HIPAA Compliance Checklist for 2025

Managing identities and access across hundreds of SaaS apps is complex, time-consuming, and risky. Manual audits, static policies, and reactive monitoring create blind spots, leaving enterprises vulnerable to insider threats, compliance gaps, and security breaches.
So, how can you transform and manage your IAM more effectively?
Explore CloudEagle.ai’s Gen AI with Eagle Eye, an AI-powered automation chatbot in identity and access management. EagleEye transforms how enterprises manage access by predicting user behavior, automating repetitive tasks, and providing proactive insights.
Here’s how EagleEye transforms IAM, making it smarter, faster, and more secure for enterprises.
TL;DR
- CloudEagle.ai’s EagleEye automates access requests, provisioning, and offboarding using Generative AI, speeding up processes and reducing manual IT work.
- EagleEye monitors user activity and adjusts permissions automatically based on role changes or project needs for secure identity management.
- CloudEagle.ai helps enterprises stay compliant by automating audits, access reviews, and detecting unusual behavior quickly.
- Automating repetitive tasks with CloudEagle.ai minimizes errors, saves IT time, and improves efficiency.
- Employees can easily request app access via chat (Slack, Teams) with CloudEagle.ai, making access management faster and boosting productivity.
The Hidden Risks IT Teams Face Today
With the constant changes in the IT landscape, enterprises face risks that threaten security, compliance, and efficiency. Here are the key challenges IT teams must tackle:
1. Shadow IT Risks
Employees often use unauthorized SaaS apps and AI tools (Shadow IT), creating security and compliance blind spots. A Gartner study found that shadow IT accounts for 30–40% of IT spending in large enterprises, with some reports estimating it could reach up to 50%.
Unapproved tools increase the attack surface, risking data breaches and non-compliance with regulations like ISO 27001, SOC 2 Type II, and GDPR. At the same time, redundant tools and unused licenses waste IT budgets and expose the enterprise to fines and security vulnerabilities.
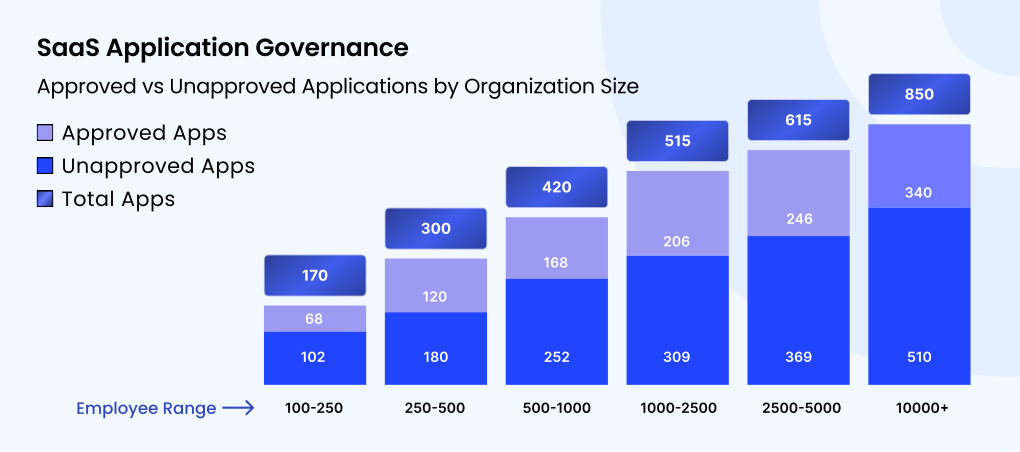
This graphical representation highlights that regardless of company size, a significant percentage of SaaS apps remain unsanctioned.
2. Overwhelmed Security Teams
Security teams are often understaffed and overwhelmed by repetitive tasks such as patching vulnerabilities, resetting credentials, and training users. This leaves little time for proactive threat hunting and strategic improvements, while excessive effort goes into explaining cybersecurity to leadership instead of strengthening defenses.
3. Third-Party and Vendor Management Risks
Many enterprises overlook the cybersecurity practices of their third-party vendors, which exposes them to potential breaches through supply chain attacks. Weaknesses in vendor security can directly impact the enterprises, and often, there is no clear ownership of managing these third-party risks.
