows (incl. SaaS) and tag crown-jewel data.
Output: risk register + data-flow maps for IT audit management.
2. Freeze scope guardrails
Document in-scope systems, controls, sampling depth, and a change-control rule (“new asks roll to next cycle”).
Output: 1-page scope charter signed by sponsor/audit lead.
3. Run a shadow-IT sweep
Pull SSO/CASB/expense logs; assign owners, retire or onboard apps.
Output: app/owner/usage list used in IT audits.
4. Publish Evidence Acceptance Criteria
Define source-of-truth exports, timestamp/approver, redaction, and immutable storage.
Output: EAC one-pager + evidence folder skeleton in your IT audit software.
5. Define sampling plans
State population, method (statistical/judgmental), size, and seed.
Output: sampling appendix reproducible by another auditor.
6. Tier access recerts; schedule restore tests
Privileged (Q), sensitive (S/A), low (A); book monthly restore drills with proof.
Output: recert calendar + restore tickets and artifacts.
7. Parse vendor SOC CUECs → controls
Extract CUECs from key vendors; create tasks and link to renewals.
Output: CUEC tracker with owners/ETAs for IT compliance audit.
8. Turn on CAATs for two controls
Start with JML and privileged-change logs; schedule exports to your IT auditing software.
Output: automated evidence feeds.
9. Stand up POA&M with SLAs
Track findings with owners/dates; set P1/P2 closure SLAs; hold a weekly stand-up.
Output: live POA&M dashboard.
10. Book pre-mortems per domain
60-90-minute dry runs to walk narratives and pull evidence live; log gaps and fixes.
Output: an action list that de-risks the information technology audit process.
How CloudEagle helps with IT audits
Audits slow down when you can’t see every SaaS app, who has access, or what vendors promised. CloudEagle smooths those rough spots so evidence is ready and reviews finish on time.
- See your SaaS footprint. It discovers apps from SSO and expense data, shows the owner, users, and where data sits, so scoping and shadow-IT cleanup are straightforward.
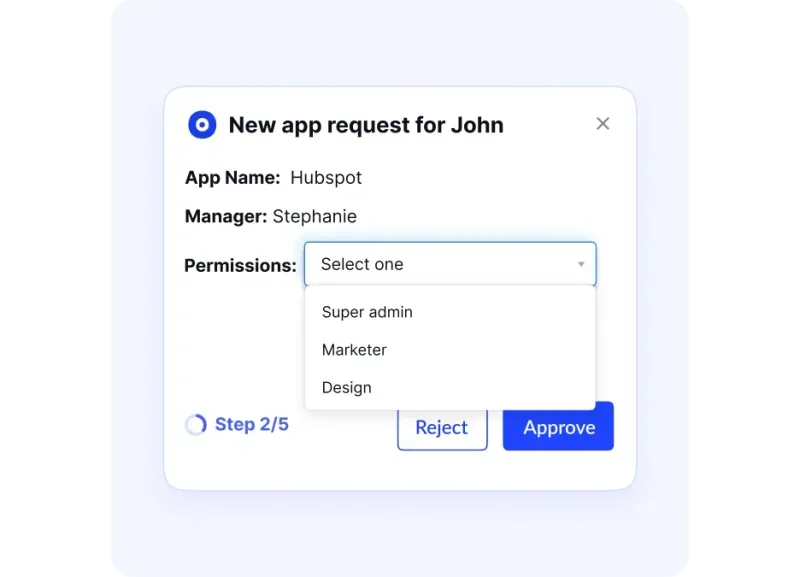
- Run access reviews on time. Set risk-based recertifications (quarterly/semi-annual/annual). Owners approve in email/Slack, stale and privileged access gets cleaned up, and a clear trail is kept.

- Keep vendor promises. Store SOC/ISO reports in one place, turn CUECs into tasks with owners and dates, and link them to renewals; renew only when the gaps are closed.
- Have proof ready, not last-minute. Schedule exports (app lists, user access, admin changes) to your GRC or IT audit tool, so evidence arrives in the right format on a set cadence.
- Remove risky OAuth scopes. See which apps have broad permissions, flag high-risk grants, and nudge owners to tighten them.
- Close findings, don’t carry them. Track each item with an owner and due date, send reminders, and show progress; you can even hold renewals until fixes are done.
- Right-size licenses. Spot inactive seats, reclaim or downgrade, and remove matching access so cost and risk go down together.

- Keep recovery proof handy. Attach restore logs and checklists to apps and set reminders, making recoverability easy to show.
- Works with your stack. Connects to SSO/IAM, HRIS, ticketing, finance, and major SaaS apps with role-based access and activity logs for control and traceability.
When Dezerv’s IT team struggled with slow, spreadsheet-based access reviews, CloudEagle centralized the process across Slack, Microsoft 365, and Snowflake. Within the first review cycle, they cut unnecessary accounts, improved compliance confidence, and now run smooth monthly reviews.

Stay Audit Ready with CloudEagle
You now have a playbook: risk-first scope, clean inventory, defensible sampling, clear evidence rules, and tight metrics. Use it to run calmer, faster audits across SaaS, vendors, and cloud.
When visibility, access reviews, or vendor tasks slow progress, CloudEagle.ai centralizes apps, automates reviews and exports, and gates renewals on fixes. Book a demo to see audit-ready workflows in action.
FAQs
1. What is an IT audit?
An IT audit is a structured review of technology systems, processes, and controls to verify security, availability, integrity, and compliance. It tests control design and operation, documents gaps, and recommends fixes to reduce risk.
2. What is an example of an IT audit?
Example: an access management audit of cloud and SaaS. The auditor checks MFA, least-privilege roles, join/move/leave workflows, admin logs, and separation of duties, samples users, and verifies timely revokes and approvals.
3. What are the different types of IT audits?
Types: compliance (e.g., SOC 2, ISO 27001), ITGC/controls, security, operational, application/system, SDLC/change, privacy/data protection, cloud/SaaS, and third-party/vendor audits.
4. What is the role of the IT auditor?
The IT auditor defines scope, assesses risk, designs tests, samples data, and evaluates whether controls are designed and operating effectively. They report findings, confirm remediation, and remain independent and evidence-driven.
5. What are the 4 phases of IT audit?
Four phases:
1) Planning and risk scoping,
2) Fieldwork and testing,
3) Reporting and management response,
4) Follow-up to verify remediation and close findings.
.avif)
%201.svg)







.avif)




.avif)
.avif)




.png)









