HIPAA Compliance Checklist for 2025

According to CloudEagle.ai’s IGA report, 1 in 2 employees have more access than they actually need. This overprivileged access creates serious security risks. In fact, 28% of companies have faced major security issues because of it.
For CIOs and CISOs, this means a constant battle to keep data safe, stay compliant, and control who accesses what. Using spreadsheets and emails only makes things harder, causing blind spots and audit problems.
CloudEagle.ai is a simple, all-in-one IGA platform. It automates giving and taking away access, so permissions are always correct. IT teams can see all user access in one place, control access based on roles, and enforce policies quickly.
Let’s explore how CloudEagle.ai can help you manage access more effectively and securely.
TL;DR
- CloudEagle.ai gives CIOs and CISOs a unified view of who has access to all SaaS apps in the enterprise.
- It offers real-time access tracking, providing visibility into user activities and helping identify suspicious behavior. Automated access reviews keep compliance in check.
- CloudEagle.ai streamlines onboarding and offboarding by automating user access, ensuring employees get immediate access to needed apps, and preventing former employees from retaining access.
- The platform enforces the "least privilege" principle by granting access based only on roles, minimizing unnecessary permissions, and boosting security.
- CloudEagle.ai automates compliance reporting, tracking app access for audits, and simplifying regulatory documentation, reducing the risk of non-compliance.
Challenges In Access Management For CIOs And CISOs
Managing access across hundreds of SaaS apps is a growing challenge for CIOs and CISOs, who must balance security, compliance, and usability without overwhelming their teams.
Here’s what they come across:
1. Complex SaaS Access Management
Keeping track of who has access to what is a huge challenge. App access rights often reside across different teams and systems, leading to confusion and excessive permissions. This scattered approach causes security vulnerabilities and wastes IT resources trying to keep everything tied together.
2. Lack of Real-Time Monitoring
Identifying risky or unauthorized user activity requires real-time monitoring across every app. Manual access reviews or delayed reports make it easy for breaches or compliance failures to slip through unnoticed. Automation is essential to maintain constant oversight and respond quickly to threats.
3. Ensuring Compliance
Strict regulations like ISO 27001, SOX, HIPAA, and GDPR require enterprises to ensure users only have access needed for their role. When access data is spread across many disconnected systems, enforcing these rules becomes a challenge. Without centralized access control, you will face audit failures, fines, and reputational damage.
4. Managing Privileged Access
Privileged accounts hold the keys to sensitive systems, but if these are mismanaged, they become a major insider threat vector. Credential theft or insider misuse can cause devastating breaches. Enterprises must enforce tight controls around privileged accounts and automate the immediate removal of access when no longer needed.
5. Limitations of IDP-Only Solutions
Identity Providers like Okta focus on verifying user identity, but don’t cover the full SaaS access lifecycle needs. Many SaaS apps limit advanced integrations to expensive plans. License tracking is inefficient, meaning wasted admin time and cost from unused licenses and manual provisioning errors.
6. Shadow IT Risks
SaaS apps acquired outside IT control create security blind spots. These “Shadow IT” apps raise the risk of data leaks or regulatory violations because they are unmonitored and unmanaged. Detecting and managing shadow IT is a critical ongoing challenge.
Collaboration Gaps: How Silos Impact IAM?
In many enterprises, CIOs (Chief Information Officers) and CISOs often work in silos, each with different priorities. CIOs focus on driving digital transformation, innovation, and operational efficiency, while CISOs are responsible for security, risk management, and compliance.
As per CloudEagle.ai’s IGA report, Chetna Mahajan, Global CDO & CIO of Webflow, said:
“IAM is often the most underfunded yet mission-critical part of security. But those taking a proactive approach, starting with automation and AI-driven governance, are not just reducing risk, they’re unlocking efficiency and long-term cost savings.”
These differences often create challenges for IAM, which requires collaboration between both teams to be effective.
Below are the key challenges:
1. Conflicting Priorities
CIOs are often focused on accelerating digital transformation and streamlining IT operations, prioritizing speed and cost-efficiency. This push for innovation can sometimes bypass necessary security measures, leaving critical IAM processes underdeveloped or fragmented.
CISOs, on the contrary, focus on minimizing risk and ensuring regulatory compliance, often requiring a slower, more cautious approach to security. This emphasis on security can conflict with the push for speed, delaying IAM projects or leaving critical vulnerabilities unaddressed.
2. Poor Communication
Lack of alignment between CIO and CISO teams creates fragmented communication, causing misunderstandings and misaligned expectations. This leads to duplicated efforts, wasted resources, and delays in IAM deployment. Inconsistent IAM policies, especially across departments or technical environments, can expose the enterprises to security risks.
