HIPAA Compliance Checklist for 2025

ISO 27001 isn’t just a certification you chase before an audit.
It’s a signal to customers, partners, and regulators that your organization takes information security seriously.
Yet many teams approach ISO 27001 compliance reactively. They scramble for evidence, chase control owners, and patch gaps at the last minute. According to ISO survey data, nearly 40% of first-time ISO 27001 audits fail due to missing or inconsistent evidence, not because controls don’t exist.
In this blog, you’ll get a practical ISO 27001 requirements checklist, understand what auditors actually validate, why organizations fail certification, and how to prepare for ISO 27001 compliance with far less friction.
TL;DR
- ISO 27001 requires continuous controls, not one-time audit prep.
- Access reviews, data protection, and vendor security drive audit outcomes.
- Missing evidence and Shadow IT are the top reasons organizations fail certification.
- A structured ISO 27001 requirements checklist reduces audit risk and effort.
- CloudEagle.ai automates access governance and audit-ready evidence collection.
1. What Is ISO 27001 Compliance?
ISO 27001 compliance means implementing and maintaining an Information Security Management System (ISMS) to protect sensitive information across people, processes, and technology.
It focuses on identifying risks, applying appropriate controls, and continuously improving the organization’s security posture.
Unlike one-time audits, ISO 27001 is cyclical. Organizations must demonstrate that controls are:
- Clearly defined
- Properly implemented
- Regularly reviewed
- Continuously improved
ISO 27001 requirements span critical areas such as:
- Access control and identity management
- Data protection and privacy
- Vendor and third-party security
- Incident response and monitoring
- Governance and risk management
According to IBM’s Cost of a Data Breach report, organizations with mature security governance frameworks reduce breach costs by up to 30%, making ISO 27001 a strong business and risk-reduction investment.
2. Why Does ISO 27001 Matter?
ISO 27001 matters because it directly impacts security outcomes, customer trust, and audit readiness. It’s no longer limited to regulated industries; SaaS, fintech, healthcare, and enterprise vendors are now expected to meet ISO 27001 certification requirements.
A. Security Assurance
ISO 27001 provides a structured, repeatable framework for identifying risks and enforcing controls conistently across the organization.
- Reduces reliance on tribal knowledge and ad-hoc decisions
- Standardizes access control and risk treatment
- Strengthens monitoring and review processes
According to Verizon’s DBIR, 74% of breaches involve privilege misuse or credential abuse, both directly addressed by ISO 27001 access control requirements.
B. Vendor Trust
Enterprise buyers now expect proof of security maturity before engaging with vendors.
- Demonstrates commitment to information security
- Shortens security reviews and procurement cycles
- Differentiates vendors in competitive evaluations
Gartner reports that 60% of organizations require ISO 27001 or equivalent certification from critical vendors, making compliance a revenue enabler, not just a checkbox.
C. Audit & Certification Readiness
ISO 27001 turns audits into a predictable process rather than a last-minute scramble.
- Reusable controls and evidence pipelines
- Faster response to customer and regulatory audits
- Reduced audit fatigue across teams
Organizations with mature ISMS programs report up to 50% reduction in audit preparation time after their first successful certification cycle.
3. ISO 27001 Checklist
An effective ISO 27001 requirements checklist focuses on three things auditors care about most: consistency, ownership, and evidence. Controls without proof are treated as gaps.
Below are the critical control areas auditors evaluate in every ISO 27001 audit.
A. User Access Validation
Access control remains one of the most failed ISO 27001 audit requirements. Auditors want proof that access is granted intentionally and removed promptly.
Checklist items include:
- Documented access control policies
- Role-based access assignment
- Periodic user access reviews
- Joiner–mover–leaver workflows
- Evidence of least-privilege enforcement
CloudEagle’s IGA data shows 48% of organizations have at least one ex-employee with active system access, a direct ISO nonconformity.
