HIPAA Compliance Checklist for 2025

Cyberattacks are rising, and passwords alone no longer keep accounts safe. A Microsoft study found 99.9% of compromised accounts lacked multi-factor authentication, proving the value of added security layers
Two-Factor Authentication (2FA) provides that protection. It requires both a password and a second verification factor, making it much harder for attackers to break in.
For enterprises, the challenge is enforcing 2FA across many SaaS tools. Platforms like CloudEagle.ai help IT teams automate access policies and strengthen access governance.
In this article, we’ll explain what two factor authentication is, how it works, its benefits, and why businesses and individuals should adopt it.
TL;DR
- Two-Factor Authentication (2FA) adds a second layer of security, requiring both a password and another verification method.
- 2FA methods vary, including SMS codes, email verification, authenticator apps, hardware tokens, and biometrics.
- Benefits include stronger protection against password theft, phishing, brute-force attacks, and regulatory compliance.
- Limitations exist, such as device dependency, potential inconvenience, and vulnerabilities in weaker methods like SMS.
- CloudEagle.ai enhances enterprise 2FA, automating access management, onboarding/offboarding, compliance, and privileged access control.
What is Two-Factor Authentication (2FA)?
Two-Factor Authentication (2FA) is a security process requiring two forms of identification before account access. The first factor is something you know, like a password; the second is something you have or are.
Examples include passwords and one-time codes from an authenticator app or mobile device. This extra layer of protection reduces unauthorized access, even if attackers steal a password.
Two-factor authentication 2FA drastically decreases SaaS security risks by requiring two separate proofs for every login attempt. The goal of two factor authentication is to create an additional barrier so that even if attackers steal your password, they still need another form of proof to break in. It works on these principles:
- Something you know: Password, PIN, or security question.
- Something you have: Smartphone, authentication app, or hardware key.
- Something you are: Fingerprint, facial recognition, or voice pattern.
For example, In 2019, Twitter reported that enabling two factor authentication app helped reduce account takeovers significantly, especially for high-profile users who were frequent targets of phishing. This shows how two-factor authentication serves as a strong defense, even on platforms constantly under attack.
How Does Two-Factor Authentication Work?
Two-Factor Authentication adds an extra step to the login process requiring two types of identity proof. Typically, users enter a password (knowledge factor) and a one-time code from a phone or app (possession factor).
Both factors must be verified before granting account access, blocking attackers who only steal your password. This method greatly increases security and reduces the chances of causes of data breaches.
Here’s how it typically works:
Step 1: Enter Username and Password
The user starts with their usual credentials, like an email and password.
Step 2: Provide Second Factor
The system prompts for another form of verification, such as a code from an authentication app, a push notification, or biometric confirmation.
Step 3: Access Granted
Once both factors are verified, the user gains access to the application or system.
This layered approach ensures that even if one factor is compromised, unauthorized access is still blocked. It’s designed to balance stronger security with minimal disruption to user experience.
What are the Different Types of Two-Factor Authentication?
Two-Factor Authentication comes in several forms, each designed to verify identity in a unique way. While all authentication methods share the same goal, the methods vary depending on convenience and risk level.
1. SMS-Based 2FA
SMS-based 2FA is one of the most widely adopted methods because of its simplicity and accessibility. However, while 2FA authenticator adds an extra layer of protection compared to passwords alone, it comes with known weaknesses that organizations must consider.
- Accessibility on all devices: SMS two factor authentication 2FA works on any mobile phone, requiring no additional apps or software to set up.
- Quick adoption by users: Most employees are already comfortable with text messaging, making it easy to roll out.
- Vulnerability to SIM-swapping attacks: Hackers can trick carriers into transferring numbers, intercepting authentication methods.
As cybersecurity expert Troy Hunt once said,
“SMS 2FA is better than nothing, but it’s the first factor you should move away from when possible.”
This quote proves the importance of having a strong SMS-based two factor authentication app enabled.
2. Email Verification Codes
Email verification codes are another common two-factor authentication method, often used for both enterprise and consumer accounts. While convenient, their effectiveness depends heavily on the security of the user’s email account itself.
- Universal availability: Email is a channel nearly every user has, making this authentication method simple to adopt.