3. Budget Conflicts
CIO and CISO teams often share overlapping budgets, leading to tension over priorities. CIOs may focus on business-facing IT infrastructure, like cloud migrations, leaving IAM and security underfunded. CISOs, while advocating for strong security measures, may struggle to align their efforts with business goals, resulting in incomplete or inefficient IAM solutions.
4. Ambiguous Authority
According to reports, 42% of organizations plan to adopt identity governance measures to strengthen access control and reduce risk. However, unclear authority between CIOs and CISOs can create governance challenges, hindering effective decision-making and policy enforcement.
If CISOs report to the CEO, they may be disconnected from IT, hindering IAM implementation. When CISOs report to CIOs, security can be deprioritized. This lack of clarity delays actions and weakens incident response, leaving security policies poorly enforced.
4. Delayed Incident Response
IAM is critical during cyberattacks, but silos between CIO and CISO teams slow response times. Delayed IAM controls, such as user deprovisioning, give attackers more time to exploit vulnerabilities. This leads to greater damage, data loss, and reputational harm. Improved coordination between them can minimize these risks.
5. Compliance Risks
Regulatory compliance depends on integrated security and IT governance. Without CIO and CISO collaboration, security policies become inconsistent, risking non-compliance with ISO 27001, SOC 2 Type II, GDPR, and HIPAA. Siloed IAM efforts lead to fragmented logs, complicating audits and increasing the risk of penalties and breaches.
Why Traditional IAM Tools Fall Short?

How to Bridge the Gaps: Best Practices
For effective Identity and Access Management (IAM), CIOs and CISOs must collaborate. CloudEagle.ai helps bridge the gaps, making it easier for IT and security teams to work together, maintain control, and stay compliant.
Here’s how it helps:
1. Encourages Ongoing Communication
CloudEagle.ai provides shared dashboards, notifications, and reporting so CIOs and CISOs can stay aligned. Teams can quickly see access requests, approvals, and potential issues, keeping everyone on the same page and reducing misunderstandings.
2. Supports Unified Governance
Form cross-functional teams with key stakeholders from IT, security, and business units to share responsibility for IAM strategy. By centralizing access policies and workflows, CloudEagle.ai allows teams to collaborate efficiently. Approvals and access rights are managed consistently, reducing errors and closing security gaps.
3. Helps with Budget and Resource Planning
CIOs and CISOs should plan the IT-security budget together to avoid conflicting priorities. CloudEagle.ai tracks app usage, license allocation, and access patterns, giving CIOs and CISOs clear insights. This helps them plan budgets together, balance IT innovation and security investments, and prevent overspending or underfunded security controls.
4. Clarifies Decision-Making
Automated workflows and clear role-based approvals reduce confusion about who can grant or revoke access. This allows CISOs to enforce security policies without slowing down IT operations, creating smooth coordination between teams.
5. Enables Faster Incident Response
CIOs and CISOs must collaborate during security incidents to respond quickly and efficiently. CloudEagle.ai centralizes all access data, giving teams real-time visibility. Automated access revocation and continuous monitoring help contain risks, minimize damage, and speed up recovery.
6. Aligns Access with Business Goals
IAM should enable secure business growth by balancing access control with usability, giving employees the tools they need while minimizing risk. CloudEagle.ai ensures employees have the right access for their roles, using time-based and role-based controls to prevent unnecessary permissions and keep sensitive data secure, without slowing down productivity.
Why CIOs and CISOs Should Consider CloudEagle.ai?
CloudEagle.ai makes access management simple, helping CIOs and CISOs secure and control user access across the organization. With its advanced features, it’s become a go-to solution for enterprises to streamline access and enhance security.
CloudEagle.ai helps CIOs and CISOs with:
1. Centralized Access Control
CloudEagle.ai centralizes all user access data into one platform, providing a unified view of who has access to which apps across the enterprises. This reduces the complexity of managing permissions across multiple platforms and minimizes the potential for errors.
For instance, if an employee needs access to an app, IT teams can grant or revoke access from a single platform rather than navigating multiple systems. This centralization ensures consistent access policies, making it easier to maintain security across all SaaS apps.
2. Real-Time Access Monitoring
According to CloudEagle.ai’s IGA report, 60% of AI and SaaS apps operate outside IT's knowledge. With CloudEagle.ai, you can easily track and manage access across all SaaS apps. The platform provides a unified dashboard that gives real-time visibility into who is accessing your organization’s apps and data.
It also tracks privileged access, maintaining detailed logs for a complete history of user actions. This helps you spot suspicious behavior and ensures full accountability. The platform also automates regular access reviews, ensuring compliance with internal policies and regulations.
