HIPAA Compliance Checklist for 2025

In today’s digital-first world, customer trust depends on data security. For SaaS and cloud-based enterprises, SOC 2 certification has become a must-have; a clear signal to customers and partners that you can safeguard sensitive information.
Over 66% of B2B buyers report they require SOC 2 certification before signing contracts with a SaaS vendor, making it a mandatory business enabler.
Without it, organizations risk losing deals, falling behind competitors, and raising compliance concerns. Yet, the certification path often feels overwhelming: What does the audit include? How do SOC 2 Type 1 and Type 2 differ? What policies, controls, and documentation are required—and how much will it cost?
This guide simplifies the process into clear, actionable steps. You’ll learn what auditors look for, how to prepare for certification, and how to maintain compliance year after year without unnecessary stress.
TL;DR
- SOC 2 certification proves your SaaS or cloud company meets strict security, privacy, and compliance standards.
- To get certified, define the scope, run a readiness assessment, implement policies/controls, fix gaps, and complete an independent audit.
- SOC 2 Type 1 checks controls at a single point in time, while SOC 2 Type 2 validates effectiveness over 3–12 months.
- The process takes 3–12 months and costs $20K–$80K, depending on company size, audit scope, and firm.
- Certification builds customer trust, reduces risks, and unlocks enterprise deals that often require SOC 2 compliance.
What is SOC 2 Certification?
SOC 2 (Service Organization Control 2) is a compliance framework developed by the AICPA (American Institute of Certified Public Accountants). It focuses on how enterprises protect customer data in the cloud.
Unlike SOC 1, which relates to financial reporting, SOC 2 certification evaluates your security and data management practices across five key trust principles:
- Security: Protecting systems and data from unauthorized access.
- Availability: Ensuring systems remain available and reliable.
- Processing Integrity: Guaranteeing data is accurate and complete.
- Confidentiality: Safeguarding sensitive information.
- Privacy: Protecting personally identifiable information (PII).
Getting a SOC 2 certificate means your organization’s security and compliance practices have been independently audited and verified.
For SaaS, cloud, and IT enterprises, it’s now an industry baseline. Many customers won’t sign a contract unless you’re SOC 2 certified.
According to a recent 2025 survey by ISMS.online, companies that achieve SOC 2 compliance report a significant improvement in customer trust and faster contract closures.
What is SOC 2 Type 2 Certification?
The AICPA emphasizes that SOC 2 Type 2 certification assures that controls are not only in place but have been proven effective over time.
When learning how to get SOC 2 certification, you’ll often hear about Type 1 and Type 2 reports.
- SOC 2 Type 1: Examines your security controls at a single point in time. (Example: Do you have policies, controls, and monitoring systems in place?)
- SOC 2 Type 2: Goes deeper. It assesses how effective those controls are over a period of time (usually 3–12 months).
So, what is SOC 2 Type 2 certification?
It’s the gold standard because it proves your organization not only has security controls but also applies them consistently. Customers, regulators, and partners often require SOC 2 Type 2 certification before working with SaaS vendors.
Let's look at this quote by Shamla Naidoo, Head of Cloud Strategy, Netskope; Former CISO, who says: “Compliance is not security. But security must always be compliant.”
Why Enterprises Must Comply with SOC 2 Regulations?
Achieving SOC 2 certification goes far beyond meeting an IT compliance requirement; it’s about building trust, strengthening security, and unlocking new business opportunities.
Here’s why enterprises can’t afford to overlook SOC 2:
Building Customer Trust and Confidence
Today’s customers expect more than promises; they expect proof. A SOC 2 compliance certification demonstrates that your organization takes data protection seriously and follows industry-standard practices for security, availability, and privacy. This assurance is critical for winning and retaining customers, especially in industries where sensitive data is involved.
Strengthening Data Protection Practices
Cyberattacks and data breaches are at an all-time high. By aligning with SOC 2 controls, enterprises adopt strong access management, encryption, monitoring, and incident response policies. These safeguards don’t just meet audit requirements; they actively reduce risks and make your organization more resilient against evolving threats.