- No extra hardware required: Unlike tokens or security keys, users only need access to their inbox.
- Risk of compromised email accounts: If attackers gain access to the inbox, verification codes lose all value.
3. Authenticator Apps
Authenticator apps like Google Authenticator or Microsoft Authenticator generate time-based access on the user’s device. Unlike SMS or email, they don’t depend on networks and are considered more secure.
These apps use Time-Based One-Time Passwords (TOTP), which refresh every 30 seconds. Because the code generation happens locally, attackers can’t intercept it through network-level attacks.
Enterprises prefer authenticator apps because they offer stronger protection without introducing the hardware costs of physical tokens. They’re a middle ground between ease of use and robust security.
4. Hardware Tokens and Security Keys
Physical devices of two factor authentication 2FA like YubiKeys or RSA tokens generate or store authentication codes. A 2FA authenticator provides a high-security barrier but requires users to carry the device.
- Durability: Resistant to phishing, SIM-swapping, and malware-based attacks.
- Drawback: Higher costs and logistical challenges in distribution at scale.
According to a 2023 report by Yubico and Ponemon Institute, organizations using hardware security keys saw a 92% reduction in account takeovers.
5. Biometric 2FA (Face, Fingerprint, Voice)
Biometric authentication uses unique physical traits to verify identity, making it harder to fake or steal. Examples include fingerprint scans, facial recognition, or even voice-based checks.
While highly convenient, biometrics raise concerns about privacy and data storage. Unlike passwords, biometric data from two-factor authentication cannot be changed if compromised, so storage and encryption practices must be airtight.
Still, biometrics are rapidly becoming mainstream due to the built-in support on smartphones and enterprise devices, making them one of the most seamless forms of two factor authentication 2FA.
Why is Two-Factor Authentication Beneficial?
Two-Factor Authentication adds a vital extra layer of security beyond just a password. This significantly reduces risks from stolen credentials, phishing, and malware attacks, improving the effectiveness of passwordless authentication.
2FA protects both personal and business data, helping to prevent identity theft and fraud. It can be required for regulatory compliance in certain industries or sensitive accounts. Let’s see why two-factor authentication is beneficial:
1. Stronger Security Against Password-Based Attacks
Two-Factor Authentication adds an extra layer beyond passwords, making it much harder for attackers to gain entry. Password leaks are common, but with 2FA authenticator, stolen credentials alone aren’t enough to compromise an account.
- Blocks stolen password attempts: Even if a password is leaked in a data breach, attackers still need the second factor.
- Prevents credential stuffing: Automated attacks using reused credentials are stopped by requiring a one-time code or device check.
- Supports stronger identity proofing: Combining “something you know” with “something you have” reduces reliance on weak or reused passwords.
2. Protection From Phishing and Brute Force Attacks
Phishing remains one of the most widespread cyberattack methods. But with two-factor authentication, even if a user falls victim and shares their password, attackers cannot log in without the second factor.
Neutralizes brute force
Automated login attempts cannot bypass the second factor, cutting off large-scale password-guessing attacks.
Stops phishing dead end
Users tricked into sharing credentials still remain protected, since login requires device confirmation.
For example, in 2020, Google mandated two-factor authentication for all employees and reported zero successful phishing attacks afterward.
3. Compliance With Industry Standards and Regulations
Regulators increasingly view 2FA as a baseline security requirement. Organizations in sectors like finance, healthcare, and retail must implement it to safeguard sensitive data. This ensures both customer trust and regulatory alignment.
Many identity governance frameworks, including PCI DSS, HIPAA, and GDPR, explicitly require or strongly recommend two-factor authentication. By deploying two-factor authentication, companies not only reduce risks but also avoid penalties for non-compliance.
For enterprises, compliance-driven 2FA adoption helps create a culture of security awareness while meeting mandatory audit checks. It serves as both a protective measure and a trust-building initiative.
4. Low-Cost Security Measure for Businesses
Unlike advanced security systems, two-factor authentication is relatively inexpensive to implement but provides a strong return on investment. Cloud-based services and authenticator apps allow enterprises to roll it out at scale with minimal overhead.
Studies show its cost-effectiveness. According to Science Direct, more than 71% of online users consider dual factor authentication compared to 2017. This makes it one of the most impactful yet affordable cybersecurity defenses.
