HIPAA Compliance Checklist for 2025

In 2025, over 60% of data breaches stem from mismanaged access and identity gaps, highlighting how critical Identity and Access Management challenges have become for modern enterprises. Managing user identities, permissions, and secure access is no longer optional; it’s a business imperative.
Identity and access management is the framework that defines how users interact with applications, platforms, and data.
Yet, despite its importance, many companies fail to implement it effectively. The result is increased security risks, compliance gaps, and operational inefficiencies that can cost millions.
In this blog, you will get to know the most pressing identity and access management challenges, why they exist, and actionable strategies to overcome them. We’ll also explore how solutions like CloudEagle.ai can secure your organization while maintaining a seamless user experience.
TL;DR
- Identity and access management ensures that the right users have secure access to the right applications, platforms, and sensitive data.
- Organizations face challenges such as inefficient onboarding/offboarding, mismanaged privileged access, unauthorized shadow IT, and multi-device access complexity.
- Implementing strong authentication methods, role-based access controls, and centralized policies helps reduce security risks and maintain regulatory compliance.
- Best practices like automating user provisioning, using MFA/SSO, performing regular access reviews, and leveraging analytics help detect anomalies and improve IAM efficiency.
- CloudEagle.ai offers full visibility across SaaS and cloud apps, automates access management, maintains audit-ready logs, and simplifies compliance for enterprises.
What is Identity and Access Management (IAM)?
Identity and Access Management (IAM) helps organizations manage digital identities and control access to resources. It tackles identity and access management challenges by ensuring the right people or systems have secure access.
Identity and access management centralizes authentication, authorization, and governance, reducing security risks and supporting regulatory compliance. Modern IAM solutions and identity and access management tools manage access across devices, platforms, and cloud services.
Implementing robust identity and access management solutions or IAM tools allows organizations to:
- Provision and deprovision users efficiently across multiple systems and cloud applications, ensuring new employees and departing staff have appropriate access.
- Enforce strong authentication methods, including multi-factor authentication (MFA), single sign-on (SSO), and passwordless access to secure user credentials.
- Manage privileged access securely, protecting critical systems and databases from insider threats or unauthorized access.
- Centralize and automate access policies across hybrid environments, including on-premises infrastructure and cloud services.
- Ensure compliance with regulations such as HIPAA, SOX, and GDPR, with audit-ready visibility into access systems and user activity.
- Detect anomalies and security risks in real-time, leveraging analytics and reporting to proactively address potential threats.
Why Do IAM Challenges Exist?
Managing user identities and access has never been more complex. Organizations face a range of challenges that affect secure access, compliance, and operational efficiency.
“Ensuring that every user’s identity is properly managed, protected, and secured is one of the most crucial tasks of any modern organization.”
— Paul Martini, CEO of iboss
Organizations face growing identity and access management challenges as they scale. In fact, a recent report found that over 80% of security breaches involve compromised credentials, showing how critical robust IAM is.
Increasing SaaS and Cloud Adoption
The rapid adoption of SaaS applications and cloud services introduces new identity and access management challenges. Managing user identities and access rights across multiple platforms increases security risks if proper IAM solutions or identity and access management tools are not in place.
Expanding Remote and Hybrid Workforces
Remote and hybrid work models mean employees access corporate resources from various devices and locations. Ensuring secure access for all user identities while maintaining a smooth user experience is a key identity and access management challenge.
Complexity of Multi-Device and Multi-Network Access
Users now connect from multiple devices, networks, and cloud platforms, making identity and access management more complex. Enforcing consistent access controls and monitoring user credentials is critical to reduce security risks.
Rising Cybersecurity Threats and Insider Risks
With increasing cyber threats and potential insider threats, protecting sensitive data is more challenging than ever. Strong authentication, MFA, and monitoring of user identities are essential components of modern IAM solutions.
Pressure from Compliance and Audit Standards
Organizations face strict regulations like HIPAA and SOX, requiring clear access management systems and audit trails. Identity and access management tools help ensure regulatory compliance and reduce the risk of failing audits.
Top Identity and Access Management Challenges
Managing user identities and access has never been more complex. Organizations face a range of identity and access management challenges that affect secure access, compliance, and operational efficiency. In this section, we’ll break down the top IAM challenges and explain why they matter.
1. Onboarding and Offboarding Users Efficiently
Efficient onboarding and offboarding of new employees is a cornerstone of modern identity and access management. Poor processes can leave user credentials exposed and create security risks.
