HIPAA Compliance Checklist for 2025

Manual access reviews are slow, complicated, and prone to mistakes. IT teams spend hours checking spreadsheets, emails, and multiple SaaS apps just to verify user access. This scattered approach increases the risk of over-privileged accounts, compliance gaps, and security issues, which can affect an ITGC Audit Checklist evaluation.
According to CloudEagle.ai’s IGA report, 95% of enterprises still conduct access reviews manually, highlighting a major efficiency and security challenge.
With the rapid growth of SaaS apps and constantly changing employee roles, quarterly or manual access reviews are no longer enough. Automated workflows, continuous monitoring, and AI-driven insights are a must to simplify app access reviews.
Let’s explore how CloudEagle.ai simplifies, automates, and strengthens app access reviews.
TL;DR
- CloudEagle.ai automatically schedules access reviews and sends reminders to reviewers and managers, eliminating the need for manual follow-ups.
- The platform provides a centralized dashboard where all user access and permissions across applications can be viewed, making reviews faster and more accurate.
- AI-driven risk detection flags overprivileged, dormant, or inappropriate access, allowing IT teams to focus on the riskiest accounts first.
- Access is intelligently mapped based on user roles, departments, or locations, ensuring permissions align with business responsibilities and reducing over-provisioning.
- All review actions are logged and documented automatically, providing audit-ready reports to simplify compliance and regulatory audits.
What Is ITGC Audit?
An ITGC audit (IT General Controls audit) evaluates an organization’s core IT controls to ensure systems are secure, reliable, and compliant. The audit checks that controls are effective, consistently applied, and aligned with regulations. It helps reduce risks like data breaches, fraud, operational disruptions, and non-compliance.
ITGC audits focus on critical areas such as:
- Access Management: Ensuring only authorized users can access systems and data.
- Change Management: Monitoring and controlling changes to applications and infrastructure.
- Backup and Recovery: Validating that data is properly backed up and can be restored in case of failure.
- System Operations and Monitoring: Tracking system performance, security logs, and incident response.
Key Areas Covered in an ITGC Audit
An ITGC audit evaluates an enterprise’s IT controls to ensure data integrity, security, and compliance. It helps identify gaps, prevent unauthorized access, and reduce operational risks.
Robbie Sinclair, Director of Corporate Security, Network Associates, Says:
“Security always feels excessive—until it’s too late.”
Thus, it becomes essential for enterprises to take proactive actions to ensure their IT controls are effective, consistently enforced, and aligned with regulatory requirements, reducing the risk of data breaches, compliance failures, and operational disruptions.
Here are the key areas enterprises must cover during an ITGC audit:
1. Access to Programs and Data
This area ensures that only authorized personnel can access applications, systems, and sensitive data. Auditors review user provisioning, role assignments, periodic access checks, and account deactivation processes.
For example, if a former employee can still approve invoices after leaving the company, it creates compliance and fraud risks. ITGC audits verify that access rights are updated immediately following role changes or departures.
Reports indicate that a significant portion of IT security incidents result from improper user access or excessive privileges. Properly managing access helps reduce fraud, prevent insider threats, and avoid regulatory penalties.
2. Program Development and Change Management
Auditors examine controls around software development and system changes. This includes approvals, testing, version control, and documentation to prevent unauthorized or erroneous changes.
When a company updates its payroll system, a change request must be formally approved, tested in a sandbox environment, and documented before deployment. Unauthorized changes could result in incorrect payments, audit failures, or system downtime.
3. Computer Operations and Backup Controls
This involves reviewing system monitoring, job scheduling, and backup processes. Auditors verify that critical systems run reliably, data is backed up consistently, and recovery procedures are tested regularly.
A manufacturing company relies on ERP systems for production scheduling. If backups are incomplete or restoration procedures fail, downtime can halt operations, leading to significant financial losses.
IDC estimates that unplanned downtime costs businesses $100,000 per hour on average. Effective backup and operational controls mitigate these costs and ensure business continuity.