For small and medium businesses, this cost-benefit balance makes two-factor authentication a clear winner. It strengthens defenses without straining limited budgets, while ensuring staff and customer accounts remain safe.
How to Setup Two-Factor Authentication?
Implementing Two-Factor Authentication (2FA) may sound technical, but the process is straightforward for both individuals and enterprises. It involves choosing the right method, configuring settings, and ensuring users adopt it consistently.
1. Assessing Business Needs Before Adoption
Before rolling out two-factor authentication, organizations should assess their specific security needs. This ensures that the solution is aligned with business goals and user requirements. A clear evaluation avoids unnecessary costs and enhances user adoption.
Here are some key considerations of dual factor authentication:
Identify critical systems and data
Determine which applications and assets need the highest level of protection.
Evaluate existing authentication methods
See where passwords are failing and how two-factor authentication can fill the gap.
Balance usability and security
Avoid choosing methods that frustrate employees or slow down operations.
Assess compliance requirements
Industries like healthcare or finance may require stricter forms of authentication.
2. Choosing the Right Two Factor Authentication Method
Not every 2FA method suits all businesses. The right choice depends on user workflows, regulatory needs, and budget. A mismatch can lead to poor adoption or even poor SaaS security checklist.
- User convenience: Methods like push notifications or biometrics are easier for employees to adopt.
- Risk level of operations: High-value systems may need hardware keys, while low-risk apps can use SMS or email codes.
- Budget availability: Hardware tokens are more secure but costlier to maintain compared to app-based two-factor authentication.
- Future scalability: Choose a solution that integrates well as the business grows.
3. Educating Employees on 2FA Usage
Even the strongest security measures fail without user understanding. Training employees ensures two-factor authentication is used consistently and effectively across the enterprise. Training strategies include:
- Awareness programs: Explain how 2FA prevents data breaches and improves data loss prevention best practices.
- Step-by-step guides: Provide clear instructions for setting up and using two-factor authentication on devices and apps.
- Hands-on workshops: Let employees practice enrolling and using tokens, apps, or biometrics.
- Support channels: Offer IT helpdesks or FAQs to solve common issues quickly.
4. Integrating 2FA With IAM or SSO Platforms
For larger organizations, 2FA is most effective when integrated with Identity and Access Management (IAM) or Single Sign-On (SSO) tools. This streamlines authentication and reduces login fatigue.
- Centralized control: Manage user identities and authentication policies from a single dashboard.
- Seamless access: Allow employees to log in once and access multiple apps securely.
- Role-based enforcement: Apply stricter two-factor authentication for sensitive roles like finance or IT admins.
- API and vendor compatibility: Ensure the chosen 2FA method works with IAM or SSO solutions already in use.
5. Testing and Monitoring 2FA Deployment
Deployment doesn’t end with activation, regular testing and monitoring ensure the system remains effective. A proactive approach helps detect gaps before attackers exploit them. Ongoing measures include:
- Pilot testing: Start with a small group before a full-scale rollout.
- User feedback collection: Monitor pain points to improve usability and adoption.
- System monitoring: Track login attempts, failures, and suspicious activities.
- Regular updates: Ensure authenticator apps and hardware tokens are patched against new insider threats.
How to Turn Off Two-Factor Authentication?
Disabling two-factor authentication (2FA) is generally discouraged, but there are situations where it may be necessary. For example, a business may switch to a new authentication provider, or an individual may need just-in-time access without two-factor authentication due to a lost device.
The process to turn off dual factor authentication usually involves:
- Logging into the account with existing 2FA enabled.
- Navigating to the Security or Account Settings page.
- Locating the 2FA or Multi-Factor Authentication (MFA) section.
- Selecting the option to disable or turn off 2FA, often requiring a final confirmation.
It’s important to note that disabling two-factor authentication significantly lowers account security. As cybersecurity expert Troy Hunt once said:
“Removing 2FA is like leaving your front door unlocked just because finding your keys takes time.”
If you must turn it off, enable alternative security measures such as strong, unique passwords and consider re-enabling two factor authentication as soon as possible.
What are Some Disadvantages of Two-Factor Authentication?
