Invisible Apps, Hidden Insider Threats:
The AI-Powered Future of IGA
Executive Summary
Today, 60% of AI and enterprise SaaS applications operate outside IT’s visibility. Employee-bought AI & SaaS, and unnecessary excessive privileged access have made traditional identity governance tools and processes obsolete. Most breaches now originate from within, not from sophisticated hacks. Unmanaged apps, excessive access and stale permissions are at the root of these breaches.
Manual provisioning, siloed deprovisioning, sporadic access reviews, and a patchwork of legacy IAM tools create delays, compliance risks, and insider threats. In 2025, 80% of companies reported incidents tied to privileged access. Traditional IGA tools were never designed for the unmanaged employee brought AI and SaaS environments we operate in today. Simply having an IAM tool is no longer enough, as not all applications are managed by IT or sit behind an IDP & SSO.
As identity becomes the new security perimeter, forward-thinking companies are starting to treat IT teams with the same urgency and investment as they have thought of security teams.
CIOs and IT teams, who have long been underfunded in this area, are now gaining the visibility, budget, and authority needed to lead this transformation. And with AI as the catalyst, modern IGA programs & tools are delivering not just better security but also better employee productivity, faster operations and better cost controls across the enterprise.
This report is your framework to
activity
Survey Results
Future-Ready Checklist
AI powered Identity and Access Governance (IGA)
While many enterprises rely on Identity and Access Management (IAM) solutions like Okta for security, the reality is that not all applications sit behind these systems and many operate completely outside IT's knowledge.
Enterprises struggle with visibility and control over hundreds of AI and SaaS applications running outside IT oversight, resulting in excessive user privileges, orphaned accounts, and an expanded attack surface ripe for exploitation.
1. Unmanaged AI and SaaS is getting harder to manage
1a. SaaS adoption in organizations
Larger enterprises (10,000+ employees) are expanding their SaaS portfolios by 20-22% as AI tools become operational essentials, while mid-sized companies (500-5,000 employees) follow closely with 19.3% growth, signaling widespread digital transformation across all business sizes.
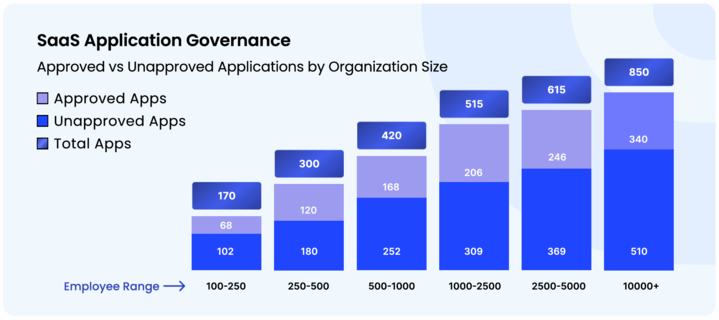
1b. How many of these SaaS apps are approved vs. unapproved (shadow IT)?
While enterprises expand their SaaS stacks by over 19% year-over-year, the alarming reality is that 60% of these AI and SaaS applications operate as shadow IT, completely outside IT's oversight and control.
Shadow IT isn’t just an IT problem, it’s a business risk. Every unapproved app is a potential security gap, a compliance liability, and an unwanted cost. Without centralized visibility, enterprises are flying blind, exposing sensitive data and overspending on redundant tools, says Simon Yeo, CIO, WatchGuard.
The SaaS adoption trend reveals an alarming reality: 60% of applications are operating outside IT's oversight.

But which departments use the most unapproved AI and SaaS tools?
The Marketing department leads in unauthorized app purchases, due to its fast paced, campaign heavy work environment. In contrast, Finance and Legal departments have fewer unauthorized purchases due to stricter procurement oversight and compliance driven workflows.
Key Takeaways:
- 60% SaaS and AI operate outside IT visibility
- Marketing and Sales teams have the most shadow AI apps
1c. The dangers of AI Sprawl
AI tools boost productivity and are becoming like digital workers, but need oversight to prevent security and rule-breaking issues. The main challenge is making sure employees protect sensitive information when using AI, with proper controls and training in place. With the right safeguards, companies can get AI benefits while keeping data safe and following regulations, says Paul Heard, Veteran CIO & Technology Advisor.
AI apps like ChatGPT and DeepSeek boost productivity, but often bypass IT oversight. Employees adopt them quickly, creating new security blind spots. For example, DeepSeek was being used by Monday after launching quietly on a Friday, before IT had a chance to evaluate it. See on the most commonly used AI tools in organizations.
As AI becomes the new digital workforce, enterprises must balance speed with governance. Without proactive guardrails, productivity gains can come at the cost of data exposure.
Key Takeaways:
- 7 out of 10 CIOs see unapproved AI usage as a major risk
- 5% are unsure, signaling a gap in awareness
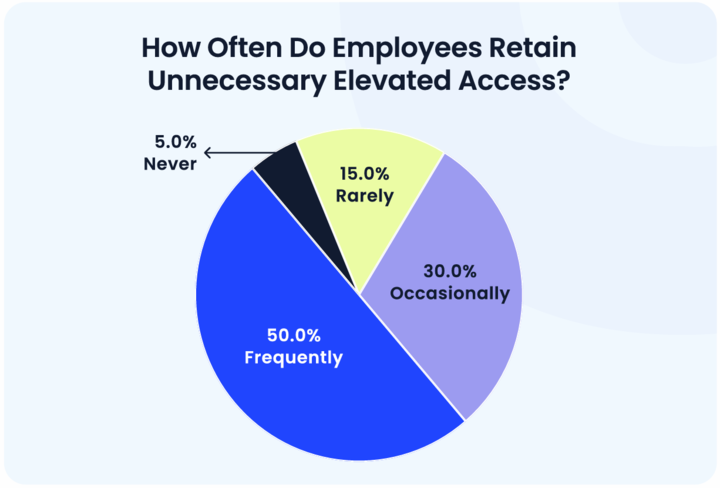
1d. Instances of overprivileged access in applications across departments
Privilege creep happens when employees retain access they no longer need, quietly piling up over time. Without regular access reviews, these outdated permissions become a hidden threat to security and operational integrity, says
Noni Azhar, CIO, ProService Hawaii.
Employees often retain elevated access long after it's needed, a phenomenon known as privilege creep. Without regular reviews, these elevated permissions increases risks across various departments, see Appendix B.
Key Takeaways:
- 1 in 2 employees frequently retain unnecessary privileges, increasing risk
- Only 5% of enterprises strictly enforce least privilege policies.
28% of enterprisers have experienced a major security incident due to overprivileged access, see Appendix B.

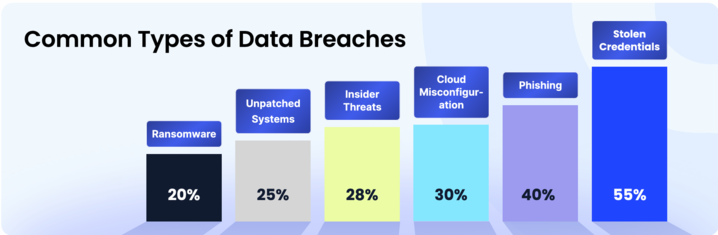
1e. Most compromised data categories and causes
Poor access management is a leading driver of security incidents, with 77% of data breaches involving compromised personal information and credentials, see .
Breaches reveal what's exposed, but stopping them requires understanding the root cause: identity failures. Today's attackers don't hack in, they just log in, with 55% of breaches involving stolen passwords and 40% from phishing attacks.
Relying on passwords alone today is a losing battle. Once credentials are stolen, they grant attackers the same level of access as legitimate users, making breaches almost undetectable until it’s too late. Without stronger authentication and identity controls, businesses are leaving the door wide open for cyber threats, says Teza Mukkavilli, CIO/CISO, Tekion Corp.
2. Employee Onboarding and Offboarding Challenges
2a. Onboarding time breakdown by department (Hours)
Access security starts at employee onboarding. Onboarding times vary across teams due to complex approvals and compliance training, directly impacting both productivity and access governance. For more data on how employee onboarding across teams, see Appendix D.
2b. Poor and slow onboarding leads to lower Digital Employee Experience (DEX)
An exceptional Digital Employee Experience (DEX) is no longer a luxury; it’s a necessity. Delays in access and clunky onboarding don’t just frustrate employees; they slow down business. A seamless digital experience isn’t just about IT efficiency; it’s about enabling people to do their best work from day one, says Lenin Gali, Chief Digital and Business Officer, Atomicwork Seamless day-one access sets the tone for productive employee journeys, but provisioning delays create poor first impressions, with 45% of respondents citing manual provisioning as the biggest impact on their experience, see Appendix E for detailed onboarding delay data.
2c. What percentage of ex-employees retain access to business applications post-termination?
Offboarding isn t always immediate or effective. In many organizations, former employees continue to have access to sensitive systems well after they ve left. We surveyed enterprises to understand how often access lingers, and why it s a growing concern for IT and security teams.
Key Takeaways
- 48% of former employees still retain access
- Only 10% of organizations keep access retention under 10%.
Department-wise, IT teams had the highest rate of retained access (75%) due to admin rights and system dependencies. Finance teams (60%) face complex revocation processes across sensitive, multi-system environments.