Reducing Risk of Security Breaches
SOC 2 requires enterprises to implement continuous monitoring, regular auditing, and clear incident response procedures. This proactive approach helps detect unusual behavior early, minimizing the risk of a major breach and avoiding the reputational and financial fallout that comes with it.
Meeting Industry and Partner Expectations
Increasingly, enterprises, partners, and even investors demand SOC 2 certification before doing business. For many SaaS vendors, it has become a mandatory requirement to close enterprise contracts. Without it, enterprises may face delays, lose deals, or be excluded from competitive bids.
Competitive Advantage in SaaS and Cloud
In crowded SaaS and cloud markets, a SOC 2 certificate is a key differentiator. It signals that your company operates with maturity, discipline, and reliability. This trust factor can help shorten sales cycles, unlock enterprise opportunities, and give you a competitive edge over uncertified competitors.
How To Be SOC 2 Compliant: 6 Steps
If you’re wondering how to get SOC 2 certification, here’s the roadmap most organizations follow:
Step 1: Define Scope and Choose Trust Principles
Start by defining the scope of your SOC 2 audit. SOC 2 is based on five Trust Services Criteria (TSC):
- Security (mandatory)
- Availability
- Confidentiality
- Processing Integrity
- Privacy
Not every business needs all five. For example:
- A SaaS app handling personal data may need Privacy.
- A cloud infrastructure provider may need Availability.
At this stage, also decide between:
- SOC 2 Type 1 certification: Evaluates your controls at a single point in time.
- SOC 2 Type 2 certification: Tests your controls over several months, proving they work in practice.
Step 2: Perform a Readiness Assessment
Before the official audit, conduct a readiness assessment to measure how close you are to being SOC 2 compliant. This involves:
- Reviewing existing security controls, policies, and procedures.
- Checking documentation and evidence readiness.
- Assessing monitoring and reporting tools.
Think of it as a “practice run” that helps identify what’s missing before the real audit begins.
Step 3: Implement Security Policies and Controls
SOC 2 requires formal, documented security policies. At a minimum, you’ll need:
- Data protection and encryption policies.
- Access control and identity management policies.
- Change management procedures.
- Incident response plans.
- Vendor and third-party risk management policies.
Without these policies clearly written and enforced, you won’t pass the SOC 2 audit.
Step 4: Conduct Gap Analysis and Remediation
Your readiness assessment will uncover gaps—now it’s time to close them. Examples include:
- Enforcing multi-factor authentication (MFA).
- Centralizing logging and monitoring.
- Documenting employee security awareness training.
- Automating access reviews and license management.
Addressing these issues upfront ensures a smoother audit and reduces the risk of failure.
Step 5: Undergo SOC 2 Audit With an Independent Firm
Only a licensed CPA firm accredited by the AICPA can issue a SOC 2 certificate. The audit process includes:
- Reviewing your security controls, policies, and logs.
- Testing control effectiveness (for Type 2 certification).
- Providing a detailed SOC 2 compliance certification report.
This report becomes powerful evidence you can share with customers, partners, and regulators to demonstrate your security maturity.
Step 6: Maintain Controls and Prepare for Recertification
SOC 2 isn’t a one-time project; it’s an ongoing commitment. To stay compliant, you must:
- Continuously monitor and update security controls.
- Run internal audits regularly.
- Maintain and update policies as systems evolve.
- Undergo annual SOC 2 recertification audits.
This ongoing effort ensures you don’t just “get certified” once—you maintain your SOC 2 compliance and keep customer trust year after year.
What are the Criteria for SOC 2 Certification?
Research by CertPro shows that the most common readiness challenges involve documentation gaps and a lack of automated monitoring, which can be alleviated with compliance automation tools.
SOC 2 certification is built around five Trust Services Criteria (TSC) developed by the AICPA. These criteria define the standards organizations must meet to prove their systems are secure, reliable, and trustworthy.