B. Data Protection Verification
ISO 27001 compliance requirements emphasize data confidentiality, integrity, and availability. Data controls must exist throughout the lifecycle.
Checklist items include:
- Data classification frameworks
- Encryption for data at rest and in transit
- Secure backups and recovery testing
- Restricted access to sensitive datasets
- Audit logs for data access
IBM reports that breaches involving unencrypted data cost 28% more on average, making encryption evidence critical during audits.
C. Third-Party Security Checks
Vendor risk is one of the fastest-growing audit focus areas. ISO 27001 certification requirements demand visibility into third-party access and security posture.
Checklist items include:
- Vendor risk assessments
- Security clauses in vendor contracts
- Periodic vendor access reviews
- Defined vendor offboarding procedures
- Evidence of ongoing monitoring
According to Ponemon Institute, 51% of breaches originate from third-party access, making vendor controls a high-risk audit area.
D. Incident Response Readiness
ISO 27001 audit requirements include having a documented, tested incident response plan. Auditors look for readiness, not just documentation.
Checklist items include:
- Incident response policy
- Defined escalation and communication paths
- Incident logging and tracking
- Tabletop or simulation exercises
- Post-incident reviews
Organizations that test incident response plans reduce breach containment time by over 50%, according to IBM.
E. Control Ownership Checks
Auditors consistently flag missing control ownership. Every ISO control must have a named, accountable owner.
Checklist items include:
- Documented control owners
- Defined responsibilities
- Evidence of owner reviews
- Approval workflows
- Change tracking
Lack of ownership is one of the top three causes of ISO 27001 audit failures.
F. Ongoing Control Reviews
ISO 27001 is built on continuous improvement. Controls must be reviewed, updated, and validated regularly.
Checklist items include:
- Scheduled internal audits
- Risk assessment updates
- Management review meetings
- Corrective action plans
- Evidence of improvements
Organizations that conduct quarterly control reviews experience 35% fewer audit findings compared to annual-only reviews.
4. ISO 27001 Checklist Template
5. Why Organizations Fail ISO Certification?
Most organizations fail ISO 27001 certification not because they lack controls, but because they lack proof, consistency, or ownership.
A. No Proof of Access Reviews
Access controls without evidence rarely pass ISO audits. Manual processes often fail under scrutiny.
- No logged or repeatable access review process
- Spreadsheet-based reviews with no audit trail
- Email approvals that can’t be verified
- Inconsistent review frequency across systems
ISO auditors expect documented, repeatable, and traceable access reviews.
B. Shadow IT
Untracked applications introduce unmanaged risk and automatic audit gaps.
- Apps operating outside IT visibility
- No centralized access or ownership
- Missing logging and monitoring
- No vendor risk or compliance reviews
Gartner estimates 30–40% of SaaS usage exists outside IT visibility, making Shadow IT a frequent cause of audit failure.
C. Missing Controls Evidence
Policies alone don’t satisfy ISO requirements; execution must be provable.
- No logs to show control operation
- Missing screenshots or review records
- Incomplete incident or risk documentation
- Controls defined but not enforced
Auditors validate what was done, not what was intended; missing evidence remains one of the most common ISO findings.
6. How CloudEagle.ai Supports ISO 27001 Compliance?
ISO 27001 requires organizations to demonstrate strong controls around information assets, access management, operational security, and auditability.
While ISO 27001 certification is a process, CloudEagle.ai acts as a compliance enabler, helping IT, Security, and GRC teams operationalize key controls with less manual effort and lower risk.
A. Complete Visibility Into SaaS Assets (Including Shadow IT)
ISO 27001 requires organizations to identify and manage all information systems that process data. In modern enterprises, this is difficult due to SaaS sprawl and employee-purchased tools.

CloudEagle ensures no application or data path remains undocumented.