Some sales reps may need access post-termination for handoffs, pipeline management, or deal transitions. They also use external platforms (LinkedIn Sales Navigator, prospecting tools, etc.) that may not be centrally managed by IT, causing delays to deprovisioning.
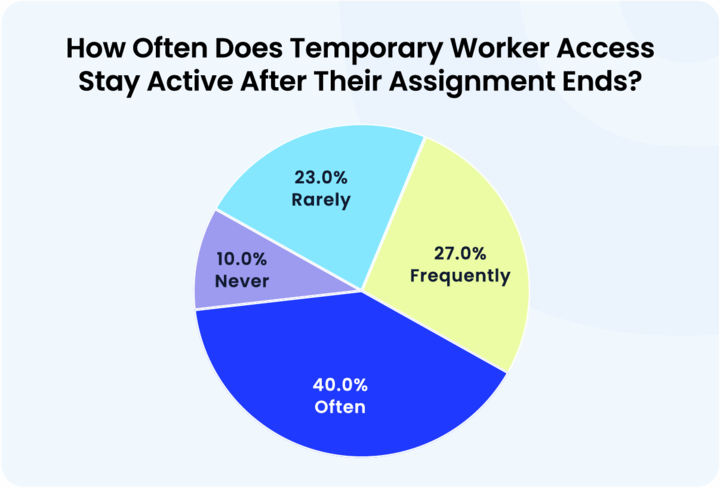
2d. Temporary access
Offboarding isn’t just for full-time employees. Contractors and temp workers need equal attention. These roles often involve short-term access to sensitive systems, making timely deprovisioning essential for security.
Key Takeaways
- 67% of organizations say temp workers retain access beyond their assignment"
- Only 10% have implemented Just-In-Time (JIT) controls.
3. Excess Access Privleges Is a Risk
3a. Privileged access reviews
I’ve seen it happen too many times, an employee changes roles, yet months later, they still have admin access to systems they no longer need. Manual access reviews are just too slow to catch these issues in time. By the time someone notices, privilege creep has already turned into a serious security risk., says Nidhi Jain, CEO and Founder, CloudEagle.ai
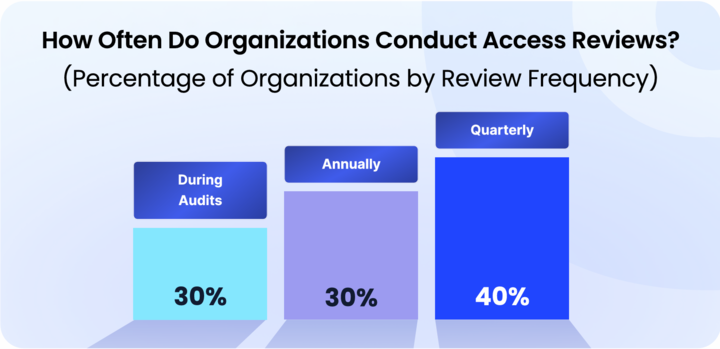
Key Takeaways
- 7 out of 10 organizations still rely on quarterly or annual access reviews.
However, the real question is, are they using AI for access reviews?

Key Takeaways
- 95% don t use AI-driven continuous reviews, leaving AI tools and access largely unchecked.
As AI adoption accelerates, enterprises must move from awareness to action, replacing outdated reviews with faster, smarter, and more secure governance, see for detailed data on privilege access violations by company size.
4. Risk of Traditional IAM Tool and Reactive Access Governance
Enterprises that fail to modernize identity governance are increasingly exposed to insider risk, shadow AI, and compliance violations. While many organizations believe their existing IAM tools are sufficient, our survey of CIOs and CISOs revealed a very different reality.
85% of organizations still rely on legacy IAM frameworks, tools built for on-prem environments and static access models. These systems were never designed to handle the rapid adoption of AI and SaaS applications, remote users, or the dynamic nature of AI-powered workflows.

Yet, they continue to be the default, giving leaders a false sense of control.
What’s clear is this: Traditional IAM tools were never built for today’s reality and treating them as a complete solution has only widened the governance gap.
4a. IT teams think ‘security is a CISO’s responsibility’
Many IT teams still treat IAM as the CISO’s responsibility, leading to fragmented governance, delayed deprovisioning, and rising insider threats. Even with IAM tools in place, access is often managed as a backend admin task without consistent coordination with security leaders.
Part of the problem? IT teams have historically been underfunded and overlooked when it comes to identity governance. Lacking the budget or mandate to modernize outdated IAM systems, they’ve been forced to rely on legacy tools that weren’t built for SaaS, AI, or hybrid environments.
Most believe they have access controls in place but in reality, policies are scattered, unenforced, and rarely updated.
When security, IT, and HR operate in silos, identity management becomes a case of the blind men and the elephant, each team only sees part of the picture, but no one has full visibility. CISOs enforce policies, CIOs focus on efficiency, and HR manages user records, yet critical access gaps fall through the cracks. Without collaboration, IAM turns into a fragmented system where security risks go unnoticed until it's too late, Karl Mosgofian, CIO, Gainsight.
4b. Poor app access provisioning & deprovisioning
IT teams reliance on IAM tools with limited integrations is forcing them to manage app access manually, resulting in delays, errors, and security gaps. “Just in case” provisioning leads to privilege creep, especially when new hires like SDRs require access to a wide range of tools often managed outside IT.
With no centralized control, revoking access becomes nearly impossible as 48% of former employees still retain access to business-critical apps after leaving. Manual deprovisioning across hundreds of tools, departments, and time zones is unsustainable.
4c. Excessive admin privileges & privilege creep
Admin access is powerful and it’s meant to be exclusive, granted only to those who truly need it, exactly when they need it. It’s not just IT teams either. Across Marketing, Sales, HR, and Finance, line- of-business users often end up with overprivileges they were never meant to have.
Overprivileged access is a compliance nightmare waiting to happen. If employees keep unnecessary permissions, it’s only a matter of time before sensitive data ends up in the wrong hands. Regulations like SOC 2 and GDPR demand strict access controls, but without regular reviews, companies are flying blind, and that’s a costly risk to take, Datta Junarkar, CIO - Maritime, Boeing.
As our survey shows, privileged access reviews are often done quarterly or annually, leaving long gaps where excessive permissions go unnoticed.
4d. Poor IAM hygiene leads to increased costs and IT security risks
IAM hygiene refers to the ongoing best practices and maintenance tasks that ensure your Identity and Access Management (IAM) systems are secure, accurate, and compliant.
Identity hygiene isn’t just about securing access; it’s about ensuring that the entire identity lifecycle is governed effectively. Yet, even after years of investment in IAM technologies, many organizations still struggle with poor IAM hygiene, leaving them exposed to security risks.
The apps and access crisis is real
Why 60% of SaaS Apps Are Invisible and Why It’s Riskier Than You Think
The Problem - Unseen Apps, Unchecked Access
Part II: A Strategic Framework to Solving Identity and Access Challenges
5. Building a Comprehensive IAM Framework
The access management challenges identified in Part I require a total shift from reactive, siloed approaches to a proactive, integrated IAM strategy.
Simply having an IAM tool is not enough; the core challenge is that IT doesn't manage all applications, and not everything sits behind traditional IAM systems. Enterprises cannot solve these complex problems through a patchwork of fragmented IAM tools and processes.
To strengthen IAM hygiene and reduce security risks, CIOs and CISOs need to:
- Eliminate organization silos
Unite security, IT, and HR teams under a shared identity management approach instead of operating separate, disconnected systems. - Automate access reviews & remediation
Replace time-intensive manual access reviews with continuous monitoring that automatically flags and removes inappropriate access. - Leverage AI for identity security
Deploy smart analytics to identify users with excessive permissions and unusual access patterns before they become security risks. - Enhance stakeholder engagement
Engage business leaders, HR, and end-users as active participants rather than leaving access decisions solely to IT and security teams.
Achieving these objectives requires more than point solutions or ad-hoc fixes. CIO s and CISOs must establish a comprehensive framework that addresses access challenges holistically.
The most successful implementations are built upon three interdependent pillars that work in harmony to create a robust identity governance ecosystem:

