HIPAA Compliance Checklist for 2025

Cyber threats are getting smarter every year, and in 2025, keeping your business network safe is more important than ever. Experts predict cybercrime will cost the world $10.5 trillion this year, and attacks happen every 39 seconds. That means no business is too small or too big to be targeted.
This growing risk shows the need for advanced network security tools and managed services that deliver strong protection. These include managed network security, advanced threat protection, and a wide range of security tools for network defense to protect your data, block attacks, and keep systems running smoothly.
To tackle these challenges, it’s important to use complete computer network security tools, such as network security monitoring tools for real-time threat detection and response. Using vulnerability tools in network security helps find and fix gaps before attackers can exploit them, while network security audit tools support ongoing compliance and reduce risks.
Let’s look at 10 leading IT security solution providers and networking and security solutions specialists that can help your business stay safe, meet compliance standards, and minimize downtime, no matter what new threats come your way.
TL;DR
- Network security tools deliver advanced tools and expertise to protect enterprise networks from cyberattacks, data breaches, and downtime.
- Partnering with a network security tool ensures 24/7 monitoring, threat detection, and rapid incident response.
- Networking security monitoring services help businesses meet compliance and improve resilience.
- Leading network and security services vendors combine firewalls, intrusion prevention, and vulnerability management into one platform.
- Choosing the right network security solution companies boosts protection, lowers costs, and supports long-term business continuity.
What Is Network Security?
Network security is the practice of protecting a computer network from unauthorized access, attacks, or data loss. It uses a mix of network security tools and processes to keep information secure and systems running safely.
Common security tools for network protection include firewalls, antivirus software, network security monitoring tools, and computer network security tools like intrusion detection systems (IDS) and vulnerability scanners.
Organizations also use network security audit tools to check for risks, network security management tools to control user access, and network security software tools to monitor, detect, and block threats in real time.
What Are Network Security Tools?
Network security tools are specialized computer network security tools and services that help organizations manage, protect, and secure their network infrastructure. These security tools for network safety ensure reliable communication, safeguard sensitive data, and defend against cyber threats across both the internet and private networks.
Key aspects of network security tools include:
Network Connectivity and Management: These tools and providers maintain the infrastructure required for safe and high‑performance network operations, offering monitoring, traffic control, and network security management tools for smooth connectivity.
Cybersecurity Protections: They deploy and manage network security software tools like firewalls, intrusion detection and prevention systems (IDPS), antivirus solutions, and network security monitoring tools to block unauthorized access and detect threats in real time.
Managed Network Security Solutions: Many act as fully managed services—handling threat detection, incident response, vulnerability tools in network security, patch management, and network security audit tools to ensure compliance and continuous protection.
Network Infrastructure Services: Beyond security, they assist in network design, installation, and optimization to ensure resilience and performance.
Cloud and Remote Access Security: With growing cloud adoption and remote work, modern tools for network security protect cloud environments, remote connections, and hybrid infrastructures from potential cyber risks.
What Are The Five Types of Network Security?
The five common types of network security are:
Firewalls: Firewalls are network security tools that block unwanted traffic between your internal network and the outside world. They check data moving in and out and stop unauthorized access. They can be part of network security software tools or separate hardware devices.
Antivirus Software: Antivirus is a computer network security tool that finds and removes harmful programs like viruses, worms, and Trojans. It helps keep your data safe and works with other security tools for network protection.
Intrusion Detection and Prevention Systems (IDS/IPS): These network security monitoring tools watch your network for unusual activity or known attack patterns. IDS alerts you about threats, while IPS blocks them. They also use vulnerability tools in network security to find weaknesses before hackers do.
Virtual Private Networks (VPNs): VPNs protect data sent over the internet by encrypting it. They are part of network security management tools, helping remote workers connect securely to company networks.
Access Control Policies: Access controls decide who and what devices can use your network. Using network security audit tools and network security management tools, enterprises can ensure only approved users get in and sensitive data stays safe.
How Network Security Tools Can Help Your Enterprise?
Partnering with a trusted network security tool has become essential for today’s enterprises to protect their data, ensure compliance, and maintain uninterrupted operations.
Here’s how network security tools can help your enterprise:
Reduce Risk from Increasingly Complex Cyber Threats
Modern cyber threats are growing in both volume and sophistication. Enterprises face targeted attacks like ransomware, phishing, and zero-day exploits, which demand constant vigilance and specialized defenses.
Advanced network security software tools and security tools for network defense help detect and block these threats before they cause damage, lowering risk to critical systems and data.
Access to Expert Knowledge and Advanced Technologies
Building an in-house cybersecurity team is costly and complex. Leading providers of computer network security tools offer dedicated experts and innovative solutions like AI threat detection, real-time monitoring with network security monitoring tools, and automated incident response, helping enterprises stay ahead of attackers and keep systems secure.
24/7 Monitoring and Rapid Incident Response
Cyberattacks can happen anytime, and delays can cause major damage. Enterprise-grade network security management tools provide continuous, around-the-clock monitoring and fast incident response to contain breaches quickly, reducing disruption and keeping operations running smoothly.
Cost Efficiency and Scalability Compared to In-House Teams
Maintaining an in-house team involves high costs in salaries, training, and infrastructure. Outsourcing to providers with advanced tools for network security offers predictable subscription pricing, reduces overhead, and lets enterprises scale their security services flexibly as they grow.
