HIPAA Compliance Checklist for 2025

In an era where data stands as one of the most valuable assets, enterprises face a growing and complex risk of data loss. Sensitive information ranging from customer details and financial records to intellectual property can be compromised not only through cyberattacks but also by accidental leaks or insider errors.
These breaches result in severe financial penalties, regulatory scrutiny, and lasting damage to a company’s reputation. Despite the critical nature of these threats, many enterprises struggle to fully understand what data loss prevention entails and how to implement an effective data loss prevention strategy.
As work moves remote, SaaS use grows, and data flows get complex, we need smart data loss prevention techniques to watch and stop risks quickly. Knowing good data loss prevention methods and having a strong plan is very important.
Let’s explore the top 10 key data loss prevention best practices every enterprise should follow to protect sensitive data.
TL;DR
- Identify and classify your data as public, confidential, or restricted to protect key information and follow privacy laws; an important data loss prevention best practice.
- Encrypt sensitive data when stored and transmitted to block unauthorized access, which is an essential data loss prevention technique.
- Control data access using roles, least privilege, multi-factor authentication, and regular reviews as part of a solid data loss prevention strategy.
- Monitor data movement and train employees on safe data handling to prevent leaks, following effective data loss prevention methods.
- Use automated data loss prevention tools with AI for real-time threat detection and update policies often to keep your data loss prevention framework strong and up to date.
What is Data Loss Prevention?
Data Loss Prevention, or DLP, helps enterprises keep their important information safe. It uses advanced security tools and rules as part of effective data loss prevention techniques to stop sensitive data, such as customer info, financial records, or company secrets, from being lost, stolen, or accidentally shared with the wrong people.
DLP works by monitoring how data moves within a company and blocking actions that could put that data at risk. For example, it can stop someone from sending confidential files outside the company, either by mistake or intentionally.
This protects companies from costly fines, reputational damage, and helps them comply with important data privacy laws, making it a central part of any strong data loss prevention strategy.
What Are The 4 Types of DLP?
Data Loss Prevention (DLP) can be categorized into four main types, each focusing on protecting data in different states and environments, an essential part of understanding how data loss prevention works within a comprehensive data loss prevention framework.
Network DLP: Monitoring Data in Motion
Network DLP focuses on tracking and controlling sensitive data as it travels across an enterprise’s network. It monitors emails, web traffic, and other data transmissions to detect and block unauthorized sharing or leakage of confidential information. This is a key data loss prevention technique to secure data in transit.
Endpoint DLP: Securing Data on Devices
Endpoint DLP protects data stored and used on individual devices such as laptops, desktops, and mobile devices. It prevents data from being copied, transferred to external drives, or shared in unauthorized ways directly from these endpoints, aligning with effective data loss prevention methods.
Storage DLP: Protecting Data at Rest
Storage DLP targets data that is stored within databases, file servers, and other storage locations. It ensures that sensitive information residing on these platforms is properly secured and access is limited to authorized users only. This technique is central to any solid data loss prevention strategy.
Cloud DLP: Managing Data Across SaaS and Cloud Platforms
Cloud DLP addresses the protection of data stored or processed in cloud environments and SaaS applications. It helps monitor and control the flow of sensitive data in cloud platforms to prevent exposure or unauthorized access, which is especially important given the rise in SaaS adoption and is part of data leakage prevention best practices.
Why is Data Loss Prevention Important for Enterprises?
The global data loss prevention market is growing fast, expected to reach $10 billion by 2030. This shows how important DLP is for protecting data.
Data Loss Prevention (DLP) is crucial for enterprises to protect their most valuable asset—their data. Here’s why having a strong data loss prevention strategy matters:
Protect Sensitive Data: Enterprises handle a lot of confidential information, like customer details and financial records. Implementing effective data loss prevention techniques helps keep this data safe by stopping leaks and preventing unauthorized access, which is a core goal of data loss prevention best practices.
Stay Compliant with Laws: Regulations like GDPR and HIPAA require businesses to protect sensitive data. Using proper data loss prevention methods makes it easier to follow these rules and avoid heavy fines by controlling who can access and share information.
