HIPAA Compliance Checklist for 2025

Most teams believe they know the software their organization runs until a deeper audit tells a different story. Cisco found that 80% of employees use apps not cleared by IT, and even 83% of IT professionals admit to doing the same. Only 8% of enterprises truly understand how widespread their Shadow IT actually is.
Shadow IT grows in the spaces where visibility fades, draining budgets, weakening governance, and quietly creating security gaps.
In this article, we’ll explore how CloudEagle detects and controls Shadow IT, where current tracking methods fall short, and how better visibility leads to stronger control and compliance.
TL;DR
- Shadow IT is everywhere: Up to 60% of SaaS apps operate outside IT’s visibility, creating compliance, cost, and security risks.
- Current methods fall short: Manual tracking, spreadsheets, and SSO reviews miss most unsanctioned tools and lead to outdated data.
- When left unchecked, Shadow IT causes duplicate purchases, audit failures, and unnecessary spend, while weakening governance and employee trust.
- CloudEagle fixes the blind spots: With AI-powered discovery, 500+ integrations, and automated alerts, it detects and controls unauthorized apps in real time.
- The smarter way forward: CloudEagle unifies app, spend, and usage data into one dashboard, helping teams save 10-30% on SaaS costs while improving security and compliance.
How do IT Teams Currently Track Shadow IT Today?
Most IT and finance teams still rely on manual, disconnected systems to track SaaS usage. Spreadsheets, expense reports, and one-off audits create the illusion of control, but the reality is far less reassuring. According to the IGA Report, nearly 60% of SaaS applications operate outside IT’s visibility, leaving organizations blind to a large portion of their software ecosystem.
The problem isn’t just technical; it’s cultural. As Bob Violino noted in Information Management, “Shadow IT flourishes when organizations stifle collaboration.” When teams feel restricted by slow approval processes, they seek out their own tools to get work done faster, often at the cost of compliance and control.
1. Spreadsheets and Expense Reports
Many teams build massive spreadsheets to track licenses, users, and renewals.
These take weeks to compile and are often outdated by the time they’re finalized. Without real-time updates, IT struggles to identify which apps are actually being used, leading to inaccurate data and poor decision-making.
2. Credit Card Transaction Monitoring
Some organizations review credit card statements to find unapproved purchases. It’s a reactive approach; by the time IT discovers the spend, the app is already active, the invoice is paid, and the data may already be flowing outside corporate boundaries.
3. Manual SSO Log Reviews
Checking Single Sign-On (SSO) logs is another common method. But it captures only a fraction of actual usage, especially when employees sign up for free trials or personal accounts that never touch SSO, leading to a false sense of security.
4. Employee Self-Reporting
Relying on employees to report every new tool they use sounds ideal, but in practice, it’s fragmented and inconsistent. Most employees don’t realize the compliance risks, and those who do rarely prioritize reporting.
5. Lack of Centralized Oversight
Because these methods operate in silos, IT has no unified view of all SaaS applications across the company. Employees freely purchase software with personal or corporate cards, making it impossible to enforce security policies or manage costs effectively.
In the end, Shadow IT thrives in these visibility gaps, quietly increasing risk, spend, and complexity while IT teams remain several steps behind.
What Happens When Shadow IT Goes Untracked?
When Shadow IT slips under the radar, it doesn’t just create minor operational hiccups; it quietly undermines the foundation of IT governance. A lack of visibility sets off a ripple effect across security, compliance, finance, and productivity.
Cisco’s research found that only 8% of enterprises truly understand the scope of Shadow IT within their organization. That means most leaders are managing risks they can’t even see. Below are the real consequences that follow when Shadow IT remains unchecked.
1. Security Vulnerabilities Multiply
Unapproved applications often bypass corporate security controls such as firewalls, identity management, or Single Sign-On (SSO). This increases the organization’s attack surface, giving bad actors more ways to exploit weak points.
Unauthorized apps also don’t adhere to internal security protocols, exposing sensitive data to breaches and privilege creep, where employees retain access to apps they no longer need. Each hidden account becomes another open door that no one’s guarding.