According to reports, 4.45 million dollars is the average cost of a data breach.
4. Lack of Visibility Across SaaS and AI Environments
The rapid adoption of cloud and AI tools creates fragmented systems that are difficult to monitor. IT teams often lack centralized visibility into user access, application usage, and security anomalies, resulting in delayed risk detection, such as overprivileged users, orphaned accounts, or unusual usage patterns.
5. Compliance Complexity
Ever-growing regulatory requirements demand strict controls on data access and usage, but disjointed IAM and procurement processes hinder consistent compliance enforcement. Failure to produce timely audit-ready reports can lead to significant fines and reputational damage.
6. Fragmented IAM and Access Controls
Legacy IAM tools struggle to keep up with the needs of modern identity-first environments, relying on manual processes that increase the risk of human error. Issues like overprivileged access and outdated accounts are common vulnerabilities that leave enterprises exposed.
8. Operational Inefficiencies and Cost Overruns
Fragmented SaaS environments create duplication of effort and integration issues, lowering productivity. Hidden license waste, mismanaged renewals, and approval bottlenecks inflate costs, leading to missed deadlines and service disruptions.
Why Traditional IAM Tools Are Falling Short?
Traditional IAM tools struggle to keep up with modern security needs, leaving enterprises vulnerable to inefficiencies, security gaps, and compliance risks.
Here’s why it isn't the complete solution:
1. Lack of Scalability for Cloud and Hybrid Environments
Traditional IAM solutions were built for on-premises systems and often struggle to scale across modern SaaS and AI applications. These tools can’t unify access policies across a growing variety of cloud-based platforms and tools, leading to security gaps and inefficiencies in managing user access across the ecosystem.
2. Fragmented and Siloed Ecosystems
Many enterprises use multiple IAM, IGA, and PAM tools from different vendors that don't integrate well. This fragmentation leads to siloed identity data and access policies, which result in inconsistent enforcement and limited visibility.
3. Limited Automation and Dynamic Access Controls
Traditional IAM tools typically rely on static Role-Based Access Control (RBAC), which limits flexibility. They lack automation for risk-based, real-time, or Just-in-Time (JIT) access decisions, increasing the risk of overprivileged accounts and manual errors.
4. Insufficient Support for Non-Human Identities
Enterprises now manage machine identities, like service accounts, IoT devices, and AI agents, but traditional IAM struggles to secure, rotate, and monitor these identities at scale, expanding the attack surface.
Sebastian Rohr, Senior Advisor, KuppingerCole Analysts, says:
“As GenAI agents and machine-to-machine interactions become more prominent, enterprises must move beyond human-centered security frameworks to tackle the risks posed by non-human identities.”
This highlights the growing need for solutions like CloudEagle, which helps organizations manage machine identities and secure data at scale without relying on outdated methods.
5. Poor Visibility and Monitoring
Most legacy IAM tools don't provide real-time monitoring or insights into who accessed what, from where, and when. This leaves enterprises unable to quickly detect suspicious activities or respond to breaches effectively.
6. High Operational Complexity and Costs
Traditional IAM systems often require manual configurations, scripting, and regular updates. This ongoing maintenance and integration effort drains IT resources, raising the total cost of ownership.
While traditional IAM systems present many challenges, enterprises must evolve their approach to stay secure and compliant. To do so effectively, let's check out CloudEagle.ai’s EagleEye: the next generation of AI-powered IAM.
What is CloudEagle.ai's EagleEye?
CloudEagle.ai’s EagleEye is an agentic AI assistant designed to streamline SaaS management and improve access governance. It integrates with platforms like Slack, Microsoft Teams, and other SaaS tools to help IT, procurement, and security teams efficiently manage user access and workflows.

By leveraging intelligent automation and natural language processing, EagleEye enables teams to complete tasks, access critical data, and streamline operations through simple chat commands, without the need for manual intervention.
Key Features of EagleEye:
- Continuously tracks user access to ensure permissions are always up-to-date and automatically granted based on role and requirements.
- Streamlines routine tasks like user provisioning, approvals, and access requests, reducing bottlenecks and speeding up operations.