- Discovers approved and unapproved SaaS and AI tools
- Correlates data from SSO, finance, and login activity
- Maintains a continuously updated application inventory
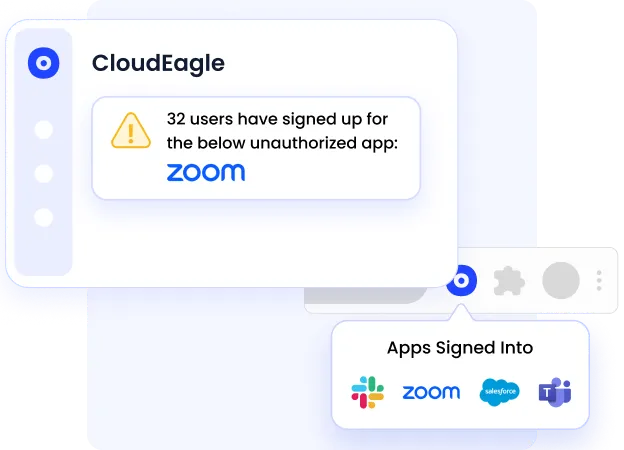
ISO alignment: Asset management, risk identification
B. Centralized Access Governance Across All SaaS
Access control is a foundational ISO 27001 requirement, yet many SaaS tools operate outside traditional IAM coverage.
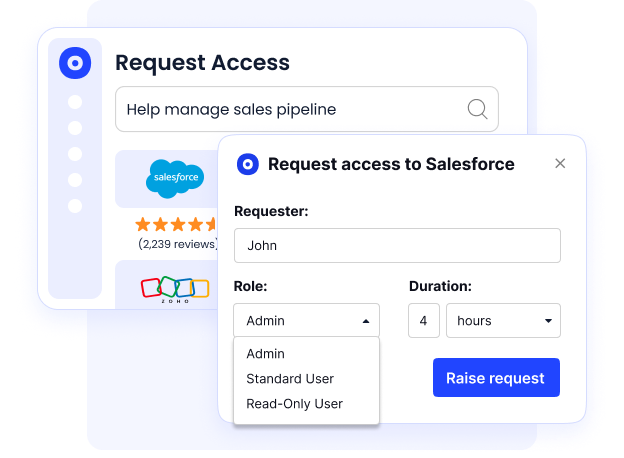
CloudEagle extends governance across the entire SaaS stack, ensuring access is controlled, reviewed, and aligned with responsibility.
- Enforces role-based and least-privilege access
- Governs both SSO and non-SSO applications
- Provides visibility into user access and ownership
ISO alignment: Access control, user accountability
C. Automated Joiner–Mover–Leaver Controls
ISO 27001 expects access to change promptly when employee roles change or end. Manual onboarding and offboarding introduce delays and audit risk.
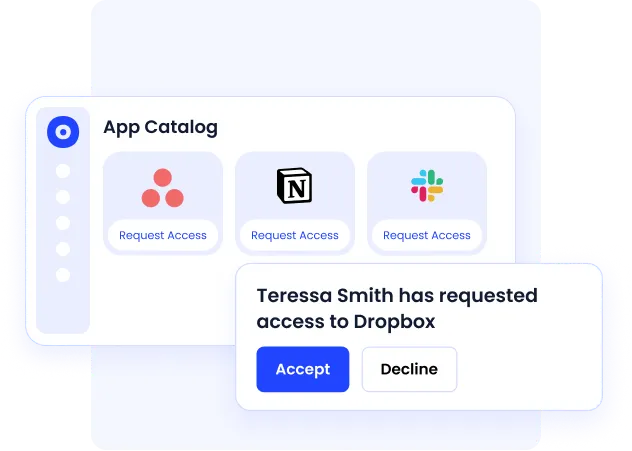
CloudEagle automates JML to ensure access is always current.
- HRIS-driven onboarding and offboarding
- Automatic access updates on role changes
- Eliminates orphaned and lingering accounts

ISO alignment: Access lifecycle management
D. Continuous Access Reviews With Audit Evidence
Periodic access reviews must be provable during ISO audits. Spreadsheet-based reviews often fail due to missing evidence or inconsistency.