Compliance with Regulations and Industry Standards
Enterprises must follow data privacy and security regulations like GDPR, HIPAA, and PCI-DSS. Providers leverage network security audit tools to enforce policies aligned with these requirements, automate audit reporting, and guide risk management. This lowers the chance of violations, fines, and reputational harm.
Comprehensive Network and Security Management as a Unified Service
Modern cybersecurity requires seamless handling of network performance and data protection. Trusted providers deliver unified solutions covering firewall management, intrusion detection, vulnerability scanning via vulnerability tools in network security, and patch updates to ensure efficient and secure system operations.
Proactive Threat Hunting and Vulnerability Management
Beyond basic defense, these providers use proactive threat hunting and continuous monitoring with advanced network security monitoring tools and vulnerability tools in network security to identify weaknesses before attackers exploit them, strengthening overall security posture.
Support for Cloud and Remote Work Environments
As cloud adoption and remote work grow, providers protect cloud platforms, SaaS applications, and remote access connections using specialized network security tools to secure distributed teams and reduce risks beyond traditional network perimeters.
Improved Business Continuity and Reduced Downtime
Continuous monitoring, rapid breach detection, backup solutions, and disaster recovery plans offered by these managed services help keep enterprises running without interruptions during cyber incidents or IT failures, safeguarding revenue and reputation.
How CloudEagle.ai Can Improve SaaS Security and Access Management?
CloudEagle.ai is an advanced SaaS management and governance platform that boosts enterprise security by centralizing access control, enforcing strong policies, and detecting threats in real time; ensuring only the right people have secure, compliant access.
Here’s how it improves SaaS security and streamlines access management:
Centralized Access Visibility & Control
CloudEagle.ai brings all your SaaS applications into one central dashboard, so you can easily see who has access to what. Instead of chasing multiple admin panels, IT teams get a single, real-time view of every user’s app permissions, usage, and activity. This helps spot security risks like shadow IT or unused licenses before they become a problem.

With this visibility, you can take quick actions such as revoking unused access, tightening permissions, or approving new requests with confidence. By controlling access from one place, CloudEagle.ai reduces complexity, strengthens security, and ensures your SaaS ecosystem is clean, compliant, and cost-efficient.
Automated User Provisioning and Deprovisioning
CloudEagle.ai automates onboarding by instantly granting new employees the exact tools and permissions they need based on their role. No more waiting days for access to start work or worrying about missed setups.

When someone leaves the company or changes roles, the system automatically removes or updates their access across all connected SaaS apps. This not only saves time but also closes the dangerous security gap of orphaned accounts, which are a common entry point for cyberattacks.

Know how CloudEagle.ai helped Bloom & Wild streamline employee onboarding and offboarding.
Role-Based Access Control (RBAC)
CloudEagle.ai uses RBAC to make sure users only get the access they truly need for their role—nothing more, nothing less. This minimizes the chances of accidental data exposure or misuse by giving employees exactly the right level of permissions.

As roles change, permissions are automatically adjusted, so there's no lingering access to sensitive apps. This not only boosts security but also makes managing access simpler and more consistent across your growing SaaS stack.
Time-Based SaaS Access Governance
Not everyone needs permanent access to every app. CloudEagle.ai allows you to set access that expires automatically—perfect for contractors, temporary workers, or special projects.
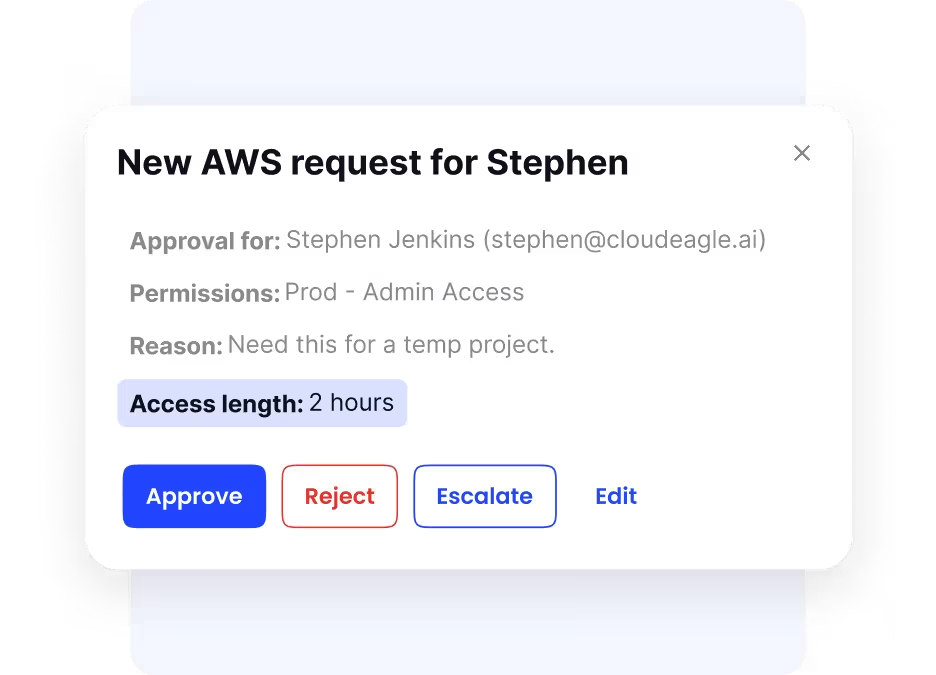
This “just-in-time” approach limits exposure by ensuring that once the job is done, access is gone. It’s a simple yet powerful way to minimize risks while keeping operations smooth and secure.