- Flags and alerts security teams to access anomalies in real-time, enabling rapid identification and resolution of potential risks.
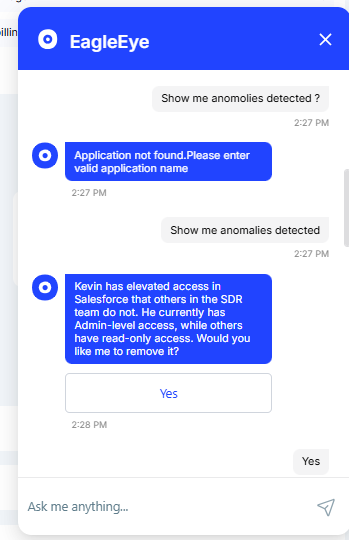
- Ensures seamless integration between IT, procurement, and security teams, aligning them to work together efficiently on access management and governance.
EagleEye is more than just a chatbot; it's a smart assistant that continuously evolves, improving decision-making and operational efficiency. By integrating agentic AI with SaaS management, it reduces the complexity of access governance, enhances security, and drives productivity across the enterprise.
How EagleEye Transforms IAM: From Reactive to Proactive?
Traditional IAM systems are often reactive, relying on manual processes, periodic audits, and fixing issues as they arise. EagleEye transforms this model into a proactive, automated system by anticipating needs, automating repetitive tasks, and enhancing overall security posture.
EagleEye is an Agentic AI bot that elevates Identity and Access Management (IAM) by automating and personalizing security tasks. With AI-driven insights, predictive workflows, and real-time automation, EagleEye ensures IAM processes are smarter, faster, and more secure.
Here’s how EagleEye transforms IAM:
1. Real-Time Access Monitoring and Anomaly Detection
EagleEye continuously monitors user behavior across your entire SaaS environment, detecting anomalies in real time. Whether it's unusual login times, access patterns, or permission escalations, EagleEye instantly flags potential security risks.
Rather than waiting for an issue to arise, EagleEye detects abnormal activity before it becomes a breach. Security teams receive immediate notifications to investigate and prevent potential breaches.
2. AI-Powered Predictive Access
With EagleEye, IAM becomes predictive. It uses AI to anticipate access needs based on users' roles and historical behavior, allowing for automated provisioning and deprovisioning.
As soon as a new hire joins, EagleEye predicts their app access needs and automates provisioning based on their role, department, and behavior. EagleEye instantly adjusts permissions when roles change, ensuring compliance with the principle of least privilege.
3. Automated Access Remediation and Compliance
EagleEye not only detects issues but also automatically resolves them. When it detects excessive or unauthorized access, it can trigger workflows to either approve or revoke access.
Maintain continuous compliance without manual oversight. EagleEye performs access reviews and certifications on a regular basis. If a user's access violates policy, EagleEye automatically sends notifications and reverts permissions, ensuring your IAM stays aligned with security best practices.
4. Personalized IAM Experience
EagleEye is designed to adapt to your organization’s unique needs. It customizes workflows based on departments, roles, and individual preferences, ensuring a personalized experience for each user. For example, the HR team might need different access than the marketing team; EagleEye automates app access and permissions based on departmental requirements.
5. AI-Driven Decision Support
With EagleEye, security teams no longer have to sift through data manually. The Agentic AI bot offers smart, data-driven suggestions, helping teams make better decisions about who needs access to what, when, and why.
EagleEye can suggest access changes based on usage patterns or role evolution, helping reduce manual reviews. By continuously analyzing usage trends, it identifies potential risks, such as unused licenses or excessive access.
6. Streamlined Integrations with Collaboration and ITSM Tools
EagleEye integrates seamlessly with ITSM and collaboration tools like Slack, Microsoft Teams, and ServiceNow, automating workflows and approval processes directly within these platforms. For example, when an access request is made, EagleEye automatically triggers an approval process and can even deprovision access once it’s no longer needed.
Why EagleEye is a Game-Changer for IAM
With EagleEye, IAM becomes a continuous, self-optimizing process that reduces administrative overhead, enhances security, and ensures compliance, all in real time. As an Agentic AI bot, EagleEye helps security teams automate complex workflows, anticipate access needs, and continuously monitor activity.