As Kevin Townsend asserts in SecurityWeek, the more confidence a company has in its ability to address security threats from the technologies employees bring on, the greater acceptance there is of employee choices.
He writes that when companies manage from a strong security posture, “it solves the problem of Shadow IT by finding methodologies to include staff preferences so that it is no longer 'shadow' IT. From that position, organizations can enjoy all the benefits of employee app choice and use, without being stymied by the security threat of uncontrolled Shadow IT.”
2. Compliance Risks Escalate
When IT doesn’t know what software is in use, compliance becomes a guessing game. Untracked apps may fail to meet frameworks like GDPR, SOC2, or HIPAA, putting organizations at risk of violations or failed audits.
During audits, missing logs or incomplete access records from Shadow IT make it nearly impossible to demonstrate proper governance. One missed SaaS subscription could turn into a costly non-compliance penalty.
3. Costs Spiral Out of Control
Without oversight, duplicate purchases and redundant tools slip through easily. Marketing might buy one analytics app while Sales subscribes to another with the same features, both billed monthly, both untracked.
This redundant spending compounds over time. Unused licenses, overlapping apps, and auto-renewals from forgotten contracts lead to bloated SaaS costs. As noted in CloudEagle’s messaging framework, procurement teams can’t negotiate effectively when they don’t even know what’s being used or paid for.
4. Operational Inefficiencies Increase
The absence of a unified system forces IT to rely on manual tracking, wasting hours chasing spreadsheets and card statements. These reactive processes slow down incident response, onboarding, and vendor management.
Meanwhile, employees face inconsistent access to the tools they need, resulting in frustration and lower productivity. As Marcel Schwantes wrote for Inc., restricting preferred collaboration tools can lead to “frustration and neglect which eventually lead to low morale, burnout, inefficient operations and turnover.”
5. Visibility and Governance Collapse
Shadow IT thrives in blind spots.
Without a central system of record, organizations experience tool sprawl - a tangled web of overlapping apps, multiple logins, and fragmented data. IT and procurement lose sight of vendor contracts and renewal timelines, making governance reactive rather than strategic.
The longer this continues, the harder it becomes to untangle. Untracked apps don’t just waste money; they weaken decision-making by hiding the true cost and scope of the SaaS ecosystem.
Leaving Shadow IT unchecked leads to a perfect storm of wasted spend, security blind spots, and compliance risks. The cost isn’t just financial; it’s strategic. Organizations lose control of their technology landscape, leaving IT teams to manage chaos they can’t see.
How CloudEagle Detects and Controls Shadow IT
Think about how most IT teams try to track their software stack today.
They rely on scattered systems, delayed reports, or an occasional finance audit that surfaces a few surprise charges. But by the time those tools show up, they’ve already been paid for, used by multiple teams, and connected to company data.
That’s where CloudEagle changes the game.
CloudEagle doesn’t wait for a manual audit or expense report. It catches Shadow IT at the source where usage begins. By connecting every data stream that shows how software is actually used, not just what’s officially approved, it gives you complete visibility into your real SaaS environment.
1. Deep, Real-Time Integrations Across Your Stack
Every Shadow IT footprint begins in a different system: an SSO login here, a credit-card charge there, a browser extension installed quietly in the background. CloudEagle connects to all of them.
With 500+ integrations spanning SSO, finance, HRIS, MDM, Netskope, ERD logs, ITSM platforms, and cloud services, CloudEagle pulls together the data that typically lives in silos.
This single view shows:
• which apps employees are using
• which subscriptions were purchased on personal or corporate cards
• which apps are used on BYOD or remote devices
• who owns each app
• what data the app touches
• whether the app is SCIM or non-SCIM
• whether the app is approved, risky, or completely unknown
Without this foundation, Shadow IT remains invisible. With it, IT leaders get a live, correlated map of their real SaaS ecosystem, not a stitched-together spreadsheet or an occasional audit snapshot.