3. Automated User Provisioning and Deprovisioning
CloudEagle.ai streamlines employee onboarding and offboarding with auto-provisioning and deprovisioning workflows. New employees gain immediate access to the apps they need, enabling them to start working right away. Also, automating onboarding with CloudEagle.ai can save up to 500 hours annually.
Similarly, when an employee leaves or changes roles, CloudEagle.ai immediately revokes their access to apps they no longer need. It automatically updates access permissions, ensuring that former employees or those who have switched roles don’t retain access to unnecessary apps.

Know How CloudEagle.ai helped Treasure Data streamline employee offboarding, saving 1354 hours annually.
5. Role-Based Access Control (RBAC)
CloudEagle.ai strengthens security by following the "least privilege" principle, giving users only the access they need to do their jobs. With role-based access control (RBAC), it minimizes over-permissions and accidental data exposure, ensuring employees have access only to what’s necessary for their roles.
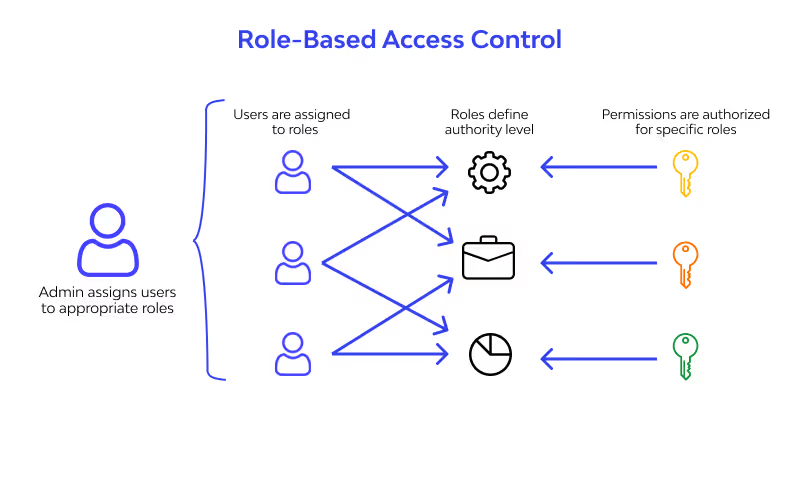
For example, a marketing employee doesn’t need access to financial data or customer details. CloudEagle.ai ensures that each user gets access only to the resources relevant to their role, keeping sensitive data secure.
Plus, when a user’s role changes, their access is automatically updated. This ongoing management prevents employees from retaining permissions they no longer need, maintaining tight security across your organization.
6. Time-Based Access Management
CloudEagle.ai also offers time-based access controls. It allows you to grant users access only during specific periods. It helps restrict app access during off-hours, reducing the risk of potential security threats when no one is available to monitor the systems.

This feature is particularly useful for contractual employees, interns, or vendors who need access to certain systems for a limited time. Once the contract ends, access is automatically revoked, preventing unauthorized access and saving IT teams time and effort.
7. Access Reviews and Compliance Reporting
CloudEagle.ai automates the creation of audit logs and compliance reports, making it easier for organizations to meet regulatory requirements. These reports track who accessed which app and when providing a clear audit trail for transparency. With CloudEagle.ai, enterprises experience an 80% reduction in time spent on user access reviews.

For example, if a compliance officer needs to check who accessed sensitive financial data, they can easily pull a report from CloudEagle.ai instead of manually reviewing logs from various systems.
8. Self-Service App Catalog
CloudEagle.ai’s Self-Service App Catalog lets employees request access to approved SaaS apps on their own, without waiting for IT. They can browse available apps, submit requests, and provide necessary details in a single platform.

IT teams can automate approvals based on roles and policies, ensuring secure and consistent access. Every request is logged, making audits and compliance simple. This self-service approach speeds up access, reduces repetitive tickets, and lets IT focus on higher-value work while keeping systems secure.
9. Customizable Access Policies
CloudEagle.ai lets you create custom access policies based on factors like department, role, or risk level, ensuring users have access to the right apps at the right time. For example, HR employees may require access to sensitive personnel data, while IT staff may need access to broader system controls.
The tool lets you adjust access policies as business needs change, ensuring users have the right access based on new behaviors or risks. It updates policies when new apps are added or usage patterns change, keeping security strong and control intact.
How To Get Started with CloudEagle.ai?
You can manage app access with CloudEagle.ai in a few simple steps.
The "Access Management" module has seven tabs: Active Users, Inactive Users, Auto Provisioning, Auto Deprovisioning, Approval Policies, Access Requests, and Run Logs—each streamlining and securing your access management.

1. Active Users: This tab helps you manage users who are currently active in your system. It ensures employees have the right access based on their roles. When a new employee joins or someone changes roles, you can easily assign the necessary apps.