Security – Protecting Data From Unauthorized Access
Security is the mandatory criterion for every SOC 2 audit. It ensures that systems are protected against unauthorized access, both from outside attackers and insider threats. Controls often include firewalls, intrusion detection, multi-factor authentication (MFA), and strict access policies.
Availability – Ensuring Reliable Access to Systems
Availability measures whether systems are accessible when customers need them. This doesn’t guarantee 100% uptime, but it requires organizations to implement monitoring, disaster recovery, performance tracking, and incident response to minimize downtime.
Processing Integrity – Accuracy and Completeness of Data
This criterion ensures that data is processed correctly, consistently, and on time. It applies to organizations where data accuracy is critical—such as financial services, SaaS platforms, or analytics providers. Controls may include automated checks, error detection, and data validation processes.
Confidentiality – Safeguarding Sensitive Information
Confidentiality focuses on protecting data designated as sensitive, such as intellectual property, financial records, or business strategies. This typically involves encryption (in transit and at rest), access restrictions, and contractual agreements with third parties to maintain confidentiality.
Privacy – Protecting Personally Identifiable Information
Privacy ensures that personal data (such as names, emails, health records, or financial details) is collected, stored, used, and shared in accordance with defined privacy policies and regulations like GDPR or HIPAA. It includes controls for consent management, data retention, and secure disposal.
What Documents are Required for SOC 2?
During the audit, you’ll need to provide:
To complete a SOC 2 certification audit, organizations must provide documented evidence that their controls and processes are in place and working effectively. Auditors will review these documents to verify compliance with the Trust Services Criteria. Key documents include:
1. Security and Access Control Policies
Defines how access is managed across systems and applications. This includes role-based permissions, password requirements, MFA enforcement, and least-privilege policies.
2. Change Management Records
Tracks all changes to IT systems, applications, or infrastructure. These records show that updates are tested, reviewed, and approved before deployment to minimize risks.
3. Incident Response Plans
Outlines the steps your organization takes to detect, respond to, and recover from security incidents. A strong plan demonstrates readiness to handle breaches or system failures.
4. Risk Assessment Reports
Documents results from internal risk assessments, showing how your organization identifies threats, evaluates impact, and implements mitigation strategies.
5. Vendor and Third-Party Management Records
Includes contracts, security reviews, and monitoring reports for third-party vendors. Since many enterprises rely on external SaaS or cloud providers, auditors want proof that third-party risks are managed.
6. Audit Logs and Monitoring Evidence
Centralized logs, system alerts, and monitoring reports that provide visibility into user activity, system access, and security events. These logs help prove that controls are working as intended.
How Much Does It Cost to Get SOC 2 Certified?
Gartner predicts that by 2027, over 90% of SaaS procurement requests will begin with verified SOC 2 certification status, making it an essential part of IT vendor risk management.
One of the most common questions enterprises ask is: How much does it cost to get SOC 2 certified? The answer depends on your company's size, scope of the audit, and how well-prepared you are before starting the process.
Typical SOC 2 Certification Costs by Company Size
- Small startups: $20,000–$40,000
- Mid-sized SaaS enterprises: $40,000–$60,000
- Large enterprises: $60,000–$80,000+
These estimates cover the external audit itself but don’t include the hidden internal costs of preparing for certification.
Factors That Influence SOC 2 Certification Costs
- Scope of the audit: A SOC 2 Type 1 certification (point-in-time review) is generally less expensive than a SOC 2 Type 2 certification (which tests controls over several months).
- Number of trust principles: Adding extra principles like Availability, Confidentiality, or Privacy increases the scope and the cost.
- Complexity of your systems: More applications, integrations, and users mean more testing, evidence collection, and review time.
- Audit firm reputation: Well-known audit firms often charge higher fees but may offer more credibility in the eyes of customers and partners.
How CloudEagle.ai Helps with Compliance Management?
Achieving and maintaining SOC 2 certification isn’t a one-time milestone; it’s an ongoing process. Enterprises must continuously monitor systems, enforce strict access controls, and generate evidence for auditors at any given time.