Cost Savings: By eliminating manual work and reducing over-provisioned access, organizations save time and money.
Enhanced Security: EagleEye proactively detects and mitigates risks, providing real-time protection without human intervention.
Improved User Experience: With automated provisioning and role-based access control, users get the apps they need when they need them, without delays or errors.
How to Streamline Identity and Access Management with EagleEye?
Using EagleEye, you can automate and simplify the IAM process. From smoothly onboarding new employees with the right access to continuously monitoring permissions, EagleEye helps IT teams manage user access securely and efficiently, without the need for manual work.
Here’s how:
Step 1: Log in to the CloudEagle.ai platform and click on the EagleEye icon.
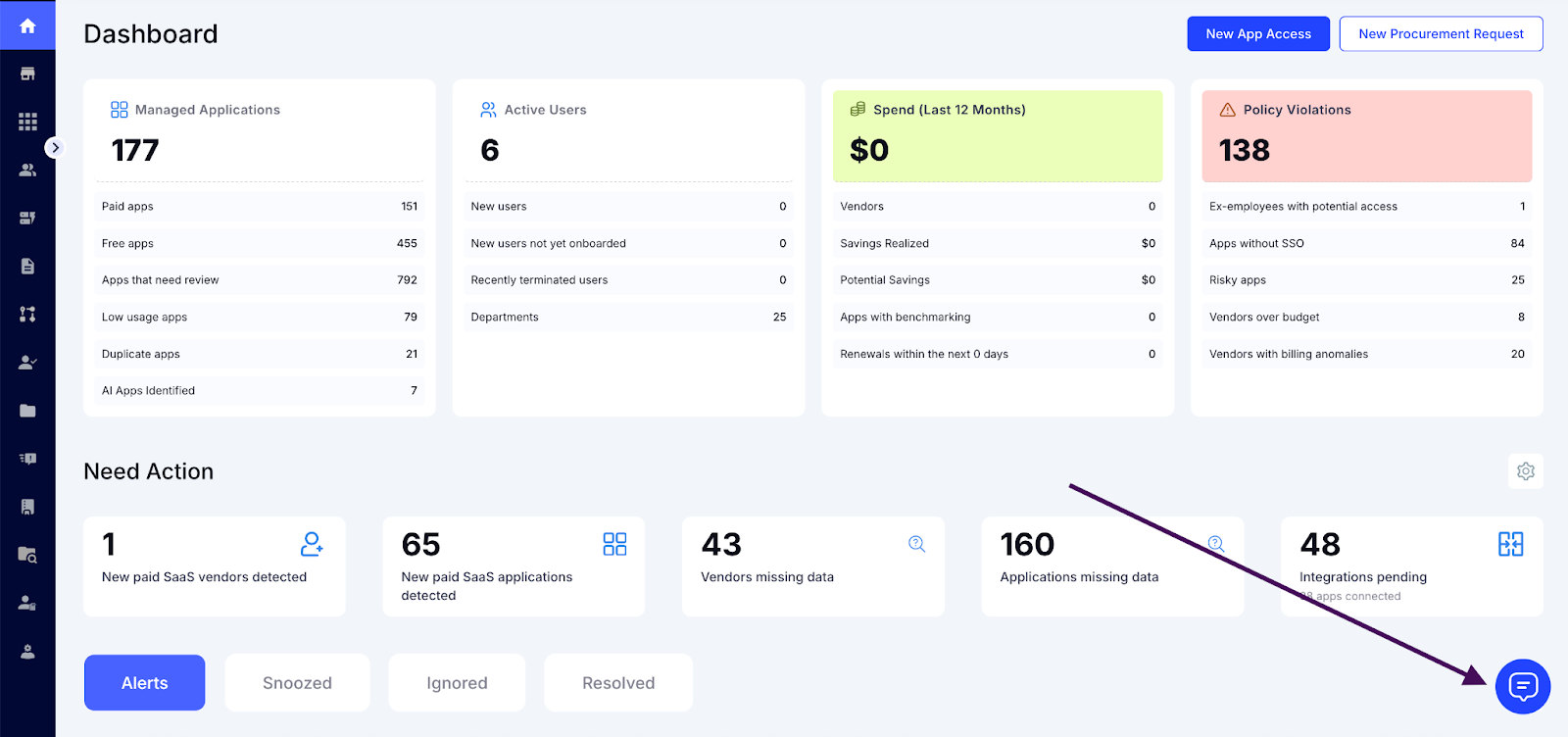
Step 2: Ask EagleEye your query.