2. AI-Driven Discovery Across Your SaaS Stack
Once the integrations are in place, CloudEagle’s AI begins analyzing behavioral signals across identity, usage, spend, and device activity.
It scans identity activity from tools like Okta and Microsoft AD, flags unfamiliar logins, and correlates these events with browser activity, app traffic, and credit-card purchases. This is critical in remote and BYOD environments, where apps are installed outside corporate networks and never touch IT-managed devices.
This is where hidden tools emerge:
• free trials never reported to IT
• AI tools and browser extensions collecting sensitive data
• non-SCIM tools purchased at the team level
• personal card subscriptions used for business work
• tools introduced by contractors, interns, or temporary staff
CloudEagle then performs risk scoring on every discovered app, evaluating:
This single view shows:
• which apps employees are using
• which subscriptions were purchased on personal or corporate cards
• which apps are used on BYOD or remote devices
• who owns each app
• what data the app touches
• whether the app is SCIM or non-SCIM
• whether the app is approved, risky, or completely unknown
This helps IT prioritize which tools require immediate action and which simply need review.
3. Unified Dashboard for Full Visibility
Instead of chasing information across reports, logs, receipts, and conversations, IT teams get one place where everything comes together.
CloudEagle’s dashboard displays:
• vendor spend, renewal dates, and usage