Stop Insider and Outside Threats: Not all risks come from hackers, sometimes employees accidentally or intentionally cause data leaks. DLP monitors how data is used and spots unusual behavior before it causes damage, demonstrating how data loss prevention works to prevent internal threats.
Keep Your Business Running Smoothly: Data breaches can disrupt work and hurt your reputation. With a strong data loss prevention framework, risks are caught early so your company can avoid downtime and recover quickly.
Build Trust with Customers: When customers know you protect their data, they feel confident doing business with you. A solid data loss prevention strategy shows you take data security seriously and helps build lasting relationships.
Save Money: Data breaches can be very expensive, with costs from fines, legal fees, and fixing the damage. Preventing leaks with data loss prevention best practices helps you avoid these costs and protect your bottom line.
Top 10 Data Loss Prevention Best Practices
Protecting sensitive data is crucial for enterprises to avoid breaches, follow industry regulations, and keep customer trust. About 2 out of 3 companies faced data loss last year, making DLP essential to keep data safe.
A strong data loss prevention (DLP) strategy helps secure valuable information from accidental loss or theft.
Here are the top data loss prevention best practices:
1. Classify Data Based on Sensitivity Levels
The first step in protecting your data is to understand what it is and how sensitive it is. Enterprises handle a wide variety of data, ranging from general public information to highly confidential details like customer personal data, financial records, or trade secrets.
By classifying your data into different sensitivity levels, such as public, internal use only, confidential, and restricted, you can focus security efforts on protecting the most valuable and vulnerable information. This is a key data loss prevention technique.
This classification also helps with regulatory compliance because many privacy laws require special handling of personal or sensitive data. Proper classification means you apply the right protection measures where they matter most, optimizing security resources and reducing risk, which is part of a solid data loss prevention framework.
2. Use Encryption for Data at Rest and in Transit
Encryption is a strong security method that changes your data into a form unauthorized users can’t read. It’s an important data loss prevention technique to encrypt data both when it’s stored (“at rest”) and when it’s being sent (“in transit”).
Encrypting data at rest protects it if a device is stolen or storage is hacked. Encrypting data in transit stops it from being intercepted while moving across networks. These encryption methods are key parts of any good data loss prevention strategy.
Using strong standards like AES-256 for storage and TLS for transmissions ensures stolen or intercepted data is useless without the keys. Proper key management is also essential to keep encryption strong and your data safe, following trusted data loss prevention best practices.
3. Implement Strong Access Control Policies
Effective access control policies ensure that only authorized people can access sensitive data. Permissions are given based on the principle of least privilege, meaning users can only access the data they need for their specific roles. This is an important data loss prevention technique.
RBAC helps organize user permissions efficiently by grouping users based on their job functions. Adding multi-factor authentication (MFA), where users must provide two or more proof points like a password plus a fingerprint or mobile code, adds an extra layer of security. These methods form core parts of a robust data loss prevention strategy.
“Privilege creep is like giving a former employee a key and forgetting about it — it piles up creating security gaps.” — John Smith, Cybersecurity Analyst
Regularly checking who can access data, especially when employees change roles or leave, is important to stop unauthorized access. Tightening access controls lowers risks from insider threats and external attacks using stolen credentials, key goals in a strong data loss prevention framework.
4. Monitor Data Movement Across Networks and Devices
Data flows constantly across various parts of an enterprise, from internal servers to employee laptops and SaaS applications. It is important to monitor data movement closely to detect any unusual or unauthorized activity that might indicate a data breach or leak.
Network monitoring tools track data packets across your network, while endpoint monitoring watches data use and transfers on individual devices like smartphones and laptops. Monitoring SaaS environments helps secure data stored or processed externally, which follows leading data loss prevention techniques.
Real-time alerts notify security teams of suspicious data transfers, large downloads, or accesses outside of normal hours. This constant vigilance helps catch threats early, preventing data loss before it escalates into bigger problems.
5. Educate Employees on Data Loss Prevention Best Practices
Employees play a crucial role in data security, both as defenders and potential weak points. Most data loss prevention efforts involve addressing human error, such as mishandling data or falling victim to phishing scams.