4. Logical and Physical Access Security
Auditors assess both digital and physical security measures. Logical controls include passwords, firewalls, multi-factor authentication, and access logs. Physical controls cover server rooms, data centers, and devices storing sensitive information.
If a server room lacks badge access or surveillance, unauthorized personnel could tamper with critical systems. Similarly, weak passwords or unmonitored administrative accounts increase cybersecurity risks.
A Ponemon Institute report indicates that 52% of data breaches are due to insider threats or compromised credentials. ITGC audits ensure layered security to protect assets.
5. IT Governance and Risk Management
This area evaluates overall IT oversight, policies, and risk management frameworks. Auditors review how the organization identifies, mitigates, and monitors IT risks, aligns IT strategy with business objectives, and ensures regulatory compliance.
A company may have documented IT policies but lacks an enforcement mechanism. ITGC audits ensure policies are implemented and monitored, from software approvals to disaster recovery planning.
Organizations with robust IT governance are 50% more likely to successfully pass IT audits and maintain regulatory compliance, according to ISACA research.
What Is The Need For An ITGC audit?

ITGC Audit Checklist: Step-by-Step Guide
In today’s digital world, ITGC audits help ensure systems are secure, compliant, and well-governed.
Step 1: Define Scope and Regulatory Requirements
The first step in an ITGC audit is defining its scope. Organizations need to identify which systems, applications, and departments will be included, and which regulatory frameworks apply, such as SOX, ISO 27001, GDPR, or HIPAA. This focuses audit efforts on high-risk areas while avoiding unnecessary reviews of low-risk systems.
For example, a finance-focused audit may prioritize ERP systems like SAP or Oracle, while a data privacy audit may focus on cloud storage and HR systems containing personally identifiable information (PII).
Step 2: Identify Critical Systems and Applications
After defining the scope, organizations need to identify the systems and applications that are essential to operations, financial reporting, or regulatory compliance. Systems supporting core business functions or containing sensitive information should be prioritized.
For instance, payroll software, customer relationship management platforms, and cloud storage systems often represent high business impact. By categorizing systems based on risk and criticality, IT teams can allocate resources efficiently and ensure high-risk systems receive a thorough review.
Step 3: Assess User Access and Privilege Levels
User access reviews are a cornerstone of ITGC audits. IT teams must examine who has access to which systems, the type of permissions granted, and whether those permissions align with users’ roles. Implementing least privilege principles ensures users only have access required for their job function.
Orphaned accounts or excessive permissions should be flagged and remediated immediately. For example, only finance managers should have approval rights for payments, while general staff should have read-only access. Failing to manage access can lead to internal threats, data misuse, or audit failures.
Know how Treasure Data Enhanced Access Management and Reporting with CloudEagle.ai.
Step 4: Review Change Management Procedures
Auditing change management ensures that all system modifications, such as software updates, configuration changes, or emergency fixes, are properly requested, tested, and approved. Documentation of emergency changes is equally important to prevent unauthorized modifications.
A typical best practice includes maintaining change logs with approvals and testing records. For instance, any upgrade to payroll software should include a change request, testing results, and manager approval before deployment.
Step 5: Evaluate Backup and Disaster Recovery Controls
Enterprises must verify that backup schedules, storage security, and disaster recovery procedures are robust. Regular testing of backup restoration is essential to ensure business continuity.
For example, daily backups of financial data with quarterly restoration drills help mitigate the risk of data loss due to system failures or cyberattacks. An effective backup strategy reduces downtime, limits operational impact, and provides evidence of control for auditors.
Step 6: Verify Incident Response Readiness
ITGC audits also focus on incident response preparedness. Teams must review incident response plans, alerting mechanisms, and escalation protocols to confirm readiness for data breaches or system failures. Employees should be trained to respond promptly to incidents.
For example, if unauthorized access occurs in payroll or HR systems, automatic alerts to IT and management can ensure immediate containment, reducing financial and reputational damage.
Step 7: Document Findings and Prepare Plans
The final step involves documenting all audit findings, highlighting gaps, and creating actionable remediation plans. Each issue should have a clear owner, timeline, and defined resolution steps.