Privileged Access Management (PAM)
Privileged accounts have the “keys to the kingdom” in your SaaS environment, so they need extra care. CloudEagle.ai helps by restricting high-level permissions to only approved users, and even then, only for the time needed to complete the task.
Every privileged action is tracked, logged, and easily auditable, preventing misuse and detecting suspicious activities early. By tightening control over admin-level access, PAM greatly reduces the risk of insider threats and external breaches.
Compliance Automation and Audit Readiness
Keeping up with compliance rules like GDPR, SOC 2, and ISO 27001 can be overwhelming. CloudEagle.ai makes it easier by automatically tracking access changes, maintaining logs, and generating reports that meet audit requirements—without manual spreadsheet work.

When it’s audit time, you can instantly pull detailed access records, user activity reports, and policy compliance evidence. This speeds up the audit process, reduces stress, and helps avoid costly compliance issues, all while proving a strong security posture to regulators and clients.
User-Friendly Access Request and Governance
Requesting app access shouldn’t slow down work. With CloudEagle.ai’s self-service portal (and integrations like Slack), employees can ask for access in seconds and get approvals quickly.

For IT, this means less time managing tickets and more time focusing on high-value work. Governance rules are built in, so every approval aligns with security policies—keeping everyone productive and secure without the bottleneck.
Integration with Security Monitoring Tools
CloudEagle.ai doesn’t work in isolation; it integrates with over 500 SaaS apps, including well with your existing security tools. It integrates with SIEMs, threat detection platforms, and monitoring solutions, feeding them real-time access and usage data for better visibility.
This means security teams get a fuller picture of risks and can respond faster to incidents. By connecting access management with continuous monitoring, you create a seamless shield for your SaaS environment that strengthens over time.
Top 10 network security tools in 2025
Securing SaaS environments and managing access efficiently are top priorities for enterprises. CloudEagle.ai offers advanced solutions to centralize access control, automate provisioning, and ensure compliance, while the top 10 network security tools also help you protect your enterprise networks from evolving cyber threats.
1. Nexpose
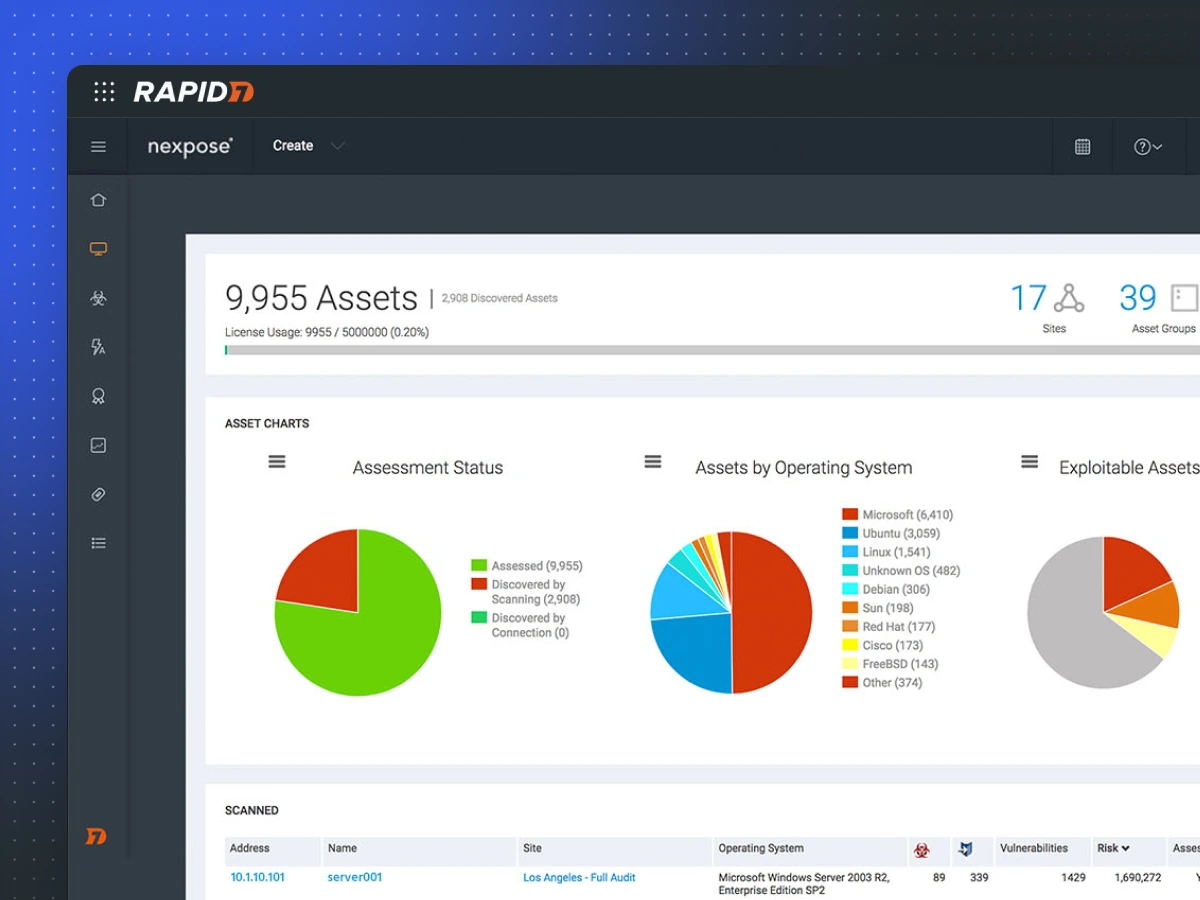
Nexpose, developed by Rapid7, is a powerful on-premise vulnerability scanner that helps enterprises identify, assess, and prioritize security weaknesses across networks, systems, and applications. It uses real-time data, risk-based scoring, and integrates with Metasploit for efficient threat remediation.