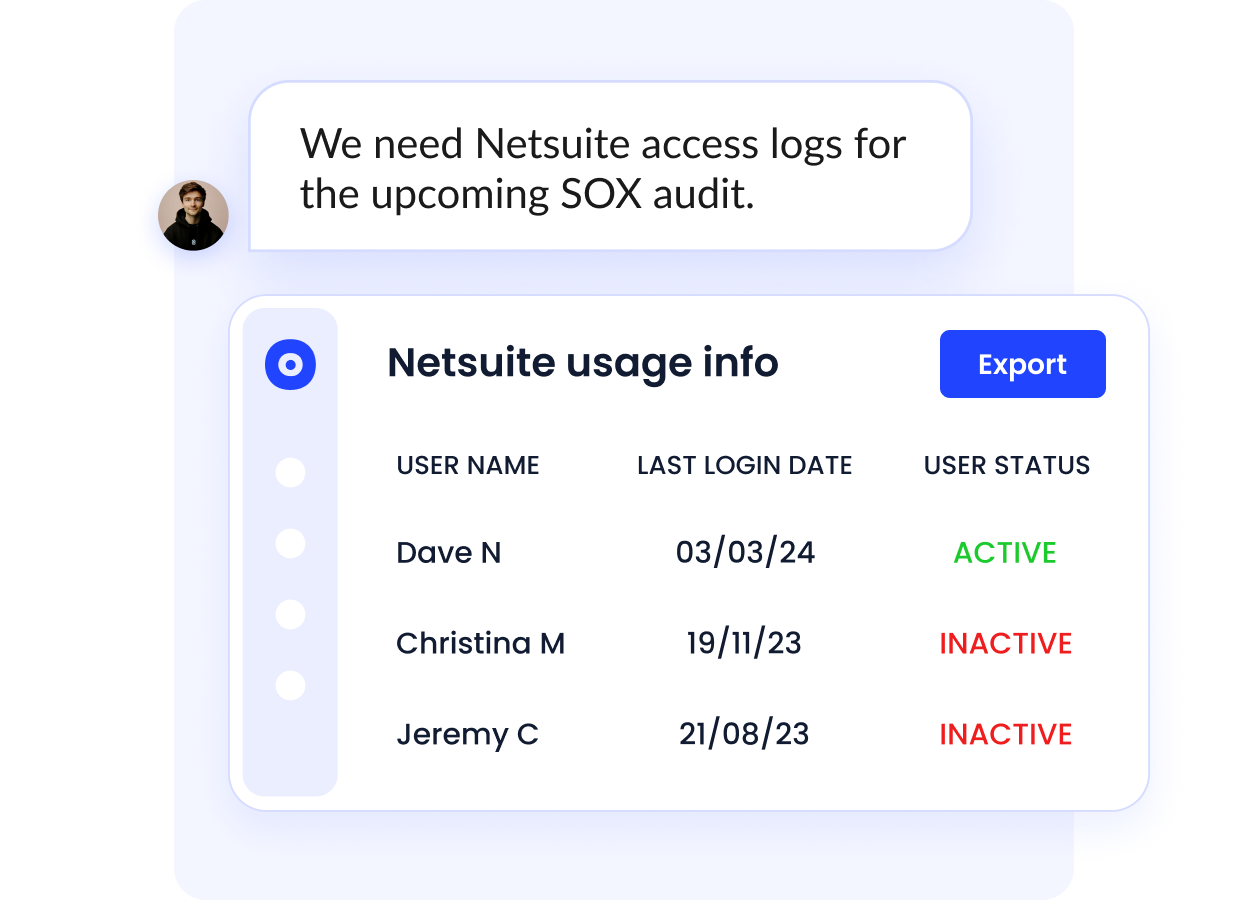
CloudEagle enables continuous, evidence-backed access certifications.