6.The Right Tools Augmented by AI Make All the Difference
Enterprises need AI-powered identity governance tools that can discover and secure the entire AI and SaaS landscape. Traditional tools no longer work because not all apps are managed by IT, nor does IT know about these applications operating in the shadow IT landscape.
Traditional access management breaks down in modern SaaS environments. Rule-based systems can't handle hundreds of applications with constantly shifting permissions, leaving IT teams blind to who has access to what. Manual reviews are impossible at scale, excessive privileges go undetected, and security gaps emerge faster than teams can close them.
AI-driven identity governance solves this by automatically detecting anomalies, predicting access needs, and continuously optimizing permissions across your entire AI and SaaS landscape.
6a. AI-augmented identity tools
Managing Identity Governance and Administration (IGA) is a time-consuming and costly challenge for enterprises.
However, the rise of generative & agentic AI, large language models (LLMs), and machine learning (ML) is transforming IGA, offering a lifeline to overworked IT and security teams.
I’m seeing a real shift in how CISOs approach IAM. It’s no longer a “set it and forget it” exercise, teams are using AI to monitor behavior and make smarter, ongoing access decisions. In one case, AI flagged employees hanging onto permissions they hadn’t used in months, and access was automatically revoked.
It’s not just about automation; it’s about making IAM proactive instead of reactive, raising the bar for security and compliance.
The need is clear: 60% of SaaS apps are invisible to IT, and 48% of ex-employees still have access to critical systems. Without smarter, continuous oversight, the risks (and costs) pile up quickly,” says Chet Mandair, CIO, Guidewire Software.
AI-driven identity governance is gradually gaining traction, according to our survey, 40% of enterprises are actively integrating AI into their IGA strategy to streamline access reviews, automate compliance, and enhance security.
But, let’s not get this mixed up. Artificial Intelligence (AI) is not replacing humans in IGA; it is augmenting their ability to manage identities proactively, reduce access risks, and automate governance at scale.
1. Automatically adjusting access based on role changes
Managing who gets access to what tools used to be a slow, manual task with traditional IAM tools. IT teams had to assign roles and update permissions every time someone changed jobs or joined a new team. But now, AI is making this much smarter and faster.
Instead of waiting for someone to notice access needs, AI looks at your role, what your teammates use, and your past activity to give you the right access from day one, without the approval and provisioning delays or back-and-forth.
Here’s how AI augmented IGA improves access:
2. Privileged access management
Privileged access isn’t just an IT issue, it extends across multiple departments, often in ways organizations don’t realize. While IT & Security teams are expected to have elevated permissions due to their role in managing infrastructure and user access, privilege creep is a growing problem across marketing and sales teams.
Many non-IT employees, especially Line-of-Business (LoB) staff, accumulate admin rights they don’t need, making them prime targets for cyberattacks, insider threats, and misconfigurations.
How AI is changing PAM:
Adopting just-in-time access is the closest thing to a 'never trust, always verify' model for user permissions. If you’re still leaving standing privileges unchecked, you’re giving attackers exactly what they need to exploit your systems, says Jim Palermo, CIO, Red Hat.
3. Enforcing Just-In-Time access for privileged users
We conducted a poll to understand how CISOs are adopting Just-in-time access and which departments leverage it the most. The results showed that companies are yet to completely implement JIT across the organization.
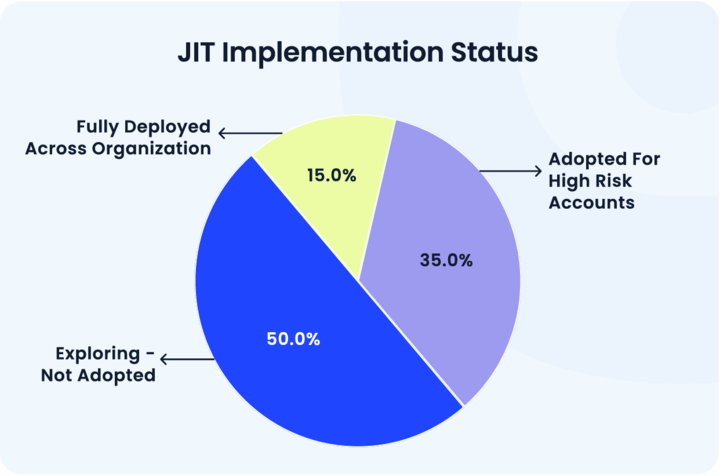
50% enterprises are still exploring how to implement Just-in-Time (JIT) access, while only 15% have fully adopted it across all departments. Another 35% apply it selectively to high-risk roles.
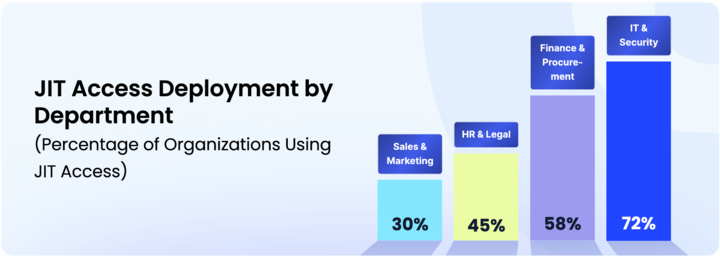
The chart shows that IT & Security (75%) leads in Just-in-Time (JIT) access adoption, which aligns with their high-risk privileged accounts and administrative roles. Finance & Procurement (58%) follows, as JIT access helps secure high-value transactions and financial approvals while minimizing standing privileges.
As organizations enhance their privileged access management (PAM) strategies with AI-driven automation, it will likely accelerate JIT adoption across all departments, reducing standing privileges and strengthening security.
7. Process - Automated Workflows and Continuous Governance
Even the most advanced AI tools might fall short without clear, streamlined processes. To be effective, modern IAM must be automated, continuous, and risk-driven, enabling real-time reviews, instant access revocation, and ongoing compliance.
7a. Streamlining employee onboarding & offboarding process
Onboarding and offboarding aren’t just security concerns; they directly impact Digital Employee Experience (DEX), IAM hygiene, and operational efficiency. When onboarding is slow and fragmented, new hires struggle to access the tools they need, leading to lost productivity.
Similarly, inefficient offboarding leaves behind orphaned accounts and lingering privileges, creating security vulnerabilities that put organizations at risk due to unauthorized access.
With AI, IT teams no longer have to visit each app manually to grant or revoke access.
1. Onboarding: Seamless access with an enhanced DEX
A well-structured onboarding process influences the employee’s first impression of their digital workplace. When access is delayed, new hires experience frustration and decreased engagement, impacting overall productivity.
AI-driven onboarding eliminates these inefficiencies by:
2. Offboarding: Eliminating orphaned accounts & privilege creep
While onboarding impacts DEX, offboarding is critical for IAM hygiene and security. Manual offboarding often leads to orphaned accounts that cybercriminals can exploit.
AI-driven offboarding ensures that the moment an employee leaves, their access footprint is cleaned up automatically.

7b. Intelligent compliance and audit readiness
40% of CIO’s & CISOs conduct access reviews quarterly, meaning that excessive or unnecessary privileges can remain active for months before being detected and 95% aren’t using AI to streamline access reviews, indicating that most enterprises still rely on slow, manual processes instead of automated, real-time governance.
During access reviews, teams get decision fatigue and just approve all the users, but if they get a filtered view of just the risky ones, they'd be paying way more attention to the right things.
1. AI augments IT teams with access reviews:
Instead of periodic manual audits, AI enables continuous, intelligent access reviews that remove outdated permissions before they become risks.
The goal isn’t just audit readiness, it’s scalable, risk-based access governance.
Instead of burdening IT teams with manual, repetitive access checks, AI provides continuous, risk-based automated reviews that only flag risky users for manual attention, allowing safe users to be auto-approved and giving teams a much smaller, focused list to review.
- Stronger Compliance
AI keeps access records audit- ready, eliminating compliance violations. - Faster Reviews
What used to take weeks is now
completed in real-time. - Reduced Attack Surface
Unused and excessive access is revoked automatically, stopping threats before they happen.
As the number of SaaS apps and privileged accounts continues to grow, AI-driven access reviews are no longer a luxury, they’re a necessity to keep organizations secure and compliant.
7c.Enhancing authentication with AI: Tackling the stolen credentials crisis
Stolen credentials remain the leading cause of data breaches, as our data confirms. Traditional authentication methods can’t keep up with modern threats. AI is changing the game, enabling adaptive, context-aware authentication that continuously analyzes user behavior and adjusts security measures based on real-time risk.
How Generative AI is strengthening authentication security
8. People: Cross-Functional Collaboration
Technology and processes alone cannot solve access management challenges without engaged stakeholders who understand their role in identity security.
Traditional IAM fails when it operates in silos, with IT and security teams working separately, business users confused about access requests, and executives disconnected from identity risks.
Effective IAM requires active participation from the C-suite (CIO, CISO, CFO, CPO), collaboration between IT and security teams, HR for lifecycle management, business leaders for access decisions, and end-users who understand security policies, creating a culture where identity governance becomes a shared responsibility across all organizational levels.
8a. IT teams should partner with security
For years, IT teams have operated with limited budgets, tasked with managing access, provisioning users, and supporting operations without the strategic recognition or resources of their security counterparts.
But that’s changing.
As identity becomes the new security perimeter, IT is no longer seen as just a support function. CIOs and IT leaders are being pulled into core security conversations and increasingly, their budgets and responsibilities are starting to look like those of the CISO.