Key Features
- RealRisk™ Scoring: Prioritizes vulnerabilities based on exploitability, malware exposure, and asset value to focus remediation efforts effectively.
- Adaptive Security: Automatically detects new devices and vulnerabilities as they appear on the network, keeping scans up-to-date.
- Compliance Auditing: Includes built-in policies for PCI-DSS, HIPAA, CIS benchmarks, assisting organizations in meeting regulatory requirements.
Pros
- Real-time vulnerability updates ensure scanning data is always current.
- Integration with Metasploit enables penetration testing for validation of vulnerabilities.
Cons
- On-premise deployment requires dedicated resources for setup and maintenance.
- Can be complex for beginners; requires skilled users for full optimization.
Pricing
- Pricing varies by number of assets scanned and features, generally requiring a customized quote based on organizational size.
2. Wireshark
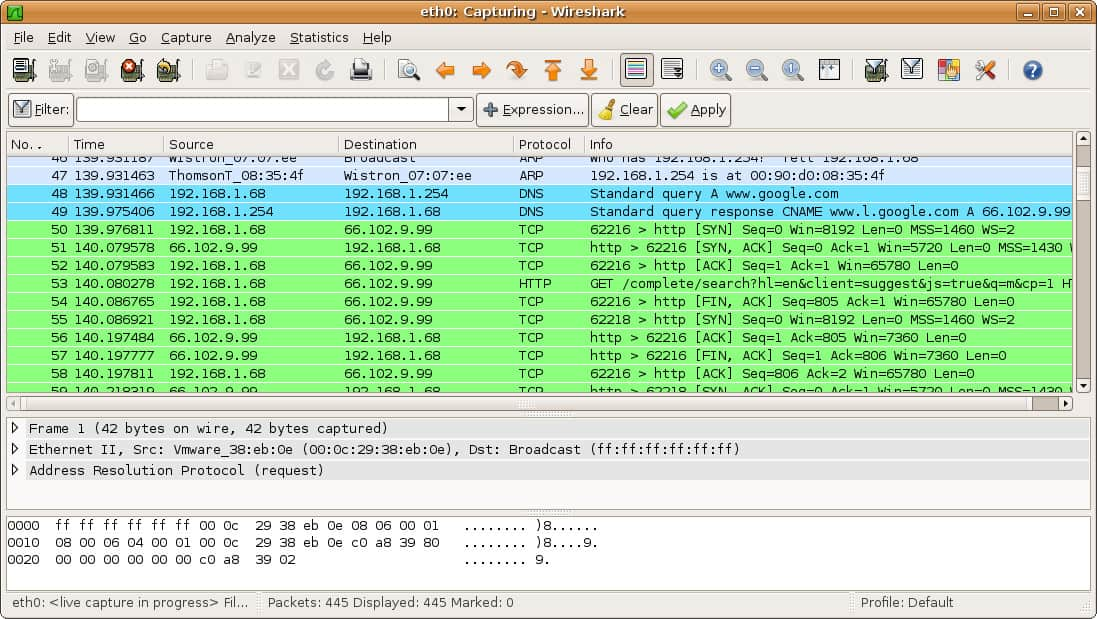
Wireshark is a free, open-source network protocol analyzer widely used for real-time traffic capture and analysis. It helps network and security professionals troubleshoot issues, detect suspicious activities, and perform detailed packet-level inspection to strengthen network security.
Key Features
- Deep Packet Inspection: Allows detailed analysis of network traffic including headers and payloads across hundreds of protocols for forensic and troubleshooting purposes.
- Real-Time Monitoring and Filtering: Enables users to capture live network data and apply advanced display filters to isolate relevant packets quickly.
Pros
- Open-source and free, supported by a large global community.
- Highly customizable with extensive filtering, decoding, and protocol support.
Cons
- Limited in capturing encrypted traffic without decryption keys.
- Requires technical expertise to interpret complex packet data effectively.
Pricing
- Wireshark is completely free to use as an open-source tool, making it accessible to individuals and organizations of all sizes.