- Automated access review workflows
- Reviewer validation and privilege cleanup
- Timestamped, exportable audit logs
ISO alignment: Control monitoring, audit readiness
E. Centralized Audit Logs and Reporting
ISO auditors validate execution, not intent. Dispersed logs and manual screenshots slow audits and increase findings.

CloudEagle centralizes evidence into a single, audit-ready system.
- Centralized access logs and approval records
- On-demand audit reports
- Faster internal and external audit cycles
ISO alignment: Logging, evidence, compliance verification
F. Reduced Risk and SaaS Spend
ISO 27001 emphasizes risk reduction, and unmanaged licenses and access increase both financial and security exposure.
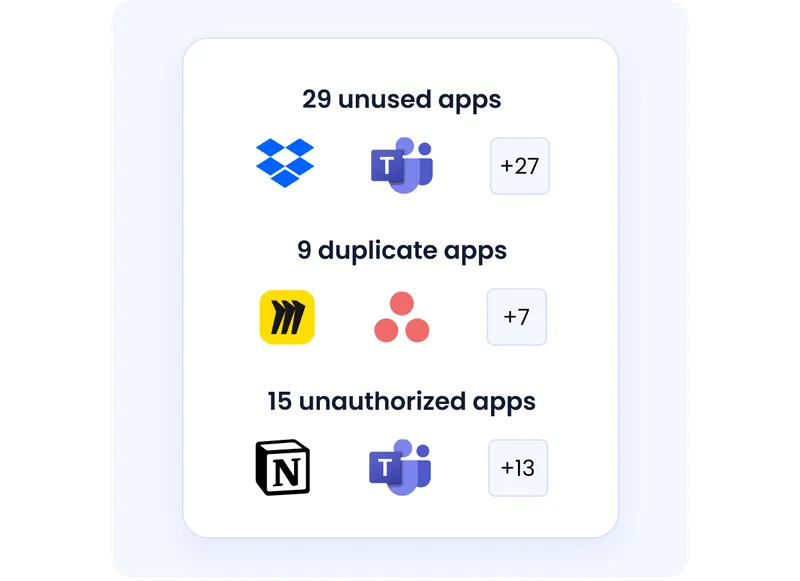
CloudEagle helps organizations reduce waste while strengthening compliance.
- Identifies unused licenses and excess access
- Detects duplicate or risky applications
- Lowers spend while improving security posture
ISO alignment: Risk management, operational efficiency
7. Final Words
ISO 27001 compliance isn’t about passing one audit and moving on. It’s about building a repeatable, defensible security system that can scale as your organization grows. Without structure, evidence, and ownership, even strong security programs struggle during audits.
A clear ISO 27001 requirements checklist helps teams stay audit-ready year-round. When access controls, data protection, vendor security, and incident response are reviewed continuously, compliance becomes predictable instead of stressful.
CloudEagle.ai makes this shift practical by automating access reviews, detecting Shadow IT, mapping control ownership, and generating audit-ready evidence across your SaaS stack. Instead of chasing spreadsheets and screenshots, teams get continuous visibility and compliance built into daily operations.
Book a free demo and see how CloudEagle.ai simplifies ISO 27001 compliance.
FAQ
1. What are the three principles of ISO 27001?
Confidentiality, integrity, and availability—often referred to as the CIA triad—form the foundation of ISO 27001.
2. What are the 6 stages of the ISO 27001 certification process?
Gap analysis, risk assessment, control implementation, internal audit, management review, and external certification audit.
3. What should an ISO 27001 checklist include?
Access controls, data protection, vendor risk management, incident response, control ownership, and ongoing review of evidence.
4. How long does ISO 27001 certification prep take?
Most organizations take 3–6 months for preparation, depending on maturity and tooling.
5. Why do companies fail ISO certification?
Common reasons include missing evidence, unmanaged access, Shadow IT, and a lack of control over ownership.

%201.svg)










.avif)




.avif)
.avif)




.png)