Regular, engaging training programs help employees understand how to identify security risks, follow company policies, and use secure methods for handling sensitive information.
Training should cover recognizing suspicious emails, securely sharing data, avoiding weak passwords, and knowing what to do in case of a suspected breach.
6. Establish Incident Response Plans for Data Breaches
Even with diligent preventive measures, data breaches can still occur. Being prepared with a well-defined incident response plan ensures your team can act quickly and effectively when a security event happens. This is an important part of a comprehensive data loss prevention strategy.
This plan should clearly assign roles and responsibilities, outline steps to contain and investigate the breach, communicate internally and externally, and meet any legal reporting requirements. Regular drills and updates to your incident response plan make sure your team stays ready and reduces the impact of breaches.
Effective incident response helps minimize damage, reduce downtime, and protect your company’s reputation by showing you handle incidents responsibly within your data loss prevention framework.
7. Regularly Audit and Review Data Access Logs
Keeping detailed logs of all data access and reviewing them periodically is a key way to detect unauthorized or suspicious activities, which is an essential data loss prevention technique.
Logs record who accessed what data, when, and where from, allowing security teams to spot patterns such as repeated failed login attempts, unusual download volumes, or access from unexpected locations.
Automated tools can help analyze large volumes of log data quickly. Regular audits promote accountability among users and help identify gaps or weaknesses in access controls.
These insights support continuous improvement of your security policies and provide valuable evidence in the event of investigations or compliance audits, helping enforce data loss prevention best practices.
8. Leverage Automated DLP Tools and AI-Based Detection
Today’s data environments are too complex for manual monitoring alone. Automated data loss prevention solutions use advanced technology, including AI and machine learning, to continuously scan data flows, user actions, and network activities. This is a cutting-edge data loss prevention technique.
AI helps reduce false alarms by learning normal usage patterns and spotting deviations more accurately. These tools can automatically enforce policies by blocking risky actions (like unauthorized file sharing), encrypting sensitive data, or alerting security teams in real time.
Using automated detection not only strengthens security but also frees up resources for higher-level analysis and response, making your data protection more efficient and effective, aligning with current data loss prevention best practices.
9. Apply Data Masking and Tokenization Techniques
Sometimes sensitive data must be used in less secure places like development, testing, or when sharing with third parties. Data masking hides real data by replacing it with fake but realistic values, letting users work safely without risking exposure. This is an advanced data loss prevention technique.
Tokenization swaps sensitive data with unique tokens that only authorized systems can link back to the original data. Both methods keep data useful while protecting privacy.
They are especially important for following rules about personal and payment data, lowering risks in non-production environments. Using these methods is part of effective data loss prevention best practices to protect sensitive information.
10. Continuously Update Policies to Adapt to Emerging Threats
Cyber threats and attack techniques evolve rapidly, so a static security approach is insufficient. It is critical to regularly review and update your data loss prevention strategy, tools, training programs, and incident response plans to address new vulnerabilities and changing regulatory requirements.
Stay updated by following threat reports and industry news. Using feedback from audits and real incidents helps your business adapt fast. A flexible, constantly improving data loss prevention framework keeps your protections strong and helps you stay ahead of new cybersecurity risks.
How CloudEagle.ai Can Help Manage and Secure Access to Data?
CloudEagle.ai is an advanced SaaS management and access governance platform that helps enterprises manage and secure access to their sensitive data effectively. It easily connects with over 500 popular SaaS apps, including security tools like SIEM, IAM, and CASB.
Plus, its AI-powered features strengthen data loss prevention (DLP) strategies to protect important information in SaaS environments.
Here’s how CloudEagle.ai helps enterprises manage and secure data access in detail:
Comprehensive Visibility into Data Access
CloudEagle.ai provides enterprises with real-time, comprehensive visibility into who is accessing data across SaaS environments. It continuously monitors data usage, user activities, and access patterns, allowing enterprises to track sensitive data movement and detect any anomalies.