For example: "Show me any pending onboarding requests."
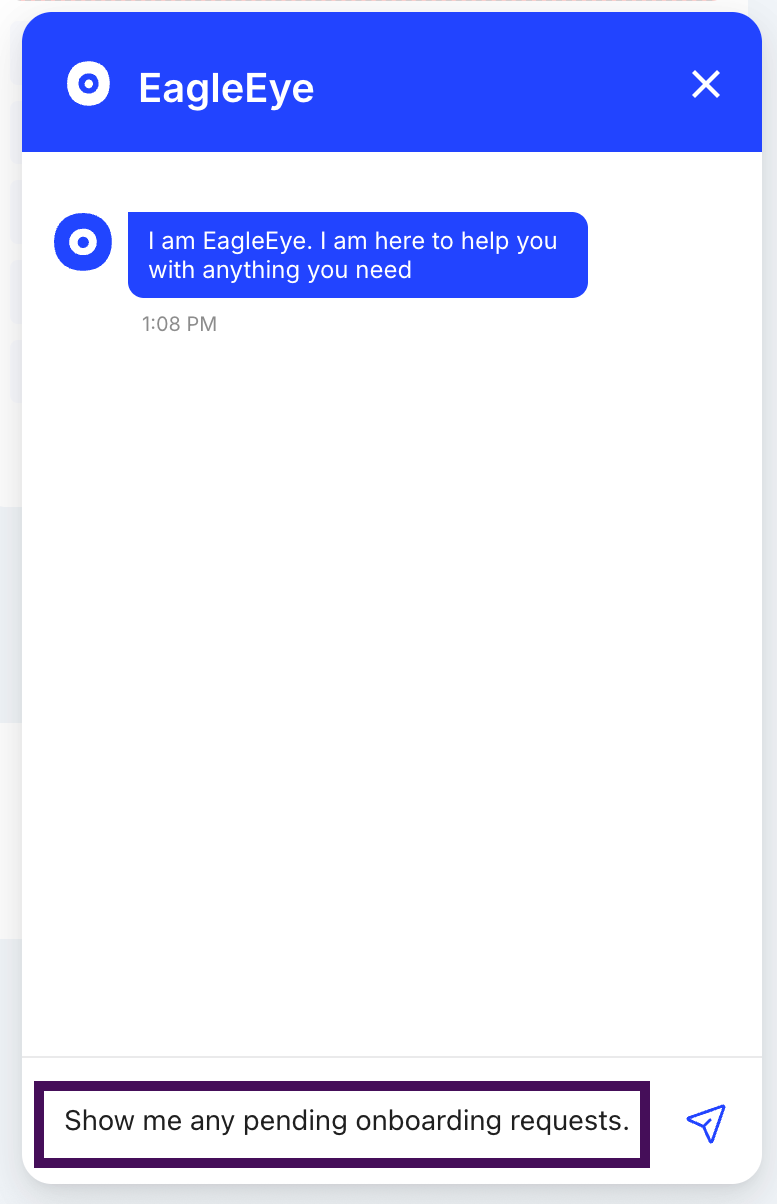
EagleEye Response: "Joe is joining the SDR team on Monday. Based on the SDR access template, he needs access to Slack, Gong, and Salesforce. Would you like me to provision these apps for Joe?"
Step 3: Click on ‘Yes’ to proceed.

Step 4: System Actions:
- The chatbot checks license availability for the requested apps.
- It then responds with the available license count for each app.
- Next, it creates a ticket in your ticketing software (e.g., Jira).
- Approval requests are sent to the assigned manager for approval.
- You will then wait for approval from the assigned manager.