Maintaining audit-ready documentation is crucial for demonstrating compliance to regulators and internal stakeholders. For instance, orphaned accounts identified during an audit should be deactivated within a defined period, with the actions logged and reported for future review.
Common ITGC Audit Challenges and Risks
Conducting ITGC audits can be complex, and organizations often face common challenges and risks that undermine effectiveness, create compliance gaps, and increase operational overhead.
1. Inconsistent Access Control Enforcement
When access policies are applied inconsistently across apps or departments, employees may end up with excessive privileges or access to sensitive data they don’t need. This raises risks like insider threats, unauthorized changes, and compliance issues. Without a unified access control system, IT teams find it hard to keep user permissions accurate.
2. Manual Tracking of Changes and Approvals
Many enterprises still track system changes, user access, and approvals using spreadsheets, emails, or paper logs. This manual method takes a lot of time, often causes mistakes, and can result in missed changes or unauthorized actions. It also slows down audits and makes keeping a reliable record difficult.
3. Poor Backup Verification Processes
Backups are critical for disaster recovery, but incomplete or inconsistent backup procedures can put an enterprise at risk. If backups are not regularly verified or tested, data loss during system failures or cyber incidents becomes a real threat. This also increases recovery time and the potential impact of downtime, affecting business continuity.
4. Fragmented System Monitoring
Monitoring multiple IT systems independently can leave gaps in supervision. Security or operational anomalies in one system may go unnoticed if monitoring is siloed. Fragmented monitoring also makes it challenging to correlate events, detect risks early, and respond proactively.
5. Inefficient Incident Response
A lack of clearly defined incident response procedures can delay detection and remediation of security events. Without standardized workflows, IT teams may struggle to respond quickly, increasing downtime, operational losses, and the chance of non-compliance.
According to Robert Davis, Cybersecurity Expert and Consultant
“Effective incident response relies on two things: information and organization.”
7. Shadow IT and Unauthorized Applications
Applications used outside IT’s purview (commonly referred to as Shadow IT) pose hidden risks. Unapproved software may introduce security vulnerabilities, create license compliance issues, or lead to data leakage. Without proper visibility, IT cannot enforce governance effectively or include these tools in access reviews and audits.

6. Limited Documentation and Audit Trails
Incomplete logs, missing approvals, or poorly organized system records can make audits difficult and stressful. Demonstrating compliance with regulations like SOX, GDPR, or ISO standards becomes challenging, raising the risk of penalties and reputational damage.
Stéphane Nappo, Global CISO, Groupe SEB, Says:
“It takes 20 years to build a reputation and a few minutes of a cyber-incident to ruin it.”
How CloudEagle.ai Can Help Automate Access Reviews
CloudEagle.ai is a purpose-built SaaS governance platform that simplifies access reviews by automating the entire process. IT teams can quickly see who has access, spot risks, and remove unnecessary permissions; all from a single dashboard. This saves time, reduces errors, and keeps your organization secure and compliant.
Here’s how it automates access reviews:
1. Automated Review Scheduling and Notifications
Managing app access reviews manually is time-consuming and prone to missed deadlines. CloudEagle.ai eliminates this by automatically scheduling access reviews according to your organization’s cadence, whether monthly, quarterly, or continuous.

Reviewers and managers receive automated reminders and notifications, ensuring that every review is completed on time. IT teams no longer need to chase approvals or follow up across multiple systems, which saves time and reduces administrative overhead.
Know this inspiring success story of how Dezerv Automated Its App Access Review Process with CloudEagle.ai.
2. Centralized Access Review Dashboard
Instead of logging into dozens of SaaS apps or reconciling spreadsheets, CloudEagle.ai brings all user access data into a single, unified dashboard. IT and security teams can instantly view all permissions, roles, and access rights across every application.