3. Tor
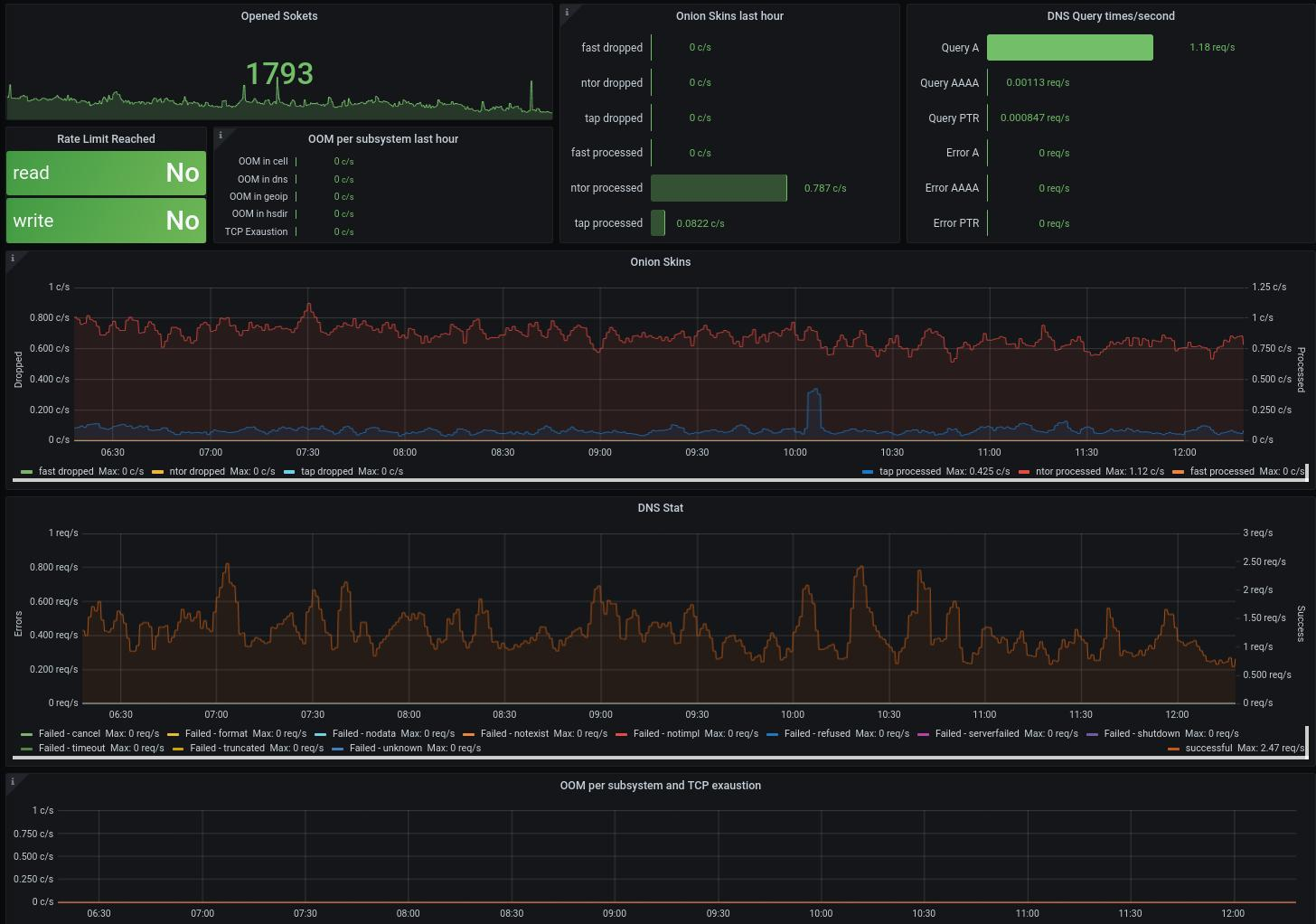
Tor (The Onion Router) is a free, open-source network that enables anonymous communication online through multi-layered encryption and routing. It helps users protect their privacy by hiding IP addresses and preventing traffic analysis, making it a powerful tool for privacy-focused network security.
Key Features
- Multi-Layered Onion Routing: Data is encrypted in layers and routed through multiple volunteer-operated relays worldwide, concealing user identity and location.
- Anonymity and Privacy Protection: Masks your IP address by making your traffic appear to originate from Tor exit nodes, effectively hiding user identity and browsing activity.
- Access to .onion Sites and Censorship Resistance: Enables access to hidden services (.onion sites) and helps bypass internet censorship through bridge relays.
Pros
- Provides strong anonymity and defends against network traffic surveillance and tracking.
- Free and open-source, supported by a global community of volunteers.
- Useful for secure, private browsing and accessing otherwise blocked or censored content.
Cons
- Slower browsing speeds due to multiple layers of encryption and routing.
- The exit node traffic to the open internet is unencrypted, which can expose traffic at that point.
- Some websites block Tor traffic or restrict functionality due to known Tor exit node IPs.
Pricing
- Tor is entirely free to use and open-source, with no licensing fees.
4. Splunk

Splunk is a powerful security information and event management (SIEM) platform that enables enterprises to monitor, analyze, and respond to security threats in real time. It delivers advanced analytics, customizable dashboards, and automation to strengthen network security defenses.
Key Features
- Advanced Threat Detection: Uses AI and machine learning to identify and prioritize risks across users and systems.
- Comprehensive Data Ingestion: Monitors data from multiple sources including endpoints, networks, and cloud environments.
Pros
- Deep integration capabilities and customizable dashboards for detailed security insights.
- Strong compliance support with audit-ready reporting features.
Cons
- Pricing can be high, especially for large data ingestion volumes.
- Initial setup and tuning can be resource-intensive for smaller teams.
Pricing
- Pricing mainly depends on data ingestion volume, starting at about $1,800 per year for 1GB/day. Other models include workload-based and entity-based licenses, with cloud and enterprise tiers offering custom pricing based on needs.