While two-factor authentication (2FA) greatly enhances security, it also comes with certain drawbacks. These challenges can affect both enterprises and individuals, especially when convenience and accessibility are priorities.
User Frustration and Inconvenience
Entering codes, using tokens, or waiting for SMS messages can slow down logins. For employees handling multiple accounts daily, this friction may reduce productivity.
Dependence on Devices or Connectivity
Many two-factor authentication methods rely on smartphones, email access, or stable internet connections. Losing a device or facing connectivity issues can lock users out of critical accounts.
Vulnerabilities in Certain 2FA Methods
SMS-based two-factor authentication, while popular, is vulnerable to SIM-swapping and phishing attacks. Attackers may still exploit weak implementations to bypass protections.
Though 2FA is not perfect, these disadvantages are usually outweighed by its benefits. However, companies must carefully choose the right 2FA methods and provide adequate support to minimize disruptions.
Two-Factor Authentication vs Multi-Factor Authentication
Two-factor authentication (2FA) and multi-factor authentication (MFA) are both security mechanisms, but they differ in complexity and protection levels. Two-factor authentication requires two forms of verification, typically a password and a second factor such as a code or biometric.
MFA, on the other hand, may require two or more factors, often combining knowledge (password), possession (token or phone), and inherence (biometric). This layered approach provides stronger security for sensitive systems and high-risk accounts.
Security Depth
MFA adds more layers than 2FA, making it more resilient to credential theft or phishing. Organizations handling sensitive financial or healthcare data often prefer MFA over standard two-factor authentication.
User Experience
2FA is simpler and easier for users, with fewer steps to complete. MFA may introduce slightly more friction but delivers enhanced security against sophisticated attacks.
Implementation Considerations