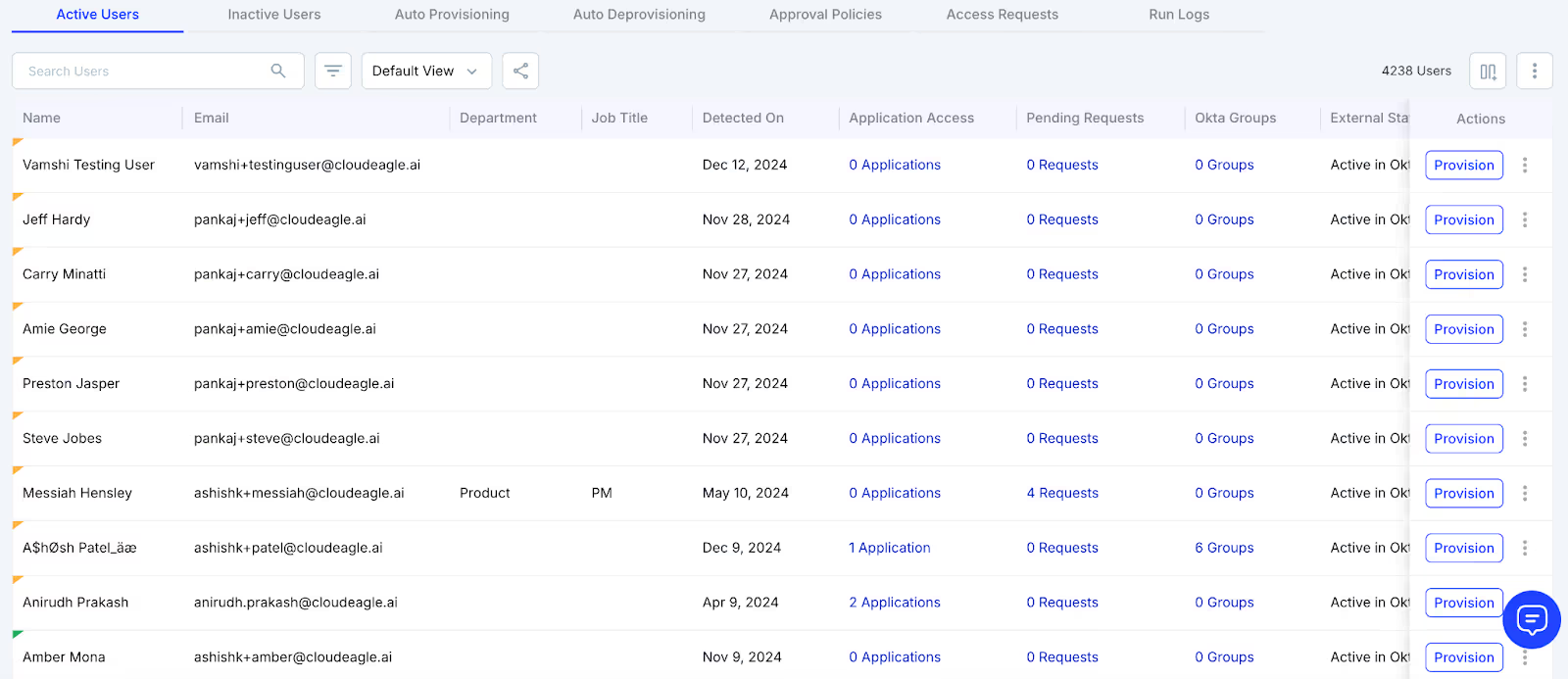
2. Inactive Users: This tab allows you to quickly revoke access from employees who no longer need it. This prevents unauthorized access and ensures security. You can also reclaim licenses for unused apps to avoid unnecessary costs.