• contract metadata
• SCIM vs non-SCIM classification
• app ownership and approval status
• risk scores and compliance posture
• user-level access insights
• where the app is being accessed (BYOD, remote, office devices)
It turns raw data into context, helping teams instantly understand what exists, who’s using it, and what it means for security and spend.
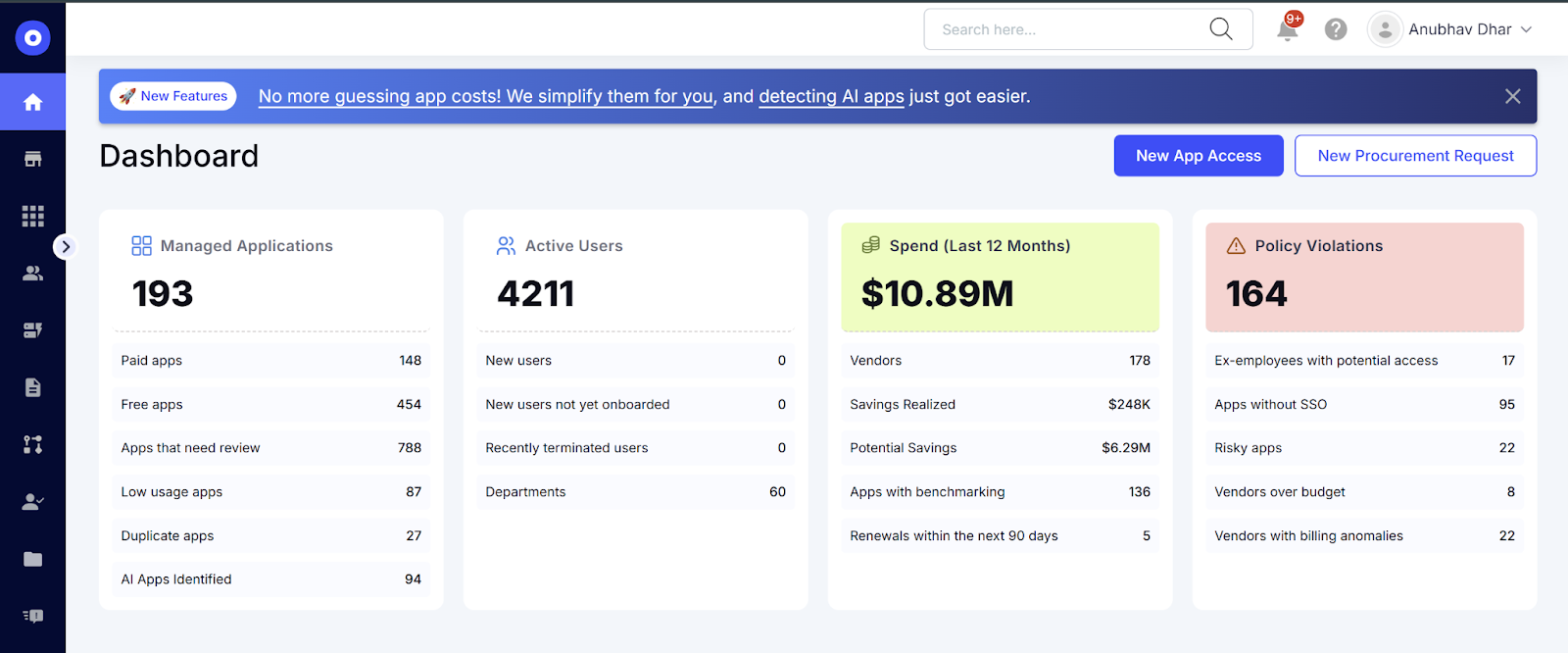
4. Real-Time Alerts, Before Problems Escalate
Shadow IT grows quietly when no one is watching. CloudEagle stops that. When a new or risky application appears, teams receive instant alerts through Slack or email, complete with user details, usage trends, cost impact, risk score, device type (managed vs BYOD), and data sensitivity involved.
CloudEagle also uses behavioral analytics to flag:
• suspicious access attempts
• unusual login patterns
• unauthorized privilege escalations
• attempts to sync sensitive files into unapproved apps
This gives IT the ability to intervene before the tool spreads across departments or exposes sensitive data.
5. Tracking Spend to Eliminate Hidden Costs
Every Shadow IT tool starts with a swipe. CloudEagle matches financial transactions against the approved vendor list, exposing:
• unapproved purchases
• duplicate subscriptions
• overlapping tools
• redundant licenses
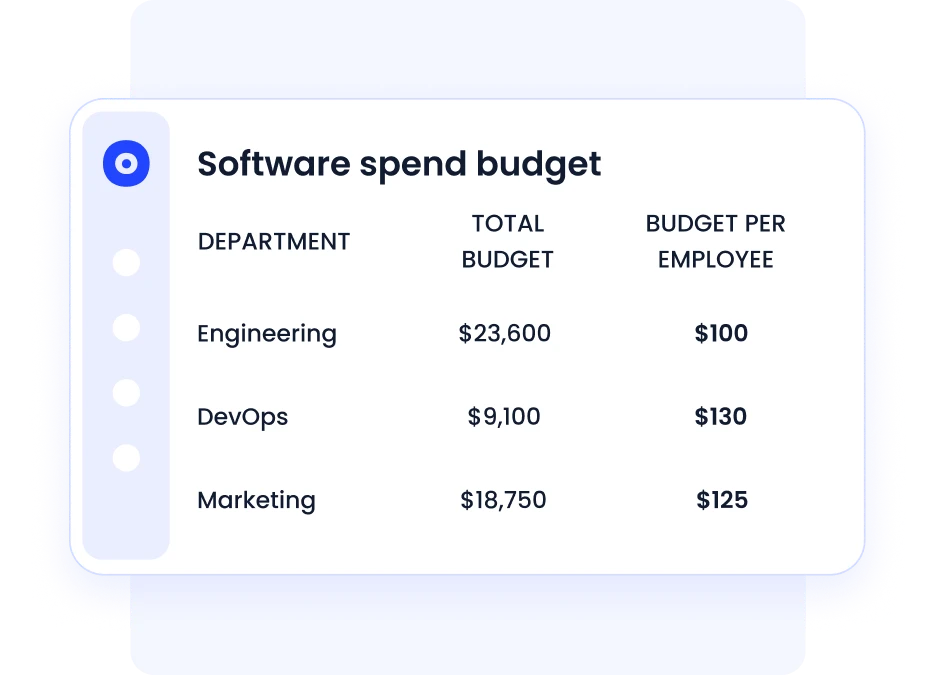
By correlating spend with usage, access, and ownership, CloudEagle ensures no dollar leaves the organization without visibility, approval, or accountability.