This visibility helps enterprises ensure that data access aligns with security policies and that any unusual or unauthorized activity is quickly identified, supporting effective data loss prevention best practices.
Know this inspiring story of how Heath Ceramics got a better understanding of their SaaS apps and usage with CloudEagle.ai.
Identifying Shadow IT
CloudEagle.ai uses its advanced AI-powered SaaS discovery engine to find and eliminate Shadow IT; apps and software employees use without IT’s knowledge. It connects with many systems, like login tools, HR, and finance, to see all the apps your company uses.

It detects every unauthorized or duplicate app being used and sends alerts immediately. Then, it automatically asks users why they need these apps, so IT can decide if they are safe or should be removed. By finding and removing these hidden apps, CloudEagle.ai helps keep your data safe and reduces wasted spending on unused software.
“You back up the data you know about, but what about the data you don’t see? Shadow IT and Shadow AI are big challenges.” — Steve Petryschuk, Director at Auvik
Automated User Provisioning and Deprovisioning
CloudEagle.ai simplifies the process of managing user access by automatically handling permissions when employees join, move within, or leave an organization.
When a new employee starts, the system instantly grants them the right access to the apps and data they need based on their role. This means there’s no waiting for IT to manually set up accounts, speeding up onboarding.

Similarly, when someone leaves the company or changes roles, CloudEagle.ai automatically removes their access. This prevents former employees or role changers from keeping permissions they no longer need, which is a common cause of security risks.

This automation not only reduces the workload for IT teams but also helps prevent outdated or excessive access rights that could lead to data loss or insider threats, which is part of a strong data loss prevention strategy.
Know how Bloom & Wild streamlined employee onboarding and offboarding with CloudEagle.ai.
Just-In-Time Access Management
CloudEagle.ai uses just-in-time (JIT) access to improve security by granting temporary access only when it’s needed. Rather than giving permanent permissions, users receive access for a specific purpose and only for a limited time. Once the task is finished or the time limit expires, the access is automatically revoked.
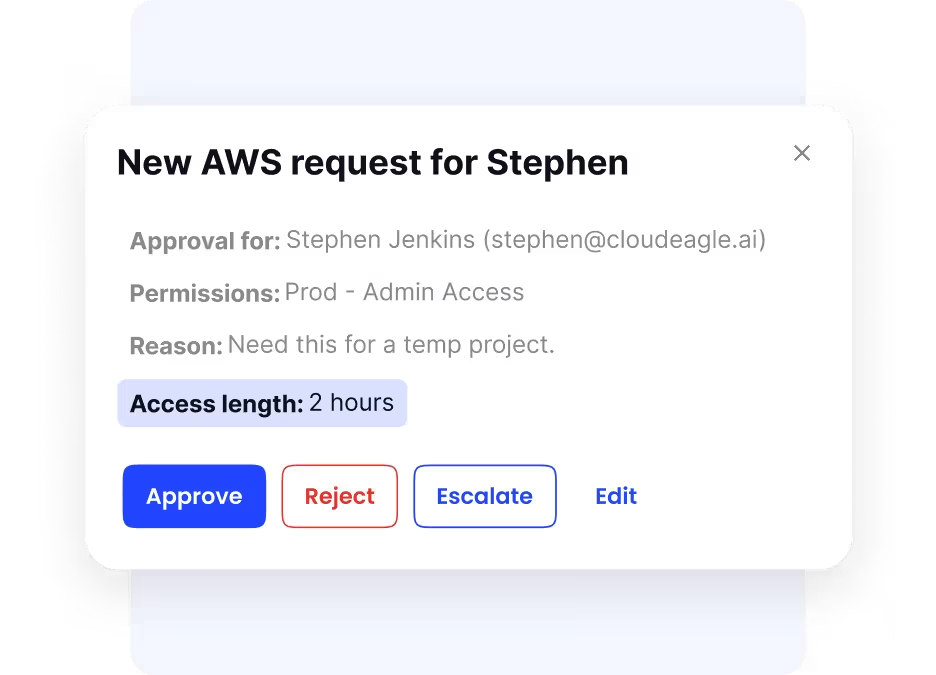
Just-In-Time Access Management
This minimizes the window during which sensitive data is exposed, reducing the chance of unauthorized use or accidental leaks. JIT access is especially helpful for contractors, temporary staff, or employees who occasionally need elevated privileges and supports a proactive data loss prevention framework.
Role-Based Access Control (RBAC)
Managing access can get complicated when each employee has different needs. CloudEagle.ai makes it simple by grouping users into roles based on their job functions. Each role, such as sales, finance, or HR, has predefined permissions that determine what data and applications members can access.

When a user is assigned to a role, they automatically inherit the correct access rights, which keeps things consistent and easier to manage. If a person changes roles in the company, their permissions are updated accordingly without manual intervention. This approach reduces errors, speeds up policy enforcement, and helps maintain strong security standards, all aligning with effective data loss prevention best practices.
Automated Access Control Enforcement
Managing and reviewing access permissions manually can be complex and error-prone, especially in dynamic SaaS environments. CloudEagle.ai automates access control by enforcing granular policies that restrict who can access sensitive data based on user roles, device types, and other contextual factors.

This automation ensures that access is granted strictly according to the principle of least privilege, reducing the risk of over-privileged users and data exposure, a key data loss prevention technique.
Centralized Policy Management and Compliance Reporting
CloudEagle.ai offers a centralized dashboard for managing data access policies across all SaaS environments, simplifying governance for enterprises with complex cloud architectures.