9. Metasploit
Metasploit is a robust, modular penetration testing platform widely used by security professionals to identify, exploit, and validate security vulnerabilities in networks, systems, and applications. It supports automated testing, payload generation, and advanced post-exploitation capabilities for comprehensive security assessment.
Key Features
- Extensive Exploit Database: Offers a vast and frequently updated library of exploits targeting various operating systems and applications, enabling thorough vulnerability assessments.
- Payload Generation and Customization: Generates a variety of payloads (e.g., reverse shells, Meterpreter) that can be customized to bypass defenses and remotely control compromised systems.
Pros
- Highly flexible and modular framework allowing custom exploit and payload development for specific penetration testing needs.
- Integrates with tools like Nmap and Metasploit’s own Meterpreter payload for advanced reconnaissance and control.
Cons
- Requires technical expertise to use effectively, with a learning curve for mastering its full suite of features.
- It can generate false positives and needs careful tuning to avoid detection by security systems.
Pricing
- The Metasploit Framework is free (open source). Commercial editions like Metasploit Pro are priced based on scale and needs, requiring custom vendor quotes.
6. Nagios
Nagios is a widely used open-source network monitoring and security tool known for continuous monitoring of servers, network devices, and services. It provides real-time alerts, detailed reporting, and helps quickly identify and resolve network issues to keep your infrastructure secure and running smoothly.
Key Features
- Real-Time Monitoring & Alerts: Continuously monitors network services like HTTP, FTP, SMTP, SSH, with instant notifications on failures or suspicious activity.
- Comprehensive Infrastructure Oversight: Tracks servers, applications, network devices, and system metrics via plugins and custom checks.
Pros
- Offers proactive alerting to prevent prolonged downtime and costly network outages.
- Provides detailed, customizable reports and dashboards for performance and security analysis.
Cons
- It can require significant manual setup and tuning, which may be complex for smaller teams.
- The user interface is functional but less modern and user-friendly compared to commercial alternatives.
Pricing
- Nagios Core is free (open source). Paid versions like Nagios XI start at around $1,995 per year, with prices increasing for larger deployments and additional support.
7. Nessus Professional
Nessus Professional is a leading vulnerability scanner known for high-speed asset discovery, configuration auditing, and identifying security weaknesses across networks, systems, and applications. It helps security teams quickly detect and prioritize vulnerabilities to reduce cyber risks.
Key Features
- Comprehensive Vulnerability Scanning: Detects software flaws, missing patches, misconfigurations, and malware threats.
- Compliance Auditing: Offers built-in policies for standards like PCI DSS, CIS, NIST, helping you stay audit-ready.
- Customizable Reports: Generates detailed, exportable reports with vulnerability scoring for prioritization and remediation guidance.
Pros
- Widely trusted with frequent vulnerability updates for accurate scanning.
- User-friendly setup with broad platform support including on-premise and cloud assets.
- Cost-effective solution ideal for security professionals and small to medium teams.
Cons
- Not a full enterprise vulnerability management platform; limited asset management features.
- Lacks native risk prioritization and advanced incident response capabilities.
- Requires manual integration with other tools for complete security workflow automation.
Pricing
- Costs approximately $2,990 to $3,390 per year for a single user. Extended versions with extra features like cloud scanning can cost about $5,350 per year.
8. Snort
Snort is a widely used, open-source network intrusion detection and prevention system (IDS/IPS) that monitors network traffic in real time to detect, log, and block potential threats. It offers flexible rule-based threat detection, protocol analysis, and supports both alerting and active blocking.
Key Features
- Real-Time Packet Capture and Analysis: Snort inspects network packets live, enabling immediate detection of malicious traffic and rapid response.
- Signature-Based Detection with Custom Rules: Uses a powerful, customizable rule language to identify known attack patterns and can be tailored to detect specific threats relevant to an organization's environment.
Pros
- Free and open-source, with a large active community contributing to continuous updates and rule sets.
- Highly customizable and flexible to adapt to various network environments and security policies.
Cons
- Requires technical expertise to configure and manage effectively, especially for creating and fine-tuning custom rules.
- It can generate false positives if not properly tuned, leading to alert fatigue.
Pricing
- Fully free as open-source software. Commercial support and advanced subscription rules are available from third-party vendors at extra cost.