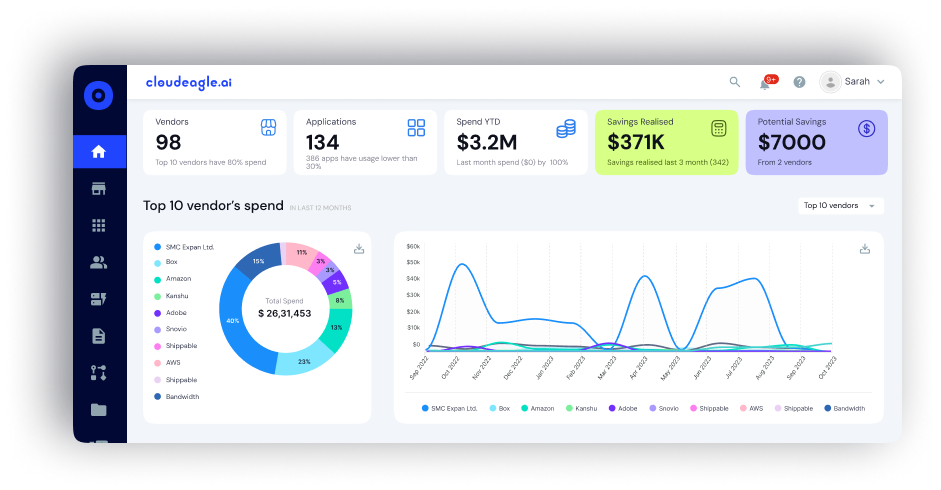
This centralization simplifies the review process, allowing administrators to quickly assess who has access to what, identify unnecessary permissions, and make informed decisions efficiently.
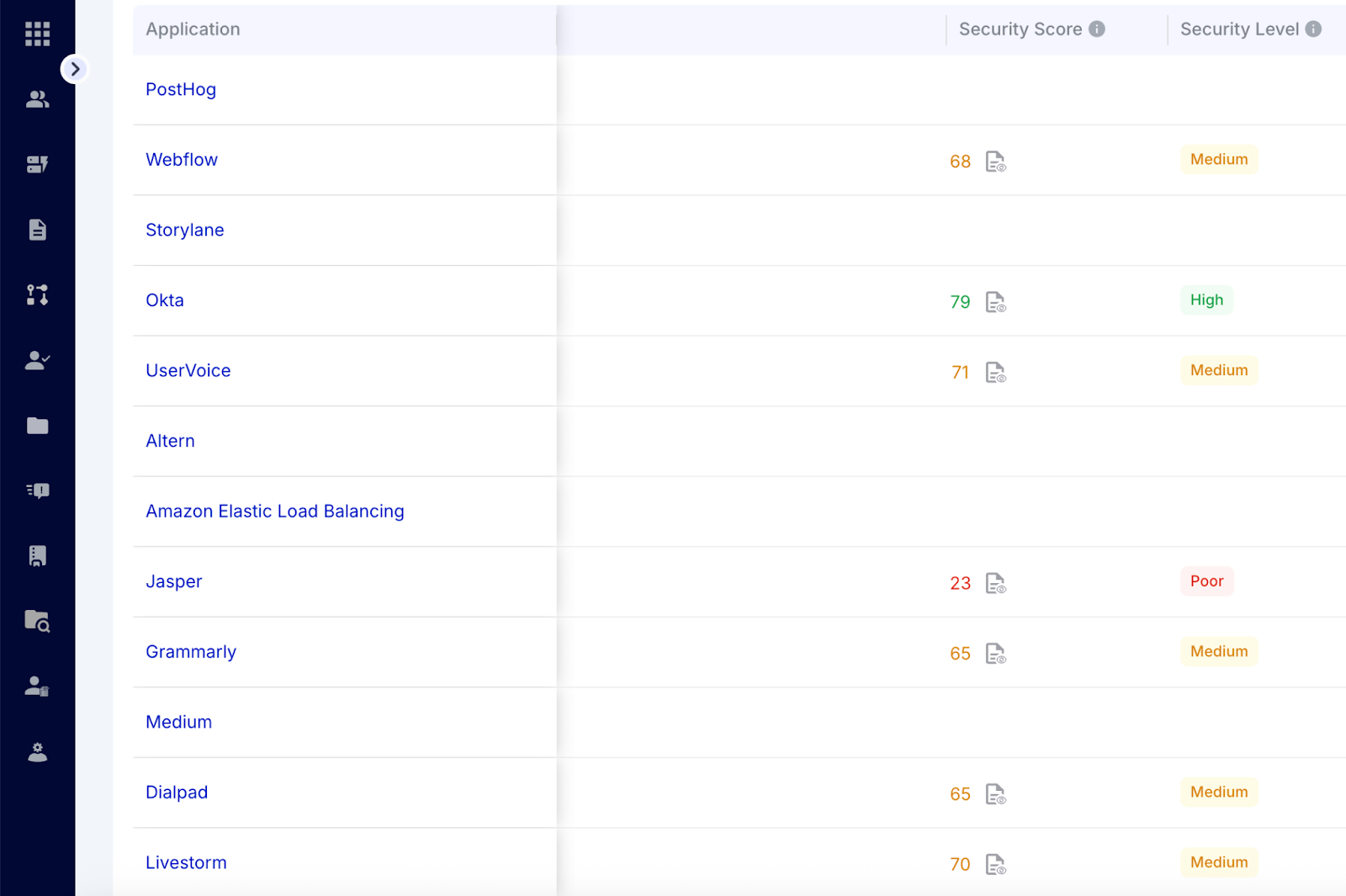
3. AI-Driven Risk Detection
CloudEagle.ai uses AI to identify unusual access patterns, overprivileged users, dormant accounts, or unauthorized permissions. By automatically flagging high-risk users, IT teams can focus on critical issues first, reducing the likelihood of human error and ensuring that risky access is addressed proactively.
4. Role-Based and Contextual Access Mapping
Access is intelligently mapped based on department, job role, or location. CloudEagle.ai ensures that each employee receives permissions aligned with their responsibilities, avoiding over-provisioning and unnecessary access.