What IT teams should do: Seven key areas
Smart organizations are embracing this shift. They're empowering IT to partner with security, embed controls at every access point, review applications collaboratively, and use AI to automate governance at scale.
IGA is no longer just about provisioning access. It s about protecting the business. The faster IT teams take the lead, the stronger their security posture will be.
8b. Appointing a CIDO to implement IAM framework
When security, IT, HR, and finance work in silos, access gaps go unnoticed, privilege creep builds up, and compliance risks escalate. Without a unified approach, IAM remains a fragmented mess instead of a business enabler. The future of identity management depends on breaking down these silos and making IAM a shared responsibility across the enterprise, says Nidhi Jain, CEO and Founder, CloudEagle.ai.
Access management isn’t just the CISO’s problem; it’s a team sport. While security leaders often take the heat for identity-related breaches, the reality is that CIOs, CFOs, CPOs, and business leaders all play a critical role in shaping access governance.
Organizations that foster strong collaboration between security, IT, and business teams see greater success with identity and access strategies. When CISOs balance operational IAM with strategic planning and stakeholder engagement, identity becomes a unifying force, aligning security initiatives with broader business goals and breaking down silos that hinder progress.
1. CISOs: Setting security policies, but lacking enterprise-wide enforcement
Chief Information Security Officers (CISOs) are responsible for defining and enforcing IAM security policies, including least privilege access, Zero Trust frameworks, and identity governance best practices. However, their effectiveness is limited without executive buy-in from other business leaders.
2. CIOs & IT Teams: Managing IAM systems, but lacking visibility across departments
CIOs and IT teams handle the technical implementation of IAM solutions, ensuring identity systems function properly across SaaS, on-prem, and cloud environments. However, they cannot single- handedly track every access change across all departments.

3. CFOs & Procurement Leaders: Overlooking IAM risks in SaaS & shadow IT
CFOs and procurement teams are responsible for managing IT budgets and vendor contracts. However, they often underestimate the financial and security risks associated with unchecked SaaS sprawl and Shadow IT.
4. HR & department heads
HR and department heads play a direct role in IAM by managing employee roles, onboarding, and offboarding. However, they often fail to revoke access when employees switch positions or leave the company, leading to orphaned accounts and insider threats due to overprivileged access during onboarding.
For too long, access management has been treated as a hot potato that is tossed between security, IT, HR, and department heads without a clear sense of ownership.
5. The Identity and Access Leader - CIDO
As enterprises accelerate digital transformation, Identity and Access Management (IAM) can no longer be treated as a standalone IT function; it must be integrated into business strategy, security frameworks, and operational efficiency models.
A Chief Identity Officer (CIDO) is the missing link to ensure IAM shifts from a reactive, compliance- driven necessity to a proactive enabler of business value.
Historically, IAM has been seen as a technical challenge, with fragmented control across IT, security, HR, and compliance teams. This results in siloed decision-making, misconfigurations, and excessive administrative burden.
A CIDO would break silos and elevate IAM from an operational function to a strategic operation. This role ensures that IAM is not just an IT responsibility but a business-critical function that enhances security, efficiency, and digital transformation.
They can directly influence an organization’s broader strategy by maximizing the value of IAM investments and driving the cultural shift needed to integrate IAM across security, compliance, and business teams. By embedding IAM into core business processes, the CIDO fosters productivity, user experience improvements, and operational efficiency.
This role would bridge security, business enablement, and compliance, ensuring IAM is recognized as a business-critical function rather than just an IT concern.
From Manual Chaos to AI-Driven Control
How enterprises can modernize identity governance before It breaks
Despite the clear advantages of AI-driven identity governance and administration, many organizations still struggle to implement it effectively. While AI enhances IAM hygiene, strengthens security, and improves operational efficiency, several barriers prevent companies from fully embracing AI-powered identity governance.
9. Building Confidence in AI-Powered Security Automation
CISOs or security teams are increasingly recognizing AI as a strategic enabler for modern access management. Rather than viewing AI adoption as an all-or-nothing decision, forward-thinking organizations are embracing intelligent automation that enhances human expertise while maintaining appropriate control.
The Human-AI Collaboration
Modern AI-powered IAM solutions are designed for transparency and collaboration, not human replacement. Today's platforms provide:
- Explainable AI Decisions
Advanced systems offer clear reasoning for access recommendations, showing the data patterns and risk factors that inform each decision. - Intelligent Risk Calibration
AI excels at processing vast amounts of access data to identify genuine risks while minimizing business disruption through sophisticated pattern recognition. - Regulatory Alignment
Leading organizations are establishing best practices for AI governance that demonstrate due diligence and responsible automation to regulatory bodies.
Nidhi Jain believes, The most successful IAM implementations leverage AI to accelerate human decision-making. Organizations that embrace this partnership model see both enhanced security and improved operational efficiency.
Smart organizations implement AI-powered IAM through a maturity-based approach that builds confidence and capability:
.png)
This progressive approach enables enterprises to harness AI s transformative potential while maintaining the confidence and control that security leaders require.

10. Embracing The New Normal
Implementing AI-driven identity governance isn’t just a tech shift, it’s a cultural change. For many CIOs and CISOs, especially those with traditional rule-based IAM systems, this transition can feel like stepping into the unknown.
The key is to introduce AI thoughtfully, beginning with high-impact, low-friction use cases as outline in the previous section where it can clearly augment existing workflows. By automating repetitive tasks like access reviews and anomaly detection, AI enables CISOs to shift their focus toward strategic decision-making and risk analysis.
The communication aspect is equally important. Leadership needs to be transparent about how roles will evolve, not disappear. When security professionals understand that AI will handle routine tasks so they can focus on more strategic work, resistance often transforms into enthusiasm, says Nidhi Jain.
Enterprises that are leading the way in AI-enabled access management understand that successful implementation is as much about people as it is about technology.
Change management, transparent communication, and role clarity are essential. When teams are brought along the journey, with training, context, and a sense of ownership, they don’t resist the future; they help build it.

11. Aligning AI with Compliance: Turning Uncertainty into Advantage
As AI becomes more central to access governance, highly regulated industries like finance, healthcare, and government are redefining how compliance can evolve alongside innovation. While regulations such as GDPR, HIPAA, and SOX may not explicitly reference AI, their core principles of accountability, transparency, and human control remain highly relevant.
Rather than viewing this ambiguity as a barrier, leading enterprise CIOs and CISOs are embracing it as an opportunity to enhance compliance practices with AI, not replace them. By ensuring human control remains essential, especially for sensitive or high-impact access decisions, enterprises are demonstrating that AI can strengthen controls rather than weaken them.
CIOs are finding that success lies in clear documentation and structured AI governance frameworks. When teams can articulate how AI supports compliance, where it applies, how it works, and when human review steps in, auditor confidence increases.
Creating this level of clarity not only satisfies regulatory expectations, it also builds internal trust across security, risk, and legal teams. The most mature programs are now leveraging AI as a compliance enabler, proving that intelligent automation and strong governance can go hand in hand.

12. Reshaping Identity Governance as a Strategic Business Enabler
While AI-driven identity governance brings immense potential, successful adoption often relies not on technology, but on culture and communication.
Many C-suite leaders continue to view IAM as a technical function rather than a strategic business enabler.
However, organizations where CISOs communicate in business terms, not just technical language, secure 60% more funding for their initiatives (Gartner). The takeaway? The message matters.
CIOs or security leaders must move beyond jargon like “entitlement mining” or “attribute-based access control” and instead connect with what matters to the business: risk reduction, operational agility, customer experience, and regulatory confidence.
1. Leadership Authority and Alignment
Effective IAM leadership today is about mindset, influence, and alignment. The most successful programs are led by practitioners who:
- Position IAM as a strategic enabler rather than a backend system
- Report into executive leadership to secure buy-in and visibility
- Use business-aligned storytelling to drive urgency and investment
In fact, enterprises that elevate IAM to a C-level conversation see AI-driven governance initiatives implemented 80% faster, thanks to streamlined decision-making and broader alignment.
2. Changing the Narrative
CISOs must evolve from reporting technical KPIs to telling stories with business impact. This shift highlights the value of identity governance in achieving enterprise goals.
Instead of
- Number of access reviews completed
Communicate
- Reduced onboarding time from days to minute.
- Decreased access-related security incident.
- Improved customer experience via frictionless authentication
- Assured regulatory compliance with measurable risk reduction
13. Cost and Resource allocation
While IAM is often underfunded, forward-looking organizations are shifting the narrative, from reactive spending to strategic investment. Instead of waiting for a breach or audit issue, they’re embracing AI-driven identity governance as a way to reduce risk and unlock long-term efficiency.
IAM is often the most underfunded yet mission-critical part of security. But those taking a proactive approach, starting with automation and AI-driven governance, are not just reducing risk, they’re unlocking efficiency and long-term cost savings, Chetna Mahajan, Global CDO & CIO, Webflow.
A phased approach is proving most effective for enterprises that want to modernize without overwhelming their resources. Starting with high-impact, low-barrier initiatives like:
- Automating access reviews
- Streamlining onboarding & offboarding
- Removing dormant accounts with data- backed triggers
These “quick wins” provide measurable ROI and help IAM teams build the business case for broader transformation.
Organizations that prioritize IAM funding today will not only reduce long-term security risks but also establish a foundation for scalable, AI-powered identity governance that enhances both security and business agility.
This incremental approach transforms what might seem like an insurmountable cost barrier into a series of manageable, value-generating steps in adopting AI to streamline IGA and enhance IAM hygiene.