It helps organizations stay compliant with regulatory requirements such as GDPR, HIPAA, and PCI DSS by providing detailed audit trails, access logs, and compliance reports. This centralized control streamlines audits and reduces the operational burden on security teams, helping enforce data loss prevention best practices.
Self-Service Application Catalog
CloudEagle.ai includes a convenient self-service catalog where employees can easily find and request access to approved SaaS applications they need for their work. Instead of submitting manual access requests and waiting for IT approval, users can browse available apps and submit access requests directly.
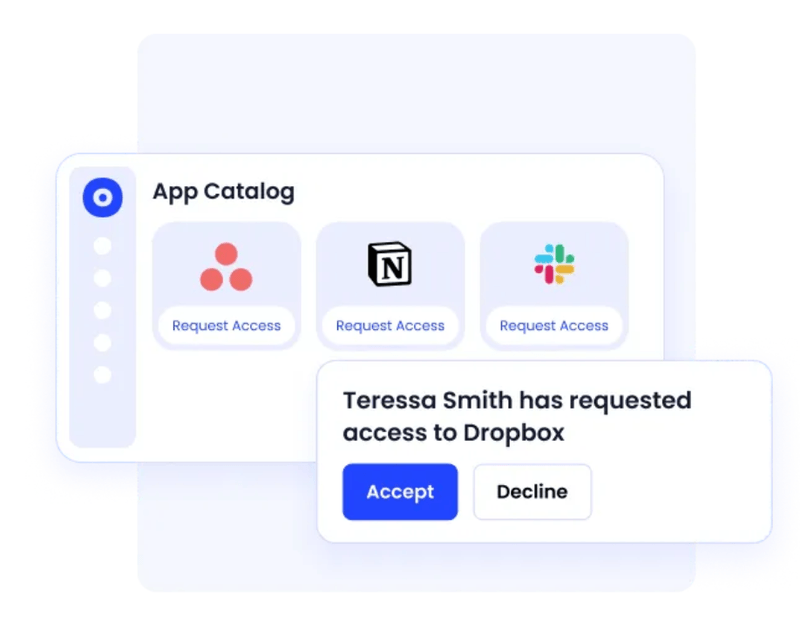
These access requests follow automatic approval steps based on company rules and the user’s role, so approvals are faster and well-controlled. This simplifies the access process, helps employees get their tools quickly, and lets IT keep control and manage access smoothly—a key part of any strong data loss prevention framework.
Integration with Existing Security Tools
By working together with these tools, CloudEagle.ai helps provide a clear view of data access, faster threat detection, and stronger enforcement of security policies, all in one simple, unified system, which greatly reinforces overall data loss prevention strategy.
Streamlining user provisioning and deprovisioning is essential for enhancing enterprise access governance. Discover how Alice Park from Remediant improved onboarding and offboarding using CloudEagle’s automated workflows in her testimonial.
Conclusion
Keeping your enterprise’s sensitive data secure is more important now than ever before. A strong data loss prevention plan helps protect your information, ensures you follow important regulations, and reduces the risk of costly data breaches.
By using the right tools and proven data loss prevention best practices, your enterprise can monitor data across networks, devices, storage, and the cloud. This not only prevents data loss but also builds customer trust and strengthens your organization.
Protecting your business data helps you avoid costly consequences and keeps your customers confident in you. Follow simple, effective data loss prevention steps to secure your information and grow your enterprise.
Are you ready to keep your sensitive data safe?
Schedule a demo with CloudEagle.ai to learn how our data loss prevention solutions can protect your enterprise.
FAQs
1. What are the techniques used to prevent data loss?
Common techniques include data classification, encryption, access controls, data masking, monitoring and alerting, employee training, and automated threat detection using AI-powered tools.
2. What are the three use cases of DLP?
Preventing accidental data leaks, protecting sensitive information from insider threats, and ensuring compliance with data privacy regulations.
3. What is the most important protection against loss of data?
Implementing a comprehensive DLP strategy that combines technology, policies, and employee awareness is the strongest protection against data loss.
4. What is an example of data loss prevention?
An email scanning system that blocks sending an email containing sensitive customer data outside the company is an example of DLP in action.
5. What is the most common cause of data loss?
Human error, such as accidentally sending sensitive data to the wrong person or mishandling information, is the leading cause of data loss.

%201.svg)








.avif)




.avif)
.avif)




.png)