9. Forcepoint
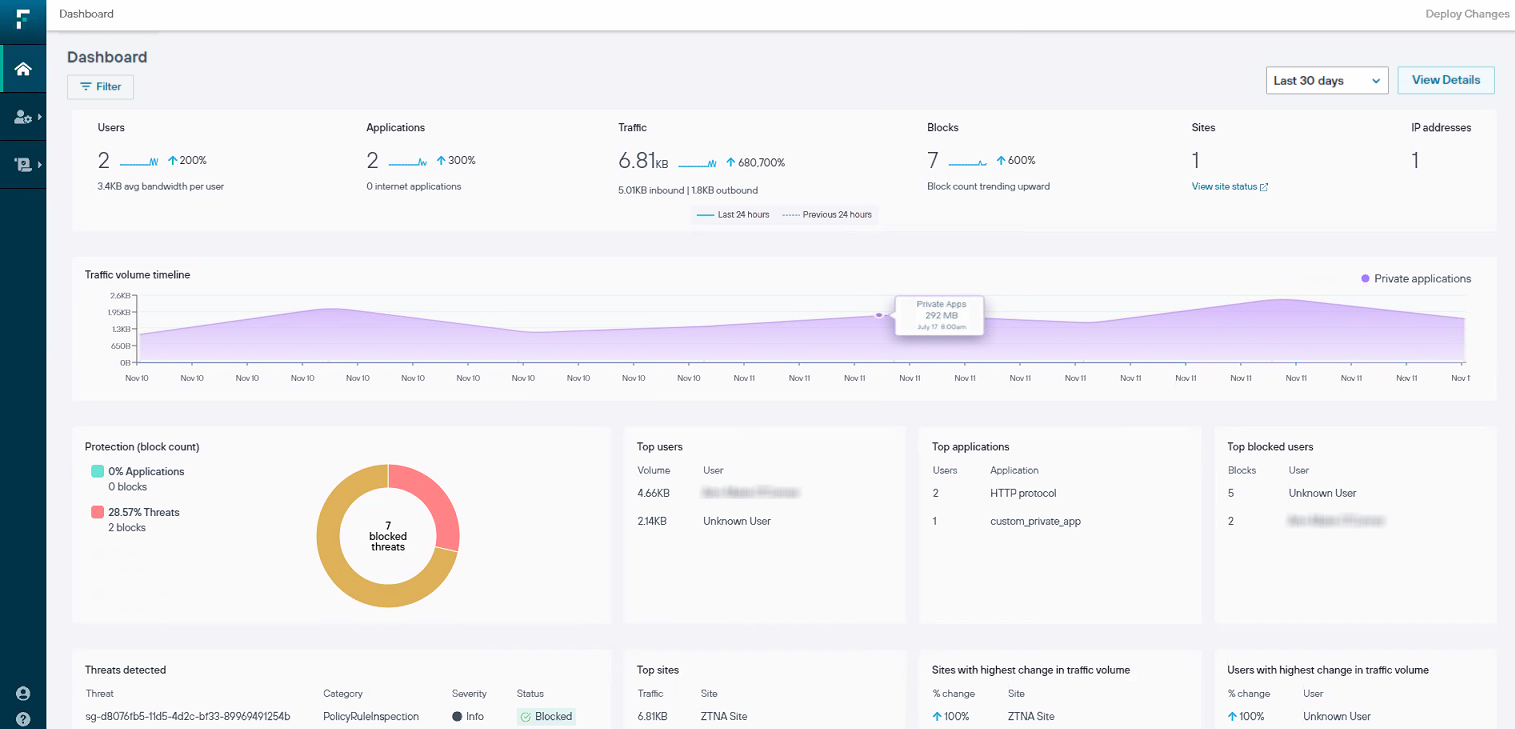
Forcepoint is a leading network security tool offering advanced solutions that protect enterprises from sophisticated cyber threats. Their platform integrates next-generation firewall (NGFW), Secure SD-WAN, and data protection technologies, delivering scalable, high-performance security and simplified management.
Key Features
- Next-Generation Firewall (NGFW) with Secure SD-WAN: Combines firewall security with high-performance, cost-effective broadband connectivity and automatic failover to protect enterprise networks.
- Advanced Threat Detection and Prevention: Includes intrusion prevention, malware detection, URL filtering, and zero trust controls to prevent breaches and minimize risk.
Pros
- Comprehensive protection integrating network security and connectivity with convenient management.
- Strong support for zero-trust architectures and segmented network security.
Cons
- Pricing and deployment can be relatively complex and may require expert setup.
- Some features may require additional licensing or subscriptions, increasing costs.
Pricing
- Pricing varies widely by solution and deployment scale, generally subscription-based with custom enterprise quotes.
10. Kali Linux
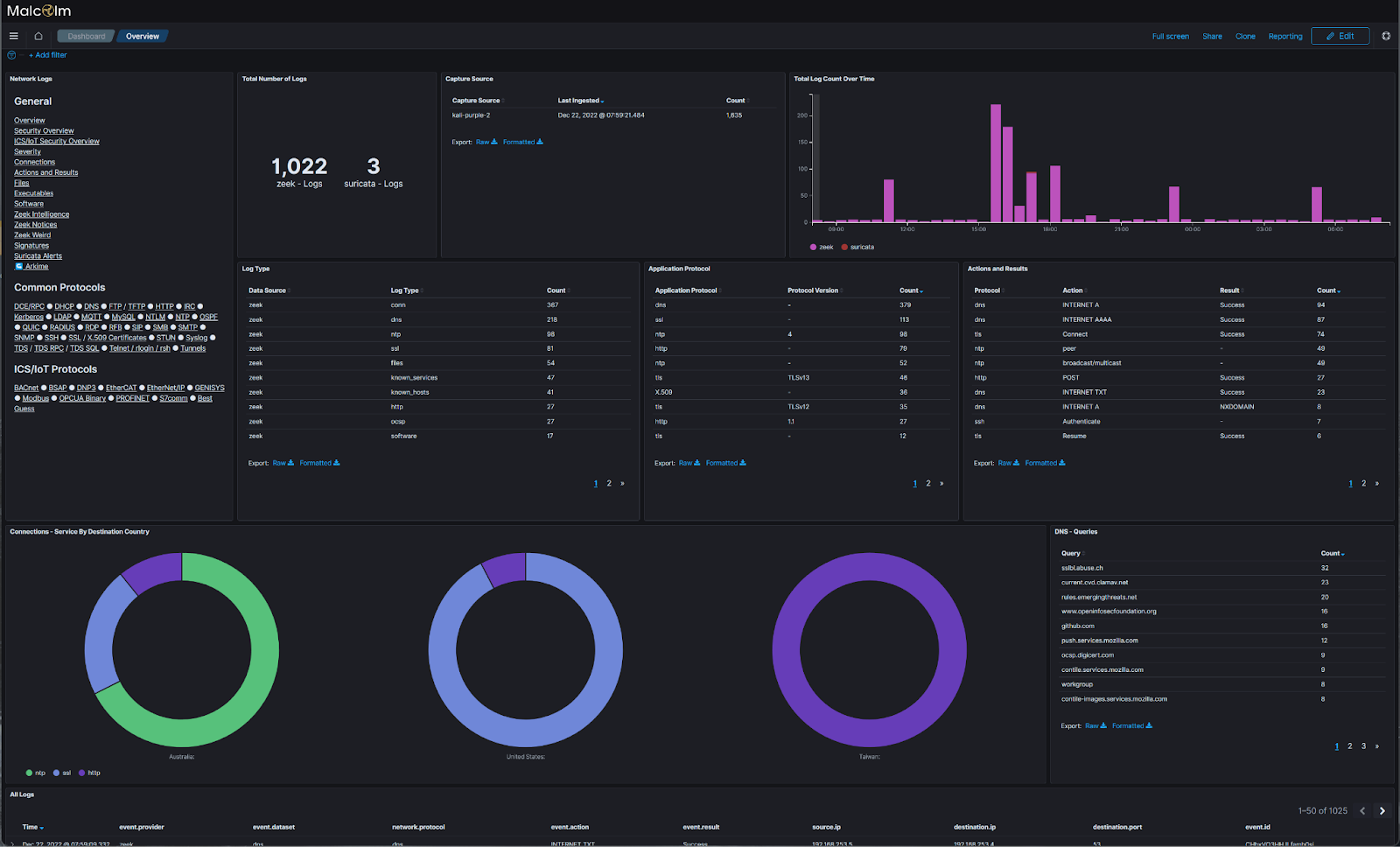
Kali Linux is a powerful, open-source Linux distribution specifically designed for penetration testing, ethical hacking, and cybersecurity assessments. It comes with over 600 pre-installed tools that help security professionals identify vulnerabilities, analyze networks, and perform advanced security testing.
Key Features
- Extensive Security Toolset: Includes tools like Nmap for network scanning, Metasploit for exploitation, Wireshark for packet analysis, John the Ripper for password cracking, and many more to cover all phases of penetration testing.
- Customizable and Portable: Supports deployment on various platforms, including desktops, virtual machines, USB drives, ARM devices (like Raspberry Pi), and cloud environments, offering flexibility for on-site and remote security testing.
Pros
- Free and open-source with a large and active community continuously updating tools and features.
- Comprehensive and all-in-one platform ideal for ethical hackers, security researchers, and network administrators.
Cons
- Requires a solid understanding of Linux and cybersecurity concepts; steep learning curve for beginners.
- Its powerful tools can be misused if operated without proper authorization and knowledge.
Pricing
- Kali Linux is completely free and open-source, available for download without any licensing fees.