Governance Is Everyone’s Job
Why Access Management Can’t Be Solved by Security Alone
14. Zero Trust: No One Gets In Without Ongoing Proof
The traditional perimeter-based security model is no longer sufficient in an era where cloud-based applications, remote workforces, and hybrid IT environments dominate. Zero-Trust Architecture (ZTA) is emerging as the gold standard for identity and access management, ensuring that no individual, whether internal or external, is automatically trusted.
At the core of Zero Trust is the belief that every access request must be continuously verified based on identity, context, and risk before granting access to any resource.
This shift is particularly critical for CISOs, who must realign their identity and access management (IAM) investments to enable an identity-first security approach that forms the foundation of an organization’s cybersecurity strategy.
To deliver identity-first security, organizations should adopt the three C’s framework:
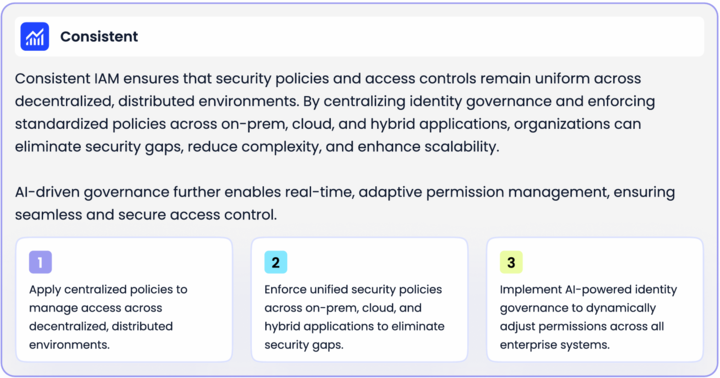


Consistent
Consistent IAM ensures that security policies and access controls remain uniform across
decentralized, distributed environments. By centralizing identity governance and enforcing standardized policies across on-prem, cloud, and hybrid applications, organizations can eliminate security gaps, reduce complexity, and enhance scalability.
AI-driven governance further enables real-time, adaptive permission management, ensuring seamless and secure access control.
- Apply centralized policies to manage access across decentralized, distributed environments.
- Enforce unified security policies across on-prem, cloud, & hybrid applications to eliminate security gaps.
- Implement AI-powered identity governance to dynamically adjust permissions across all enterprise systems.
Context-Aware Access
Context-aware access ensures that authentication and authorization decisions are based on real-time contextual signals rather than static rules. By analyzing user behavior, device posture, access patterns, and risk indicators, IAM systems can dynamically adjust access permissions and security requirements.
- Use contextual data (device type, location, access patterns) to make intelligent access
decisions. - Identify context sources (e.g., endpoint security posture, real-time threat intelligence) and integrate them into access controls.
- AI continuously analyzes contextual signals, allowing for adaptive authentication and risk-based access approvals.
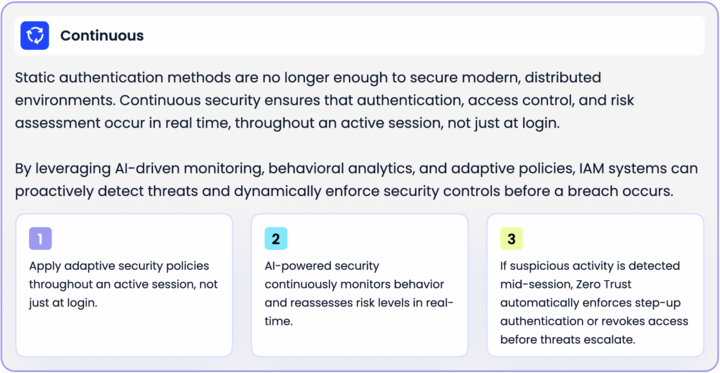
Continuous
Static authentication methods are no longer enough to secure modern, distributed
environments. Continuous security ensures that authentication, access control, and risk assessment occur in real time, throughout an active session, not just at login.
By leveraging AI-driven monitoring, behavioral analytics, and adaptive policies, IAM systems can proactively detect threats and dynamically enforce security controls before a breach occurs.
- Apply adaptive security policies throughout an active session, not just at login.
- AI-powered security continuously monitors behavior and reassesses risk levels in real- time.
- If suspicious activity is detected mid-session, Zero Trust automatically enforces step-up authentication or revokes access before threats escalate.
Zero-Trust Architecture is no longer optional, it is essential in 2025. By adopting an identity-first security approach built on Consistency, Context, and Continuous security, organizations can ensure dynamic, adaptive protection across all access points.
CISOs must shift from static, perimeter-based controls to a unified, AI-driven security framework that continuously verifies identity, enforces least-privilege access, and adapts to real-time risks.
15. Managing Machine Identities and Endpoint-Centric Security Controls
Traditional IGA has centered on human users, but machine identities, such as API keys, service accounts, IoT devices, and bots, now vastly outnumber them. These machine identities operate continuously, interact autonomously, and access sensitive systems at scale, introducing significant and often overlooked security risks.
IGA is evolving to meet this challenge. In 2025, organizations are extending identity governance frameworks to manage these high-velocity identities with the same rigor as human users.
1. Automated Lifecycle Management: Modern IGA platforms are implementing sophisticated credential management systems for machine identities. These systems automatically
- Track the creation and usage of machine credentials across environment
- Enforce time-bound access with automatic expiration
- Rotate credentials based on risk assessment and usage pattern
- Revoke access when anomalous behavior is detected
- Document machine identity dependencies to prevent service disruptions
This automation preserves uptime while minimizing credential exposure.
2. Continuous Endpoint Verification: The traditional perimeter-based security model is giving way to AI-powered continuous verification of endpoints, with systems that:
- Verify device security posture before granting access to resource
- Monitor endpoint compliance with security policies in real-time
- Automatically quarantine non-compliant device
- Implement granular access controls based on device risk scores
This approach ensures that even legitimate machine identities cannot be leveraged if there are signals received that indicate risk.
AI-Driven Risk Assessment: Gen AI has become essential for managing machine identities at scale. AI systems analyze:
- Behavioral patterns to identify potential compromise
- Access privileges relative to actual usage need
- Context-aware risk scoring that adapts to changing condition
- Relationships between machine identities to detect lateral movement risks
These assessments enable security teams to prioritize risks and implement appropriate controls.
Together, these advancements close visibility gaps, reduce attack surfaces, and make machine access fully auditable, turning one of the enterprise’s biggest blind spots into a controllable, secure layer of access governance.
16. Passwordless Authentication Is Accelerating
Despite years of awareness, password-based security remains vulnerable to breaches. In response, organizations are shifting toward password-less authentication methods that offer stronger protection and better user experience.
Biometrics and Passkeys such as facial recognition, fingerprint scanning, and behavioral biometrics are replacing passwords across devices. Meanwhile, FIDO2 standards and OS-native passkeys (from Apple, Google, Microsoft) are enabling secure, cross-platform login without credential reuse.
AI-powered authentication goes a step further, using continuous behavioral analysis and contextual signals to verify users in real time, minimizing friction for employees while shutting out attackers
- Real-time behavioral analysis detects anomalies that might indicate account compromise
- Context-aware authentication adjusts requirements based on risk factor.
- Implicit authentication happens automatically without interrupting user workflow.
- Multiple signals are combined to create confidence scores rather than binary yes/no decisions
This approach minimizes friction for legitimate users while maintaining strong security barriers against unauthorized access.