Key Points:
- Delays in revoking access can lead to unauthorized access.
- Manual processes reduce operational efficiency for IT teams.
- Incomplete tracking can result in compliance issues and failed audits.
Automating user provisioning and deprovisioning ensures secure access, reduces identity and access management challenges, and improves IAM systems' efficiency. Also, in 2025, over 60% of data breaches stem from mismanaged access and identity gaps.
2. Managing Privileged Access Securely
Privileged access management is critical for protecting critical resources. Mismanagement can create significant security risks.
Key Points:
- Users may accumulate unnecessary privileges over time (privilege creep).
- Lack of monitoring of critical resources can allow insider threats.
- Balancing security with productivity is complex.
Research shows that 80% of cyberattacks use identity-based attack methods,” highlighting the importance of securing privileged access.
Proper IAM solutions and tools help organizations monitor privileged accounts, enforce access controls, and protect sensitive data.
3. Preventing Shadow IT and Unauthorized Apps
Employees often adopt unauthorized SaaS applications, creating hidden security risks and fragmented data. These hidden tools are one of the fastest-growing identity and access management challenges for modern organizations.
Key Points:
- Unauthorized apps can store sensitive information outside secure platforms.
- Lack of visibility into apps reduces compliance visibility.
- Shadow IT increases the risk of regulatory non-compliance.
Monitoring and integrating all SaaS applications within IAM systems ensures consistent permissions and strengthens identity management.
4. Enforcing Strong Authentication Methods
Strong authentication safeguards user credentials and prevents unauthorized access. Implementing robust methods is a key part of tackling today’s identity and access management challenges.
Key Points:
- Employees may resist multi-factor authentication (MFA) or single sign-on (SSO).
- Legacy systems may not support modern IAM tools.
- Advanced authentication can be resource-intensive to deploy.
It is also proven that organizations using modern authentication reduce account takeover risk by up to 90%. Modern identity and access management solutions support MFA, SSO, and passwordless authentication to strengthen secure access without compromising user experience.
5. Maintaining Role-Based Access Controls at Scale
Scaling role-based access control (RBAC) is complex in large organizations, especially across multiple platforms and devices.
Key Points:
- Role explosion can make access management cumbersome.
- Inconsistent roles create security gaps.
- Auditing large user bases is difficult for IT teams.
Maintaining consistent access rights and regular role audits enhances IAM system capabilities and reduces identity and access management challenges.
6. Ensuring Visibility Across All SaaS Applications
With growing adoption of cloud-based IAM solutions, maintaining visibility across all SaaS applications is essential for security and compliance.
Key Points:
- Fragmented data reduces audit readiness.
- Users may have inconsistent access rights across cloud services.
- Monitoring every platform and application increases IAM complexity.
Studies indicate that 61% of organizations lack complete visibility into all SaaS applications, emphasizing the need for centralized monitoring and strong identity and access management capabilities.
Centralized monitoring of all user identities across platforms helps improve compliance visibility and strengthens identity management capabilities.
7. Balancing Security With User Experience
Striking the right balance between security and user experience is a persistent IAM challenge.
Key Points:
- Overly strict protocols frustrate end users.
- Users may bypass access controls if processes are cumbersome.
- Low adoption of IAM tools can reduce overall security effectiveness.
Designing IAM systems with user experience in mind ensures compliance, enhances productivity, and strengthens secure access across the organization.
Best Practices to Overcome IAM Challenges
Overcoming identity and access management challenges means using the right strategies. These best practices improve security, compliance, and user experience while maximizing identity and access management benefits.
1. Automating User Provisioning and Deprovisioning
Manual provisioning slows down IT teams and often leaves behind orphaned accounts that create security risks. Automation ensures new employees get the right access rights instantly, while departing staff lose access just as quickly.
- Speed up onboarding with IAM tools and connectors.
- Reduce errors and unauthorized access by eliminating manual steps.
- Improve compliance by maintaining an accurate user store in real time.
2. Implementing Multi-Factor and Passwordless Authentication
Strong authentication remains one of the most effective defenses against unauthorized access. Multi-factor authentication (MFA) and passwordless methods reduce dependence on weak or reused passwords.
- Add layers of security with MFA, biometrics, or SSO-based verification.
- Leverage single sign-on (SSO) for ease of use while improving secure access.
- Reduce friction for end users by adopting adaptive or contextual authentication.