Businesses should assess risk tolerance, compliance requirements, and user convenience. For most enterprises, combining MFA with single sign-on (SSO) creates a robust and user-friendly solution.
Securing Your Enterprise’s Access With CloudEagle.ai
CloudEagle.ai empowers IT, procurement, and security teams to gain complete control over their SaaS ecosystem. With over 500 integrations spanning finance, SSO, and HRIS, the platform delivers full visibility into applications, licenses, vendors, and spending.
It also streamlines identity and access management. Through a unified dashboard and Slack-enabled workflows, IT teams can automate onboarding, offboarding, access reviews, and license assignments, saving time and reducing security risks.
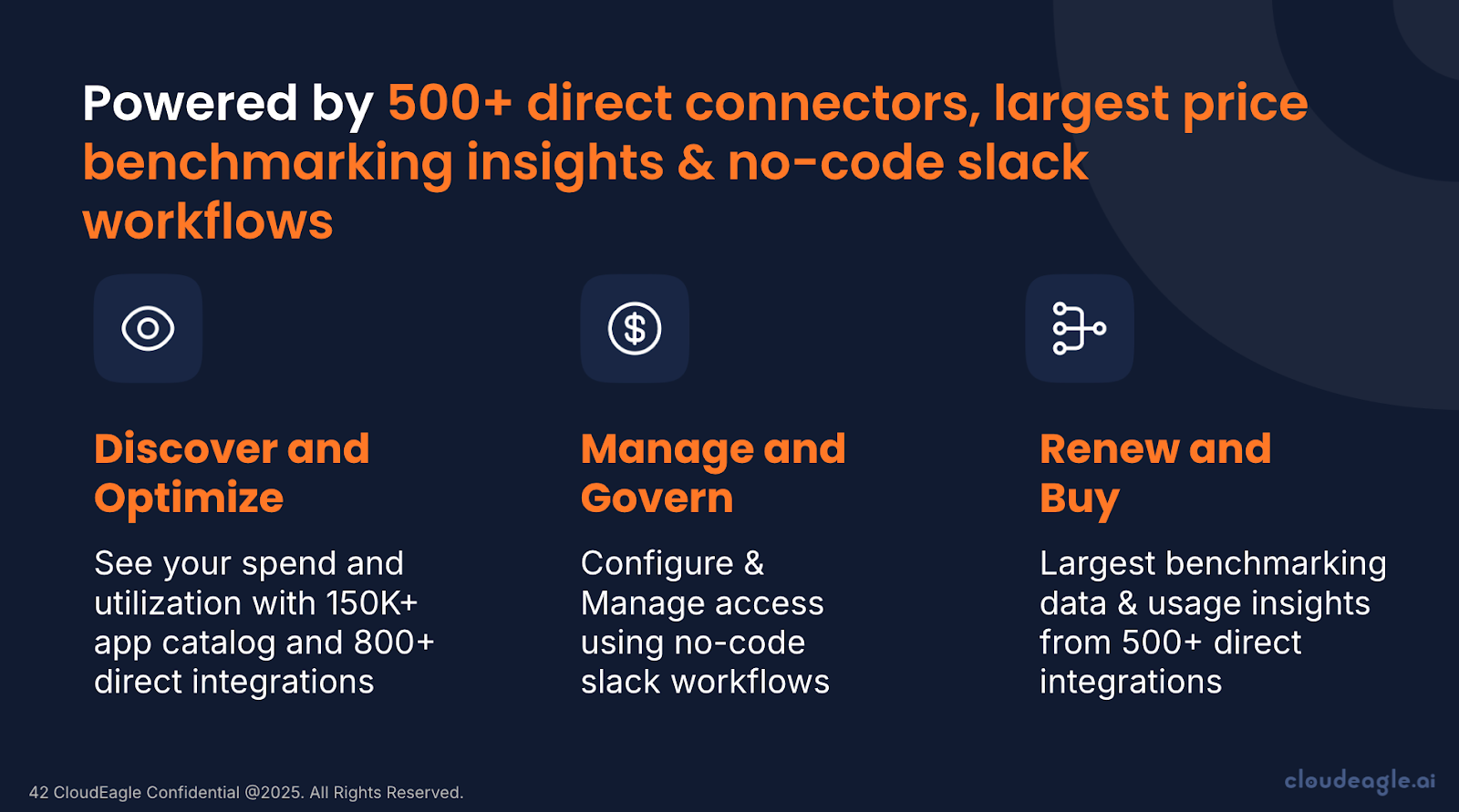
Enterprises like RingCentral, Shiji, and Rec Room rely on CloudEagle.ai to cut SaaS costs by 10–30%. With $3.5B in processed spend and over $250M in customer savings, the platform demonstrates measurable impact. Rapid 30-minute onboarding ensures immediate governance improvements and cost savings.
Just-in-Time Access
Temporary licenses often remain after tasks are completed, creating security risks and unnecessary costs. CloudEagle.ai addresses this by granting just-in-time access only for the required duration and automatically revoking it afterward.
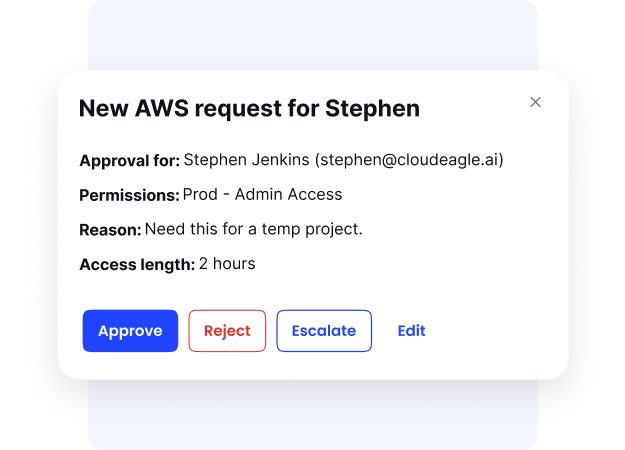
This reduces unauthorized access, cuts license waste, and simplifies governance through automated controls.
Employee App Access Catalog
Many employees don’t know which tools they can request, while IT spends hours handling approvals via emails, Slack, or tickets. Even with JIRA or ServiceNow, maintaining accurate app lists is manual, incomplete, and can lead to shadow IT, redundant purchases, and security gaps.
CloudEagle.ai centralizes app access in a dynamic self-service catalog, automatically updated through 500+ integrations. Employees see only relevant tools, Sales accesses Salesforce, Engineering accesses AWS, and requests flow through automated approvals with full audit trails.