Doing this manually is not only time-consuming but also prone to human error. CloudEagle.ai automates these requirements end-to-end, making compliance seamless and sustainable.
Here’s how CloudEagle.ai supports CIOs, CISOs, and compliance teams:
1. Full SaaS Discovery
Most IDPs and manual tracking systems only cover apps connected through SSO, leaving Shadow IT undetected. CloudEagle.ai eliminates this blind spot by discovering every SaaS application in use, even those adopted without IT’s approval.
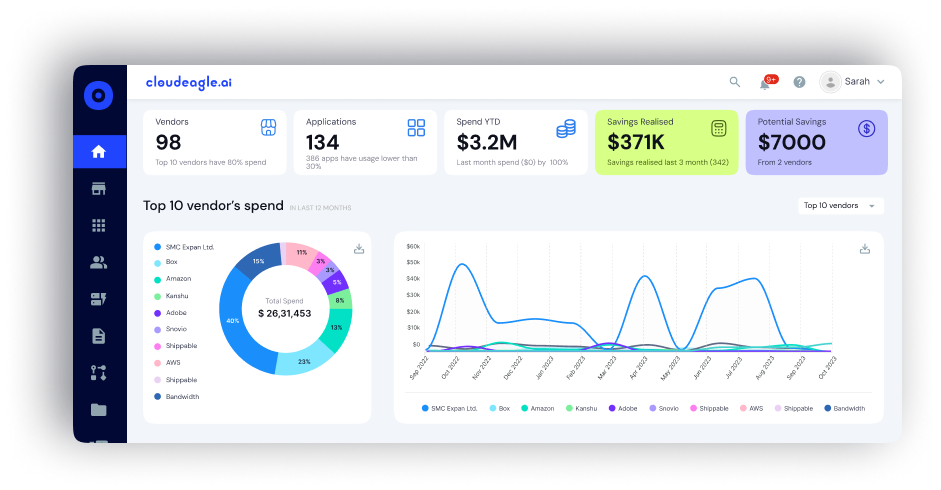
It consolidates usage, access, and spending data into a single dashboard, giving IT and compliance leaders total visibility. This ensures no unmanaged apps slip through during an audit and keeps the organization aligned with SOC 2’s visibility requirements.
2. Automated Access Reviews
SOC 2 requires regular access reviews to confirm that employees have only the access they need. Traditionally, this involves sending spreadsheets to managers, waiting for responses, and manually tracking approvals. CloudEagle.ai replaces this painful process with automation.

Managers receive automated review workflows, can approve or revoke access with one click, and every decision is logged for audit purposes. Reviews that once took weeks can now be completed in hours, ensuring accuracy and compliance.
Know how Dezerv automated its app access review process with CloudEagle.ai.
3. License Optimization with Compliance Alignment
Unused or misallocated licenses don’t just waste money; they also create compliance issues when users retain access they don’t need. CloudEagle.ai continuously monitors license utilization across SaaS tools, automatically reclaims idle licenses using license harvesting workflows when employees leave, and reallocates them to new users.
4. Role-Based & Privileged Access Control (RBAC & PAM)
Granting employees more permissions than necessary is one of the biggest compliance risks. CloudEagle.ai enforces role-based access control (RBAC), ensuring that access aligns with each employee’s responsibilities.

For high-risk accounts, such as administrators or superusers, it adds another layer of privileged access management (PAM). This reduces insider threats, prevents unauthorized changes, and demonstrates to auditors that privileged accounts are tightly controlled.
5. Just-In-Time Access Controls (JIT)
Temporary access is often overlooked; contractors, vendors, or auditors are given permissions that aren’t revoked when their work is finished. CloudEagle.ai addresses this by offering just-in-time access controls.