3. Regular Access Reviews and Certifications
Over time, user identities accumulate excess permissions, making it difficult to enforce least privilege principles. Conducting regular reviews is critical for tightening access controls and ensuring compliance with industry regulations.
- Schedule quarterly or annual access certifications.
- Involve vendors, department heads, and security professionals in the process.
- Align reviews with SOX, HIPAA, or other regulatory requirements.
4. Integrating IAM With HRIS and Finance Systems
Disconnected IAM systems often fail to reflect real-time changes in workforce roles. Integrating IAM with HRIS and finance systems ensures that access aligns with employment and budget data.
- Sync HR records to update user identities instantly.
- Revoke access when an employee changes departments or exits.
- Provide IT teams and finance departments with full visibility into license usage.
5. Centralizing Access Policies for Hybrid Environments
With cloud applications, on-prem infrastructure, and BYOD (bring your own device) policies, fragmented policies create gaps. Centralizing rules improves compliance visibility and ensures uniform security.
- Apply consistent role-based access control (RBAC) across all environments.
- Use cloud-based IAM platforms to enforce rules across hybrid systems.
- Extend secure access to critical resources, databases, and SaaS apps.
6. Using Analytics to Detect Anomalies and Risks
Traditional access logs are no longer enough. Analytics-powered IAM solutions enable continuous monitoring and anomaly detection to flag unauthorized access in real time.
- Detect irregular login attempts, privilege escalations, or shadow IT usage.
- Combine analytics with privileged access management for deeper insights.
- Use AI-driven IAM tools to adapt policies dynamically.
How CloudEagle.ai Simplifies IAM for Enterprises
Most enterprises today rely on identity providers (like Okta, Azure AD, or SailPoint) to manage access to applications. These tools do their job well for the apps they know about.
But that’s the problem.
IAM tools were never designed for a world where:
- Employees sign up for tools on their own
- AI apps bypass SSO entirely
- Contractors retain access long after projects end
- Compliance teams scramble for audit data spread across emails and spreadsheets
This is where CloudEagle.ai comes in.
Discover and Monitor All SaaS and AI Tools in Use
CloudEagle.ai delivers comprehensive application visibility across your entire software environment, including unsanctioned apps.
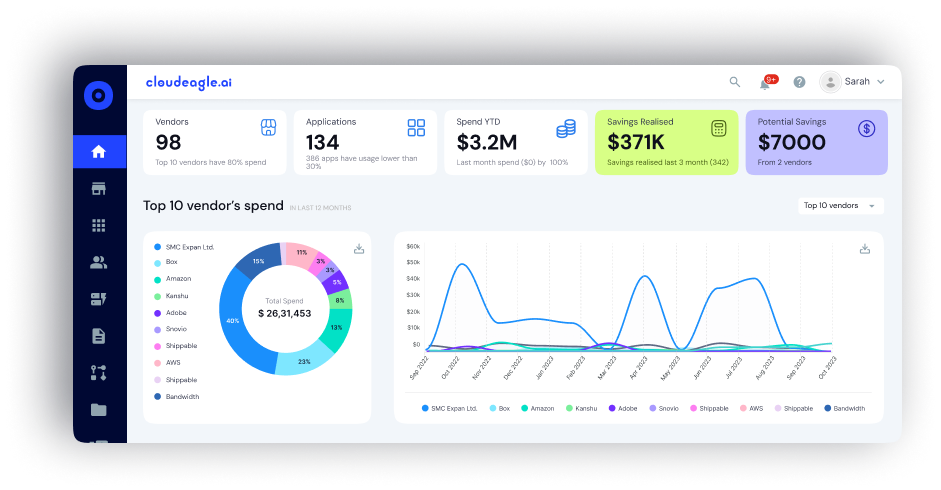
- Automatically detects all SaaS and AI tools, including those outside of SSO or IDP coverage
- Uses login, card data, and browser signals to uncover shadow IT
- Flag high-risk or redundant tools before they become liabilities
Automate Employee Onboarding and Offboarding Across Apps
Manual access management slows productivity and increases risk. CloudEagle.ai replaces this with automated, role-based provisioning and deprovisioning.

- Assigns access to apps based on department, role, or location
- Auto-deprovisioning access across all tools, even those not connected to your identity provider
- Maintains a full record of every access action for compliance
Read this inspiring success story of how JoVe streamlined employee onboarding and offboarding with CloudEagle.ai.
Enable Real-Time Access Reviews and Governance
Access reviews shouldn't be a quarterly scramble. CloudEagle.ai makes them continuous, intelligent, and auditable.