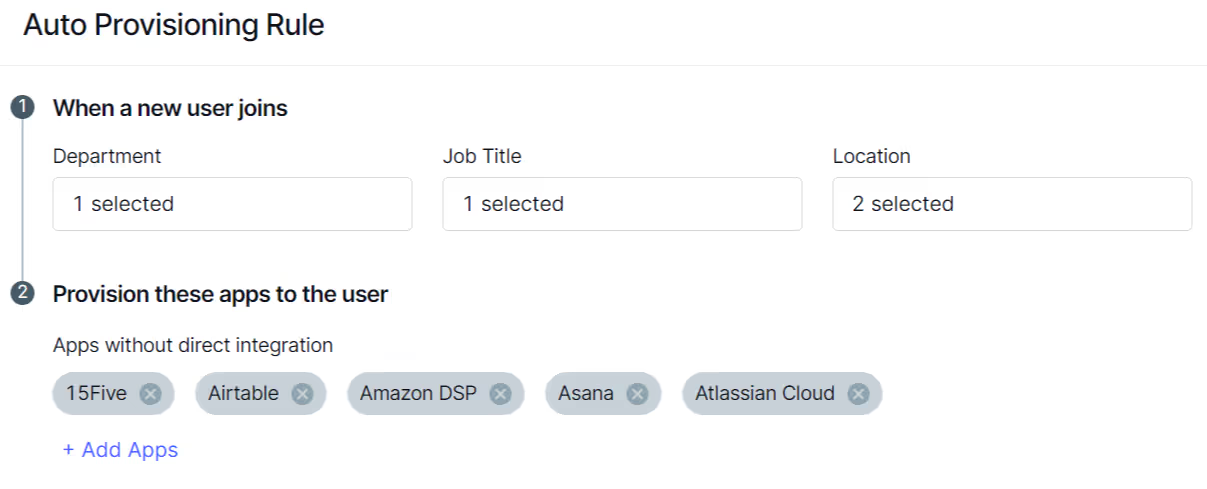
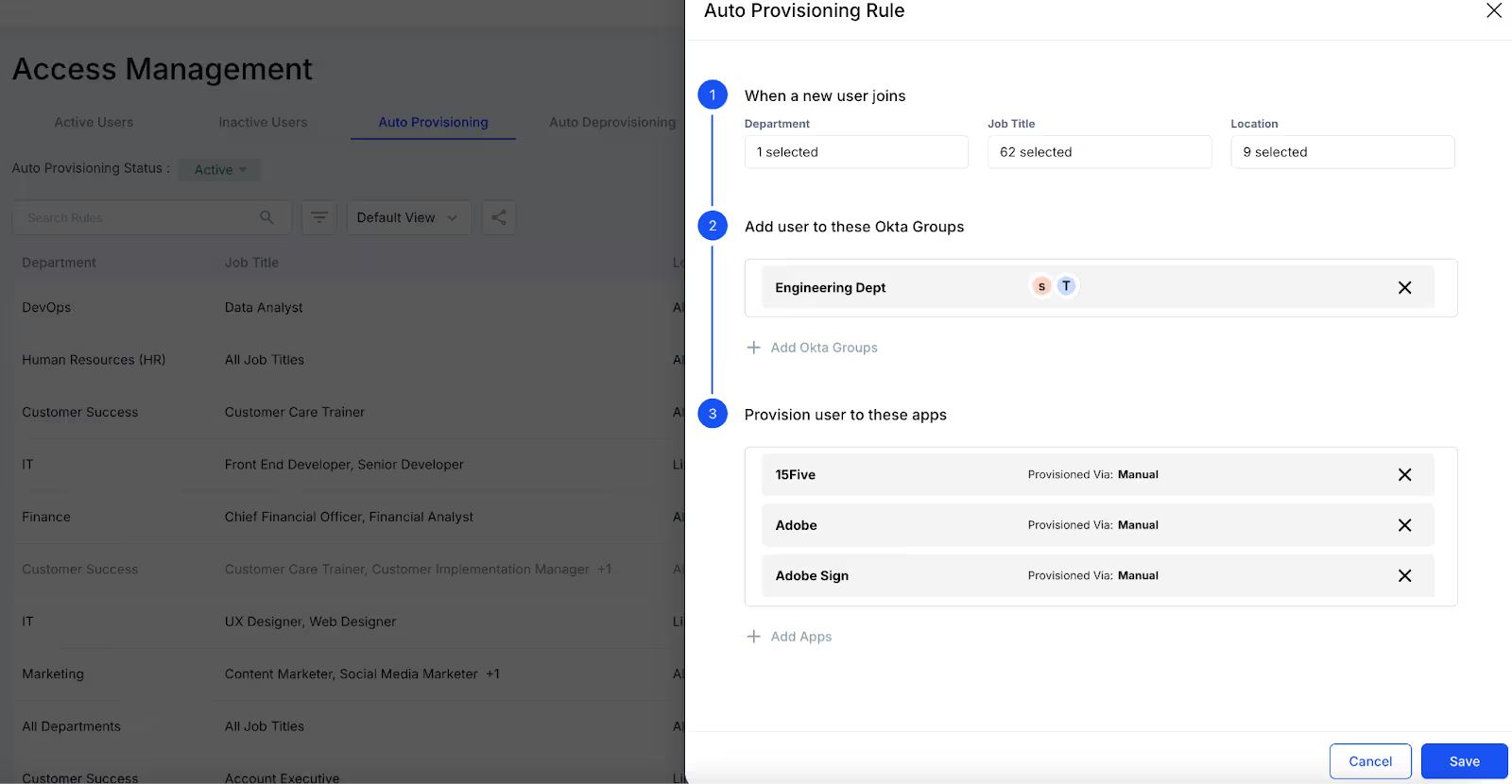
3. Auto Provisioning: Using this tab, you can automate the process of granting access when new employees join or change roles. It saves time and effort by automatically assigning the required applications based on location, department, etc., ensuring users have timely access and reducing administrative work.