From Reactive to Identity-First Security
How Enterprises Can Move from Reactive Controls to Proactive, Intelligent Governance
Conclusion
Identity Is the New Perimeter And It’s Under Siege
As SaaS and AI adoption accelerates, the enterprise attack surface is expanding faster than traditional identity and access governance can keep up. Orphaned accounts, excessive privileges, shadow AI and unsanctioned tools have turned identity into the new weak link and the new front line.
But this is no longer a challenge that one team can solve alone.
The responsibility for IGA no longer falls solely on IT or security. To effectively mitigate risk, CISOs, CIOs, IT, HR, and business leaders must align their strategies, break down silos, and operationalize identity as a shared responsibility.
Outdated quarterly reviews and spreadsheet-driven access audits have failed to scale with today’s complexity. Organizations must now move toward AI-driven, real-time access governance that is contextual, continuous, and collaborative.
The path forward is clear:
- Replace static workflows with AI-powered, behavior-based provisioning?
- Enforce least-privilege and Just-in-Time access, everywhere?
- Automate deprovisioning and access reviews to eliminate blind spots?
- Embed identity strategy across all functions, not just security.
With AI augmented identity governance and administration, organizations can predict problems before they happen and adjust automatically. This keeps the business safe while helping it grow.
Today, managing user access isn't just an IT job anymore - it's become a key business priority that requires teamwork across departments.
This shift not only prevents breaches and regulatory risks but sets the foundation for a future where access is intelligent, autonomous, and secure in an evolving AI landscape.
Appendix A - Commonly Used AI Tools
Survey results showing the most common AI tools used across various departments in etnerprises.
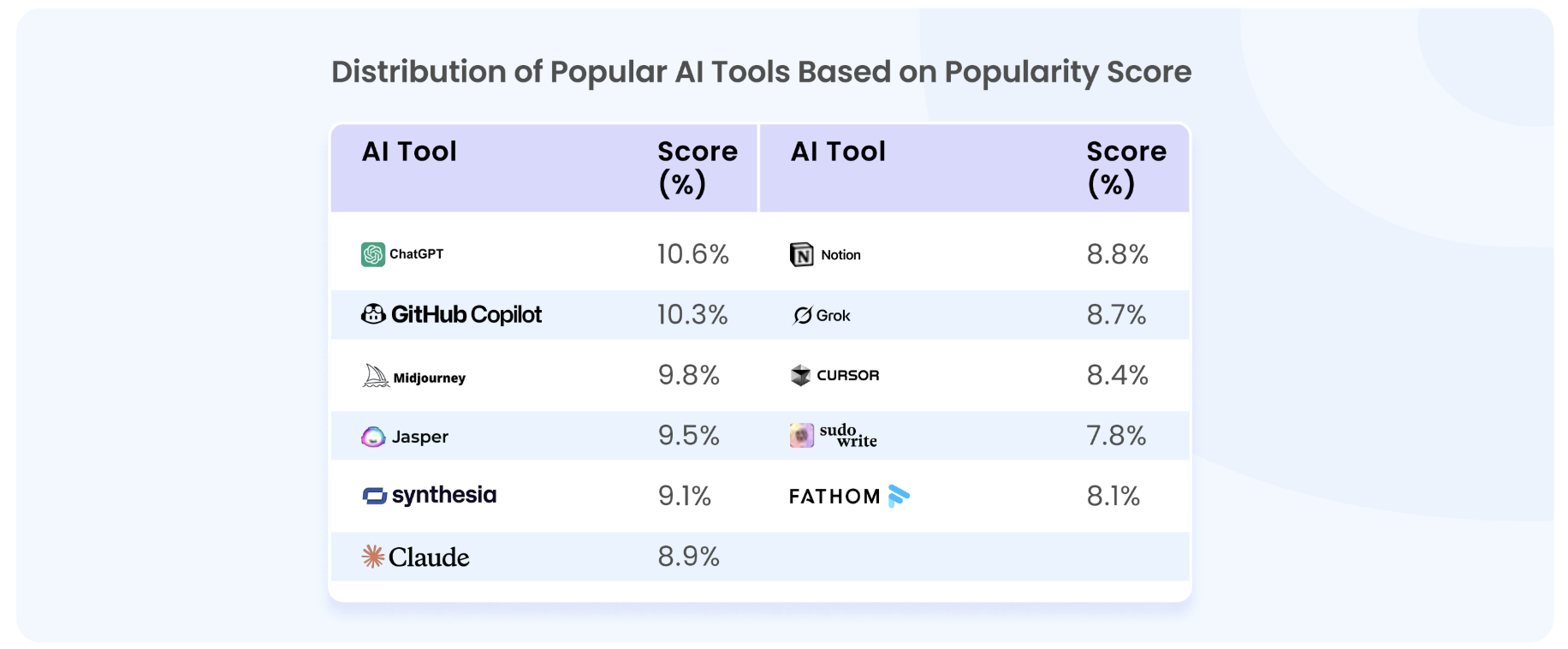
AI tools like ChatGPT, Jasper, and Notion AI are used for contract writing, financial analysis, and customer data processing. However, it's important to recognize that many AI models store or learn from input data, which can make data deletion challenging after submission.
This has implications for compliance with data privacy regulations such as GDPR, HIPAA, and SOC 2. CIOs now have a valuable opportunity to review how these tools are used and ensure their practices align with legal and regulatory standards.
Appendix B - Overprivileged Access Security Impact Survey
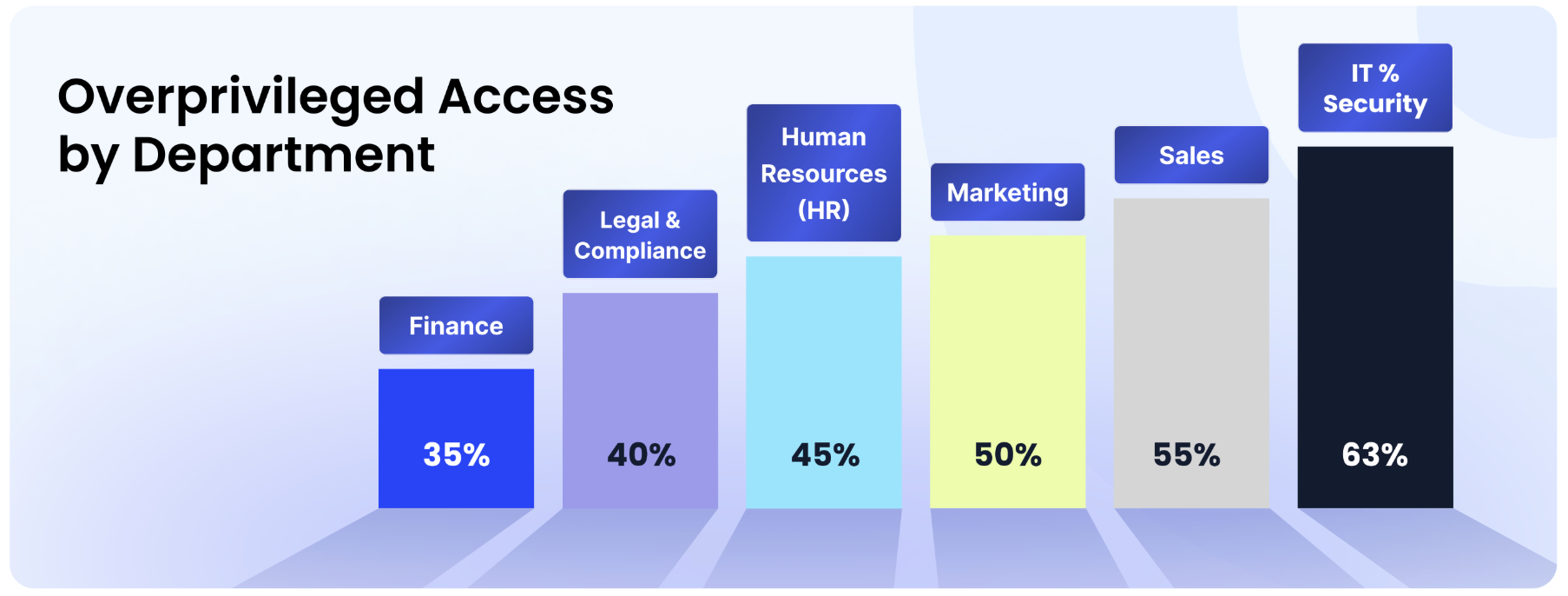