- Monitors access levels continuously and flags anomalies
- Identifies overprivileged users and role mismatches
- Reduces manual review effort and shortens audit preparation timelines
Control Temporary and Just-in-Time Access for Contractors
Many organizations struggle to manage access for contractors and temporary staff. CloudEagle.ai enforces least-privilege policies without adding complexity.
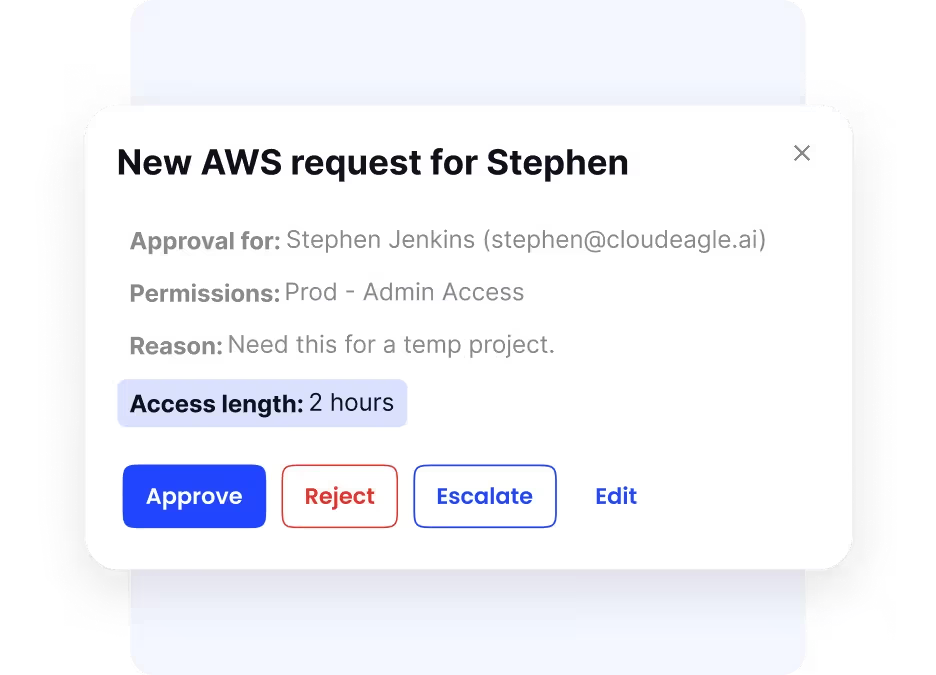
- Assigns time-bound access that expires automatically
- Supports just-in-time provisioning for sensitive tools
- Reduces the risk of forgotten or lingering access
Maintain Centralized, Compliance-Ready Audit Logs
Preparing for audits is challenging when access data is scattered. CloudEagle.ai centralizes and automates audit logging.
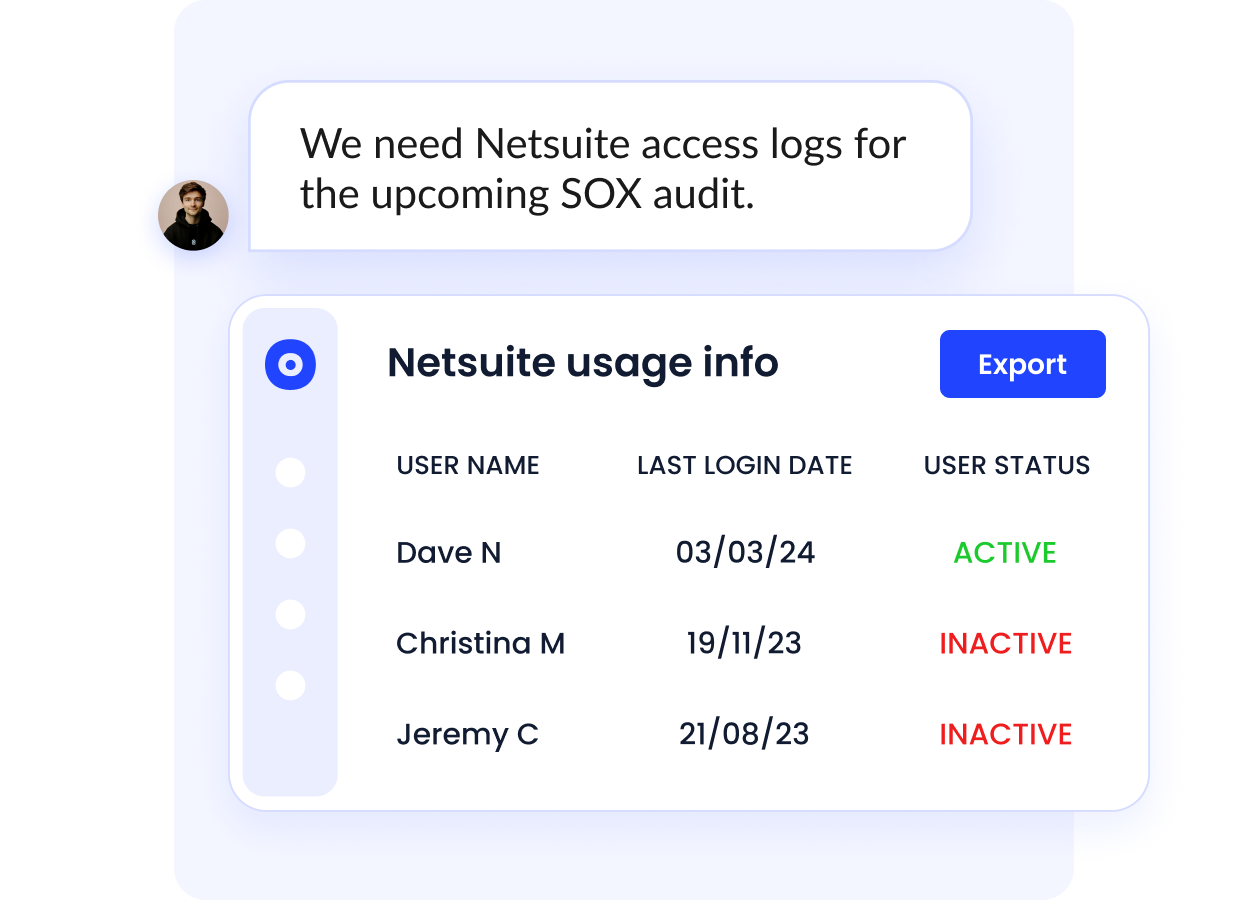
- Captures every access change, approval, and deprovisioning event
- Provides exportable reports for SOC2, ISO, GDPR, and other frameworks
- Simplifies compliance and reduces audit risk
Identify and Eliminate License Waste
SaaS overspend is often hidden in unused or low usage licenses. CloudEagle.ai identifies and reclaims them automatically.

- Tracks actual feature-level usage across all apps
- Highlights inactive users and unused licenses
- Automates license reclamation and helps optimize renewals
What You Can Achieve with CloudEagle.ai
By embedding IAM into your broader SaaS management workflows, CloudEagle.ai helps you:
- Accelerate access review cycles by 80%
- Save up to 30% by eliminating duplicate and low usage licenses
- Maintain audit-ready records for regulatory frameworks like SOC2, ISO, and GDPR
- Reduce insider risk with smarter offboarding and access control
- Improve IT productivity by automating repetitive IAM tasks
Final Thoughts