4. Auto Deprovisioning: This tab manages two use cases: offboarding and license harvesting. Offboarding removes access when an employee leaves the organization, while license harvesting revokes access when an employee is inactive in an app. Both ensure data security and help optimize license management.
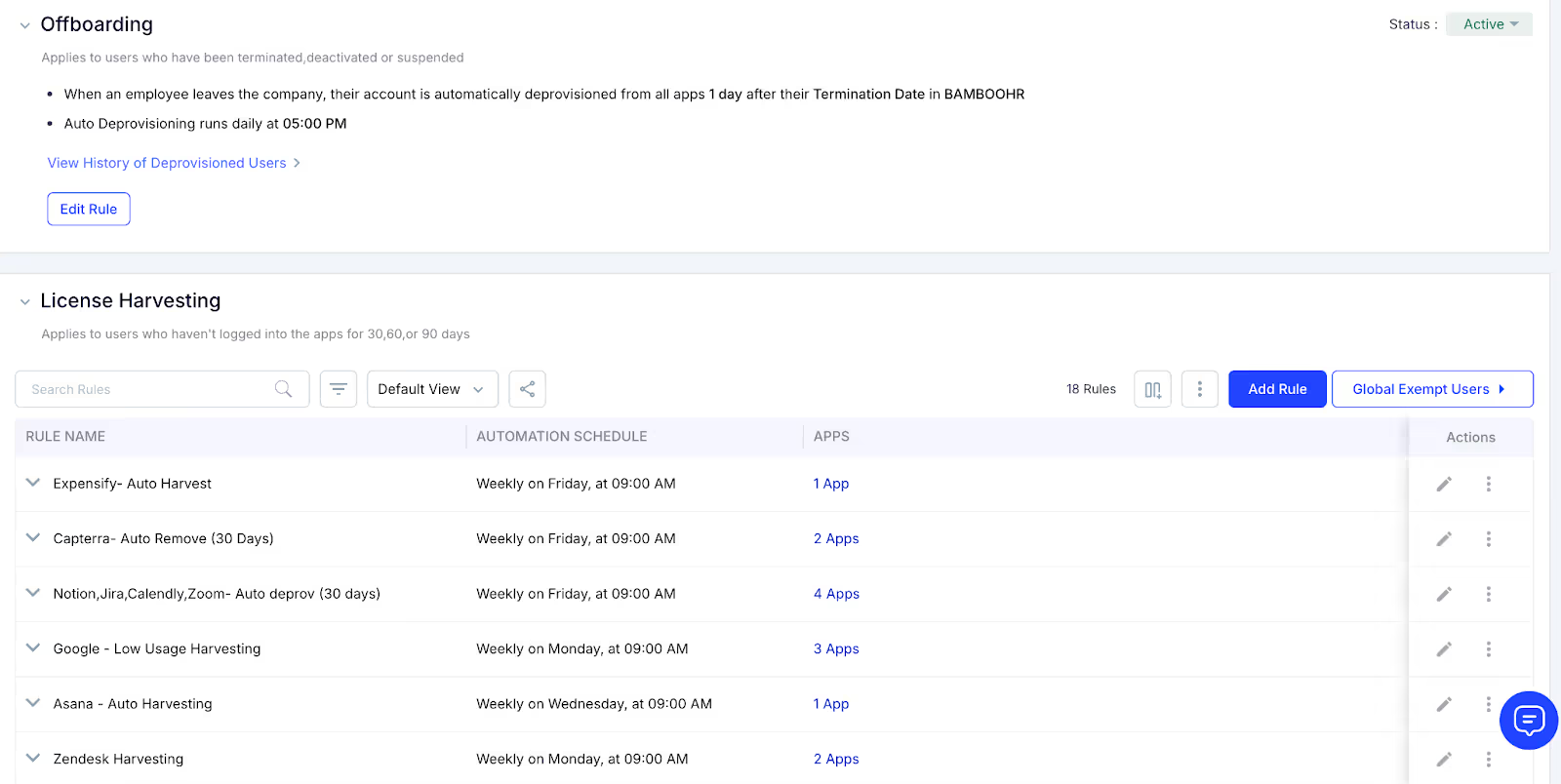
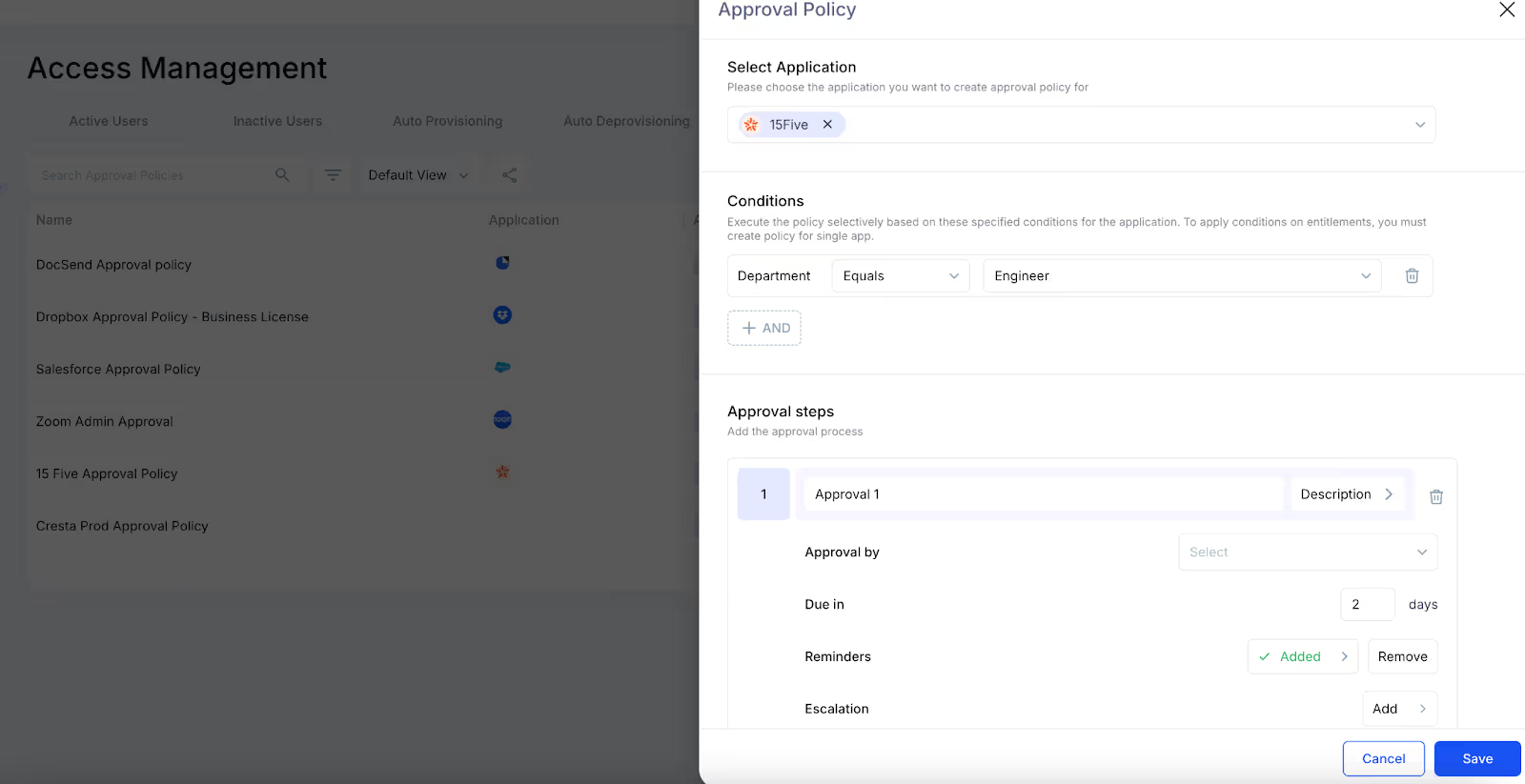
5. Approval Policies: This allows you to define who reviews access requests based on job roles or departments. This ensures that access to sensitive apps is properly approved. For high-risk applications, you can set up multi-step approvals for extra security.
6. Access Requests: This tab helps you streamline the process of requesting and granting access to applications. It allows you to create automated workflows for fast, secure approvals. Users can easily request access, and approvals are handled based on predefined rules.

You can customize your organization’s access settings with the following options:
- Applications & Entitlements: Assign apps and set entitlements like license types and roles.
- Visibility: Control which employees can view and request access to apps, based on departments, cost centers, and other factors, limiting visibility to specific roles, titles, or locations.
- Time-Based Access: Set expiry dates for temporary access to ensure automatic revocation.
- Questions: Collect necessary information by adding questions to the access request form.
- Actions: Automate workflows or approval processes using tools like Okta for real-time access.