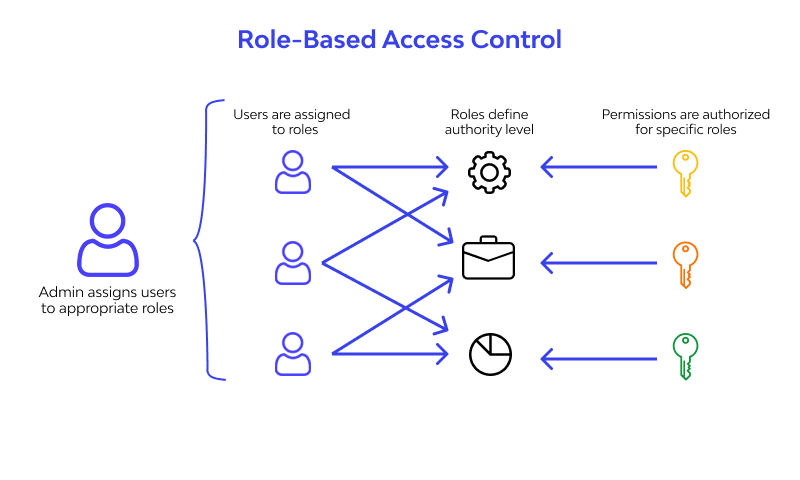
When roles or responsibilities change, access rules can be dynamically updated, ensuring continuous compliance and minimizing security gaps.
5. Seamless Integration with SaaS and Identity Platforms
CloudEagle.ai integrates with over 500 SaaS applications, identity providers (IDPs), and IT systems, pulling real-time access data automatically. This ensures that the platform always reflects the latest user access across all connected systems, eliminating manual reconciliation and providing a single source of truth for access management.
6. Automated Deprovisioning of Access
With CloudEagle.ai’s automated deprovisioning workflows, users can be removed from applications they no longer need. When excessive or inappropriate access is detected, the system automatically revokes permissions or routes them through simple approval workflows.