The result: IT resolves requests up to 80% faster, onboarding happens in minutes, shadow IT shrinks, compliance reporting is effortless, security improves, and SaaS waste decreases.
Automated App Access Reviews
Traditional access reviews are slow, error-prone, and often infrequent, leaving former employees or risky users with prolonged access.
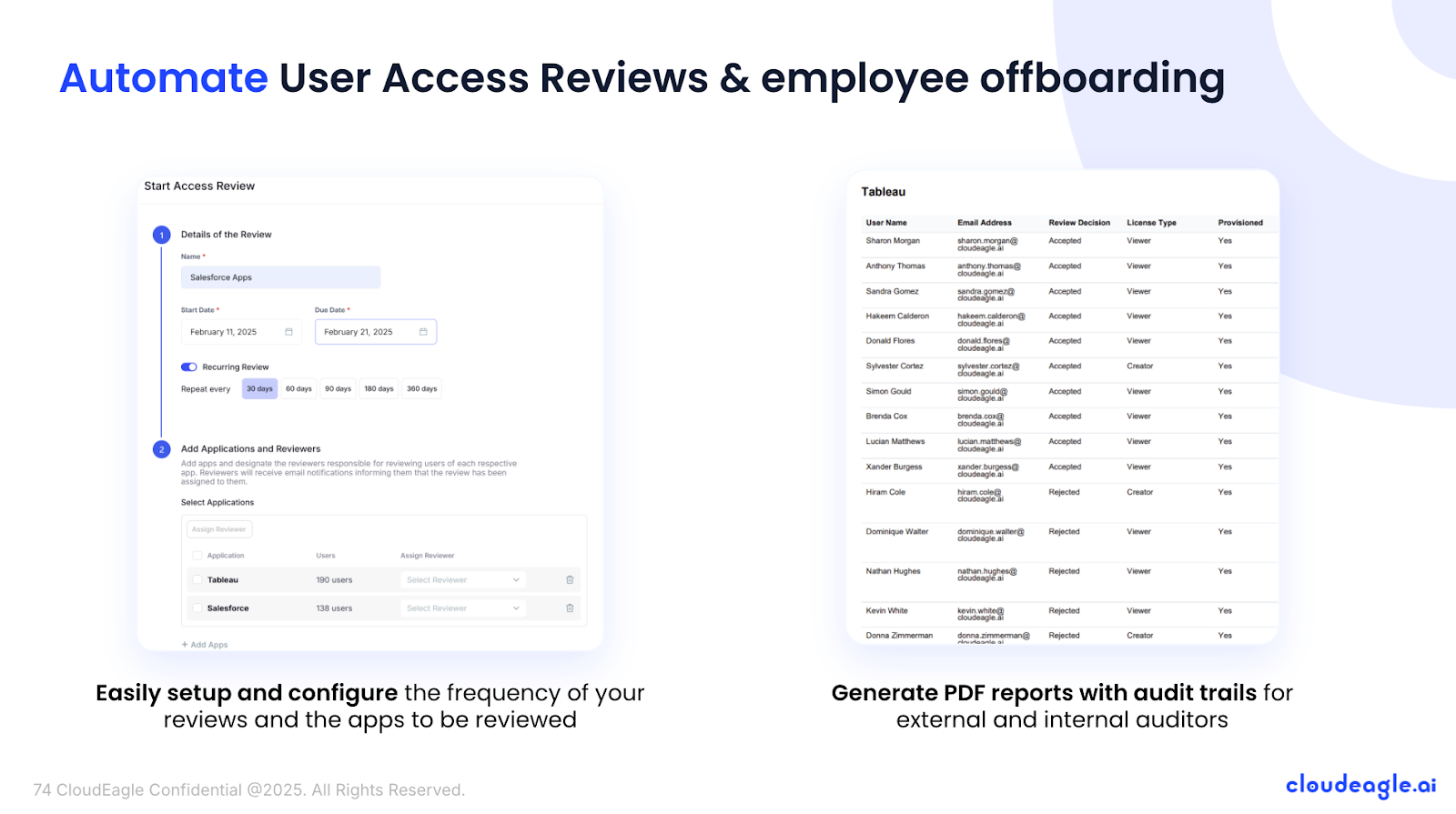
CloudEagle.ai automates these reviews, providing a centralized dashboard for IT and app owners to track roles, schedule reviews, and stay SOC 2 compliant.