Sales and HR rank highest in overprivileged access, as they handle sensitive customer data and employee records, often retaining unused permissions. Financeand Legal have relatively lower privileged access but still pose risks due to their control over financial transactions and contracts.
The real opportunity lies in addressing overprivileged access among non-IT or Line-of-Business (LoB) users. Unlike IT admins who require elevated permissions, LoB employees in Finance, Sales, Marketing, and HR often accumulate admin rights they don't actually need.
But that’s not the end, check the survey results on security incidents caused by overprivileged access.
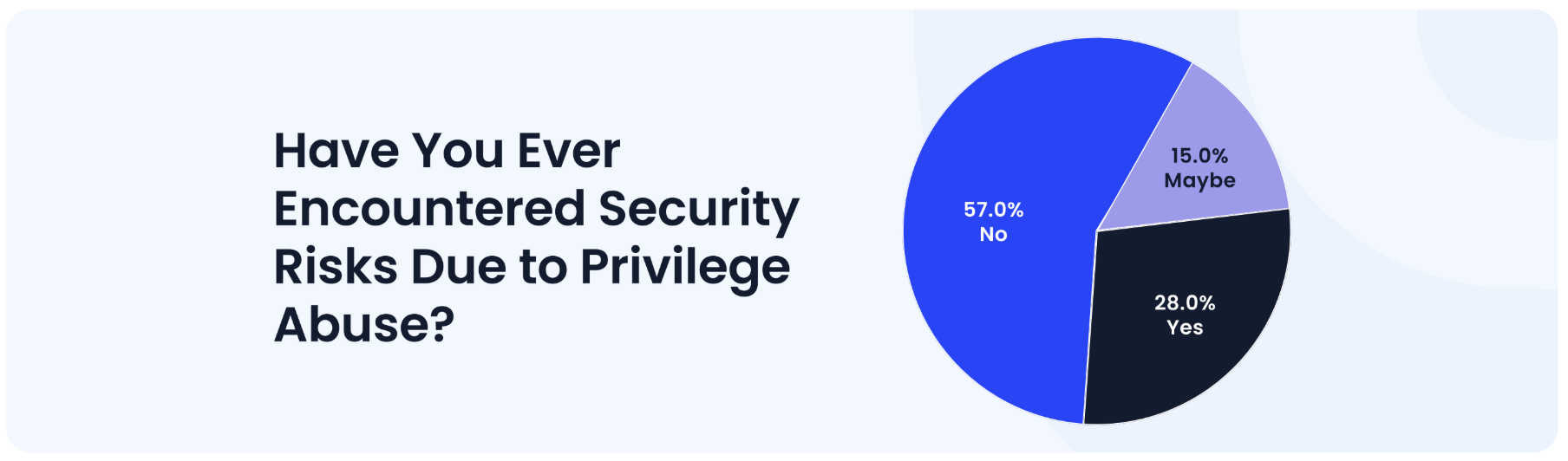
28% experienced major security incidents from overprivileged access, creating dangerous blind spots and opportunities to have strong privilege controls in place to prevent risks.
Appendix C: Data Breach Categories Survey
Detailed breakdown of the most frequently compromised data types in security breaches, based on analysis of CloudEagle.ai survey.
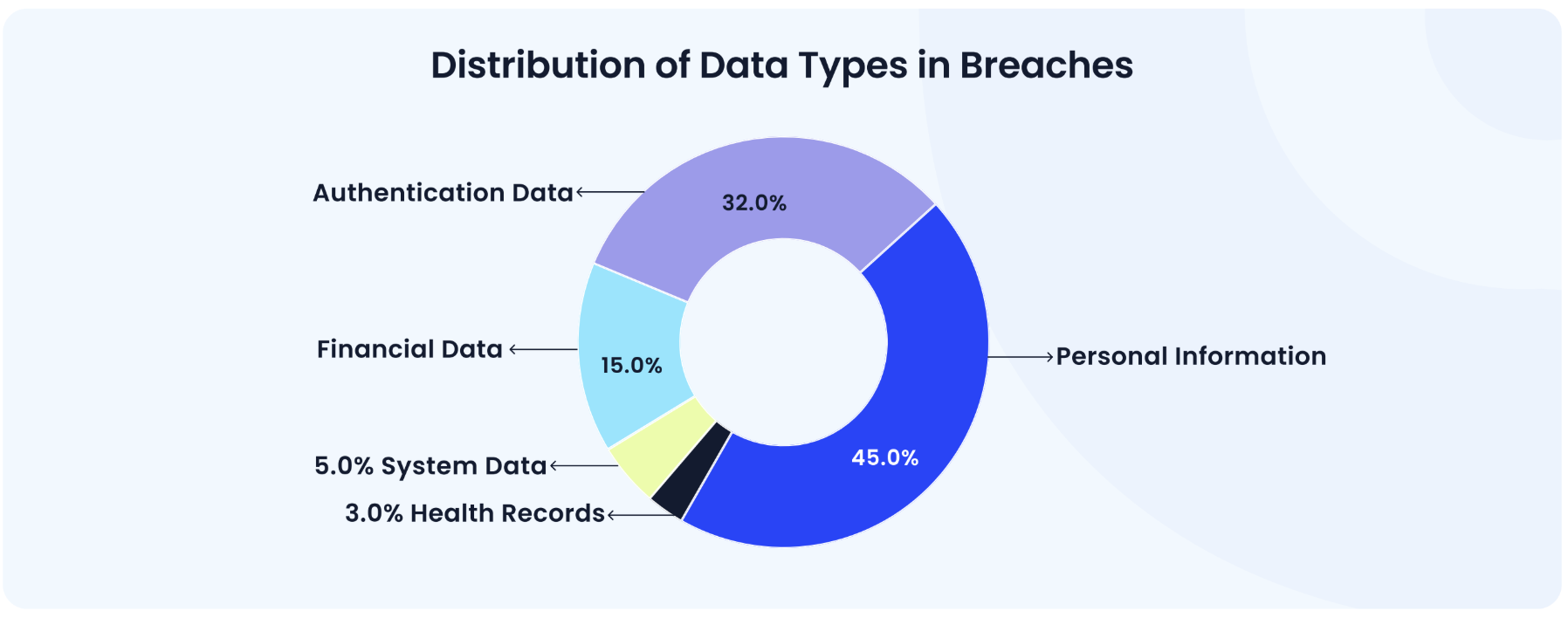
The dominance of personal and authentication data breaches highlights a critical reality: attackers don't hack systems, they simply login using stolen credentials. This pattern shows why protecting identity information is essential for organizational security.
Appendix D - Employee Onboarding Time Analysis
Detailed breakdown of onboarding duration across different departments and the key challenges affecting these timelines.
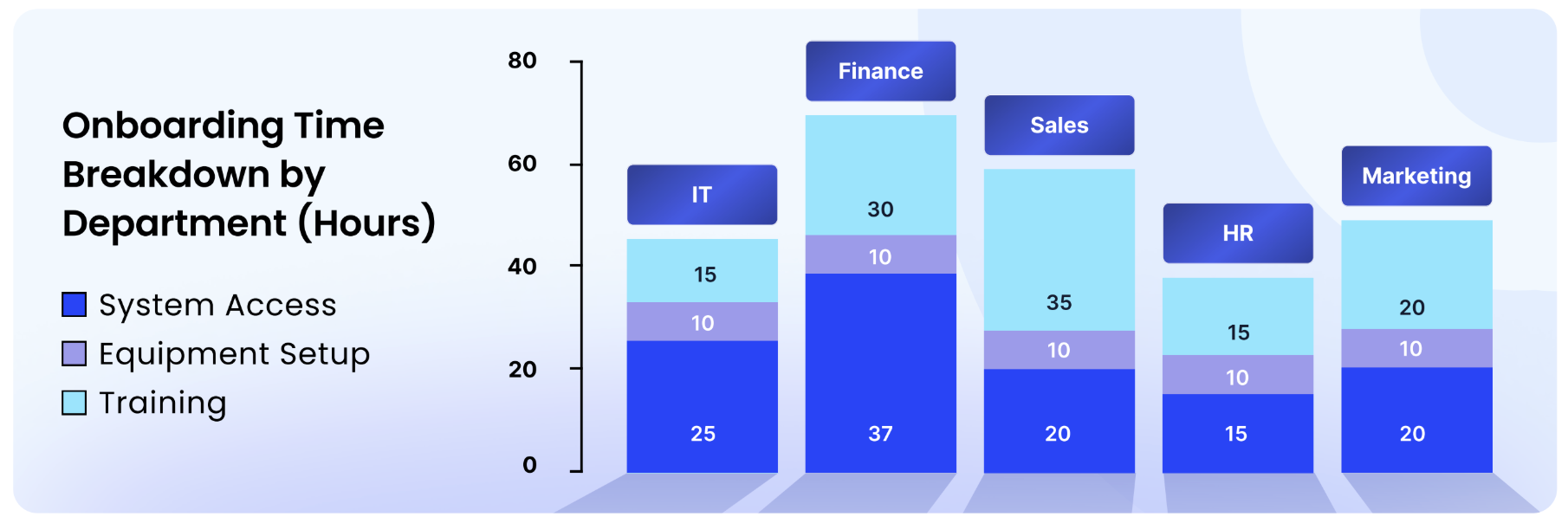
While onboarding timelines vary by department, Finance and Sales typically take longer due to their broader access needs and specialized training
- Finance has the longest onboarding time, exceeding 65+ hours, likely due to complex system access approvals and compliance training
- Sales follows closely, reflecting the need for CRM setup, access to client data, and role-based permissions
- Marketing and IT have moderate onboarding times, balancing technical access with training needs
- HR has the shortest onboarding time, as their access is often limited to HRIS and internal tools.
To better understand the challenges in onboarding, we conducted a poll among our prospects and customers.
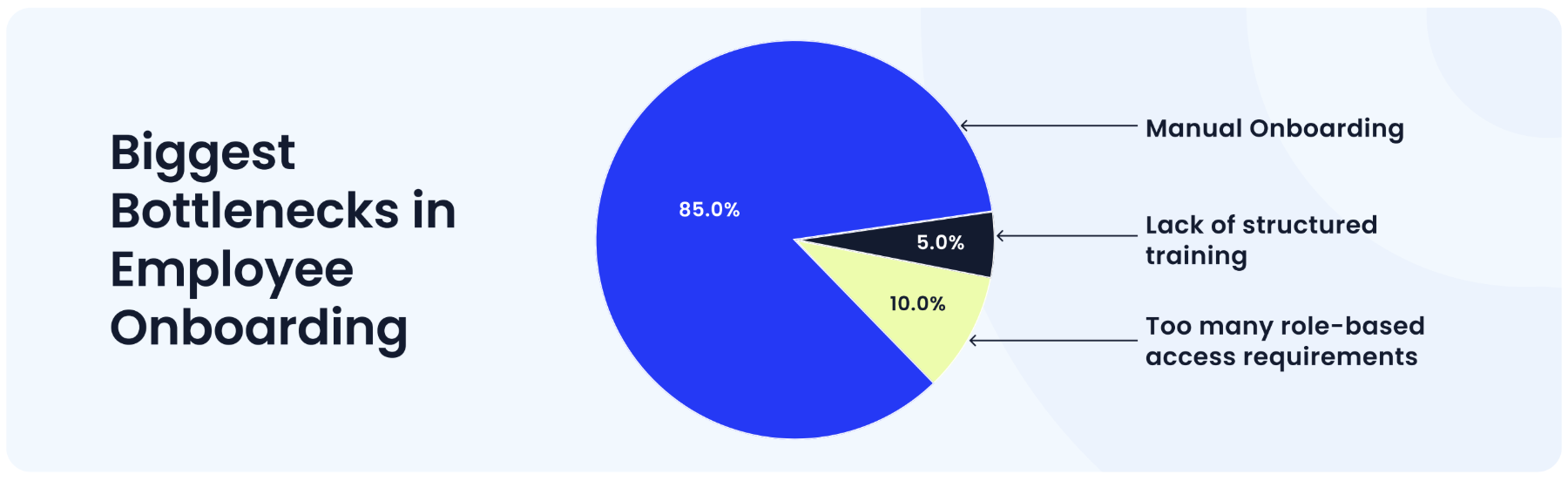
The results show that IT teams are stuck with manual processes that slow everything down. Traditional IGA tools can't solve this due to limited integrations, but AI-led systems can streamline employee onboarding by automating these workflows end-to-end.
Appendix E - Digital Employee Experience Impact Analysis
Data showing how onboarding delays and access provisioning issues affect overall Digital Employee Experience (DEX) metrics.