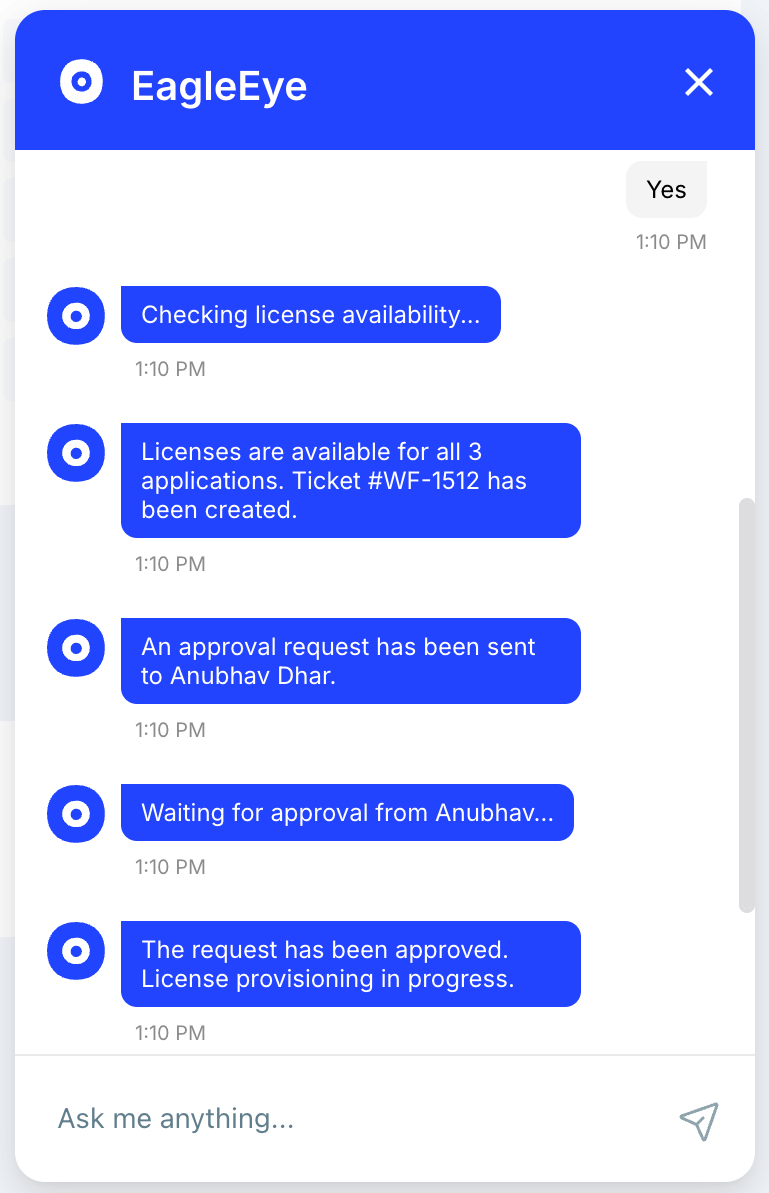
Approval Process:
- Once everything is in place, the request is approved by the manager.
- License provisioning begins automatically. If licenses are available, provisioning occurs without delays.