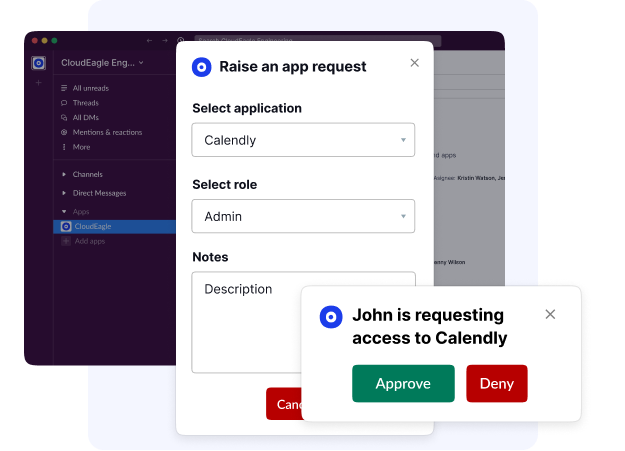
High-risk users are flagged, and deprovisioning takes just a few clicks. Access reviews become faster, security more proactive, and compliance always audit-ready.
Access Control
CloudEagle.ai provides full transparency into application access control, including who has access, the reasons behind it, and how they utilize it. With centralized access control, it oversees the entire access lifecycle, from request to provisioning and deprovisioning, all within a single platform.
Additionally, the platform simplifies compliance and security audits by offering instant access to application logs. Detailed access records can be exported directly, making audit preparation seamless and hassle-free.
Privileged Access Management
CloudEagle.ai streamlines privileged access management by automating the assignment of elevated access, ensuring that only authorized users can access critical systems like AWS and NetSuite, thereby reducing the risk of unauthorized activity.
With continuous monitoring and automated controls, the platform strengthens security and compliance while easing administrative workloads and minimizing human error.
Employee Onboarding and Offboarding
Manual onboarding and offboarding are slow and error-prone, leaving lingering access and wasting licenses. CloudEagle.ai automates the process with zero-touch workflows, using role-based rules to provision or revoke access instantly across all applications.

Freed licenses automatically return to the pool, maximizing resource efficiency. Companies like Health Ceramics have significantly improved operational efficiency using CloudEagle.ai for deprovisioning.
For instance, Health Ceramics leveraged CloudEagle.ai to automate deprovisioning, significantly boosting operational efficiency.
Compliance Management
CloudEagle.ai centralizes SaaS compliance oversight, continuously scanning for vulnerabilities, managing certifications, facilitating audits, and monitoring account activity for full visibility.
With CloudEagle.ai, enterprises can protect sensitive data, streamline access management, and maintain compliance across all SaaS applications.
Conclusion
Two-factor authentication (2FA) and multi-factor authentication (MFA) are essential tools for protecting digital assets. While 2FA offers a simple layer of security, MFA provides stronger protection for sensitive systems.
Implementing the right authentication method ensures better SaaS risk management, compliance, and user confidence. Enterprises can start by evaluating their security needs and gradually adopting MFA to safeguard critical accounts.
Secure your organization today with robust access controls and passwordless solutions. See how CloudEagle.ai can simplify access control and compliance.
FAQs
1. What are two examples of two-factor authentication?
Two common examples of 2FA are SMS-based codes sent to phones and authenticator app codes. Both add a second layer beyond passwords.
2. Is OTP two-factor authentication?
Yes, a one-time password (OTP) can serve as a second factor when paired with a password. This combination strengthens account security.
3. Who uses two-factor authentication?
Businesses, financial institutions, and individual users employ 2FA to protect sensitive accounts and digital resources from unauthorized access.
4. Is password and fingerprint a two-factor authentication?
Yes. A password (knowledge factor) combined with a fingerprint (biometric factor) counts as two-factor authentication.
5. Can I be hacked if I have 2FA?
2FA significantly reduces risk but isn’t foolproof. Sophisticated phishing, malware, or SIM swap attacks can bypass it.

%201.svg)









.avif)




.avif)
.avif)




.png)