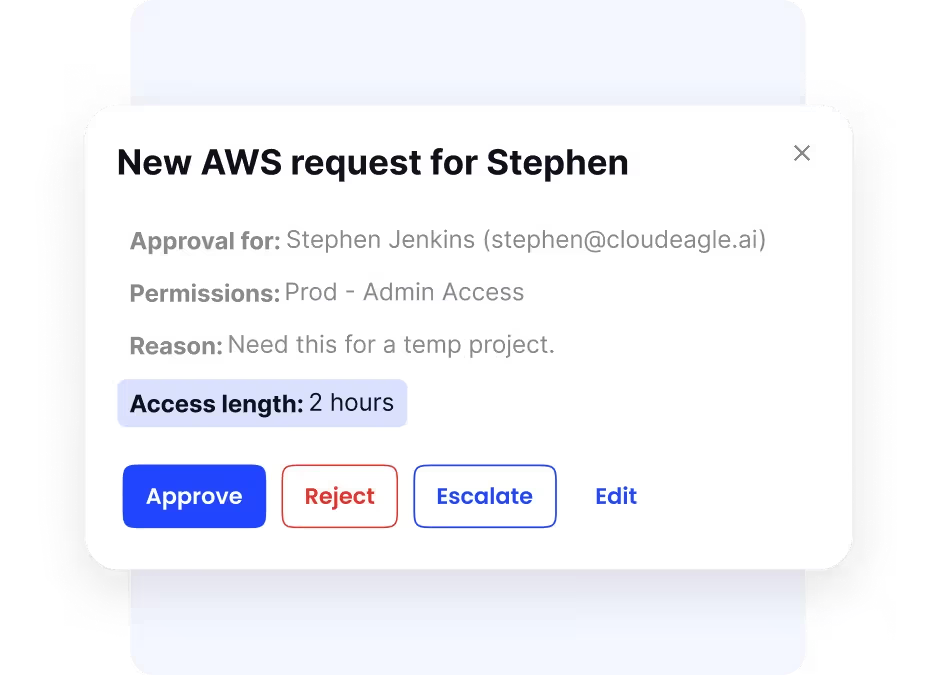
IT can grant access for a fixed period, and the system automatically removes it once the window closes. This prevents lingering accounts from becoming security risks and supports SOC 2’s requirement for controlled, time-limited access.
6. Audit-Ready Logs & Evidence
One of the toughest parts of any SOC 2 audit is pulling together evidence of who accessed what and when. CloudEagle.ai simplifies this by maintaining tamper-proof, timestamped logs of every access request, approval, and policy change.
These records can be exported instantly, providing auditors with clear evidence of compliance. What used to take IT teams days of log-hunting can now be accomplished in minutes.
Conclusion
If you’re asking how to get SOC 2 certification, the answer lies in a structured process: scoping the audit, implementing strong security policies, remediating gaps, and partnering with an independent auditor.
While it requires time, resources, and investment, the payoff is significant: greater customer trust, reduced risk of breaches, stronger data security, and a competitive edge in winning enterprise deals.
To make compliance easier, automation is key. With a platform like CloudEagle.ai, organizations can simplify access governance, enforce least-privilege policies, automate audits, and stay continuously prepared for every SOC 2 certification cycle.
Ready to ensure your organization stays audit-ready year after year?
Schedule a demo with CloudEagle.ai and see how compliance management can be seamless.
FAQs
1. What is the cost of SOC 2 certification?
It typically ranges from $20,000 to $80,000, depending on company size, scope, and audit firm.
2. How long does it take to get SOC 2 certified?
Usually 3–12 months, depending on readiness and audit scope.
3. How long is the SOC 2 valid for?
A SOC 2 certificate is valid for 12 months. You must undergo annual audits to maintain compliance.
4. What documents are required for SOC 2?
Policies, risk assessments, incident response plans, audit logs, and vendor management records.
5. Is ISO 27001 the same as SOC 2?
No. ISO 27001 is an international security standard, while SOC 2 is U.S.-based and specific to service organizations handling customer data.

%201.svg)








.avif)




.avif)
.avif)




.png)