Identity and access management challenges grow with SaaS adoption, hybrid work, and multi-device access. Effective identity and access management solutions protect data, enforce access controls, and ensure compliance.
Following best practices like automated provisioning, MFA, and centralized policies reduces security risks and enhances identity and access management benefits.
CloudEagle.ai simplifies identity and access management with full visibility across all SaaS and cloud apps. It automates onboarding and offboarding, enforces role-based access, and monitors user identities. Centralized audit logs ensure compliance and reduce security risks.
Book a free demo because CloudEagle.ai secures access and solves IAM challenges effortlessly.
Frequently Asked Questions
- What are the four pillars of IAM?
The four pillars of IAM are Identification, Authentication, Authorization, and Auditing, ensuring secure and compliant access to systems and data. - What are the 4 components of IAM?
IAM components include User Management, Access Management, Directory Services, and Policy Enforcement to control digital identities and permissions. - What is an example of IAM?
An example of IAM is Single Sign-On (SSO) with multi-factor authentication, allowing users secure access to multiple apps with one set of credentials. - What is the main goal of IAM?
The main goal of IAM is to ensure the right individuals have secure access to the right resources at the right time, reducing security risks. - What is the difference between IAM and identity management?
Identity management focuses on creating and managing user identities, while IAM also includes authentication, authorization, and access control across systems.

%201.svg)









.avif)




.avif)
.avif)




.png)