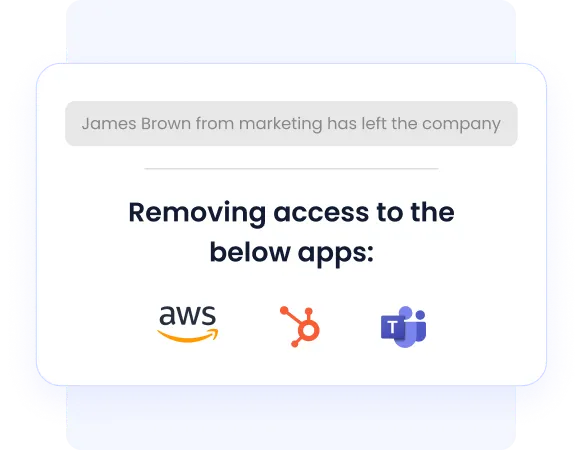
This reduces security risks, prevents human error, and ensures unnecessary access is removed promptly without adding extra work for IT teams.
Discover how RecRoom Automated Employee Offboarding and Saved $200K Annually with CloudEagle.ai.
7. Audit-Ready Reporting and Compliance
Every access review activity is automatically logged, producing detailed, audit-ready reports. Organizations can easily demonstrate compliance with standards like ISO 27001, SOC 2, GDPR, and others. CloudEagle.ai removes the need for hours of manual documentation, helping companies pass audits smoothly while maintaining transparency.
8. Flexible Review Customization and Multi-Application Reviews
Administrators can tailor review workflows by application, department, or role, and run multiple reviews simultaneously across different apps. This flexibility improves efficiency, reduces administrative burden, and ensures consistent, accurate reviews across the enterprise.
9. Improved Security Posture and Reduced IT Burden
By automating access reviews, CloudEagle.ai frees IT teams from repetitive manual tasks, reduces the risk of errors, and enforces least-privilege access across all apps. This strengthens overall security while allowing IT staff to focus on strategic initiatives, operational improvements, and proactive risk management.
See how CloudEagle.ai made a difference: Alice Park from Remediant shares that the platform streamlined their app access management, saving 1,470 hours annually on onboarding and 1,690 hours on offboarding after implementation.
Conclusion
IT General Controls (ITGCs) are the foundation of a secure and compliant IT environment. Proper access management, reliable backups, and continuous monitoring help reduce operational risks, prevent security breaches, and keep organizations compliant.
Using a structured ITGC audit checklist lets companies identify gaps early, take corrective actions, and improve governance across all IT systems. Automation and consistent enforcement make audits faster, enhance decision-making, and lower overall organizational risk.
For enterprises aiming to simplify ITGC management, enhance compliance, and gain real-time visibility, a centralized platform like CloudEagle.ai can automate access reviews, streamline audits, and provide actionable insights, all from a single solution.
Ready to automate access reviews and simplify ITGC management?
Schedule a demo with CloudEagle.ai to see how easy it can be.
FAQs
1. What does ITGC mean in audit?
ITGC stands for IT General Controls. These are the foundational policies, procedures, and controls that ensure IT systems are reliable, secure, and support compliance with regulations and audits.
2. What is the difference between ITGC and SOX audit?
ITGC audits focus on the overall IT control environment, covering access, change management, backups, and security. A SOX audit specifically evaluates financial reporting and requires ITGCs as part of compliance for internal control over financial reporting (ICFR).
3. What is the difference between ISO 27001 and ITGC?
ISO 27001 is an international standard for information security management systems (ISMS) with broader organizational policies. ITGCs are specific controls within IT systems that support ISO 27001 compliance, focusing on operational security, access, and change management.
4. Who is responsible for ITGC?
ITGC's responsibility spans IT, security, and compliance teams. IT implements the controls, security ensures protection of data and systems, and compliance or internal audit teams verify effectiveness. Executive leadership also oversees accountability.
5. How are ITGCs tested?
Testing ITGCs means checking if controls are designed well and actually work. This includes reviewing documents, observing processes, and sampling system access, change management, backups, and incident response logs. Automated tools can also track control compliance in real-time, making testing faster and more accurate.

%201.svg)







.avif)




.avif)
.avif)




.png)