Manual provisioning creates the most friction in employee onboarding, dramatically impacting the digital experience. While role complexity causes some delays, the real problem is hands-on IT work that could be automated.
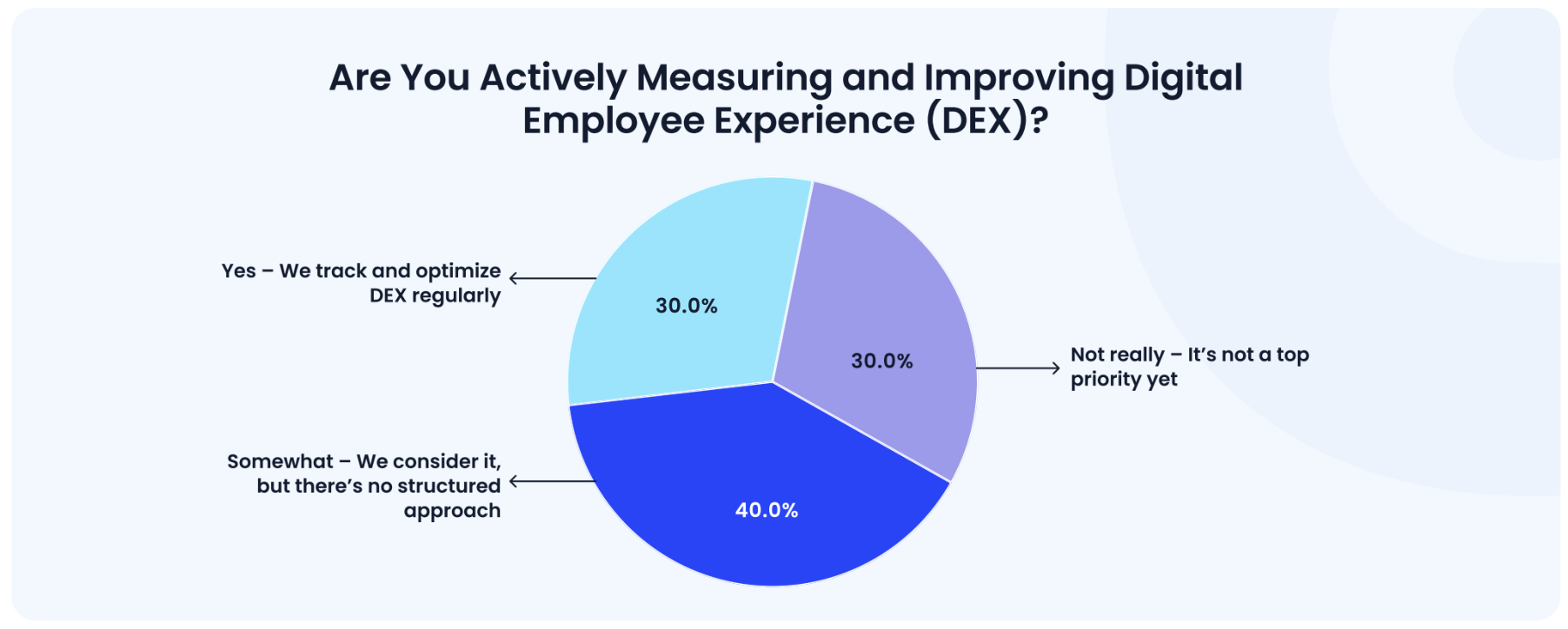
While most organizations recognize the importance of digital employee experience, only 40% are actively measuring it. The majority are still in early stages or taking ad-hoc approaches, revealing a significant gap between awareness and systematic action.
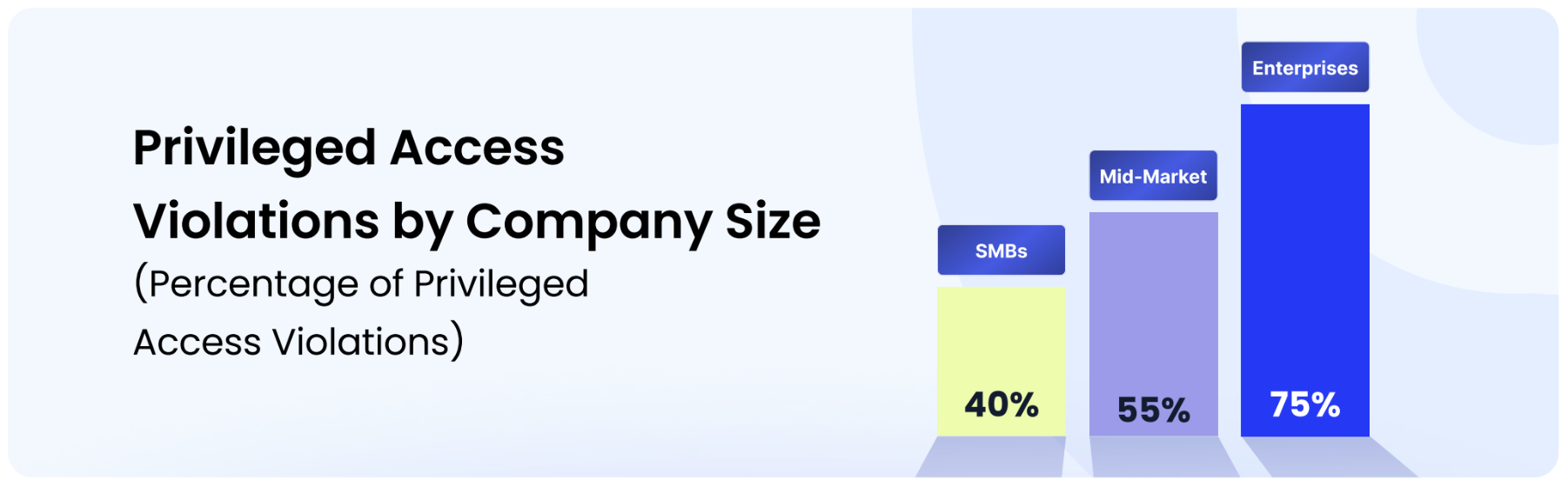
Appendix F - Privilege Access Violations by Organization Size
While smaller businesses have fewer privileged accounts, they often lack structured access controls, leading to mismanaged admin permissions. As companies grow, privilege creep increases, with more employees gaining admin rights they don’t necessarily need.
Enterprises with 1000+ employees have the highest violation rate, as they deal with complex access hierarchies, legacy permissions, and decentralized admin roles, making privilege abuse harder to track.
By strengthening access controls with restrictive permissions and transparent monitoring, enterprises ensure the right people have the right access at the right time, rebuilding customer trust and protecting shareholder value.
.webp)



.webp)
.webp)
.webp)
.webp)
.webp)