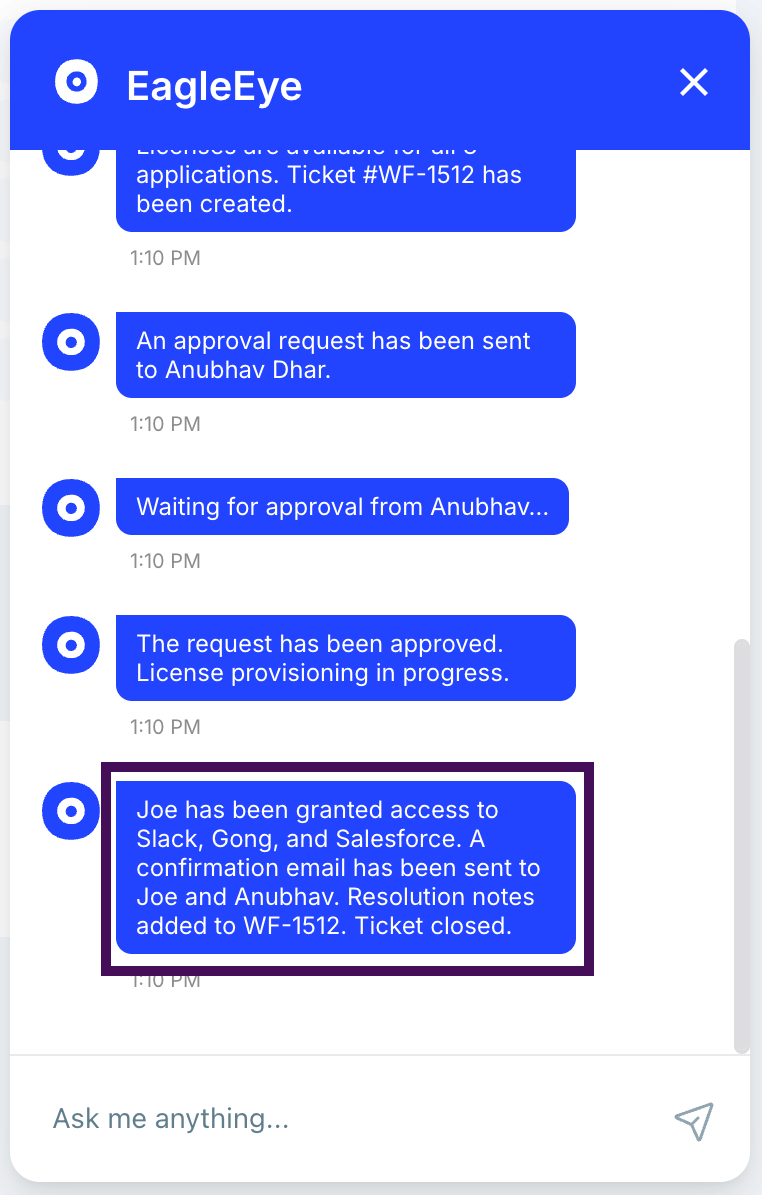
Final Steps:
- Joe is granted access to Slack, Gong, and Salesforce.
- Confirmation emails are sent to both Joe and his manager.
- Resolution notes are added to the ticket, and the ticket is marked as closed.
Benefits of CloudEagle.ai’s Gen AI and EagleEye in IAM
CloudEagle.ai’s Gen AI and EagleEye bring major improvements to IAM by automating key processes, enhancing security, and making life easier for IT teams. Here's how:
1. Proactive Monitoring & Access Control: CloudEagle.ai continuously watches user activity and app usage to detect and flag any unusual access or privilege issues. This allows security teams to act before problems become serious, reducing security risks.
2. Automating Routine Tasks: The platform automates tasks like onboarding new employees, granting them the right app access, and managing unused licenses. It ensures new hires are set up quickly and efficiently, without delays.
3. Real-Time Alerts & Actions: When issues arise, CloudEagle.ai instantly creates workflows for approval and resolution. For example, if it detects excessive access, it automatically prompts the right people to adjust permissions, cutting down on manual intervention.
4. Seamless Integration with IT Tools: CloudEagle.ai works with IT systems like ServiceNow, JIRA, and Asana. It keeps workflows smooth by automating ticket updates and resolutions, ensuring things don’t get stuck.
5. Predictive Actions for Smarter Decisions: With predictive analytics, the platform suggests the right actions, such as which apps to grant access to or which tools need attention. It helps teams make faster, smarter decisions based on real-time data.
Conclusion
CloudEagle.ai leverages Gen AI to transform your IAM processes into a proactive, automated, and secure system. By automating key workflows like onboarding, access reviews, and compliance reporting, the platform helps you save time, reduce security risks, and improve overall operational efficiency.
The results were transformative: fewer access-related incidents, faster detection of anomalies, and improved operational efficiency. By leveraging CloudEagle.ai’s Gen AI and EagleEye, enterprises can modernize IAM, proactively manage risk, and ensure that employees have the right access at the right time.
Ready to transform your IAM strategy?
Schedule a demo with CloudEagle.ai and see how you can transform your enterprise's IAM.

%201.svg)










.avif)




.avif)
.avif)




.png)