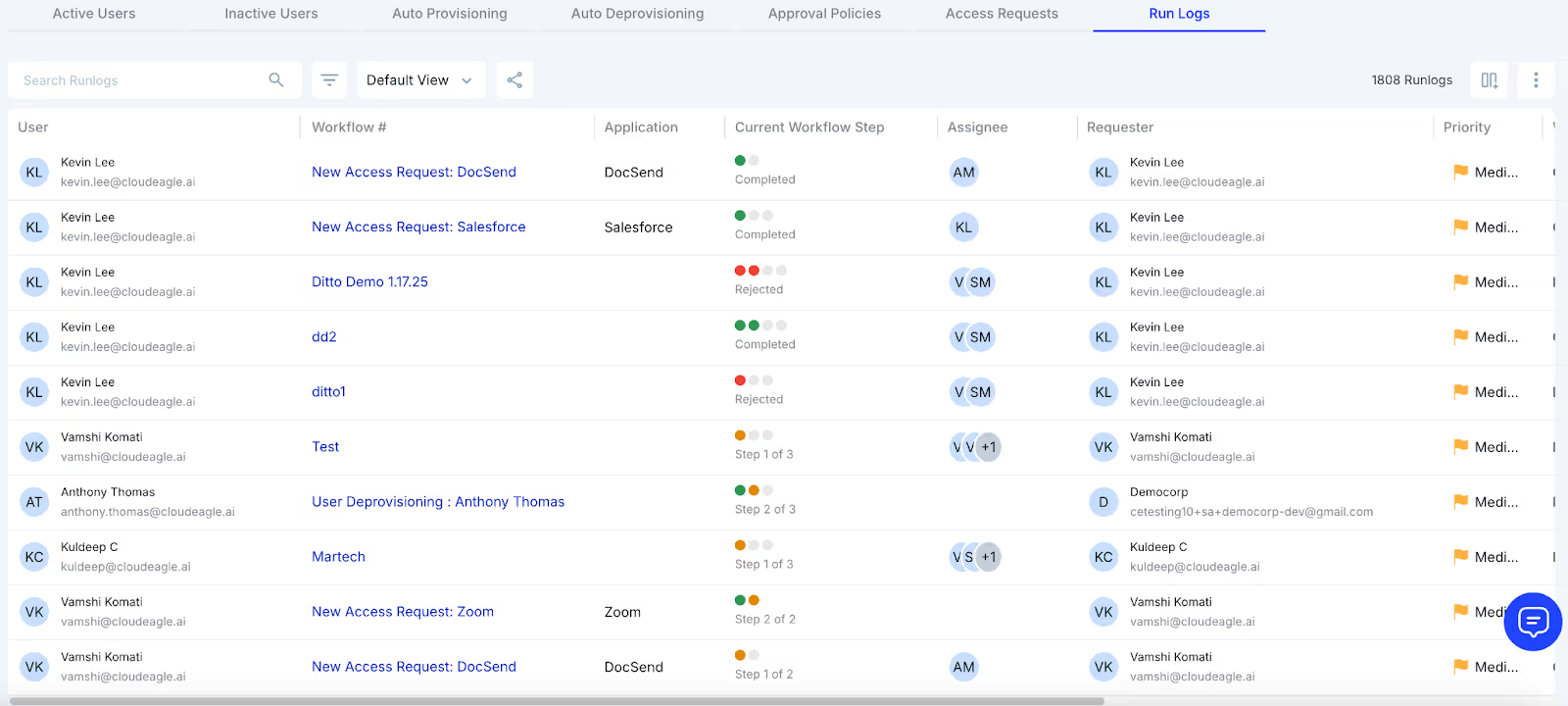
7. Run Logs: It tracks all workflows for access management, user provisioning, deprovisioning, and access requests. It provides visibility into what actions were taken for both active and inactive users.
In a recent SaaS Masterminds podcast, Karl Haviland highlights the need to balance AI-driven innovation with real-world governance for successful transformations. He shares a blueprint for CIOs and CTOs to manage both innovation speed and operational discipline. Check out the video for full insights.
Conclusion
Managing access across multiple SaaS apps can be challenging for CIOs and CISOs. Ensuring that the right people have the right access, while maintaining security and compliance, is no easy task. However, with CloudEagle.ai, this process becomes simple and efficient.
CloudEagle.ai automates access management, ensuring new hires get the right access from day one and departing employees are deprovisioned instantly. With full visibility into who has access to what, CIOs and CISOs can easily maintain control. Compliance reporting is streamlined, errors are minimized, and IT teams save valuable time.
The result? Stronger security, reduced risk, and greater operational efficiency. CloudEagle.ai empowers enterprises with complete control over SaaS access.
Ready to simplify your SaaS access management and boost security?
Schedule a demo with CloudEagle.ai to know how it can transform your access control strategy.

%201.svg)









.avif)




.avif)
.avif)




.png)