To enhance enterprise access governance, it’s crucial to simplify user provisioning and deprovisioning processes. Hear from Alice Park of Remediant about how she improved onboarding and offboarding efficiency using CloudEagle’s automated workflows in her testimonial.
Conclusion
Protecting your enterprise’s data and staying compliant requires more than traditional security measures. With cyber threats evolving faster than ever, choosing the right network security tools and a trusted partner is essential for safeguarding assets, achieving compliance, and ensuring smooth operations.
The best approach is to choose a provider that offers security tools for network protection designed for your business needs, growth plans, and compliance rules. This includes advanced network security monitoring tools, computer network security tools, and vulnerability tools in network security to spot threats early and fix gaps before attackers can use them.
If you want to go beyond basic threat detection and stay resilient against evolving cyber risks, consider a comprehensive solution like CloudEagle.ai. Its powerful compliance automation, continuous monitoring, and advanced security management capabilities ensure your enterprise remains protected while you focus on growth and innovation.
Are you ready to strengthen your network security tools strategy?
Schedule a demo with CloudEagle.ai today and discover how our network and security solutions can safeguard your enterprise.
FAQs
1. Which one is a network security tool?
A network security tool is a software or hardware solution, such as a firewall, IDS/IPS, antivirus, or VPN, that protects a network from unauthorized access and cyber threats.
2. What are NSM tools?
NSM tools, or Network Security Monitoring tools, like Zeek, Suricata, and Security Onion, track and analyze network activity to detect suspicious behavior and security threats.
3. What is CCNA network security?
CCNA Network Security is a Cisco certification that validates skills in securing networks using firewalls, VPNs, and other essential security tools for network protection.
4. What tools can be used to secure the network?
A mix of firewalls, IDS/IPS systems, antivirus software, VPNs, and network security management tools such as SolarWinds can be used to protect a network.
5. What is the best network security?
The best network security is a layered approach that uses firewalls, endpoint protection, vulnerability scanning tools, real‑time monitoring, and regular security audits.

%201.svg)








.avif)




.avif)
.avif)




.png)