This is often where companies find 10–30% in reclaimable SaaS spend tied directly to Shadow IT behaviors.
6. Smart Automation to Prevent Future Shadow IT
Finding Shadow IT is one thing; preventing it is another.
CloudEagle automates provisioning, deprovisioning, and access governance across SCIM and non-SCIM apps, ensuring users receive access only to approved tools. When someone leaves the company or changes roles, their access is revoked automatically across the entire SaaS stack, including apps discovered through Shadow IT.
This includes:
• enforcing least-privilege access
• removing unused entitlements
• blocking risky apps by policy
• automated cleanup of unauthorized tools
• continuous verification of entitlements
• full audit logs for compliance reviews
This would prevent delays, backlogs, or lingering permissions.
This creates a closed governance loop where unauthorized tools are detected early, assessed quickly, and prevented from resurfacing, whether they originate from BYOD devices, remote work habits, personal card purchases, or team-level decisions.
Why CloudEagle Is the Smarter Way to Track Shadow IT
Most organizations discover Shadow IT the hard way through security incidents, budget overruns, or compliance surprises. CloudEagle changes that outcome by transforming discovery into control, and control into measurable results.
It’s not about adding another tool to monitor SaaS usage. It’s about building a foundation where visibility, cost savings, and compliance all happen automatically.
1. Visibility That Brings Every App Into Focus
When IT, finance, and procurement teams see the same data, decisions get sharper. CloudEagle gives them a single source of truth - a unified view of every SaaS app, its cost, and its usage.
No more disconnected spreadsheets or surprise renewals. Every application is visible, categorized, and accounted for.
With integrations across SSO, finance systems, CLMs, and 500+ SaaS systems, CloudEagle brings together everything that affects your SaaS landscape in one dashboard.
2. Security and Compliance Without the Guesswork
Unapproved tools increase the attack surface. CloudEagle helps teams shrink it. By automatically detecting and managing Shadow IT, it reduces security risks and strengthens compliance across frameworks like SOC 2, GDPR, and HIPAA.
Continuous monitoring ensures that only approved tools stay active, while automated access reviews help maintain least-privilege control across all users and apps.
3. Cost Savings That Compound Over Time
Every hidden tool represents unnecessary spending on duplicate subscriptions, unused licenses, or overlapping apps. CloudEagle helps organizations reclaim that waste.
By consolidating vendors and optimizing license usage, teams typically save 10-30% on SaaS costs within the first few months. These savings don’t come from cuts; they come from visibility.
4. Procurement Decisions Backed by Real Data
Procurement teams often negotiate without knowing the full SaaS picture. CloudEagle fixes that.
With usage, spend, and contract data all in one place, teams can benchmark vendors, forecast renewals, and negotiate better deals with confidence.
What used to be guesswork becomes a data-driven strategy for managing SaaS growth.
5. Fast Results, Minimal Effort
CloudEagle delivers value in days, not weeks. Its AI automatically extracts contract metadata, ingests data from multiple systems, and starts detecting Shadow IT almost instantly.
Teams can also build new connectors quickly when needed, giving CloudEagle the flexibility to scale as your SaaS stack grows.
CloudEagle isn’t about managing Shadow IT; it’s about eliminating the uncertainty around it. You get full visibility, lower risk, and smarter spending. That’s what makes it the smarter, faster, and more complete way to govern your SaaS ecosystem.
Ready to Catch Shadow IT Before It Spreads?
You’ve seen how Shadow IT drains budgets, weakens security, and clouds decision-making. CloudEagle flips that narrative by giving teams full visibility, automated alerts, and measurable control.
If your SaaS stack feels like a mystery, it’s time to uncover it. CloudEagle detects, manages, and prevents Shadow IT so your teams stay secure, compliant, and cost-efficient without the manual chase. Book a demo or start a free trial to see how it works.
.avif)
%201.svg)







.avif)




.avif)
.avif)




.png)









